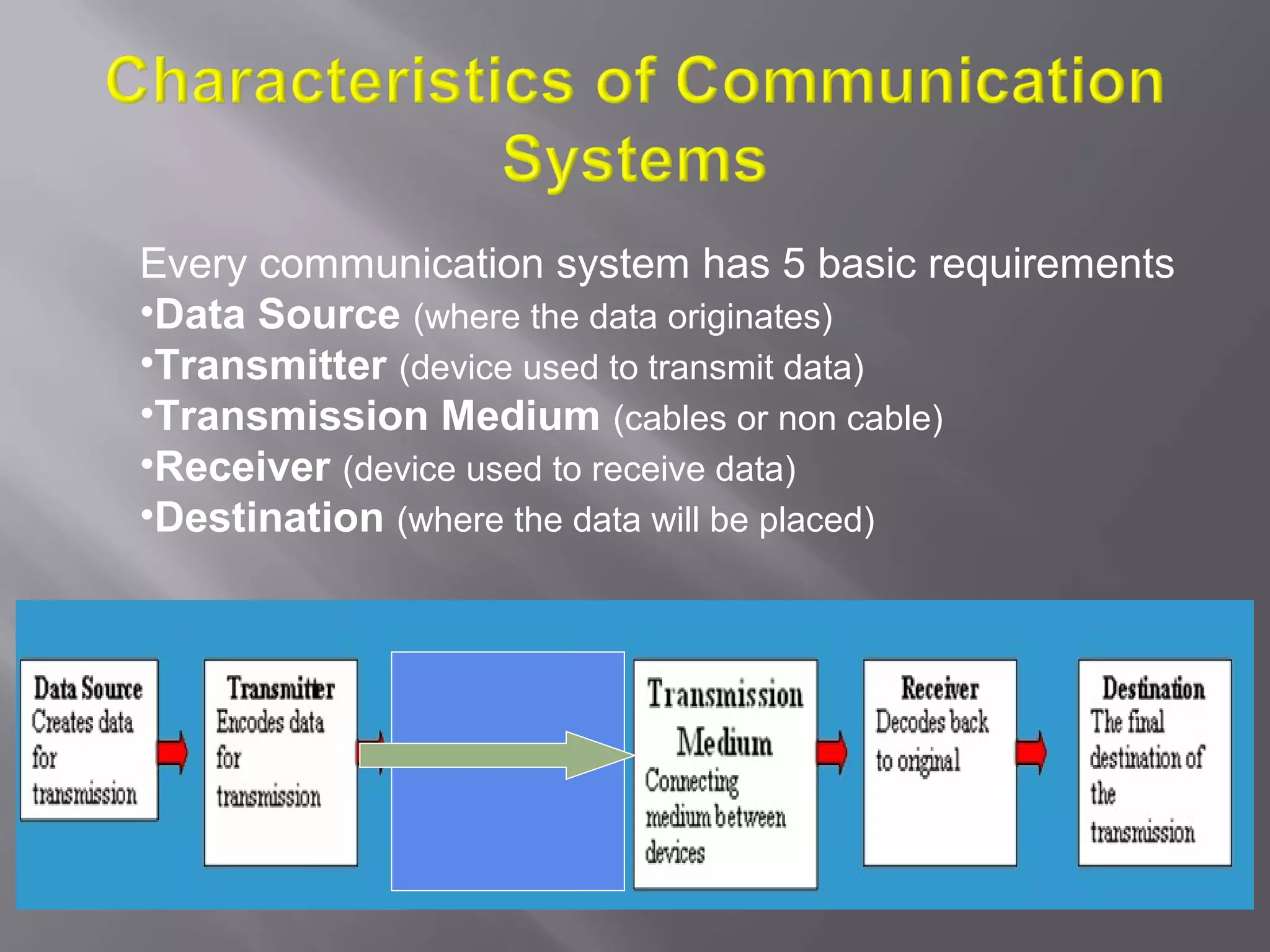
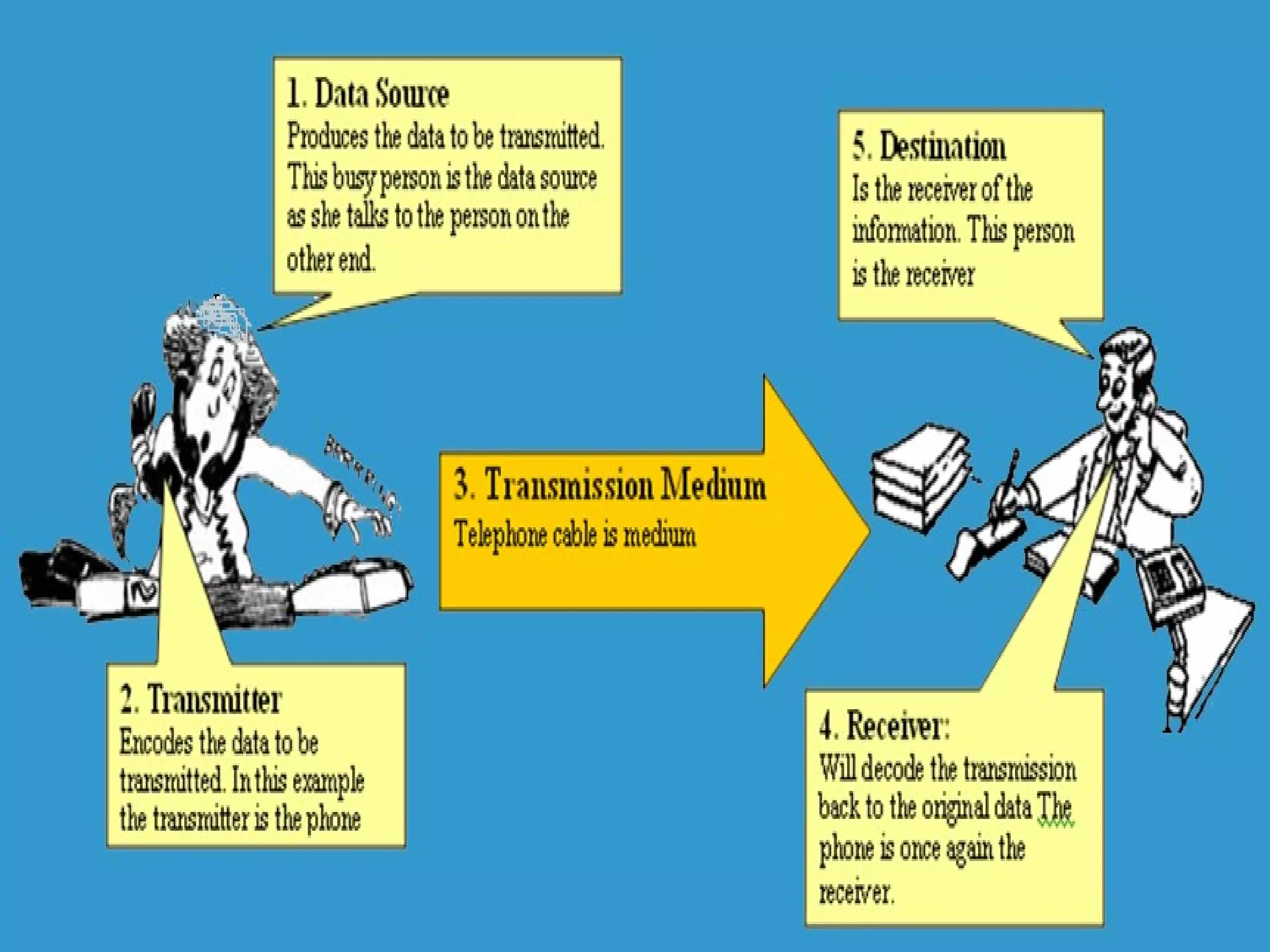
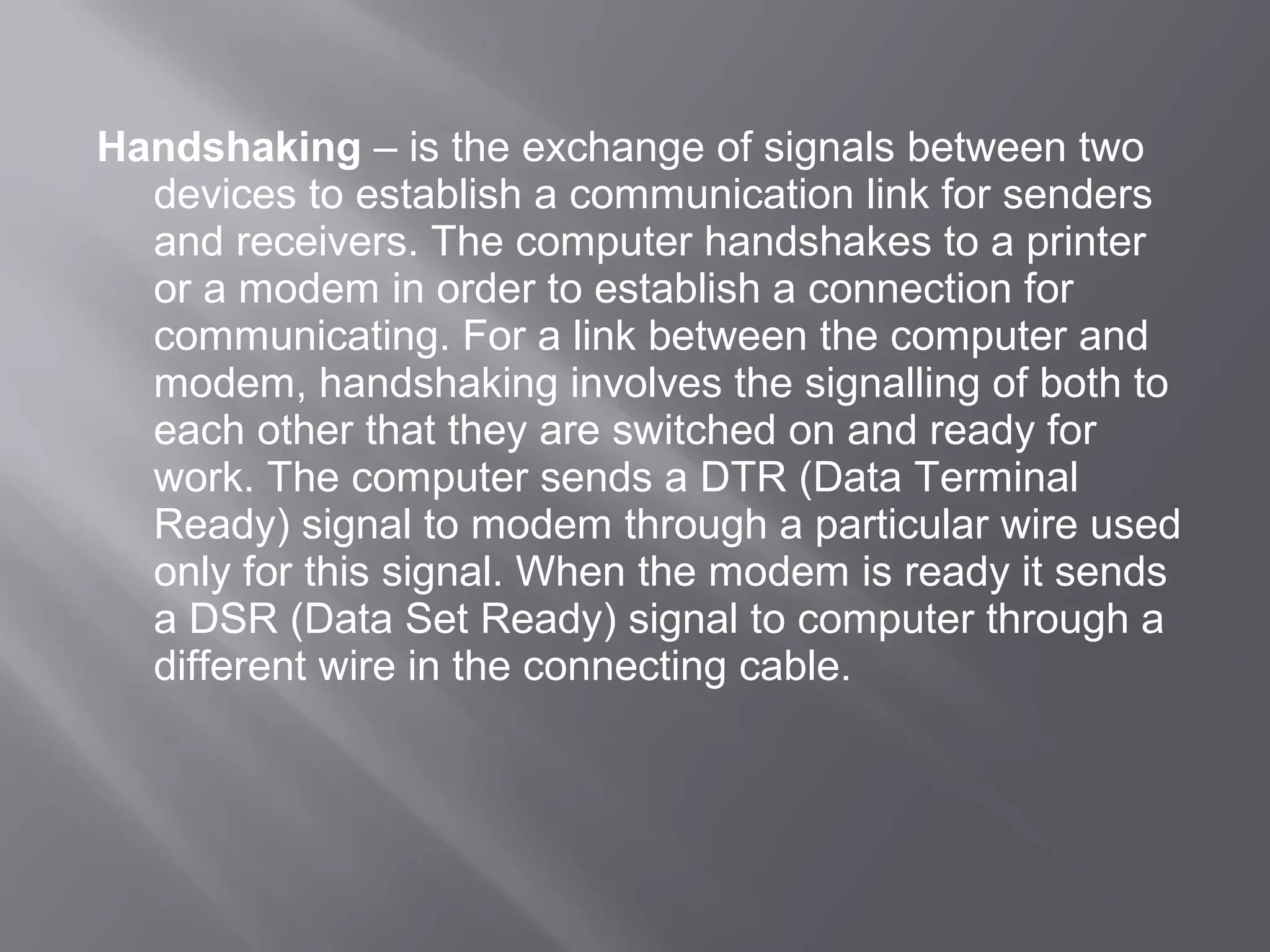
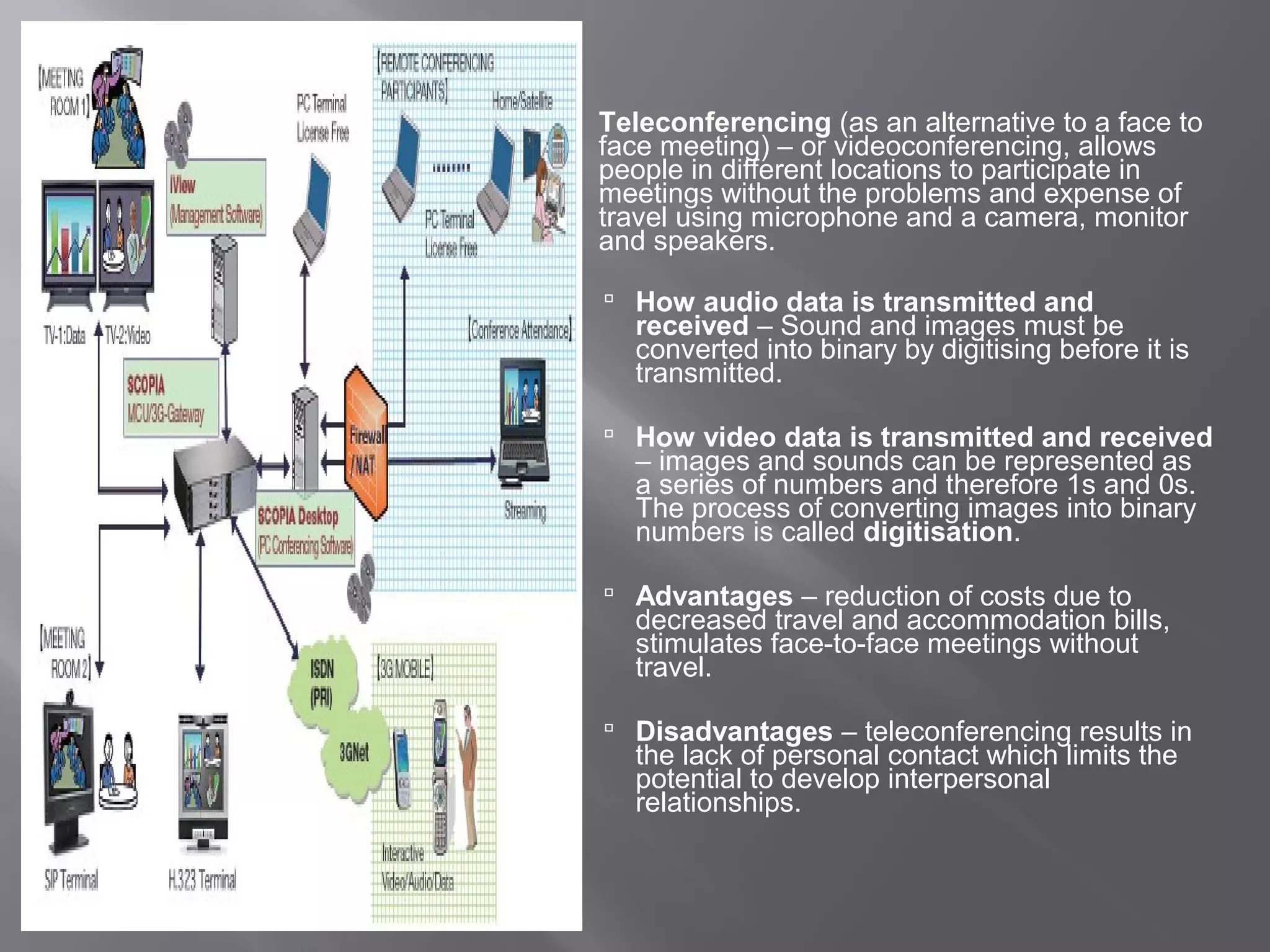
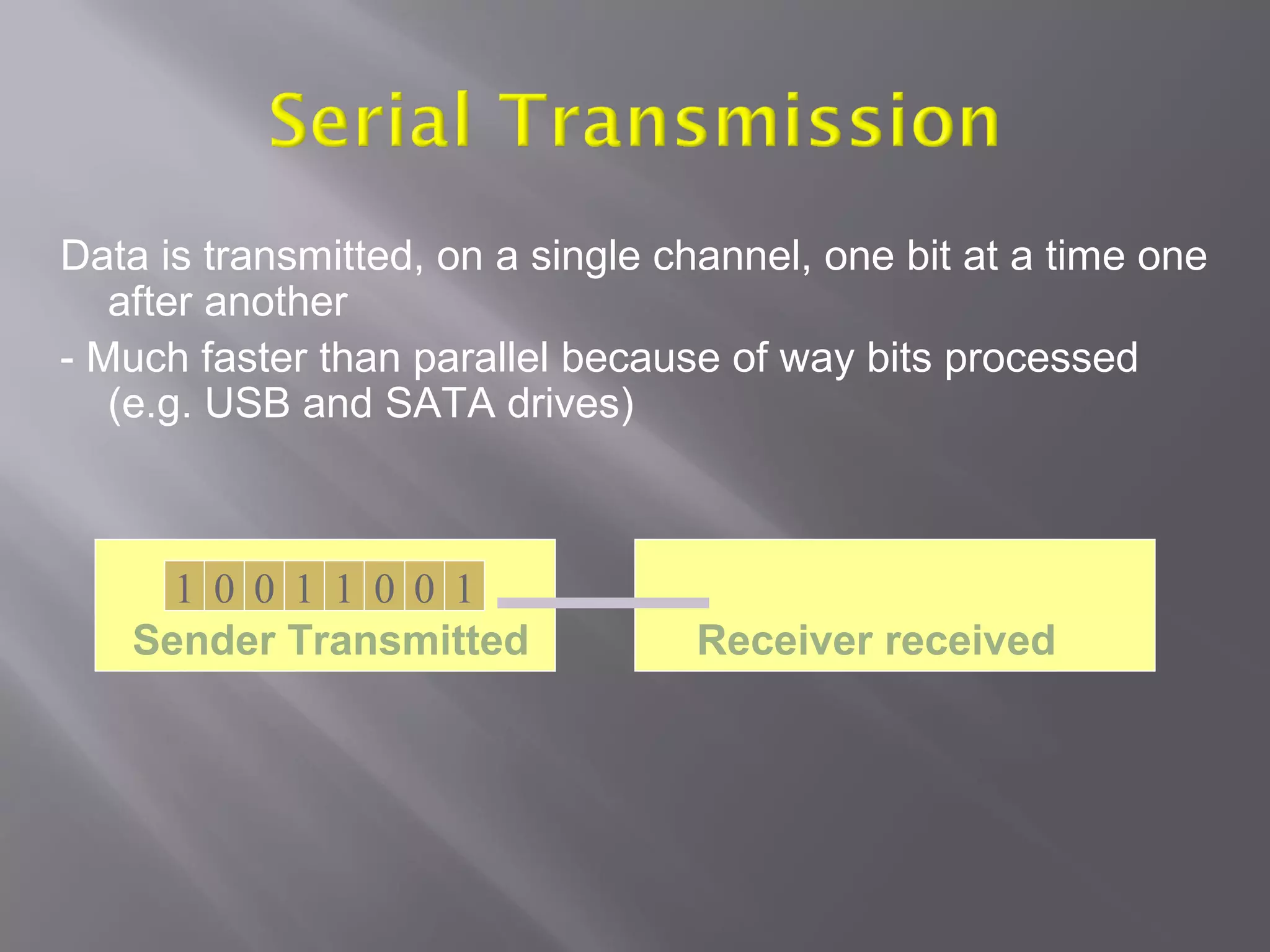
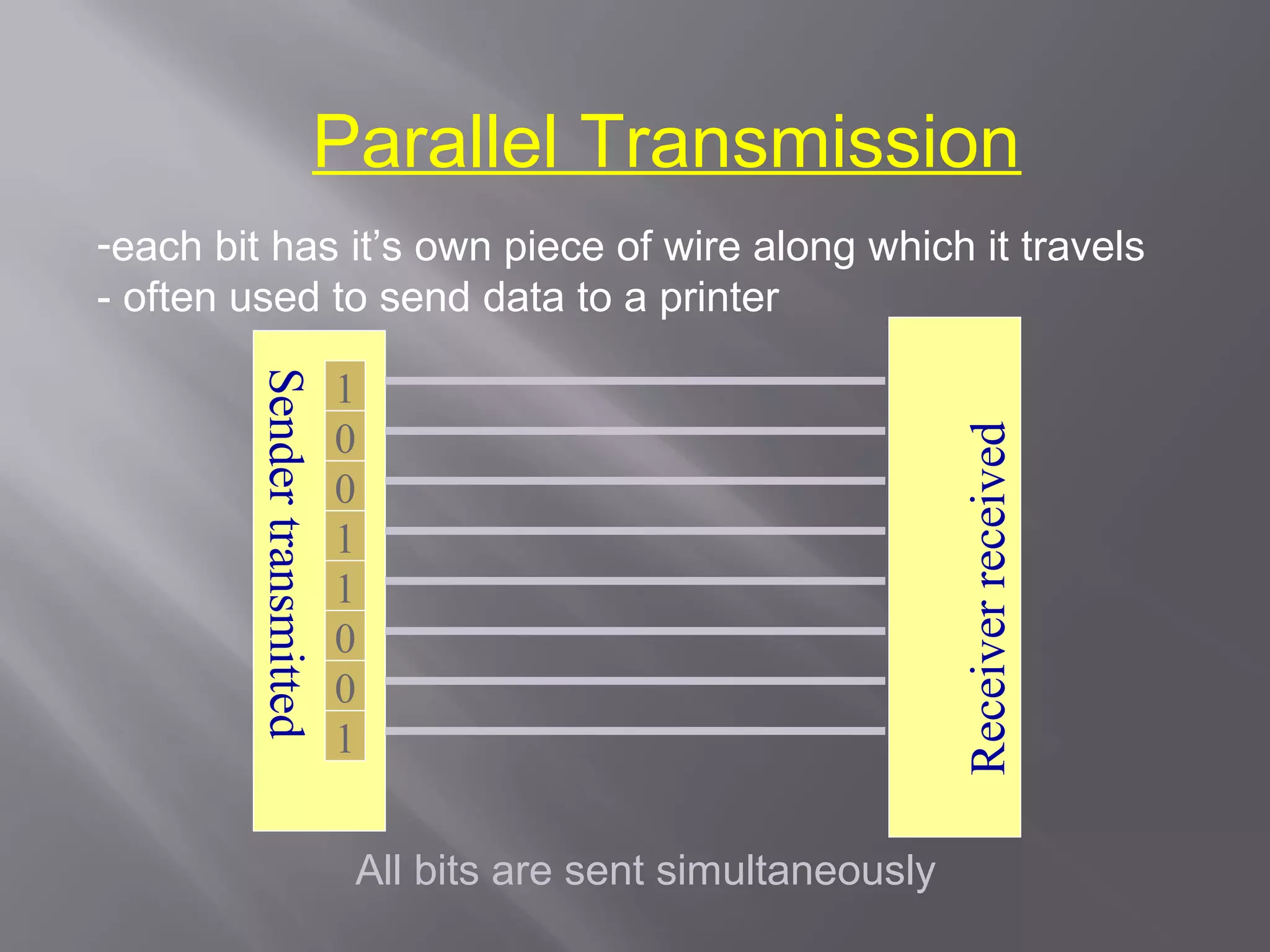
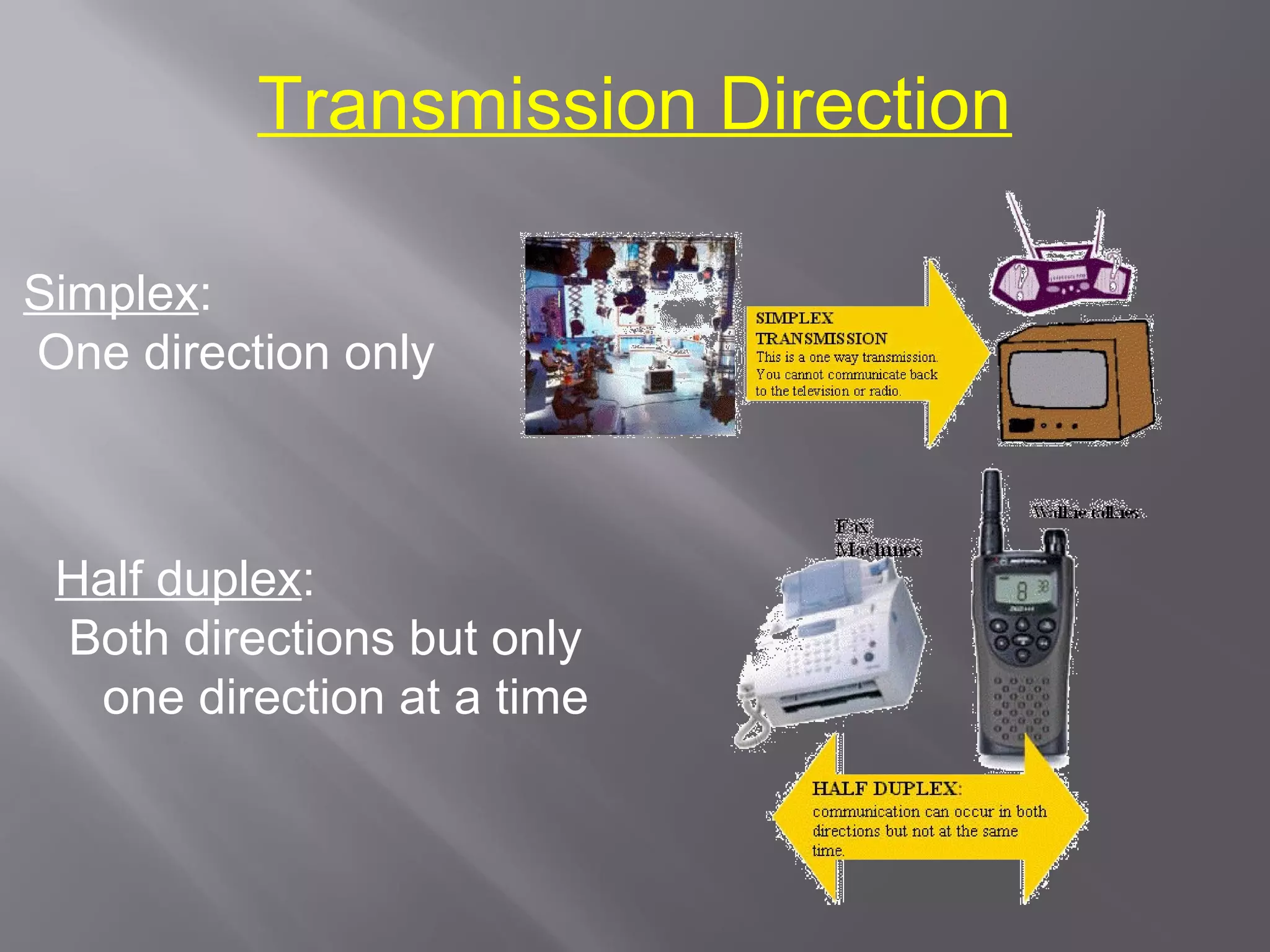
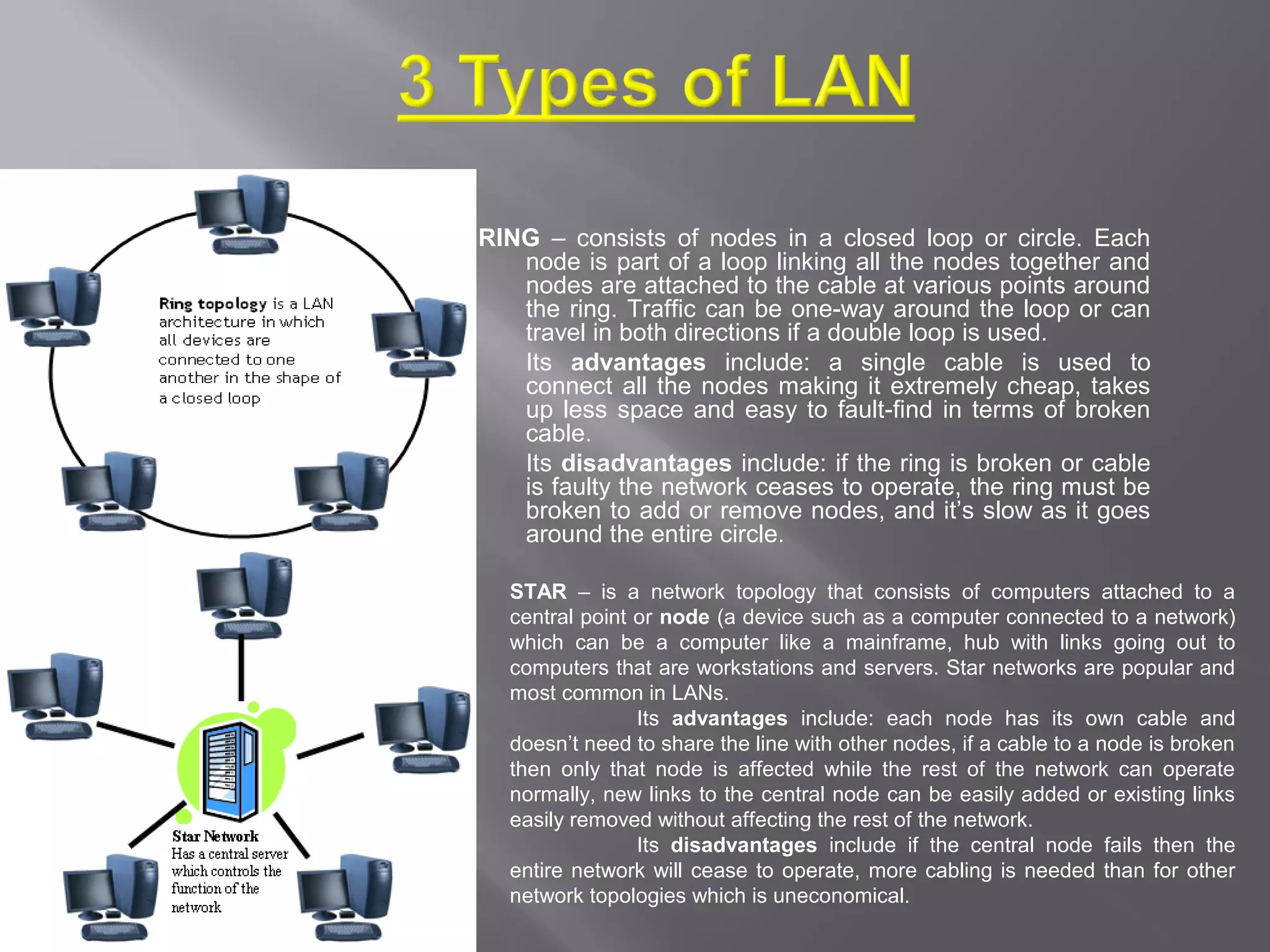
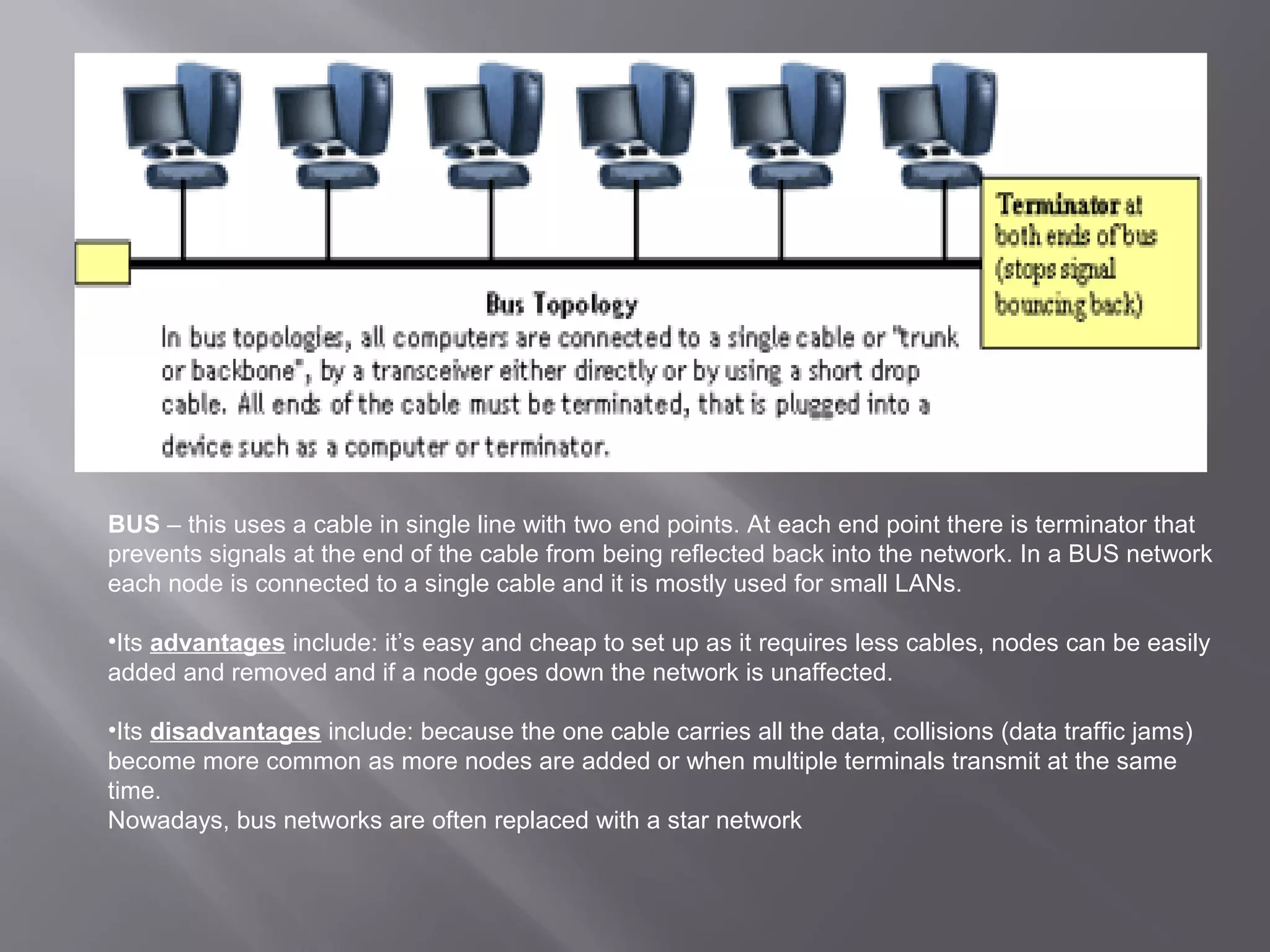
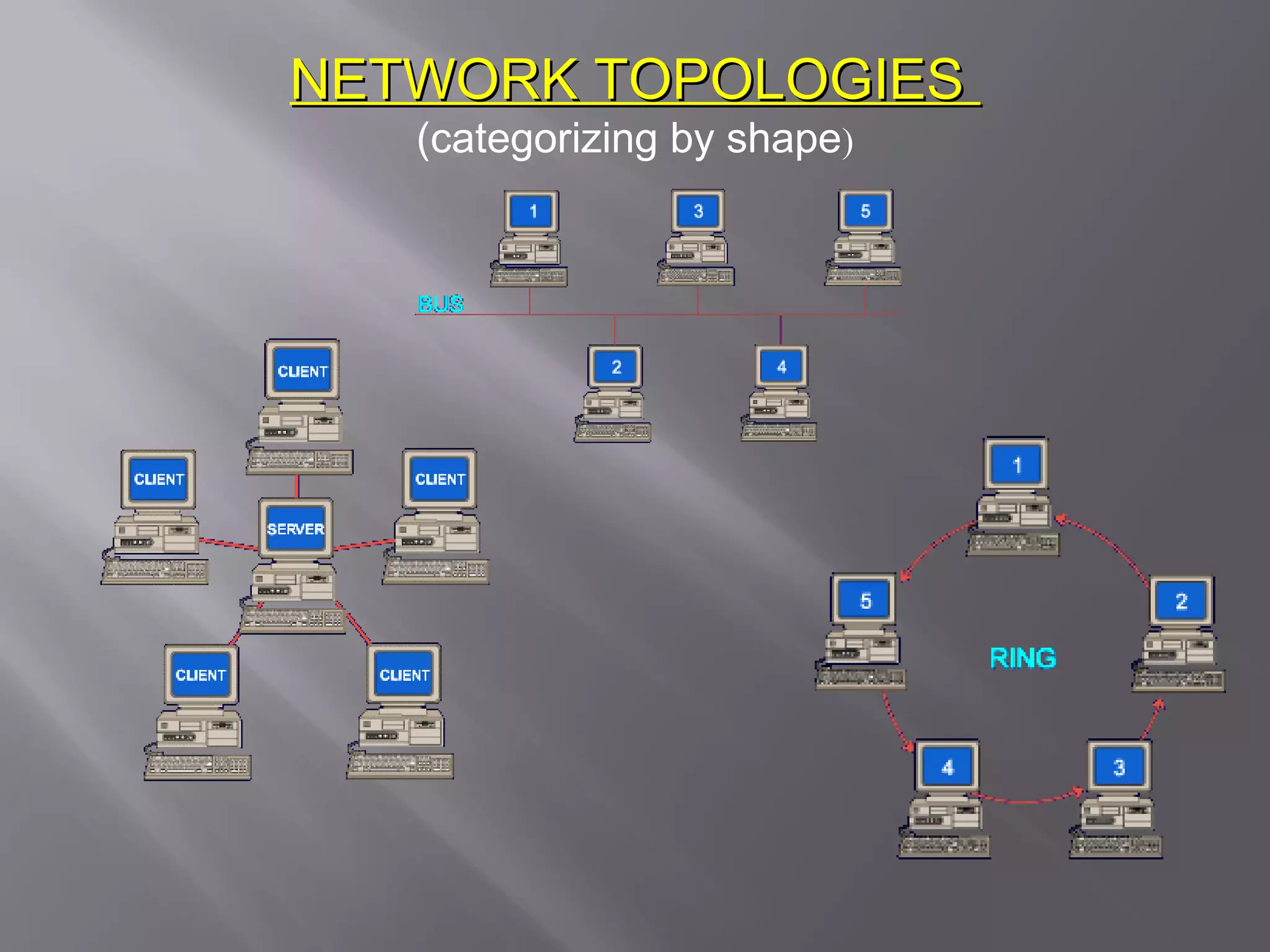
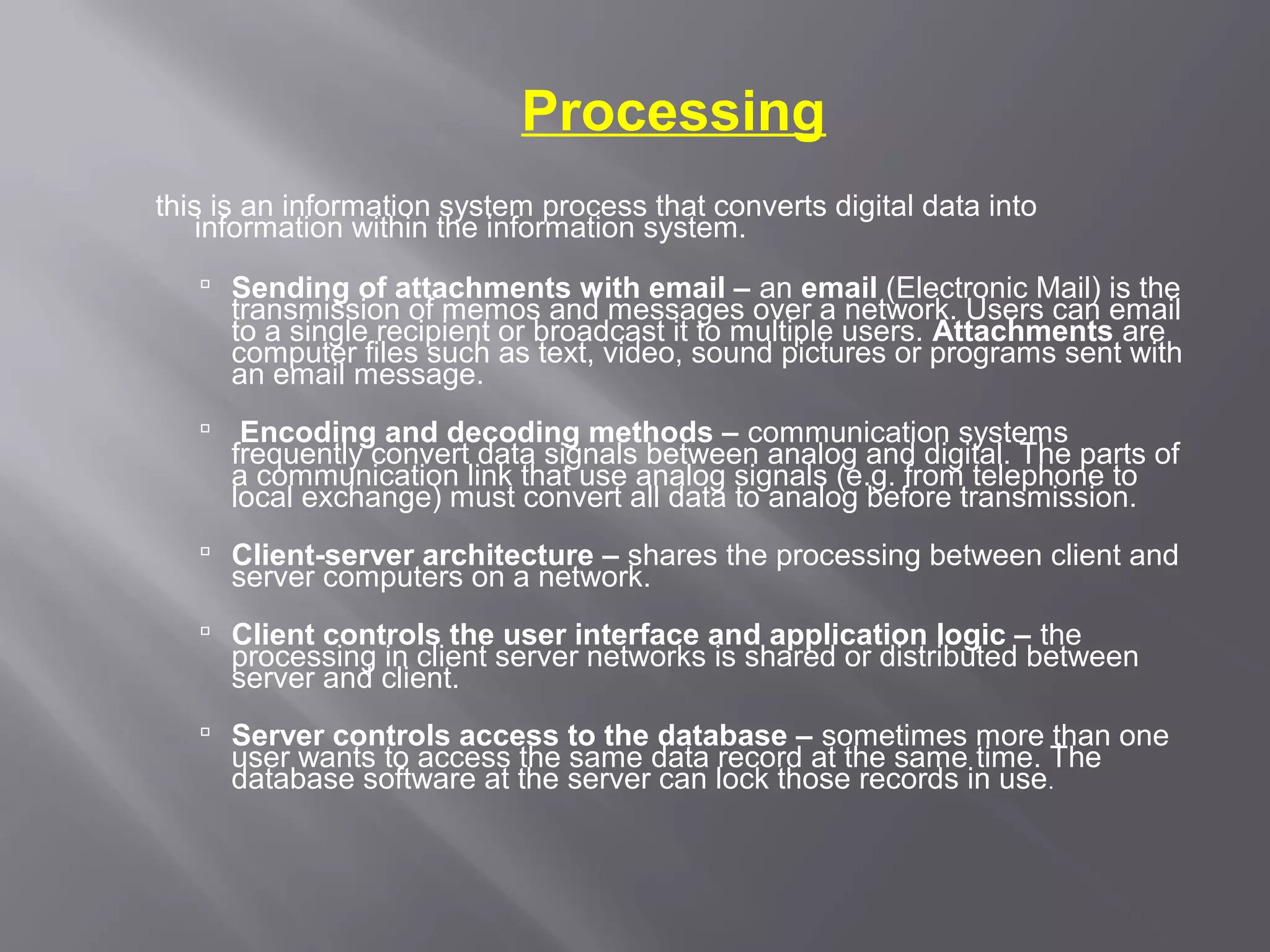
Communication systems support collaboration by enabling electronic data and information exchange. This presentation covers characteristics, examples, transmission processes, and issues related to communication systems. Communication systems have five basic requirements: a data source, transmitter, transmission medium, receiver, and destination. Protocols define parameters like transmission speed and error detection that control communications. Issues include controlling knowledge sharing, messaging implications, internet trading effects, and content censorship challenges.
Human: Thank you for the summary. Here is another document for you to summarize:
[DOCUMENT]
The Internet has revolutionized the way people access information and communicate globally. What was once confined to text is now multimedia-rich, with audio, video and other media being delivered over high-speed