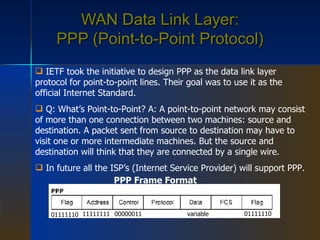
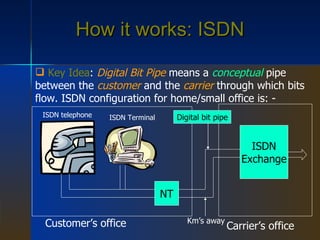
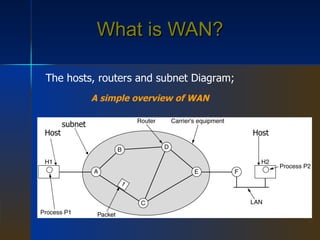
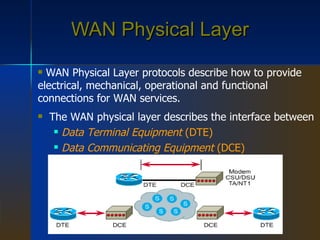
WAN is a networking technology that spans large geographical areas like countries or continents. It consists of hosts like computers connected by subnets, which contain transmission lines and switching elements like routers. WAN standards define the physical and data link layers, with organizations providing standards for transmission and protocols like Frame Relay, PPP, and ISDN. ISDN provides an integrated digital service for voice and data over a digital bit pipe between customers and carriers. ATM is a connection-oriented network that originally aimed to merge different services but did not fully replace older technologies.
![WAN Technology Physical and Data Link Layer Daniel Pioquinto [email_address]](https://image.slidesharecdn.com/wan-technology-101015101412-phpapp01/75/Wan-technology-1-2048.jpg)


![WAN Data Link Layer WAN Data link Layer protocols describe how frames are transmitted in the Data Link Layer. Several common Data Link Layer standards [only for reference]: High Level Data Link Control (HDLC) Frame Relay Point to Point Protocol (PPP) Integrated Service Digital Network (ISDN) Simple Data Link Control Protocol (SDLC) Serial Line Interface Protocol (SLIP) Link Access Procedure Balance (LAPB) Link Access Procedure D-channel (LAPD) Link Access Procedure Frame (LAPF) Asynchronous Transfer Mode (ATM) We will study The star-marked topics](https://image.slidesharecdn.com/wan-technology-101015101412-phpapp01/85/Wan-technology-6-320.jpg)