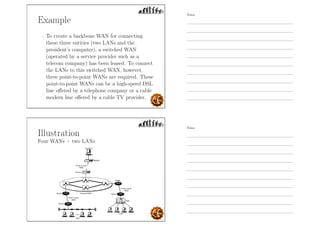
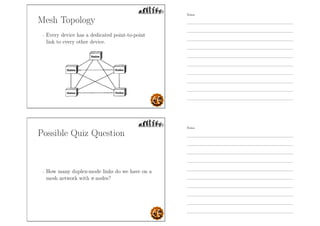
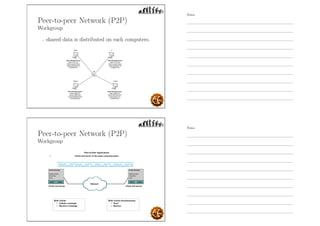
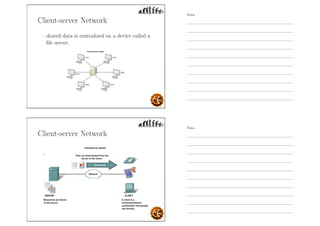
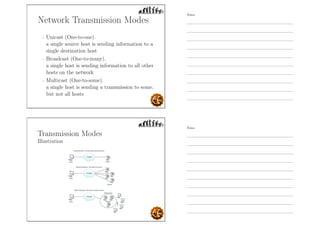
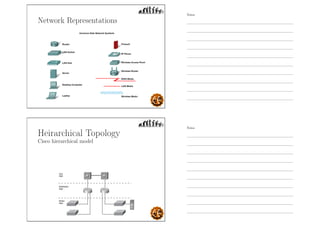
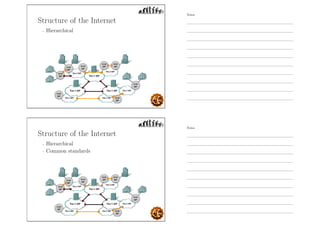
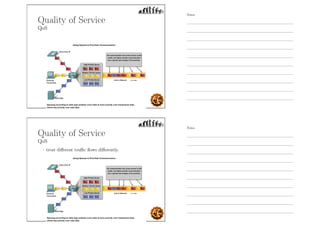
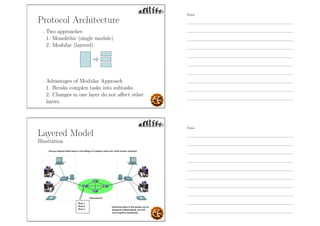
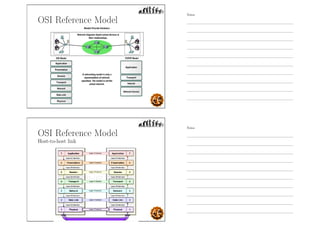
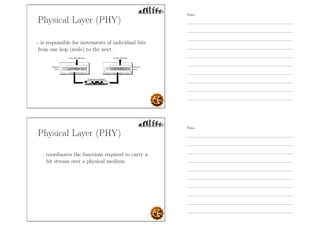
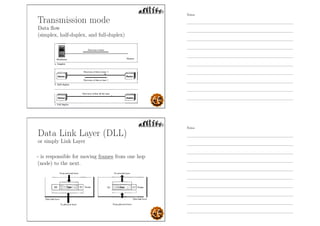
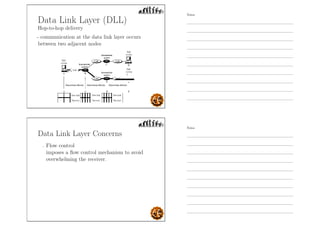
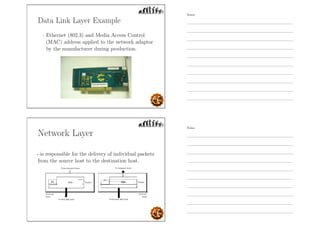
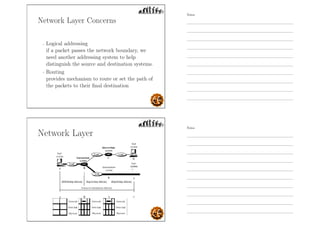
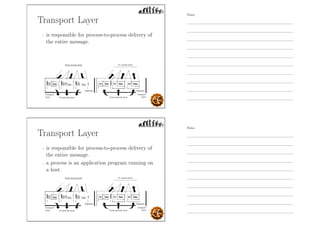
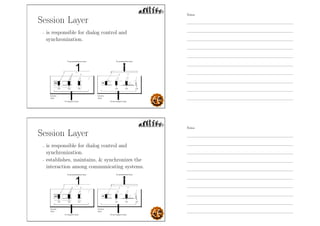
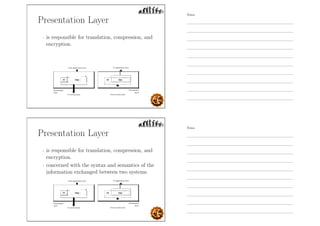
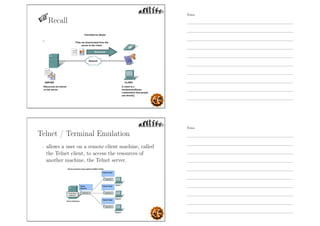
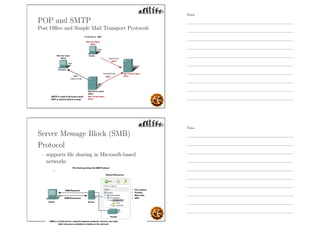
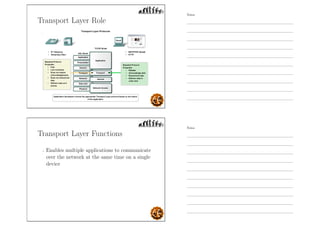
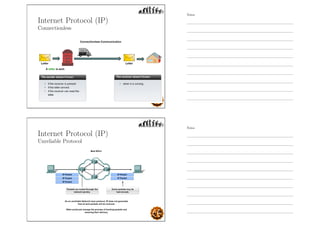
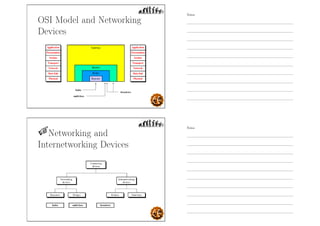
This document outlines the objectives and content for an introduction to data and computer networks course. The objectives are to identify the scope and significance of computer networking, define data communications and networks, describe network components and architecture, illustrate the internet, and explain network communication models. The document then covers topics such as the definition of a network, different network types (LAN, MAN, WAN, internetworks), network requirements, media, topologies (mesh, star, bus, ring), network architectures (peer-to-peer, client-server), and why networks are used.