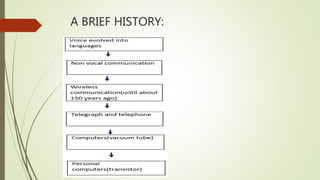
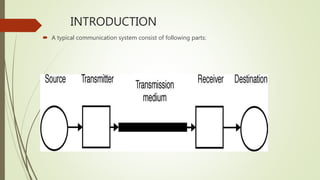
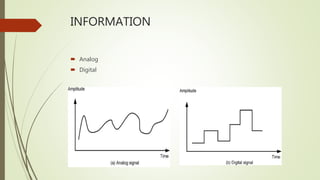
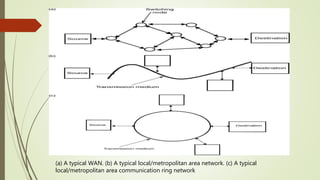
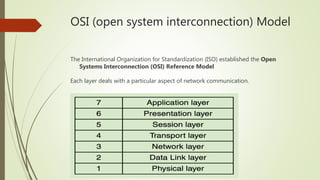
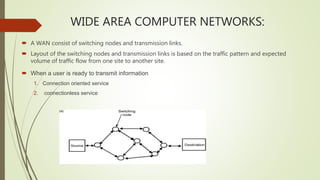
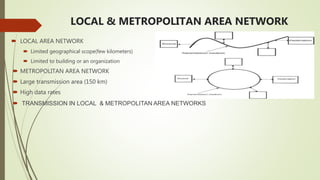
This document provides an overview of communication and computer networks. It begins with a brief history of communication methods such as smoke signals and drums. It then introduces computer networks, distinguishing between wide area networks that connect multiple locations over long distances, and local/metropolitan area networks that operate within a limited geographical scope. The document discusses how networks allocate and share resources among users. It also outlines some of the challenges in integrating different network services and maintaining security.