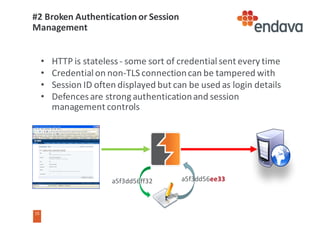
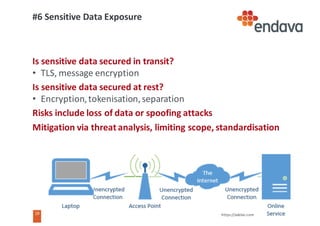
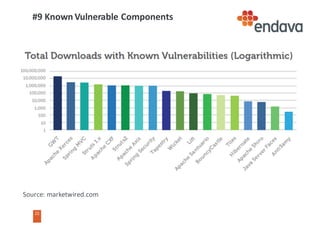
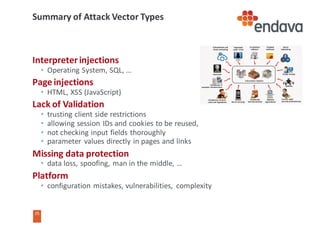
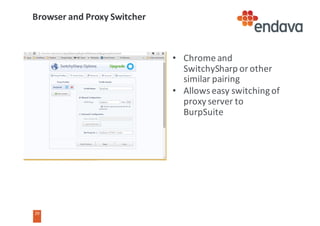
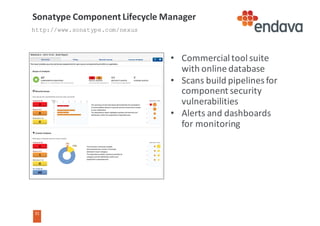
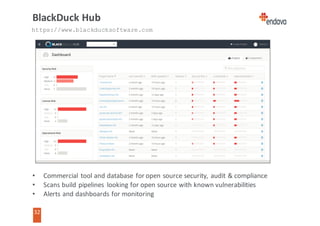
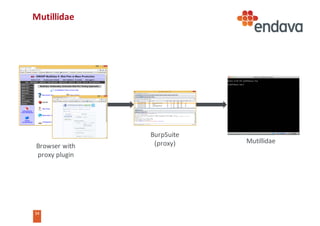
This document discusses common web security threats and how to defend against them. It begins by introducing common threats like injection attacks, authentication issues, and sensitive data exposure. It then details the OWASP Top 10 list of most critical web application security risks, which include injection, cross-site scripting, insecure object references, and more. The document recommends defenses like input validation, access control, encryption, and keeping systems up to date. It emphasizes that attacks usually combine multiple vulnerabilities and simplicity is key to security. Useful tools for analyzing threats are also presented.