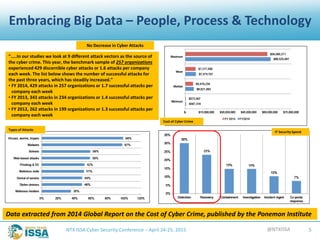
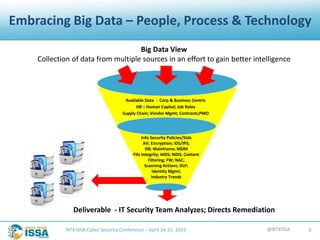
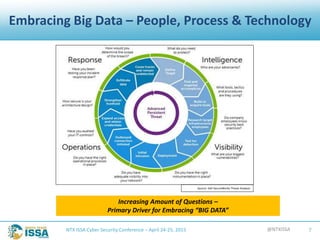
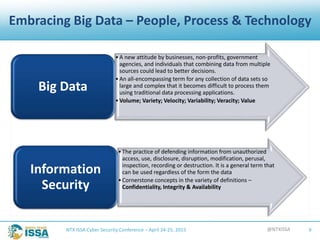
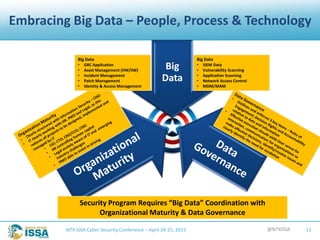
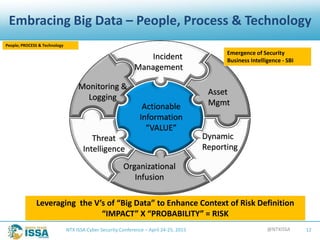
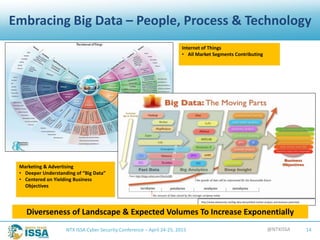
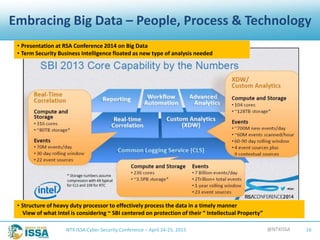
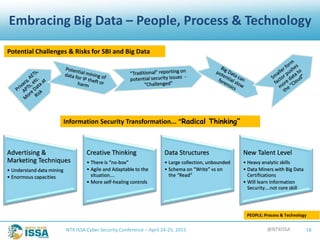
The document details a presentation by Robert L. Pace at the North Texas ISSA Cyber Security Conference focused on leveraging big data to enhance information security through people, processes, and technology. It outlines the increasing number of cyber attacks and emphasizes the need for organizations to adopt big data techniques to improve security programs and decision-making. Key concepts discussed include the definitions of big data, the challenges faced in information security, and the importance of integrating various data sources for better risk management.