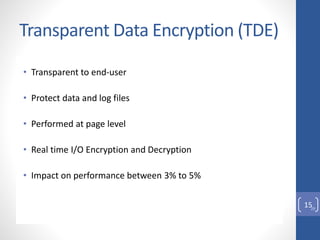
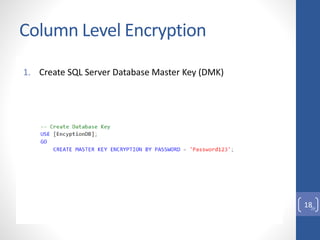
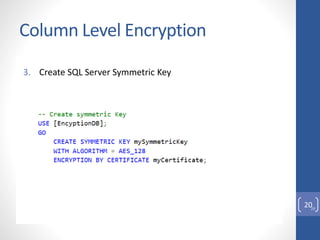
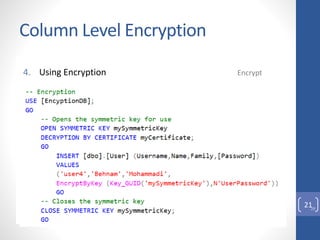
This document discusses column level encryption in Microsoft SQL Server. It begins with an introduction to the problem of protecting sensitive data like credit card numbers. It then provides an overview of encryption types in databases before detailing the encryption hierarchy and specific mechanisms in SQL Server, including Transact-SQL functions, asymmetric keys, symmetric keys, certificates, and Transparent Data Encryption (TDE). The document focuses on column level encryption, outlining the process of creating keys and certificates and using encryption at the column level, along with the advantages of high security and disadvantages of potential performance impacts.











![Certificates
• Certificate contents
• Subject public key
• Subject identifier information [name, e-mail and etc.]
• Validity period
• Issuer identifier information and digital signature
1228](https://image.slidesharecdn.com/columnarlevelencryption-161229175937/85/Column-Level-Encryption-in-Microsoft-SQL-Server-12-320.jpg)








![References
• www.msdn.microsoft.com
• www.searchsecurity.techtarget.com [Margaret Rouse]
• www.mssqltips.com [Nitansh Agarwal]
2628](https://image.slidesharecdn.com/columnarlevelencryption-161229175937/85/Column-Level-Encryption-in-Microsoft-SQL-Server-26-320.jpg)
