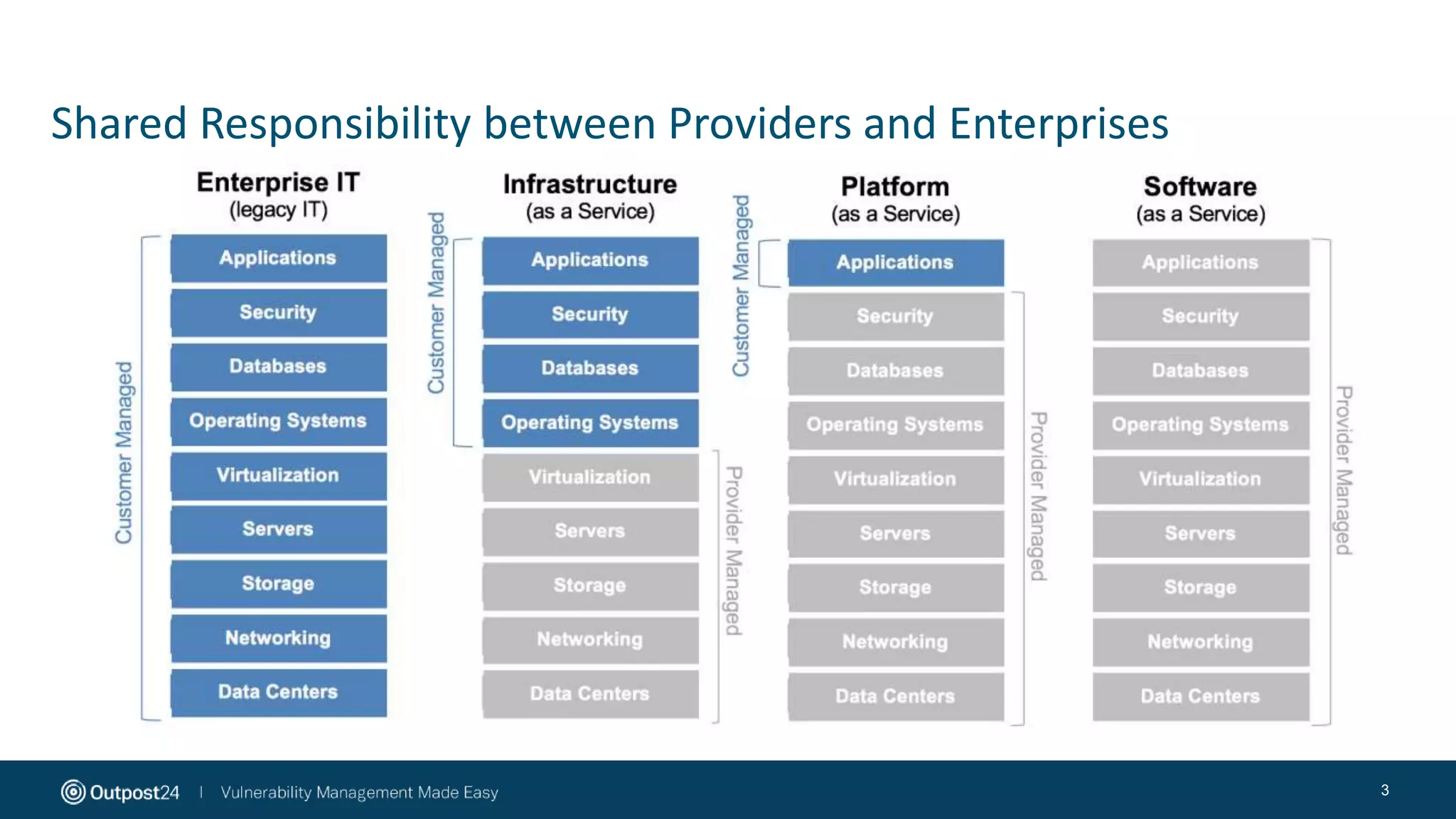
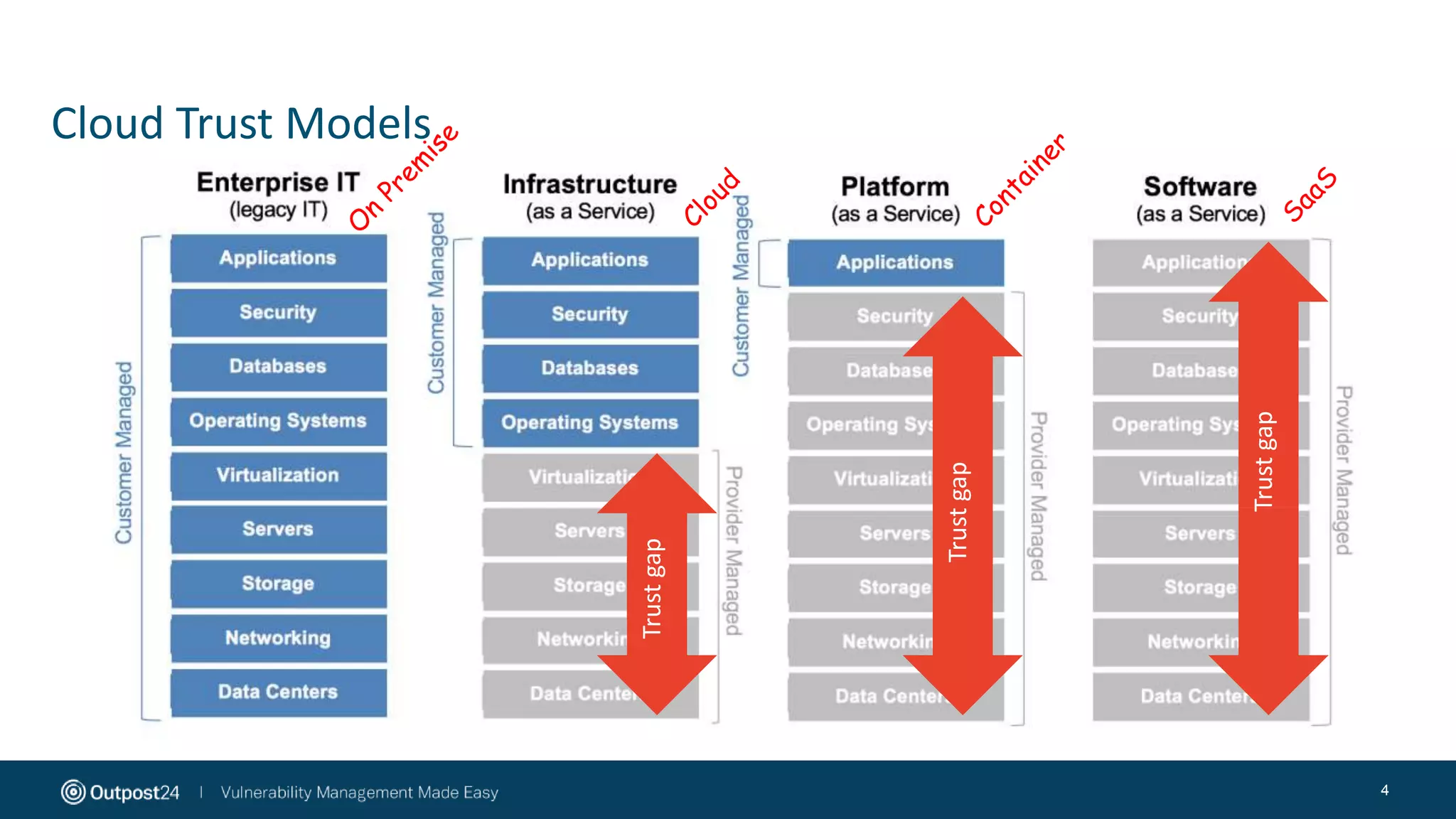
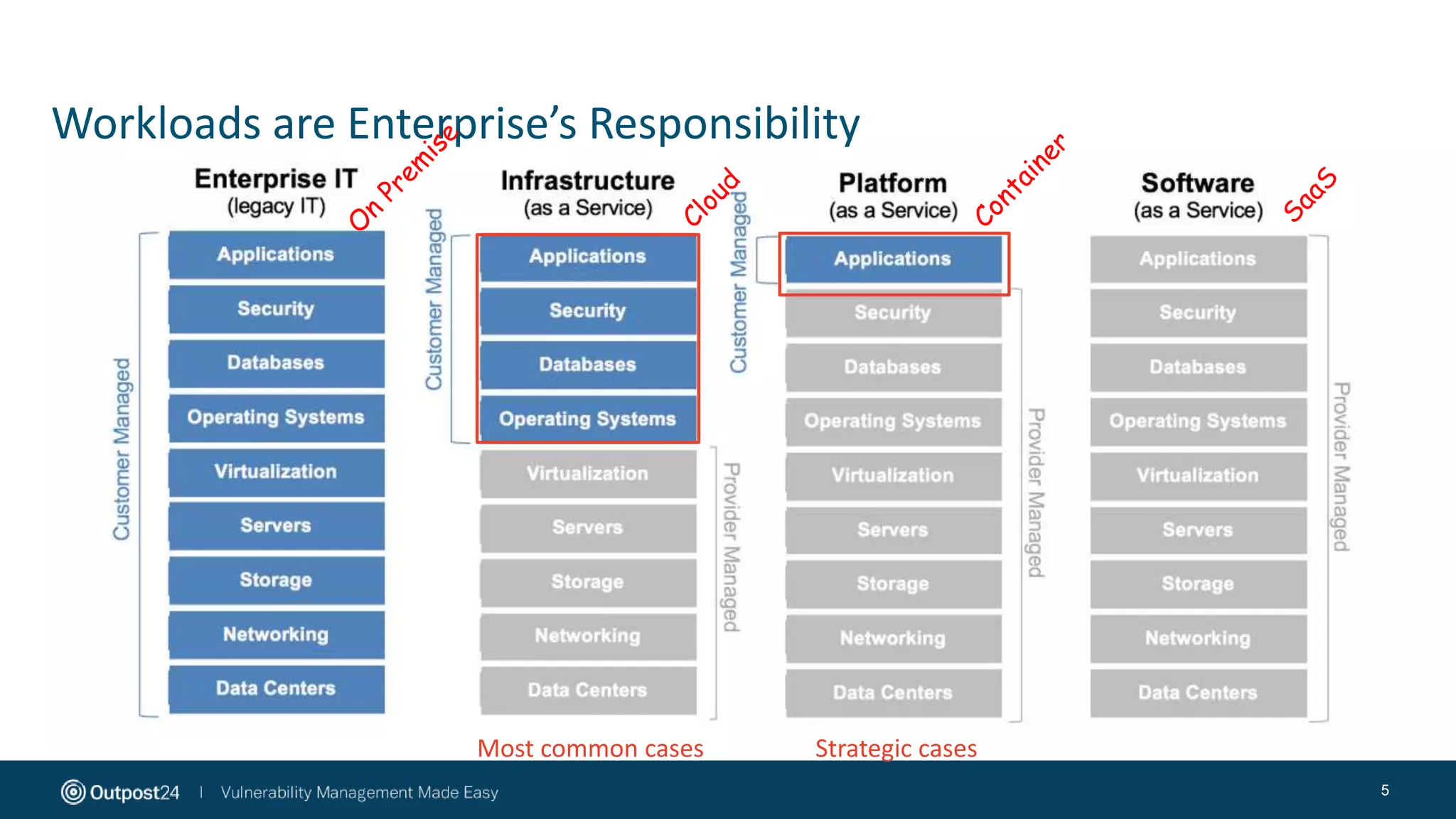
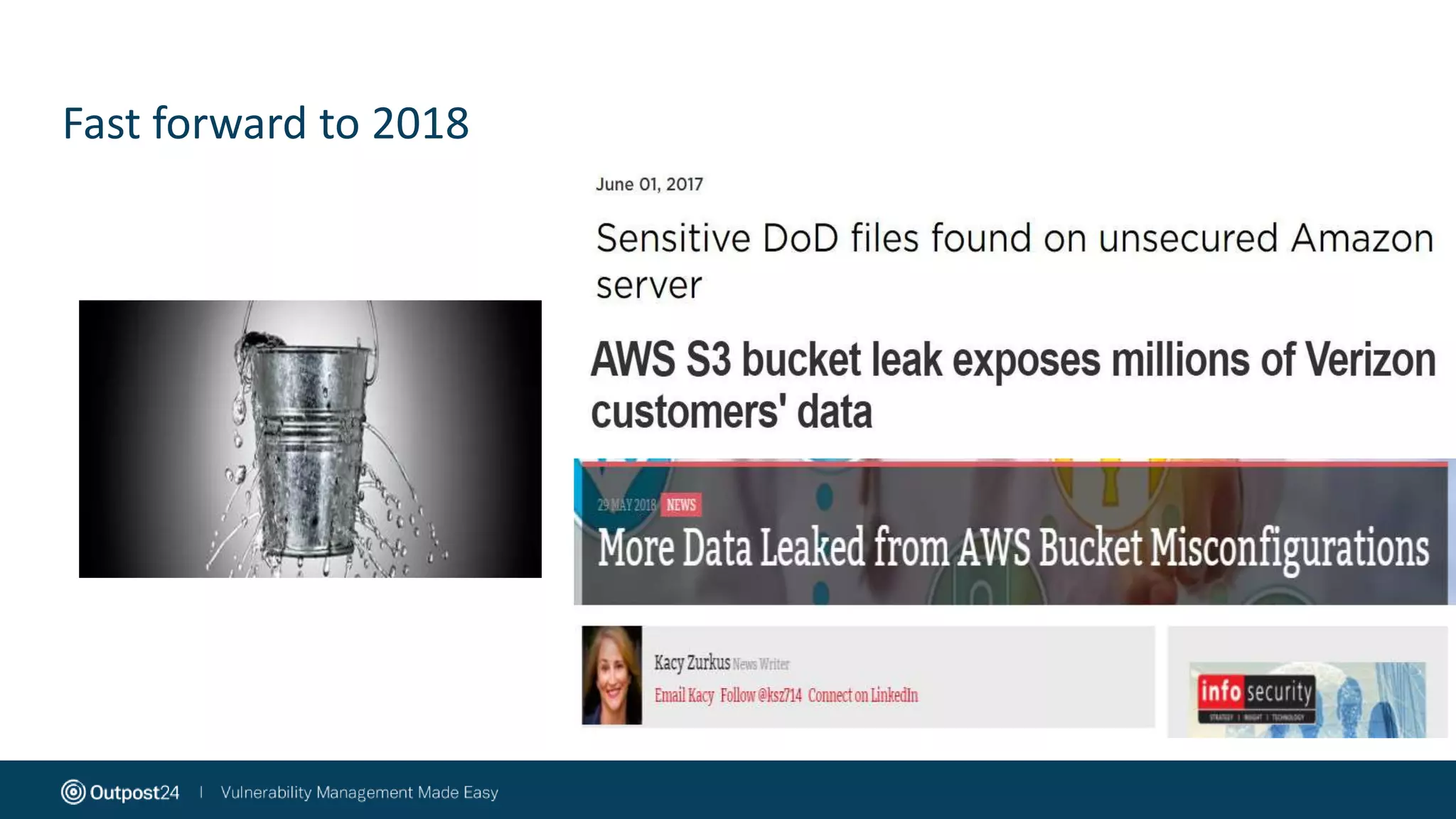
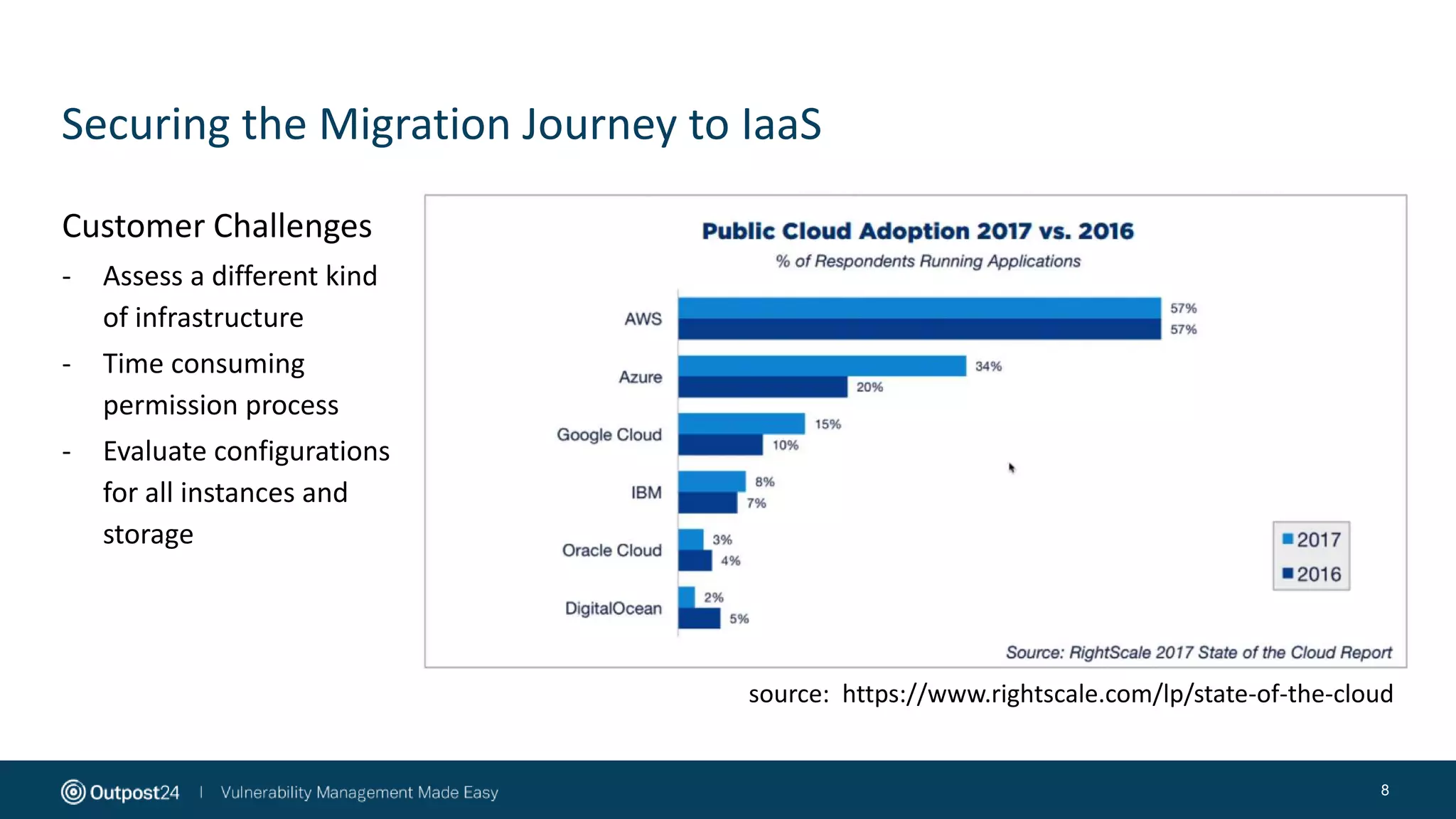
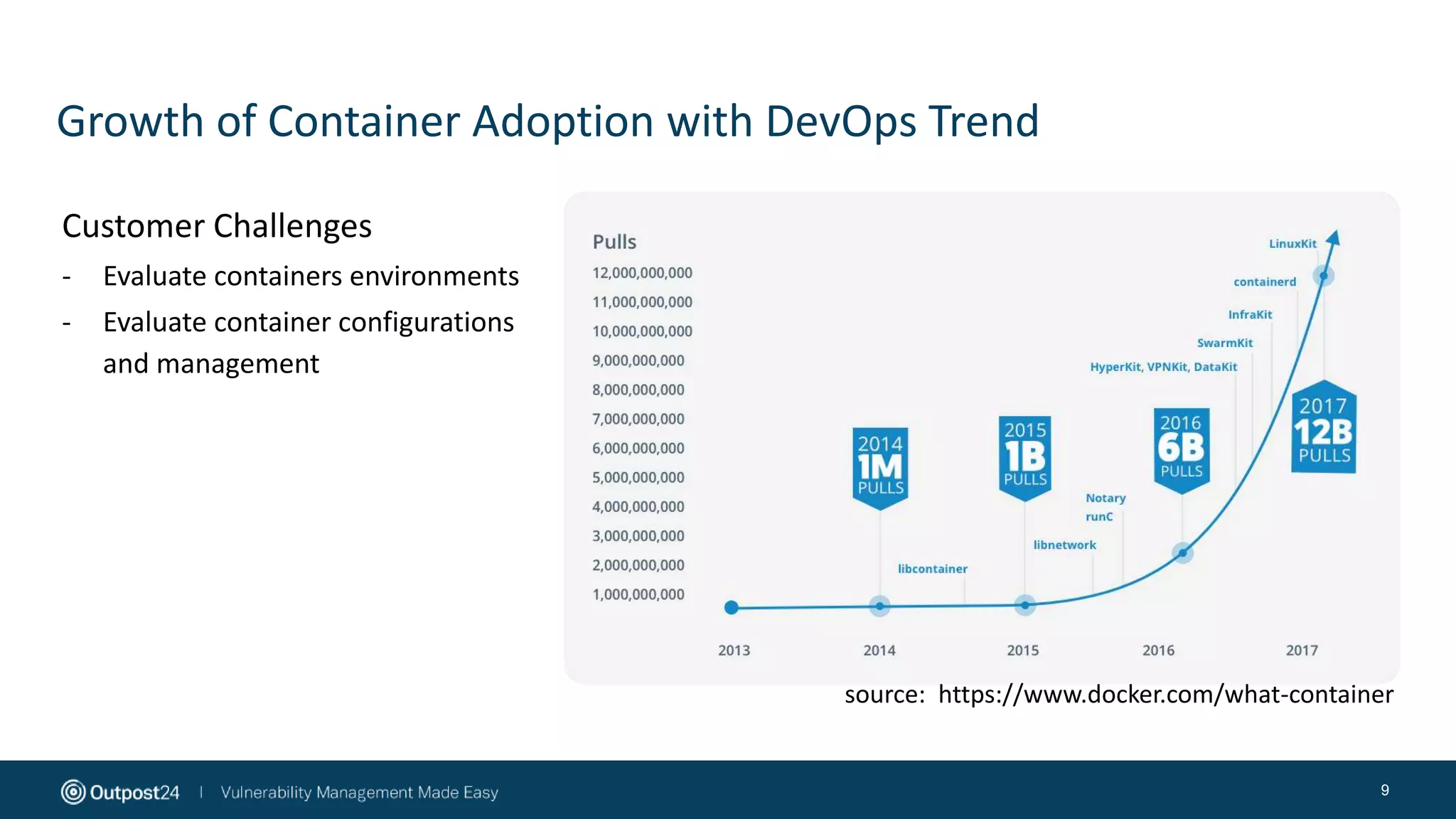
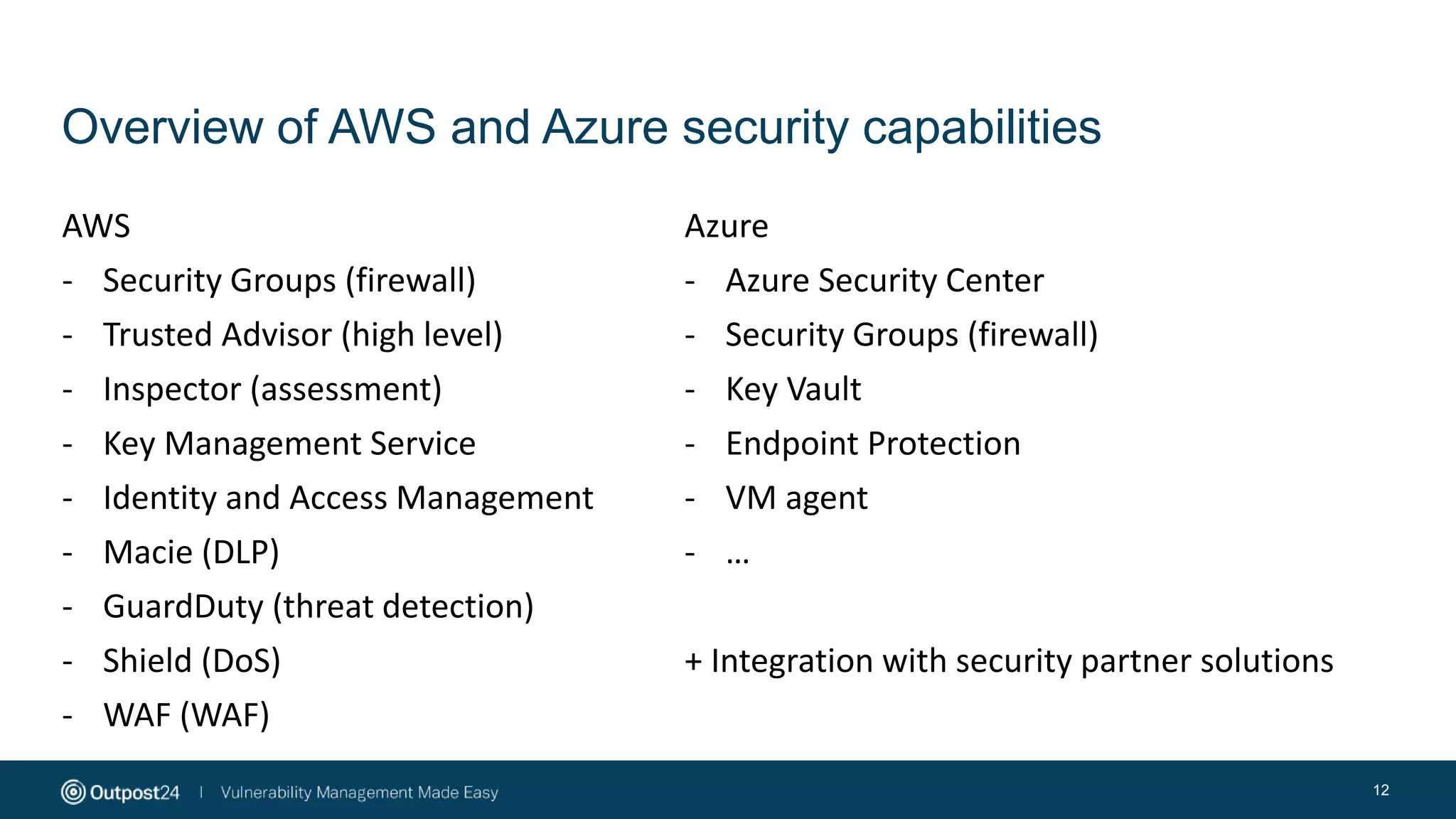
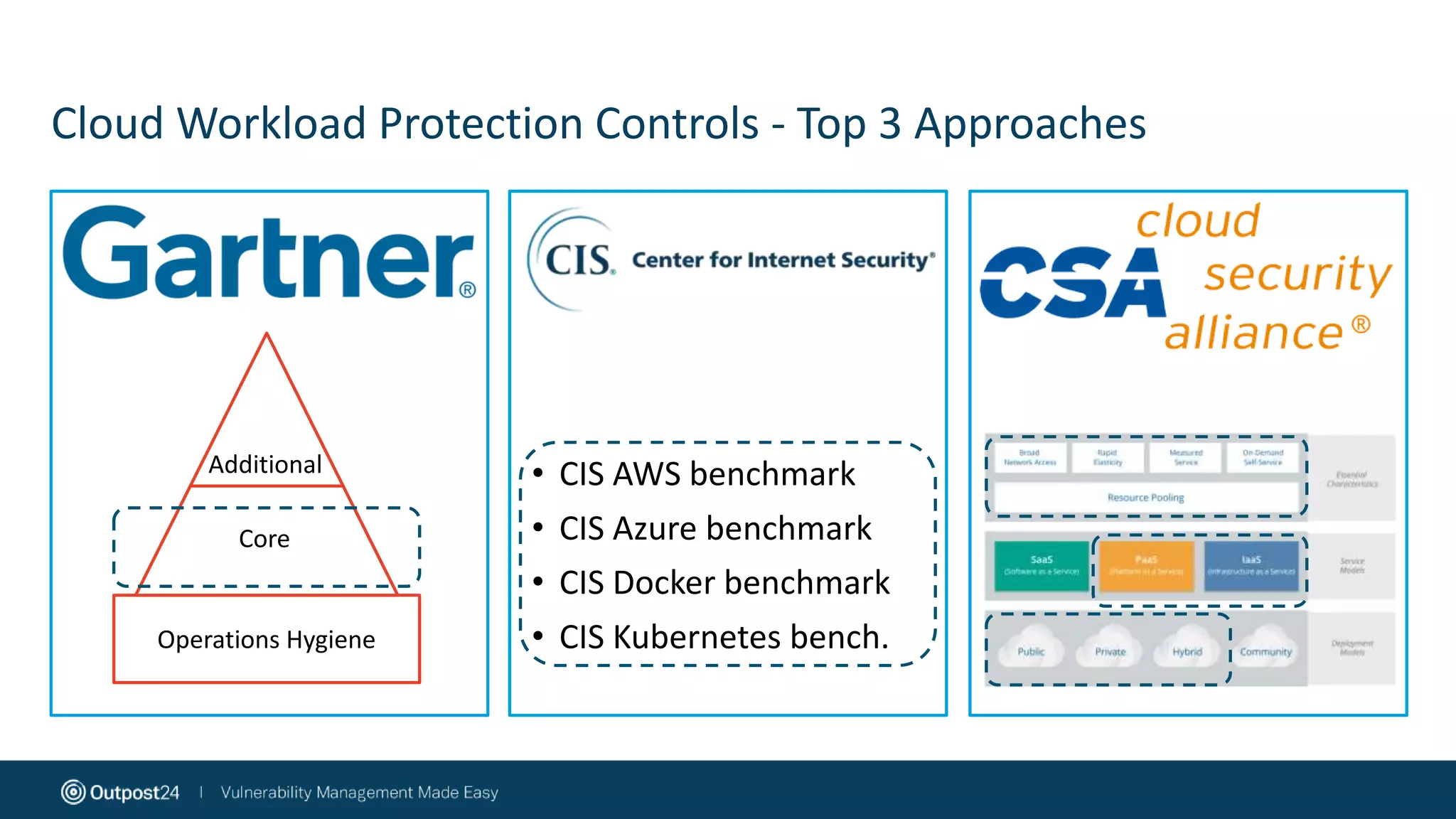
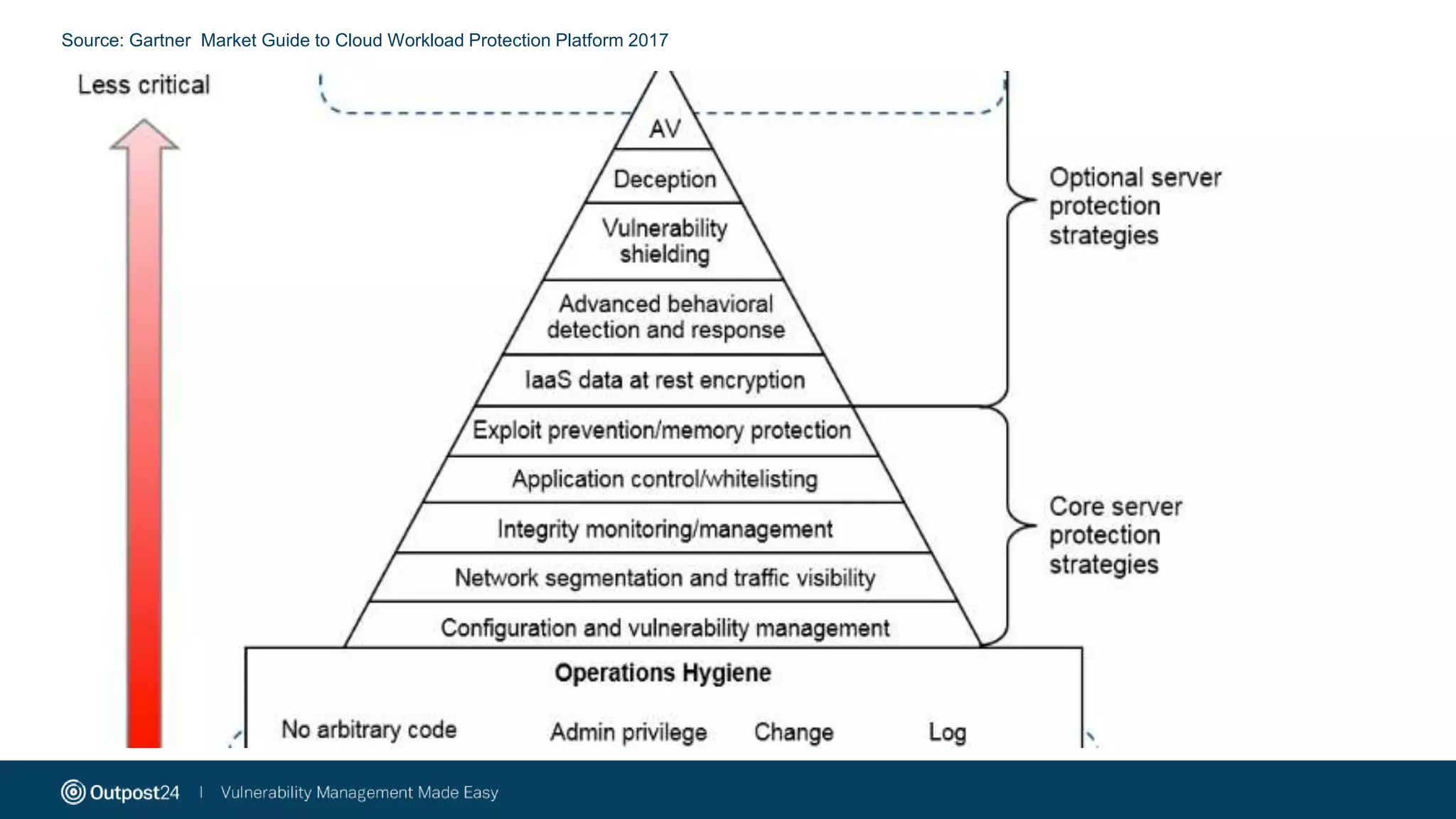
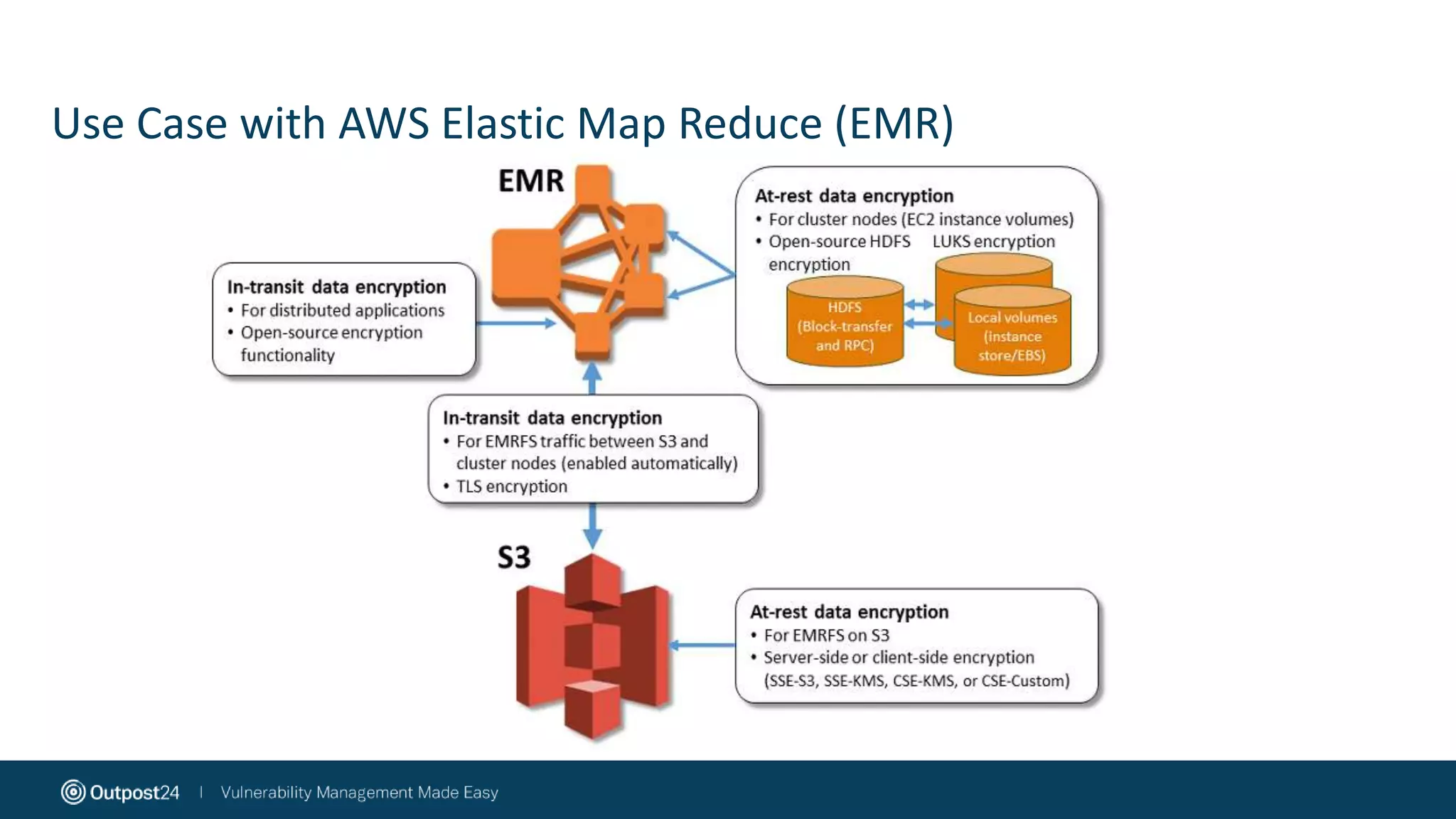
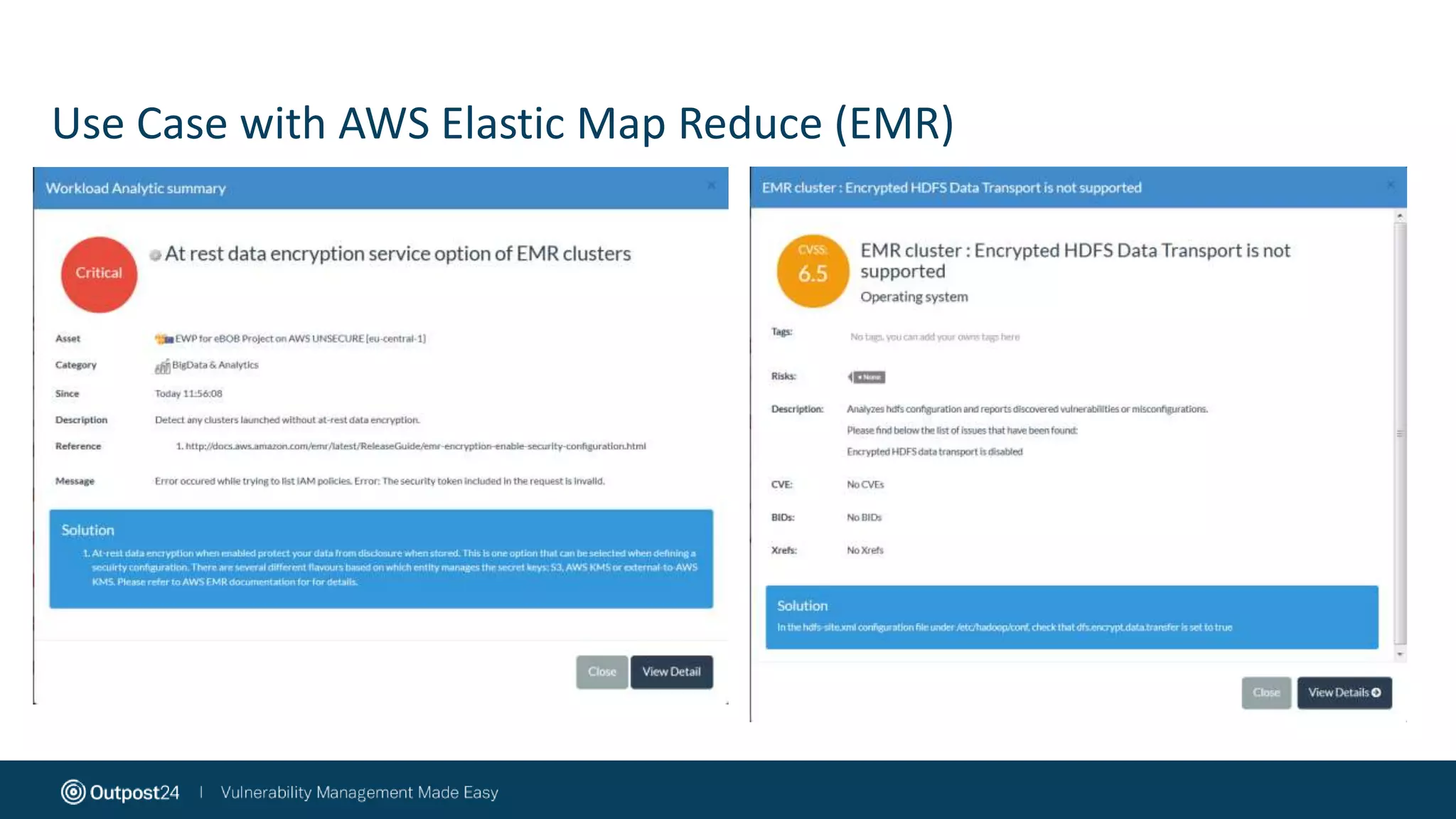
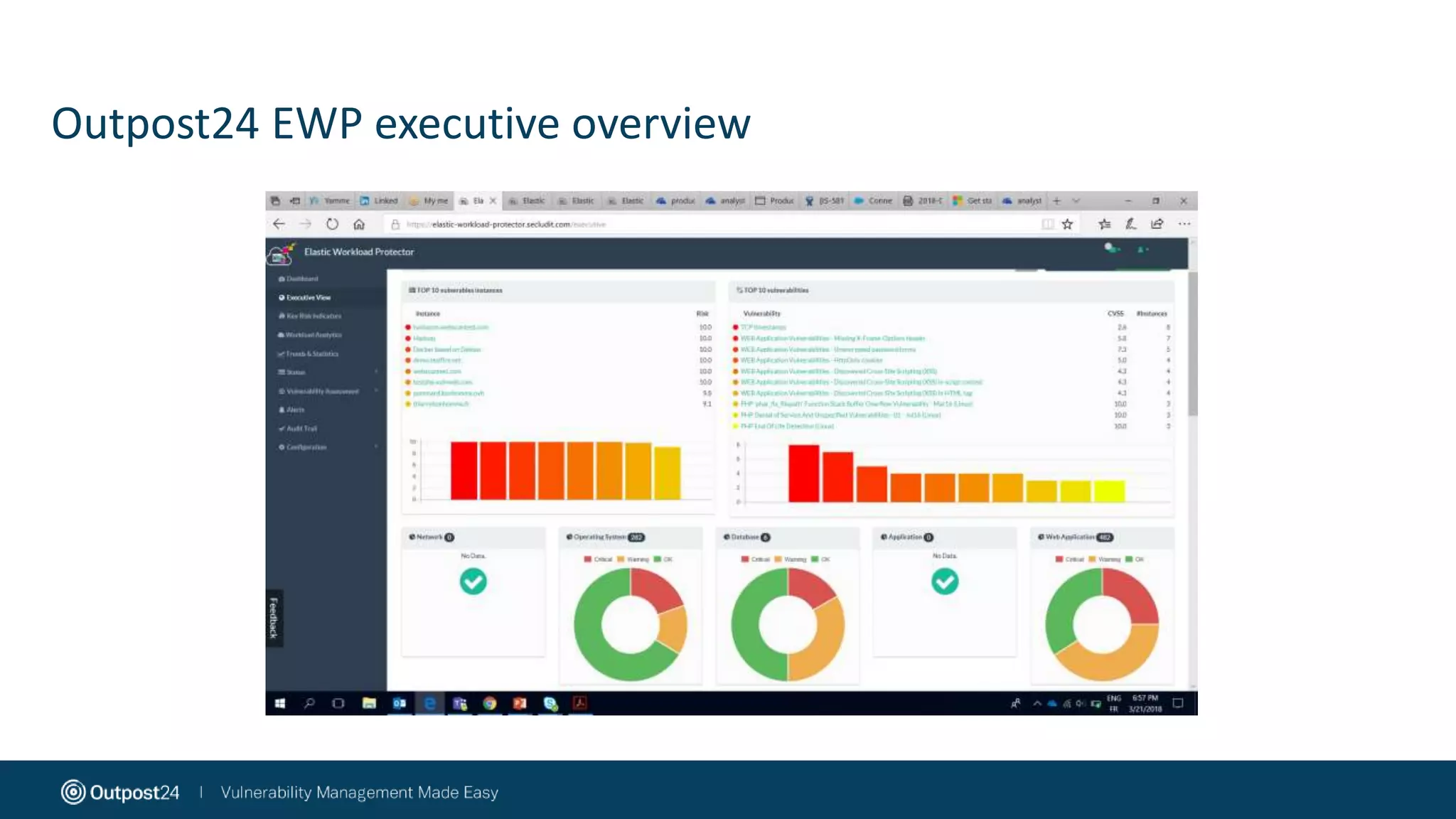
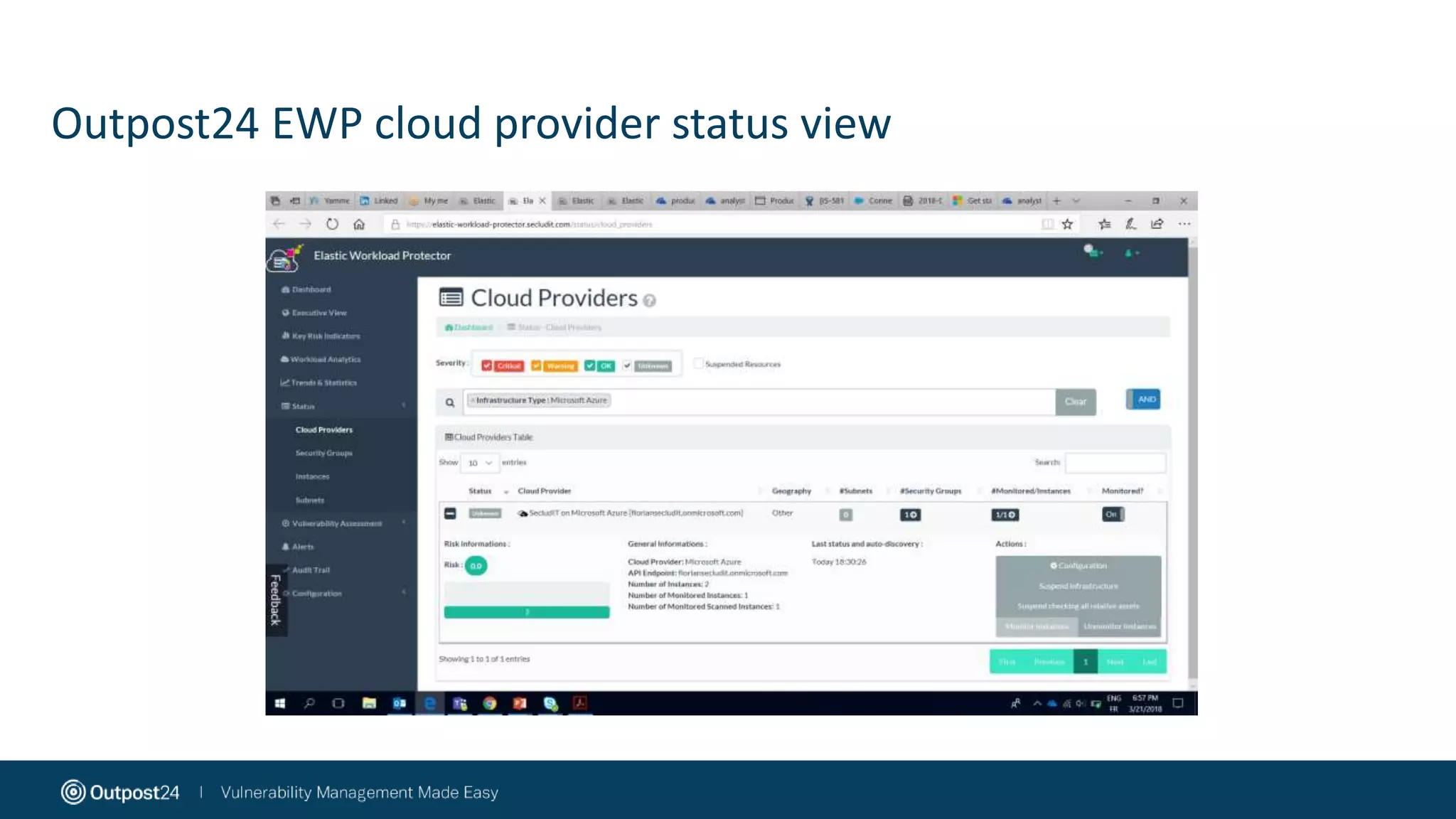
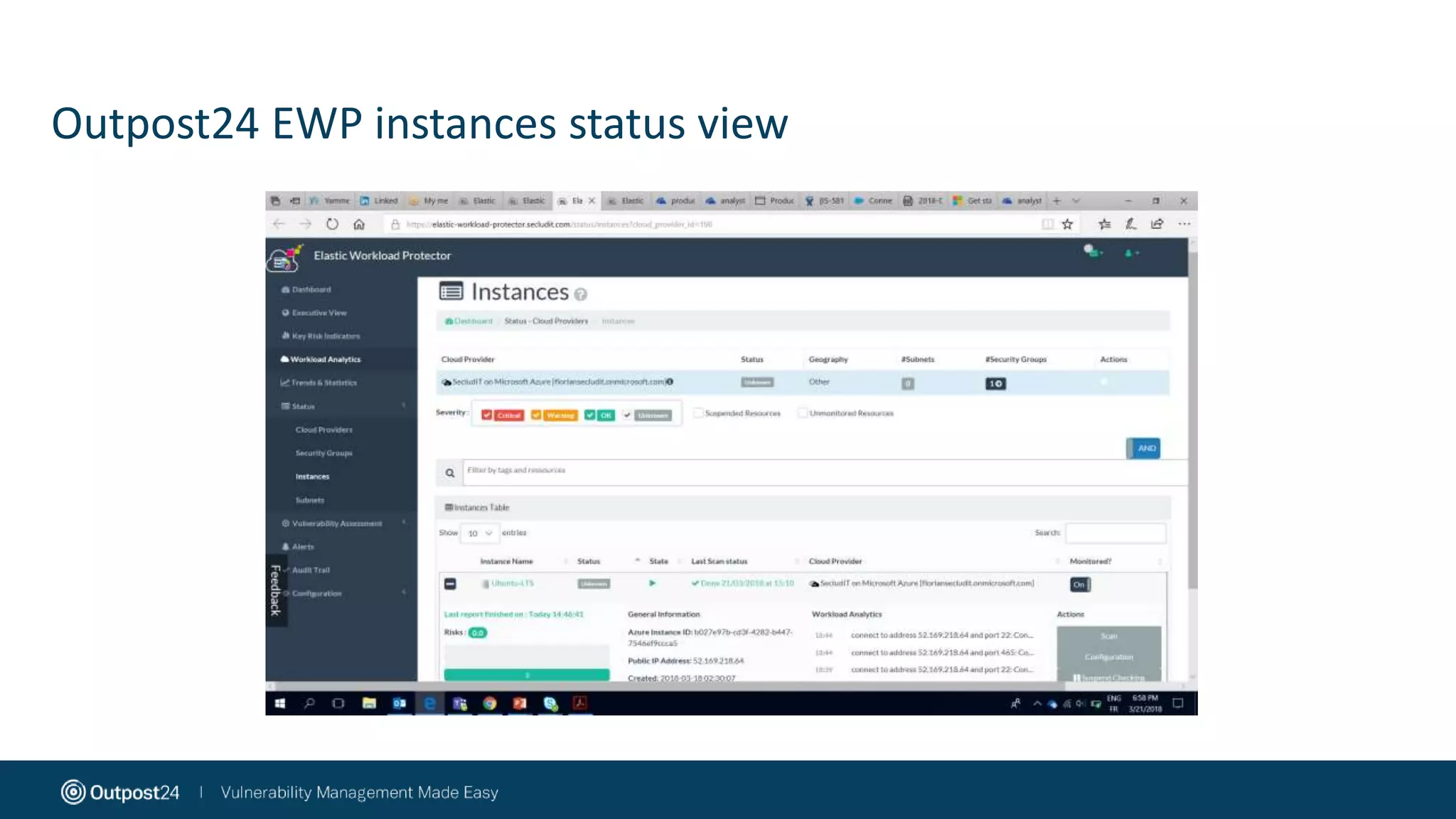
The document discusses the essential strategies for securing data in cloud environments, emphasizing the need for security automation due to traditional solutions' inadequacy in dynamic cloud settings. It outlines a three-step plan for data security in major platforms like AWS and Azure, highlighting shared responsibilities and the necessity for continuous assessment and vulnerability management. Additionally, it addresses customer challenges associated with hybrid cloud infrastructure and container security, providing recommendations for effective cloud workload protection.