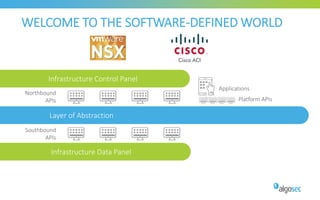
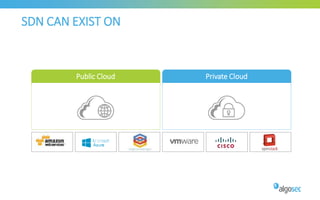
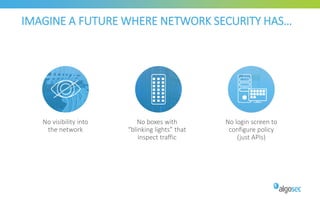
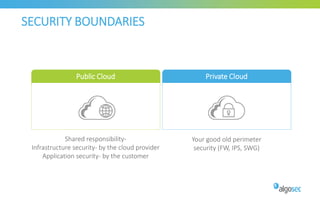
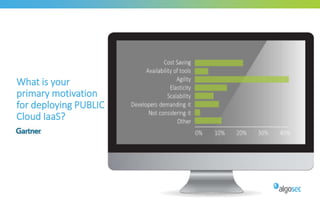
The document discusses managing security in software-defined networking (SDN) across various cloud environments, emphasizing the need for proper management to enhance security. It highlights common challenges such as visibility, responsibility blurring, and the importance of consistent security controls across hybrid cloud setups. Recommendations include adopting automation, unified management, and evaluating cloud security controls tailored to specific needs.