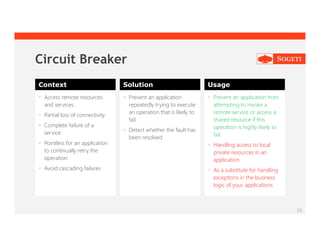
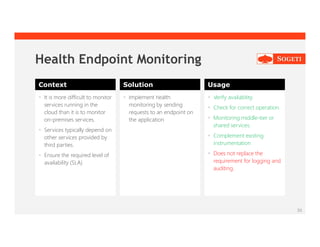
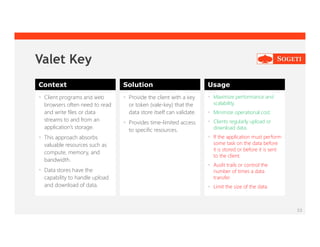
The document outlines cloud design patterns and best practices for developing applications on cloud platforms, emphasizing areas such as availability, data management, and security. It details specific design patterns like cache-aside, circuit breaker, and event sourcing, and explores operational concerns such as monitoring and resource management in cloud environments. Additionally, it highlights the importance of scalability and resiliency in cloud applications to handle varying demands effectively.