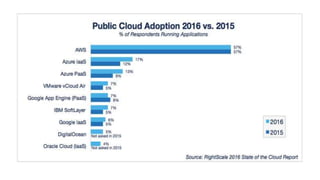
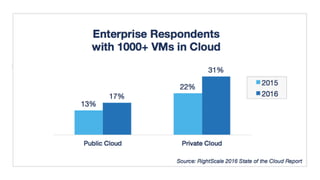
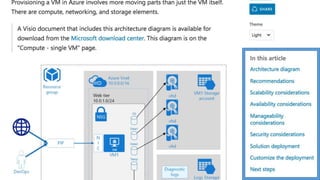
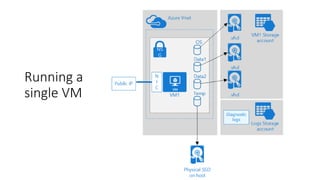
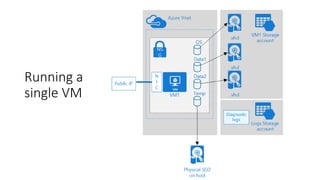
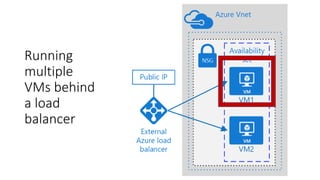
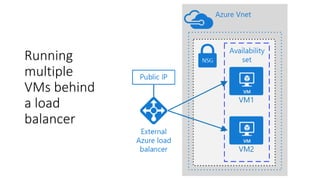
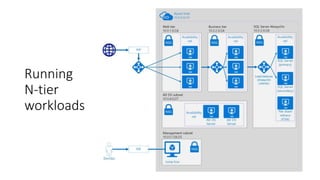
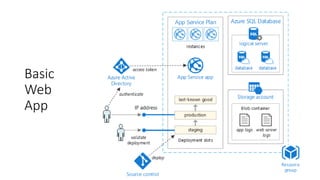
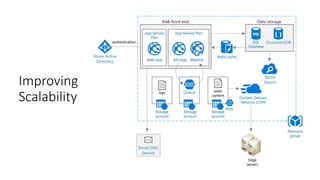
The document outlines various Azure reference architectures, focusing on proven and standardized scenarios for running virtual machine workloads, web applications, and extending on-premises networks to Azure. It covers best practices for connectivity, identity management, and cloud boundary protection, alongside recommendations for diverse storage options. It also provides resource links for further learning and implementation guidance.