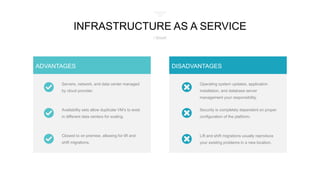
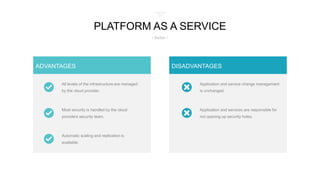
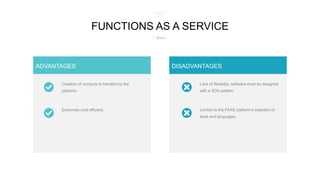
The document discusses cloud-first architecture patterns and best practices, emphasizing the use of Azure as an example due to its sophisticated offerings. It outlines hosting models, architecture styles, design principles, and common anti-patterns in cloud applications, highlighting the importance of scalability, availability, and security throughout the application lifecycle. Additionally, it provides insights on how to effectively design and manage cloud applications to enhance performance and resilience.