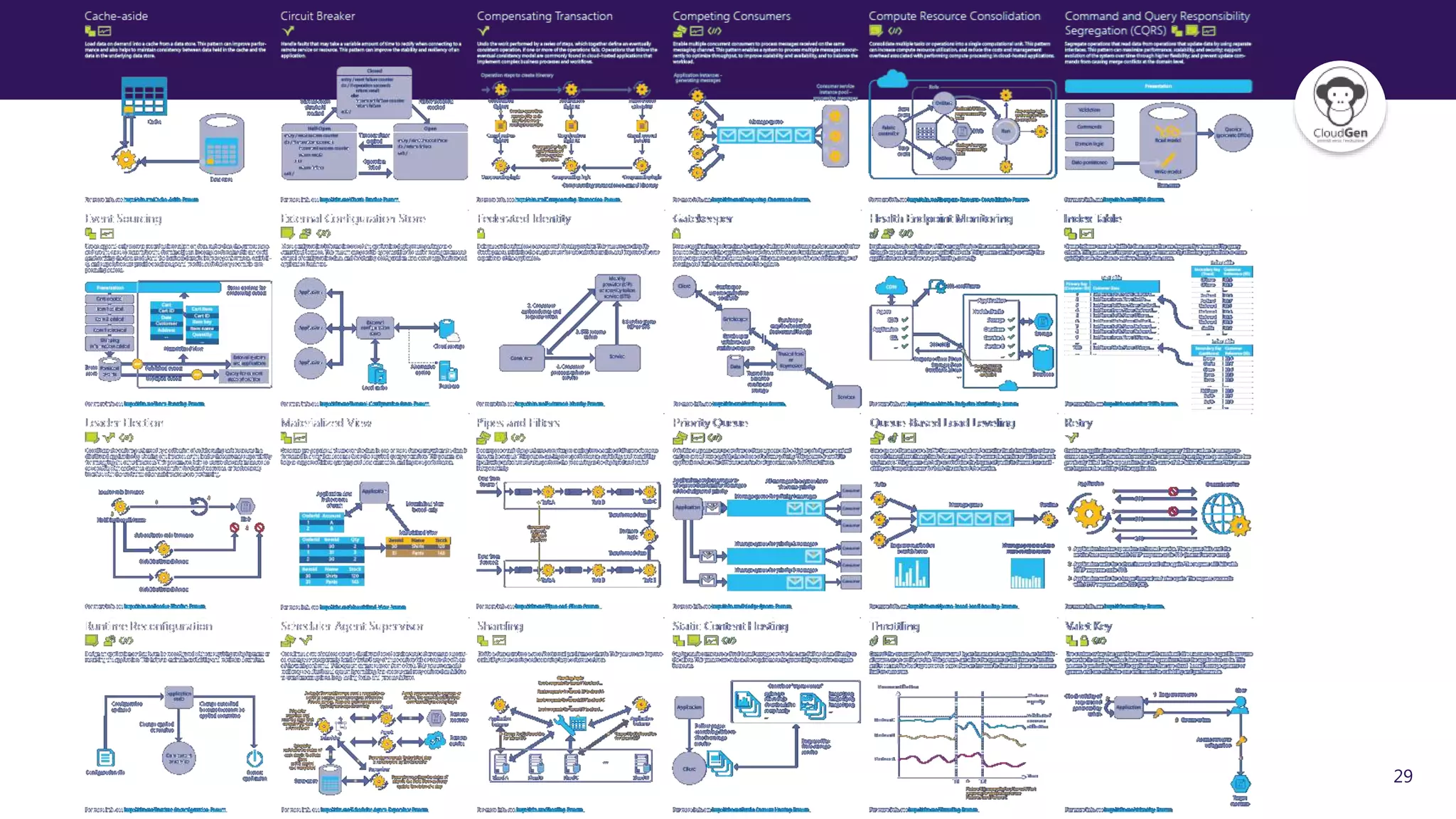
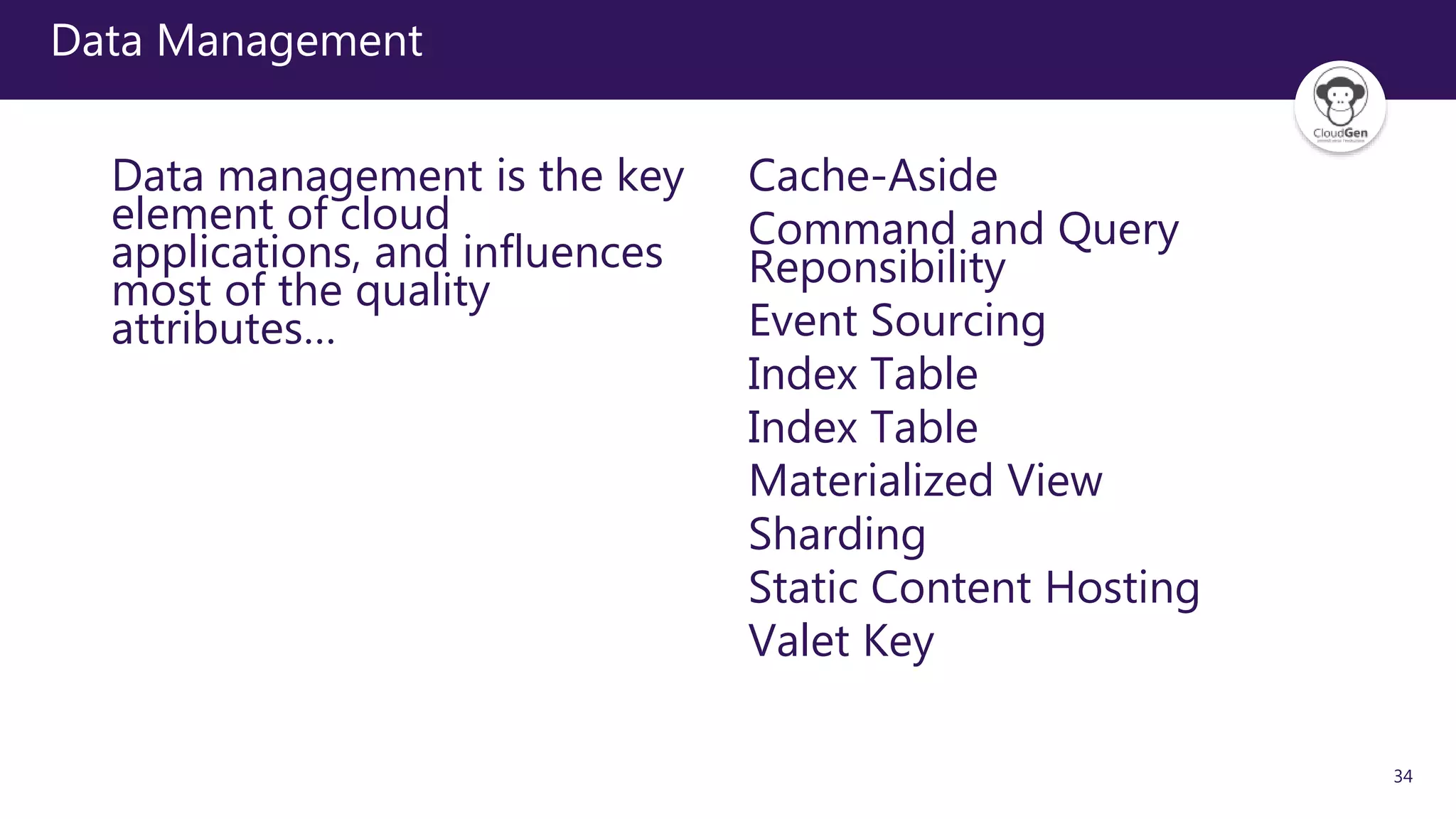
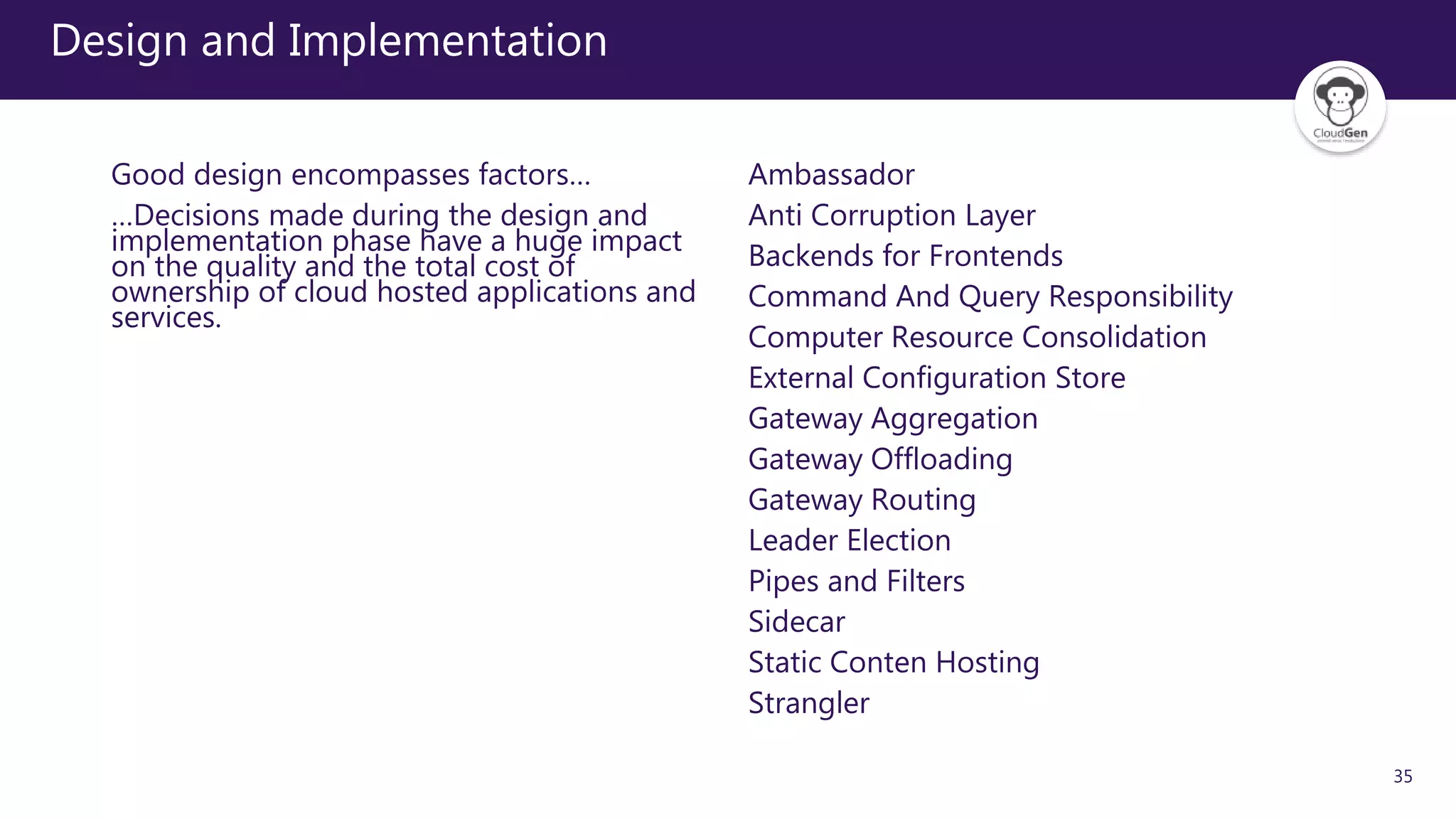
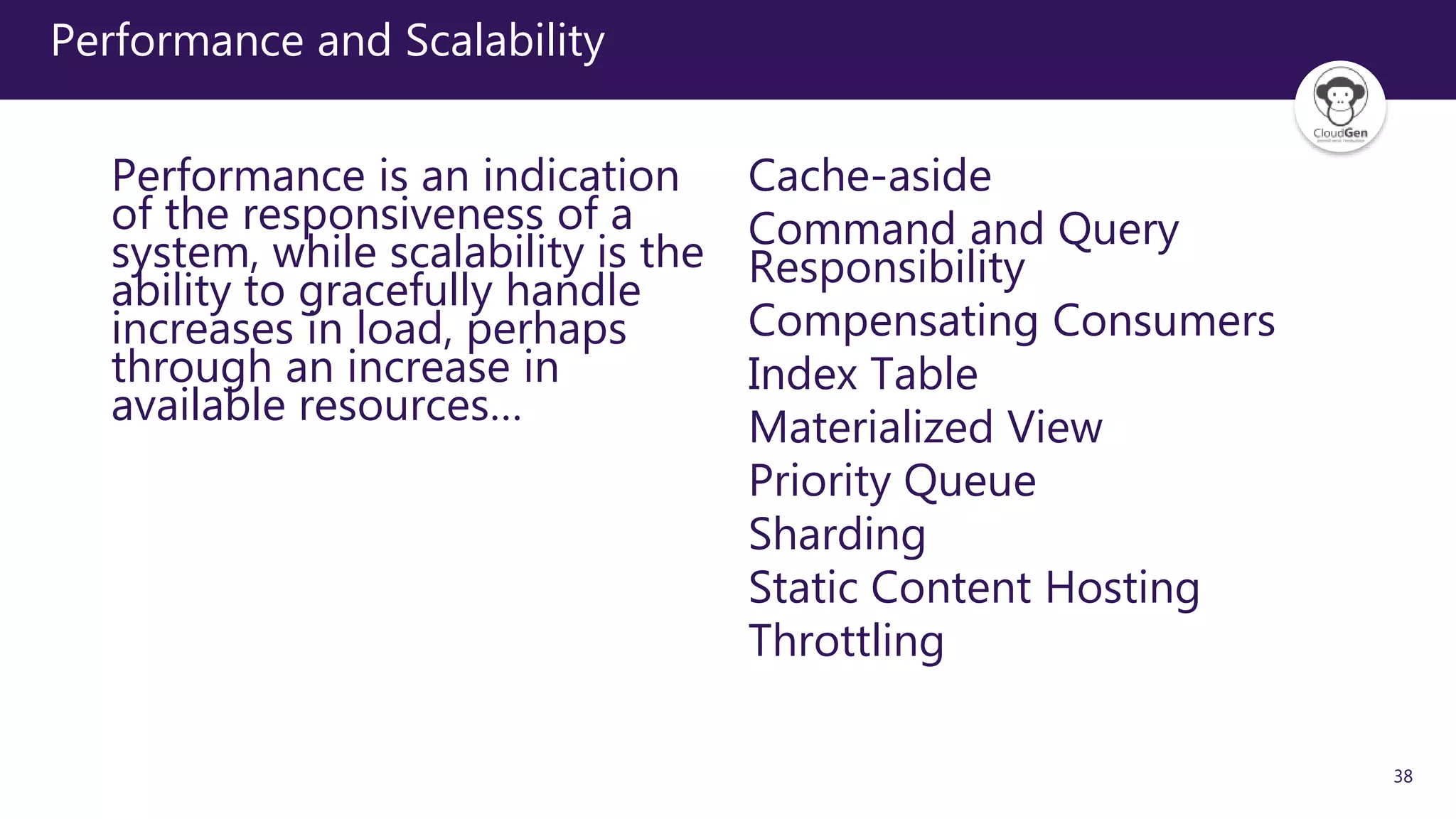
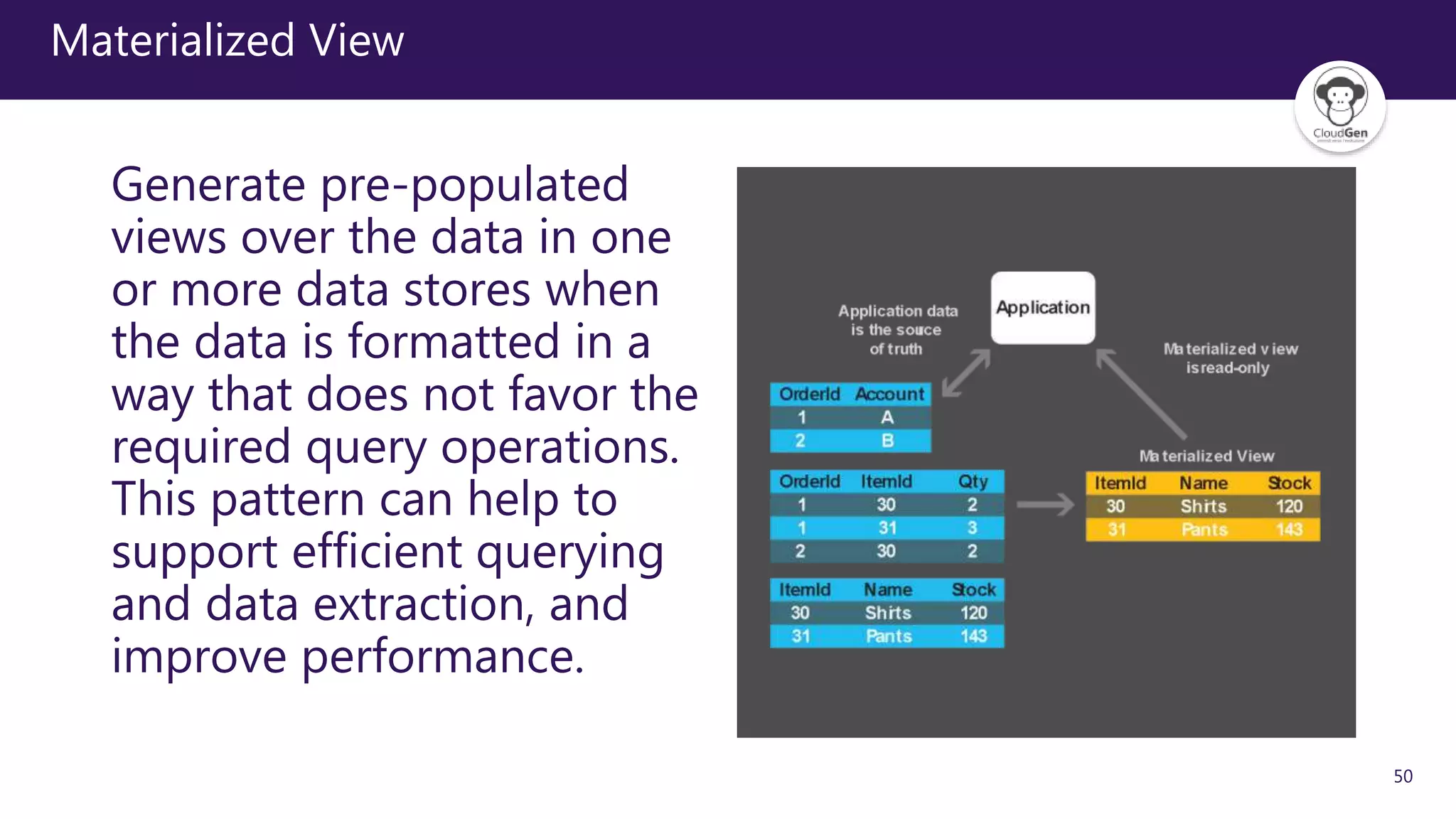
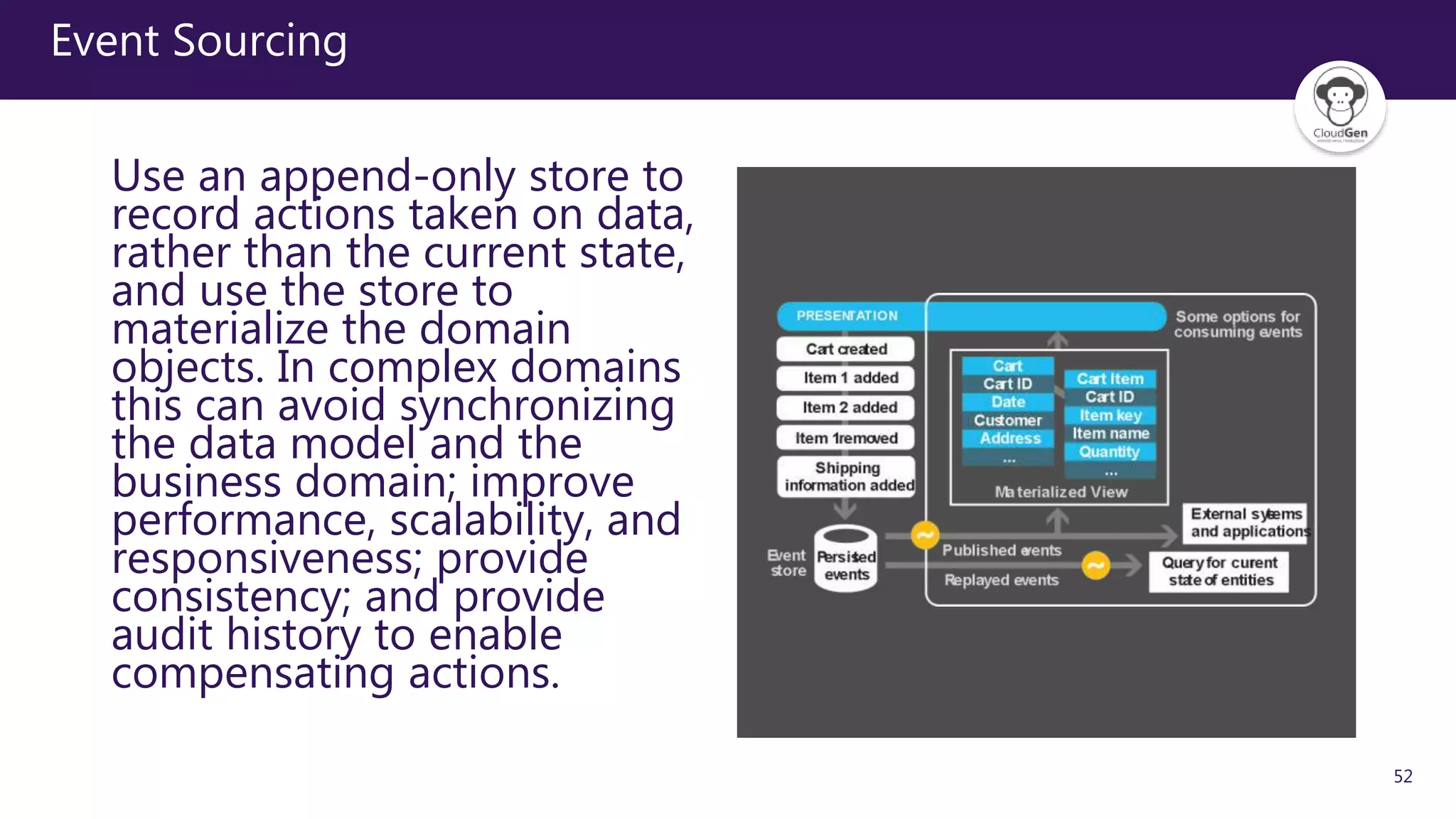
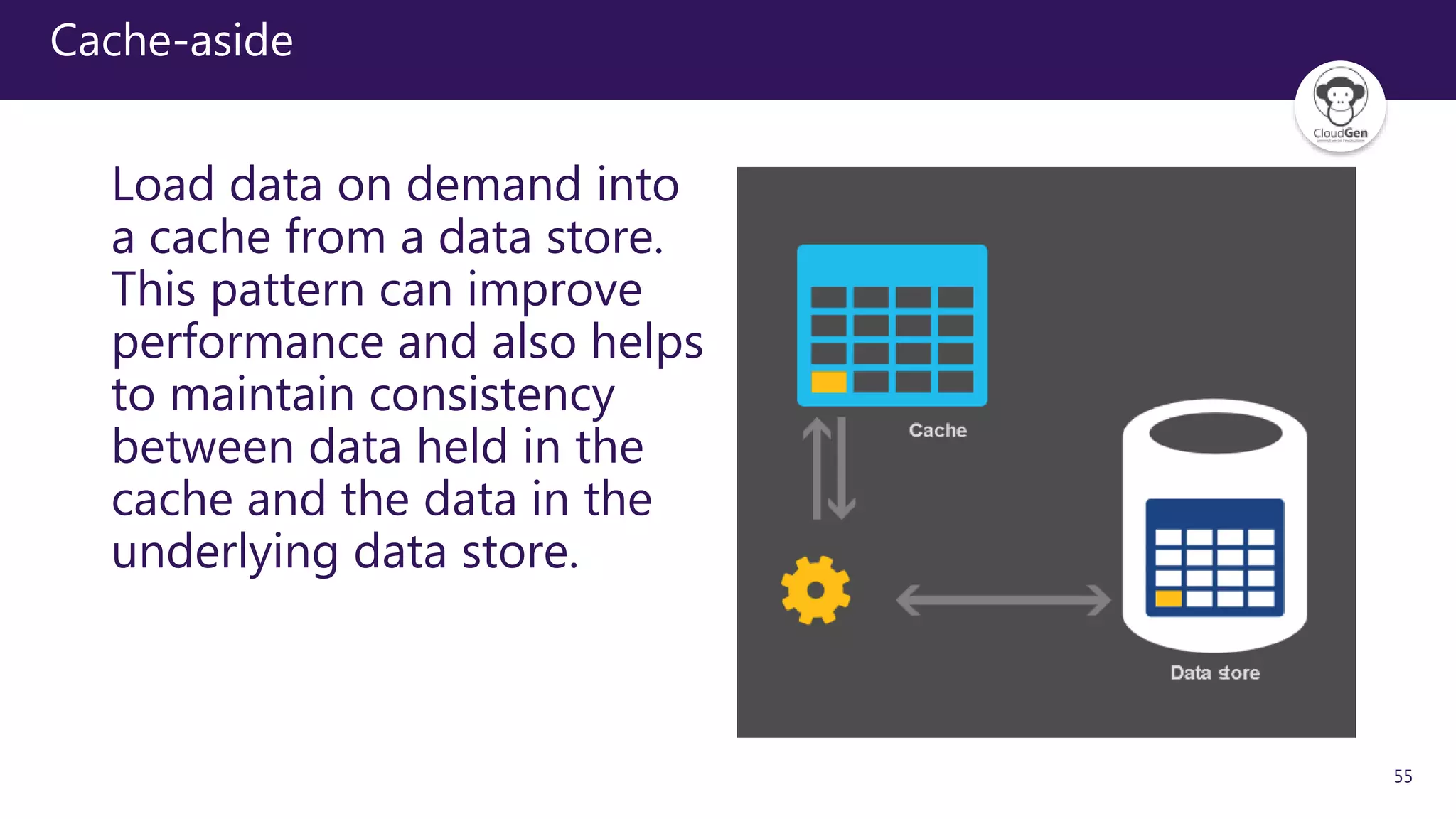
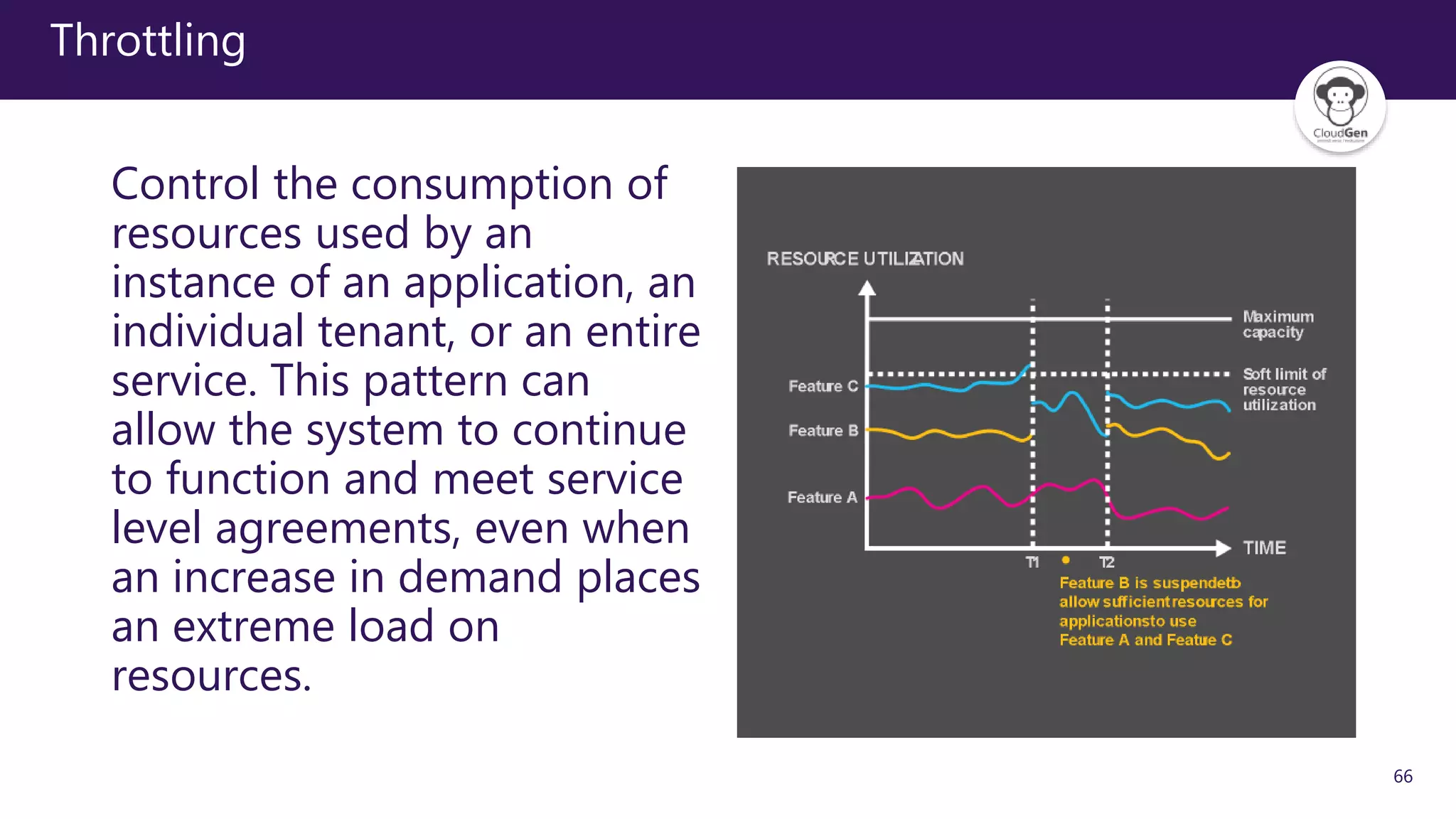
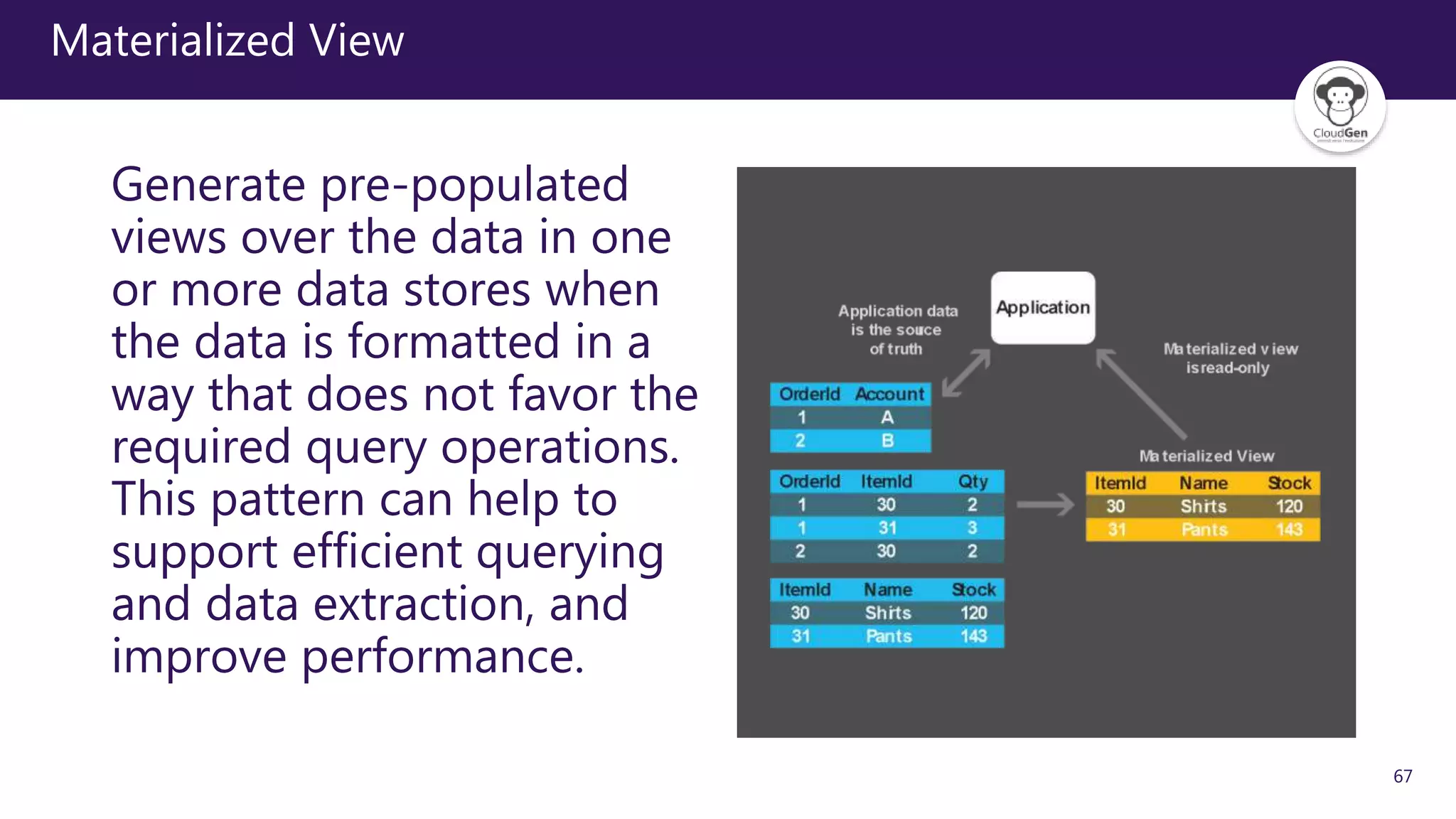
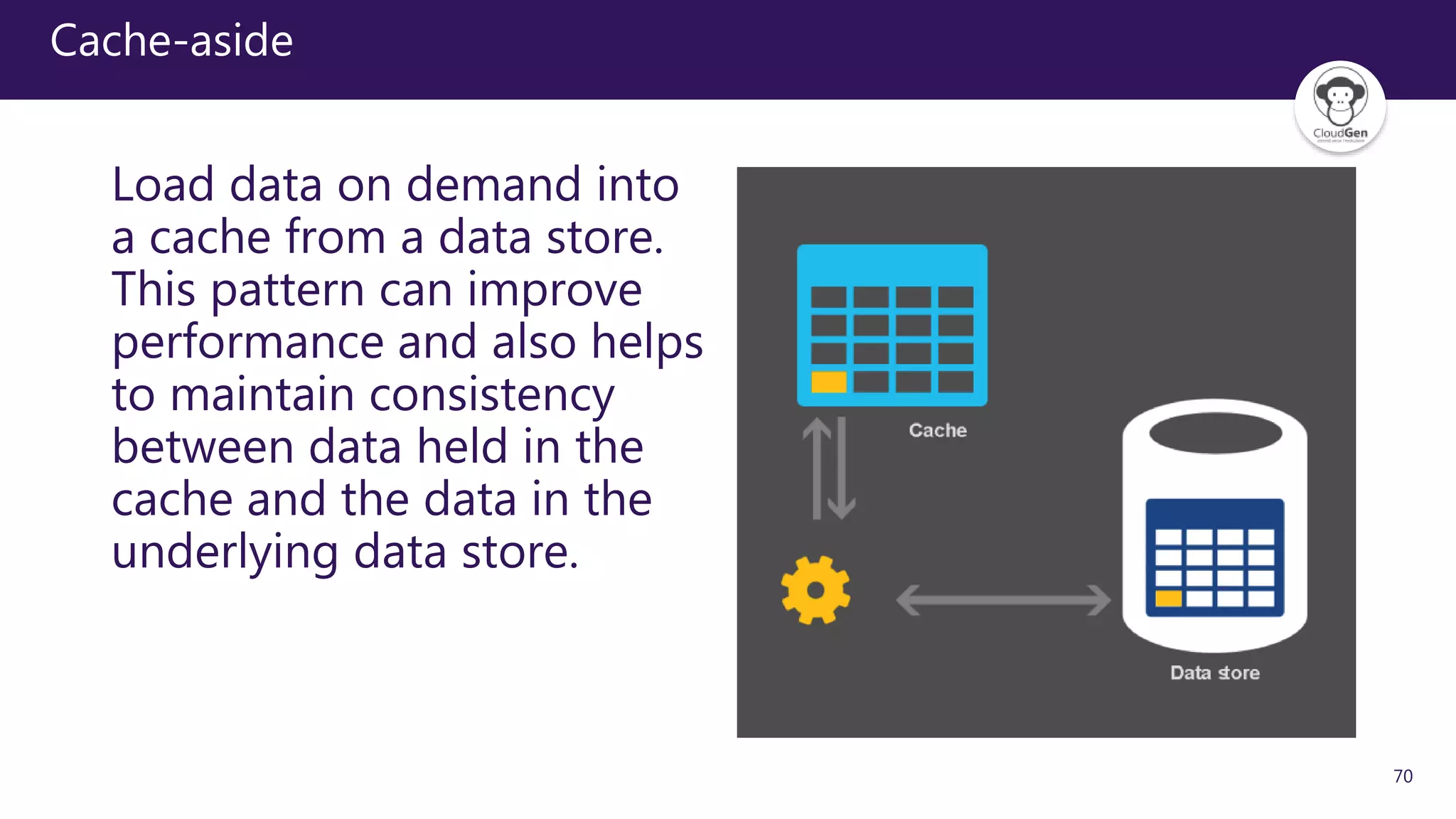
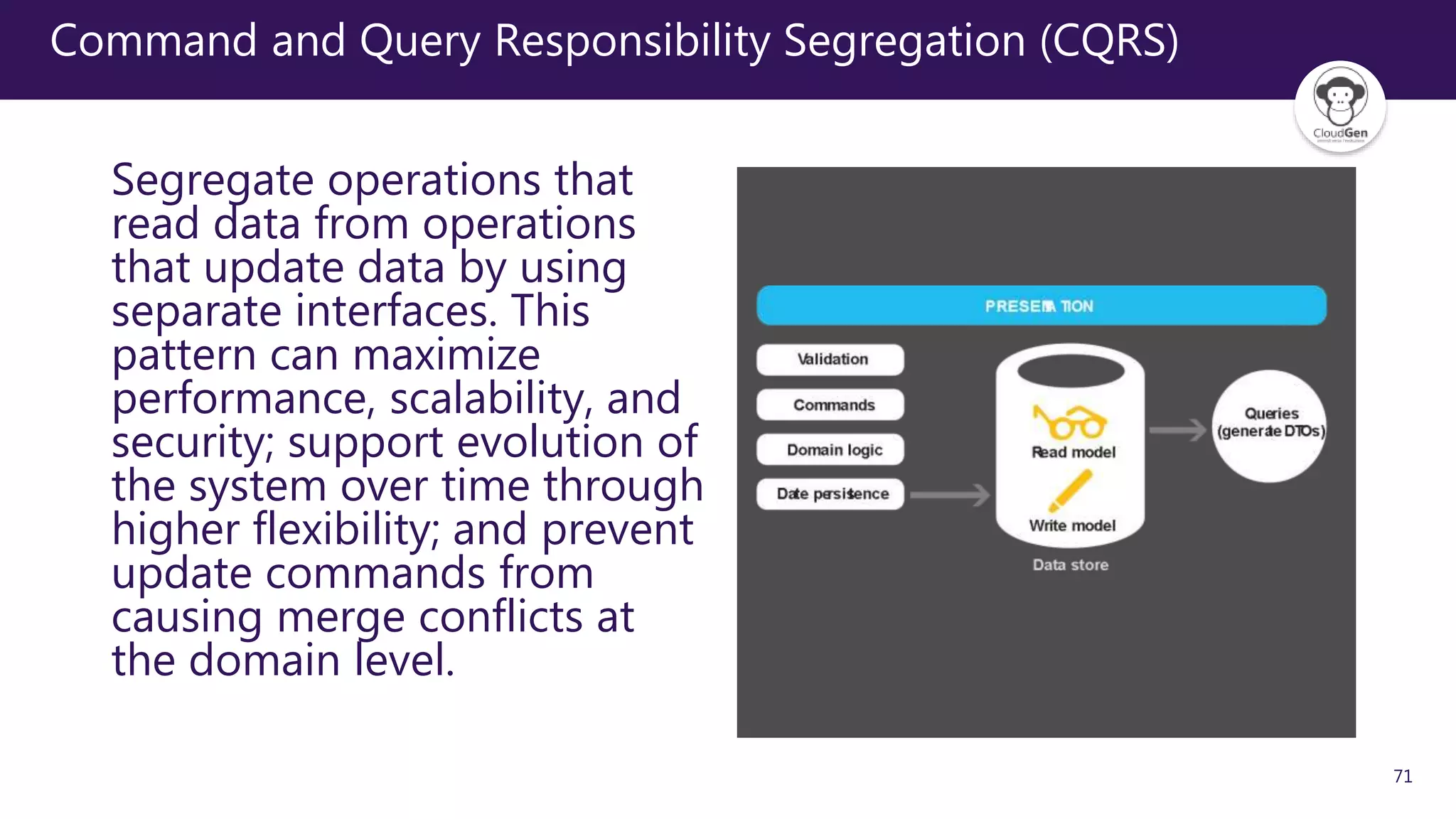
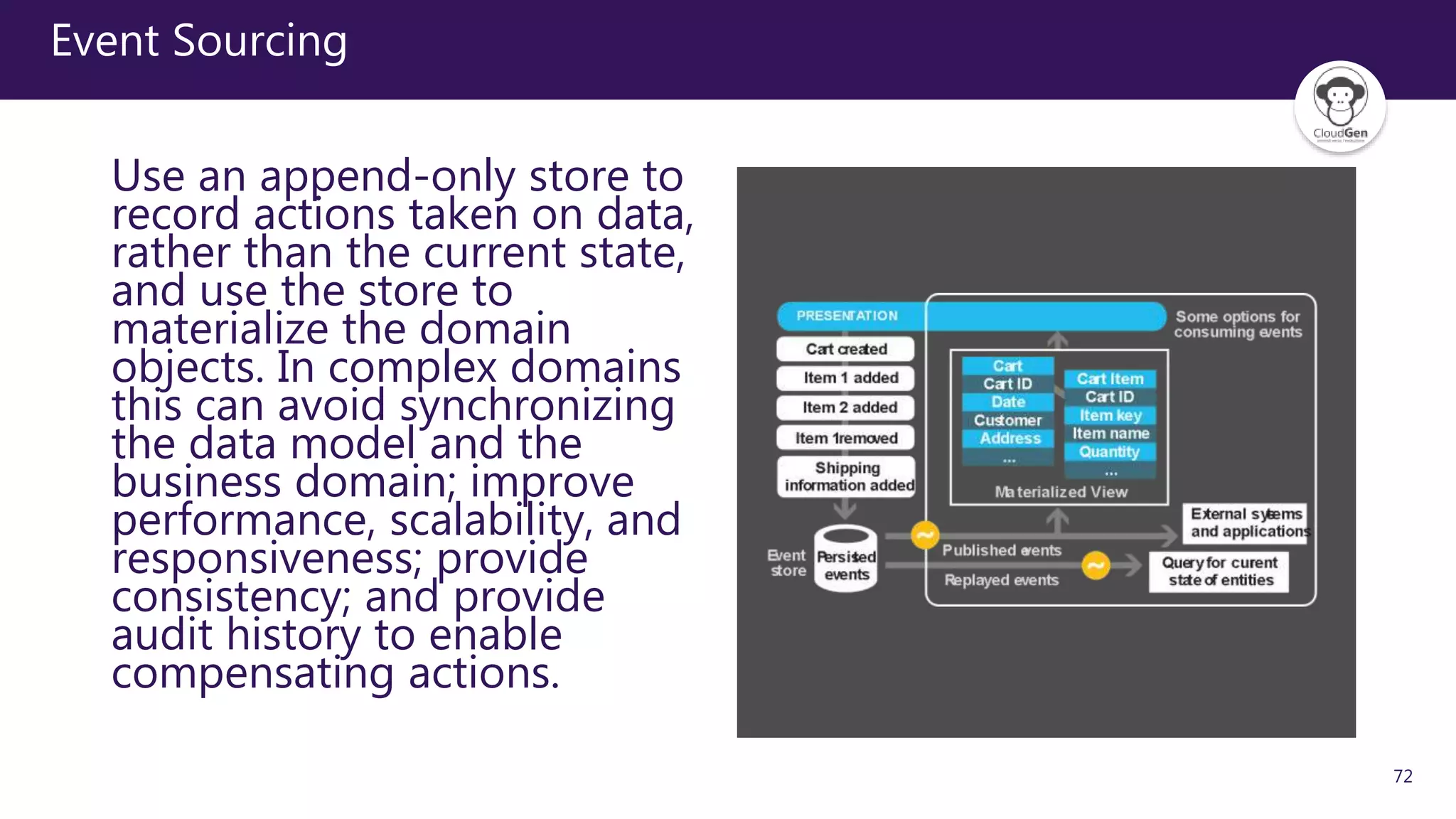
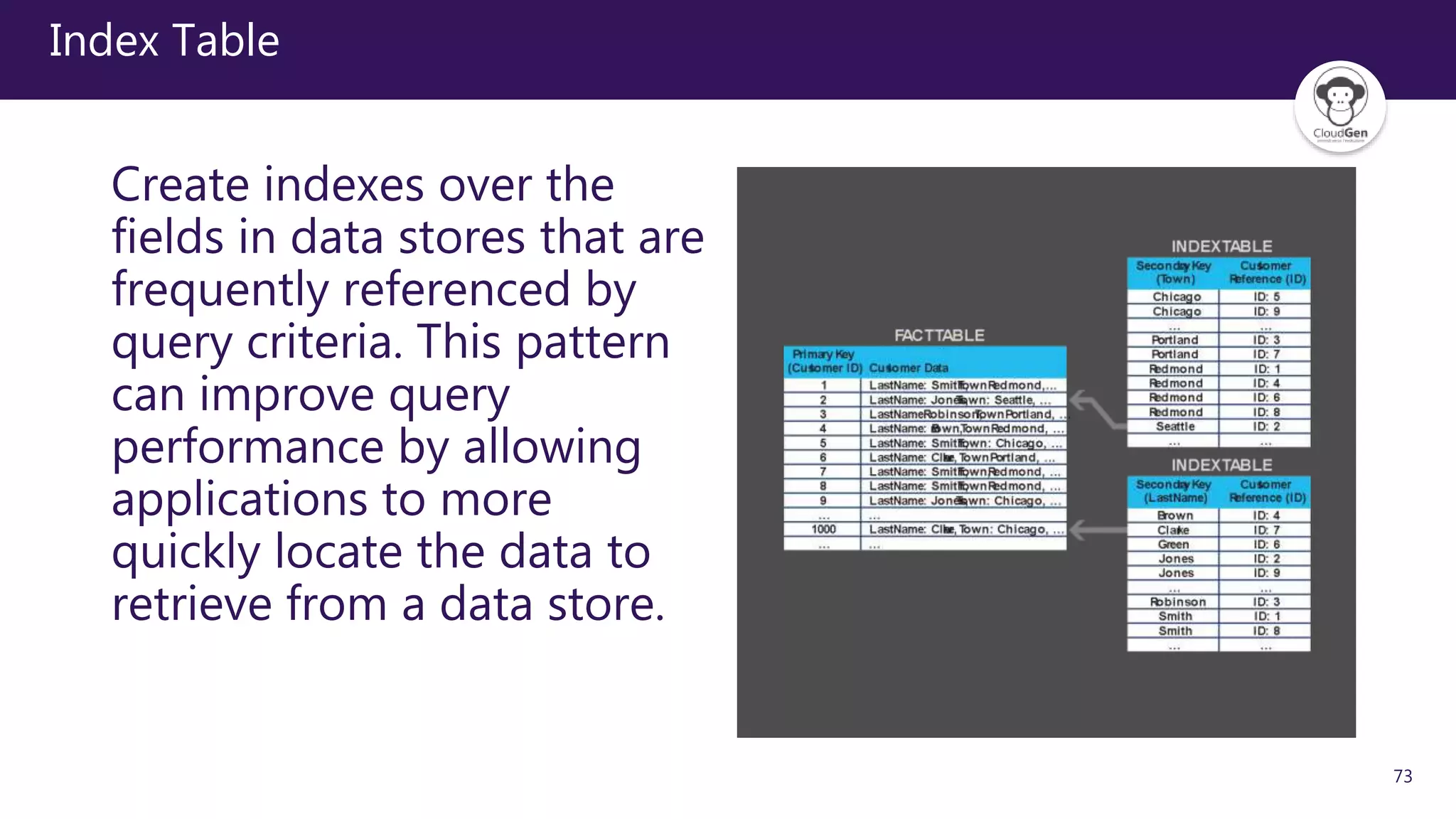
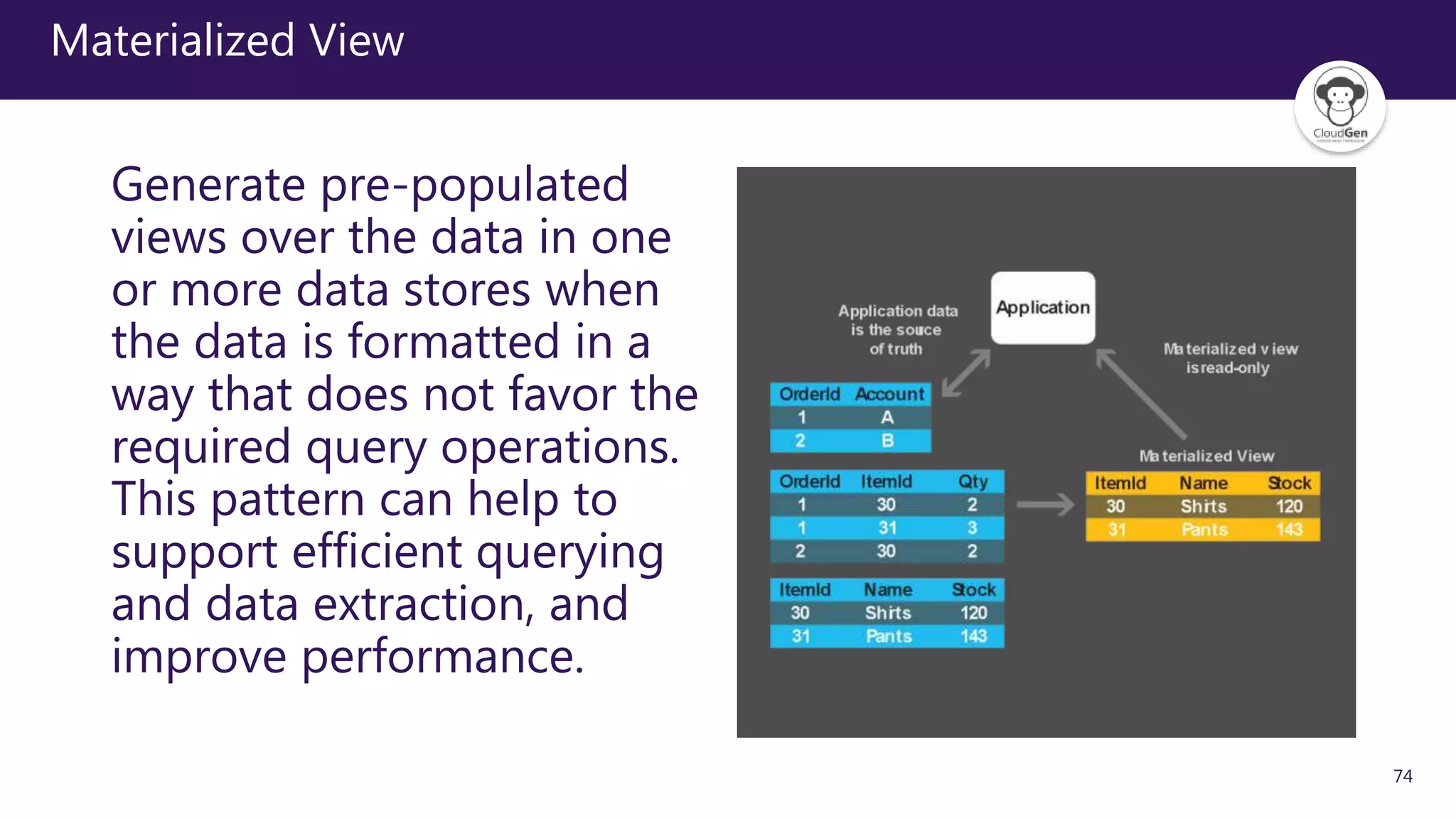
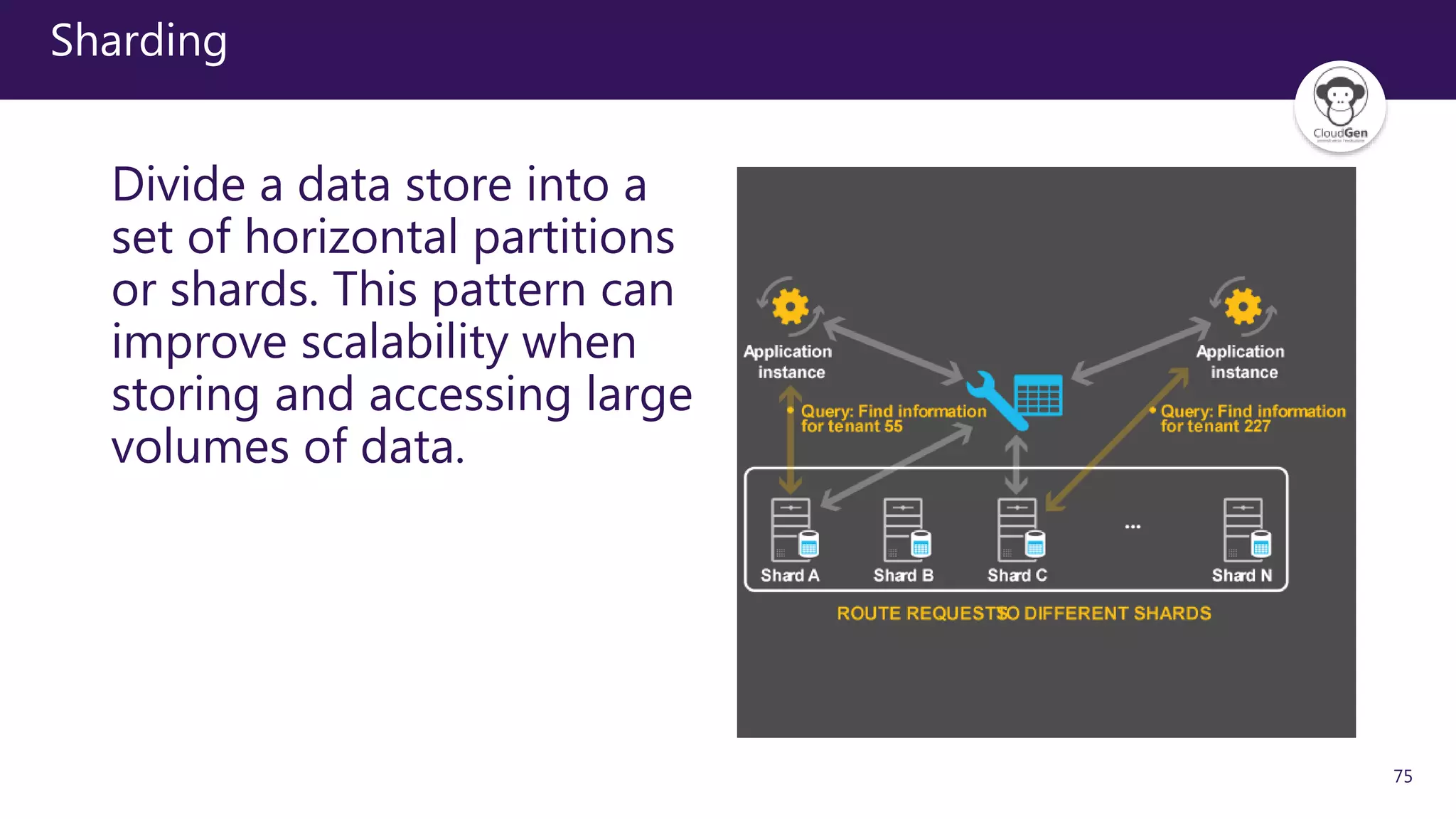
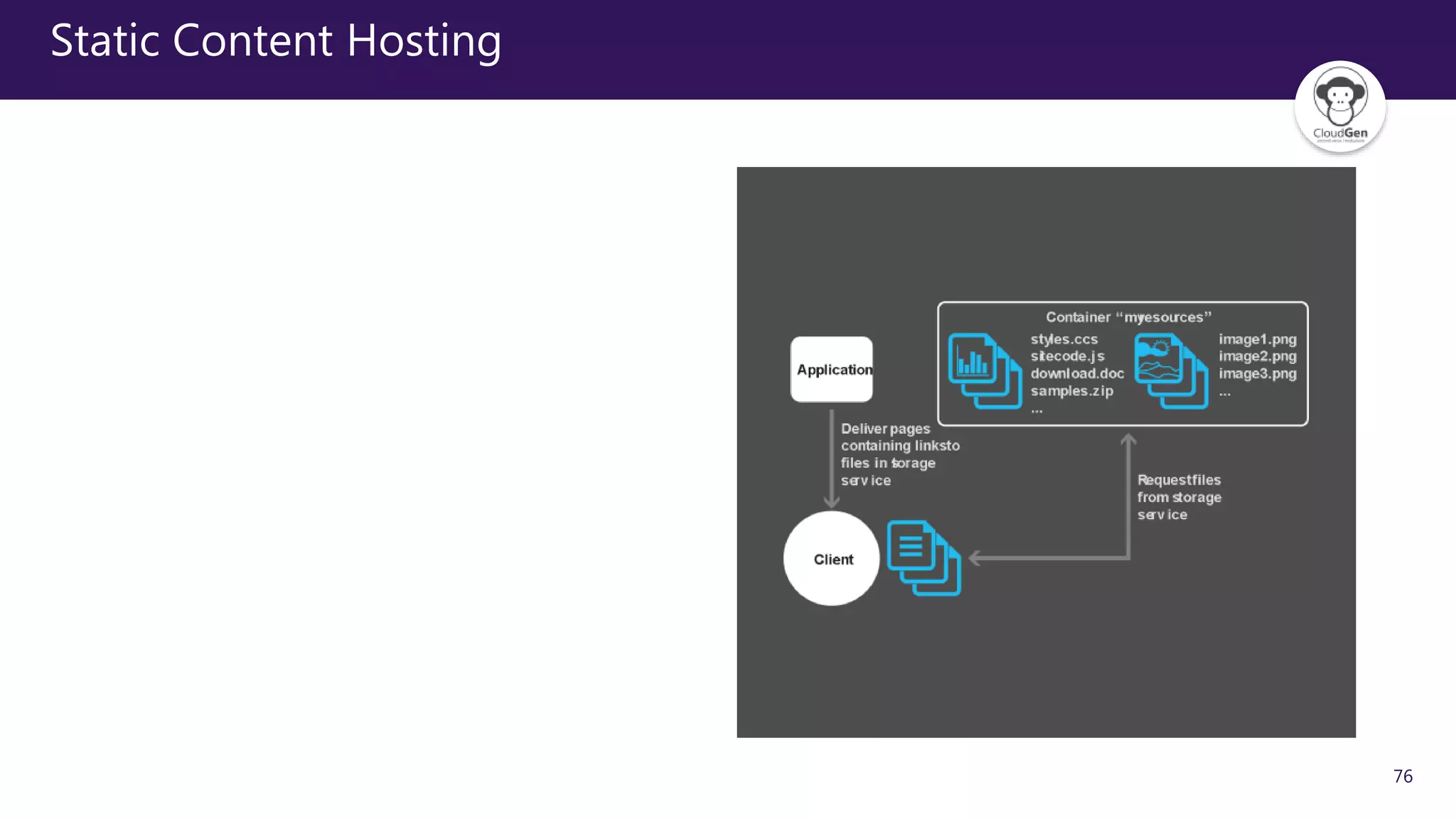
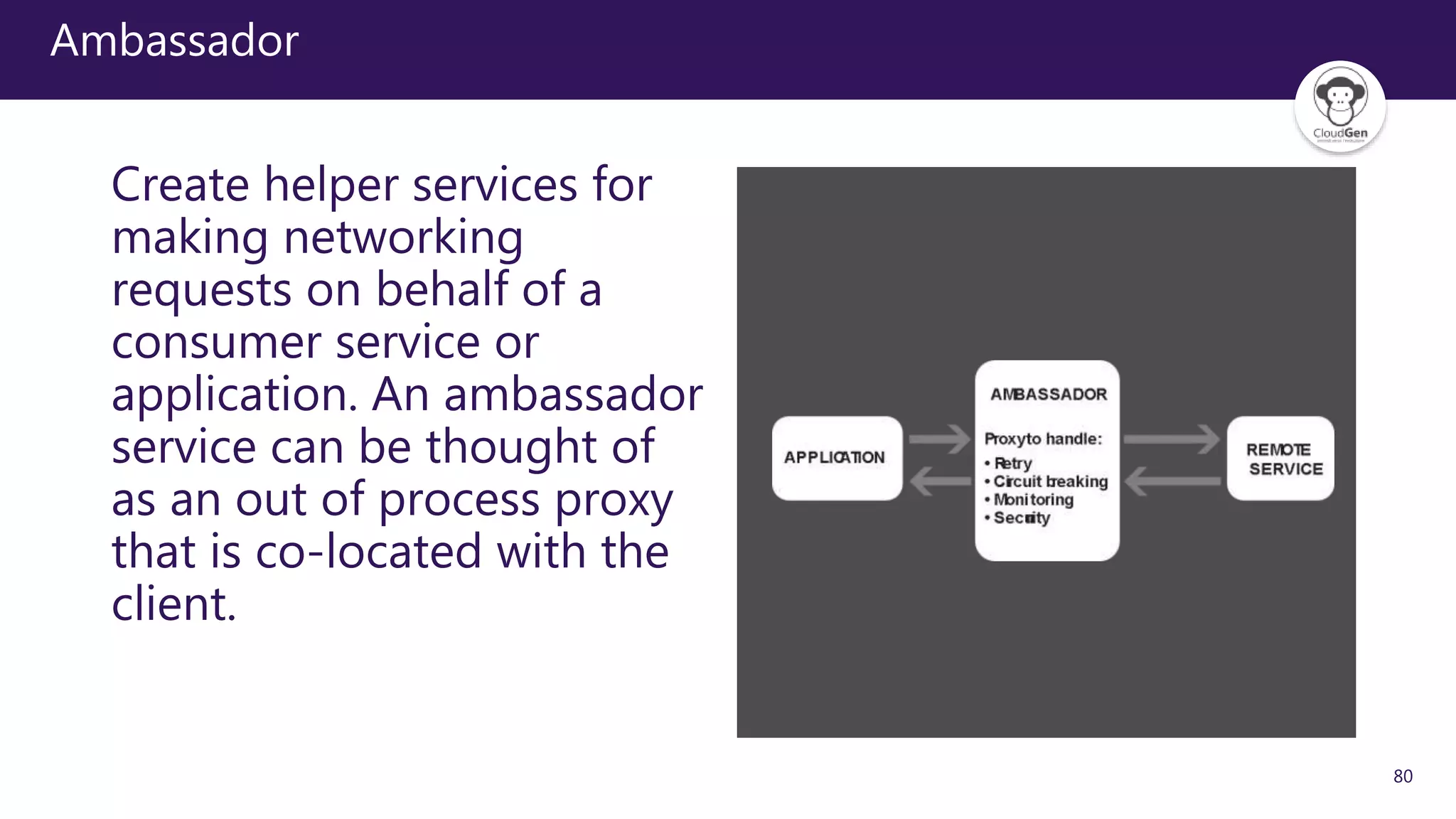
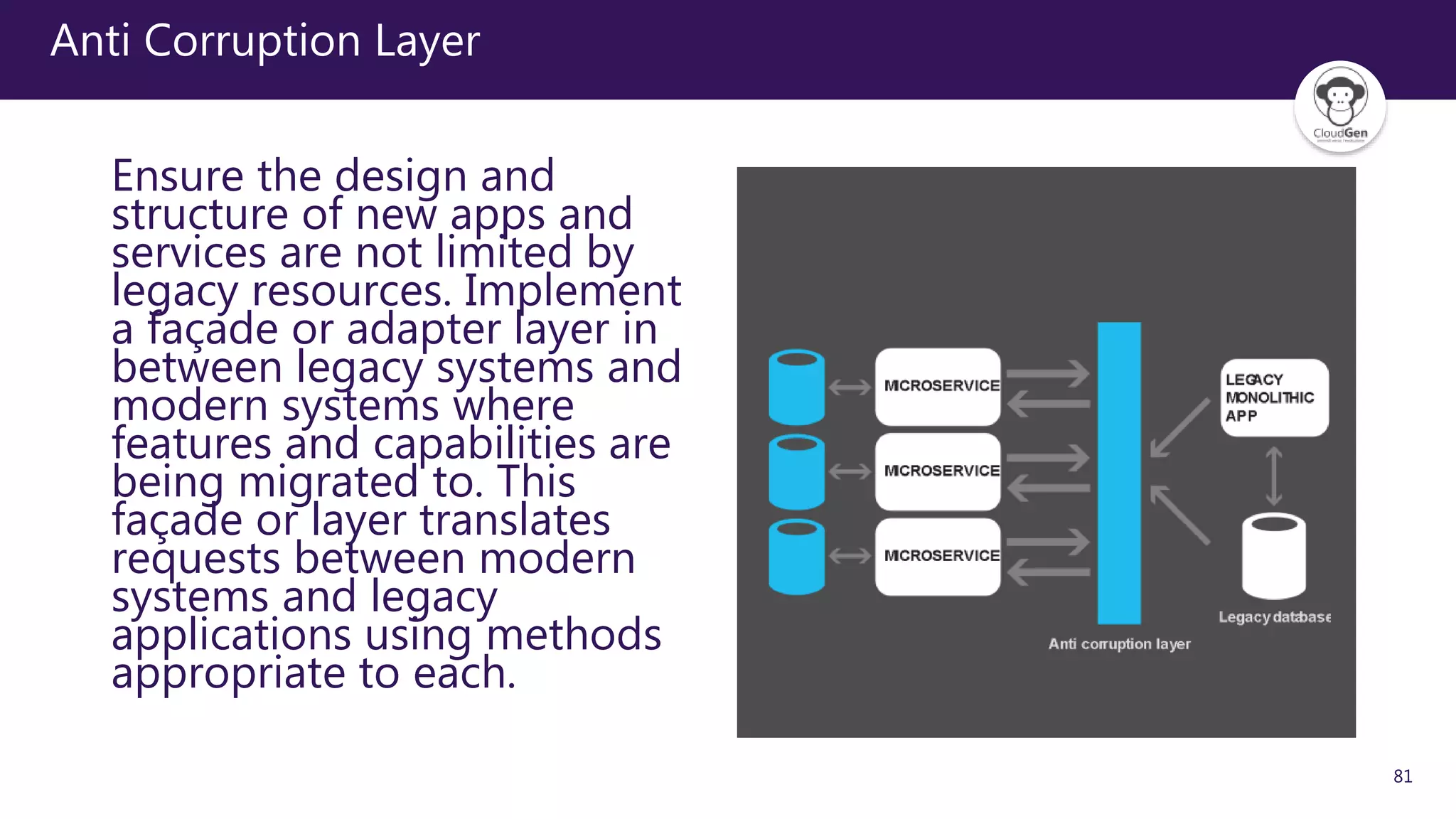
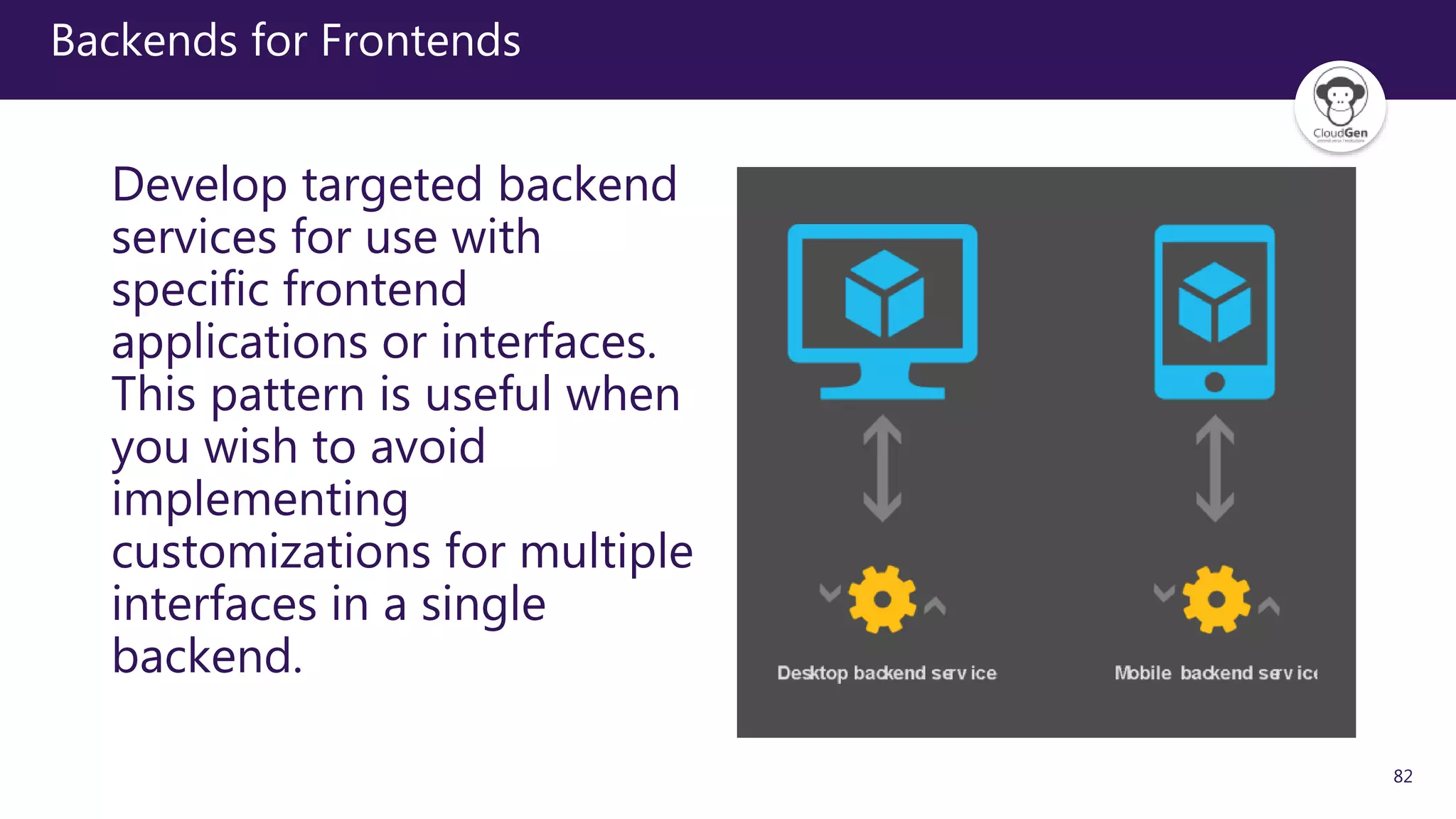
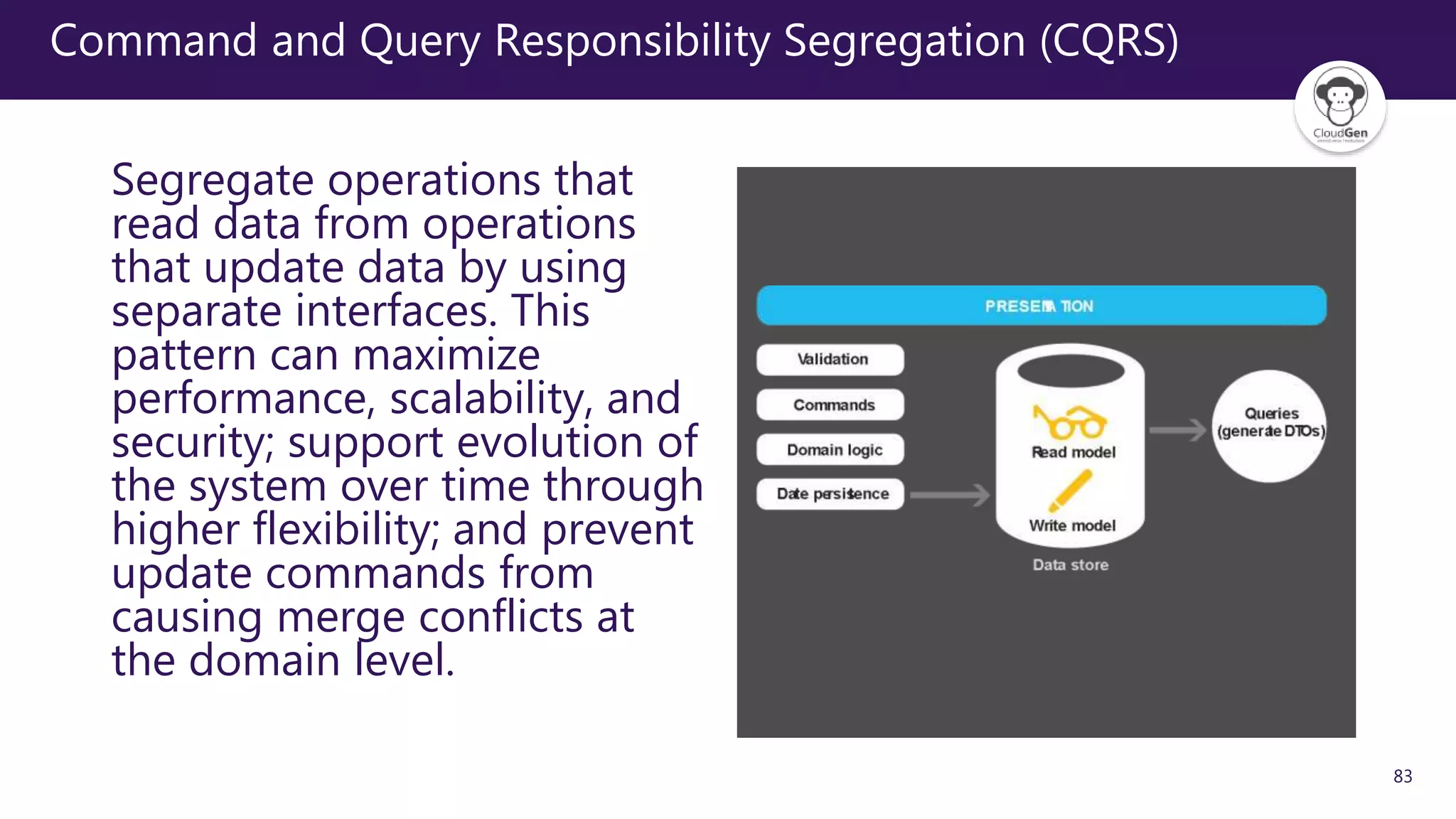
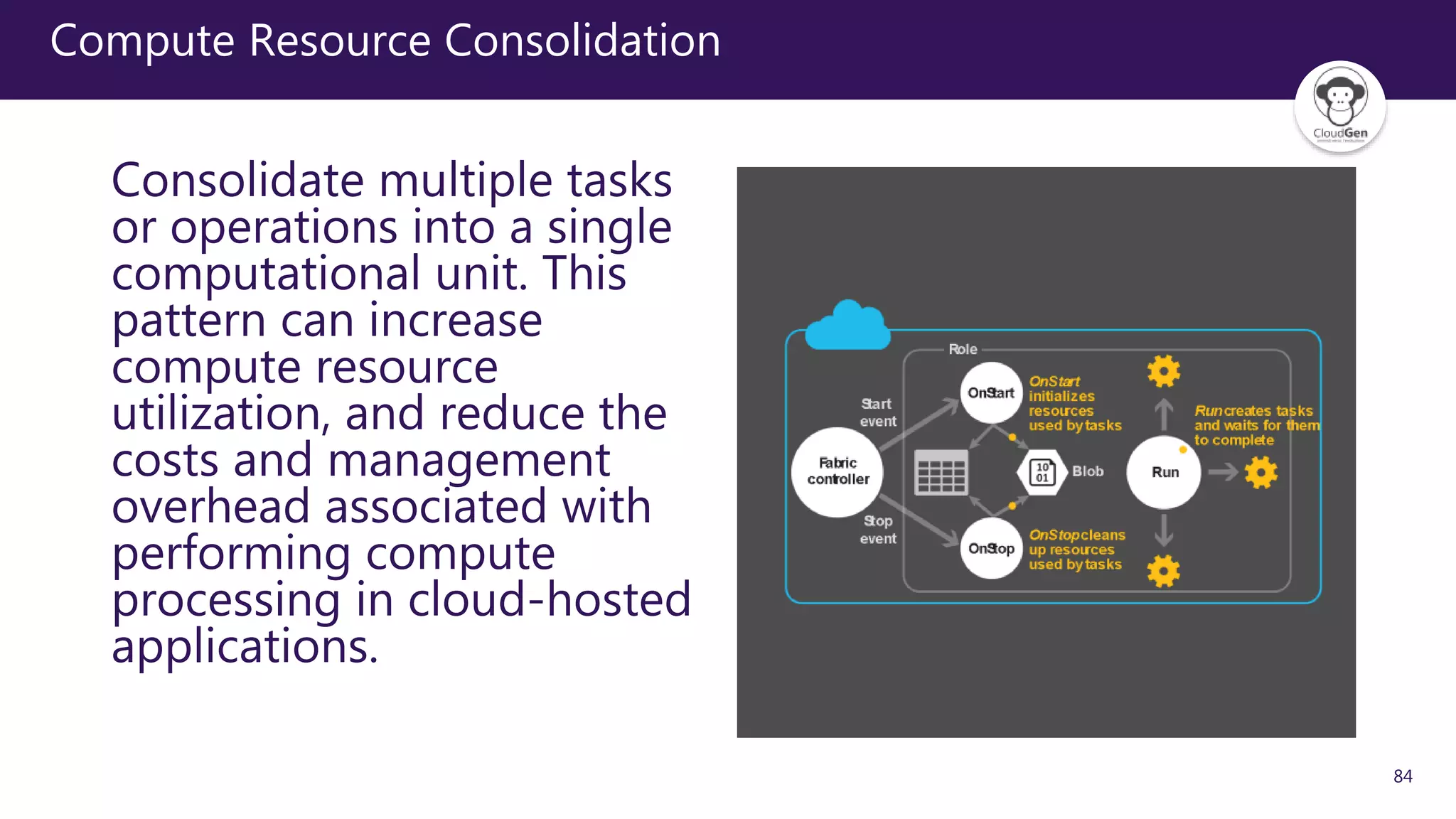
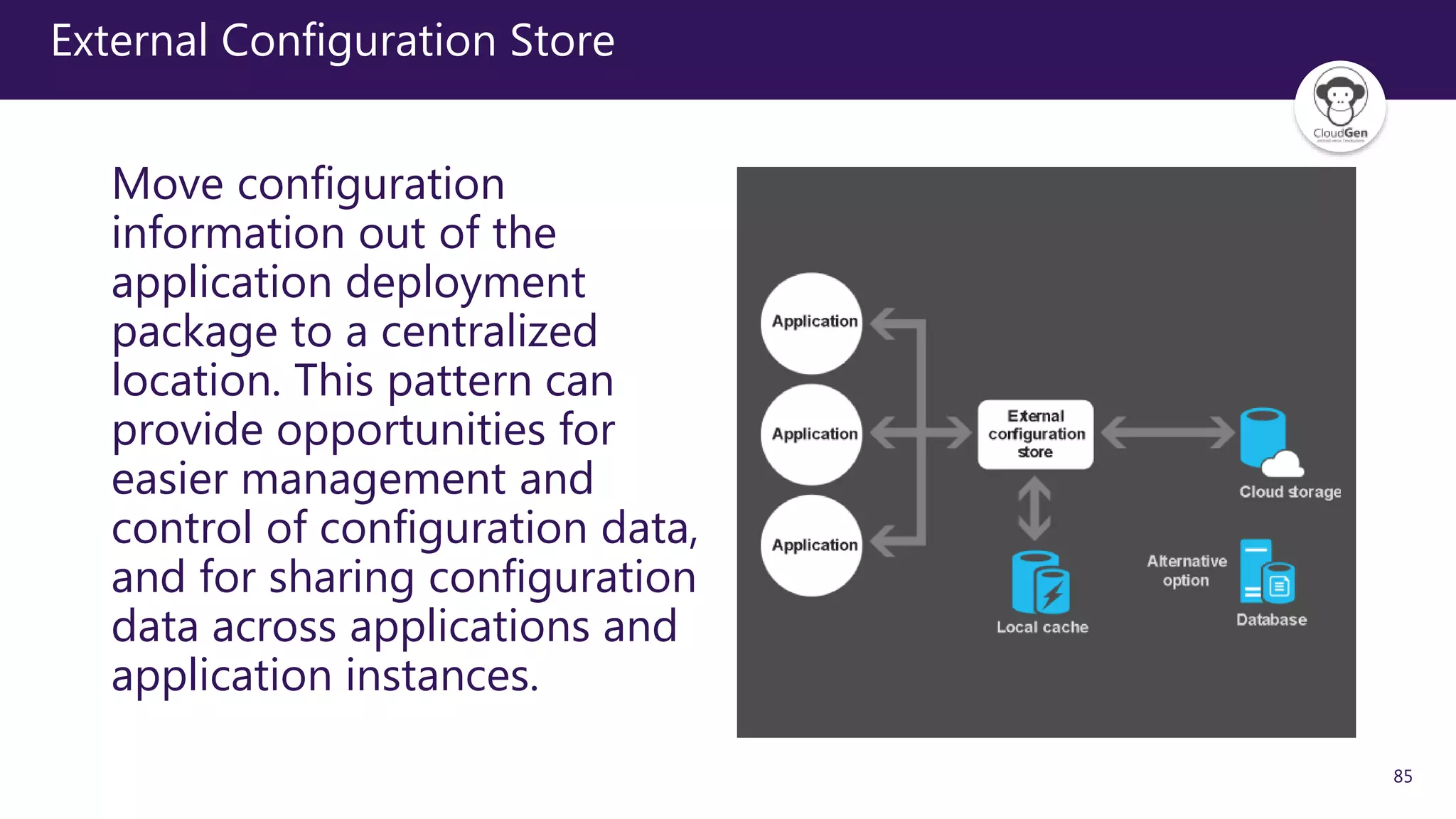
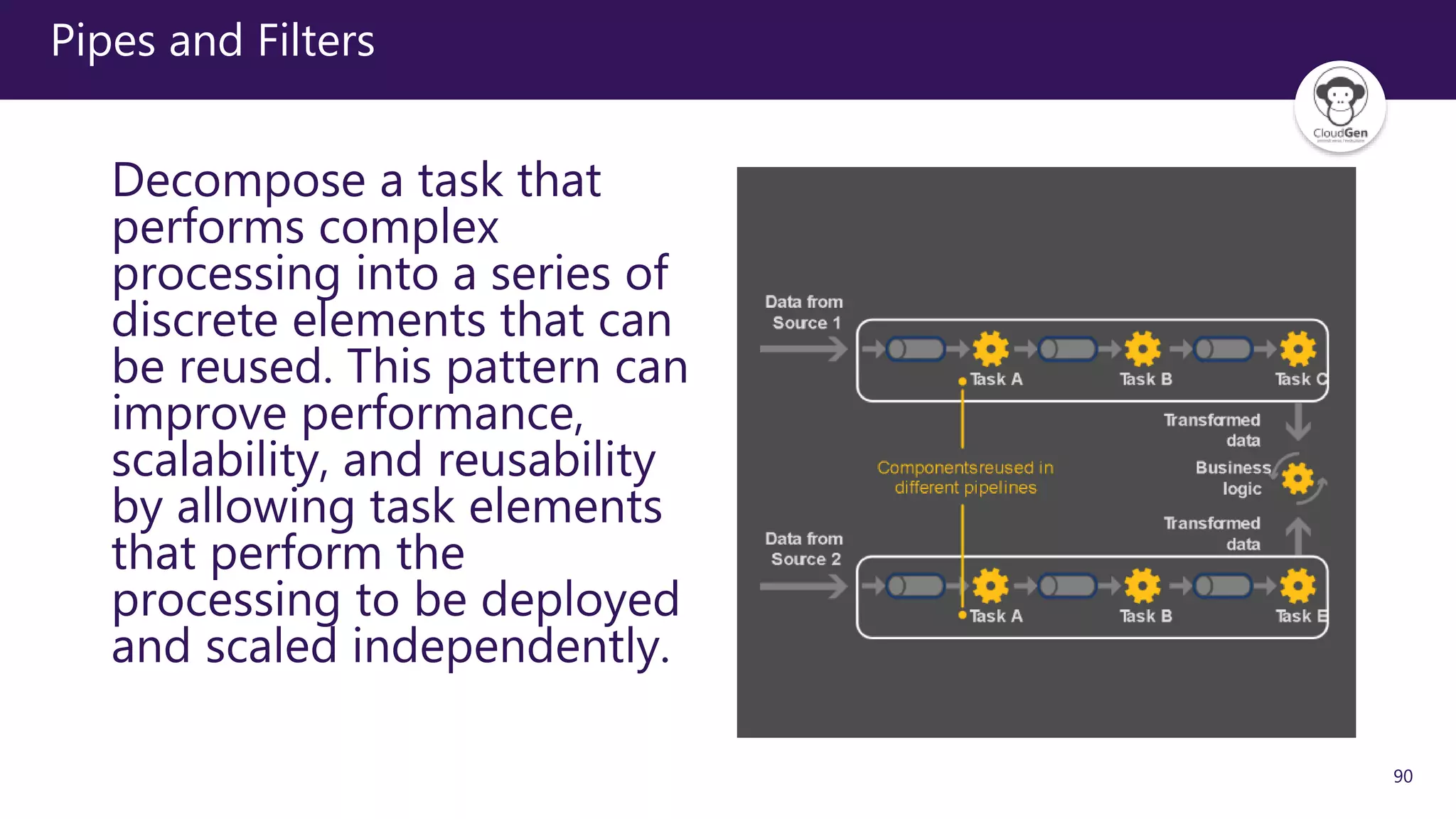
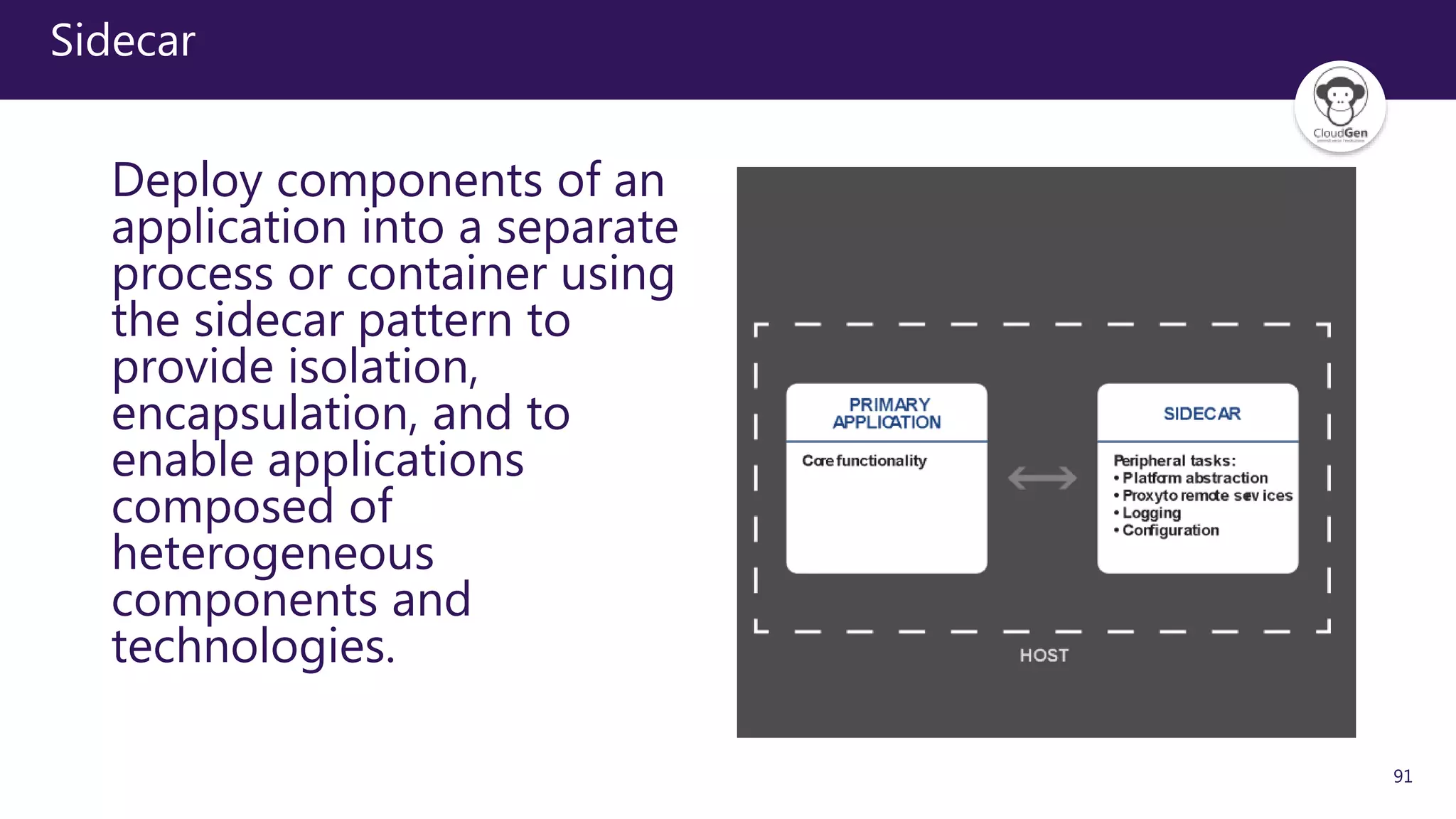
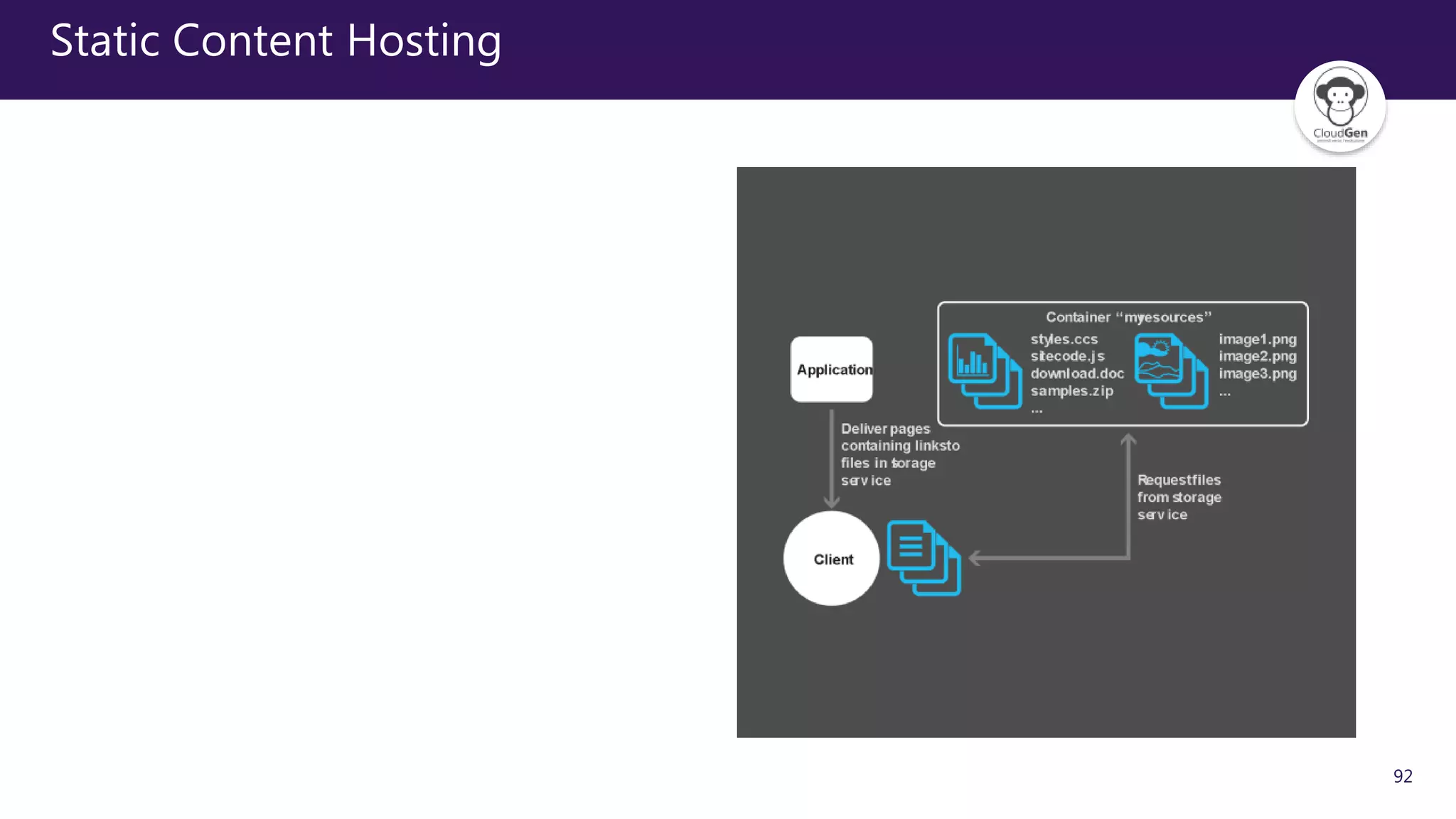
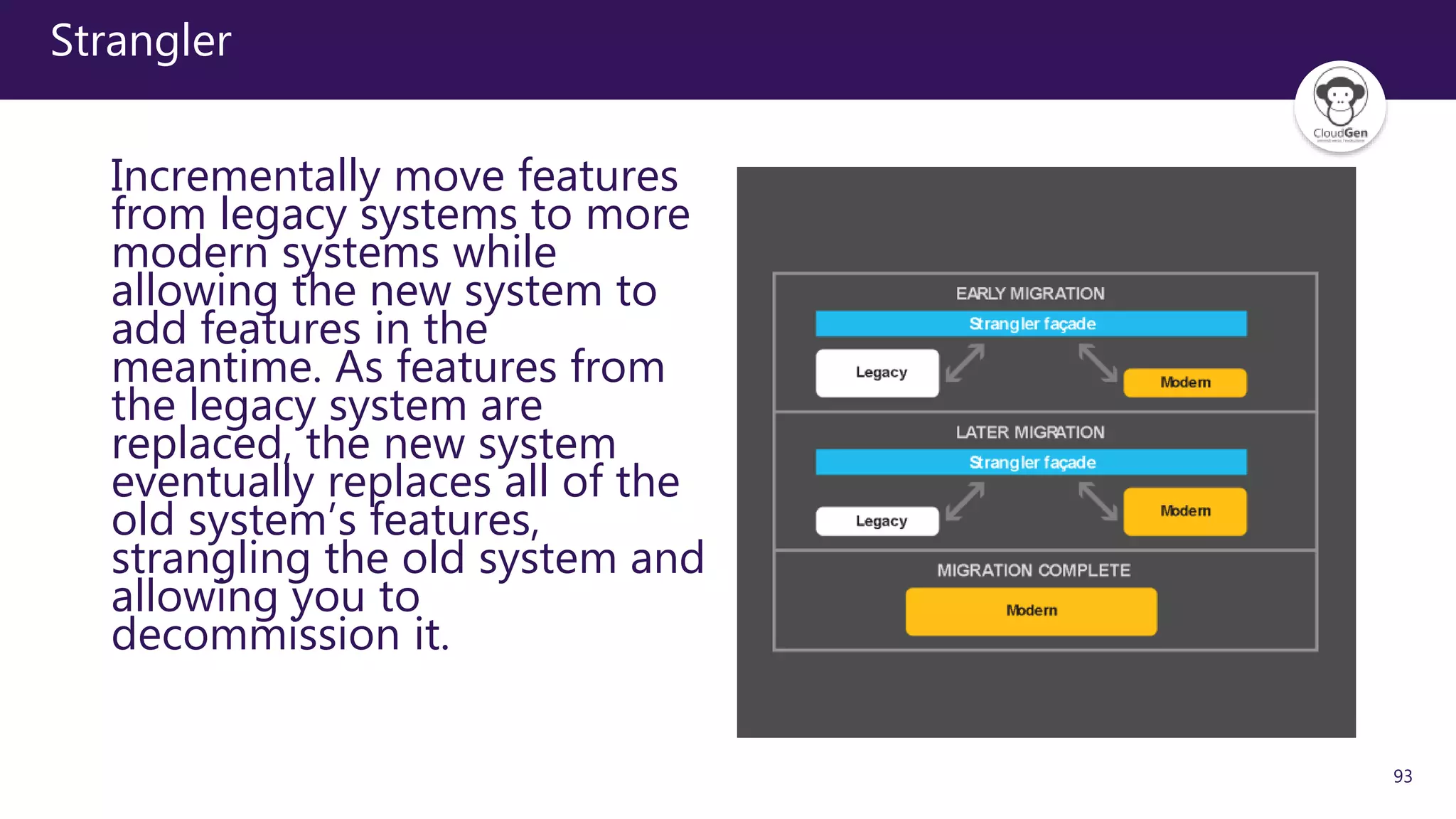
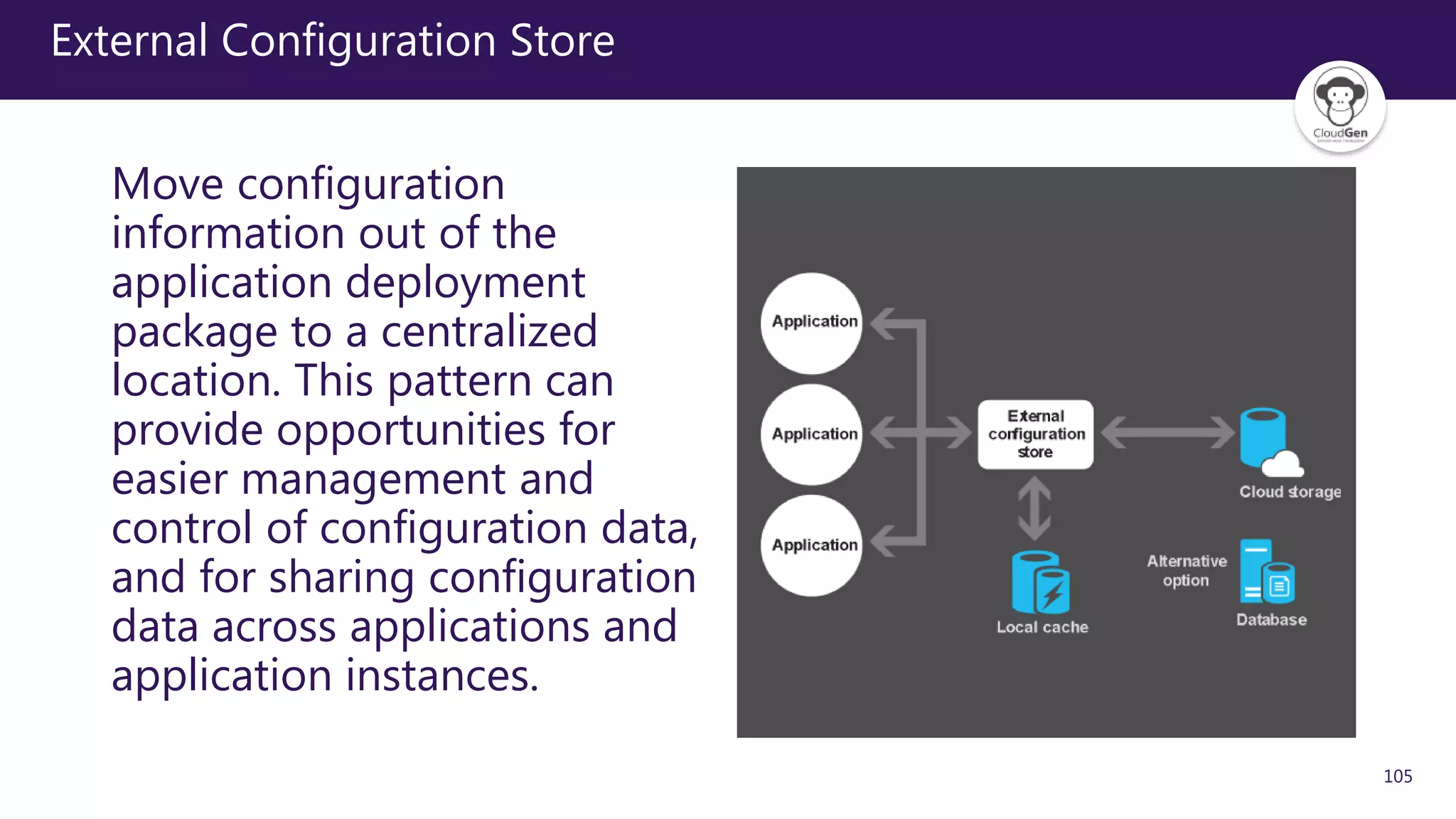
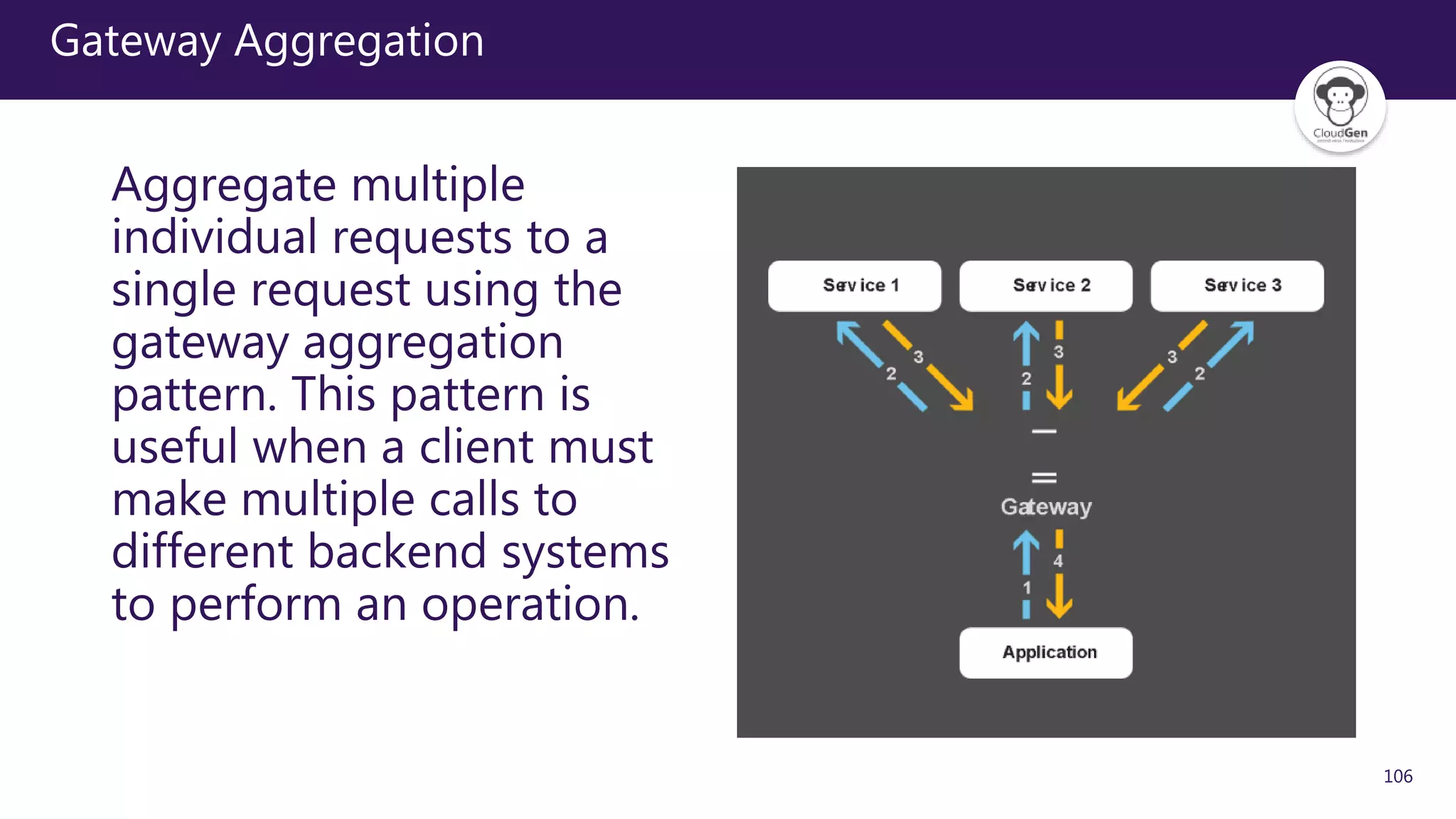
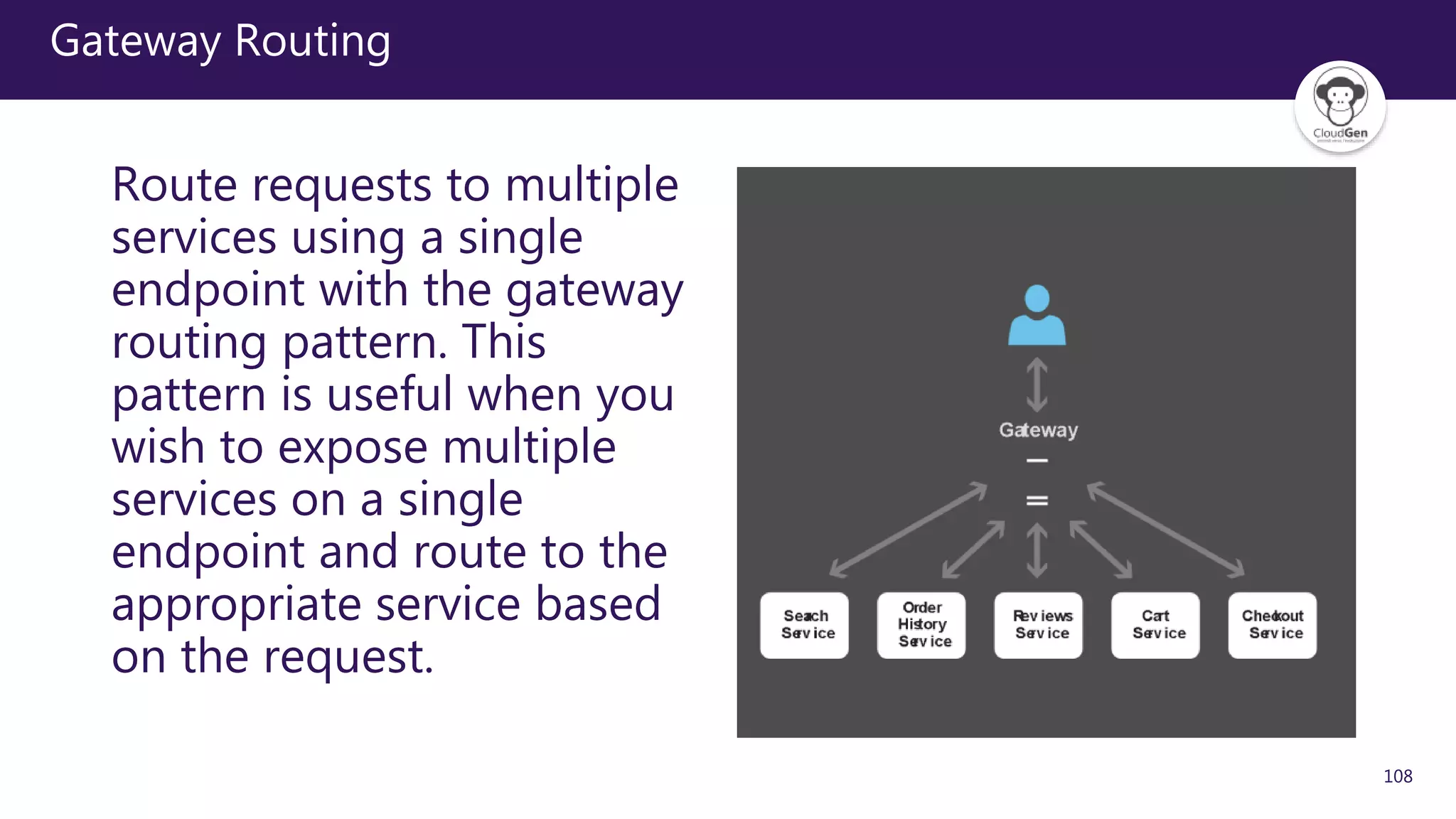
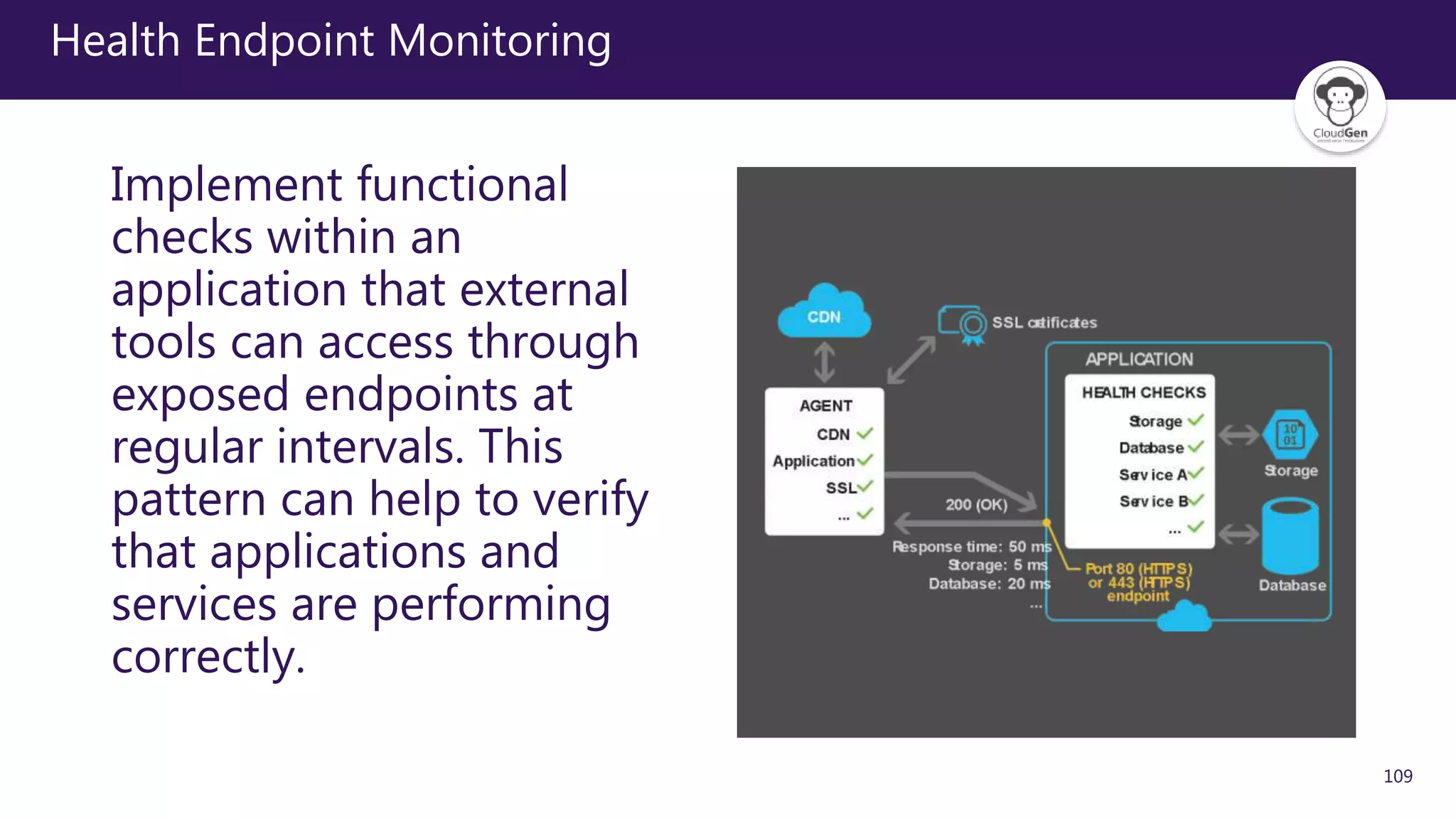
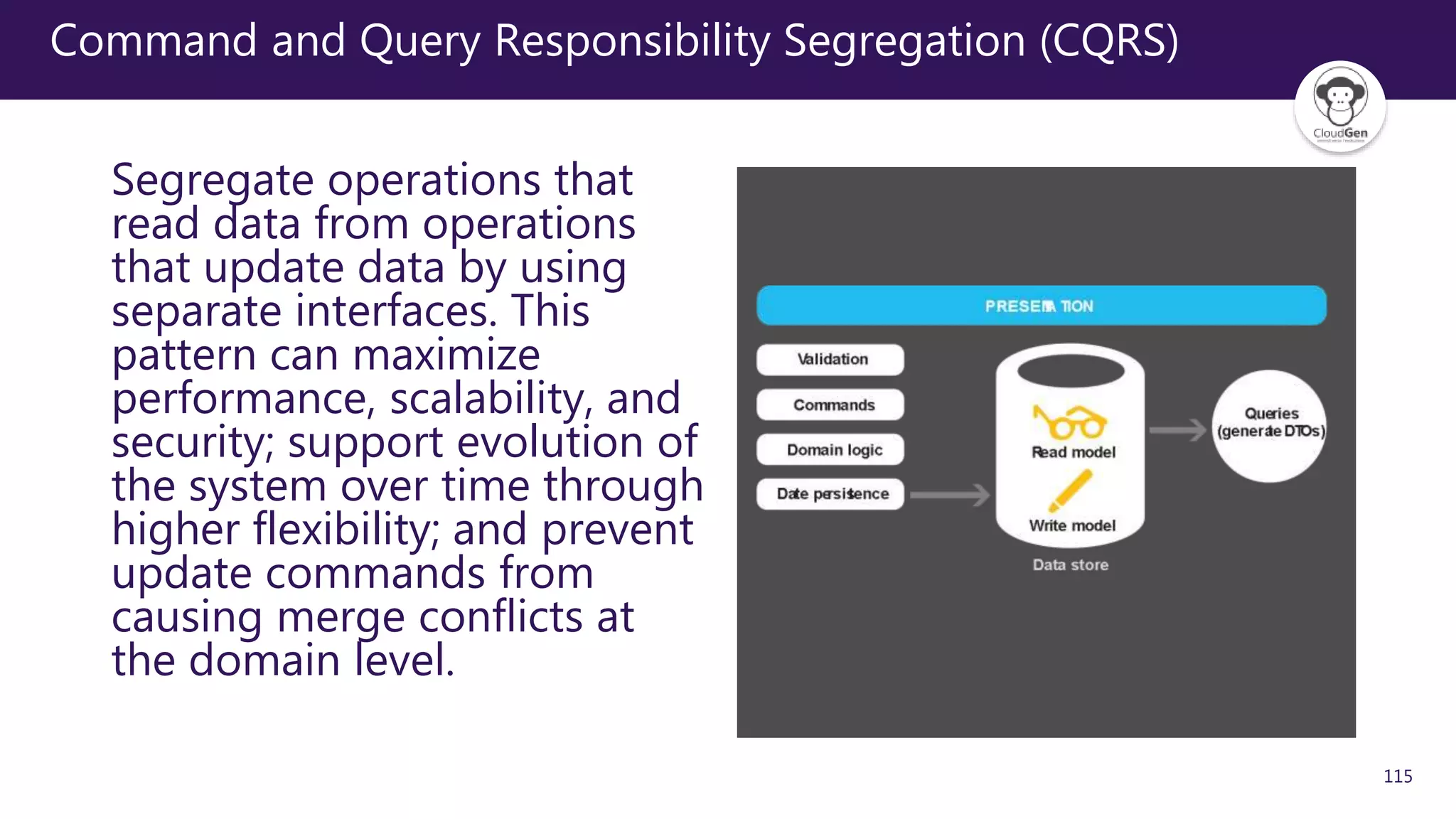
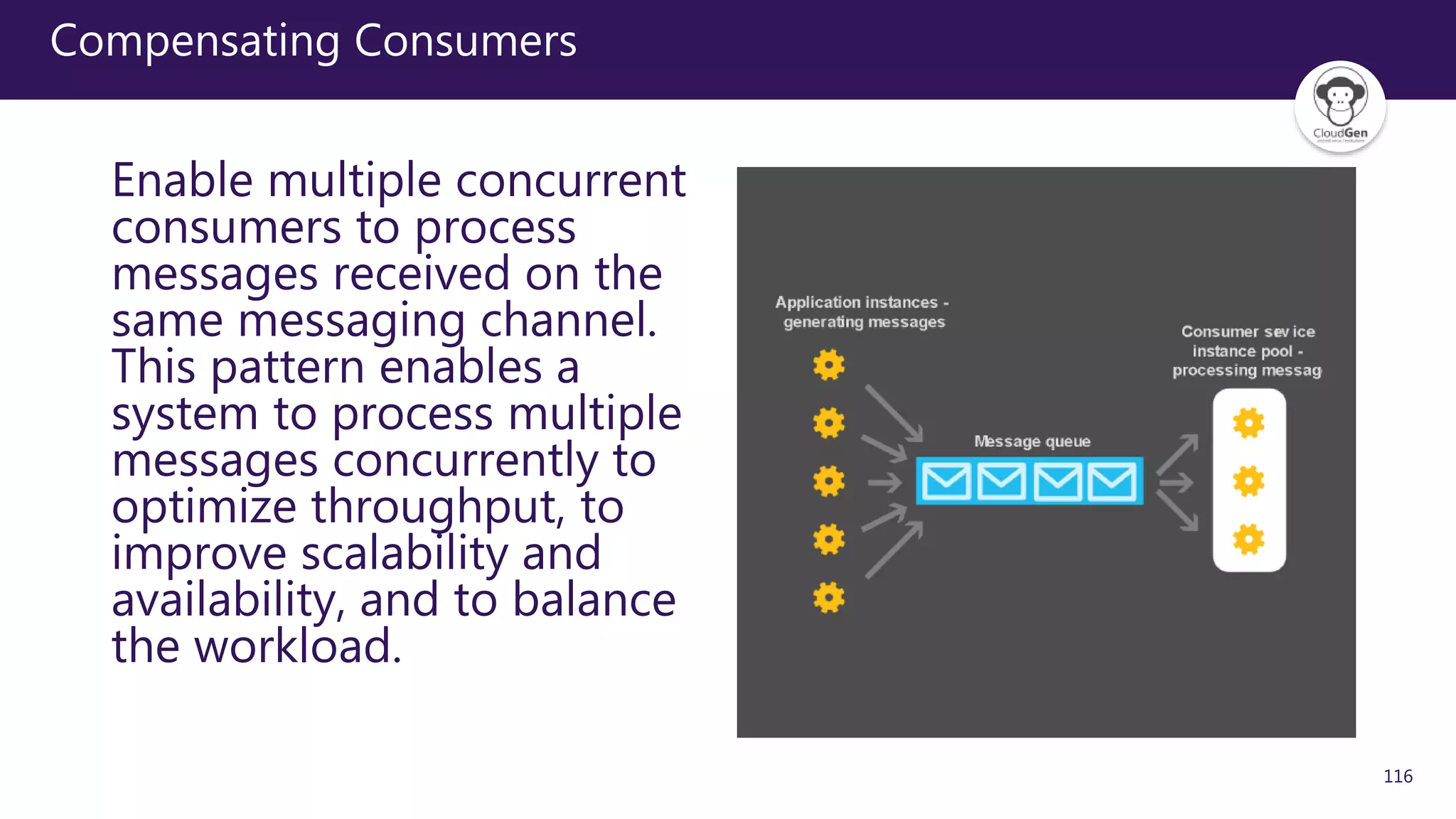
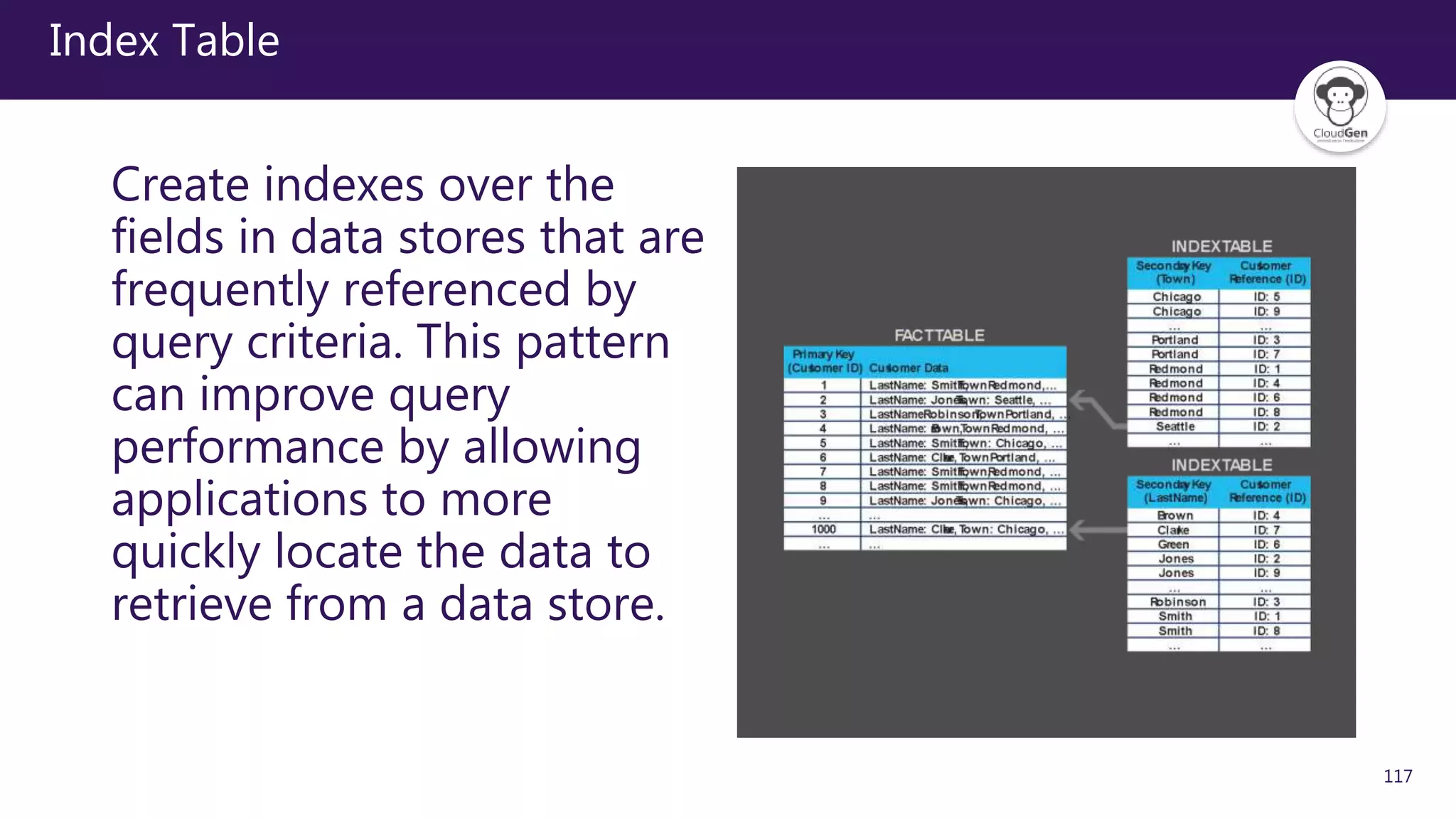
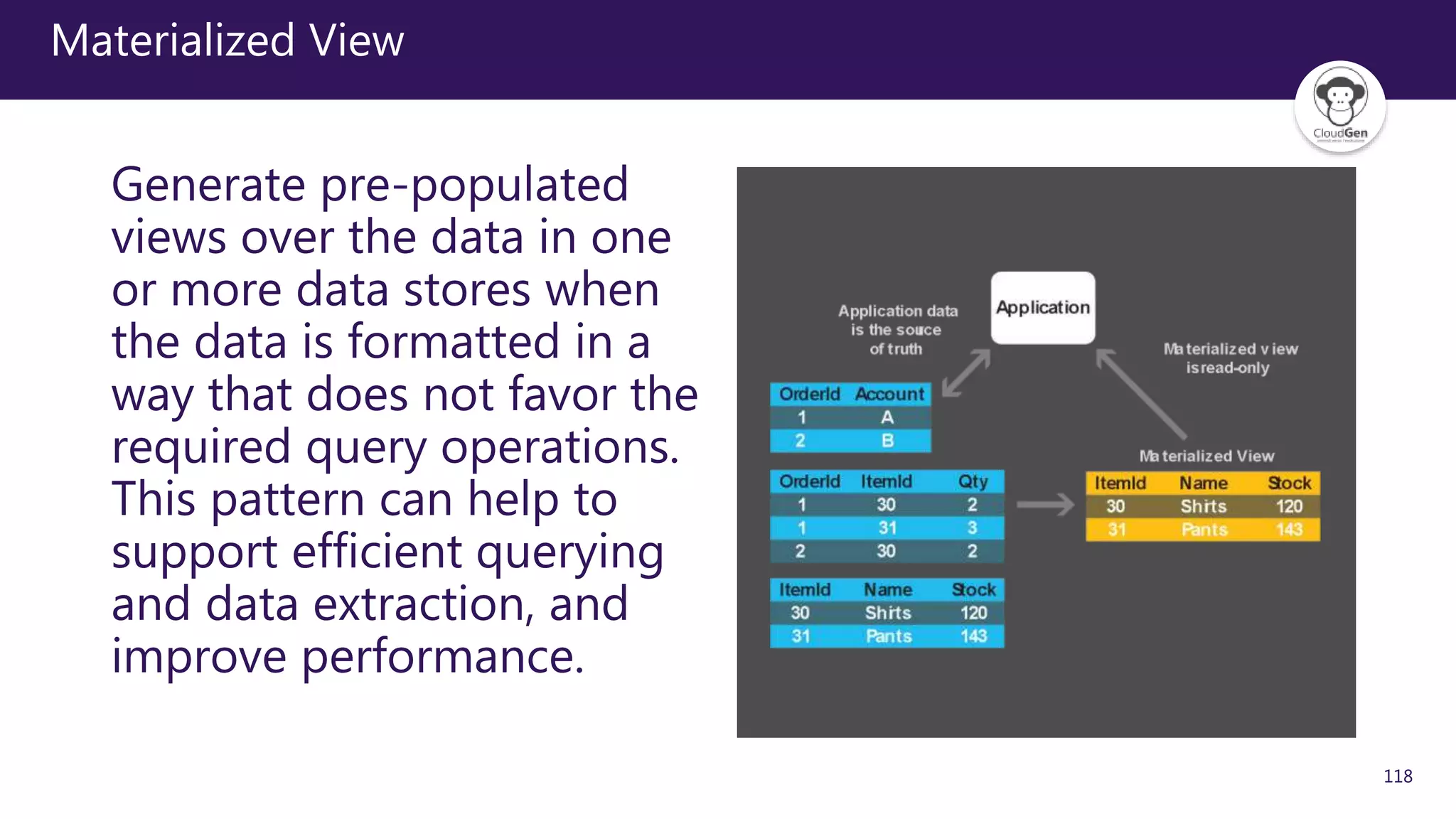
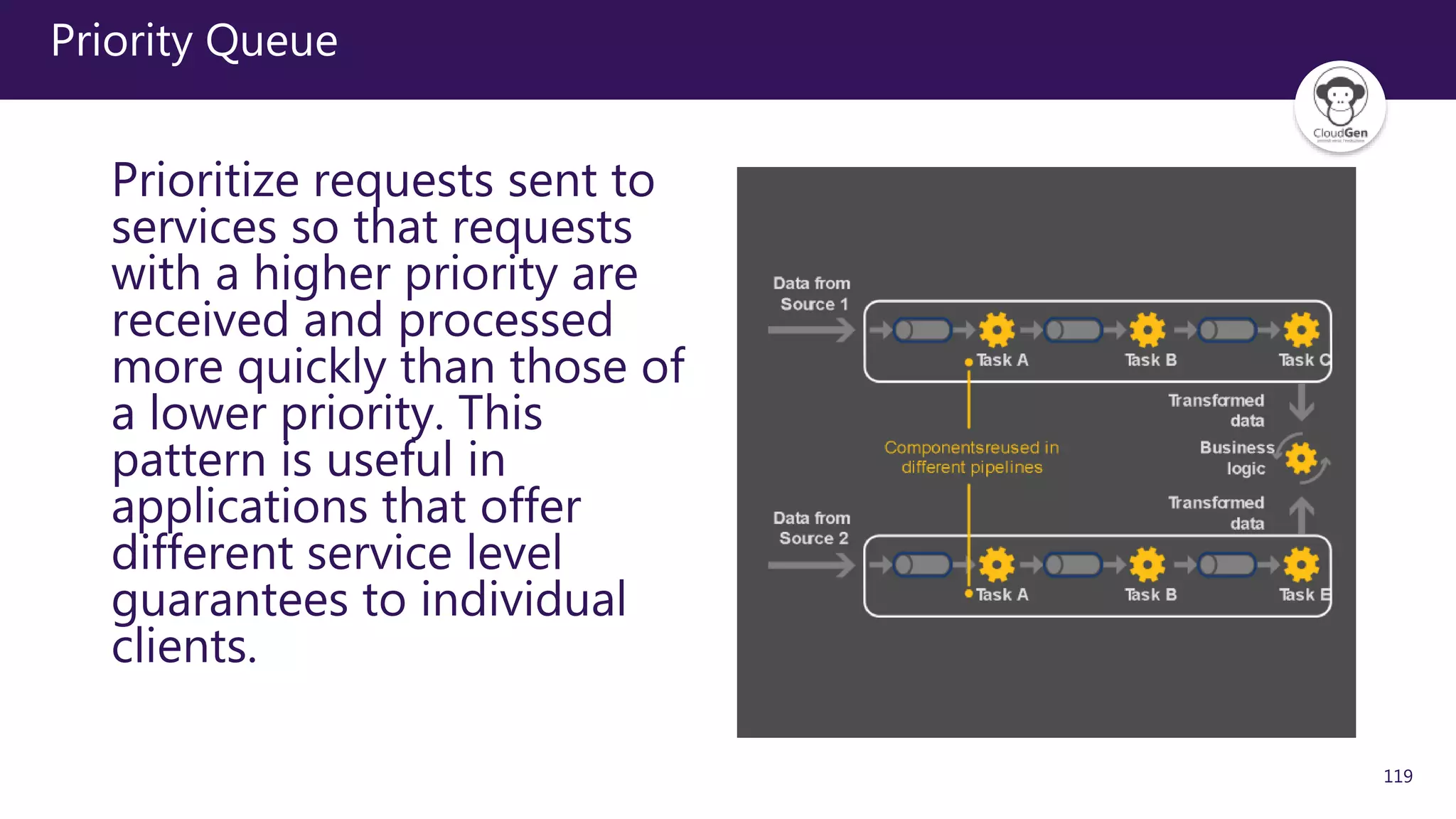
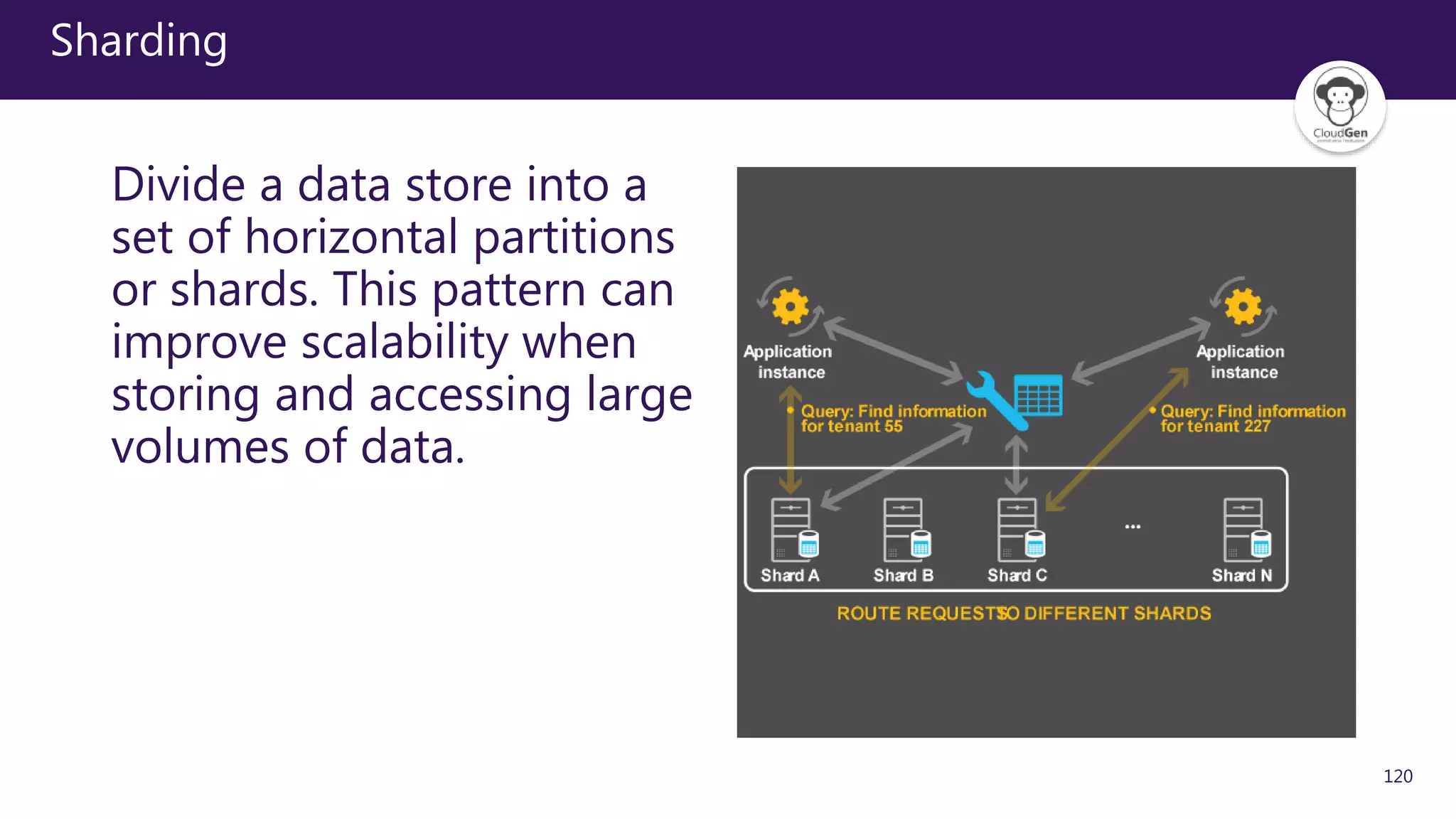
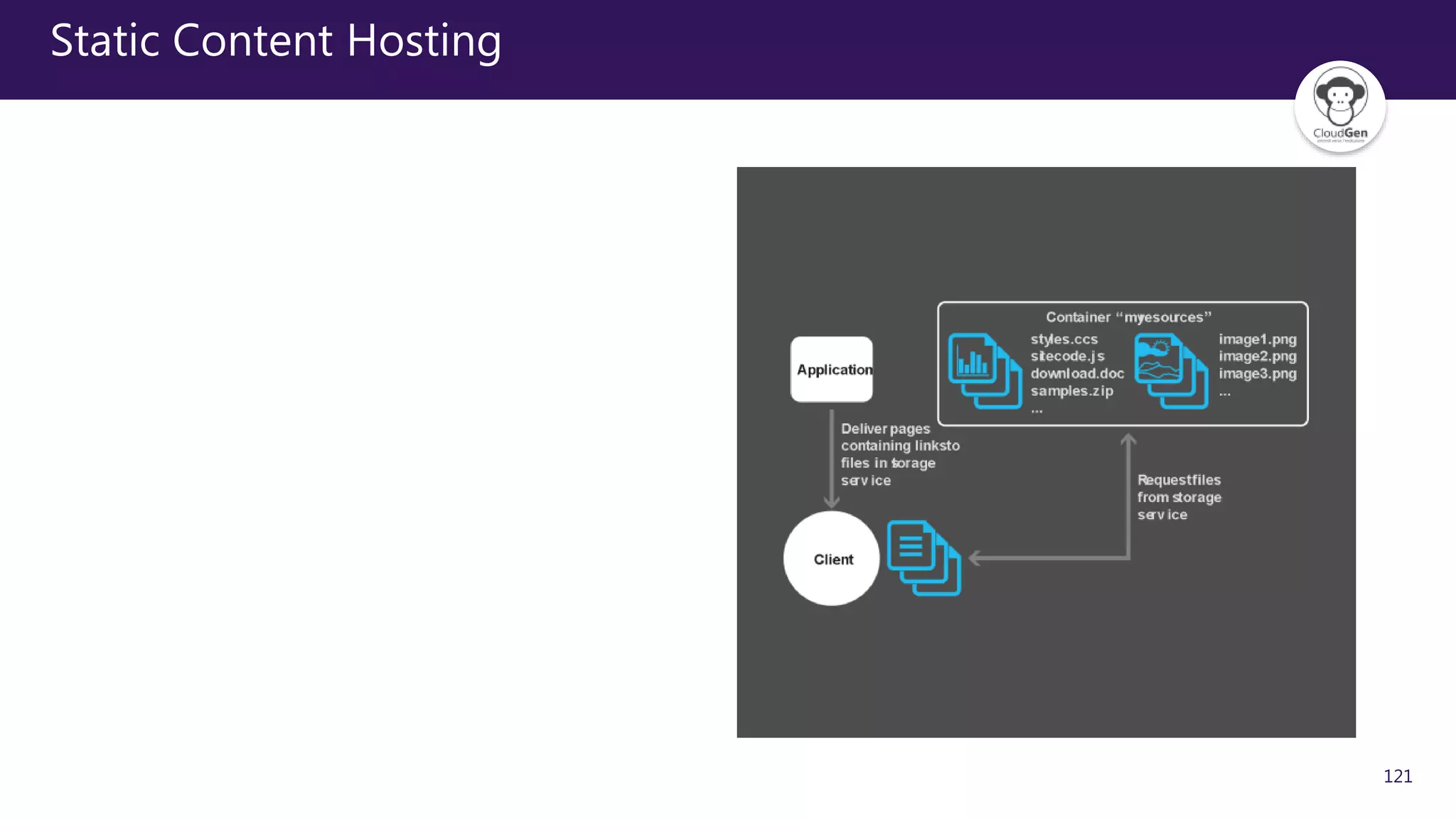
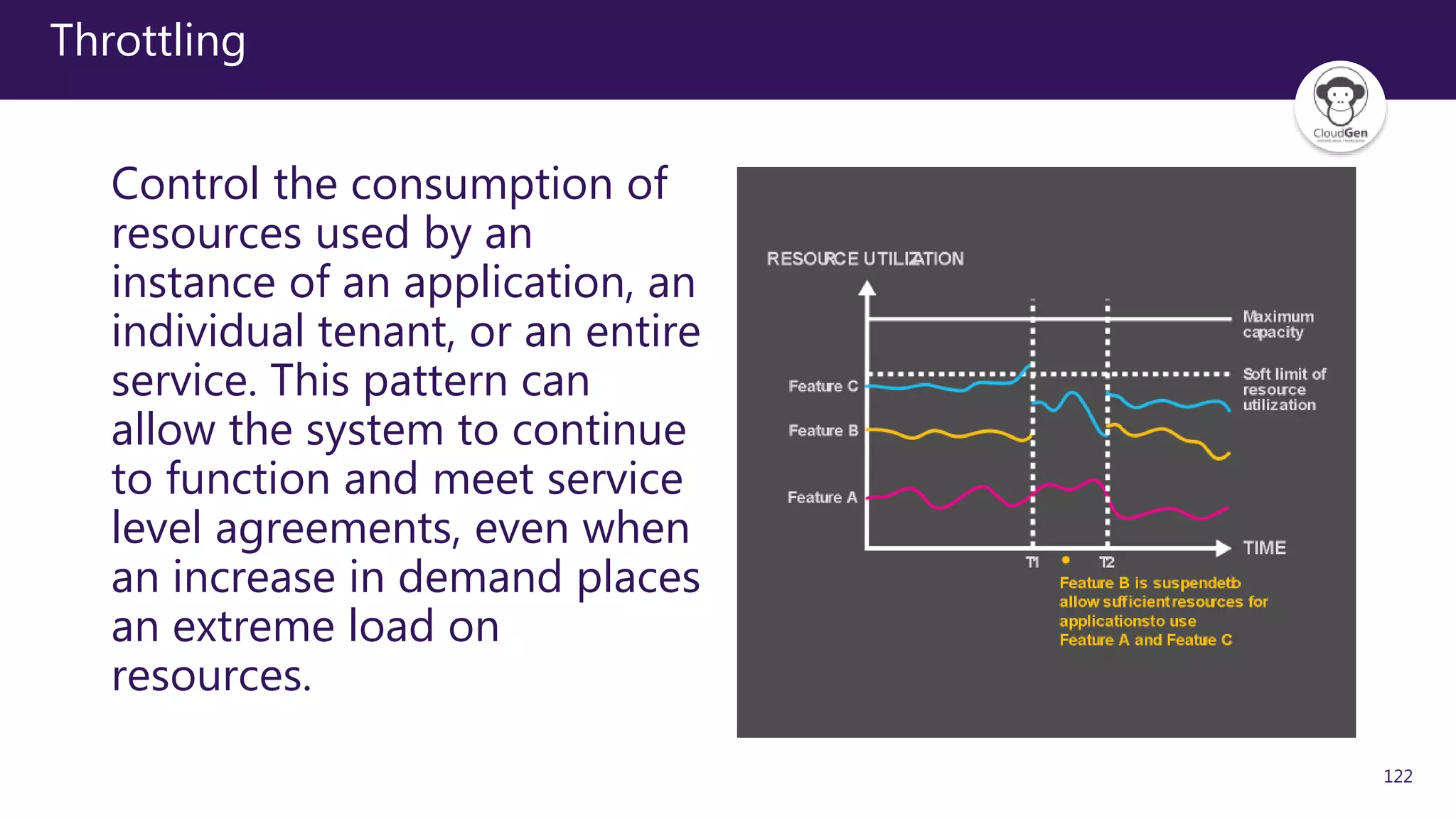
The document discusses various software design patterns that can be applied when developing applications for Azure. It begins by introducing design patterns and their use in solving common problems. It then covers specific patterns organized into categories like availability, data management, design and implementation, messaging, management and monitoring, performance and scalability, resiliency, and security. For each pattern, it provides a brief description of the problem it addresses and how it can improve qualities like performance, scalability, and availability. Examples of patterns discussed include cache-aside, command query responsibility segregation, and queue-based load leveling. The document emphasizes that understanding and applying these patterns is important for developing applications suited to cloud environments.














![17
IaaS and Lift & Shift: an anti-pattern?
From Wikipedia [https://en.wikipedia.org/wiki/Anti-pattern]:
An anti-pattern is a common response to a recurring
problem that is usually ineffective and risks being highly
counterproductive](https://image.slidesharecdn.com/2018-180924065312/75/Applicare-patterns-di-sviluppo-con-Azure-17-2048.jpg)



![22
[Software] Design pattern
From Wikipedia [https://en.wikipedia.org/wiki/Software_design_pattern]:
In software engineering, a software design pattern is a
general, reusable solution to a commonly occurring
problem within a given context in software design. It is
not a finished design that can be transformed directly
into source or machine code. It is a description or
template for how to solve a problem that can be used in
many different situations.
Design patterns are formalized best practices that the
programmer can use to solve common problems when
designing an application or system.](https://image.slidesharecdn.com/2018-180924065312/75/Applicare-patterns-di-sviluppo-con-Azure-22-2048.jpg)