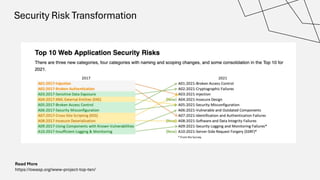
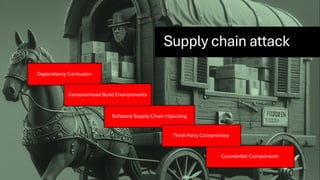
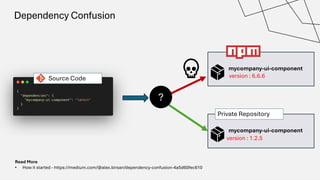
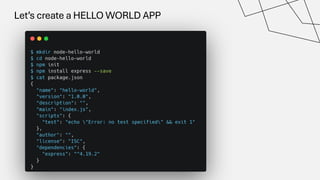
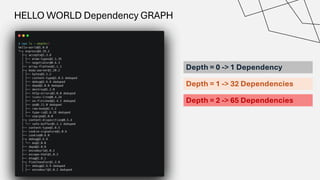
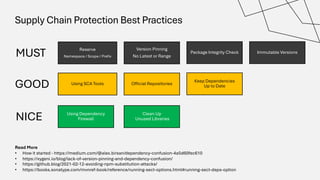
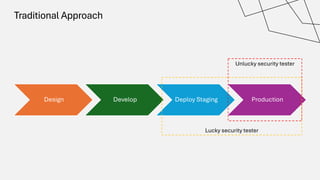
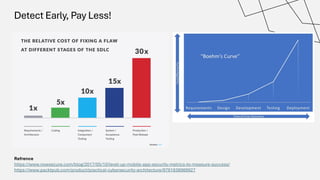
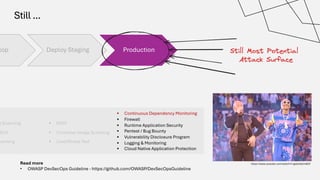
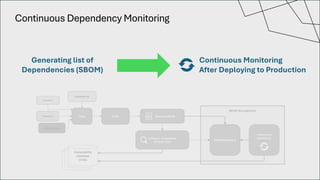
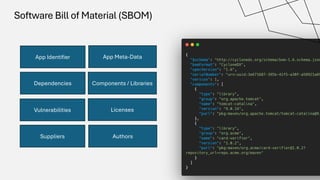
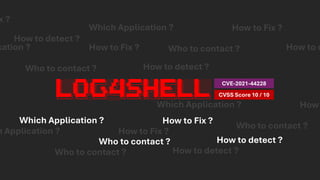
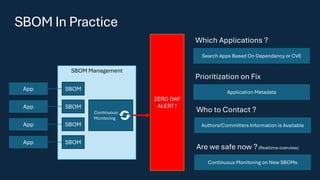
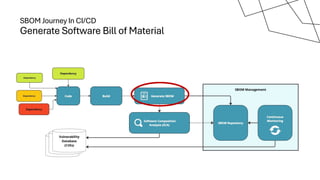
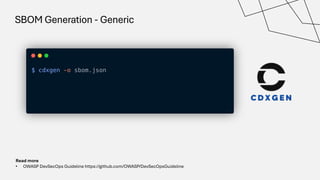
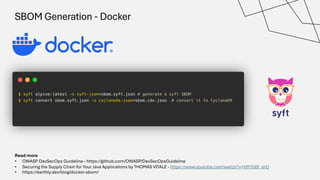
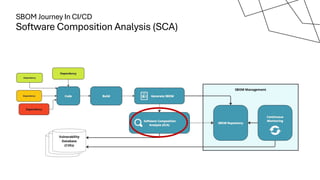
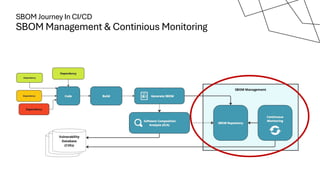
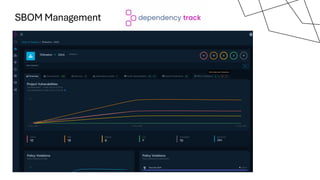
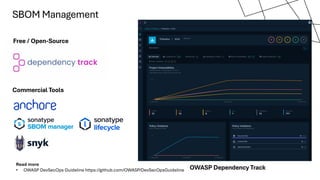
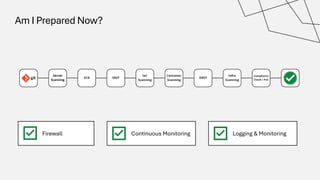
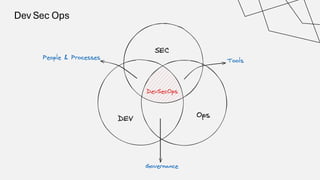
The document discusses the vulnerabilities in the software supply chain, particularly highlighting critical CVEs such as log4j, and the importance of maintaining updated and secure software components. It emphasizes best practices for secure software development including dependency monitoring, software composition analysis, and the generation of software bills of materials (SBOM). The authors, Ali Yazdani and Soroosh Khodami, advocate for a DevSecOps approach to eliminate silos in software delivery while adhering to emerging regulations on cybersecurity.