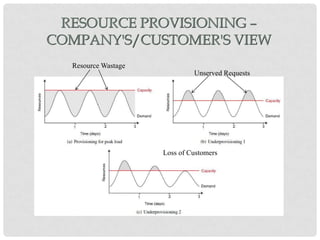
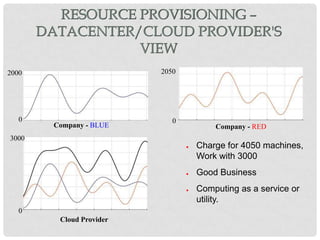
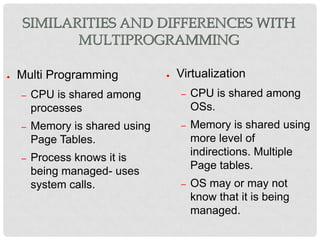
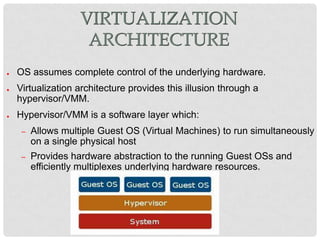
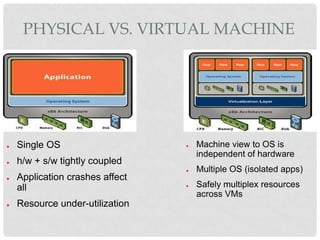
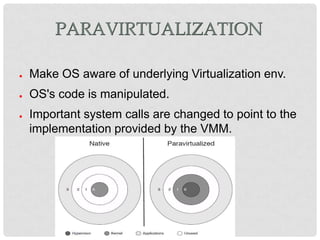
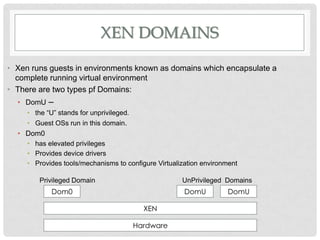
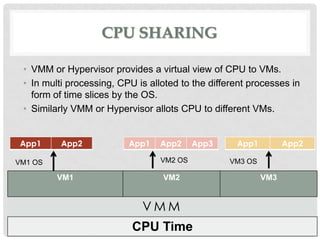
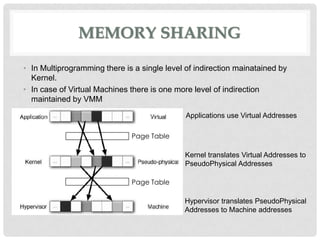
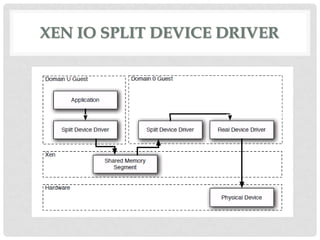
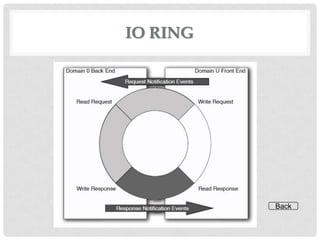
This document discusses cloud computing and virtualization techniques. It begins by defining cloud computing and its benefits like scalability and pay-as-you-go models. It then discusses virtualization, specifically how virtual machines (VMs) allow multiple guest operating systems to run simultaneously on a single physical host. The document outlines requirements for virtualization like intercepting privileged instructions. It also describes different VM implementation techniques like binary translation, paravirtualization, and hardware-assisted virtualization. Finally, it provides details on the Xen virtualization platform and how it implements CPU, memory, and I/O sharing across VMs.