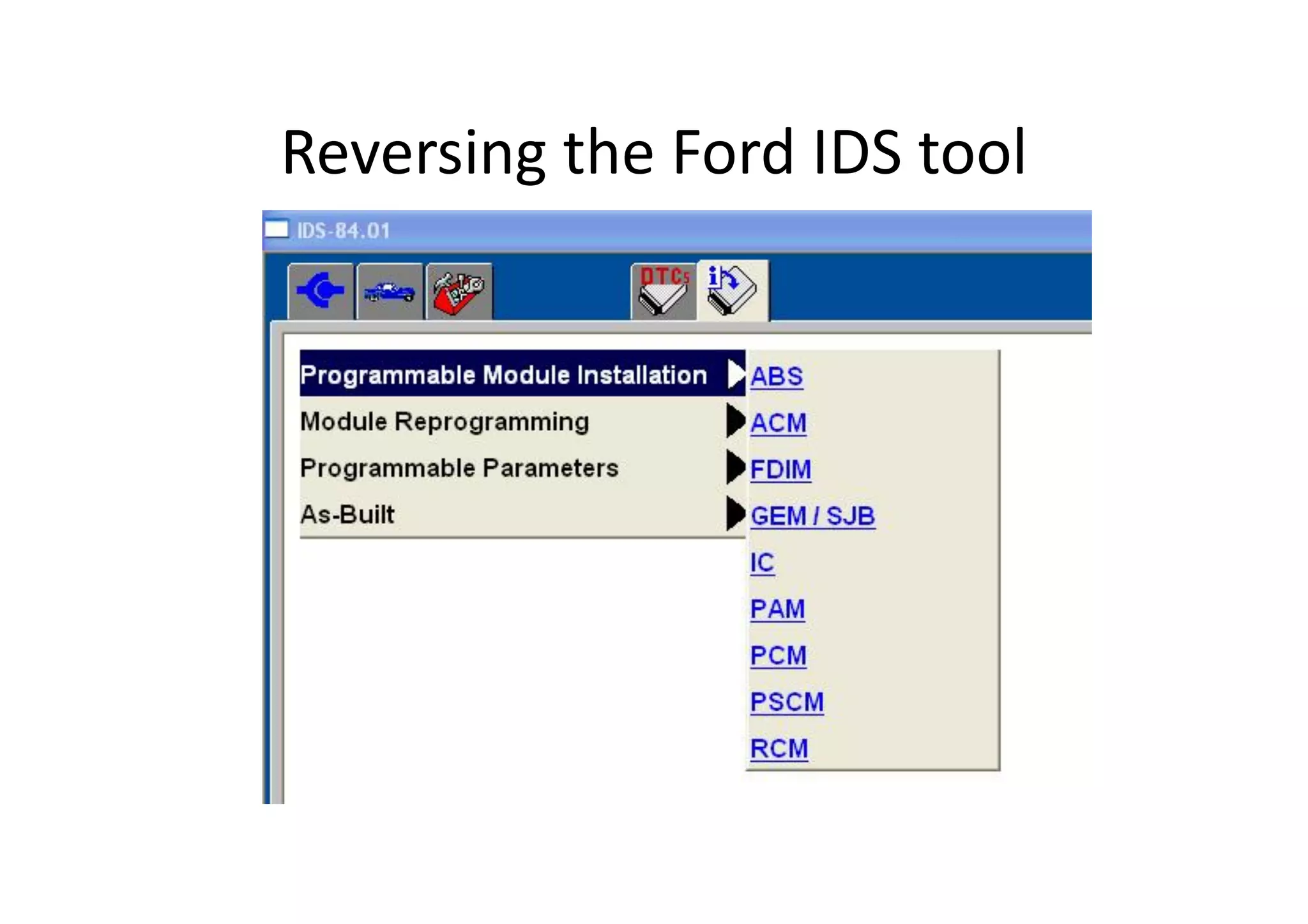
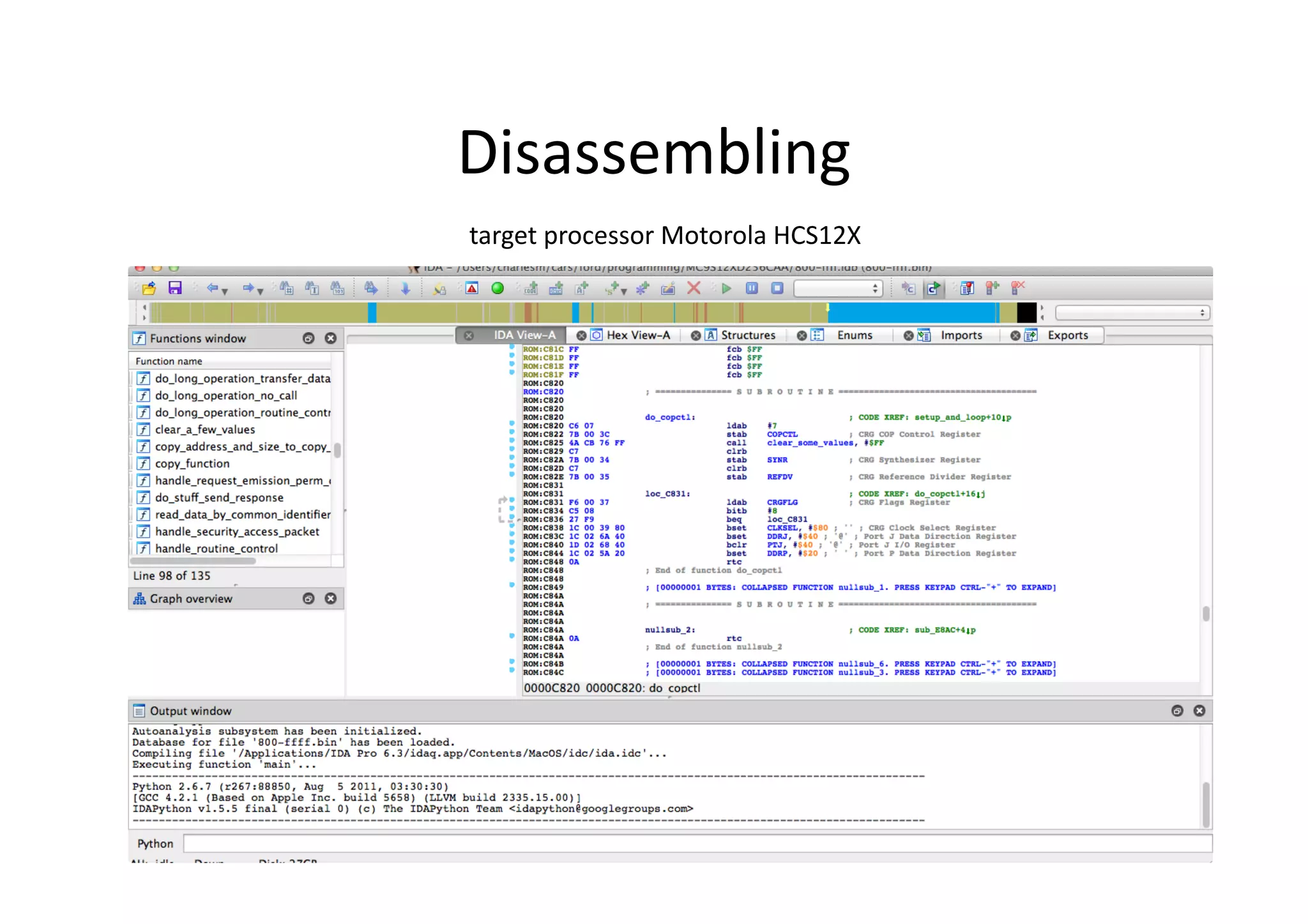
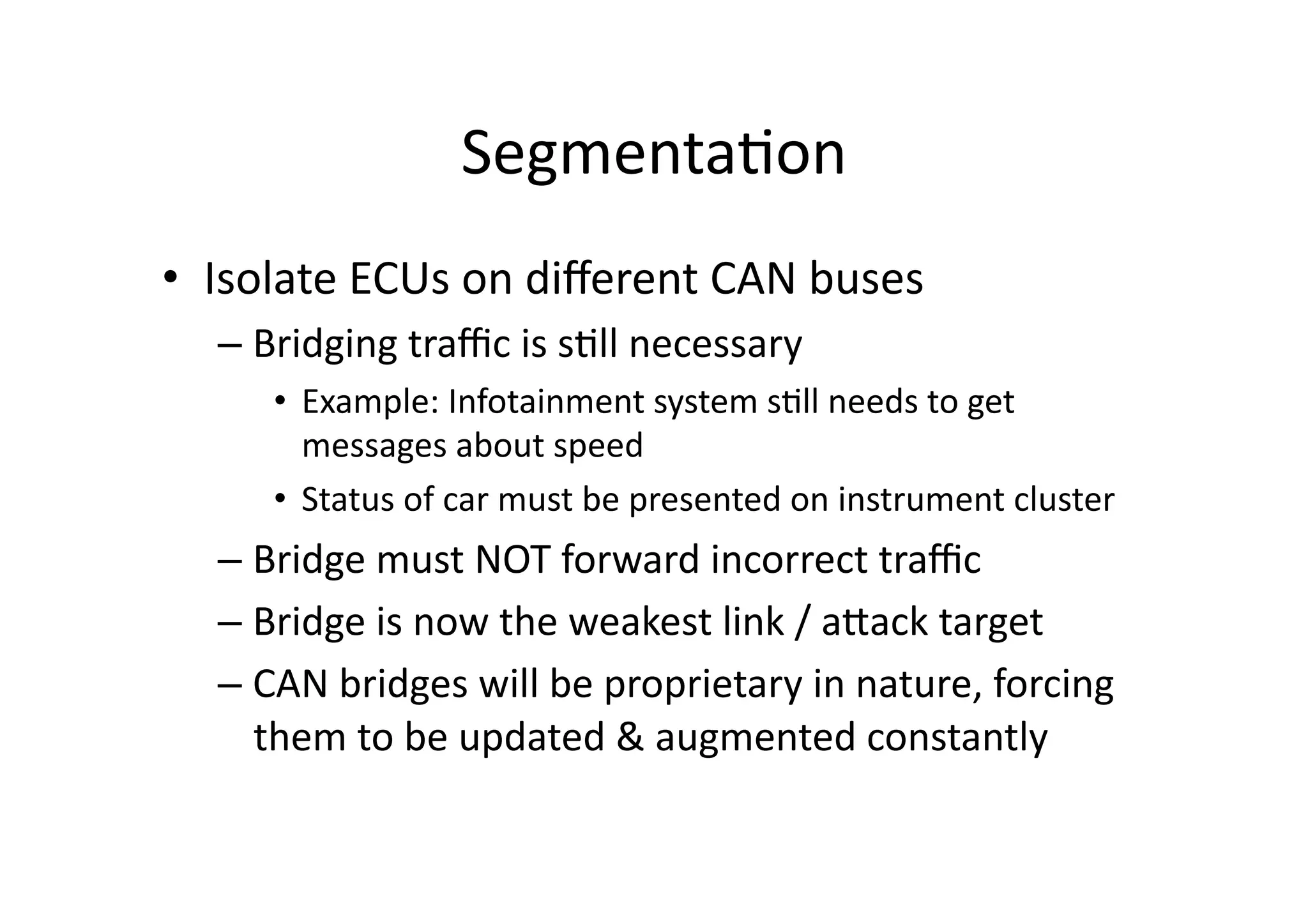
The document discusses automotive security, focusing on vulnerabilities within vehicle systems and the CAN bus architecture. It explains the anatomy of attacks, various electronic control units (ECUs), and the inherent lack of security in the design of automotive communication systems. Recommendations include improving detection of attacks, implementing layered security approaches, and segmenting CAN networks to enhance vehicle safety.


![Who
• Charlie
Miller
[Security
Engineer]
|Twi2er|
• Chris
Valasek
[Director
of
Security
Intelligence]
|
IOAc8ve|](https://image.slidesharecdn.com/chrisvalasekenpub-140312041915-phpapp01/75/The-Current-State-of-Automotive-Security-by-Chris-Valasek-3-2048.jpg)












































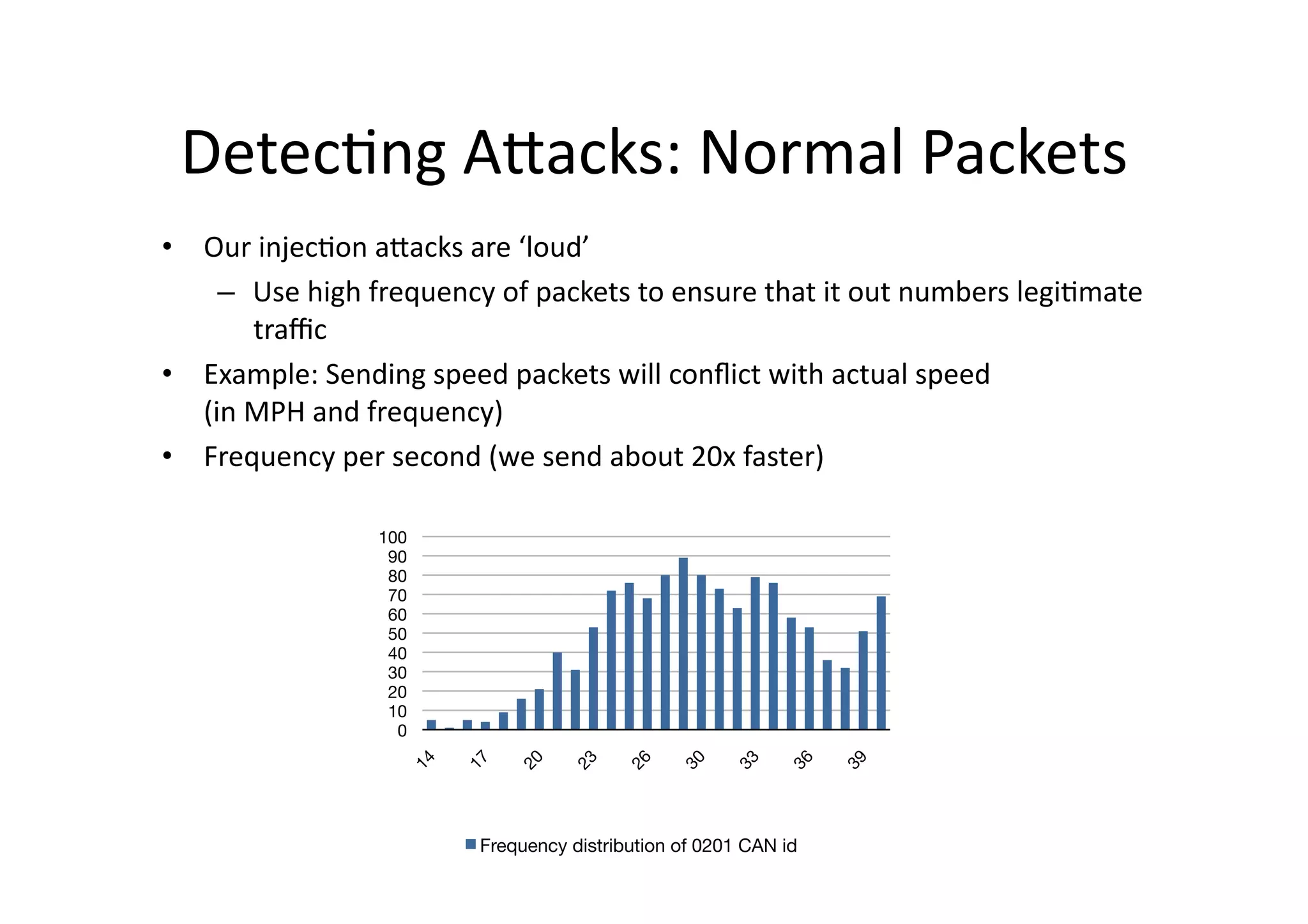
![Frequency
of
CAN
messages
• Frequency
of
messages
from
IDs
does
not
have
much
devia/on
• Comparison
of
messages
from
the
start
of
a
capture
and
in
random
loca/ons
within
the
same
capture
Hit
Counts:
Primary[03A9]
=>
9
|
Secondary[03A9]
=>
5
Hit
Counts:
Primary[0255]
=>
166
|
Secondary[0255]
=>
119
Hit
Counts:
Primary[0230]
=>
991
|
Secondary[0230]
=>
1011
Hit
Counts:
Primary[0250]
=>
168
|
Secondary[0250]
=>
209
Hit
Counts:
Primary[03C4]
=>
41
|
Secondary[03C4]
=>
46
Hit
Counts:
Primary[0340]
=>
80
|
Secondary[0340]
=>
82
Hit
Counts:
Primary[0422]
=>
83
|
Secondary[0422]
=>
36
Hit
Counts:
Primary[0423]
=>
17
|
Secondary[0423]
=>
6
Hit
Counts:
Primary[0420]
=>
83
|
Secondary[0420]
=>
47
Hit
Counts:
Primary[0200]
=>
496
|
Secondary[0200]
=>
630](https://image.slidesharecdn.com/chrisvalasekenpub-140312041915-phpapp01/75/The-Current-State-of-Automotive-Security-by-Chris-Valasek-61-2048.jpg)