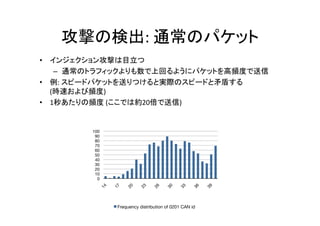
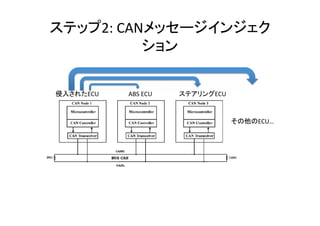
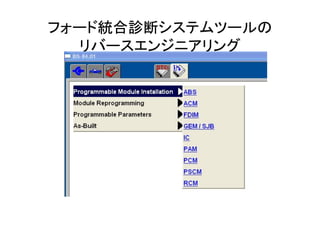
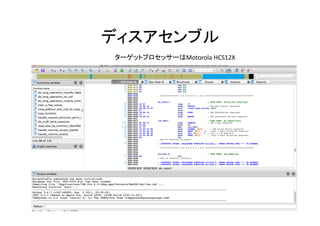
The document contains details on security measures for automotive Electronic Control Units (ECUs) and their communication protocols via CAN bus, focusing on various data packets and security access methods. Key security techniques and ECU identifiers are discussed, along with examples of data transmission for input and output control. The document emphasizes the importance of protecting sensitive automotive information to prevent malicious attacks.


![• Charlie
Miller
[Security
Engineer]
|Twi,er|
• Chris
Valasek
[Director
of
Security
Intelligence]
|
IOAc4ve|](https://image.slidesharecdn.com/chrisvalasekjapub-140312041928-phpapp02/85/by-Chris-Valasek-3-320.jpg)






















































![CAN
• ID
•
Hit
Counts:
Primary[03A9]
=>
9
|
Secondary[03A9]
=>
5
Hit
Counts:
Primary[0255]
=>
166
|
Secondary[0255]
=>
119
Hit
Counts:
Primary[0230]
=>
991
|
Secondary[0230]
=>
1011
Hit
Counts:
Primary[0250]
=>
168
|
Secondary[0250]
=>
209
Hit
Counts:
Primary[03C4]
=>
41
|
Secondary[03C4]
=>
46
Hit
Counts:
Primary[0340]
=>
80
|
Secondary[0340]
=>
82
Hit
Counts:
Primary[0422]
=>
83
|
Secondary[0422]
=>
36
Hit
Counts:
Primary[0423]
=>
17
|
Secondary[0423]
=>
6
Hit
Counts:
Primary[0420]
=>
83
|
Secondary[0420]
=>
47
Hit
Counts:
Primary[0200]
=>
496
|
Secondary[0200]
=>
630](https://image.slidesharecdn.com/chrisvalasekjapub-140312041928-phpapp02/85/by-Chris-Valasek-61-320.jpg)