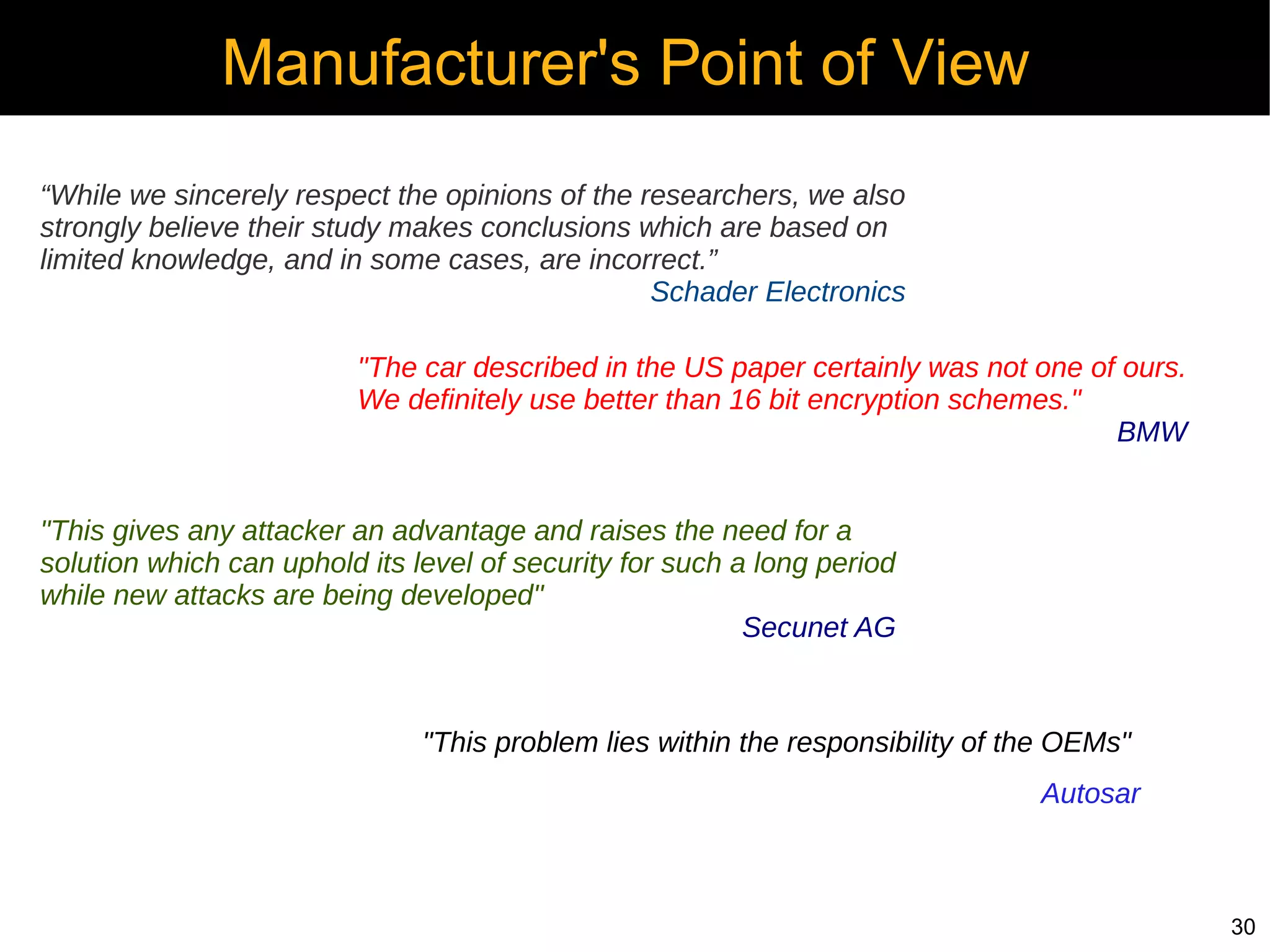
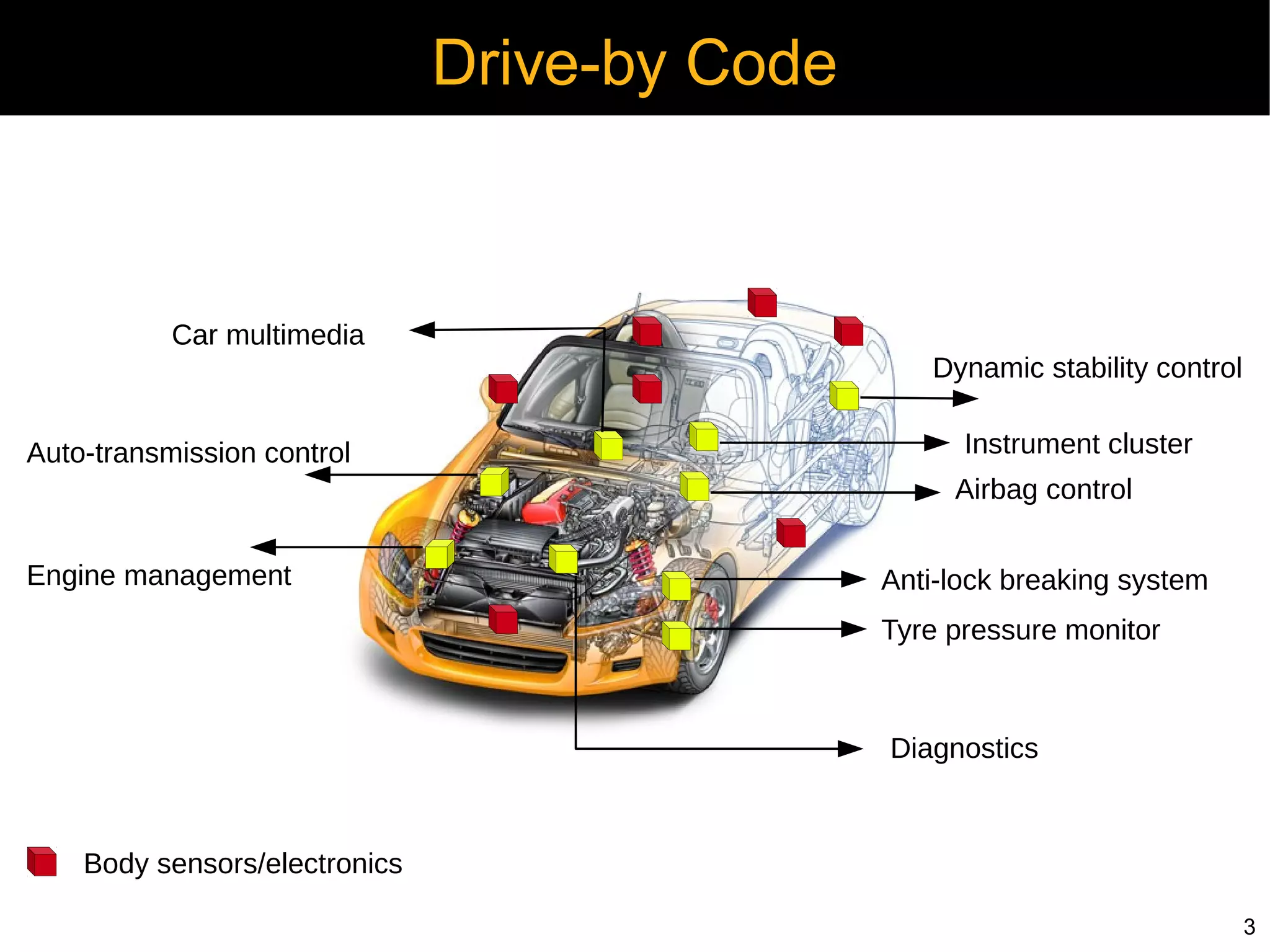
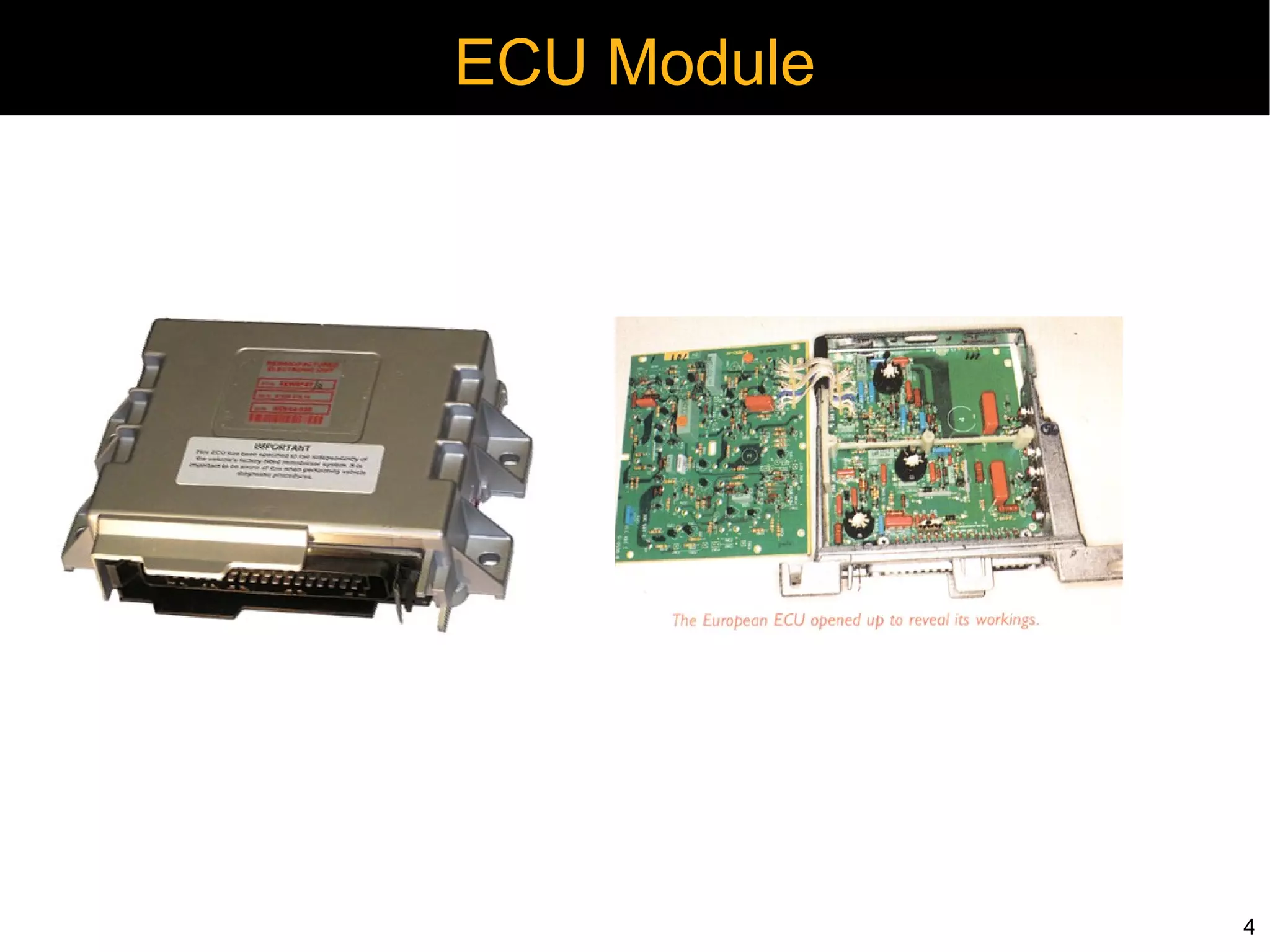
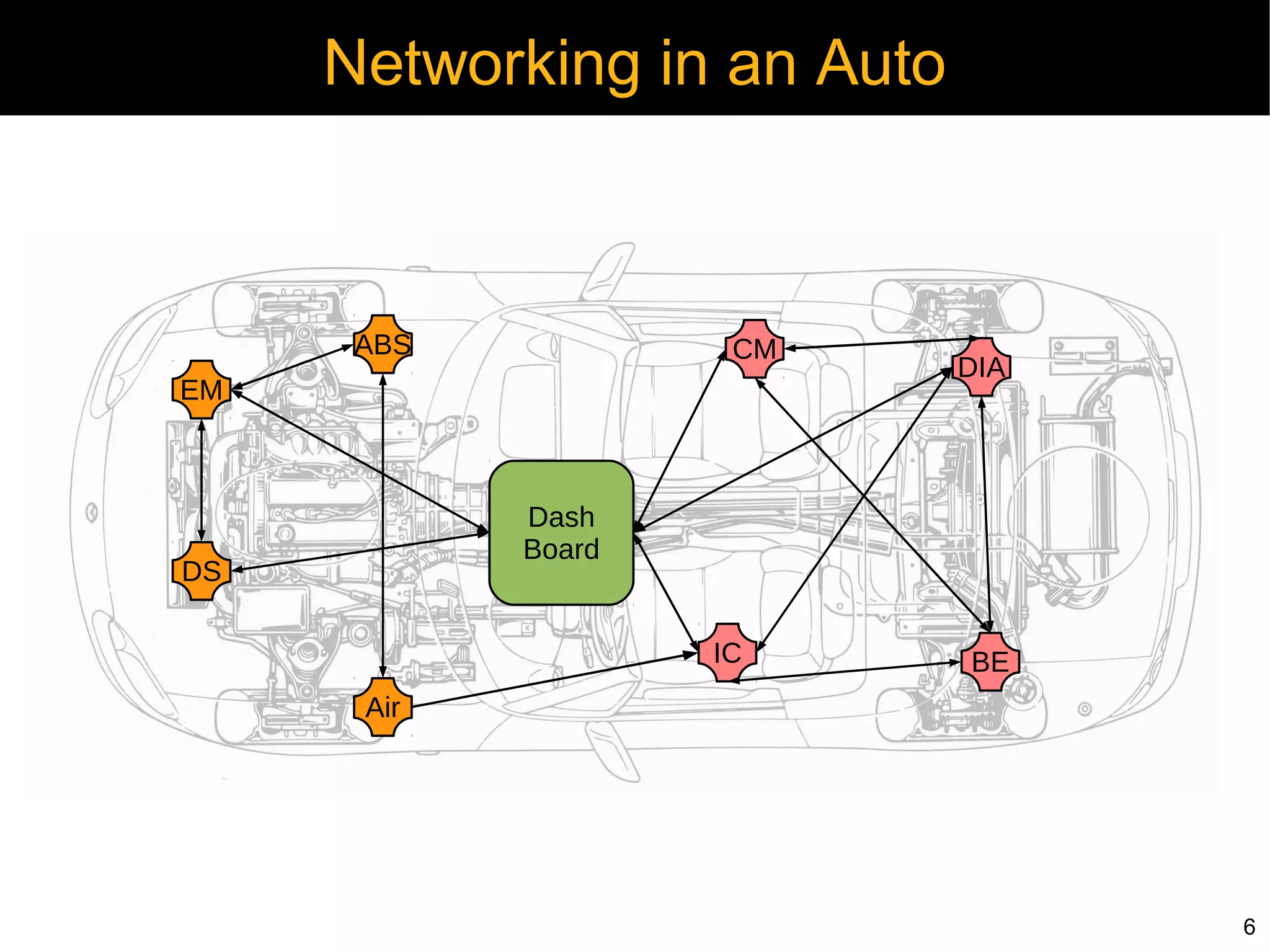
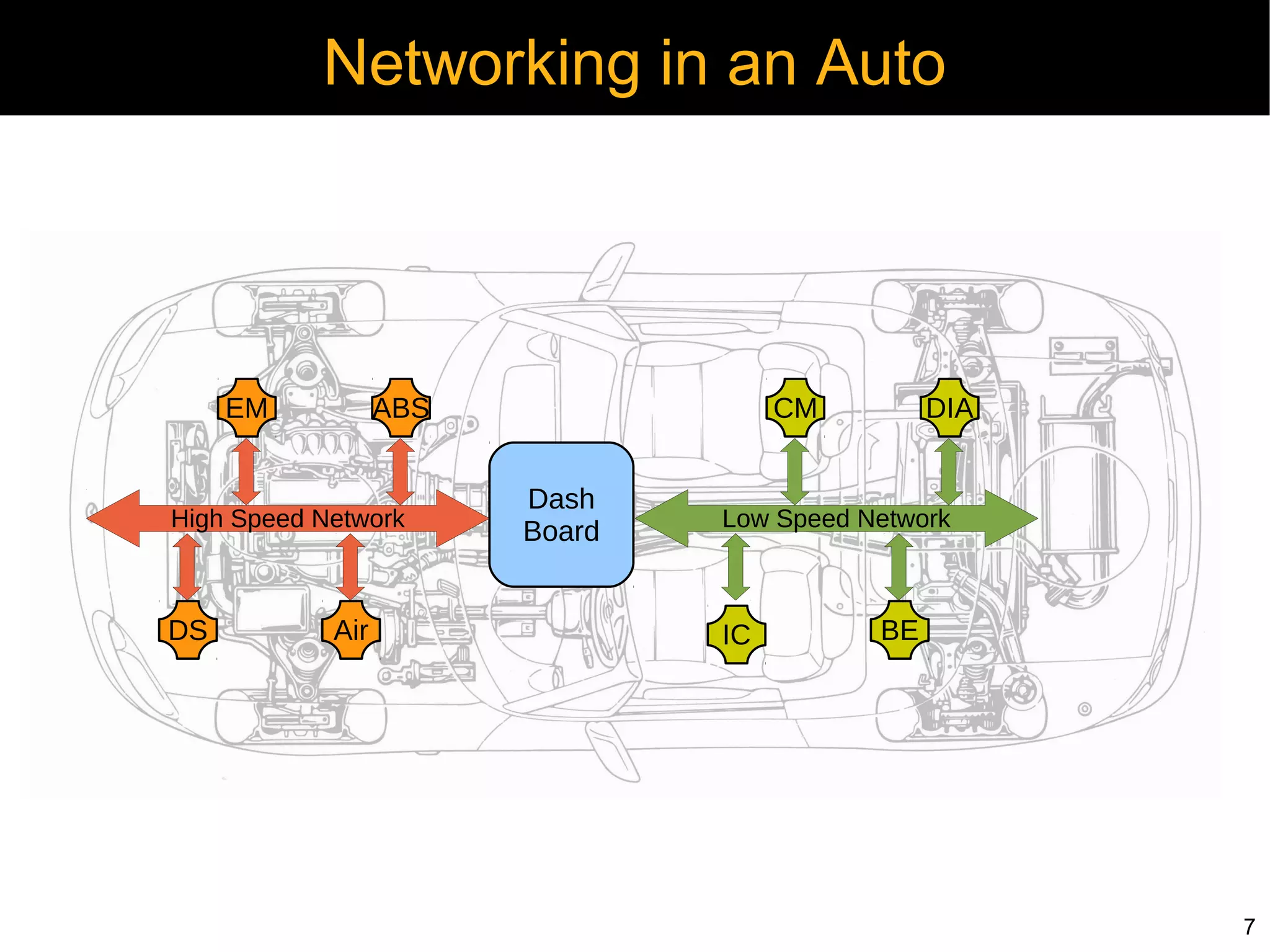
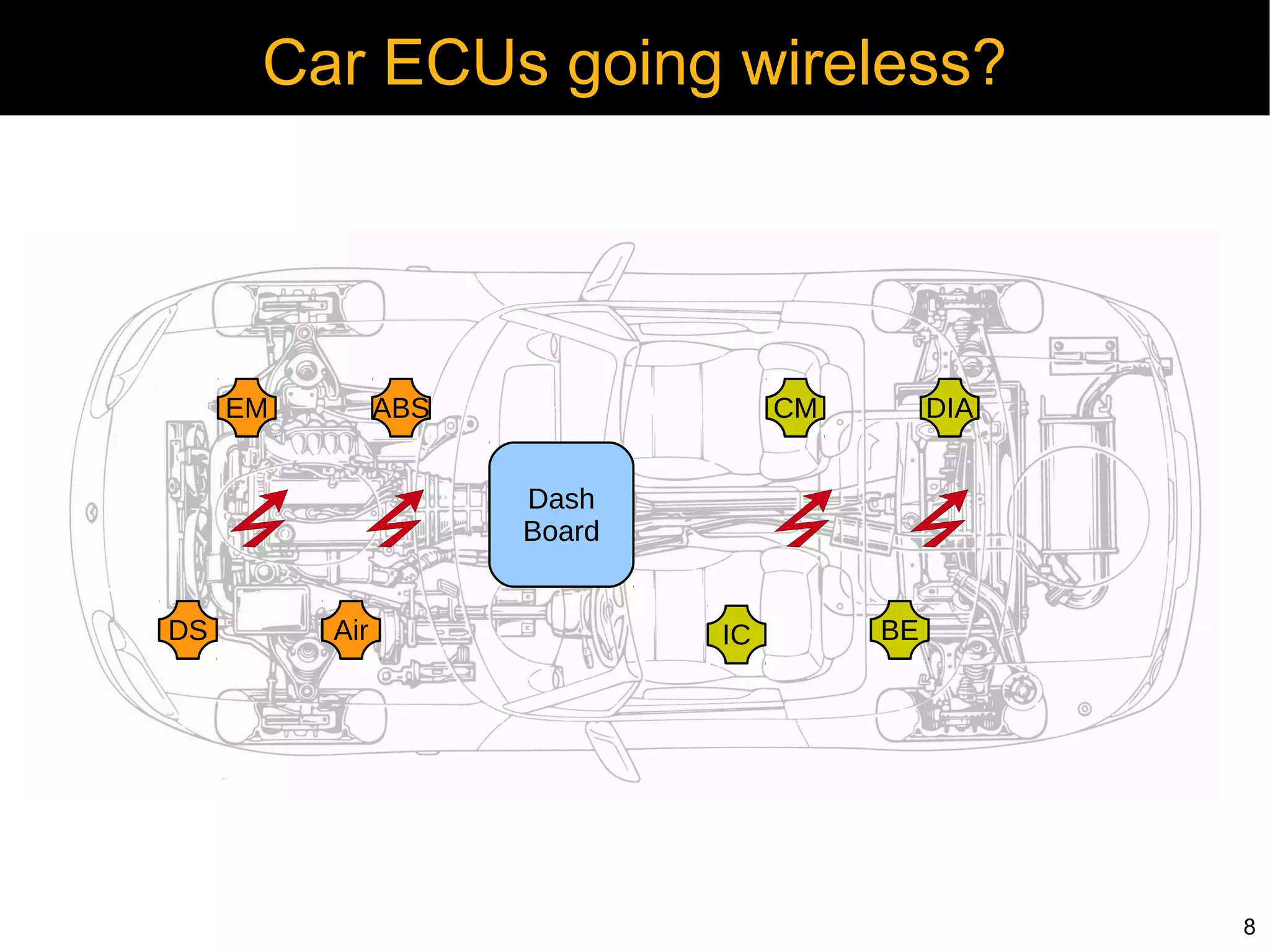
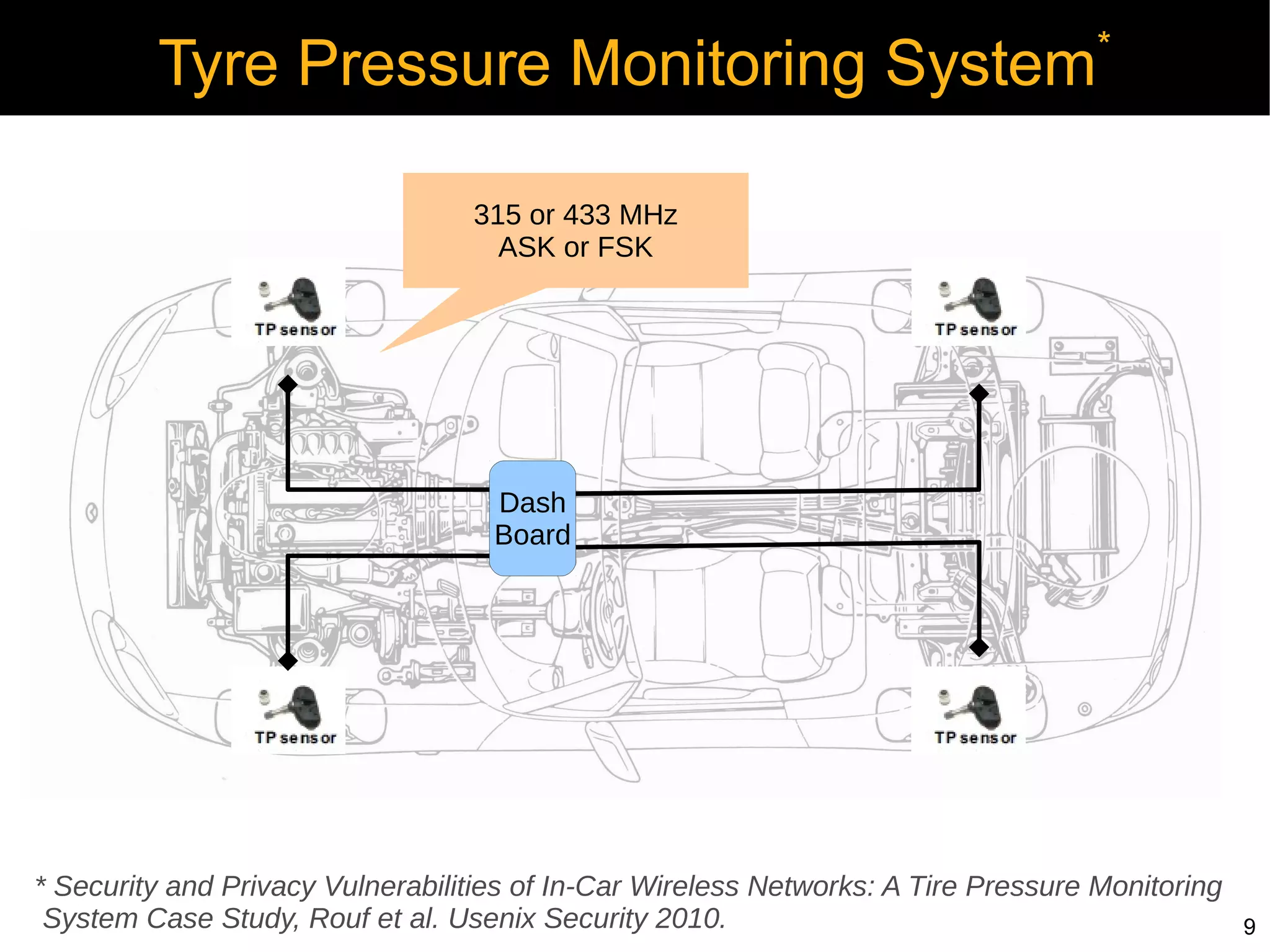
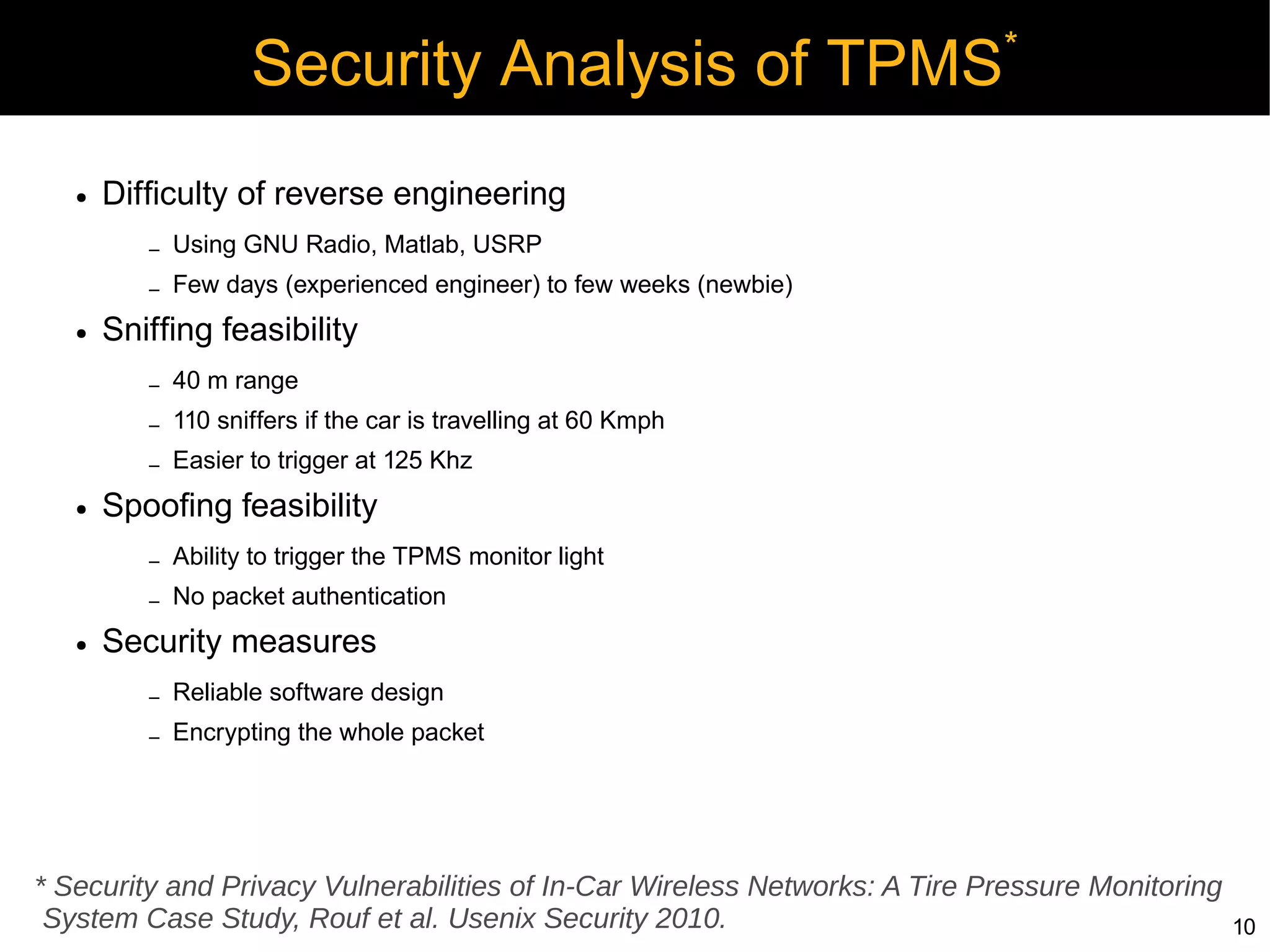
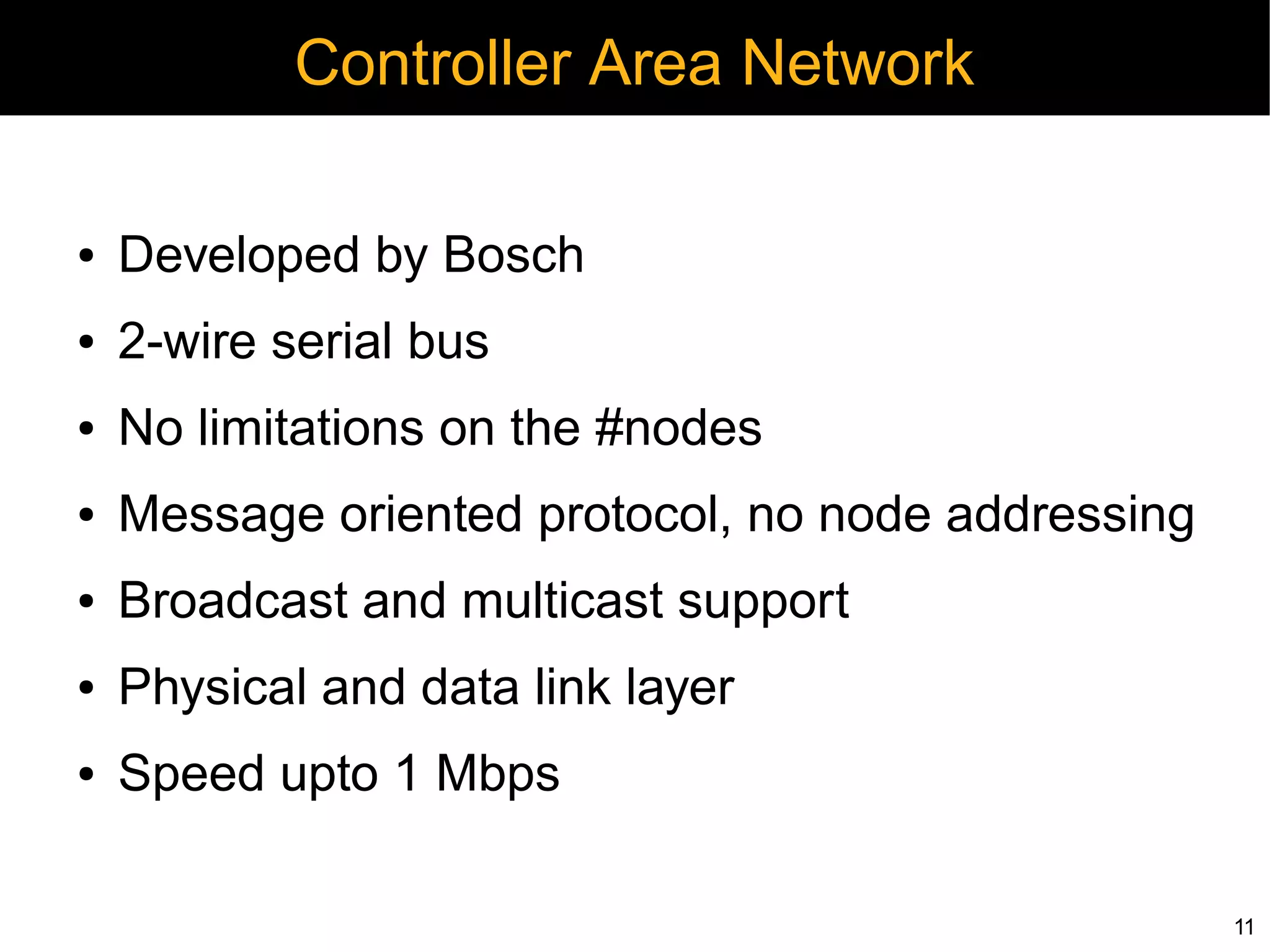
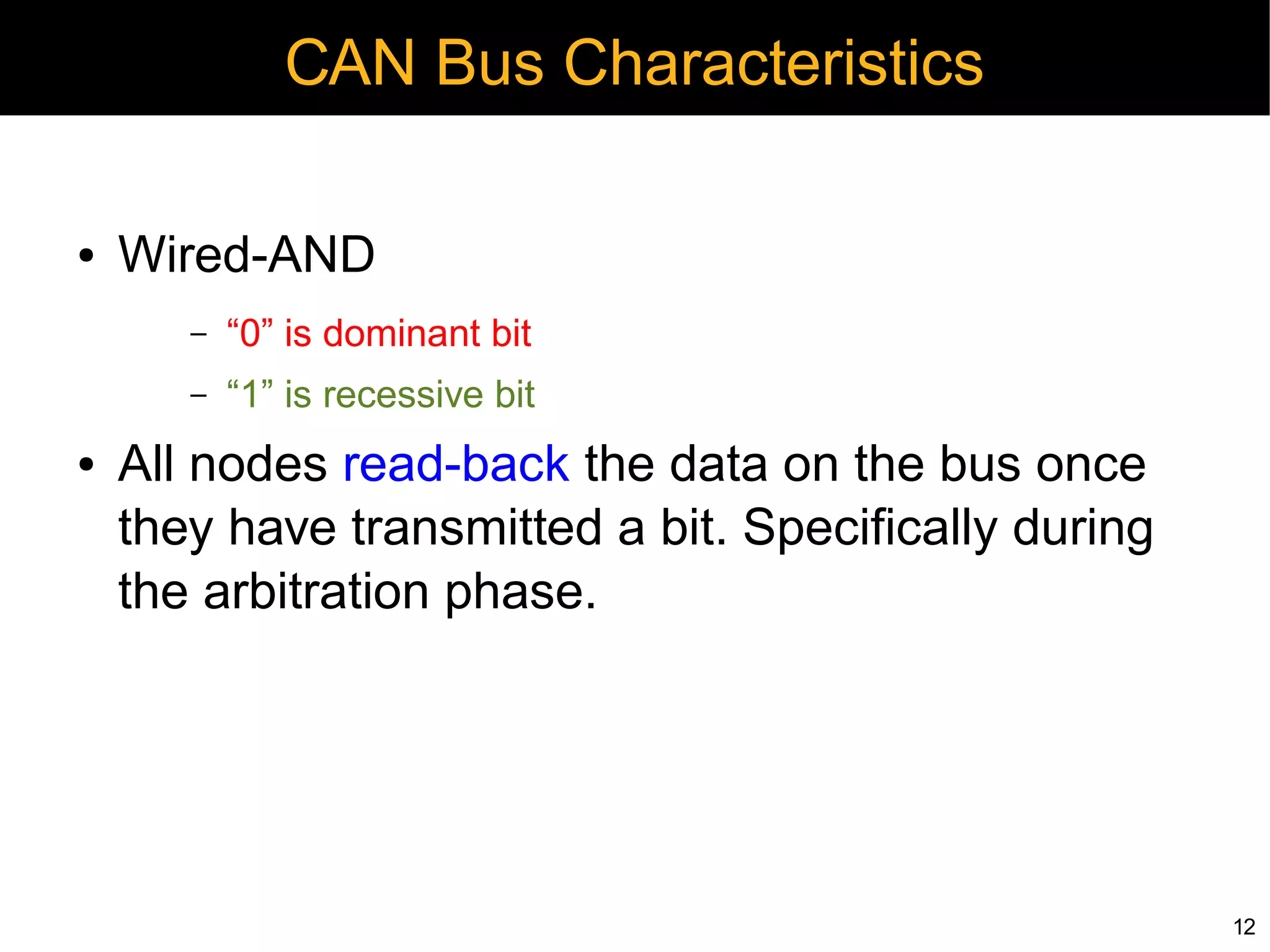
Automotive electronics have become increasingly complex, with around 40 computers controlling various systems in modern vehicles. Networks like CAN, LIN, and FlexRay connect electronic control units (ECUs) to control things like the engine, brakes, entertainment systems and more. However, the widespread use of wireless technologies and lack of strong security measures leave these systems vulnerable to attacks. Researchers have demonstrated exploits like manipulating the braking system or engine via the CAN bus. Automakers need to implement better security practices like encryption, authentication and isolating critical networks to prevent potential harm from attacks on in-vehicle networks.




![1
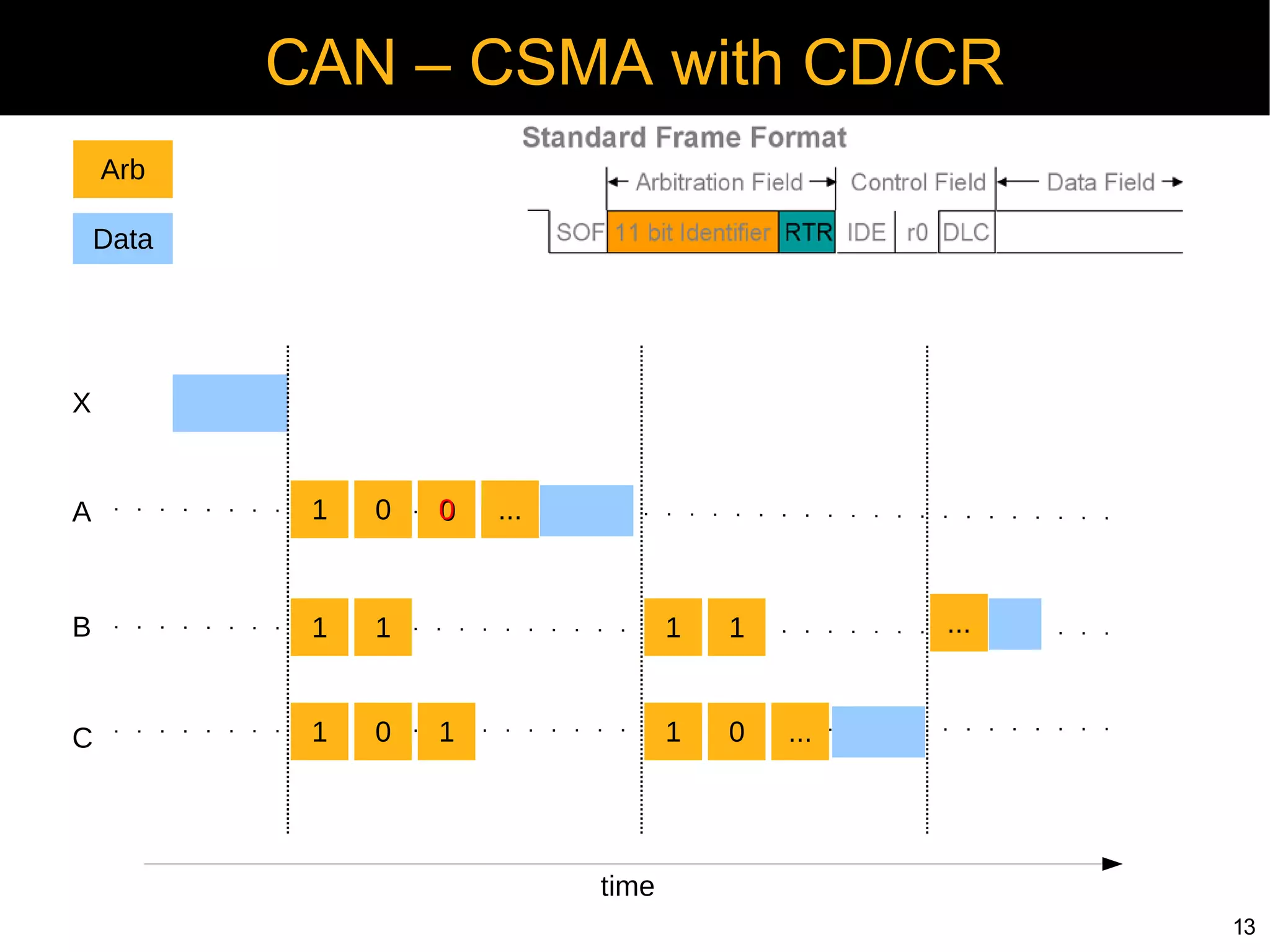
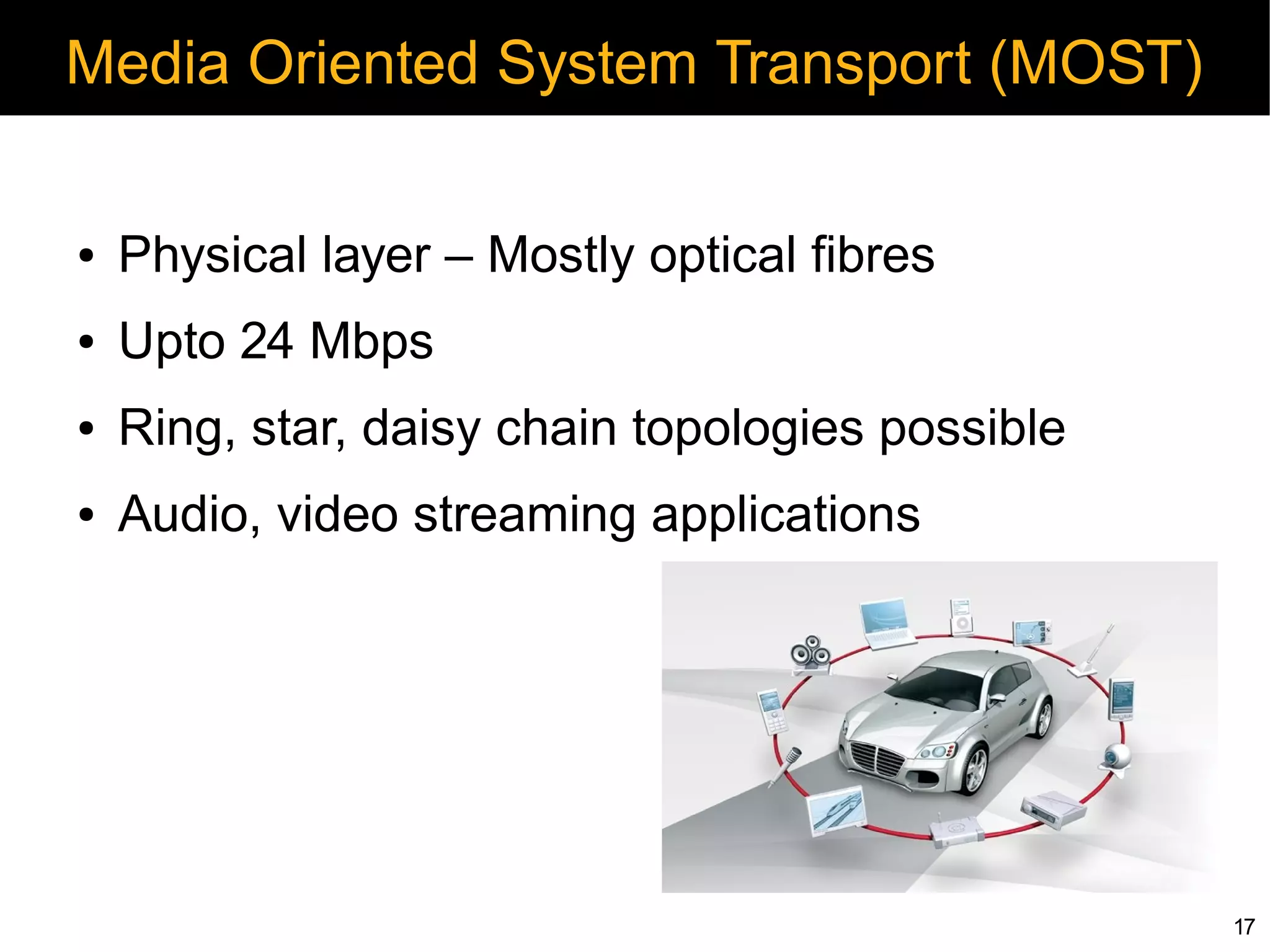
Security Challenges in CAN
● No security i.e. encryption/decryption defined
● Broadcast nature
● No node authentication
● Limited defense to denial of service attacks
● Re-programing and reset (C/R based auth)
● Open diagnostic control
[1] Experimental Security Analysis of a Modern Automobile, Koscher et al. IEEE Security and Privacy '10
25](https://image.slidesharecdn.com/automotivesecurity-retreattalk-110205131126-phpapp01/75/Automotive-Electronics-Internals-and-Security-Implications-25-2048.jpg)
![1
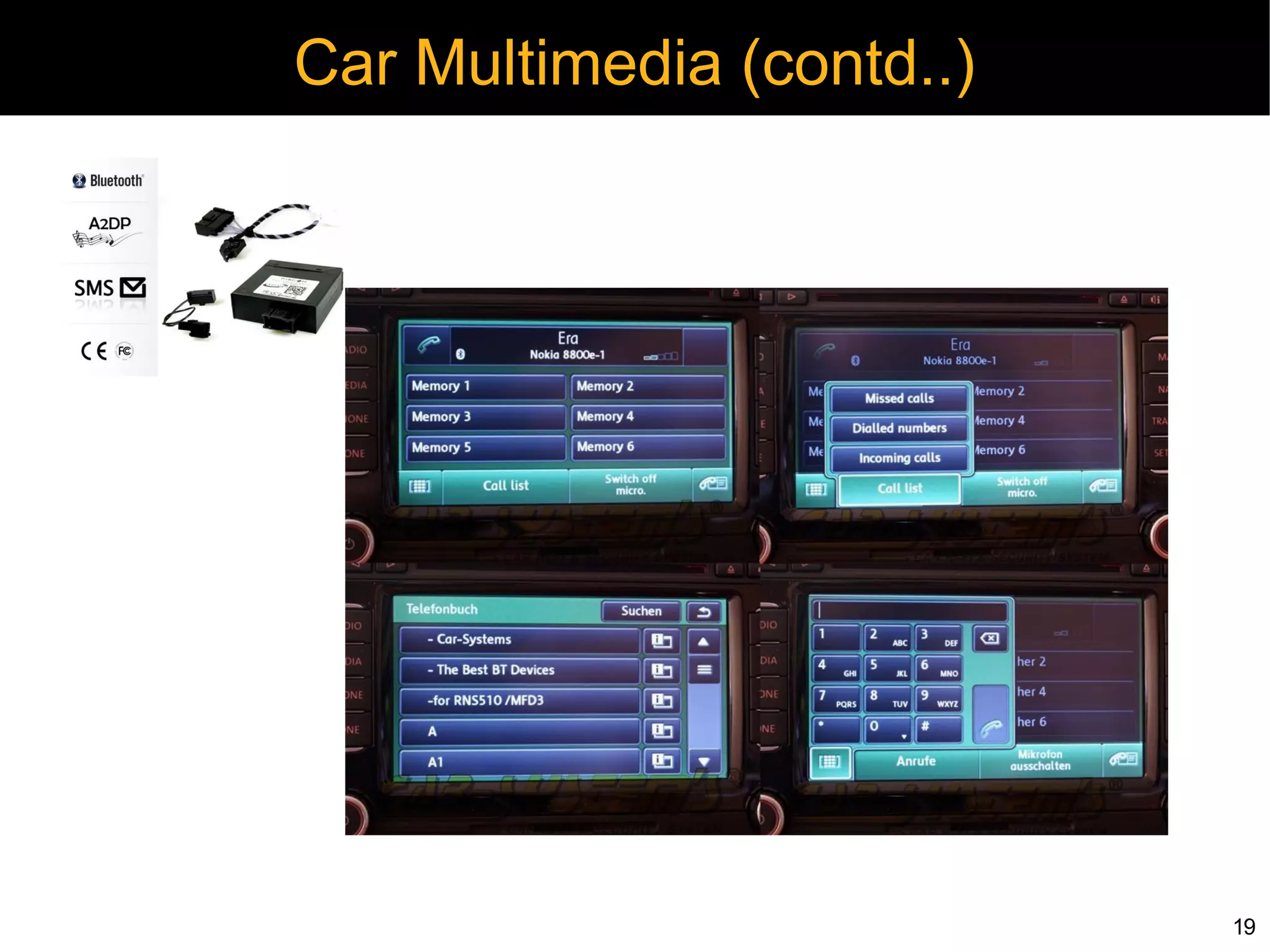
Security Analysis Setup
CarShark
[1] Experimental Security Analysis of a Modern Automobile, Koscher et al. IEEE Security and Privacy '10
26](https://image.slidesharecdn.com/automotivesecurity-retreattalk-110205131126-phpapp01/75/Automotive-Electronics-Internals-and-Security-Implications-26-2048.jpg)
![1
Security Analysis
● Deviations from standards
– Network segregation, command filtering, firmware
updates
● Radio, cluster, body electronics control
● Engine and brake control
● Code injection
[1] Experimental Security Analysis of a Modern Automobile, Koscher et al. IEEE Security and Privacy '10
27](https://image.slidesharecdn.com/automotivesecurity-retreattalk-110205131126-phpapp01/75/Automotive-Electronics-Internals-and-Security-Implications-27-2048.jpg)
![1
Security Analysis
[1] Experimental Security Analysis of a Modern Automobile, Koscher et al. IEEE Security and Privacy '10
28](https://image.slidesharecdn.com/automotivesecurity-retreattalk-110205131126-phpapp01/75/Automotive-Electronics-Internals-and-Security-Implications-28-2048.jpg)
![1
Security Analysis
[1] Experimental Security Analysis of a Modern Automobile, Koscher et al. IEEE Security and Privacy '10
29](https://image.slidesharecdn.com/automotivesecurity-retreattalk-110205131126-phpapp01/75/Automotive-Electronics-Internals-and-Security-Implications-29-2048.jpg)