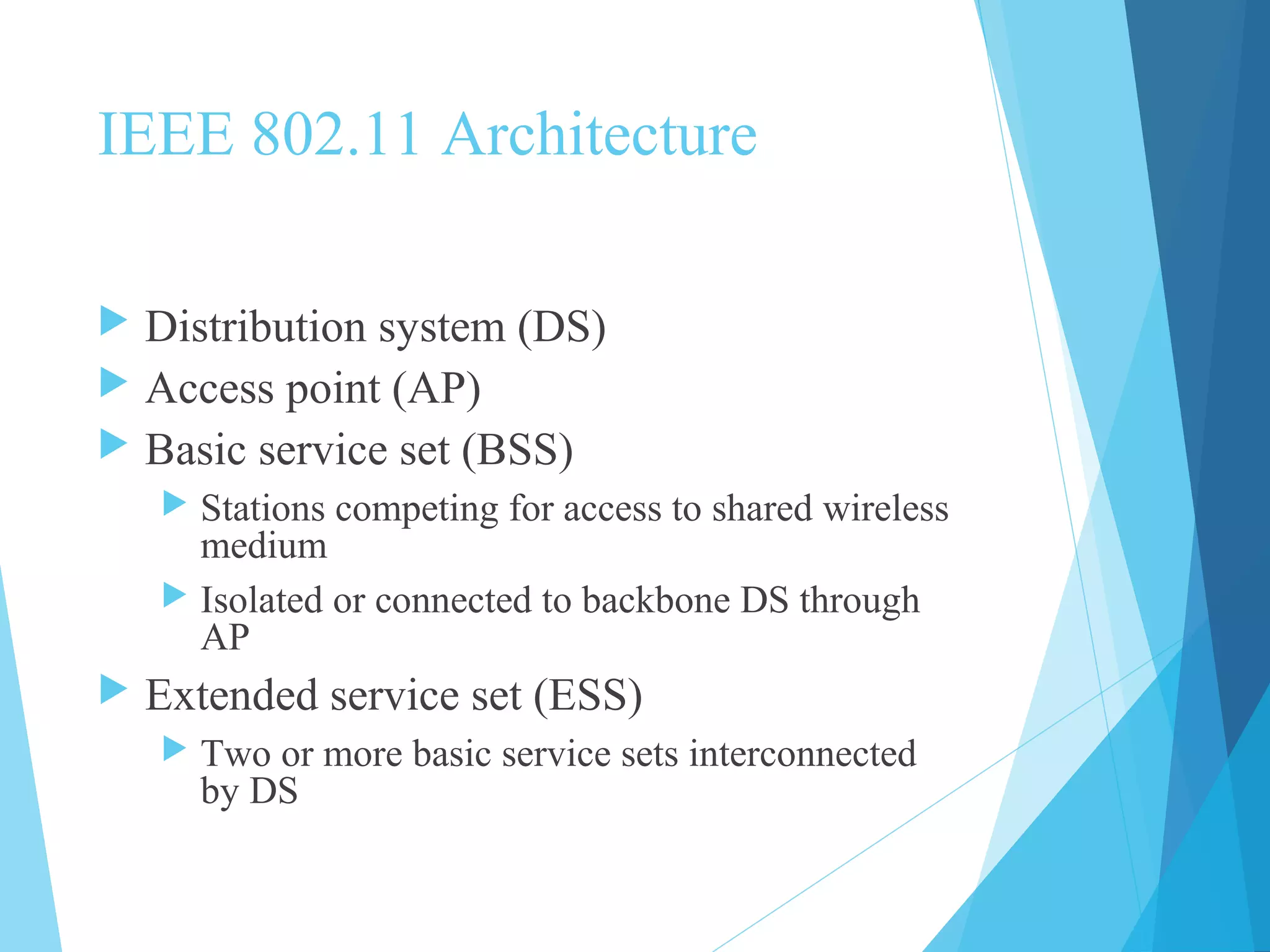
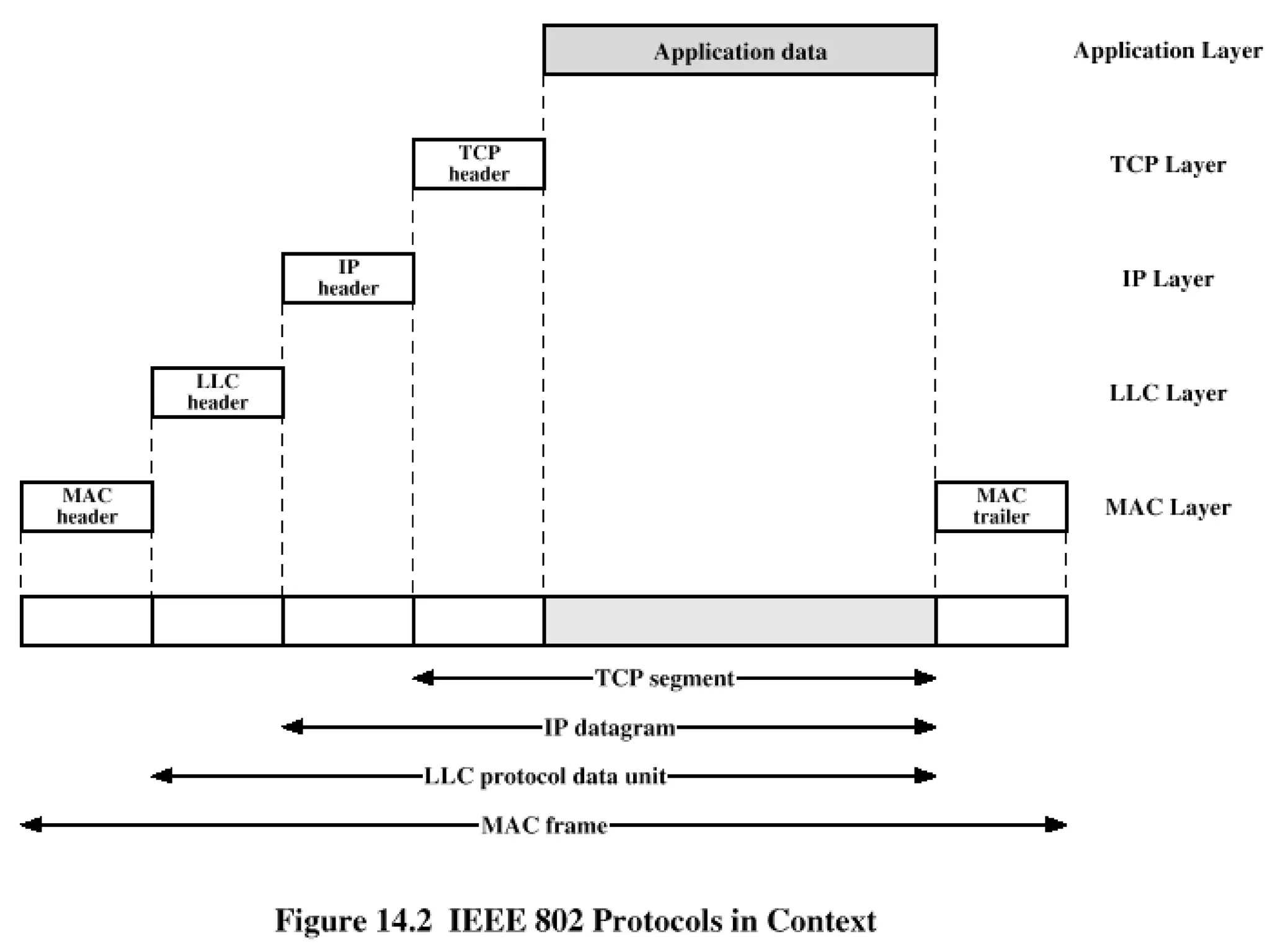
The document discusses the protocol layers and architecture of IEEE 802.11 wireless LAN standards. It describes the functions of the physical, medium access control (MAC), and logical link control (LLC) layers. The MAC frame format and access control methods using interframe spaces are also summarized. Additionally, it outlines services provided within IEEE 802.11 wireless distributions systems including distribution, integration, and mobility-related services.