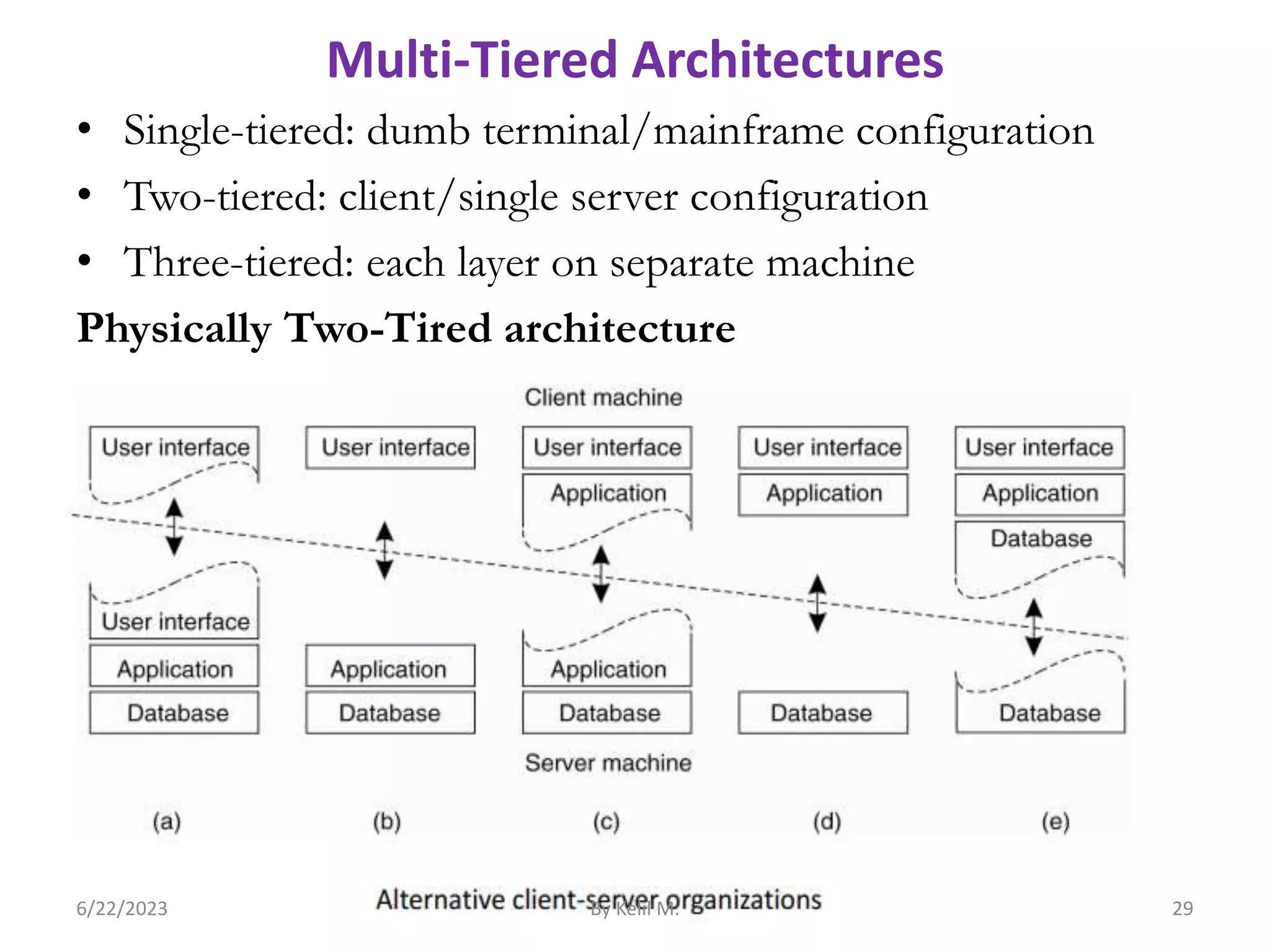
This document summarizes key aspects of distributed system architecture from Chapter Two. It discusses software and system architectures, architectural styles including layered, object-based, data-centered, and event-based. It also covers centralized architectures like client-server and multi-tiered architectures. Decentralized architectures through vertical and horizontal distribution are described as well. Specific examples like internet search engines and stock broker systems are provided to illustrate architectural concepts.