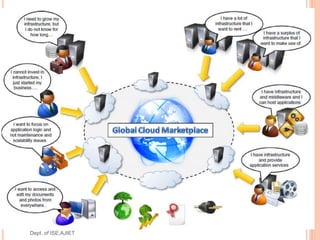
This document outlines the syllabus for a course on Cloud Computing and its Applications. It includes the course code, credits, objectives, outcomes, modules, textbook, and content to be covered. The course aims to explain cloud technology principles, compare programming models, and teach how to choose appropriate cloud models for applications. Key topics include cloud computing concepts, frameworks, data intensive computing, infrastructure as a service, platform as a service, software as a service, and virtualization.



























































![According to Goldberg and Popek[1974] -virtual machine
manager - Three properties have to be satisfied:
Equivalence: A guest running under the control of a
virtual machine manager should exhibit the same
behavior as when it is executed directly on the physical
host.
Resource control: The virtual machine manager should
be in complete control of virtualized resources.
Efficiency: A statistically dominant fraction of the
machine instructions should be executed without
intervention from the virtual machine manager.
68
Dept. of ISE,AJIET](https://image.slidesharecdn.com/cloudmodule1-230911164004-e4933afc/85/Cloud-Module-1-pptx-68-320.jpg)