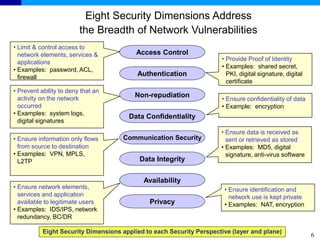
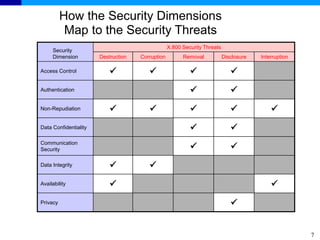
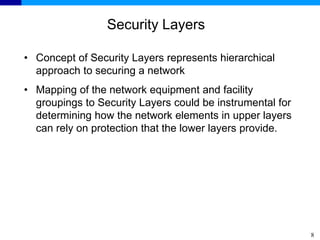
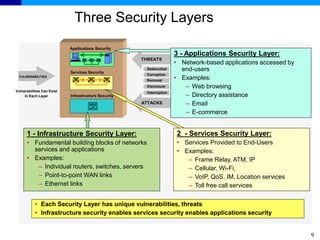
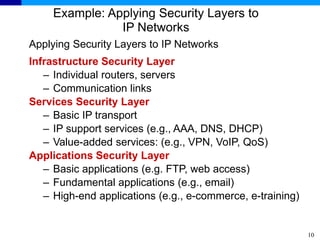
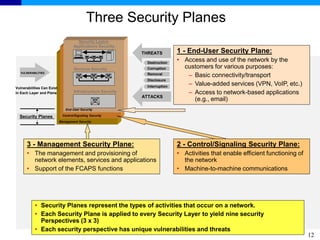
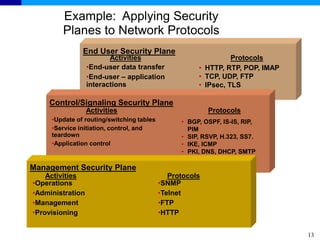
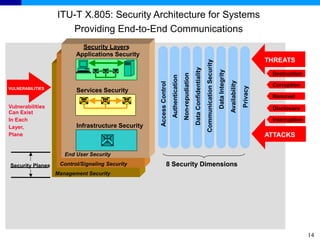
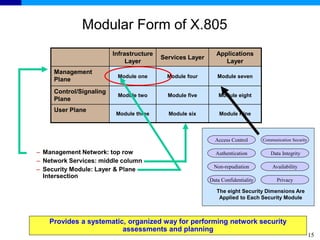
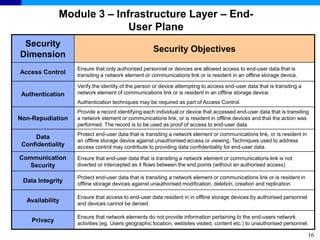
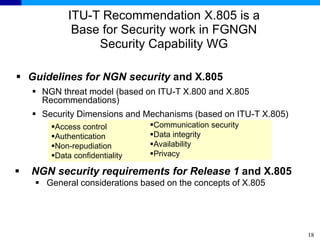
The document discusses the ITU-T Recommendation X.805 Security Architecture for Systems Providing End-to-End Communications. It addresses three main issues: the threats against which protection is needed, the network equipment and facilities that need protection, and the network activities that need protection. The security architecture defines security dimensions, layers, and planes to provide a systematic framework for assessing vulnerabilities and planning security across the network. ITU-T X.805 serves as a base for security work in the FGNGN Security Capability Working Group.