The document provides an overview of network security essentials, including:
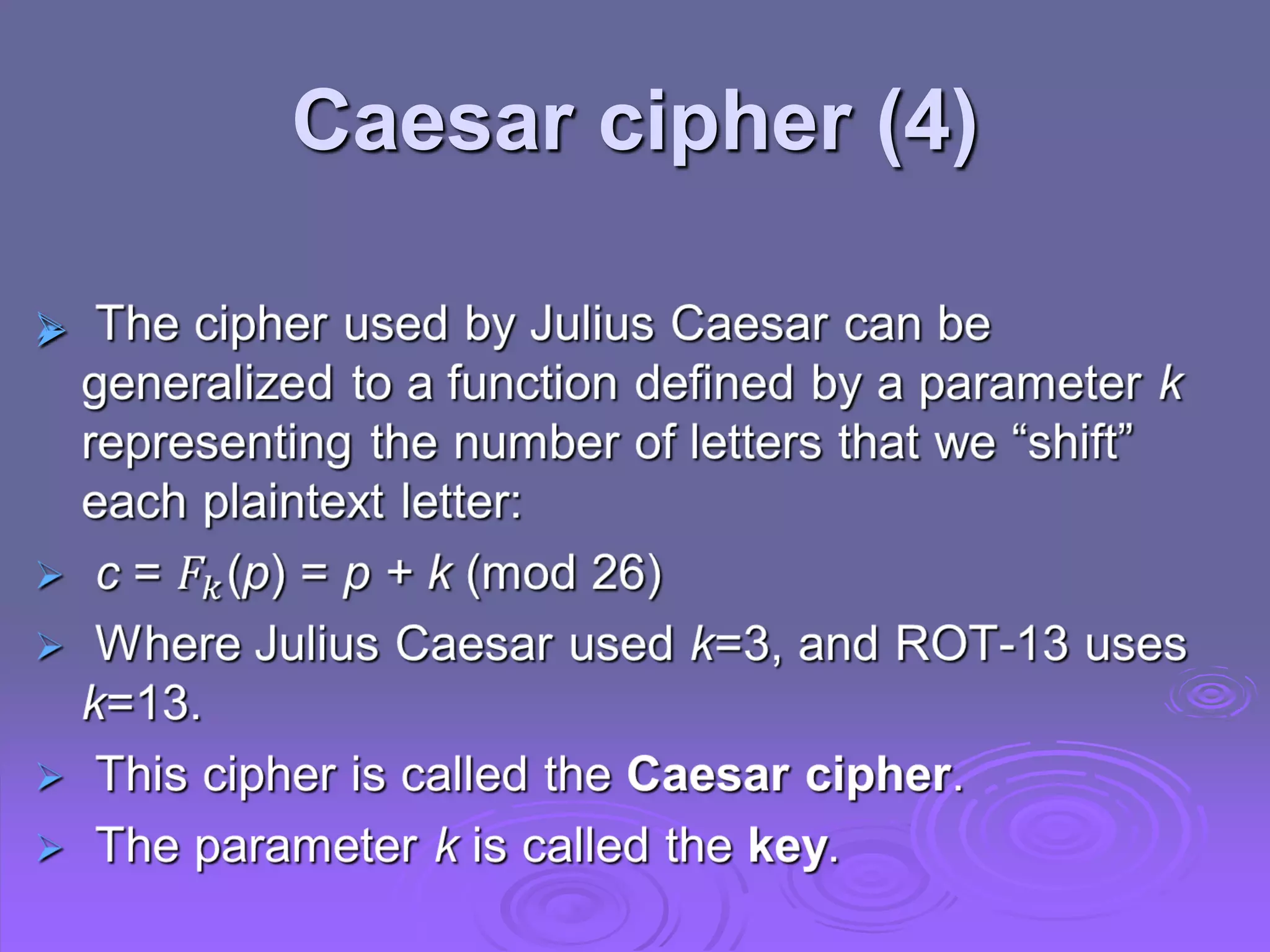
1. Symmetric encryption uses a shared secret key between sender and receiver to encrypt and decrypt messages. Common symmetric algorithms include the Shift Cipher and Caesar Cipher.
2. The Caesar Cipher replaces each letter with the letter three positions further down the alphabet, encrypting "ET TU BRUTUS" to "HW WX EUXWXV".
3. Cryptography concepts like plaintext, ciphertext, cipher algorithms, and cryptanalysis are introduced. Symmetric encryption requires secure key distribution and management.



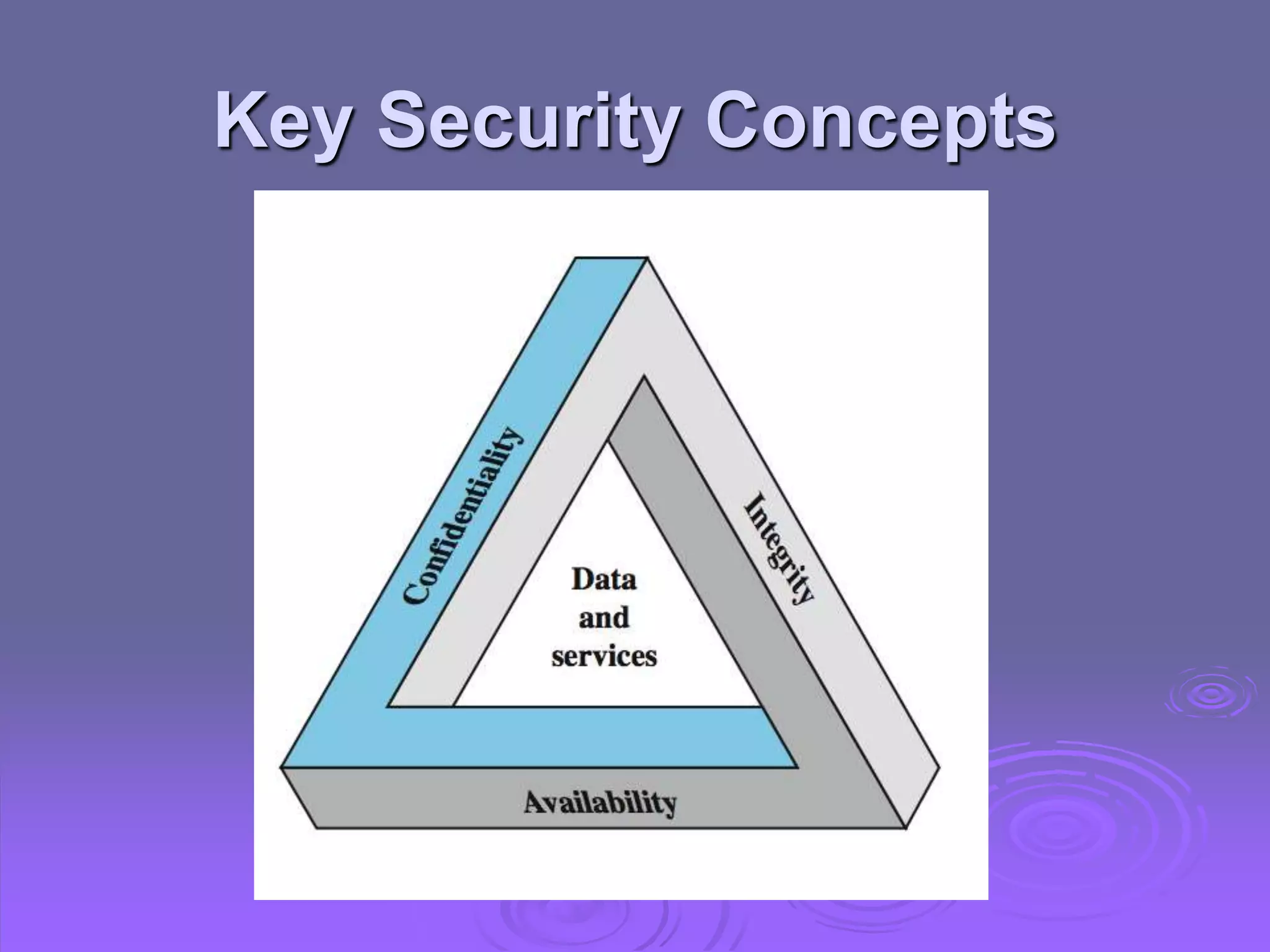
![Computer Security
The protection afforded to an automated
information system in order to attain the
applicable objectives of preserving the
integrity, availability and confidentiality of
information system resources (includes
hardware, software, firmware,
information/data, and telecommunications)
[NIST 1995]](https://image.slidesharecdn.com/ns-lec-0102-230618042859-c3b2d386/75/NS-Lec-01-02-ppt-4-2048.jpg)