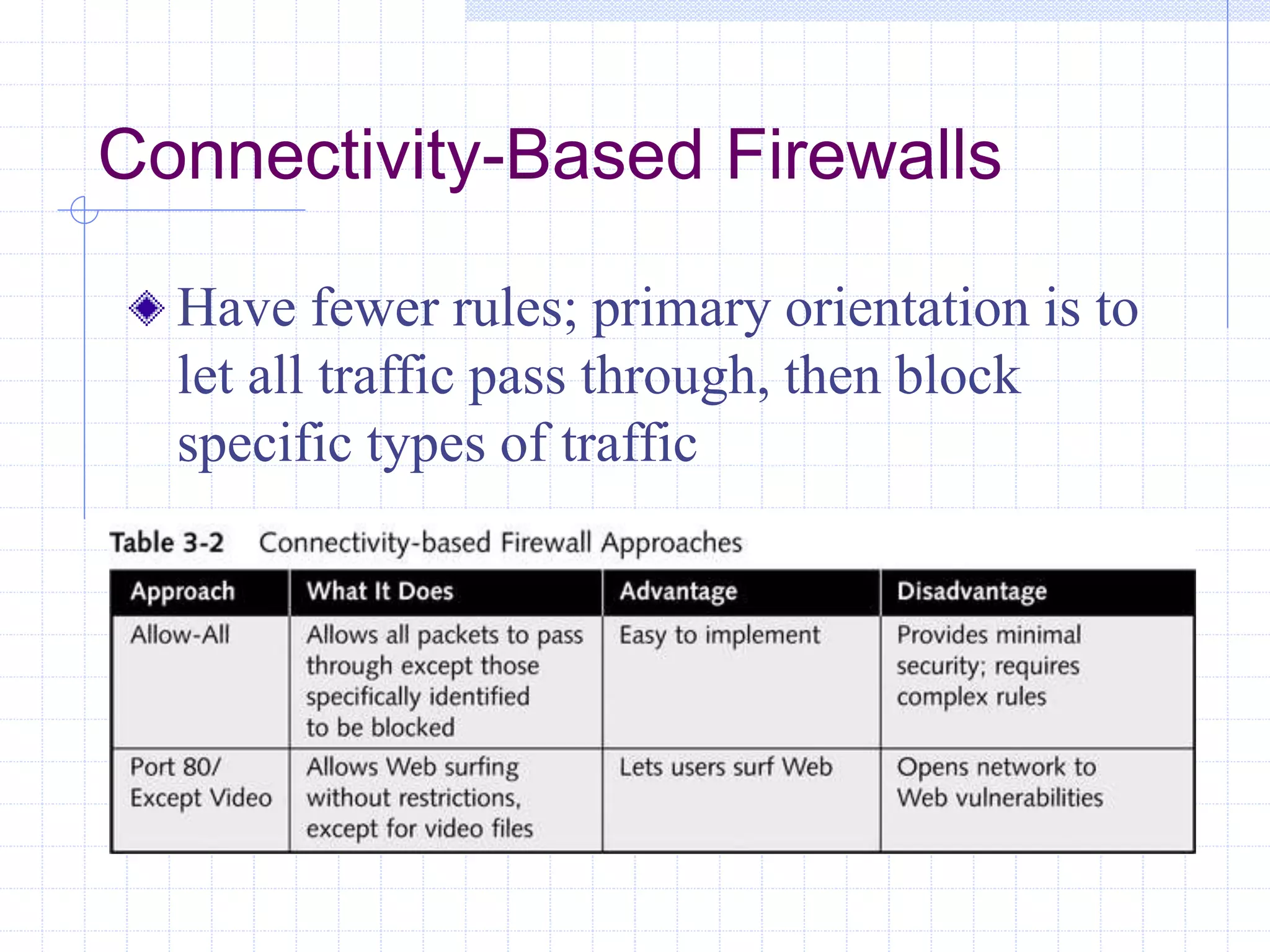
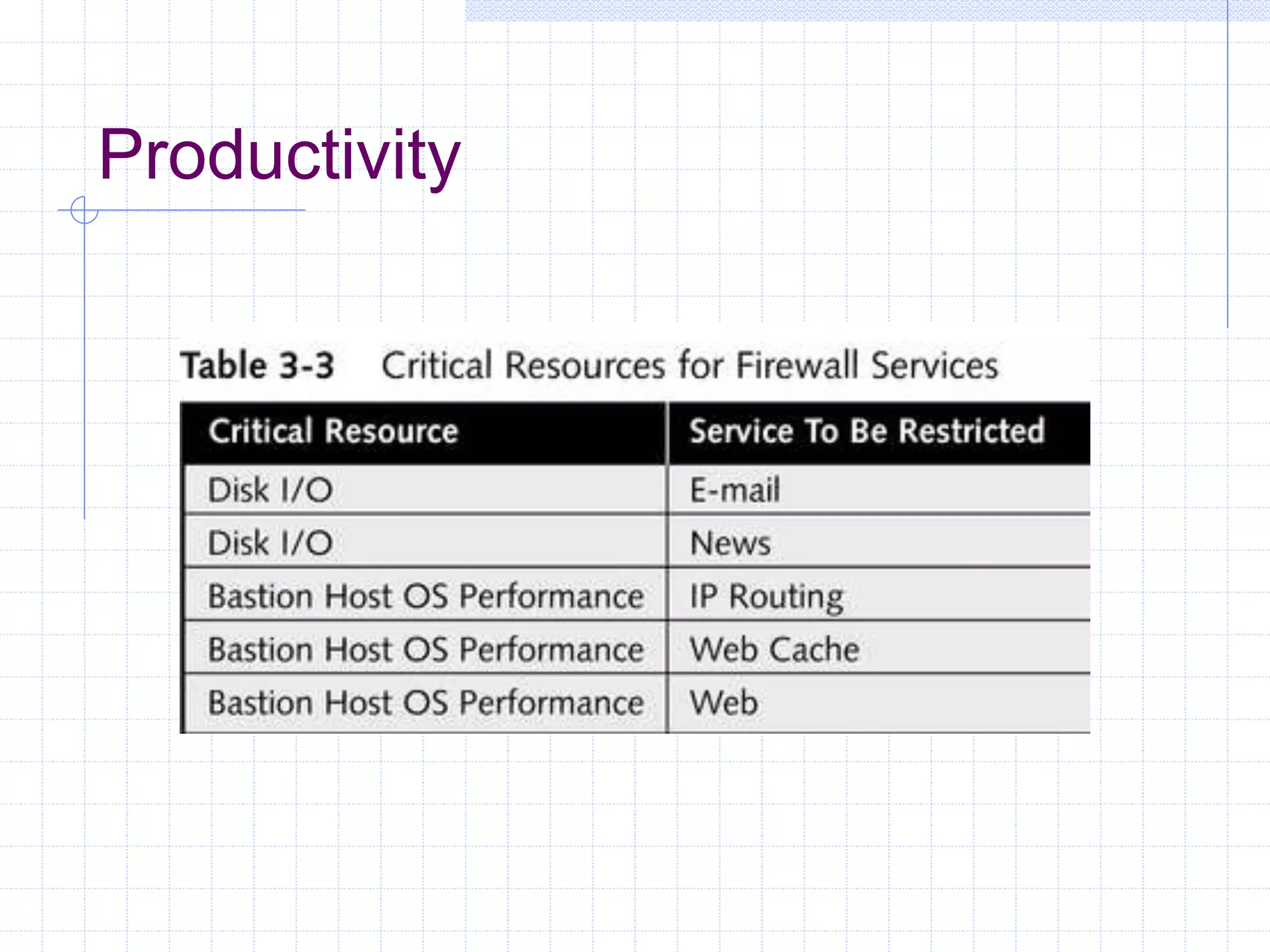
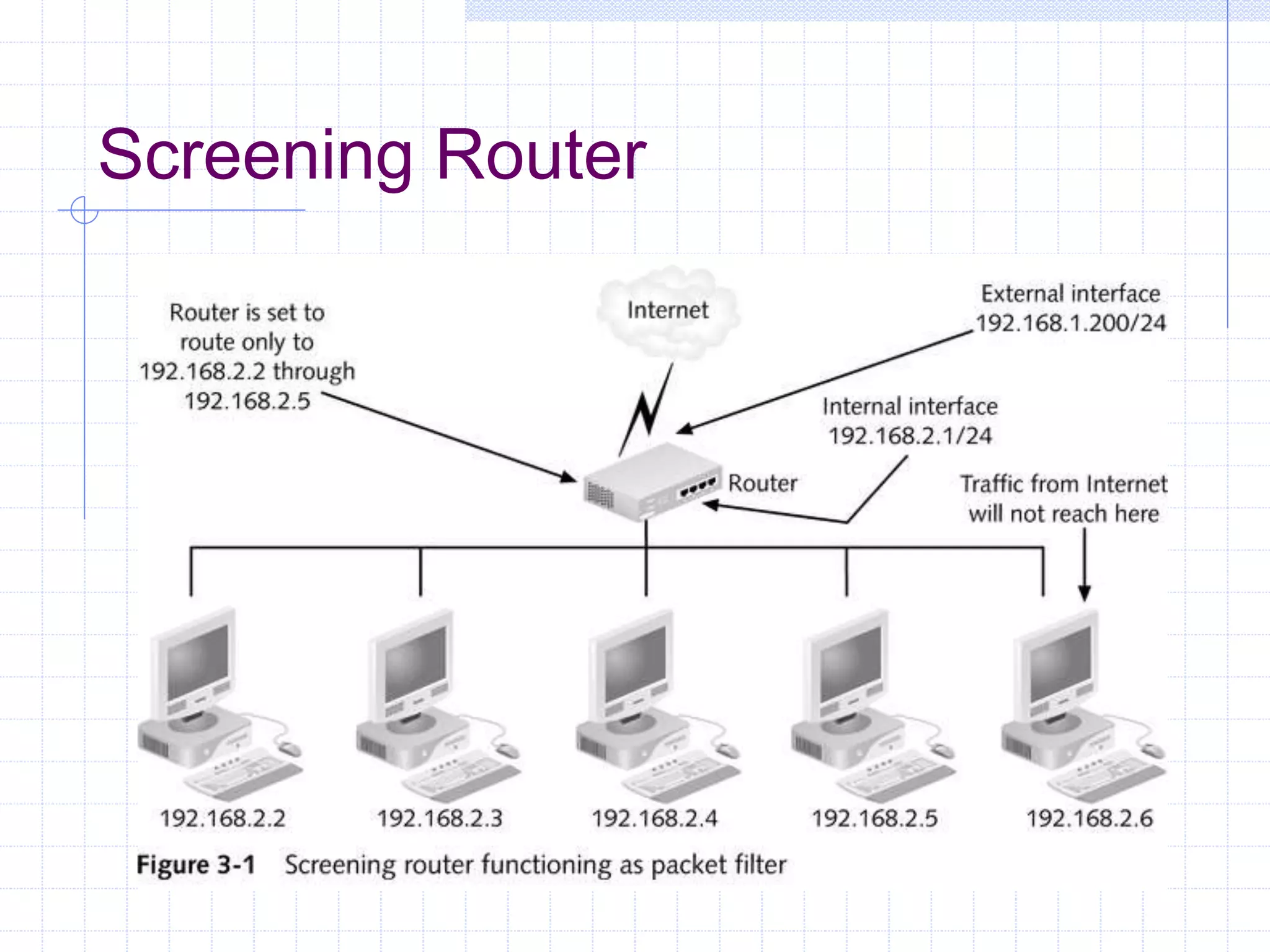
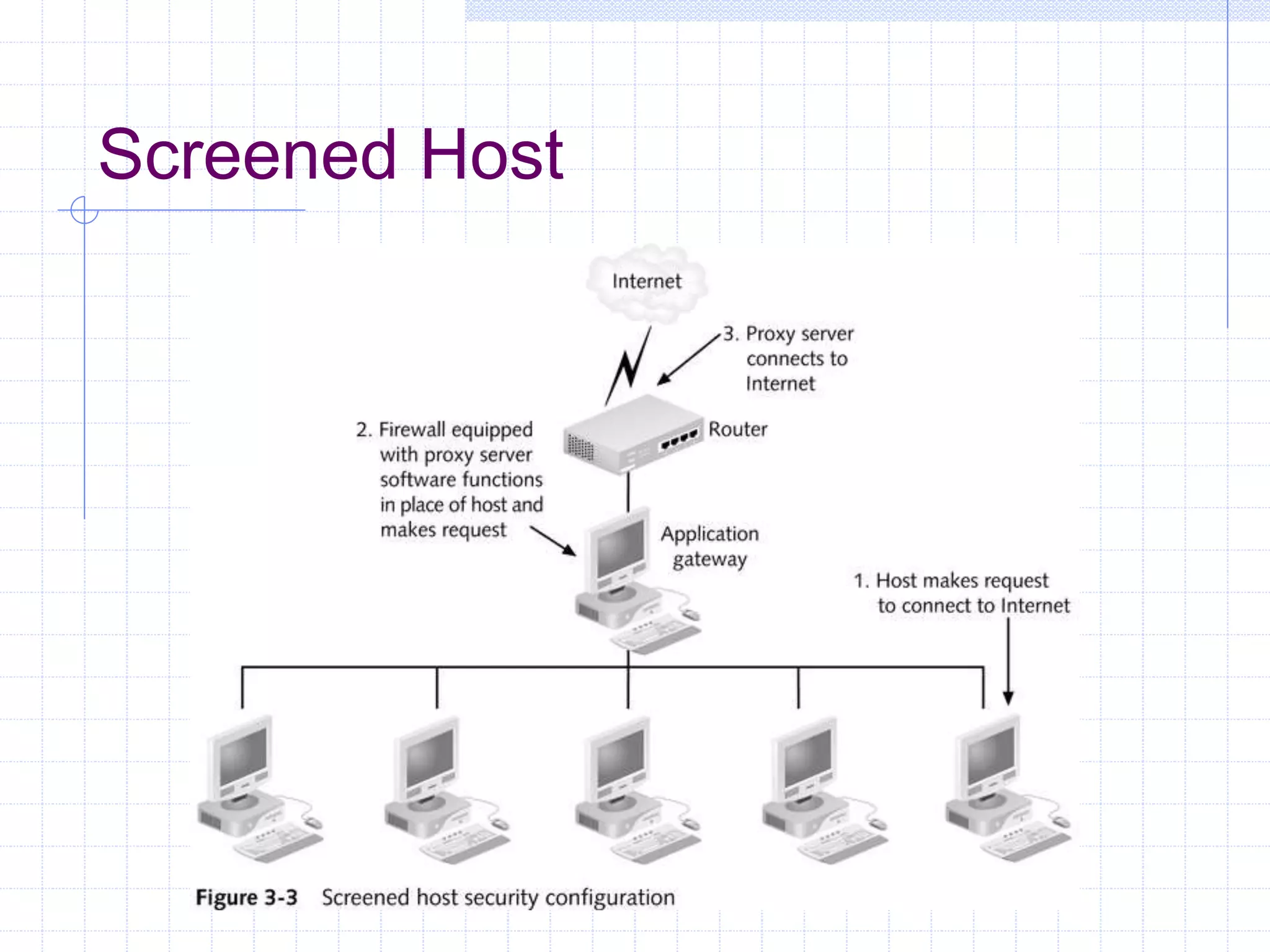
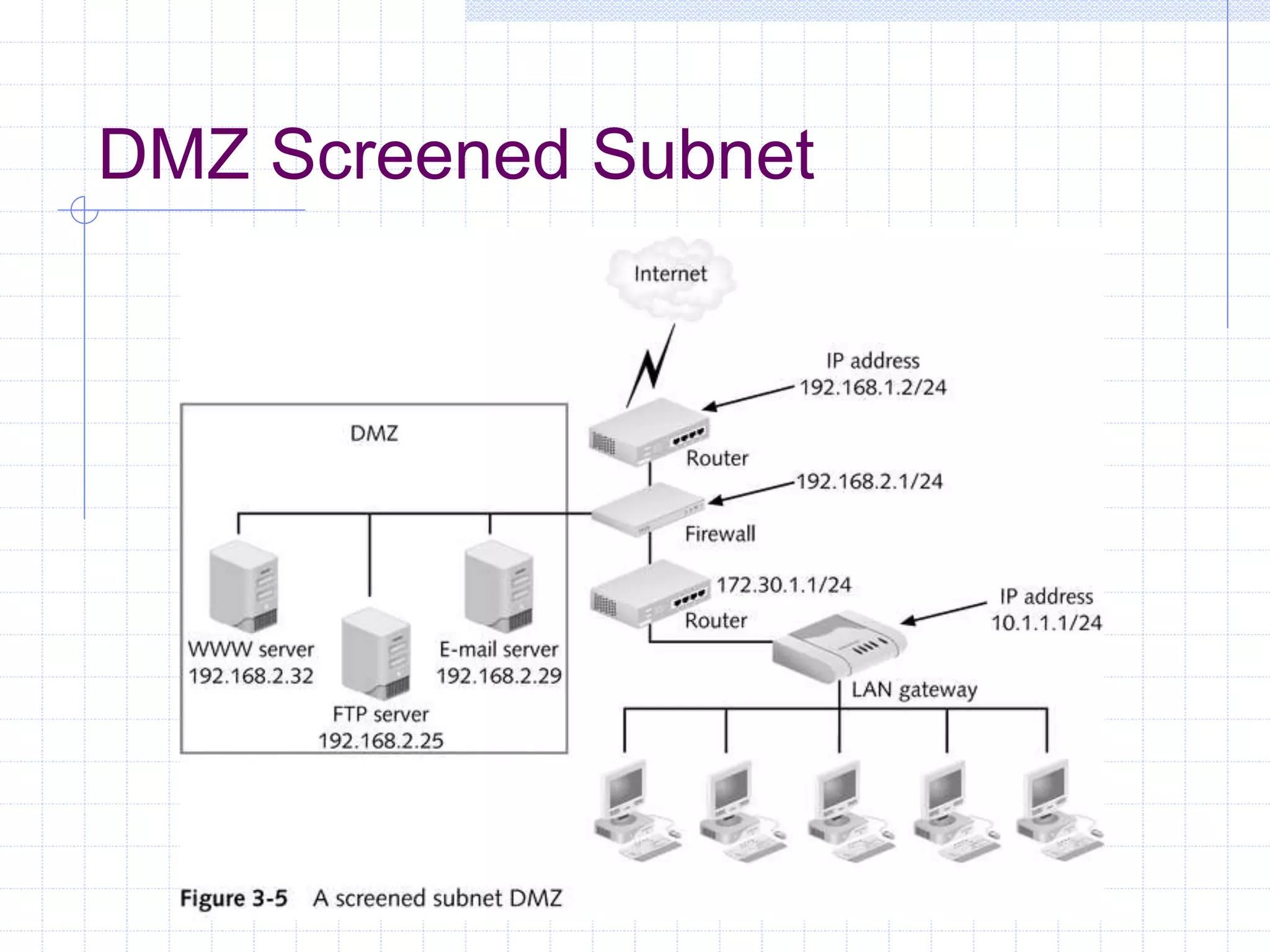
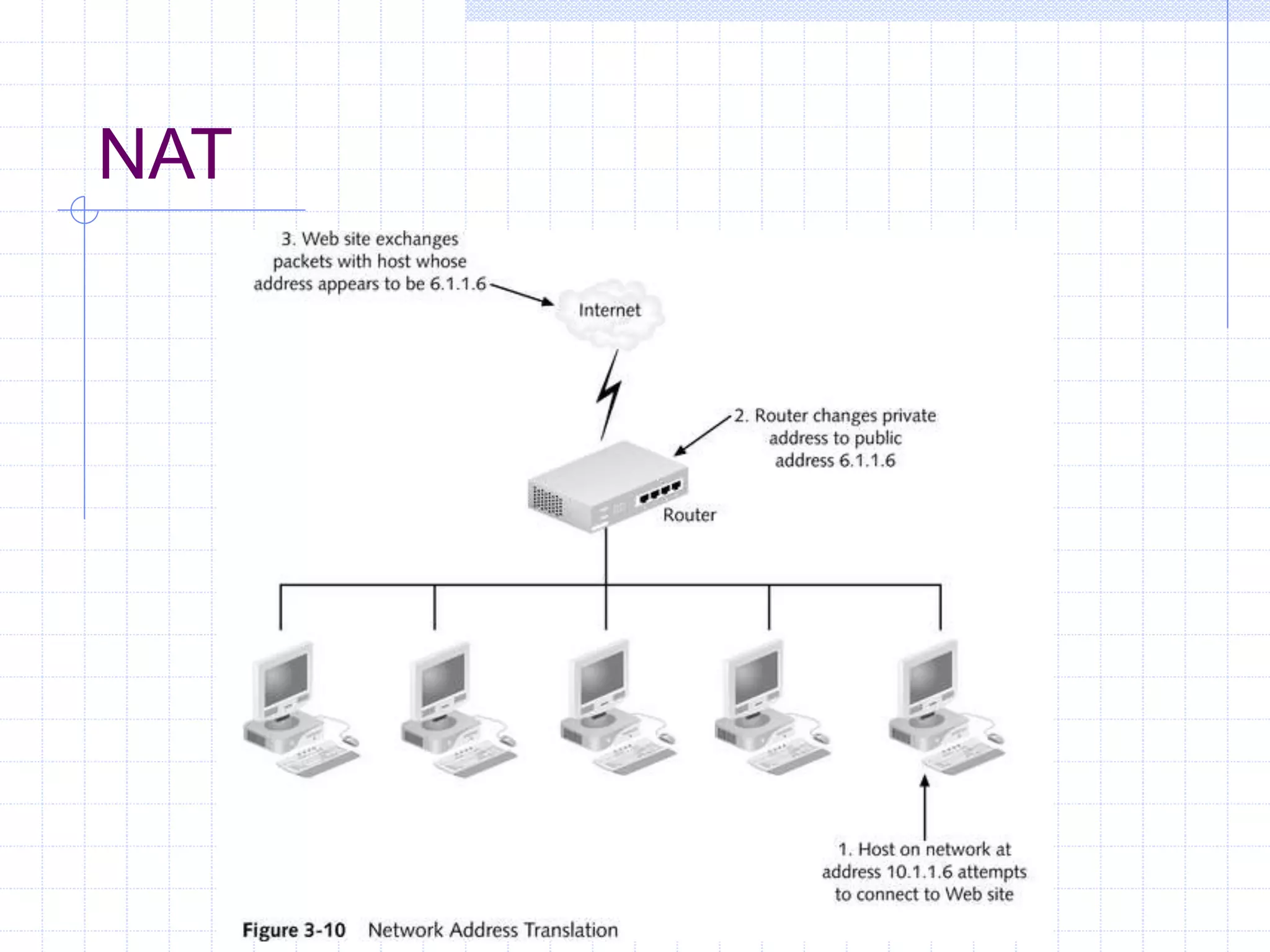
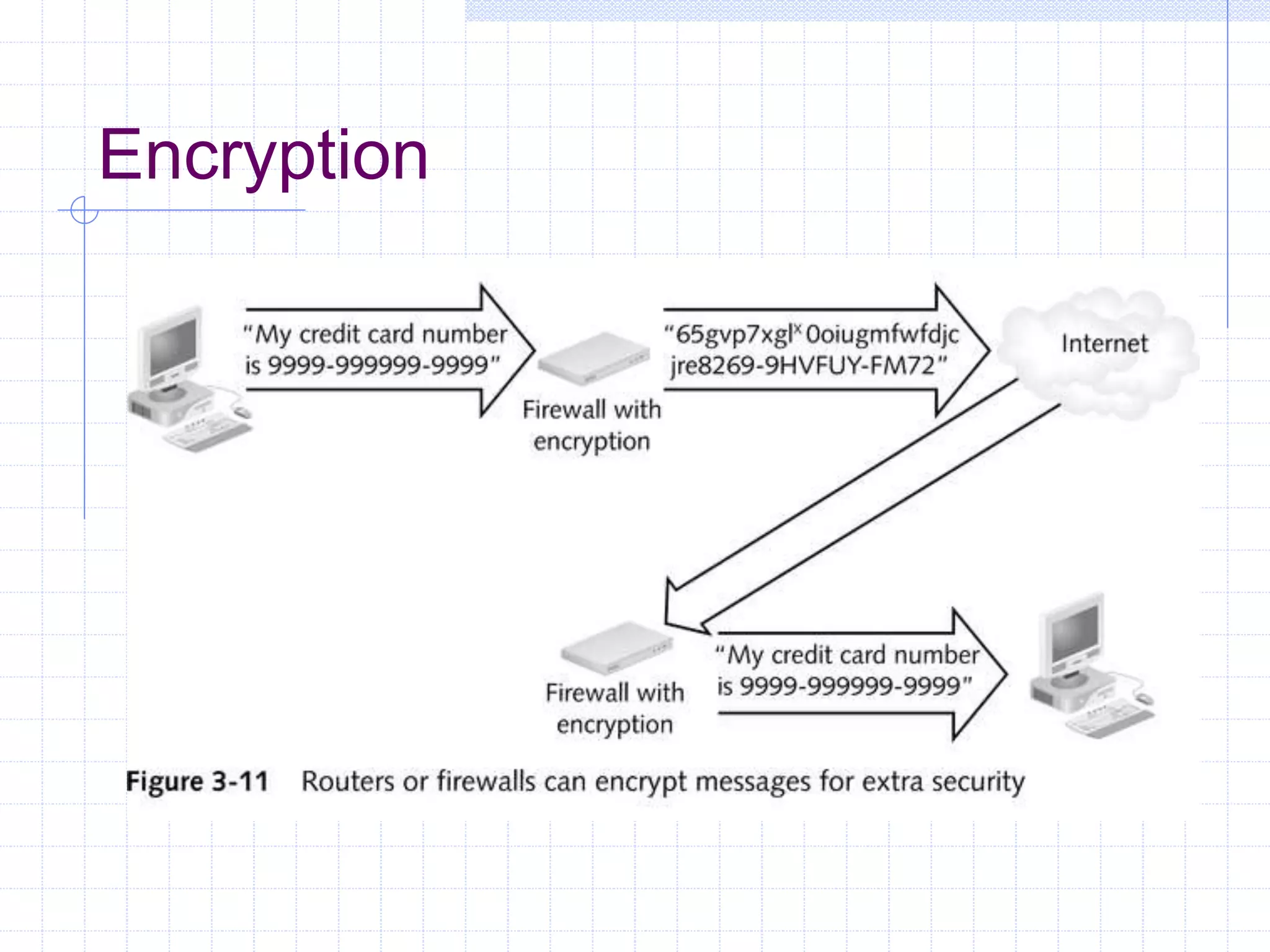
The document discusses different firewall configuration strategies, including restrictive firewalls that block all access by default and connectivity-based firewalls that allow all traffic by default and then block specific types. It describes using security components like screening routers, dual-homed hosts, screened hosts, and DMZs to implement firewall rules and defend against common attacks. The goal is to design perimeter security that integrates firewalls and components to create protected areas according to an organization's security policy and needs.