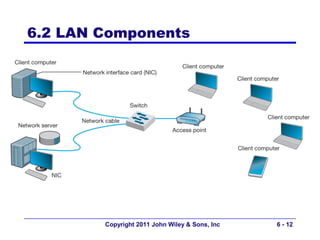
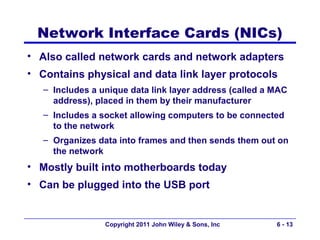
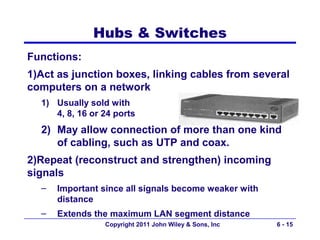
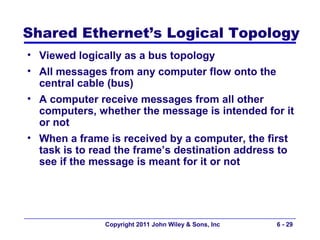
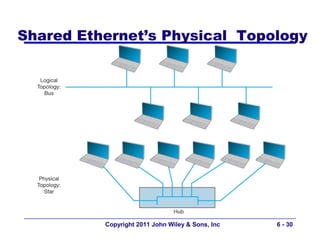
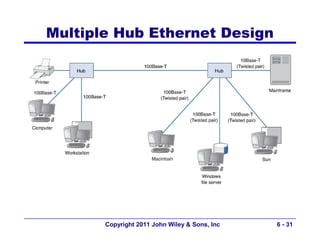
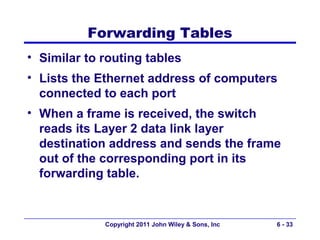
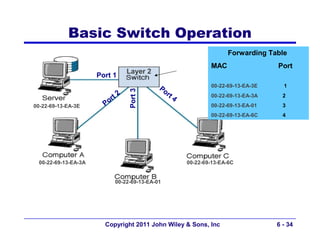
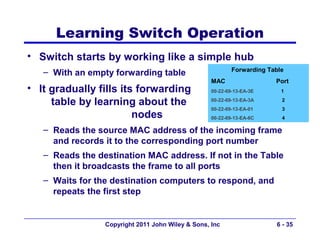
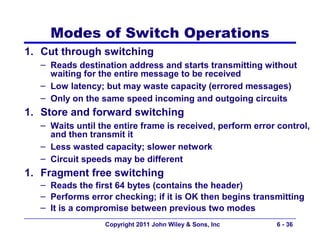
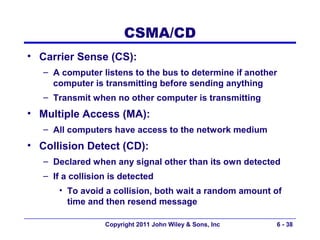
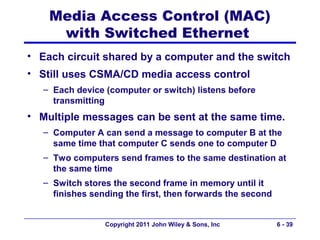
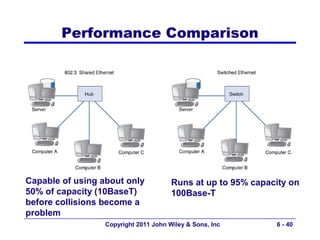
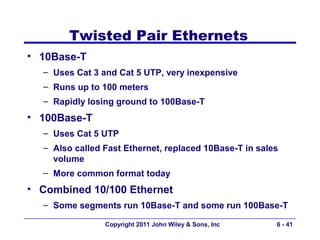
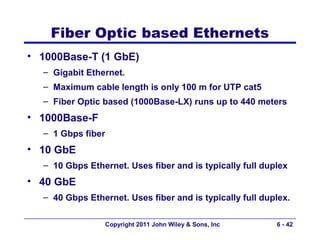
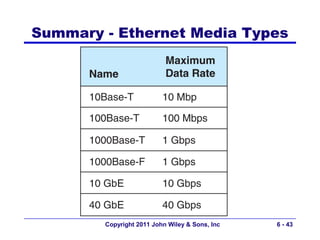
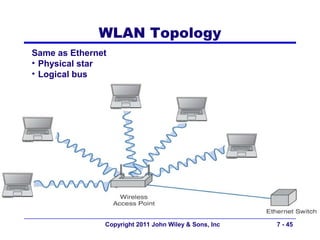
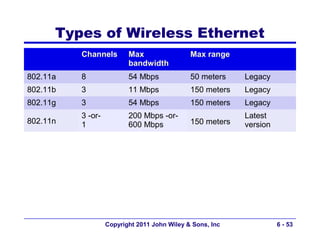
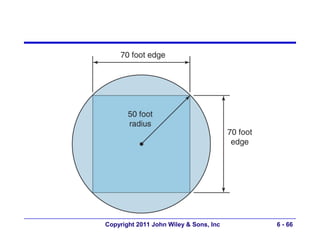
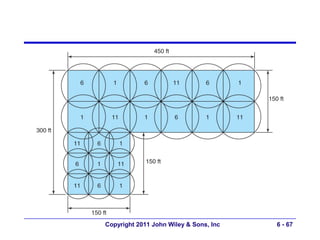
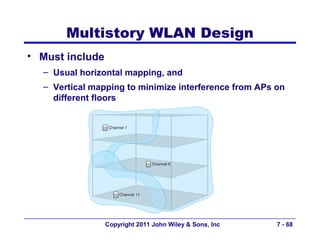
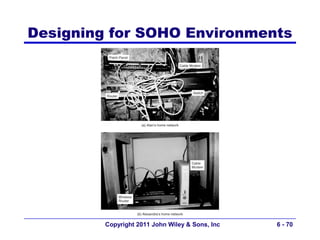
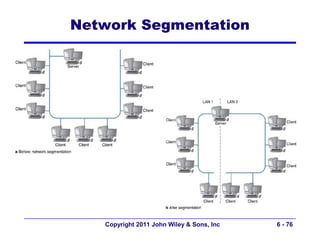
This document provides an overview of chapter 6 from the textbook "Fundamentals of Business Data Communications". The chapter discusses wired and wireless local area networks (LANs). It covers LAN components such as network interface cards, cables, hubs, switches, and access points. It also discusses wired Ethernet standards and technologies, including shared Ethernet using hubs and switched Ethernet using switches. Wireless Ethernet and considerations for LAN design and performance are also covered. The chapter concludes by discussing implications for network management.