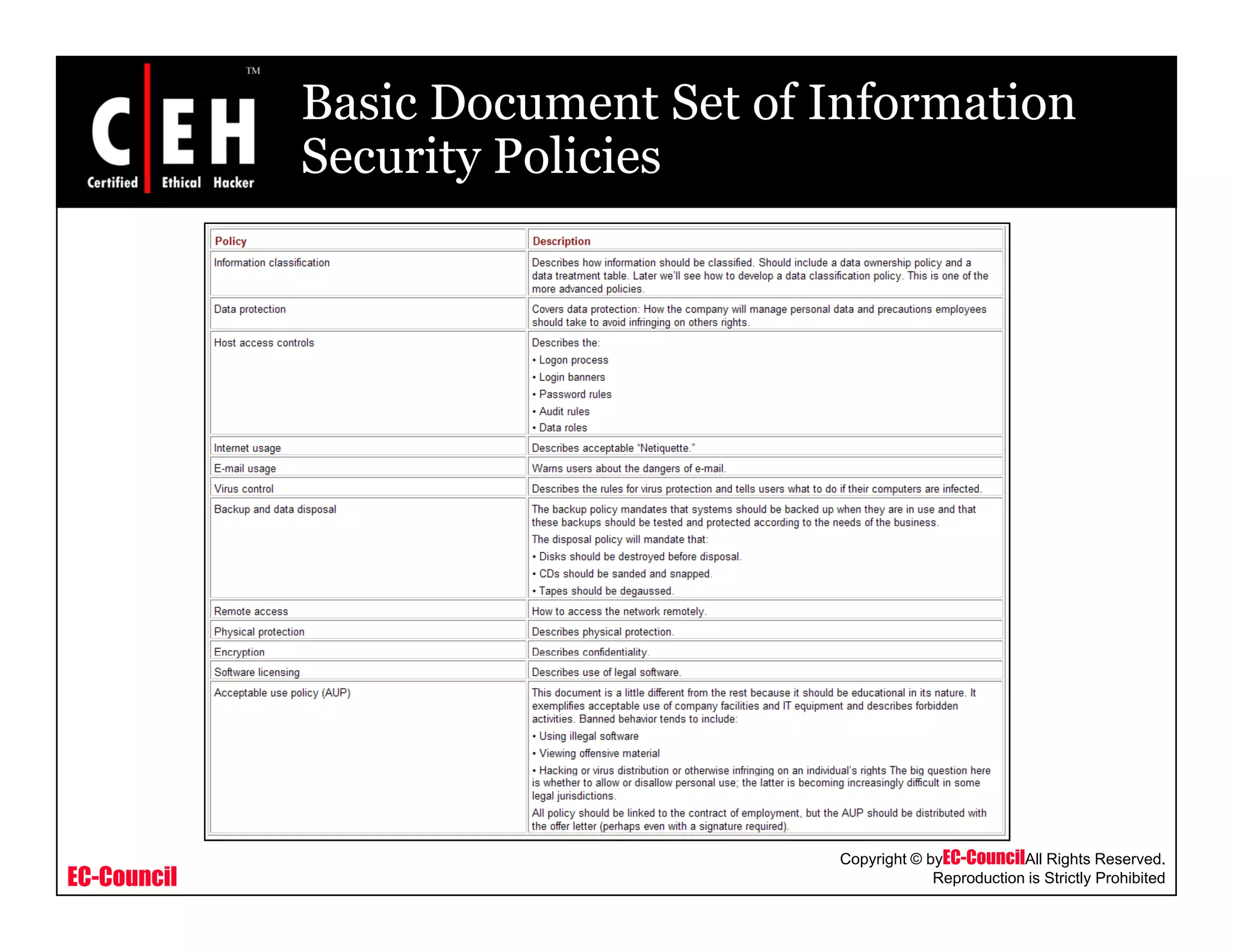
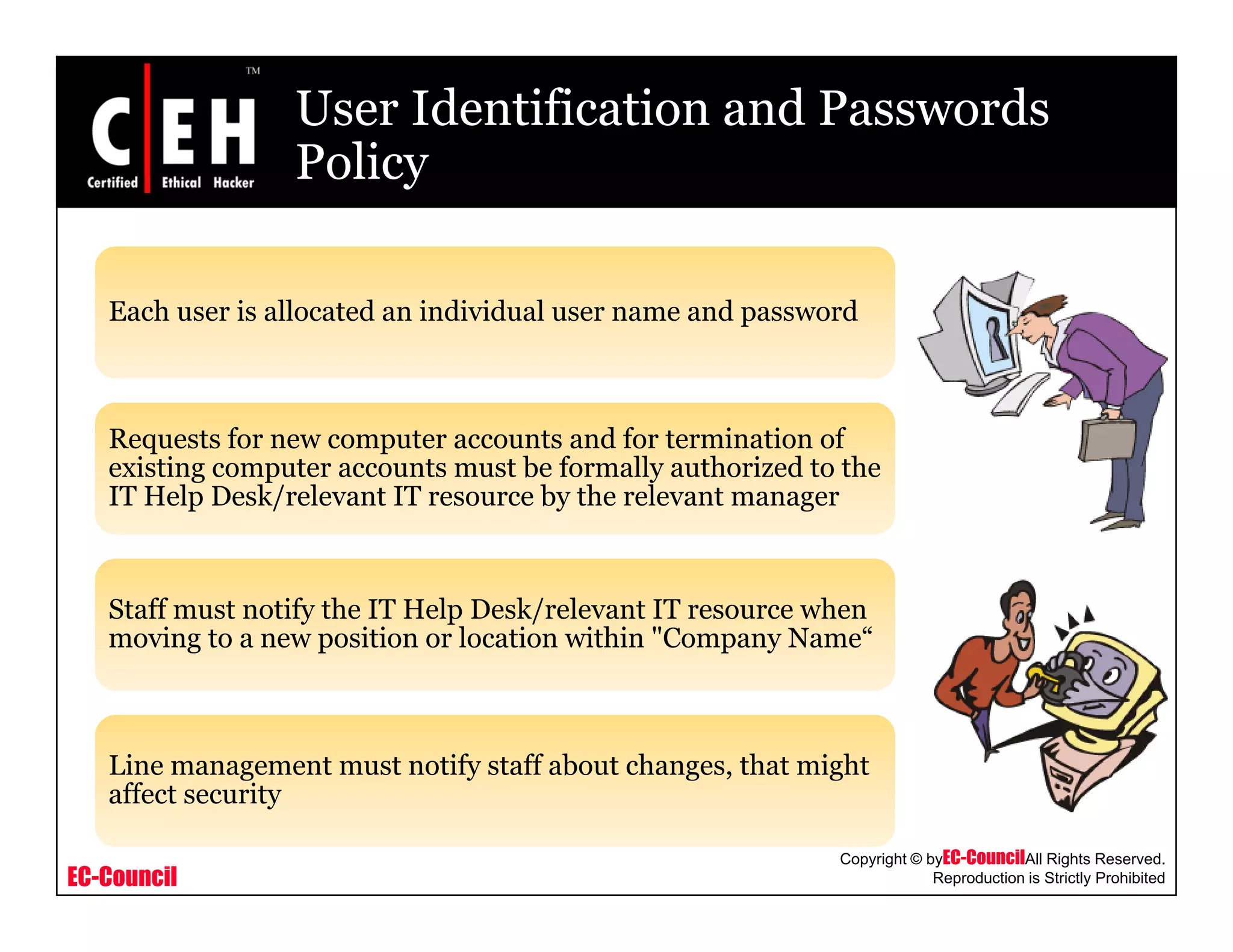
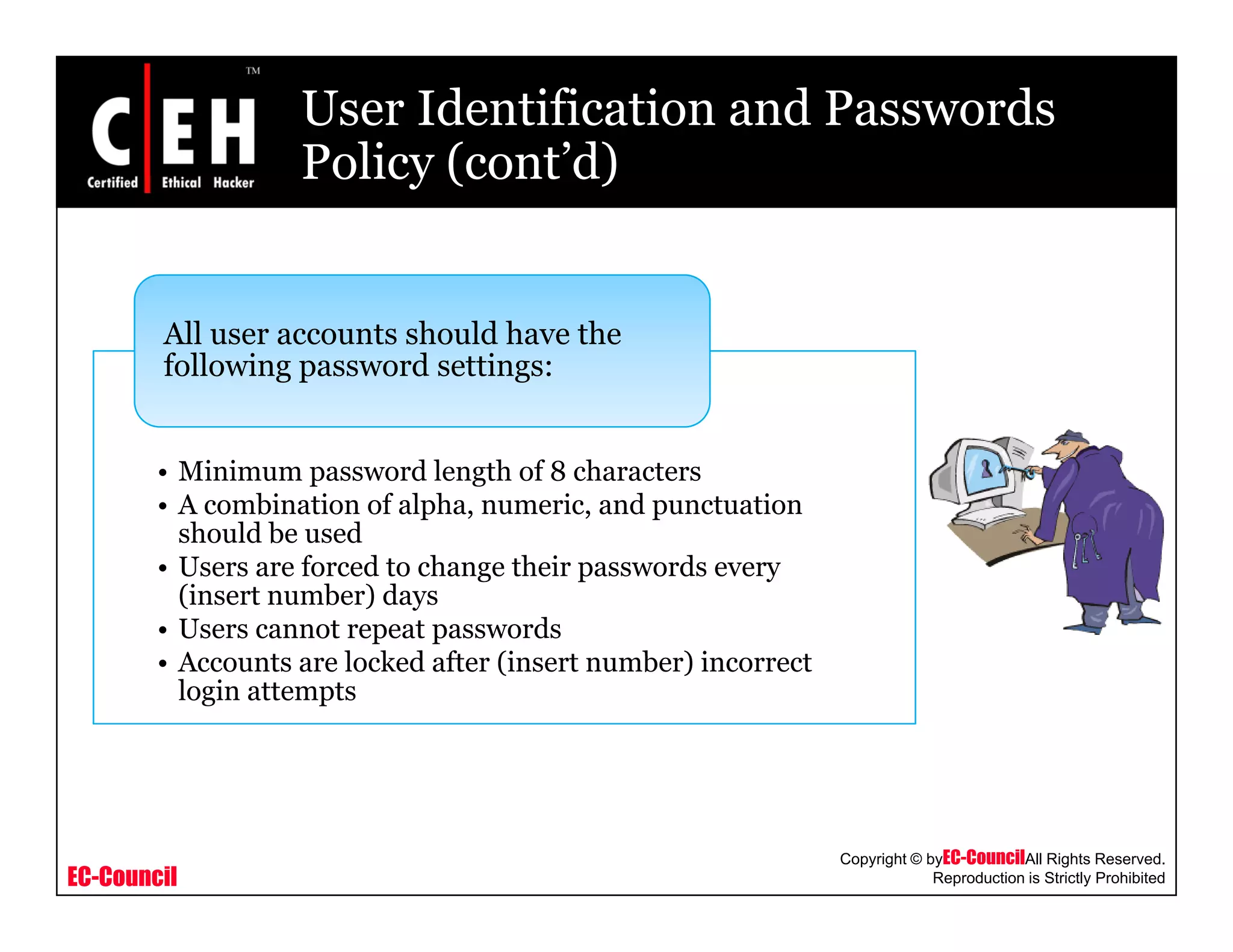
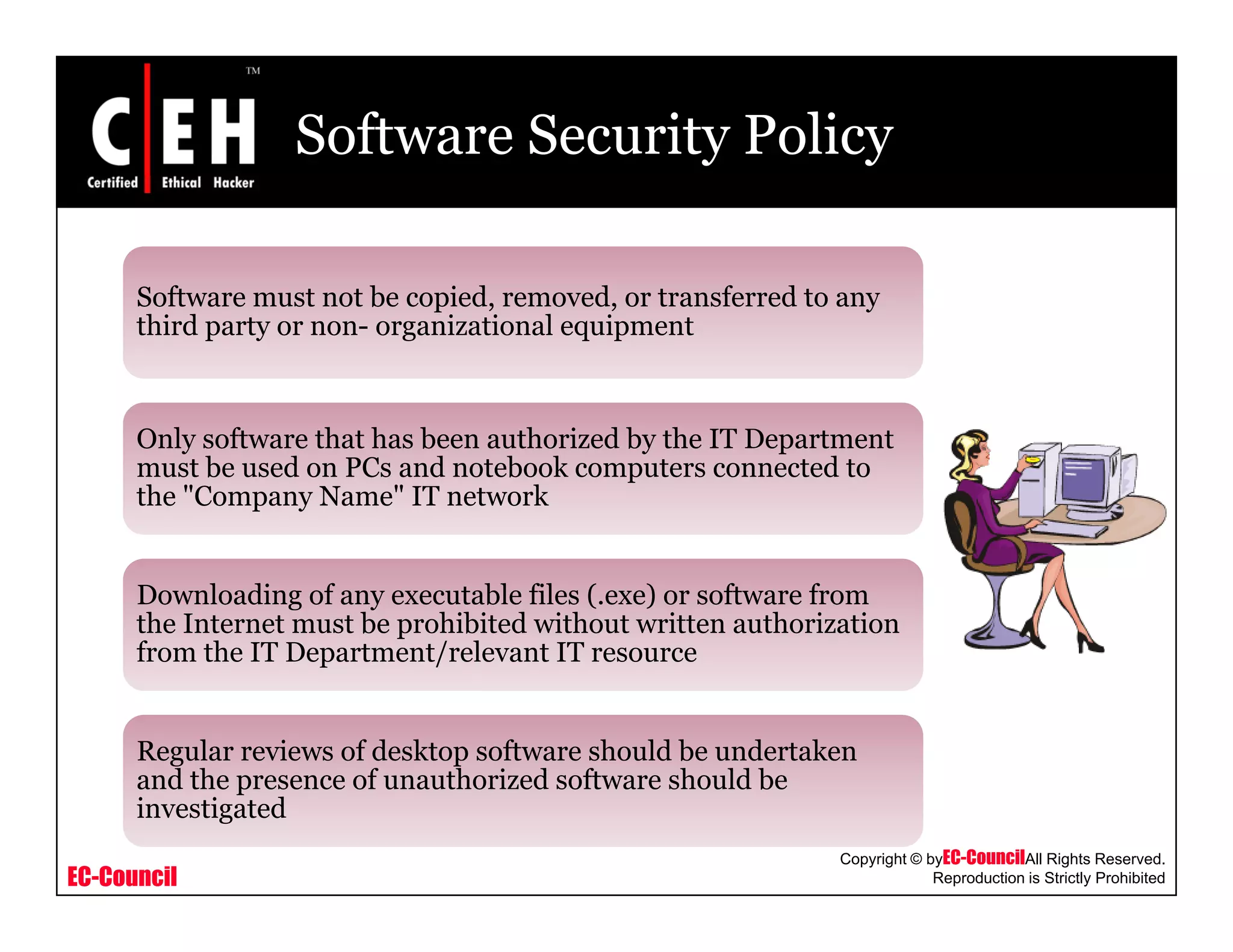
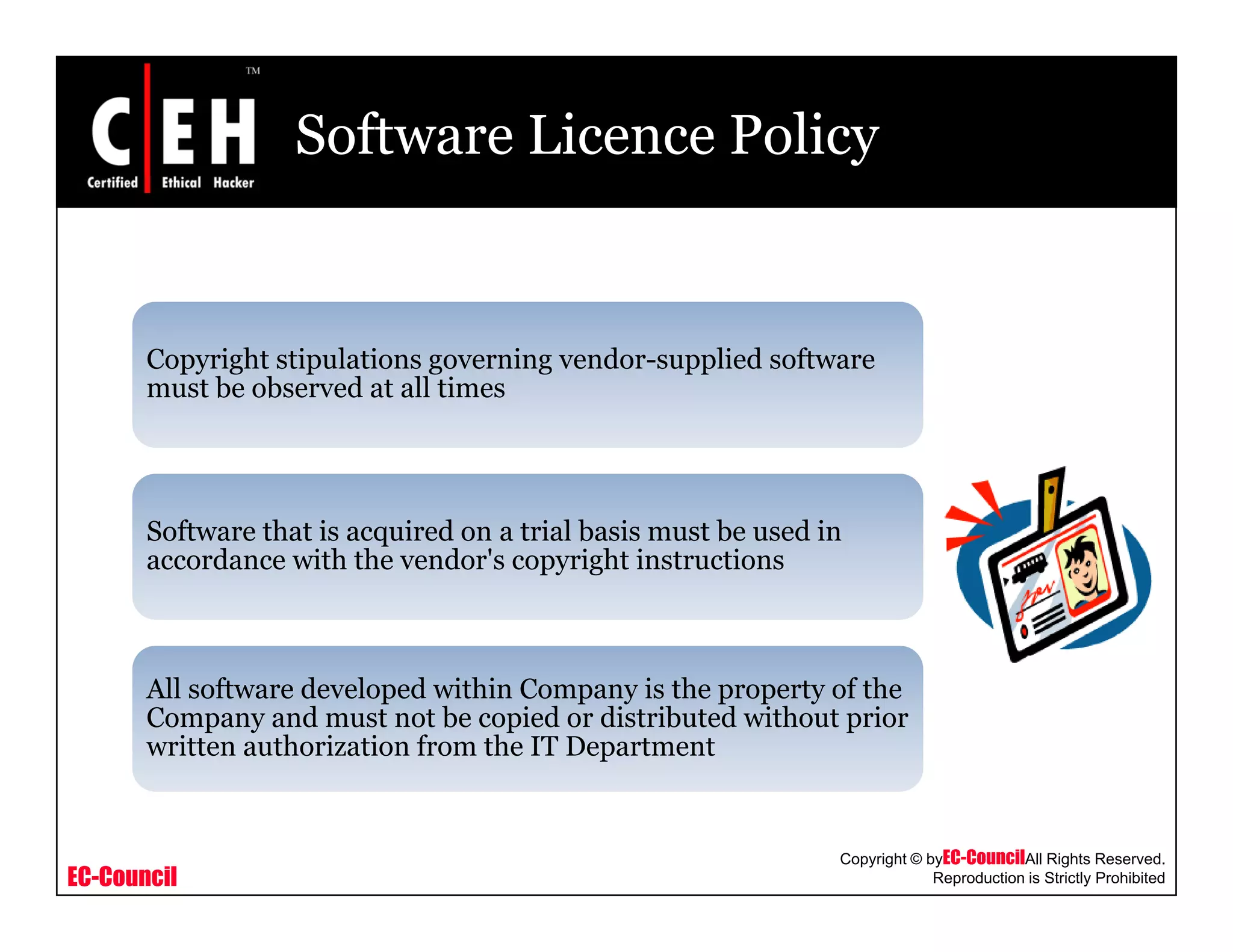
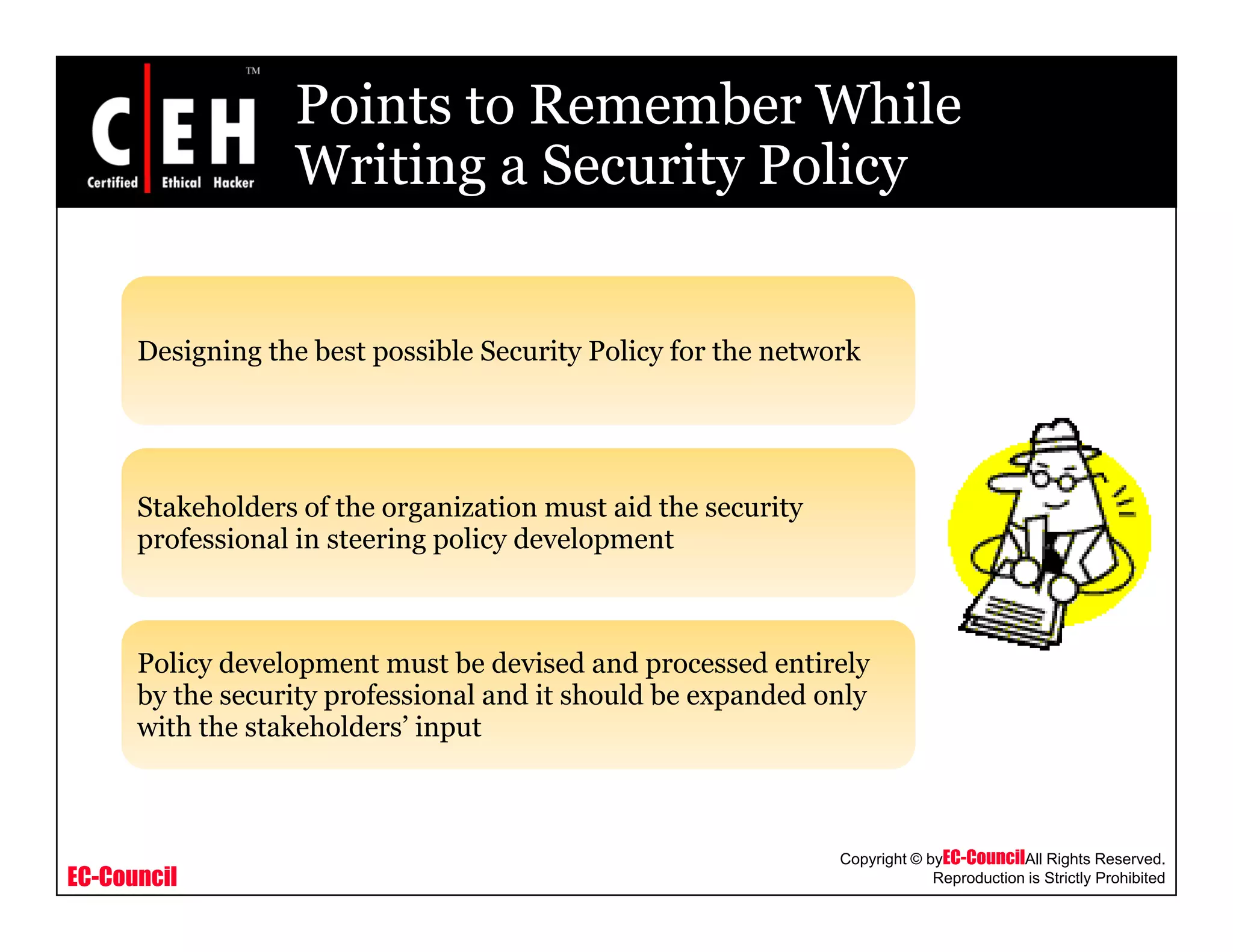
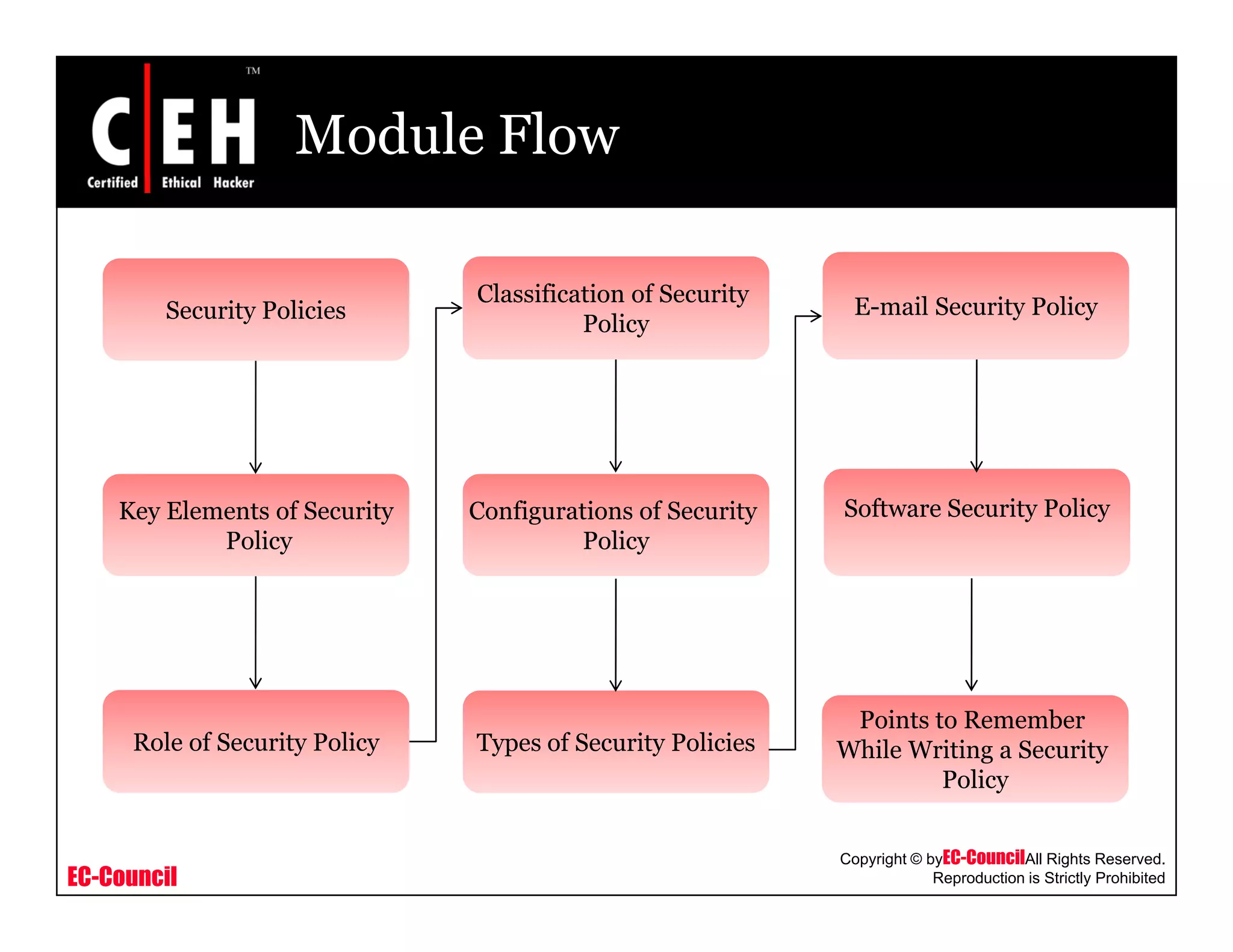
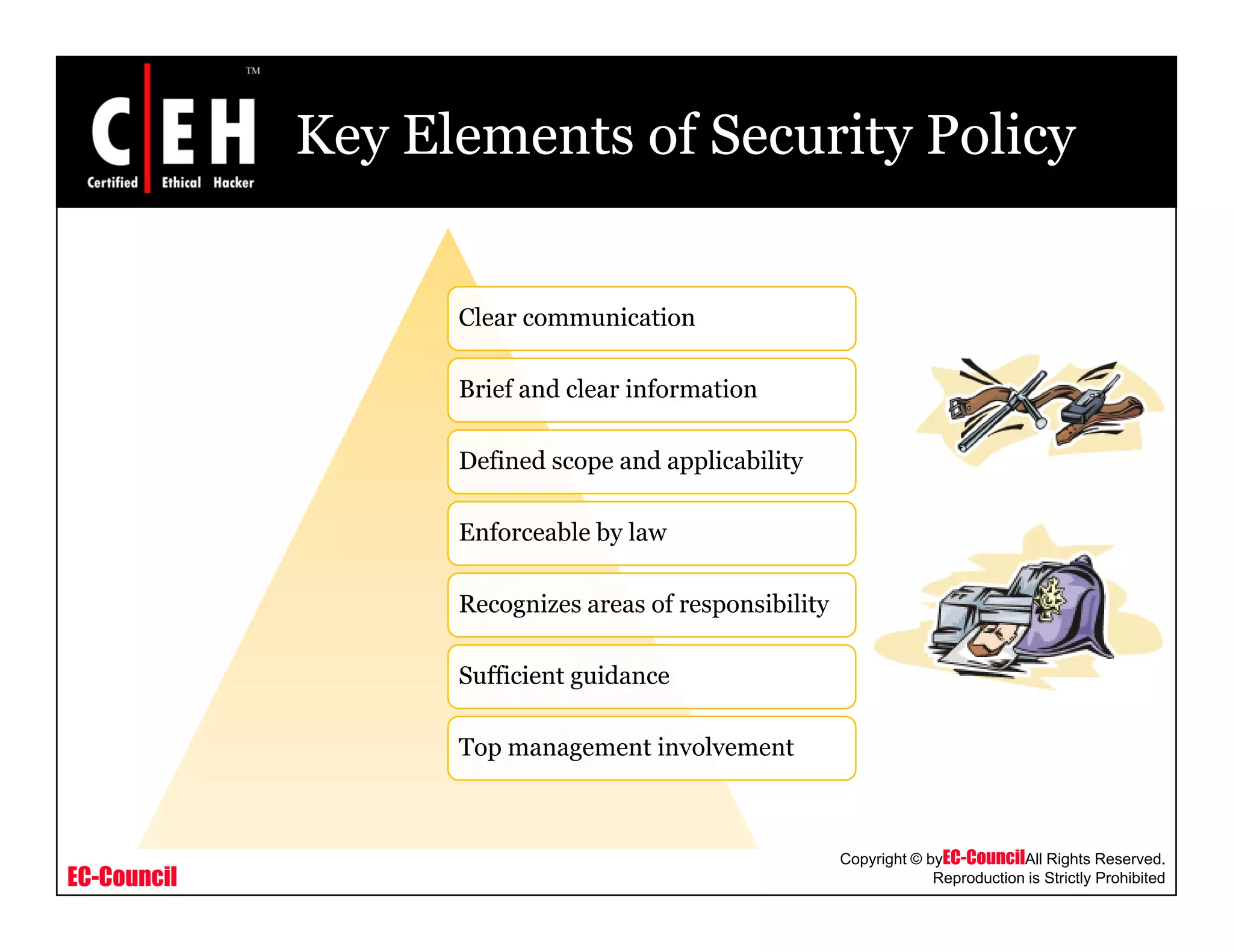
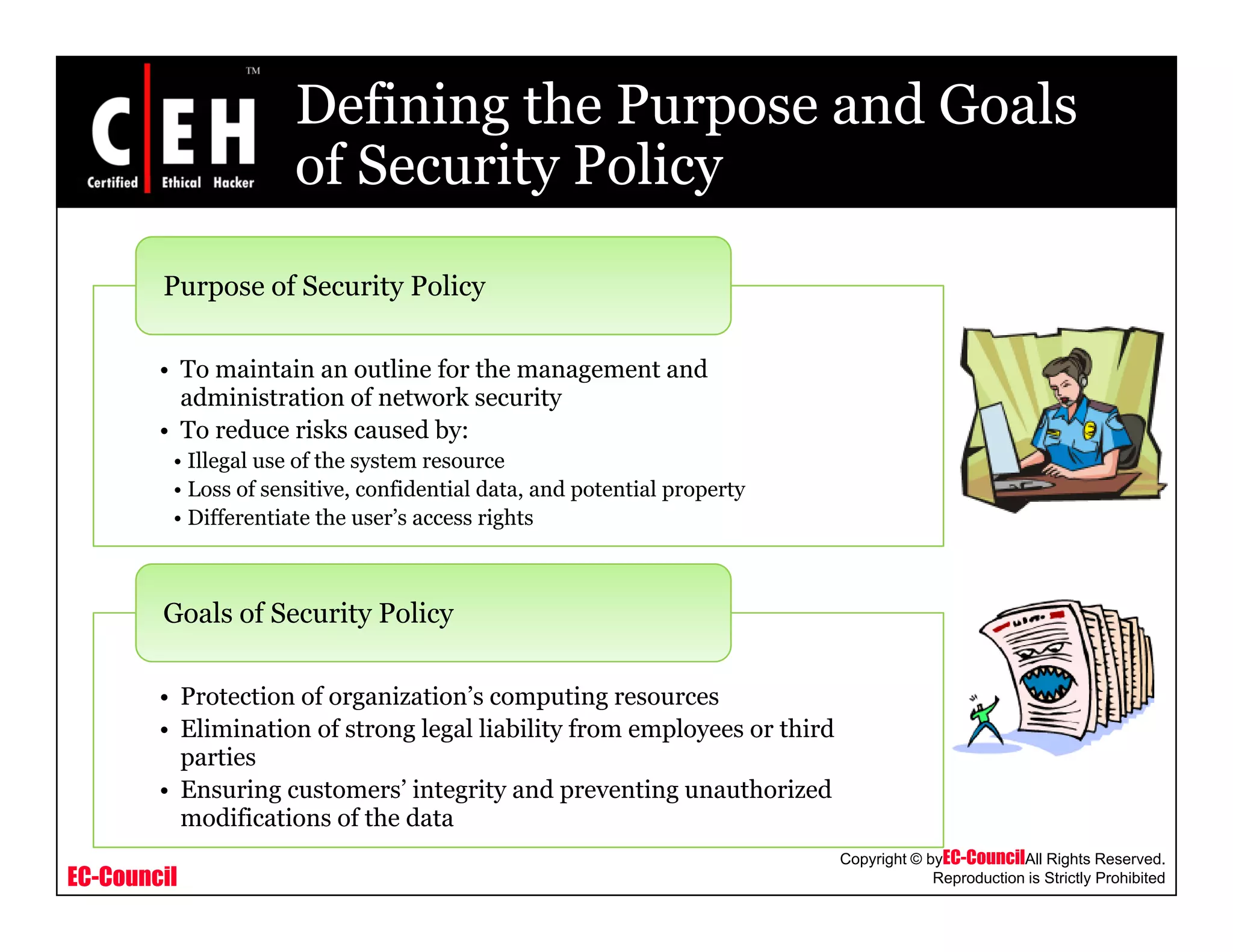
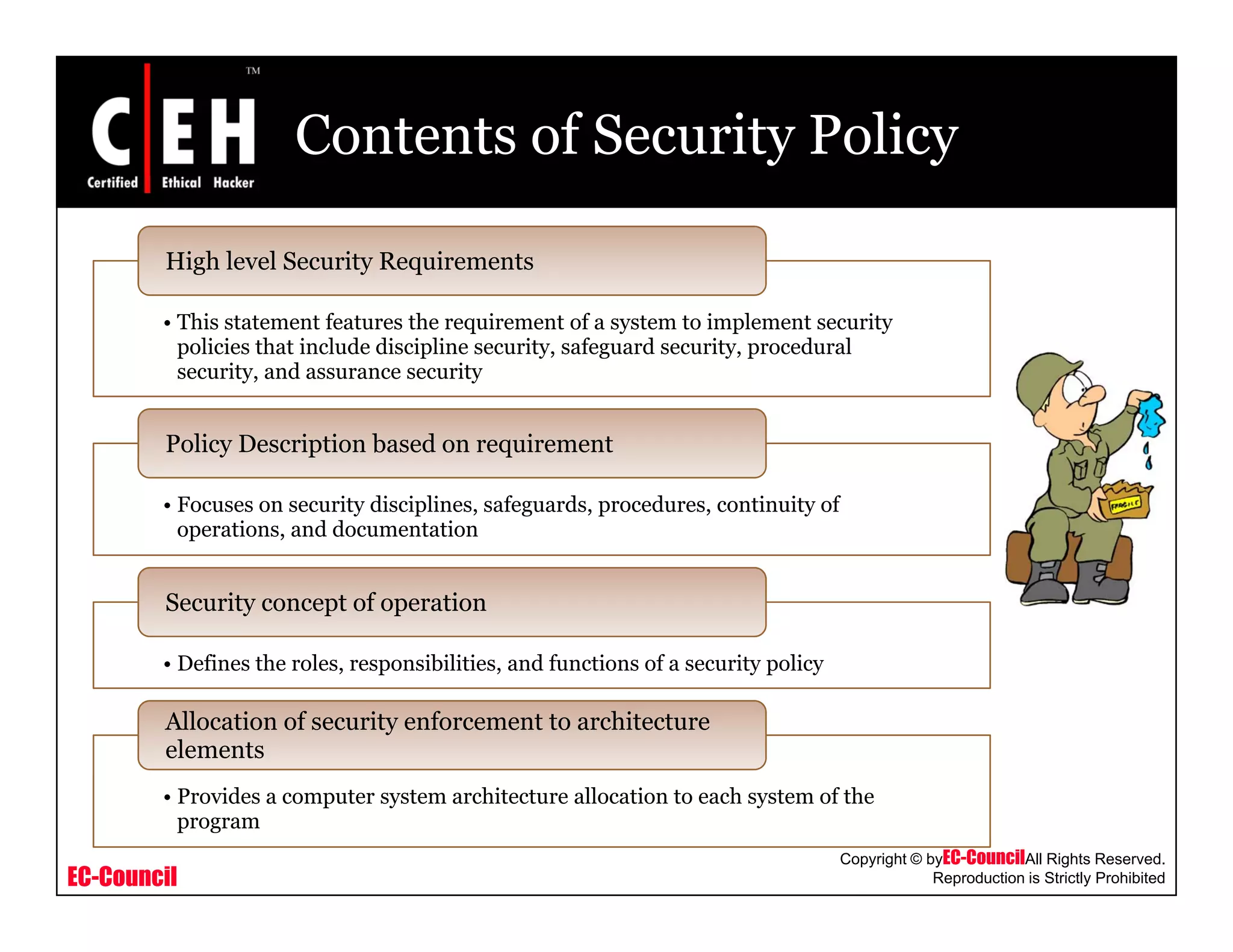
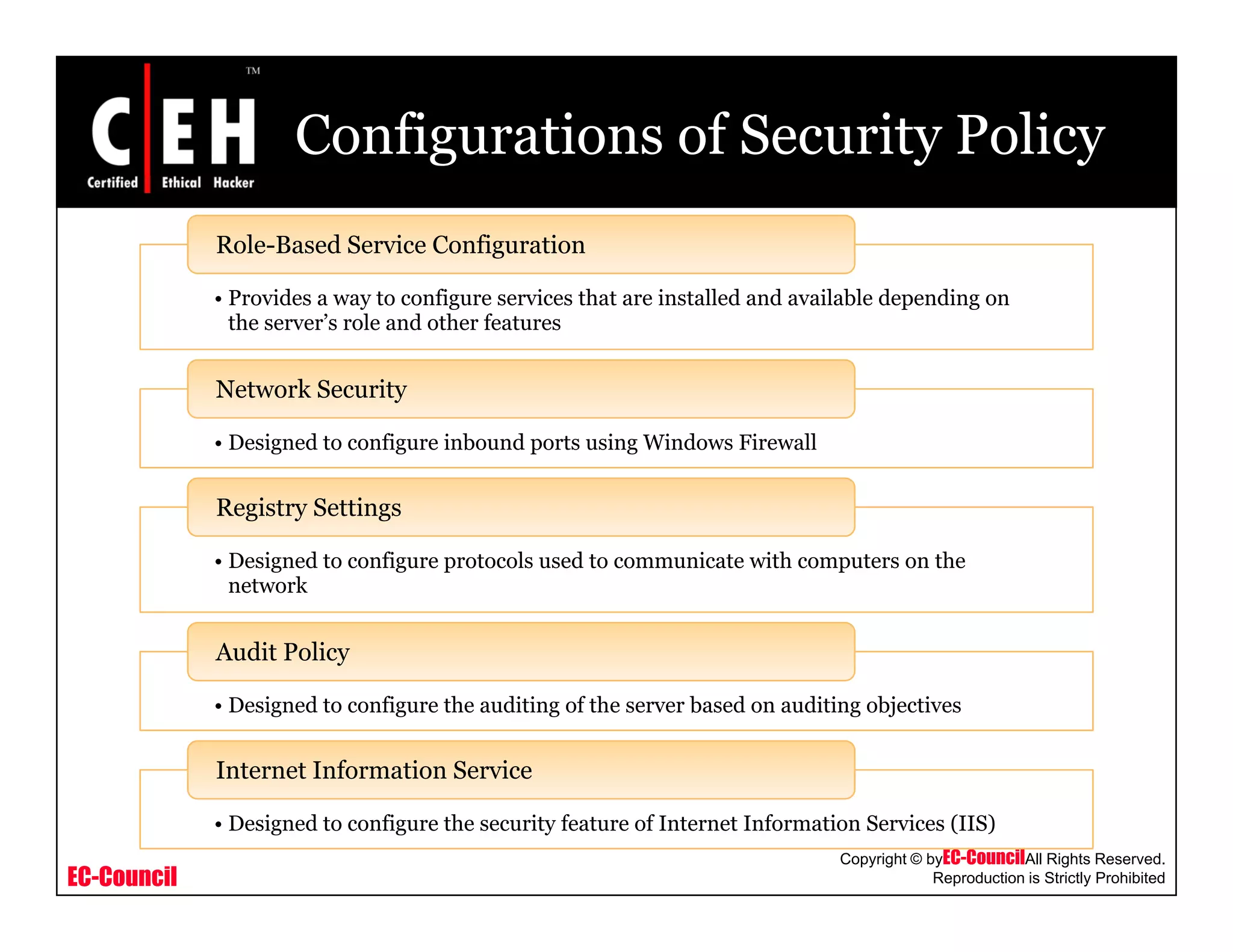
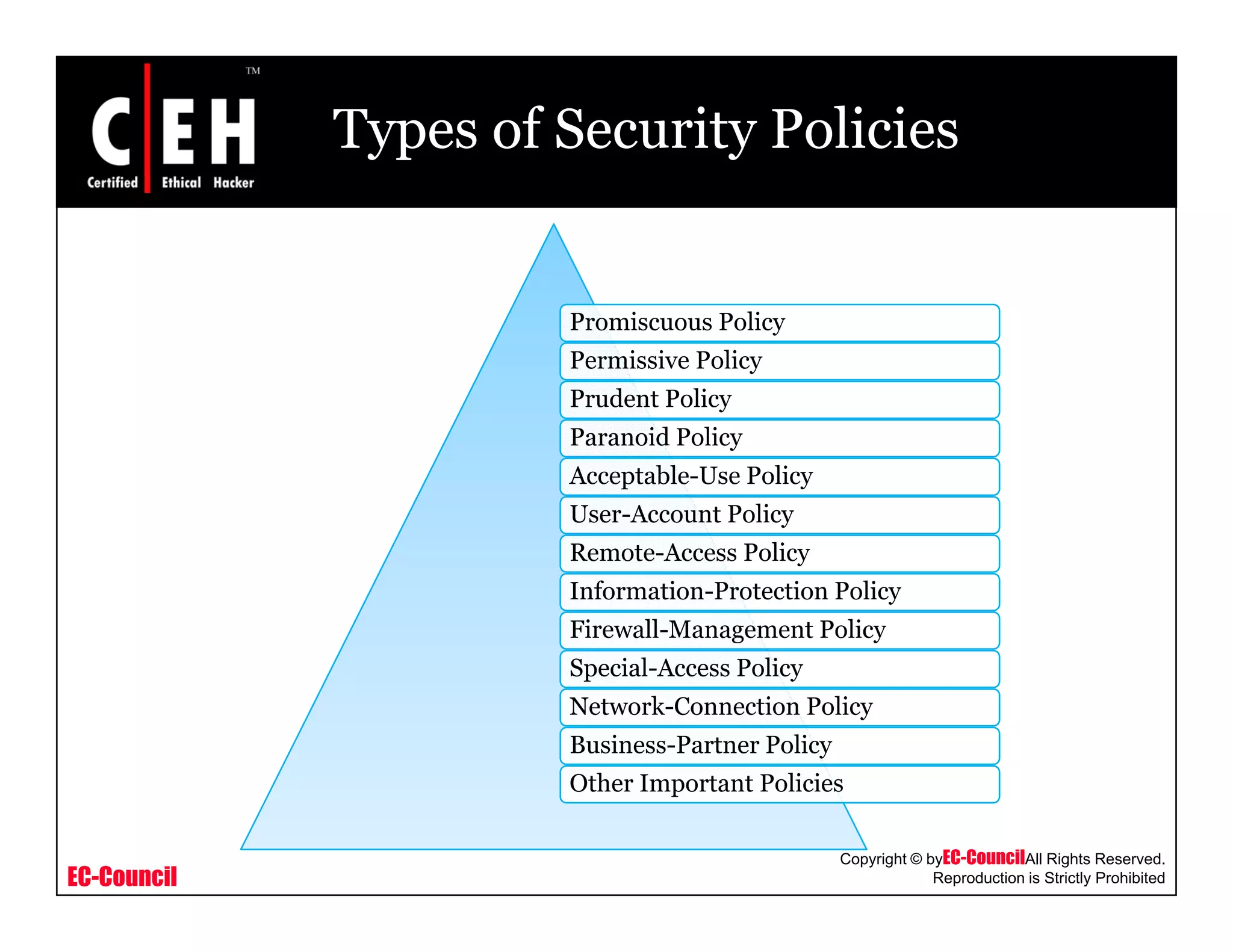
This document provides an overview of security policies, including their key elements, types, and how to implement them. Security policies are foundational documents that describe security controls and reduce legal liability, protect information, and prevent waste. Key elements include clear communication, defined scope, and top management involvement. Types of policies include user policies, IT policies, general policies, and issue-specific policies. Effective implementation requires making the final policy available to all staff and providing security awareness training.












![Business-Partner Policy
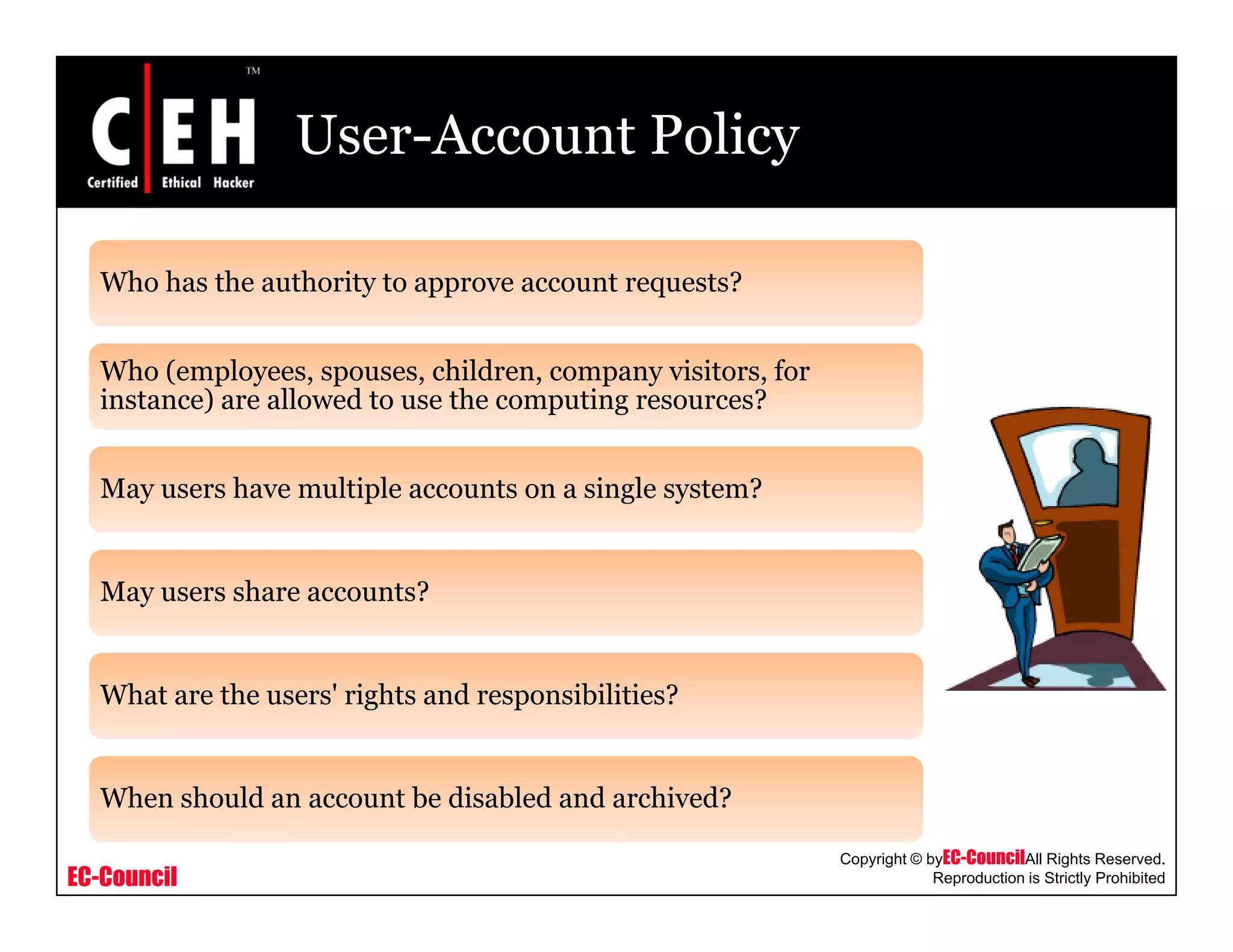
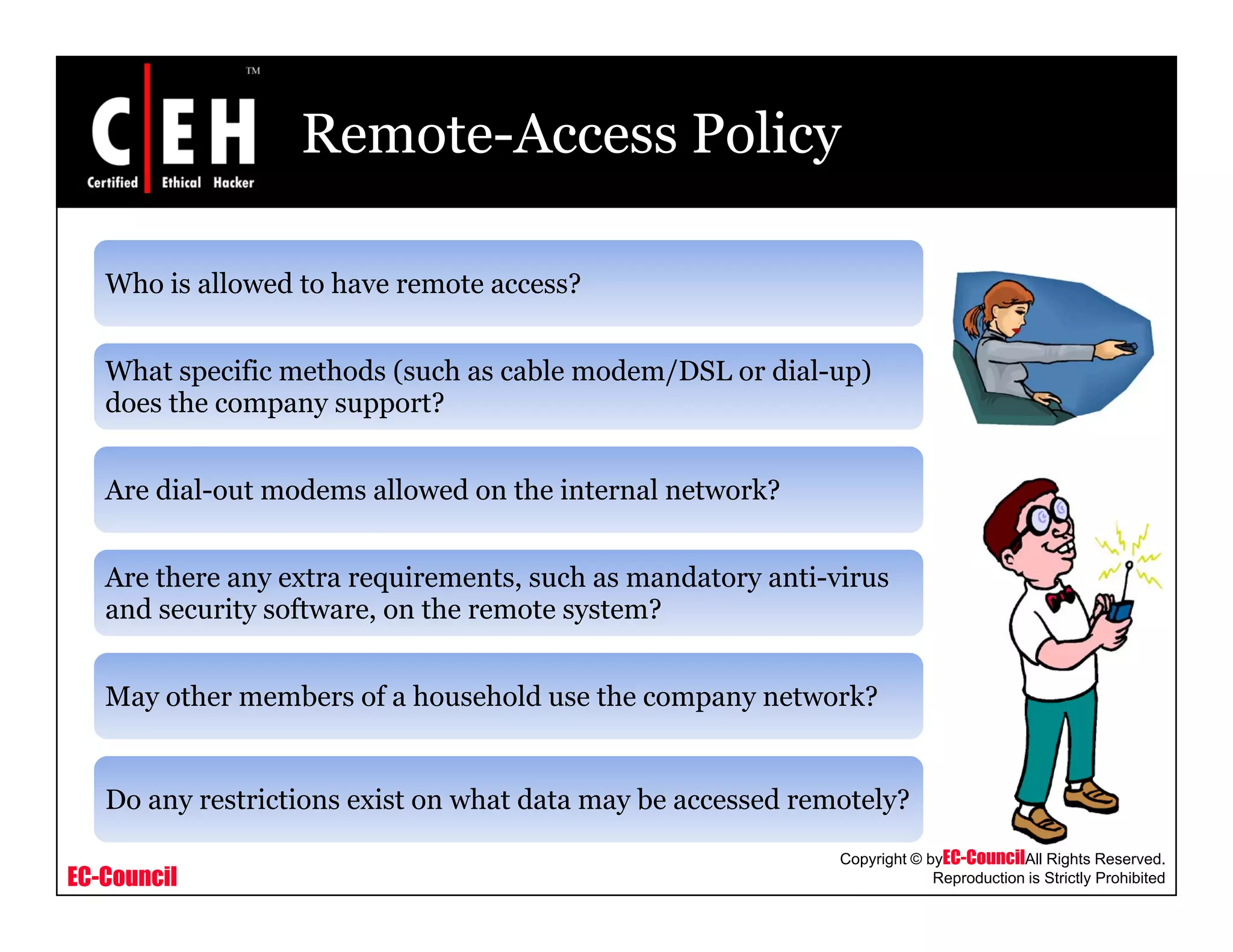
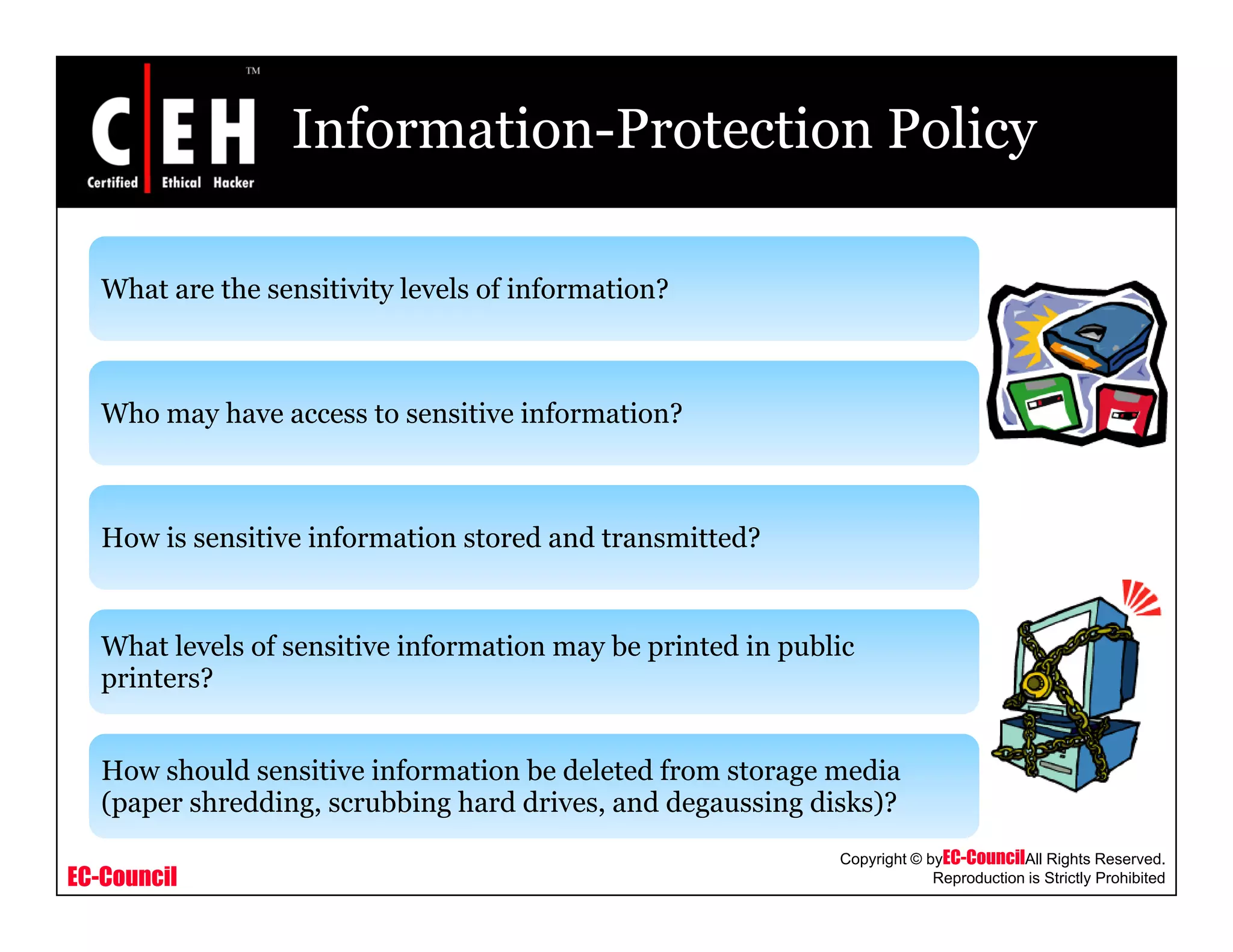
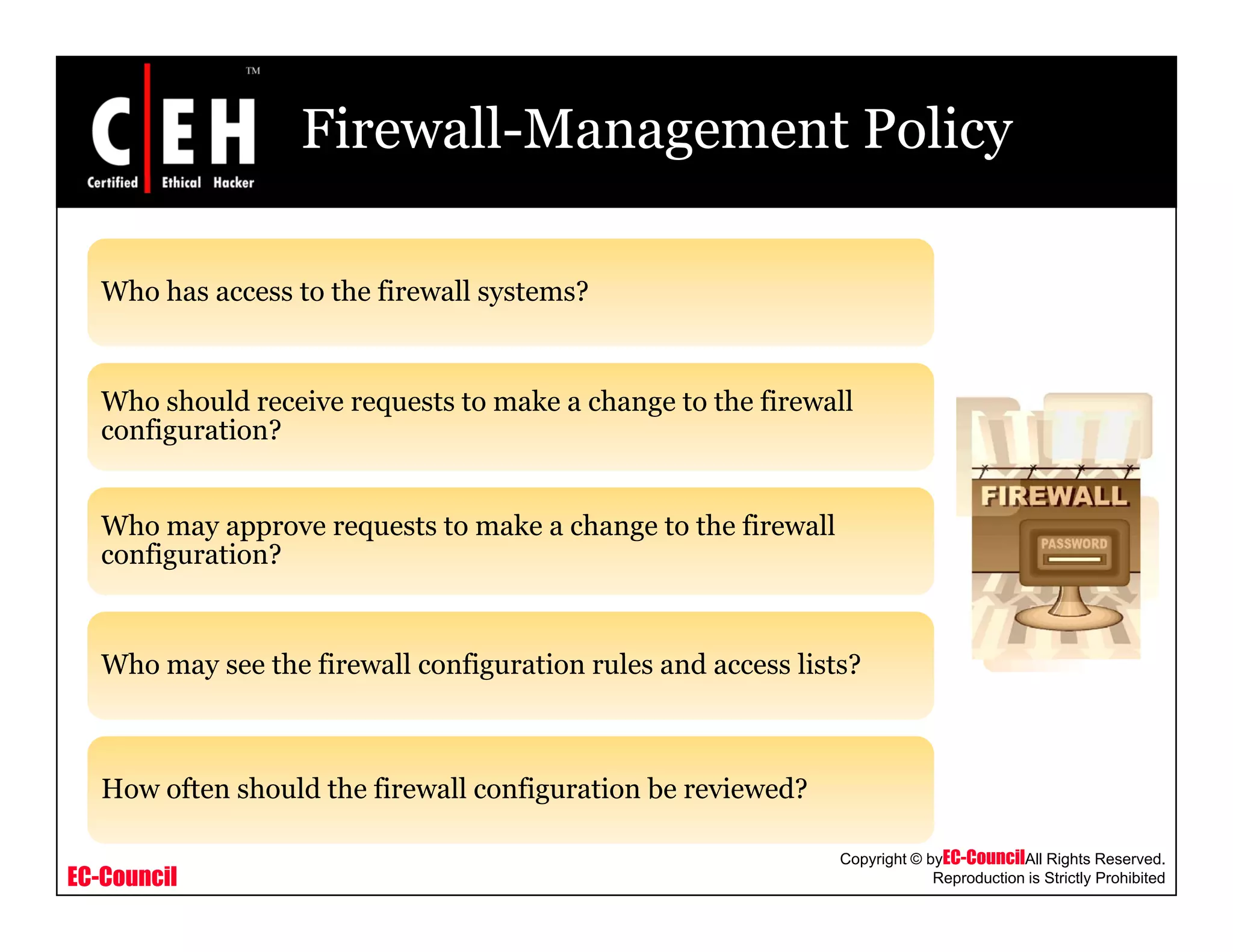
Is it mandatory for a company required toy p y q
have a written security policy?
Should each company have a firewall or other
perimeter security device?
How will one communicate (virtual private
networking [VPN] over the Internet, leased
line, and so forth)?, )
How will access to the partner's resources be
EC-Council
Copyright © byEC-CouncilAll Rights Reserved.
Reproduction is Strictly Prohibited
requested?](https://image.slidesharecdn.com/cehv6module49creatingsecuritypolicies-140722044434-phpapp02/75/Ce-hv6-module-49-creating-security-policies-28-2048.jpg)