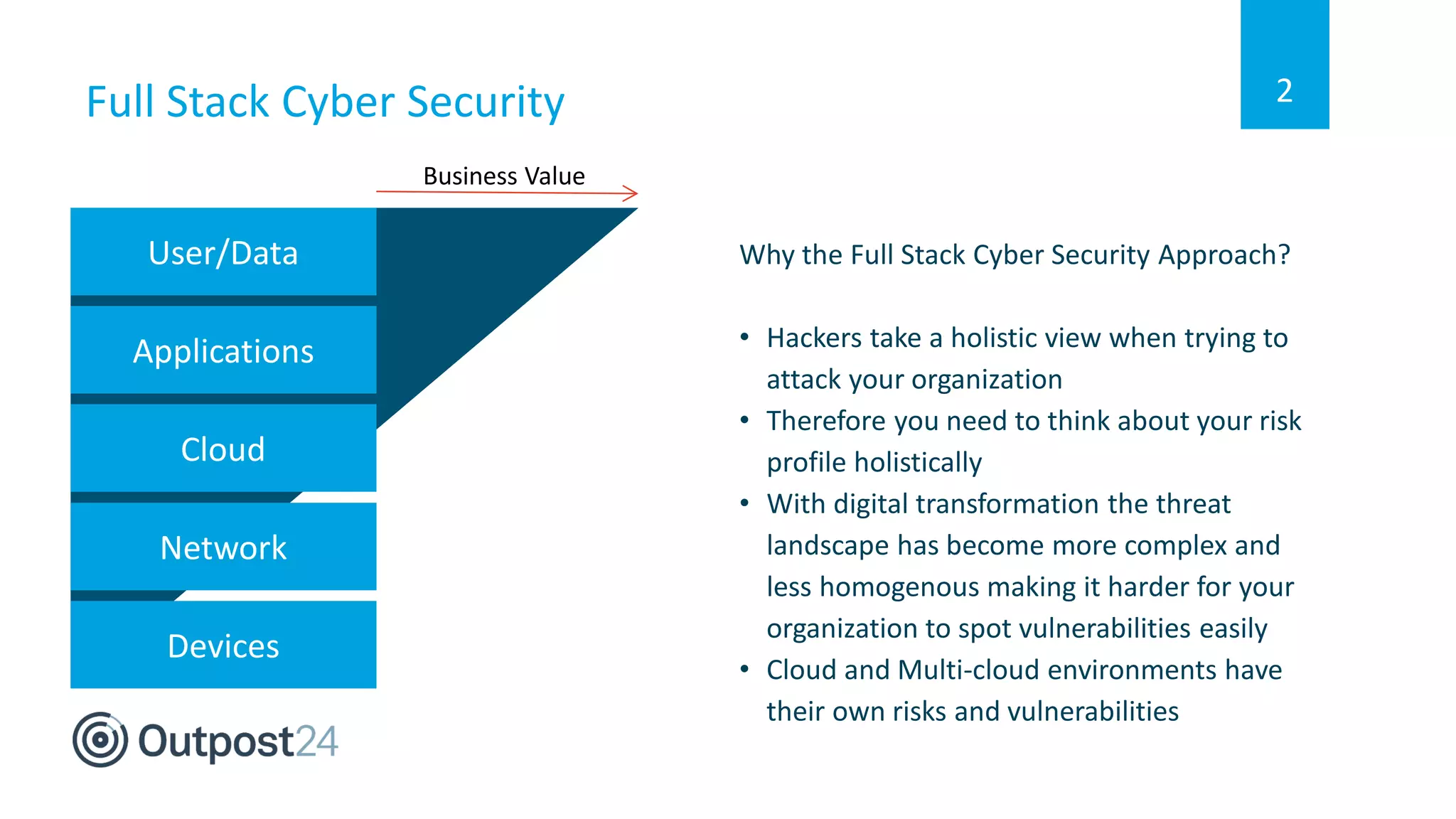
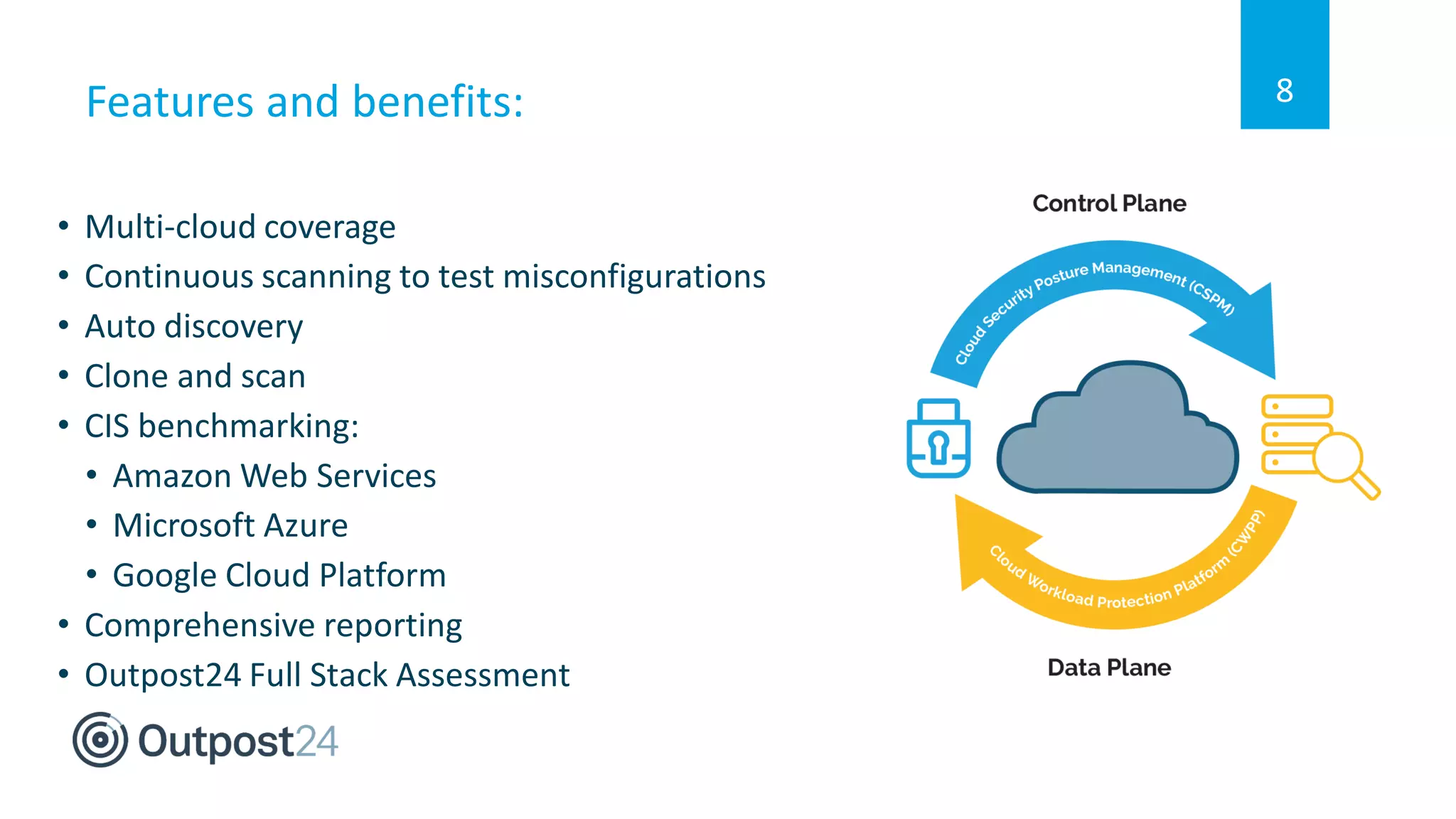
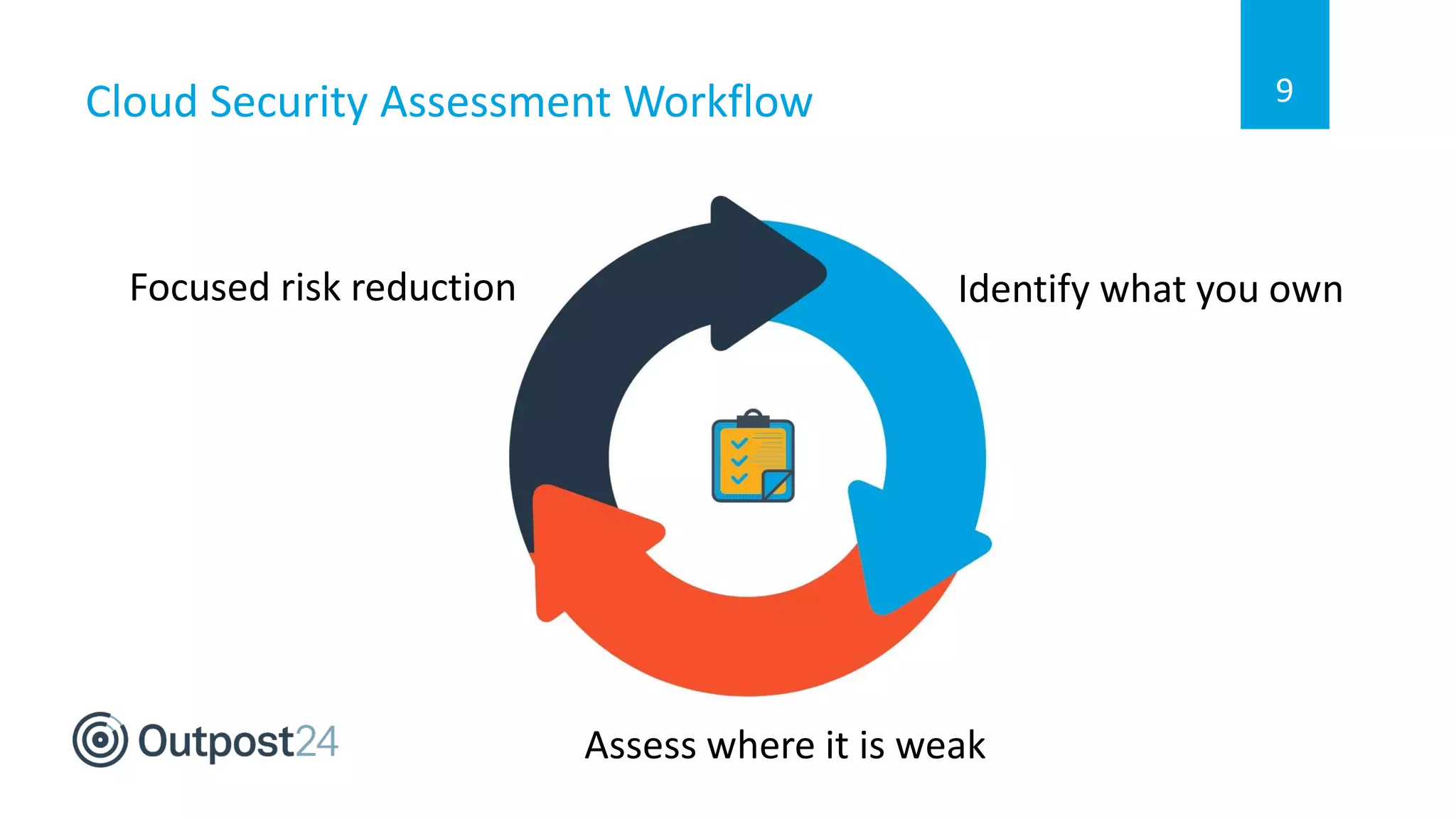
The document discusses the importance of a full stack cyber security approach for multi-cloud environments due to the complex and evolving threat landscape. It emphasizes the need for continuous assessment and protection strategies like Outpost24 CloudSec Inspect to identify vulnerabilities and ensure security compliance across various platforms such as AWS, Azure, and Google Cloud. Key features include automated risk assessment, cloud configuration awareness, and actionable insights to enhance cloud security workflows.