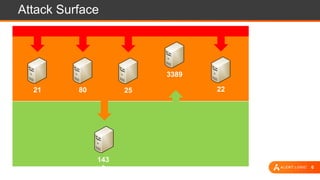
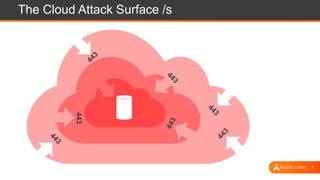
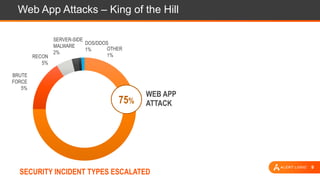
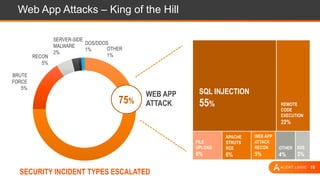
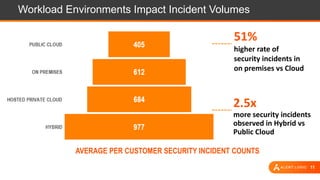
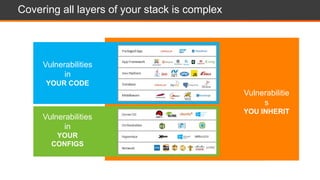
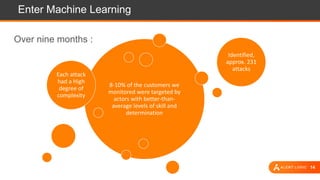
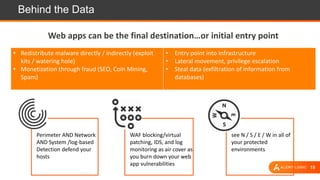
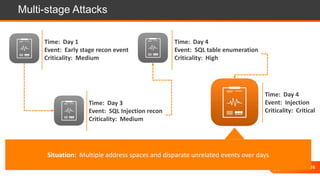
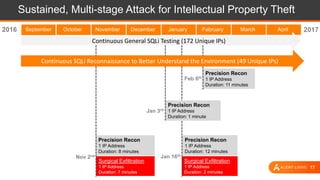
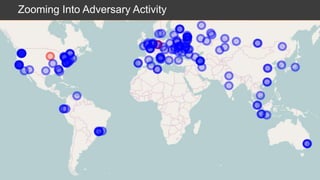
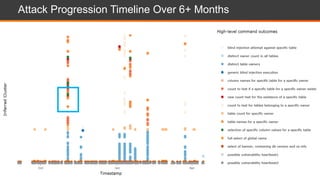
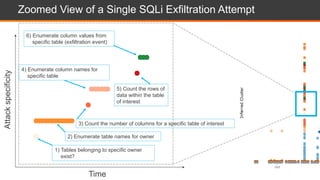
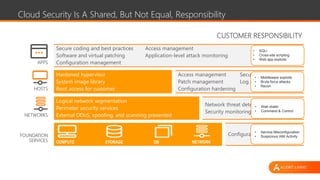
The document presents an overview of cloud security challenges, emphasizing the complex and evolving nature of cyberattacks. It highlights the increased attack surface due to cloud adoption, noting that hybrid environments face 2.5 times more security incidents than public clouds. Additionally, it discusses the significance of proactive security measures and the shared responsibility model in addressing vulnerabilities and protecting data.