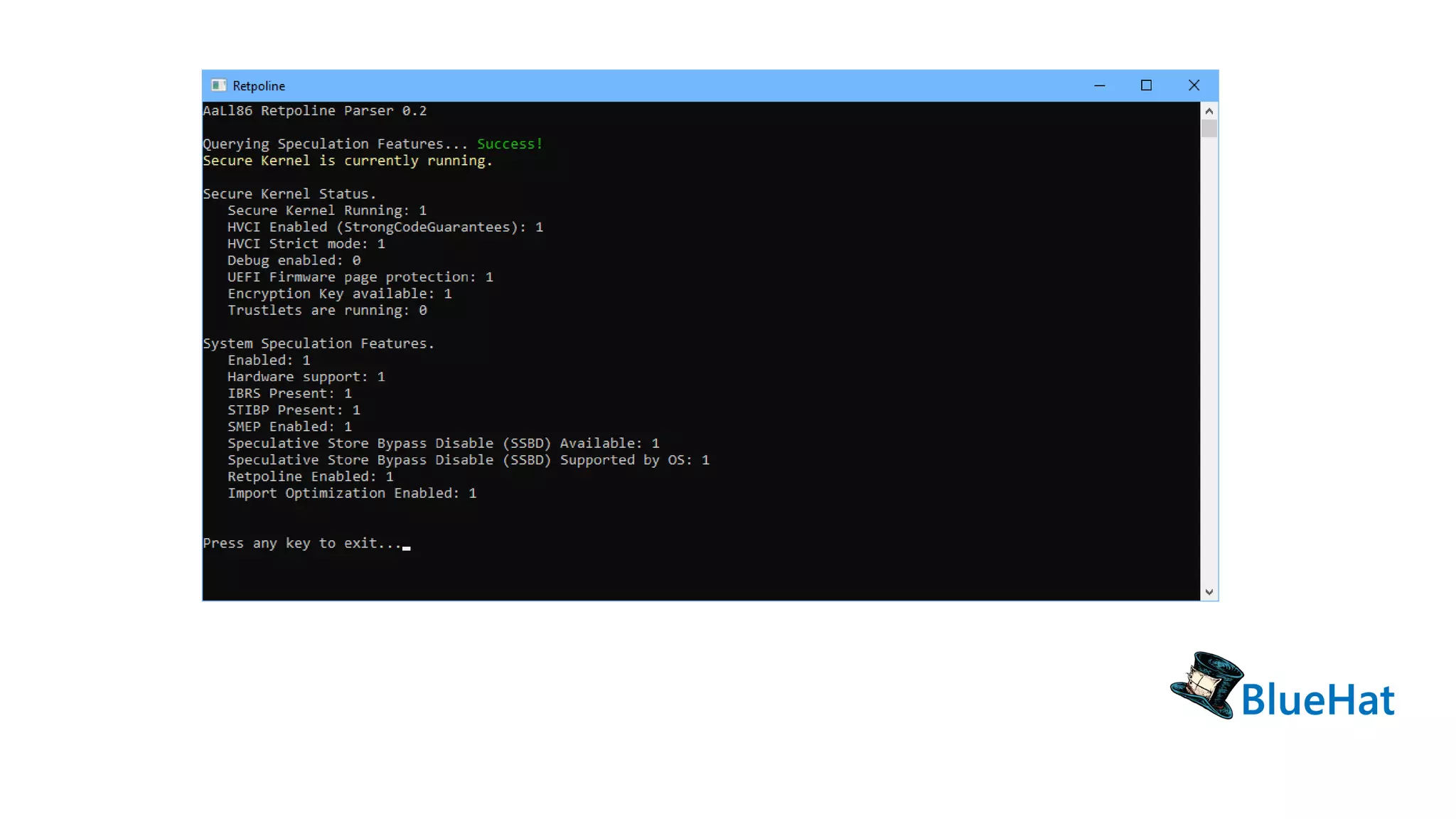
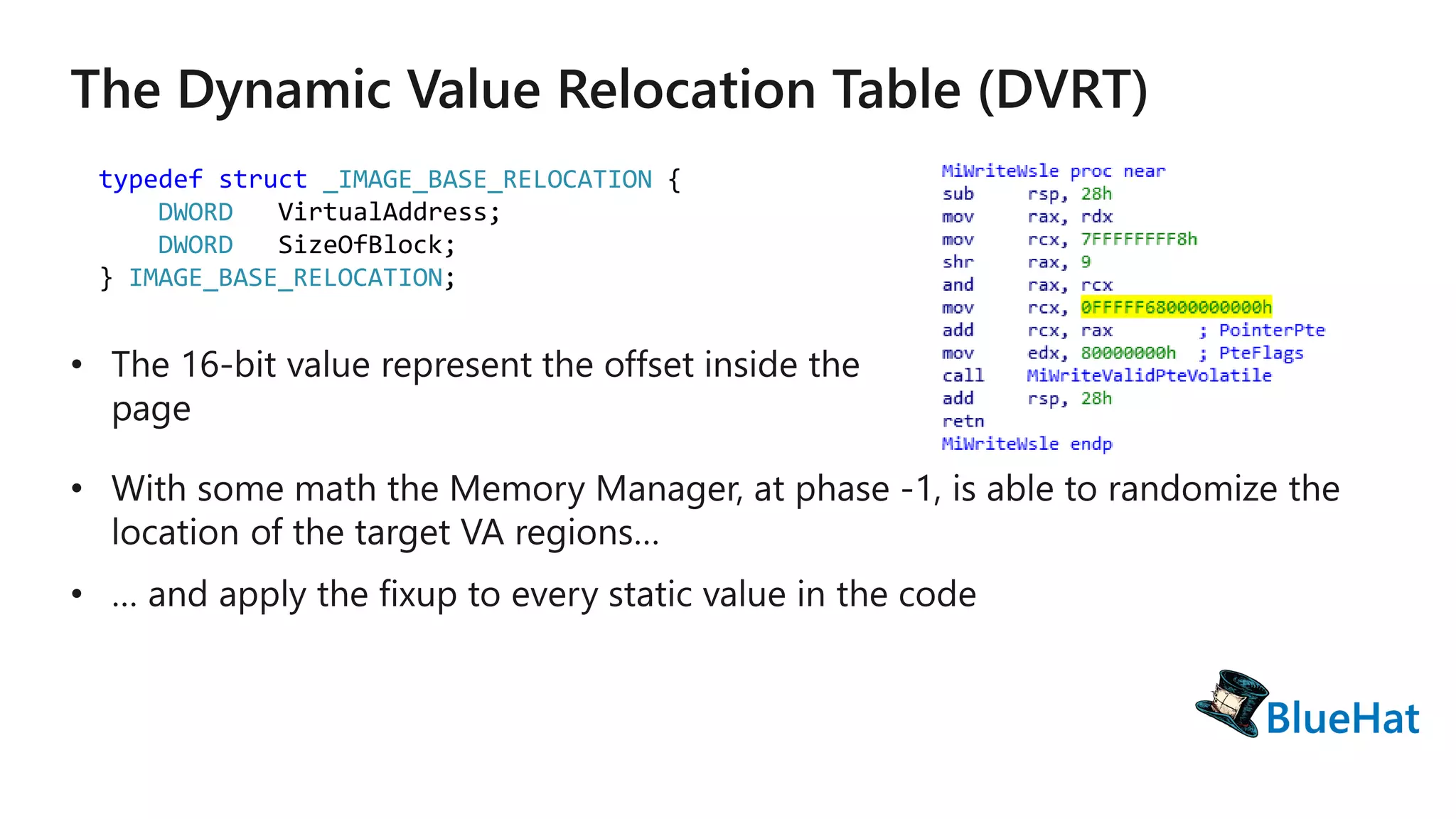
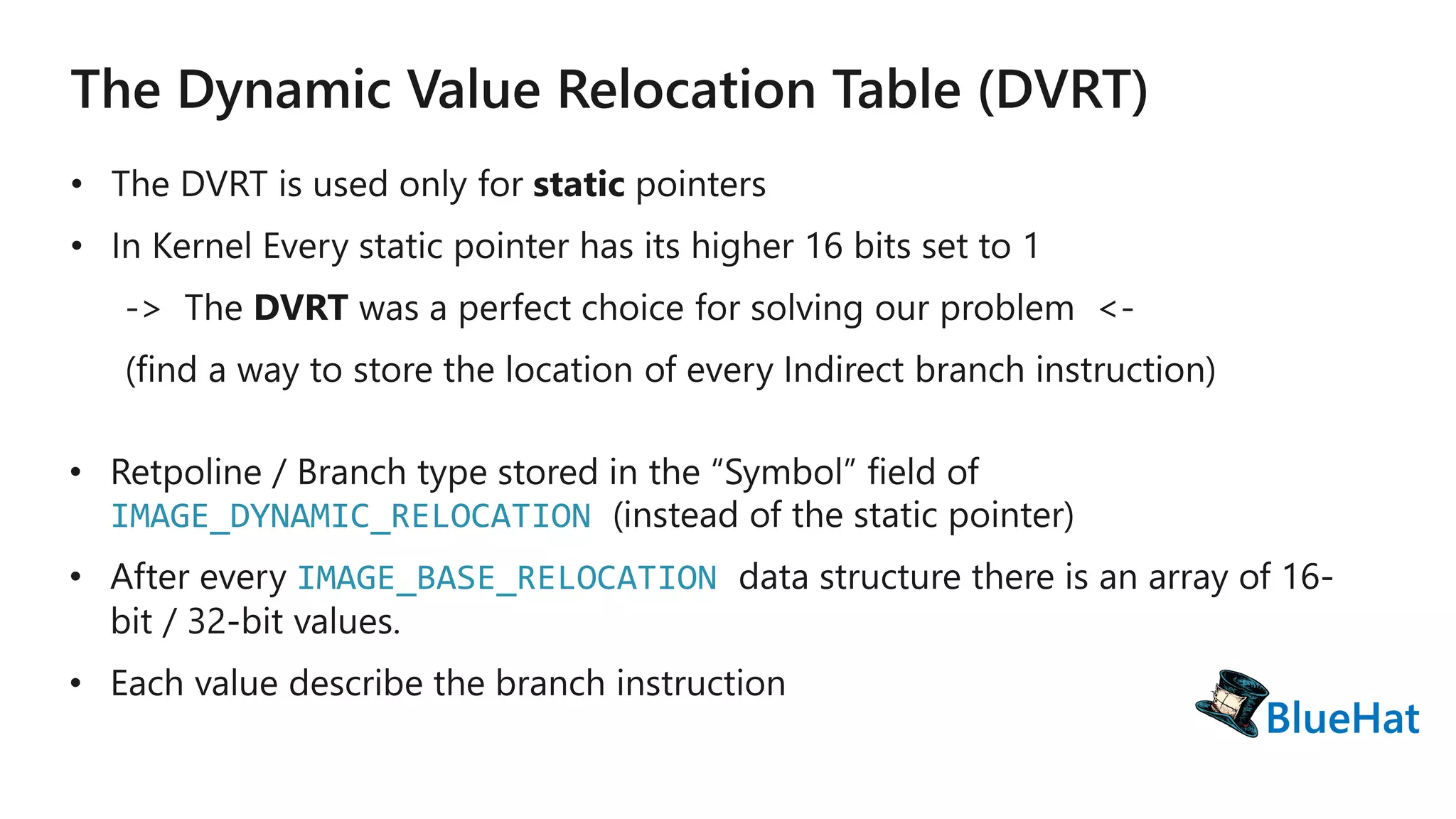
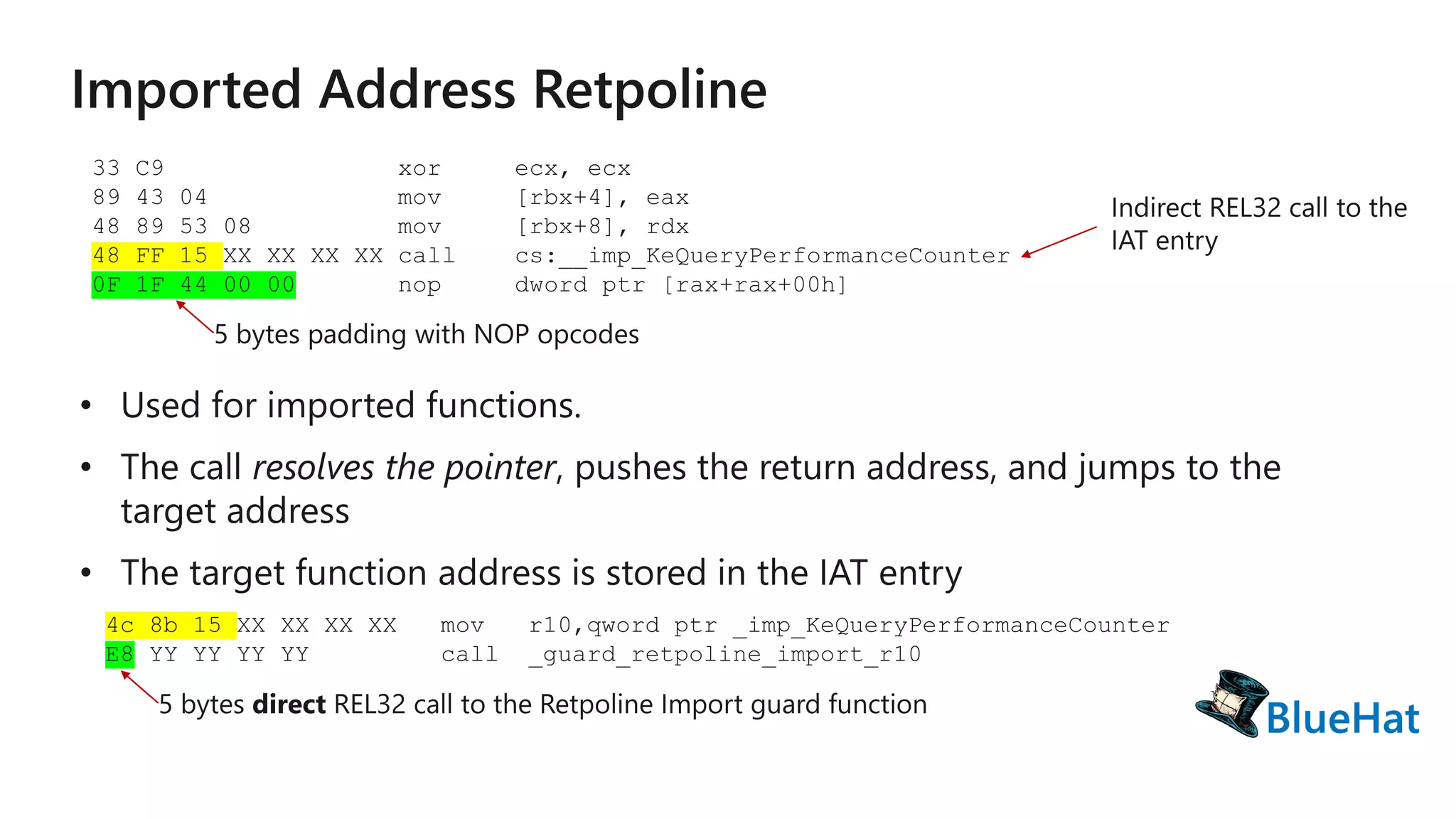
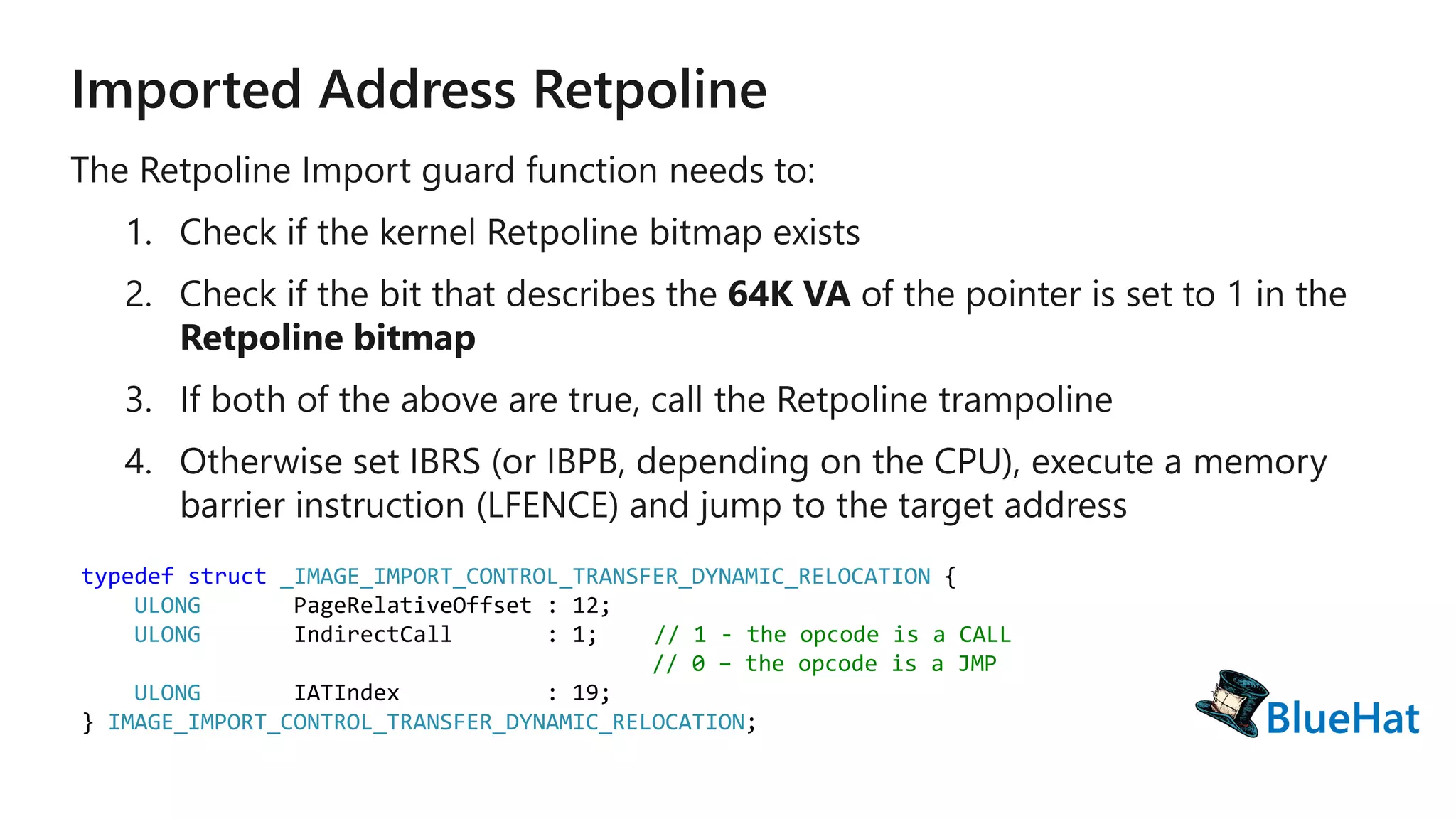
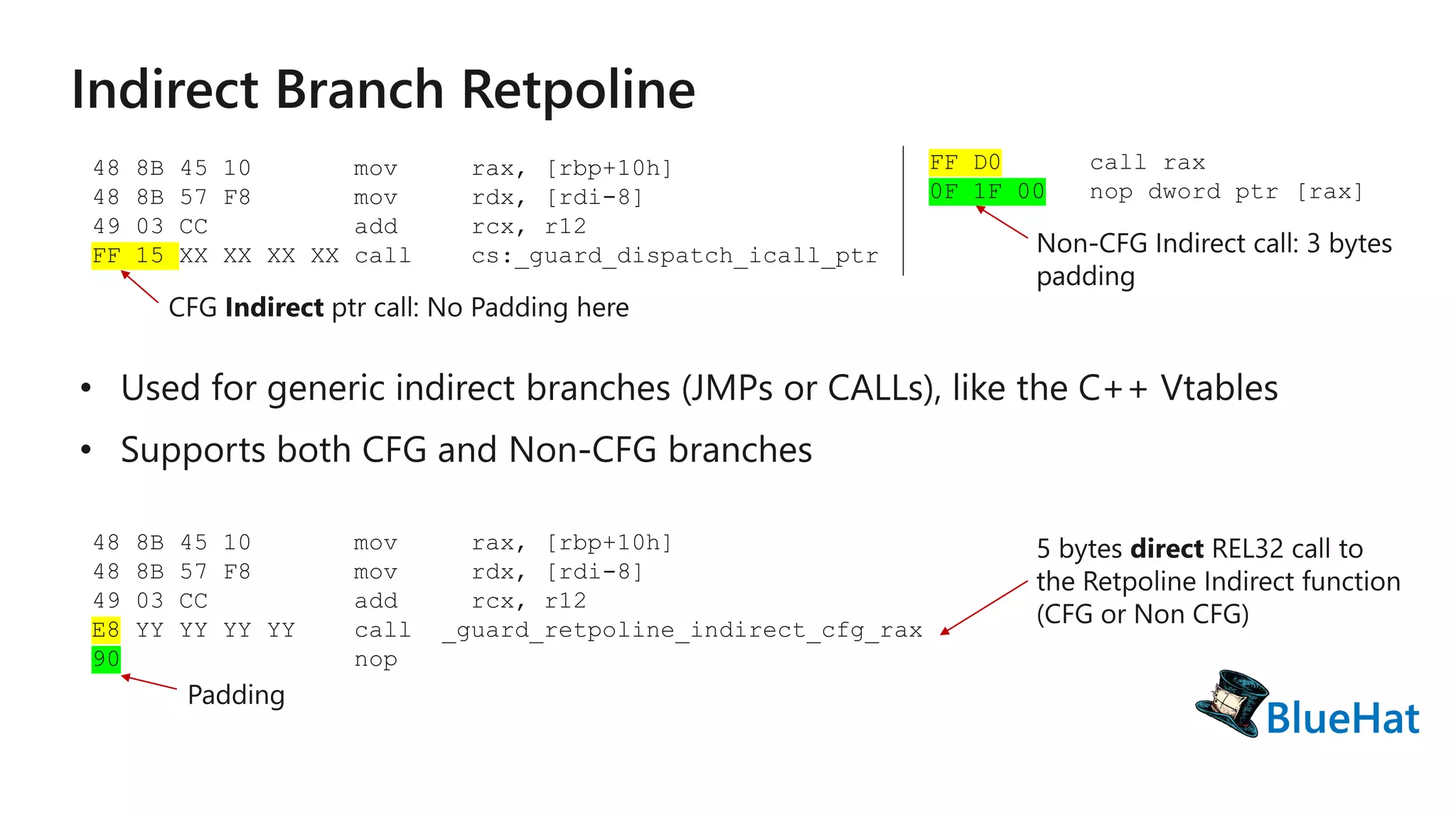
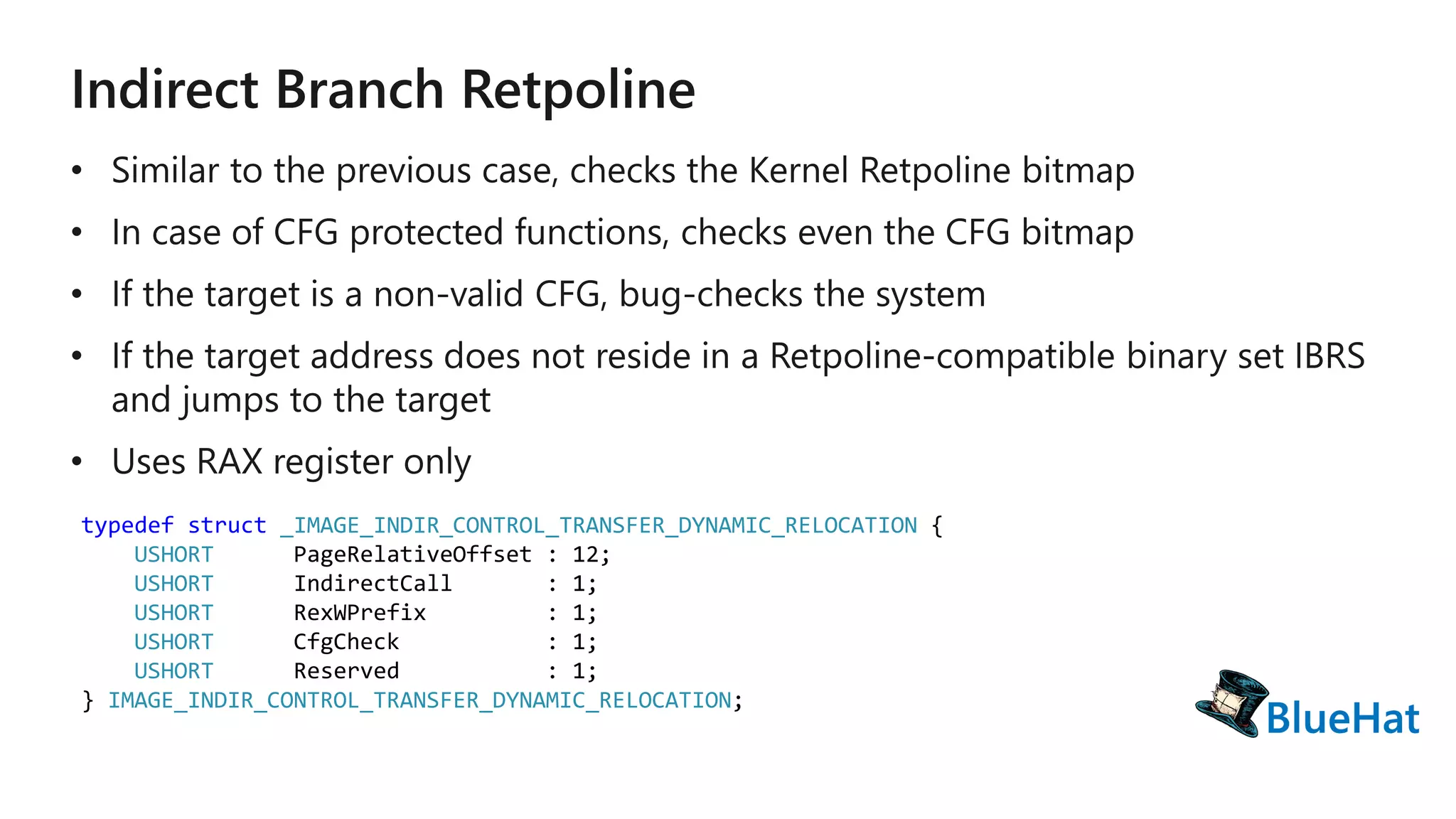
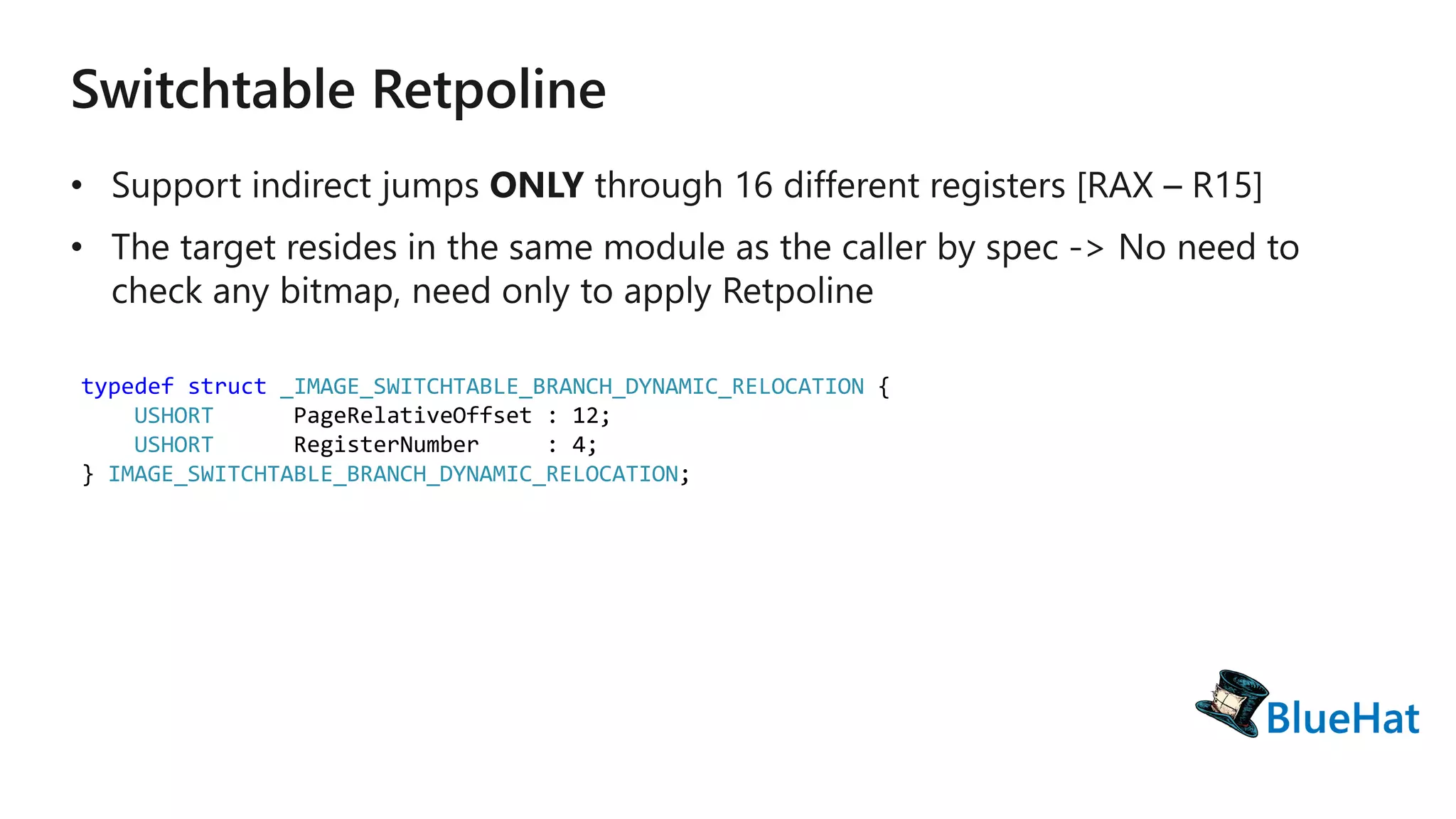
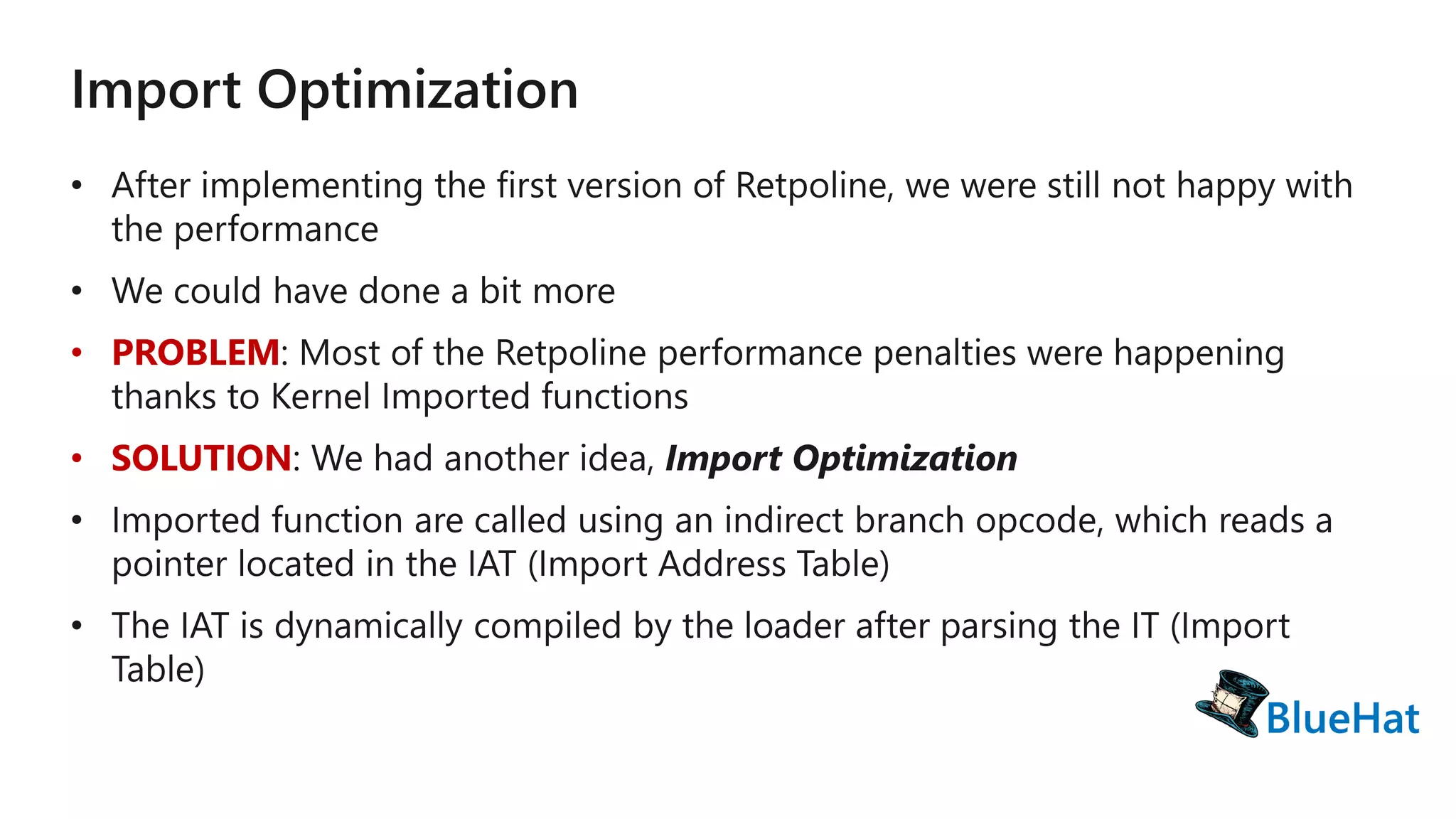
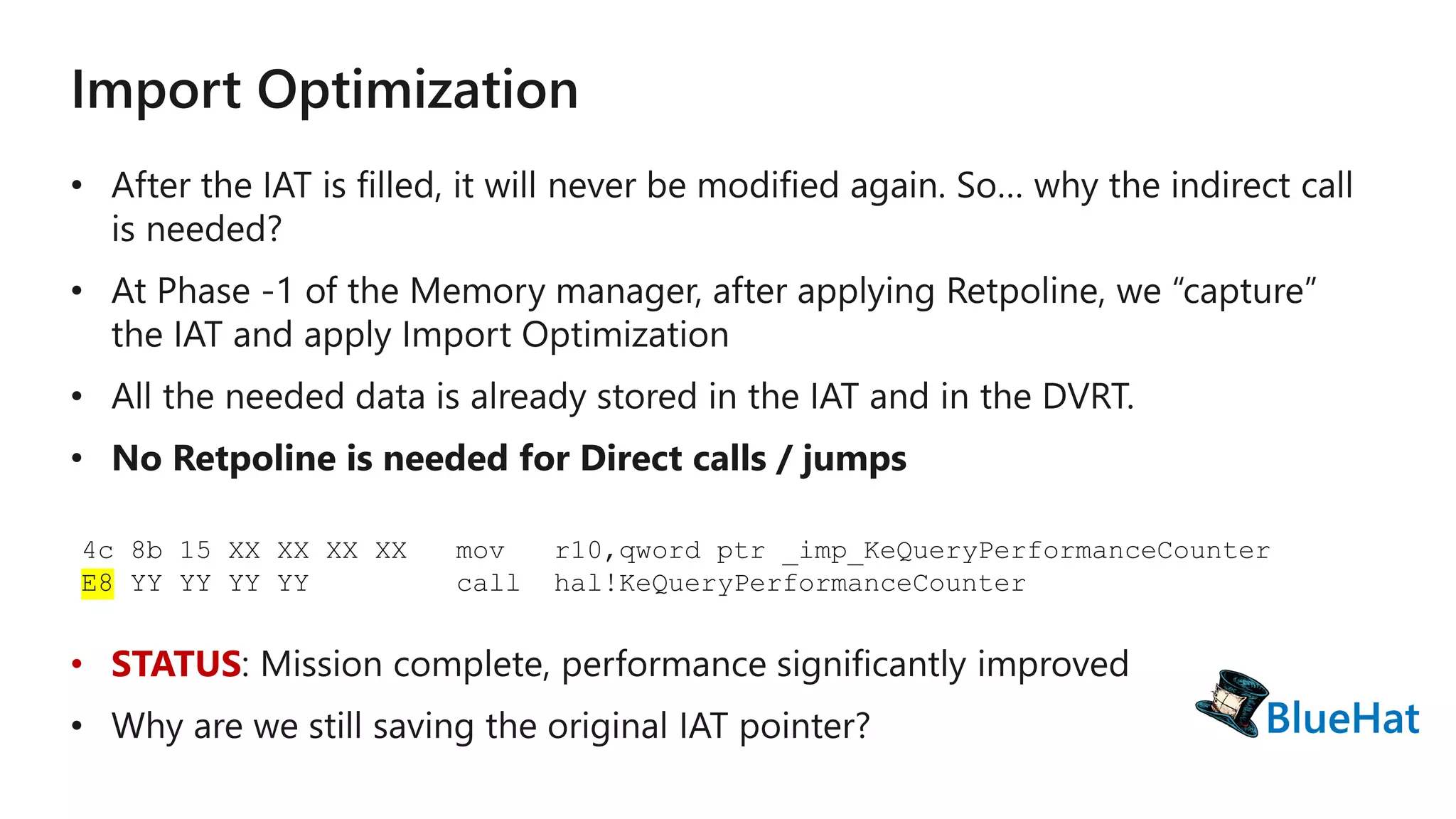
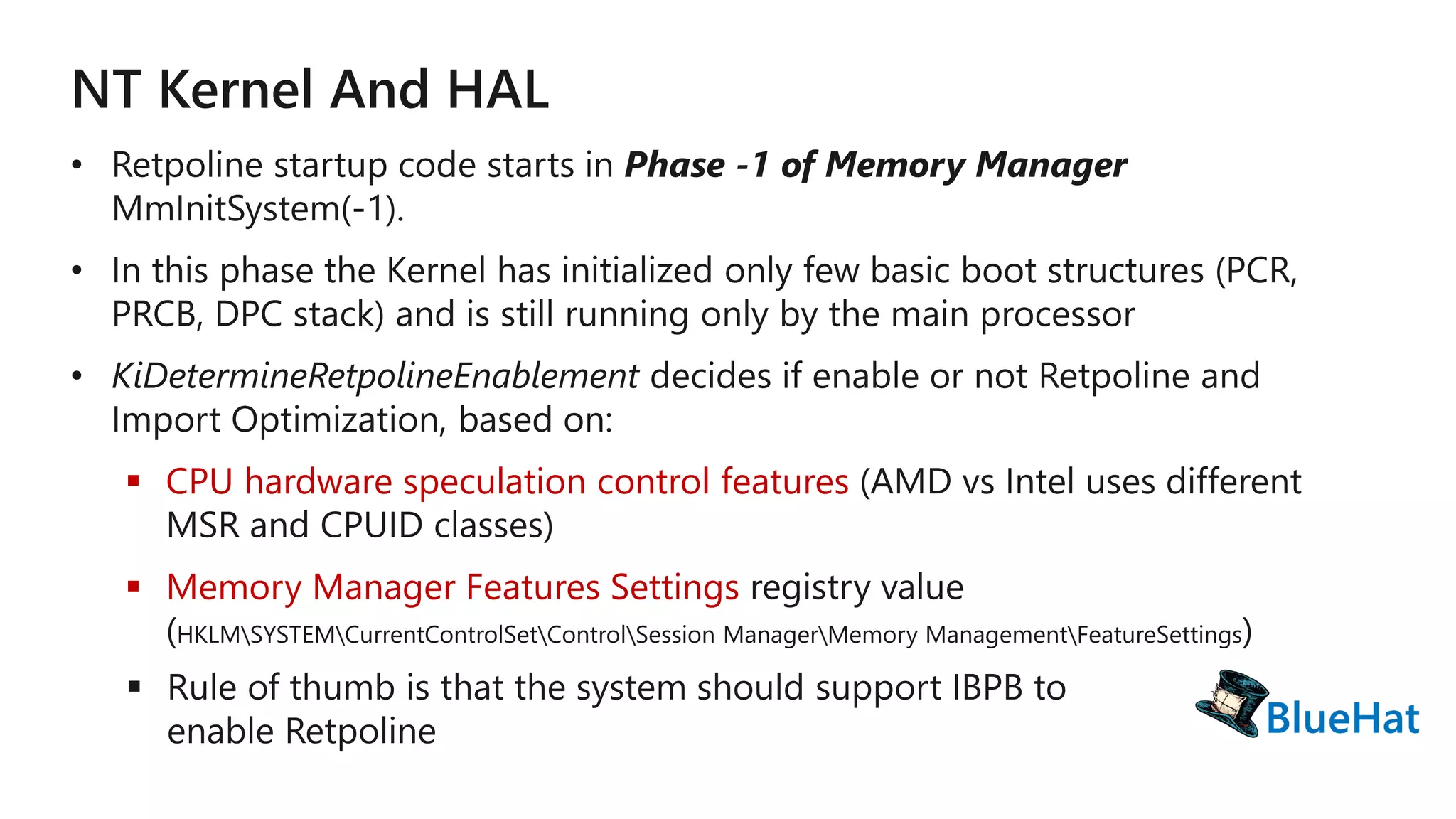
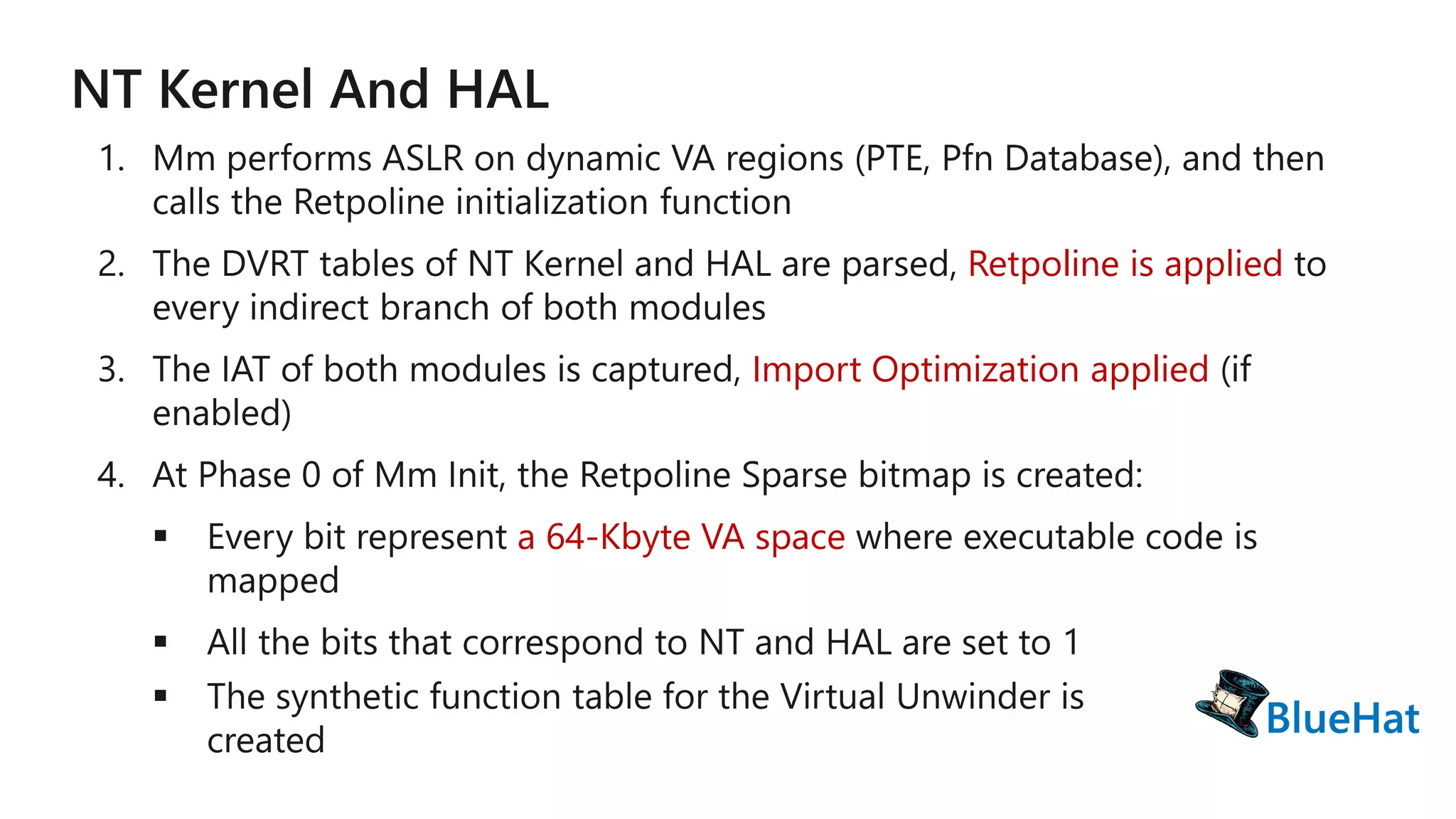
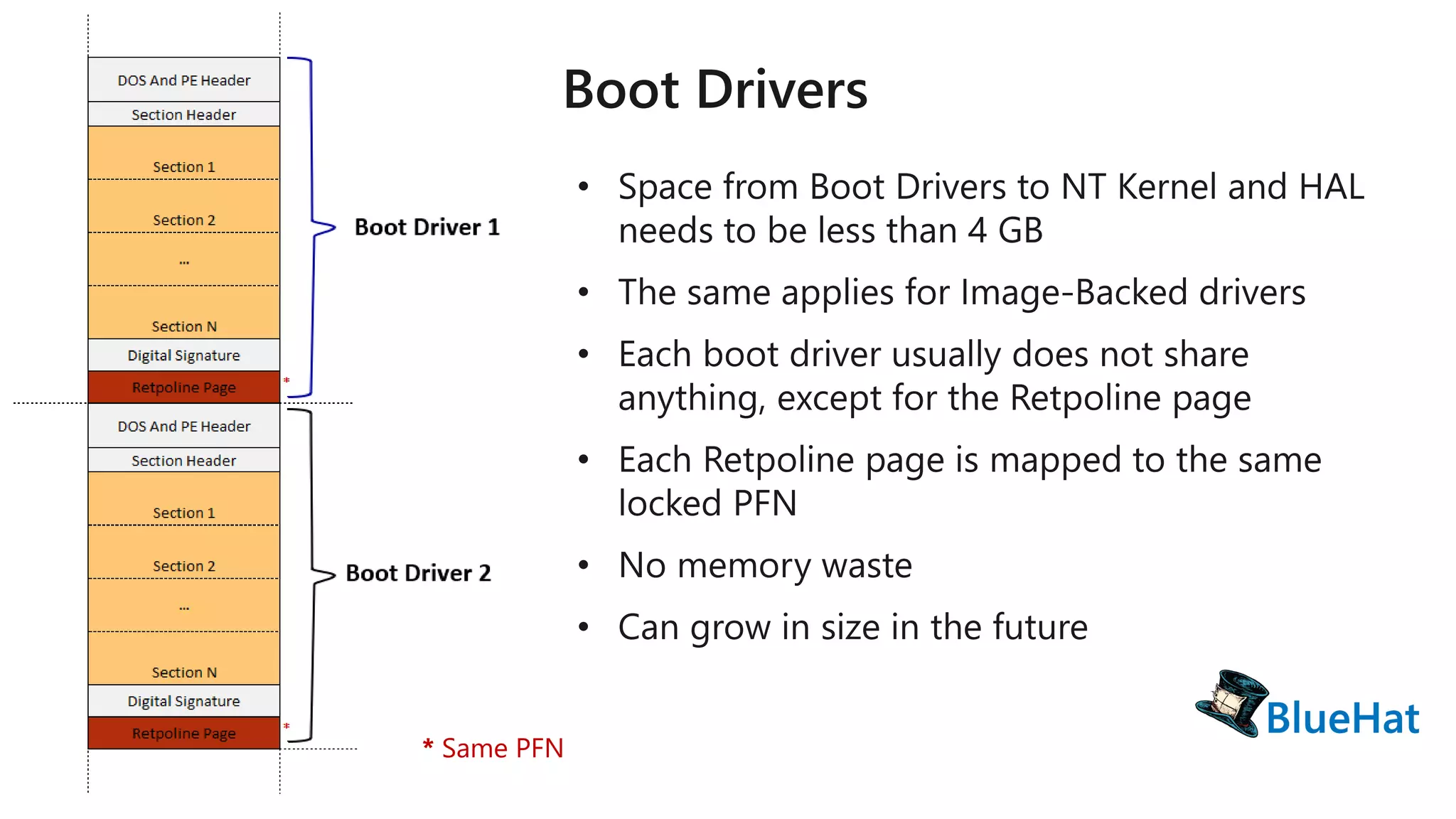
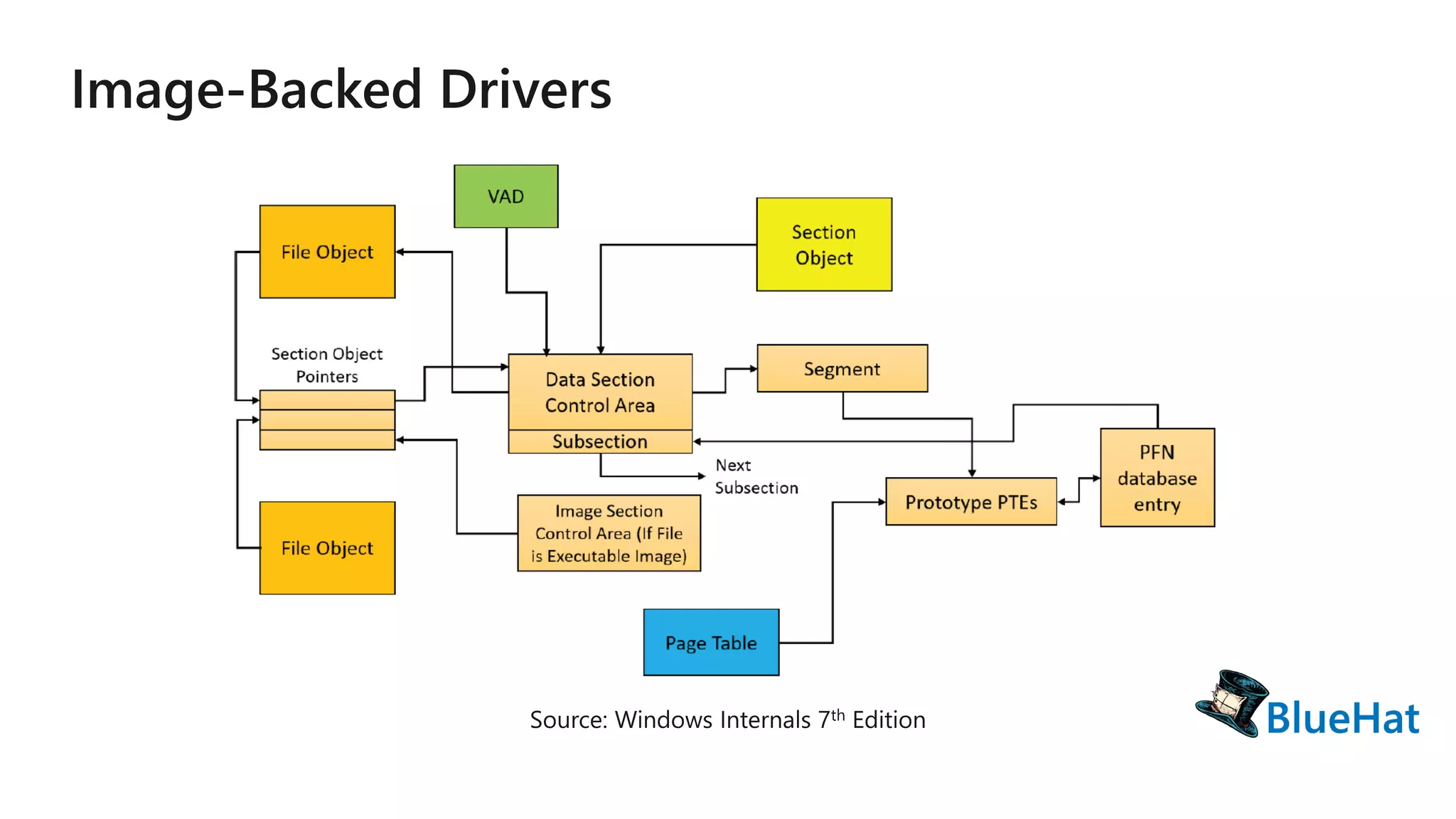
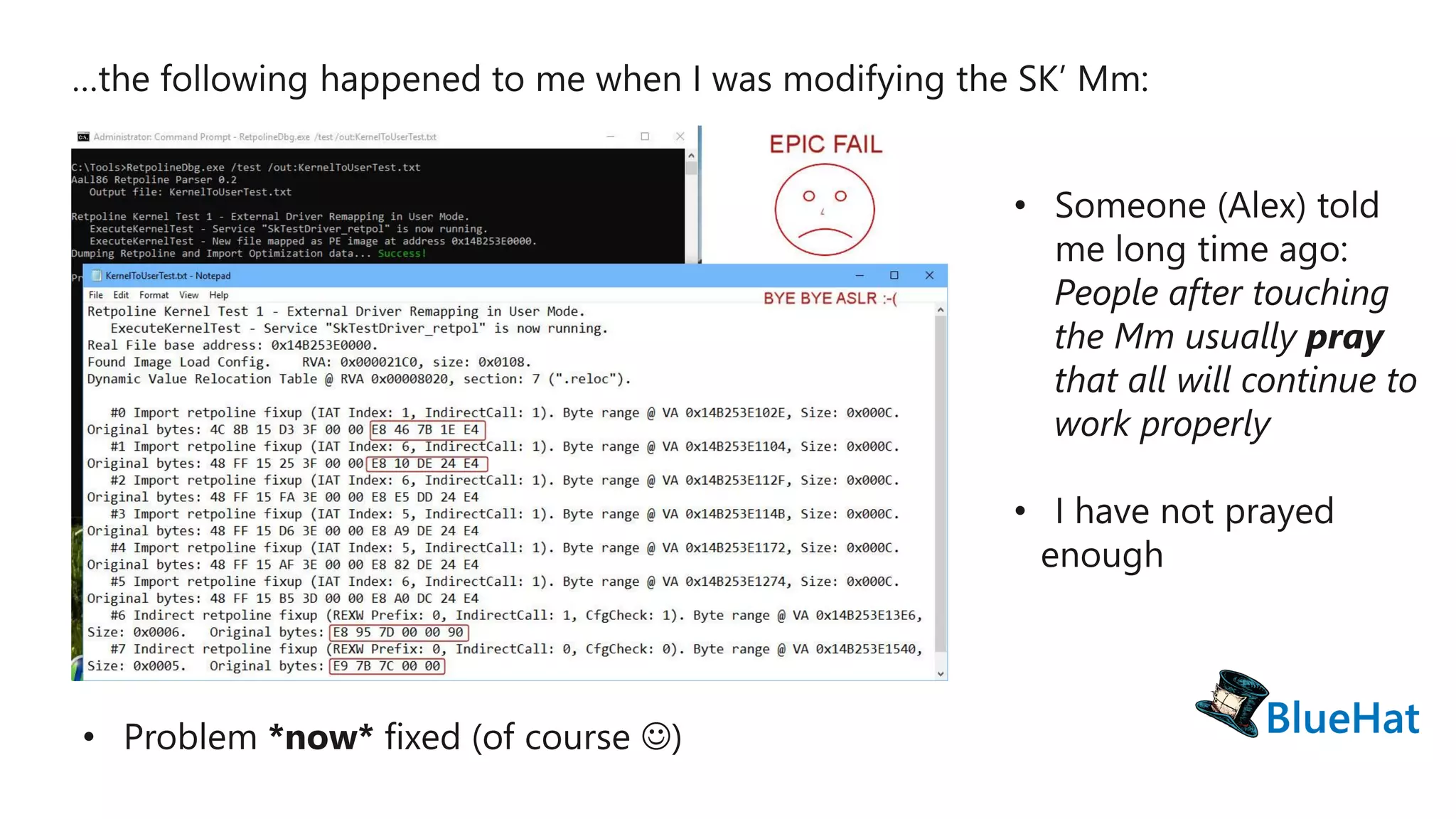
The document discusses various structures and processes related to CPU hardware speculation control, including different types of dynamic relocation structures. It also addresses issues and solutions for managing speculative execution vulnerabilities, specifically through the use of retpoline and import optimization. The document further provides insight into querying system information for speculation control settings.







![IMAGE_DYNAMIC_RELOCATION
typedef struct _IMAGE_DYNAMIC_RELOCATION {
ULONGLONG Symbol; // Contains the static symbol (PTR) value
DWORD BaseRelocSize;
// IMAGE_BASE_RELOCATION BaseRelocations[0];
} IMAGE_DYNAMIC_RELOCATION;
IMAGE_BASE_RELOCATION](https://image.slidesharecdn.com/0927-track2-am-retpoline-theanti-spectretype2mitigationinwindows-181012163929/75/BlueHat-v18-Retpoline-the-anti-spectre-type-2-mitigation-in-windows-13-2048.jpg)





![// From SYSTEM_INFORMATION_CLASS enumeration
#define SystemSpeculationControlInformation 201
typedef struct _SYSTEM_SPECULATION_CONTROL_INFORMATION {
// ...
ULONG SpecCtrlRetpolineEnabled : 1; // [13]
ULONG SpecCtrlImportOptimizationEnabled : 1; // [14]
} SYSTEM_SPECULATION_CONTROL_INFORMATION;
NtStatus = ZwQuerySystemInformation(SystemSpeculationControlInformation, (PVOID)&SpecCtrl,
sizeof(SYSTEM_SPECULATION_CONTROL_INFORMATION), &dwBytesIo);](https://image.slidesharecdn.com/0927-track2-am-retpoline-theanti-spectretype2mitigationinwindows-181012163929/75/BlueHat-v18-Retpoline-the-anti-spectre-type-2-mitigation-in-windows-37-2048.jpg)