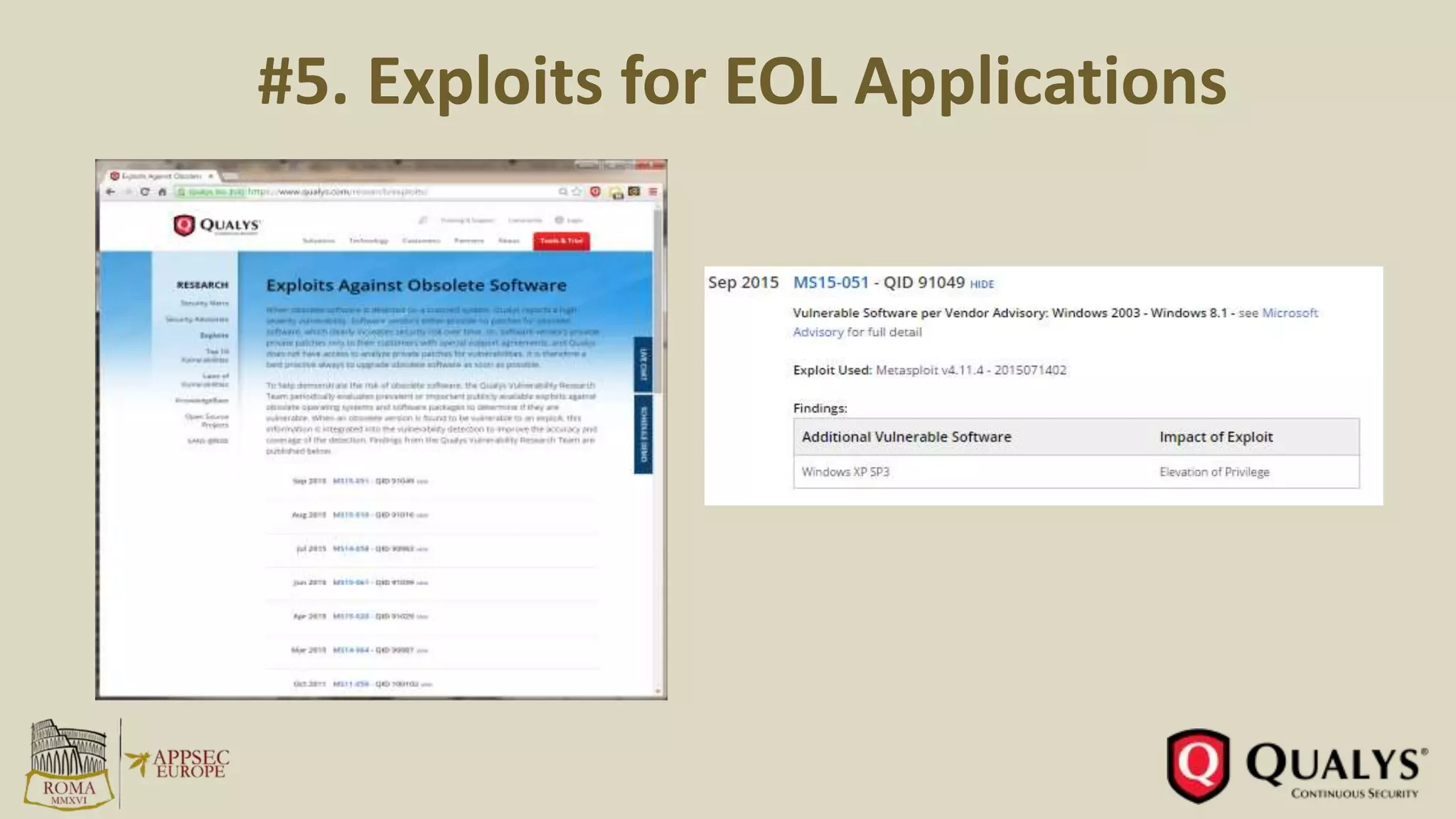
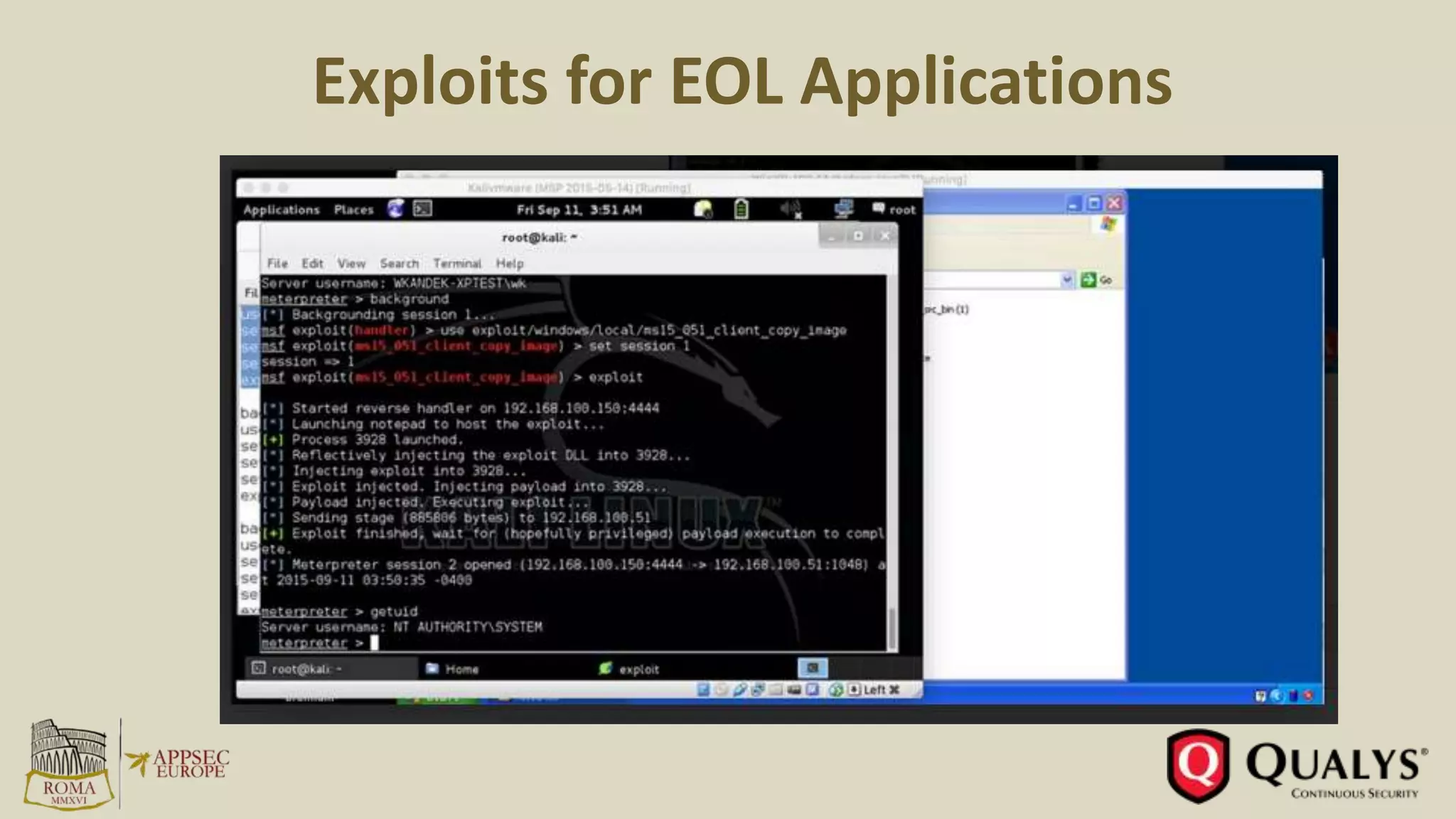
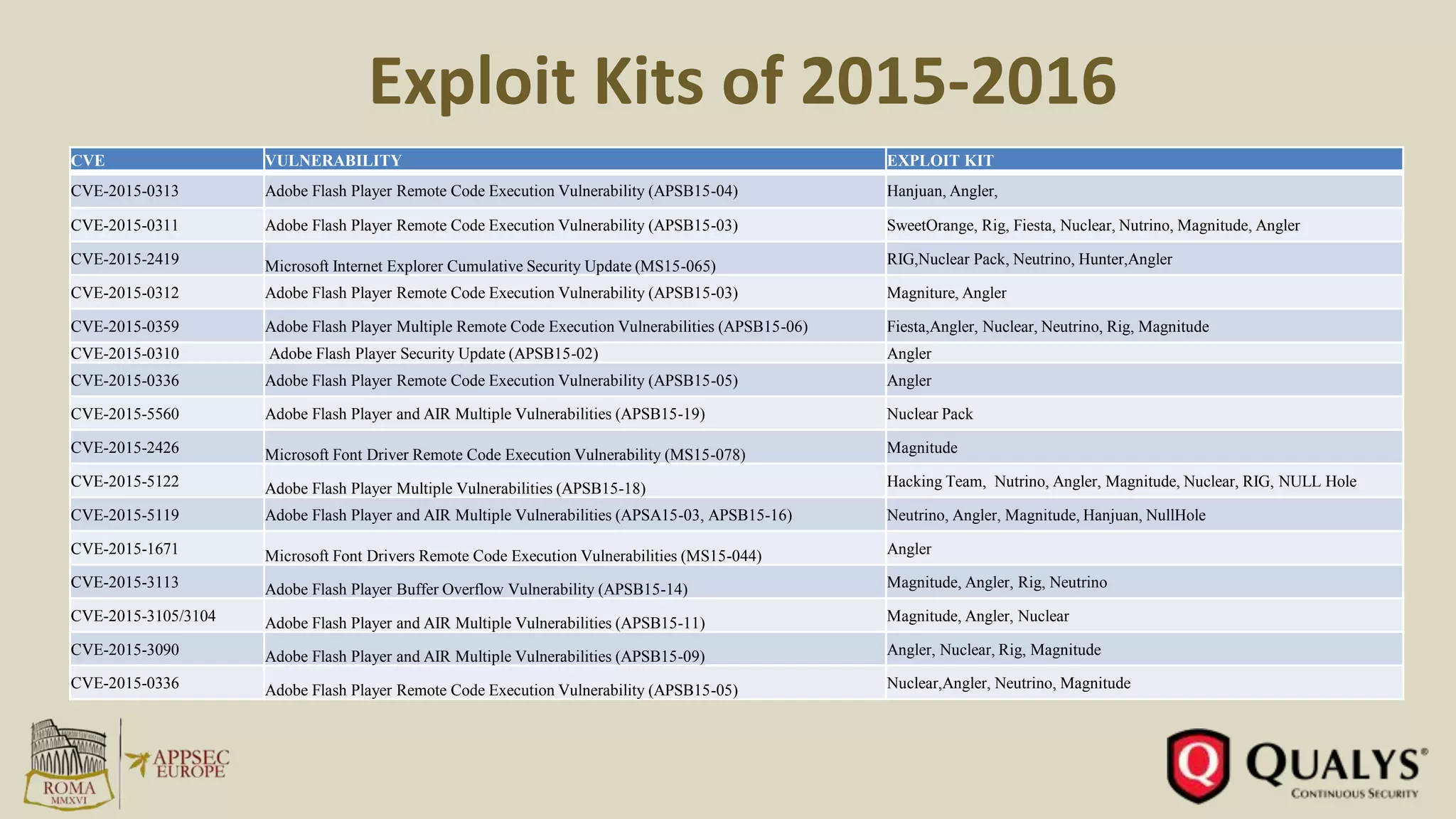
This document summarizes key trends in vulnerabilities and exploits from 2011-2016 based on a presentation by Amol Sarwate. Some of the main points include:
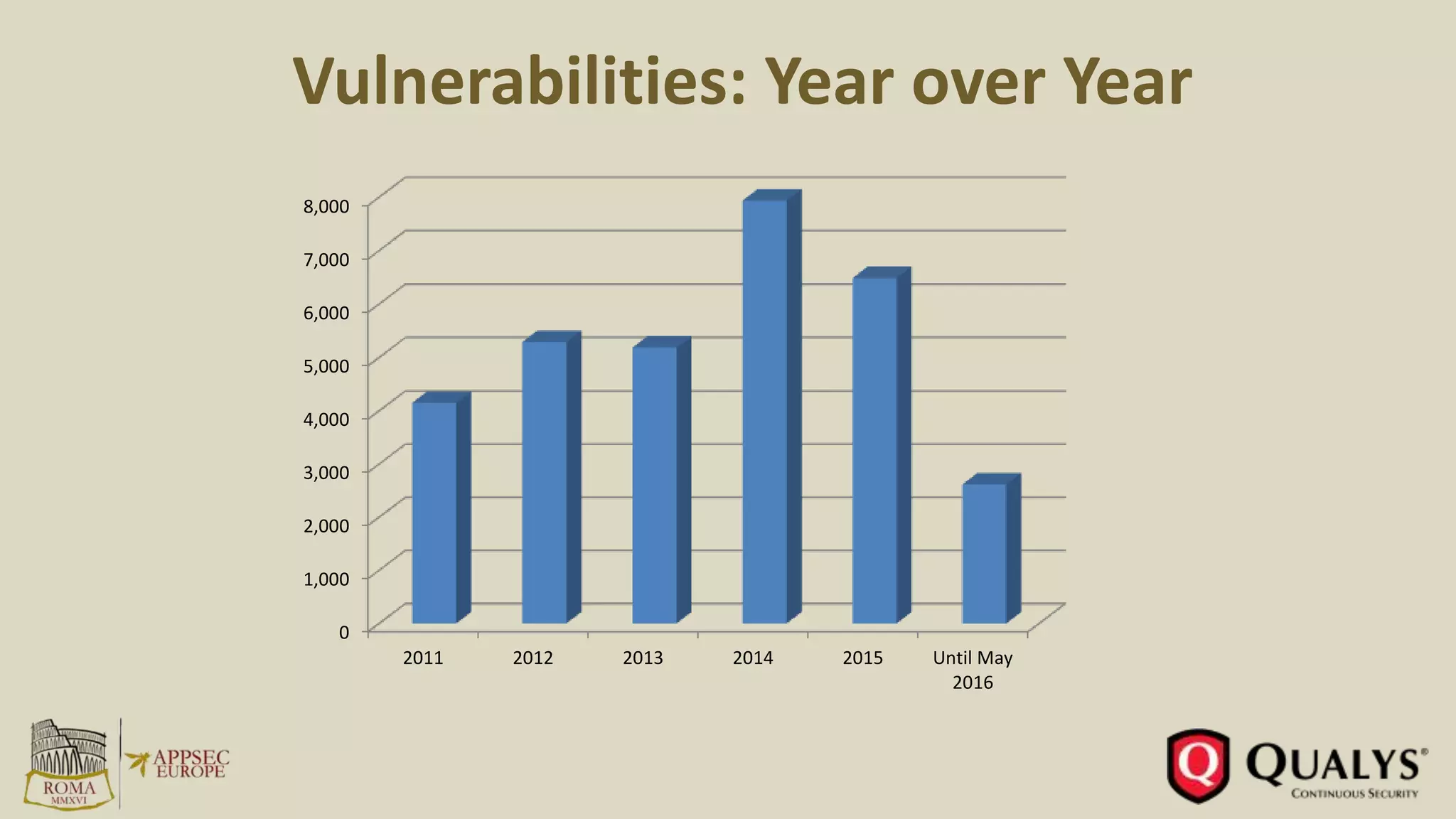
- The number of reported vulnerabilities has increased each year.
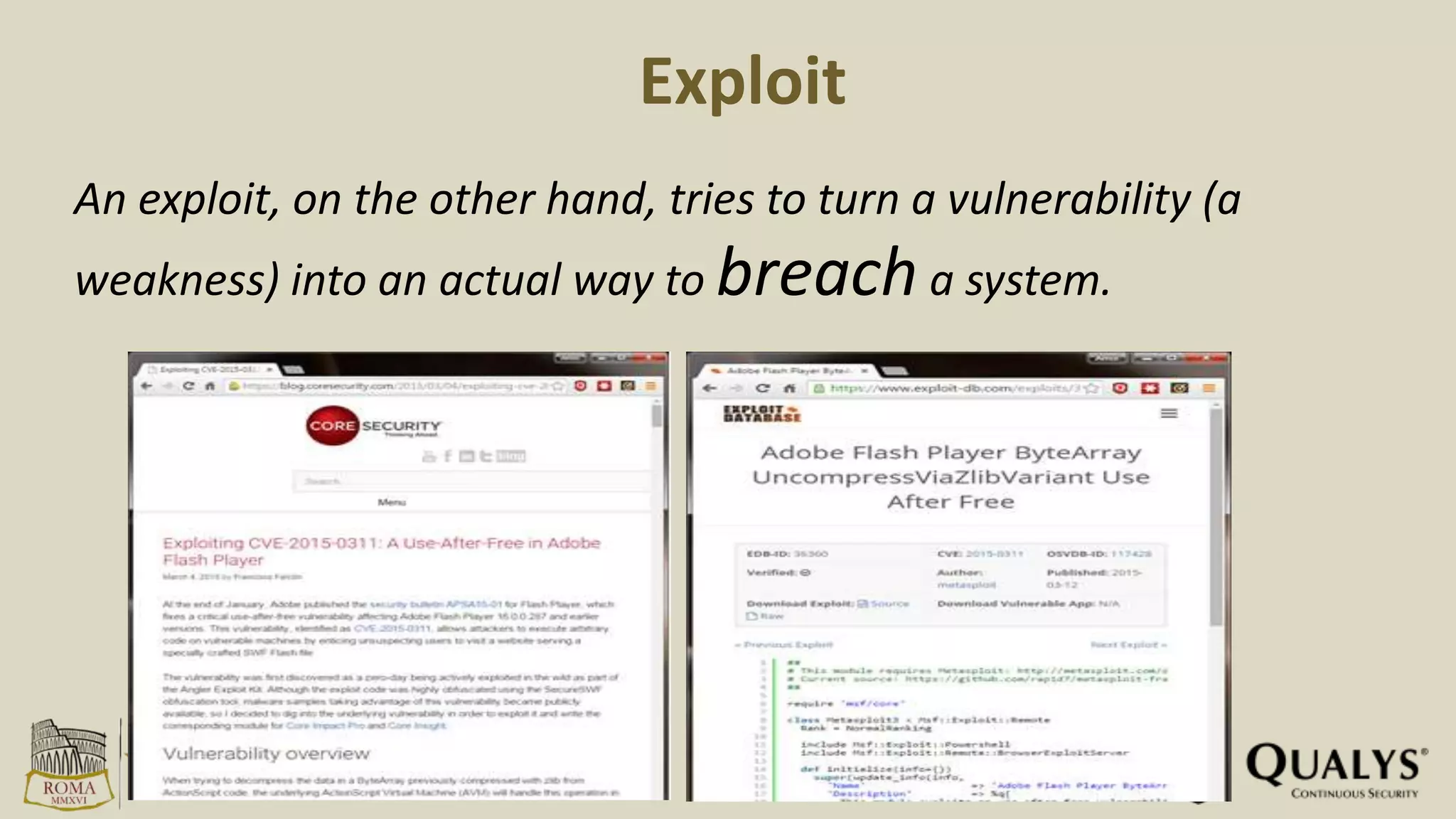
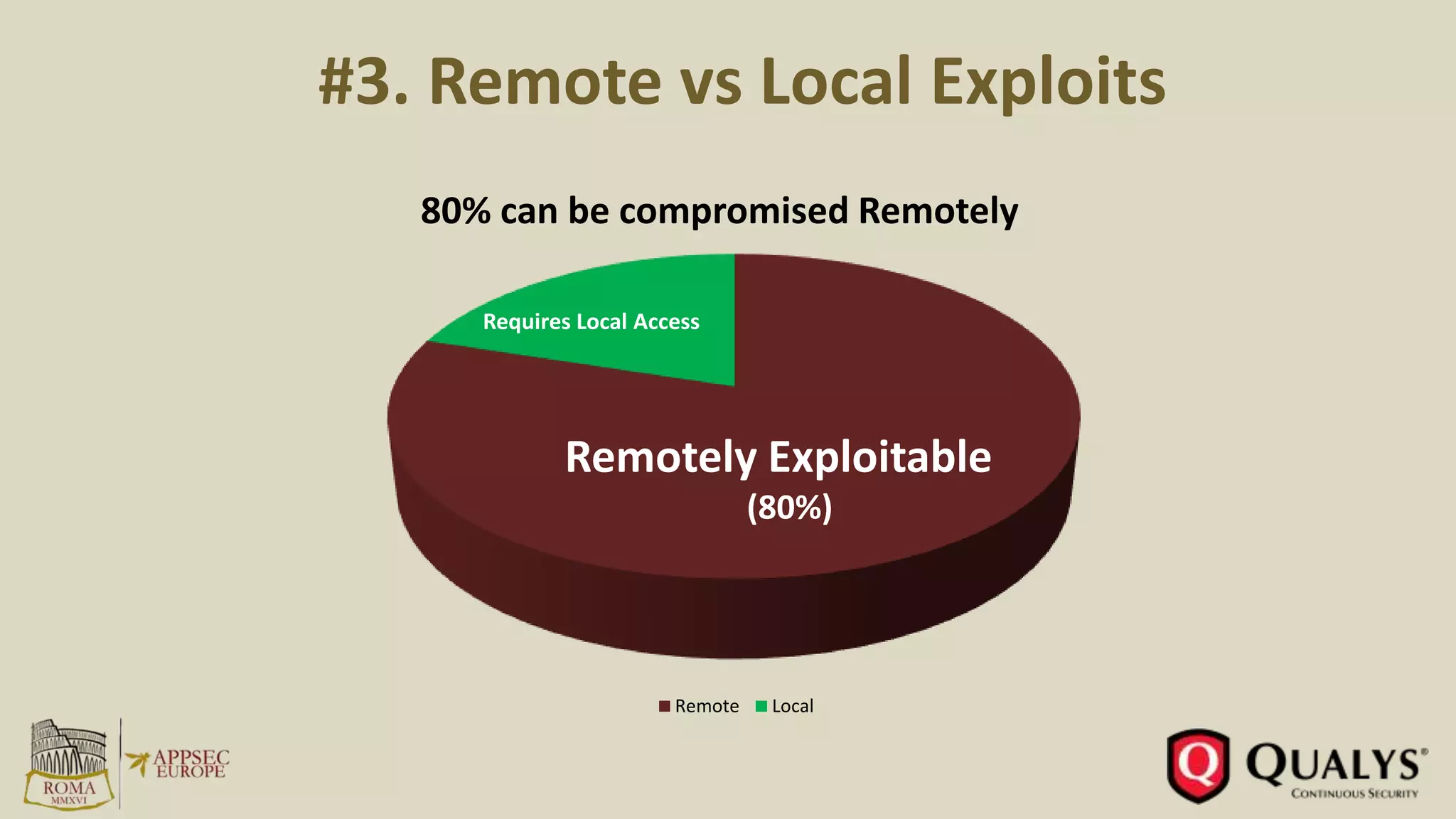
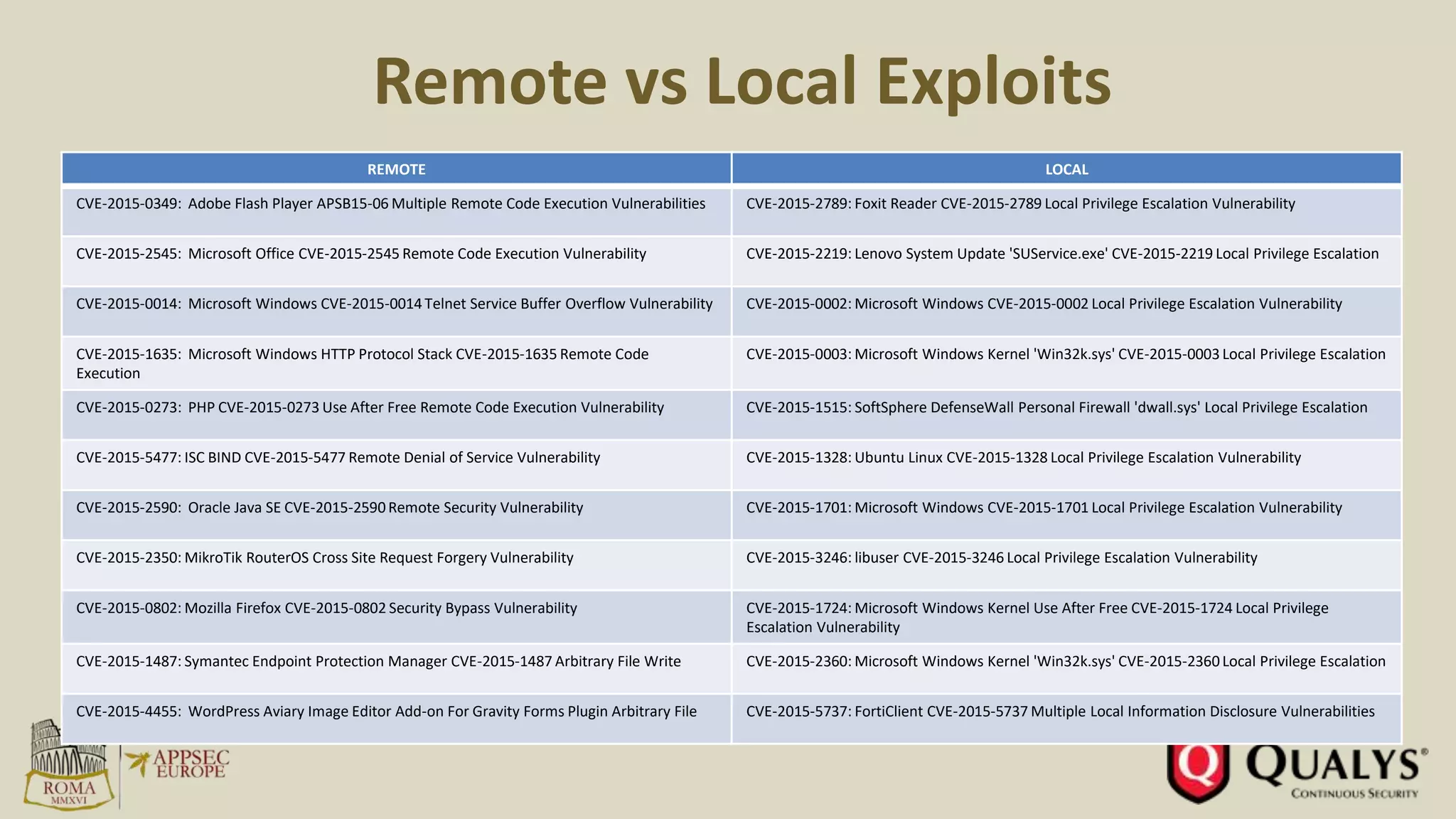
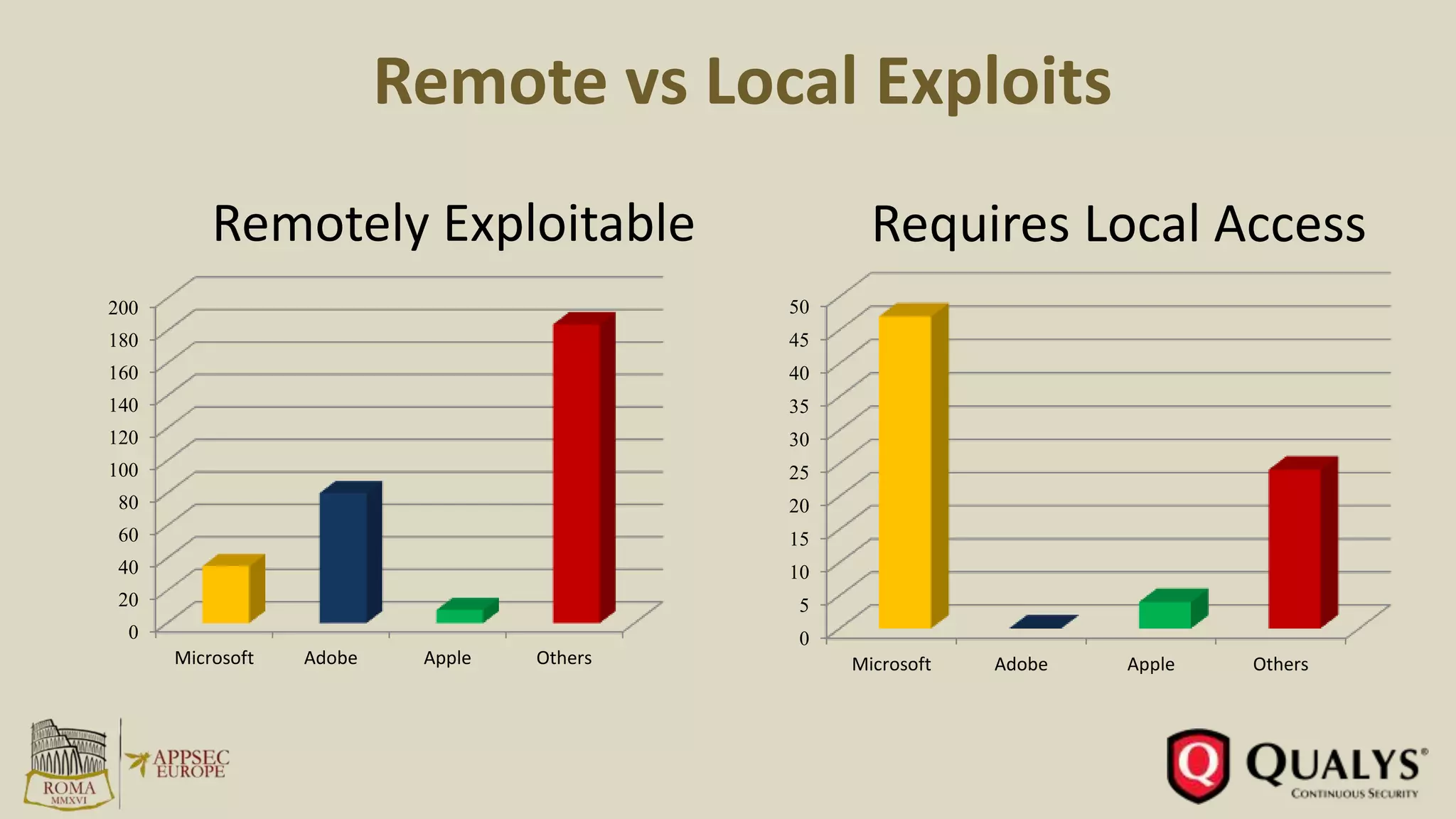
- In 2015, 80% of exploits allowed remote code execution, while only 26% targeted operating systems directly.
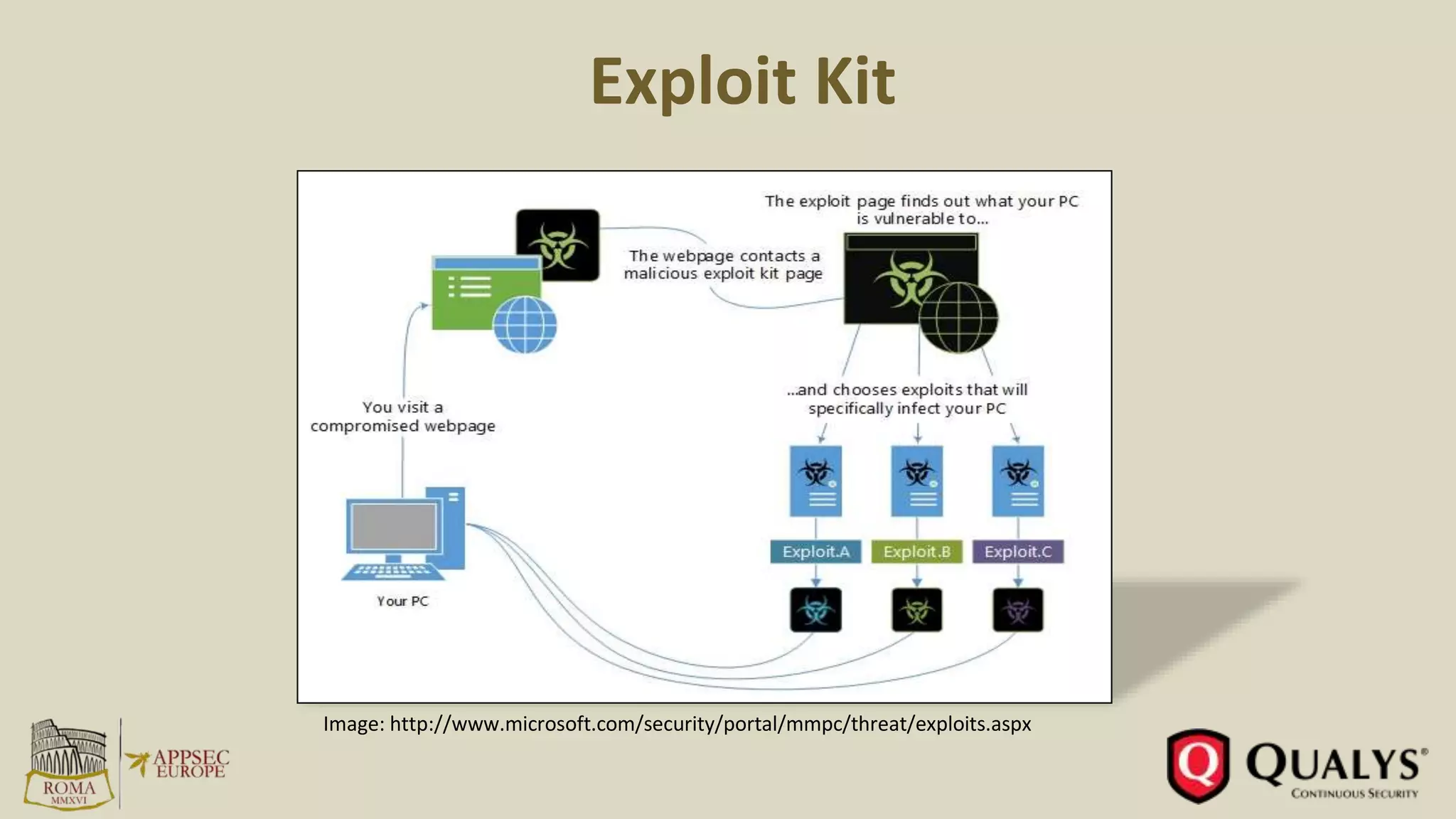
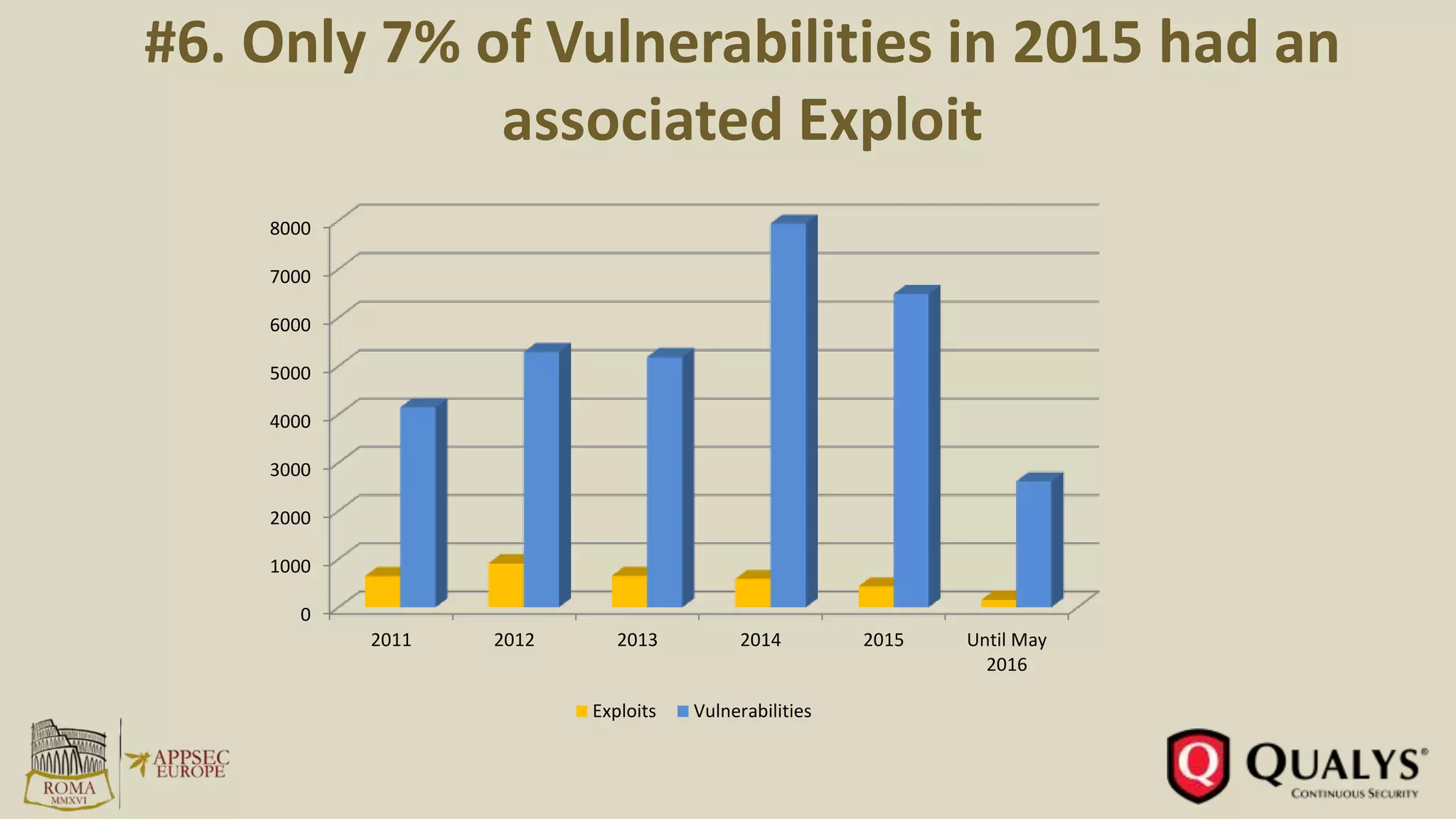
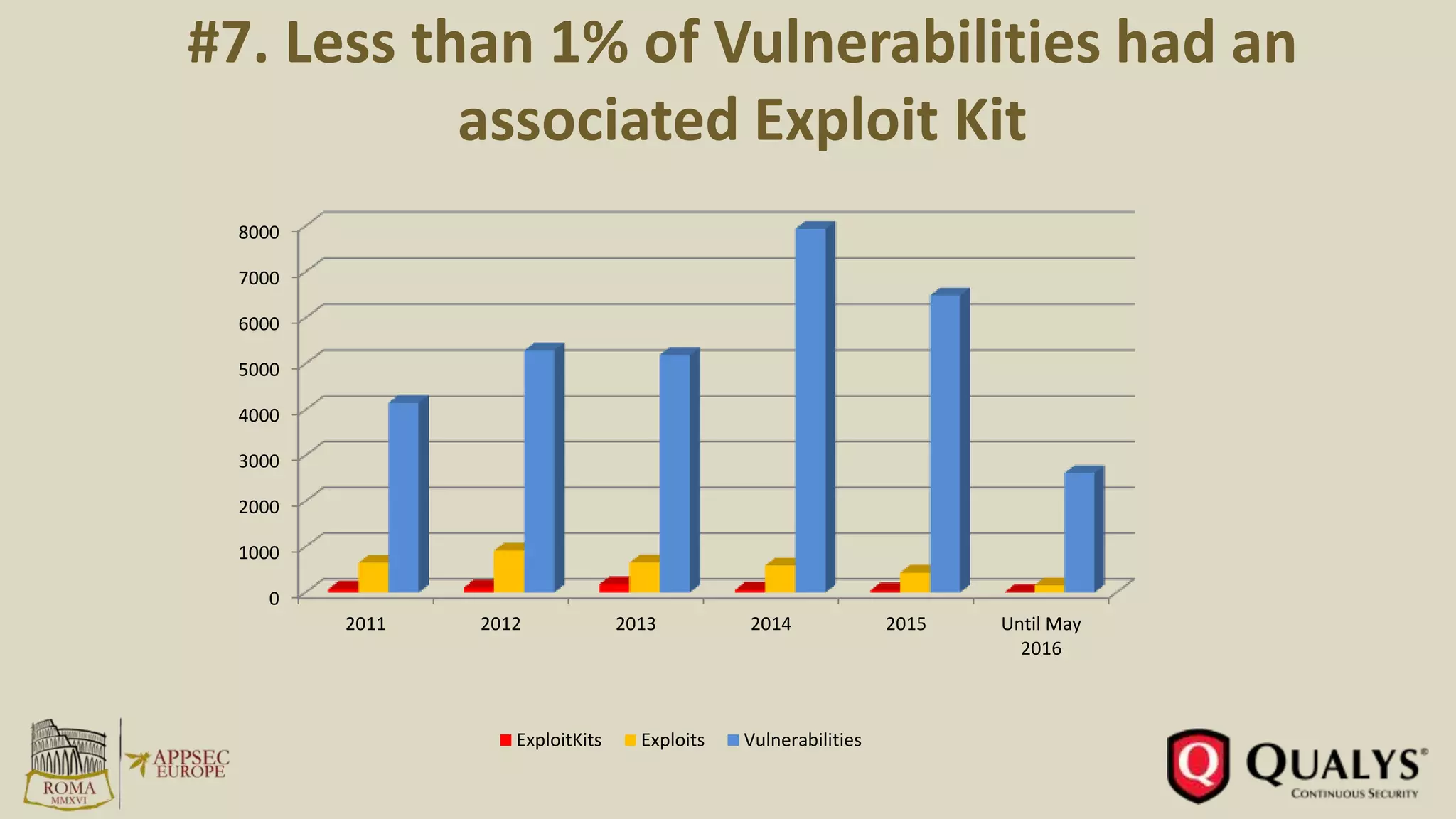
- Only 7% of vulnerabilities in 2015 had an associated exploit, while less than 1% were incorporated into exploit kits.
- The presentation provides recommendations for organizations to inventory and patch vulnerable applications and systems to improve security.