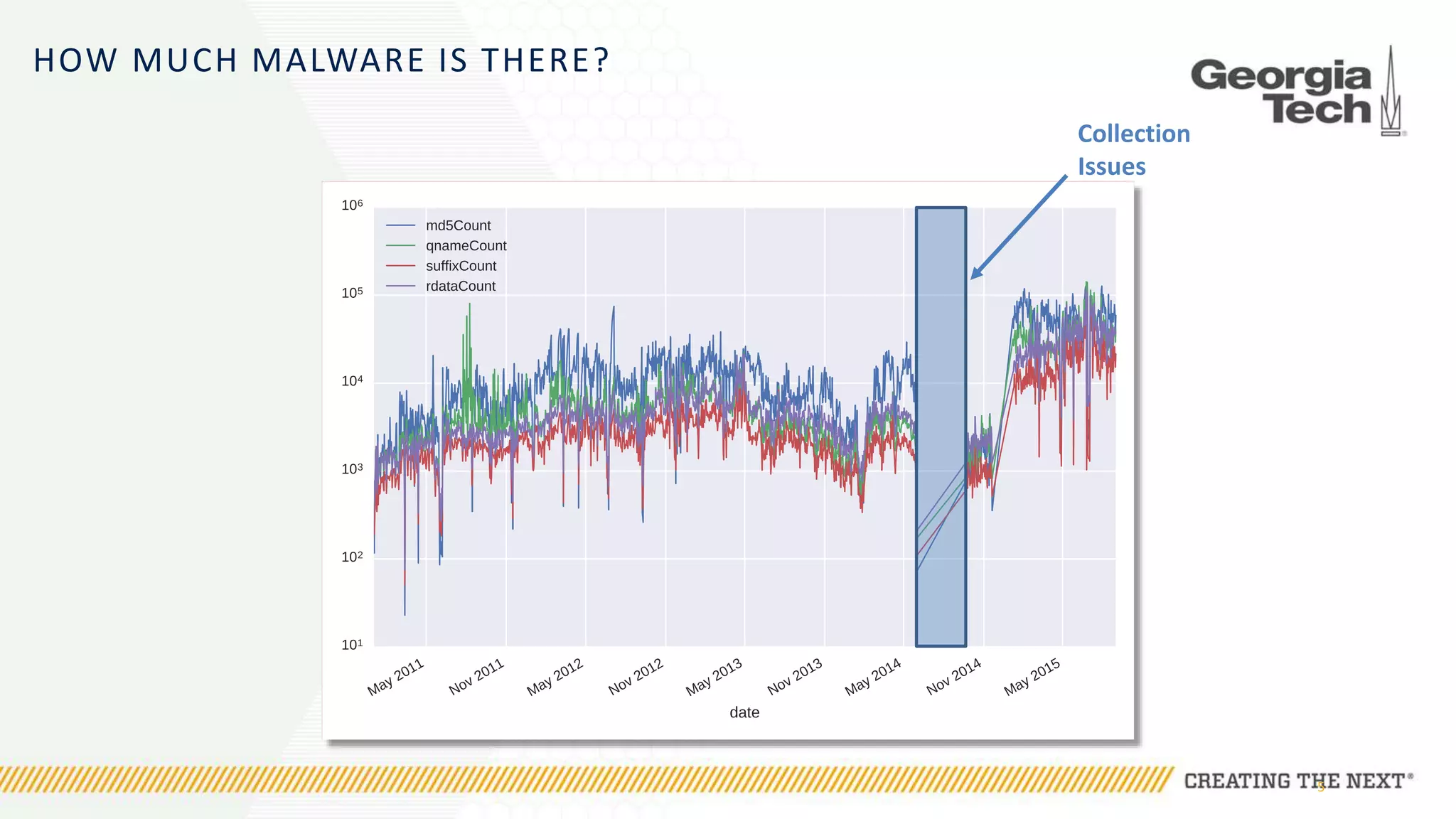
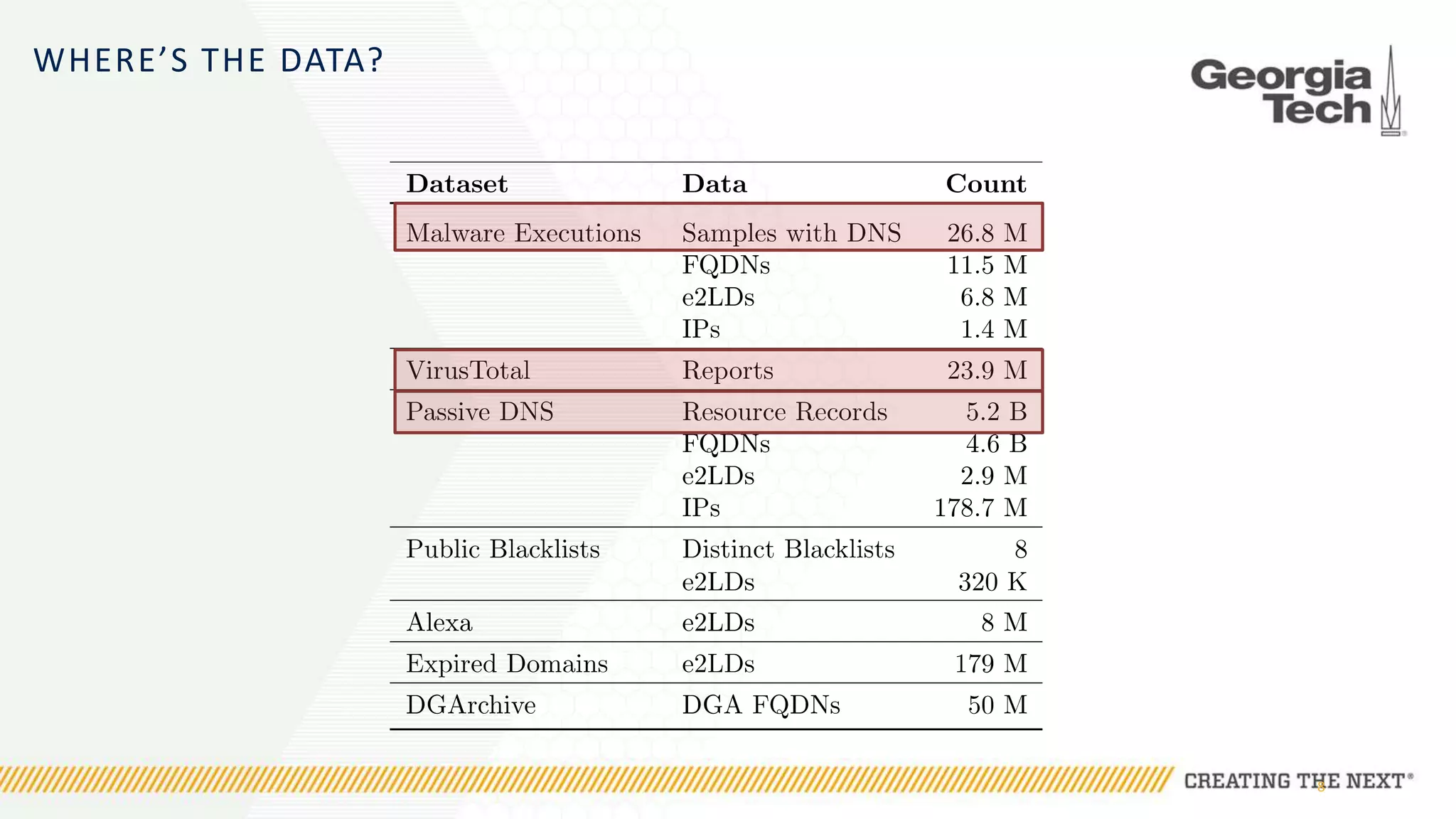
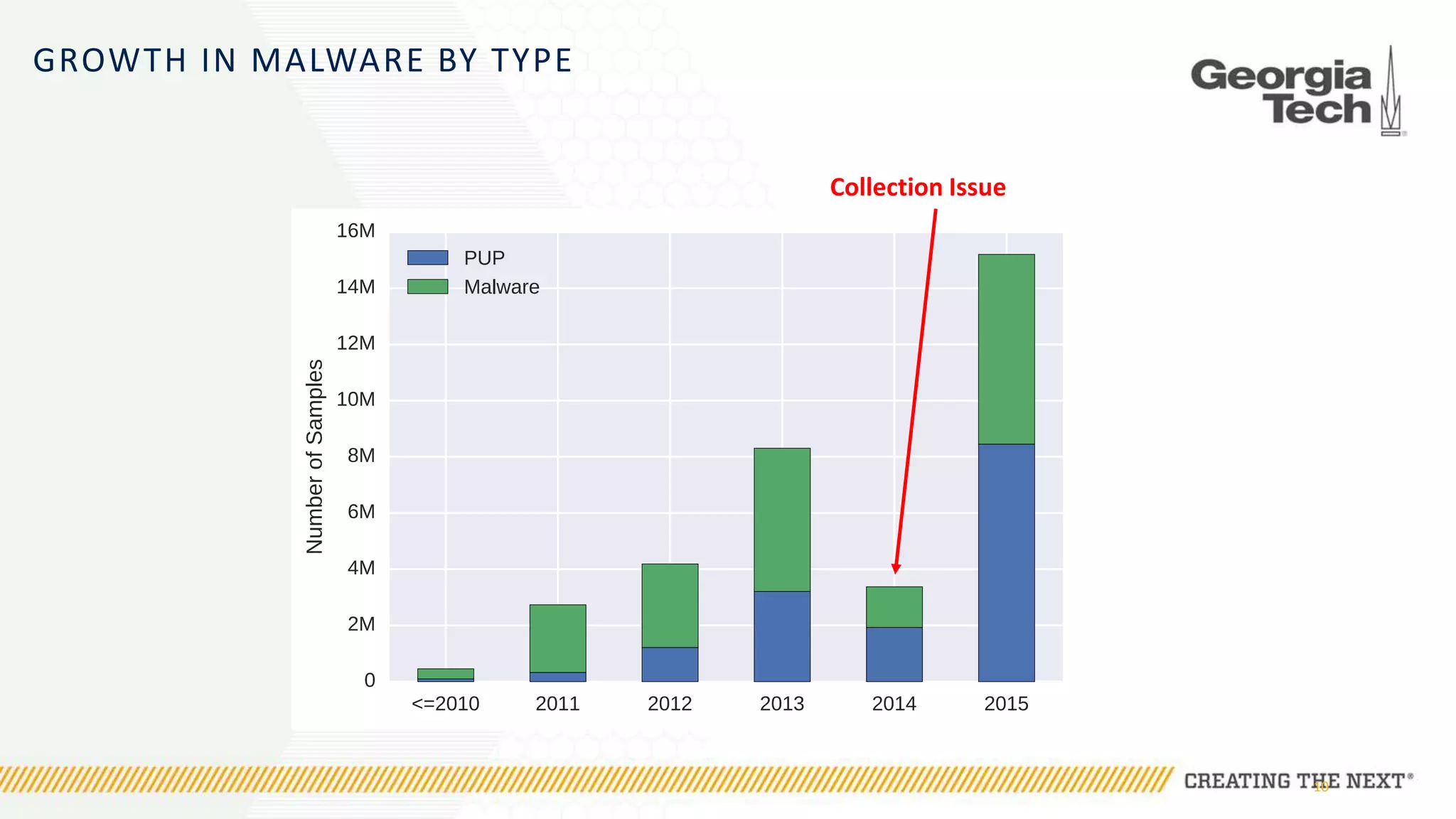
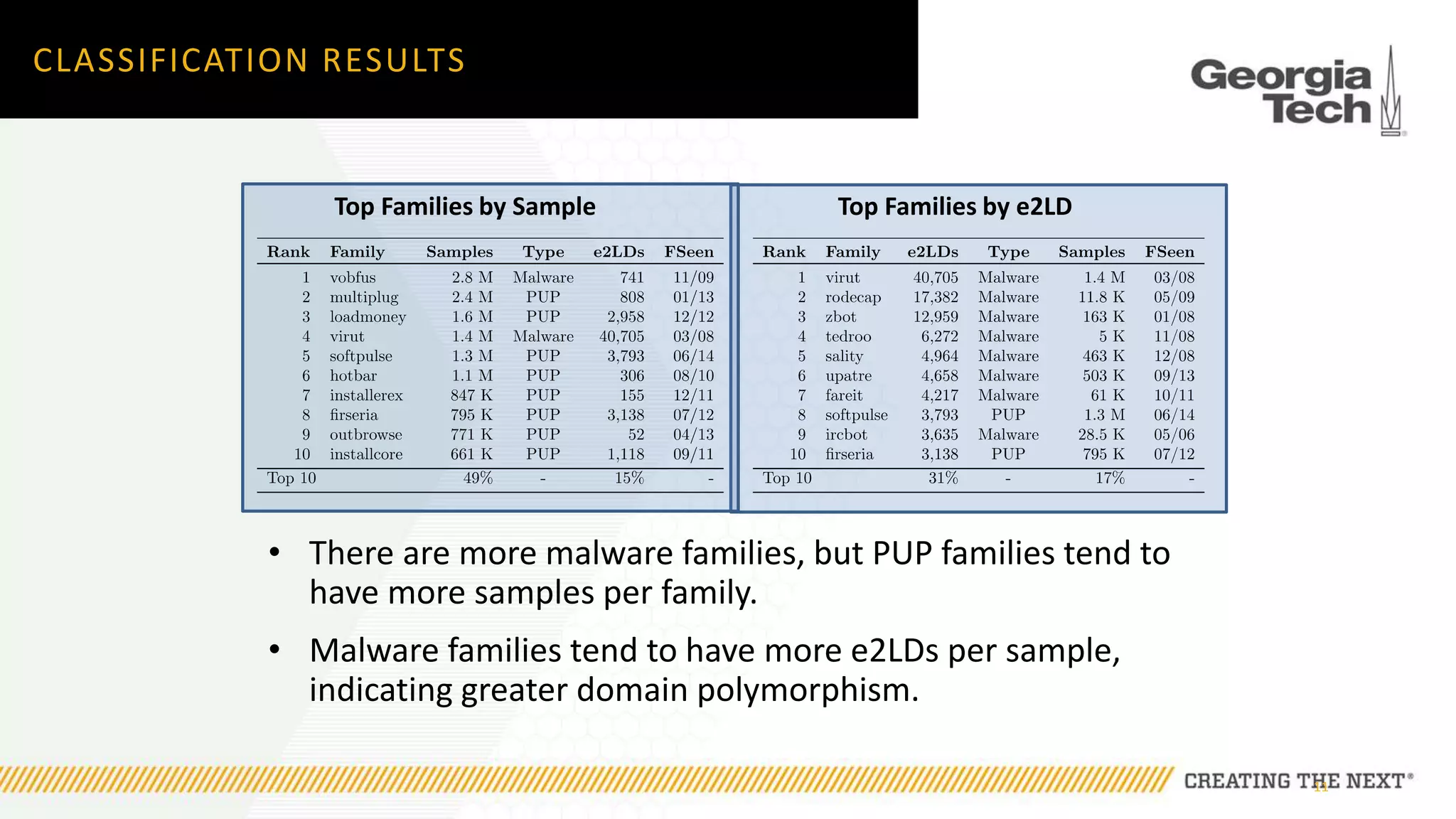
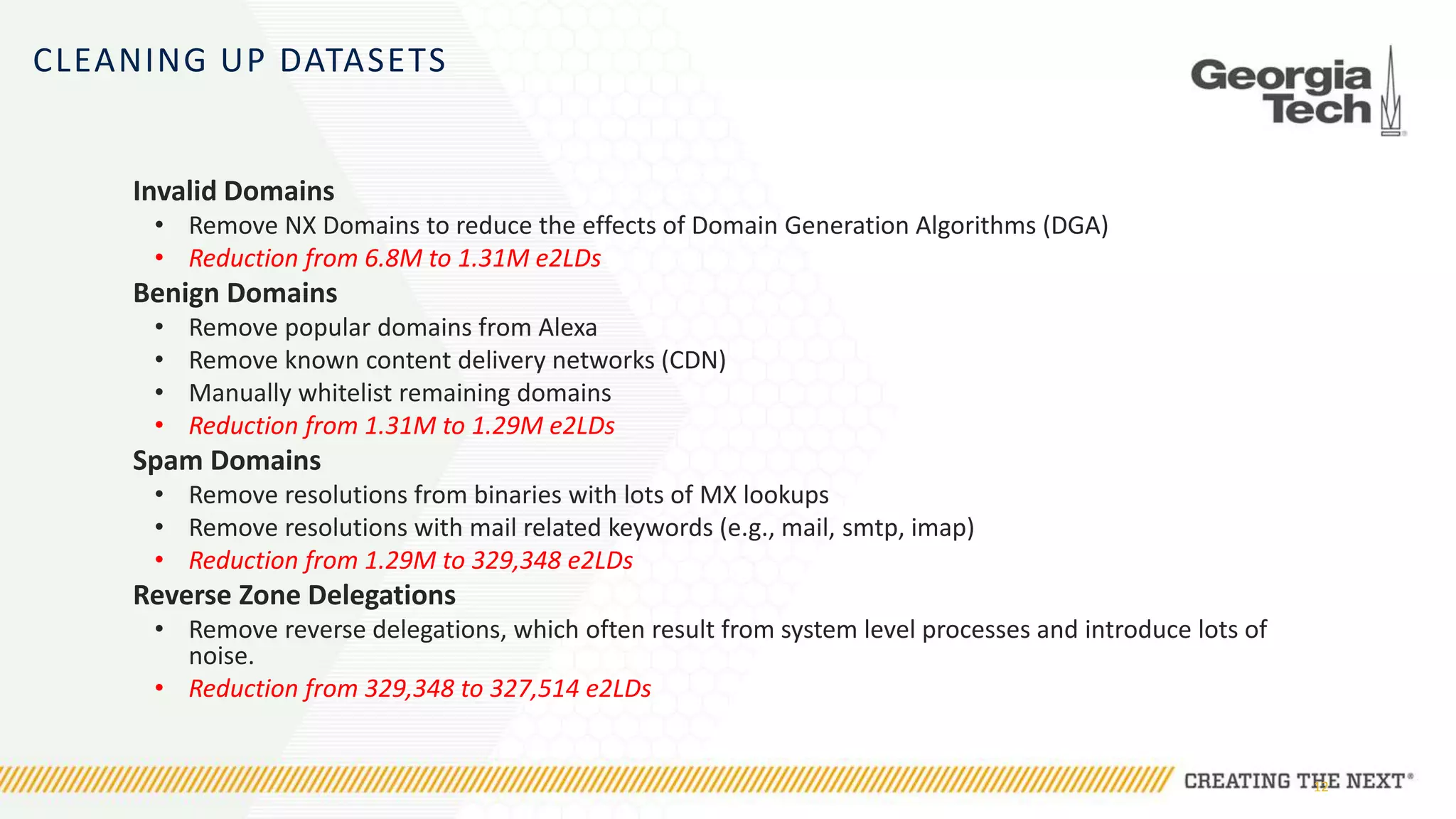
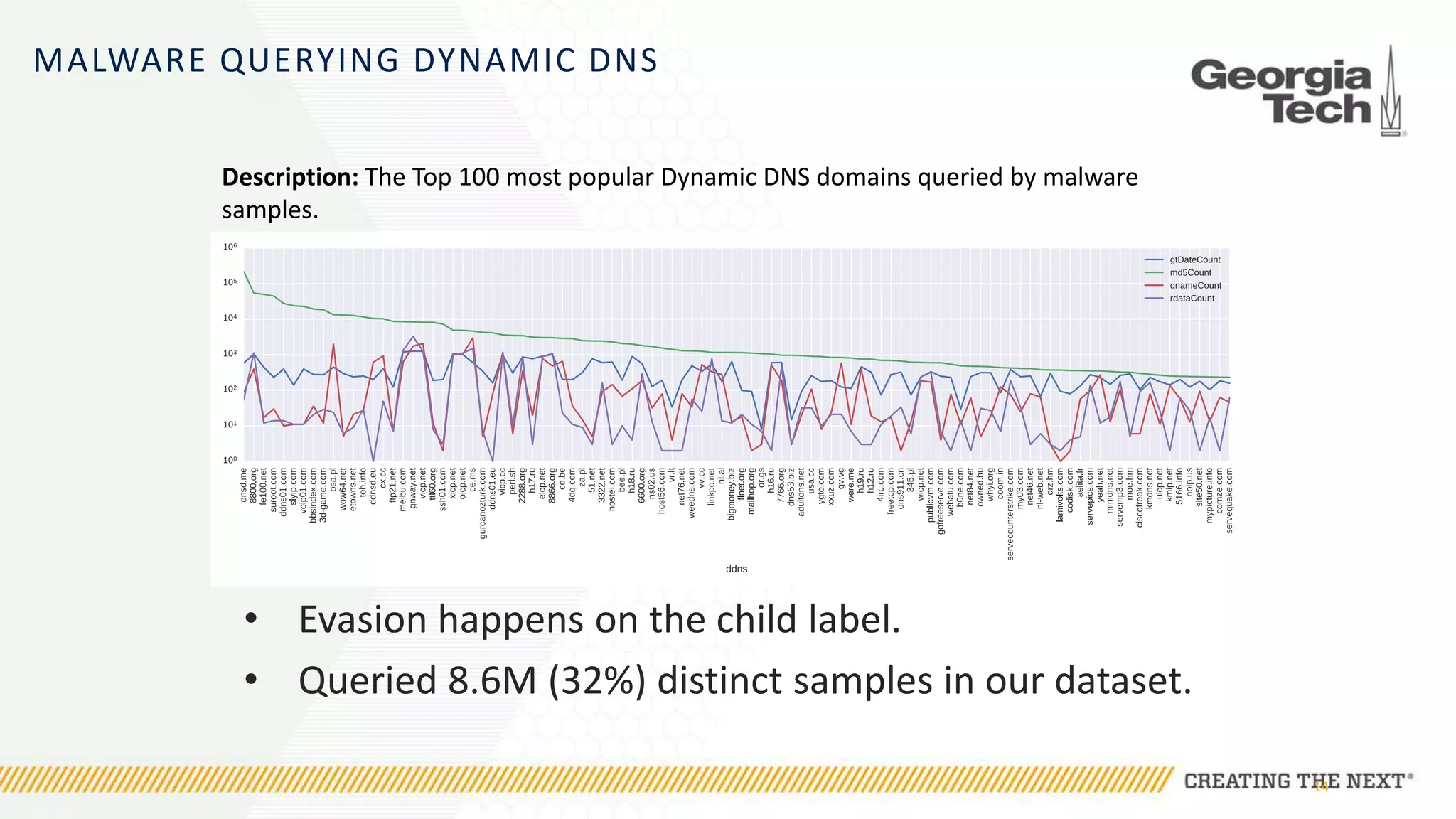
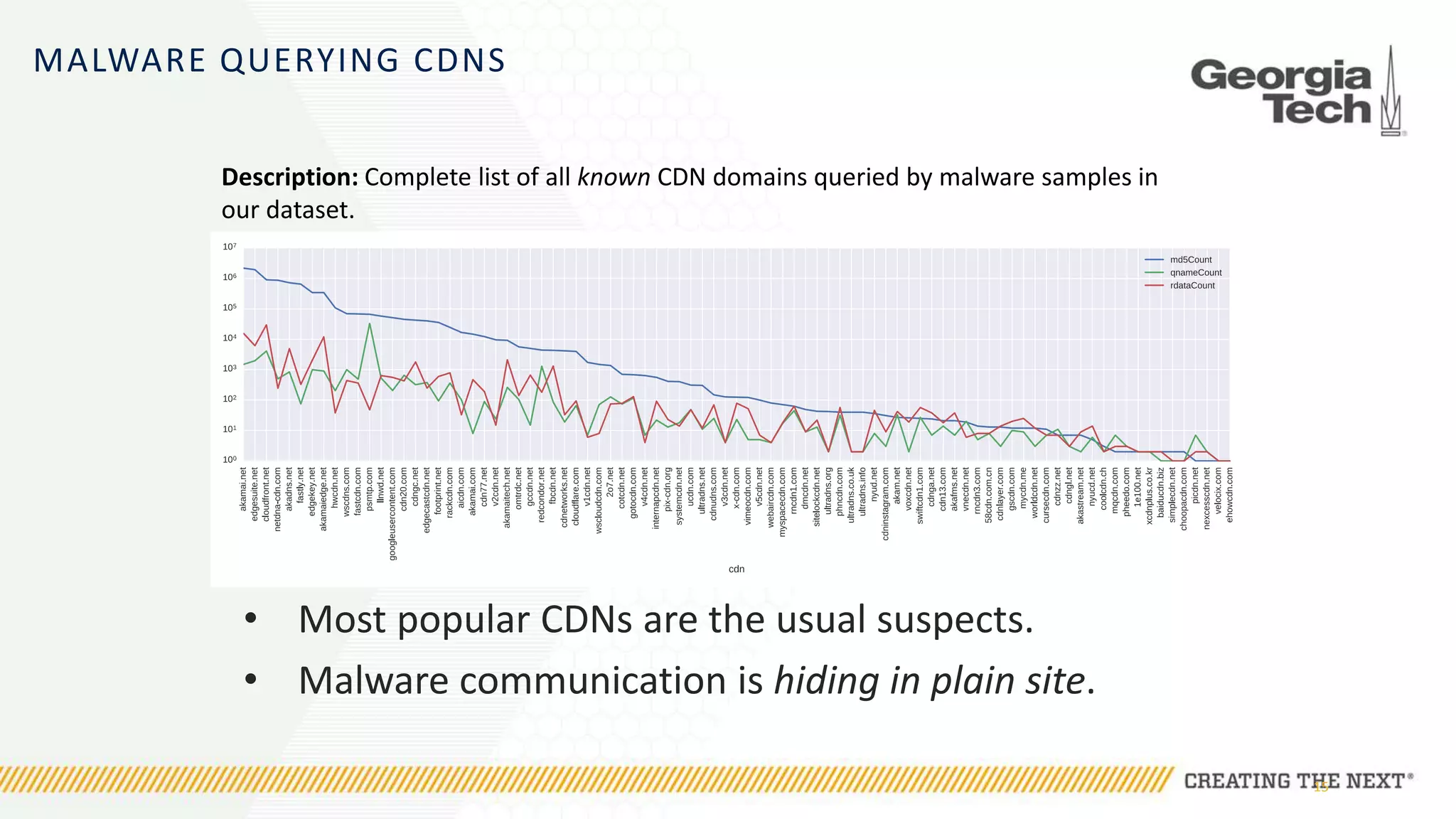
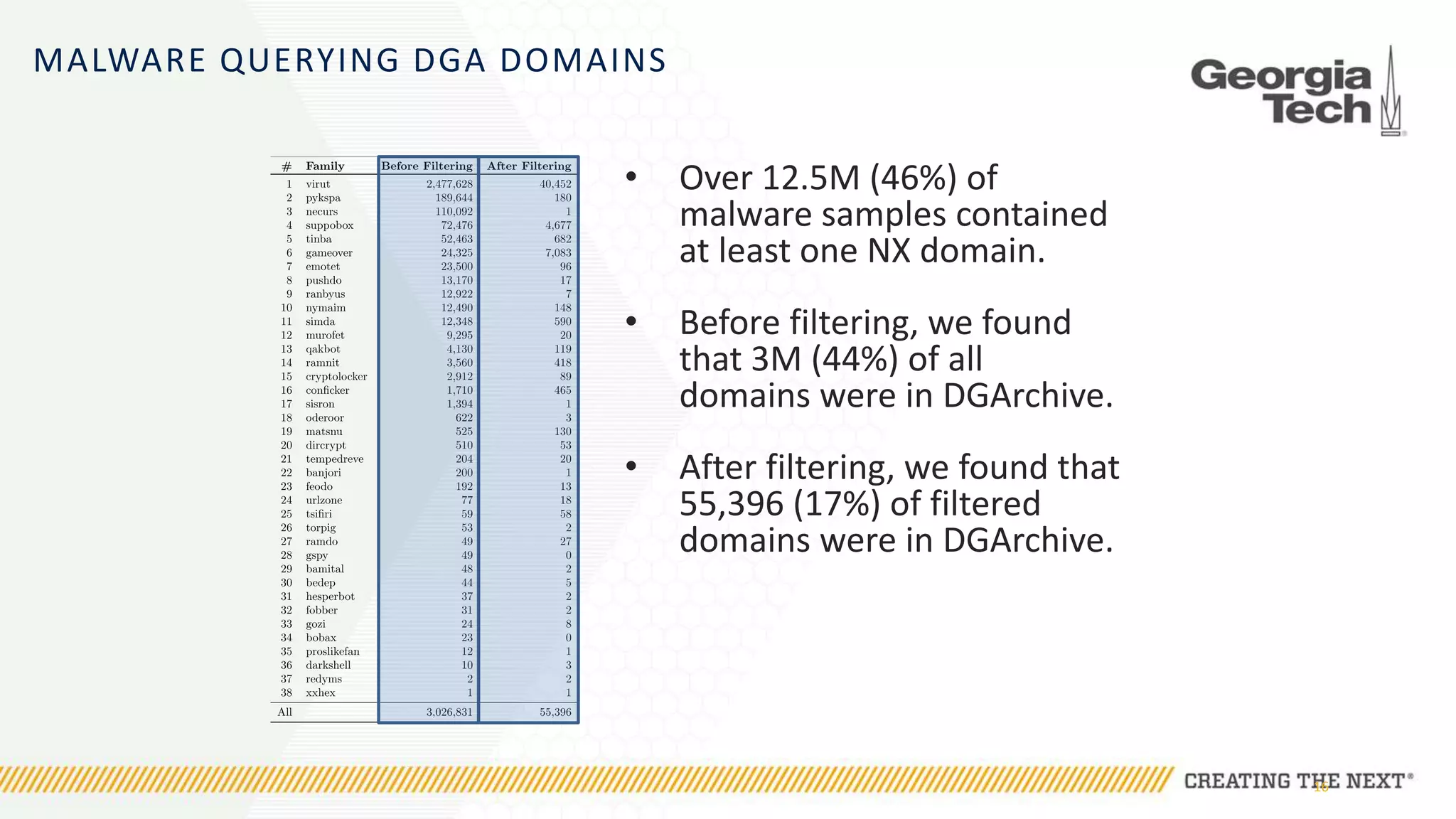
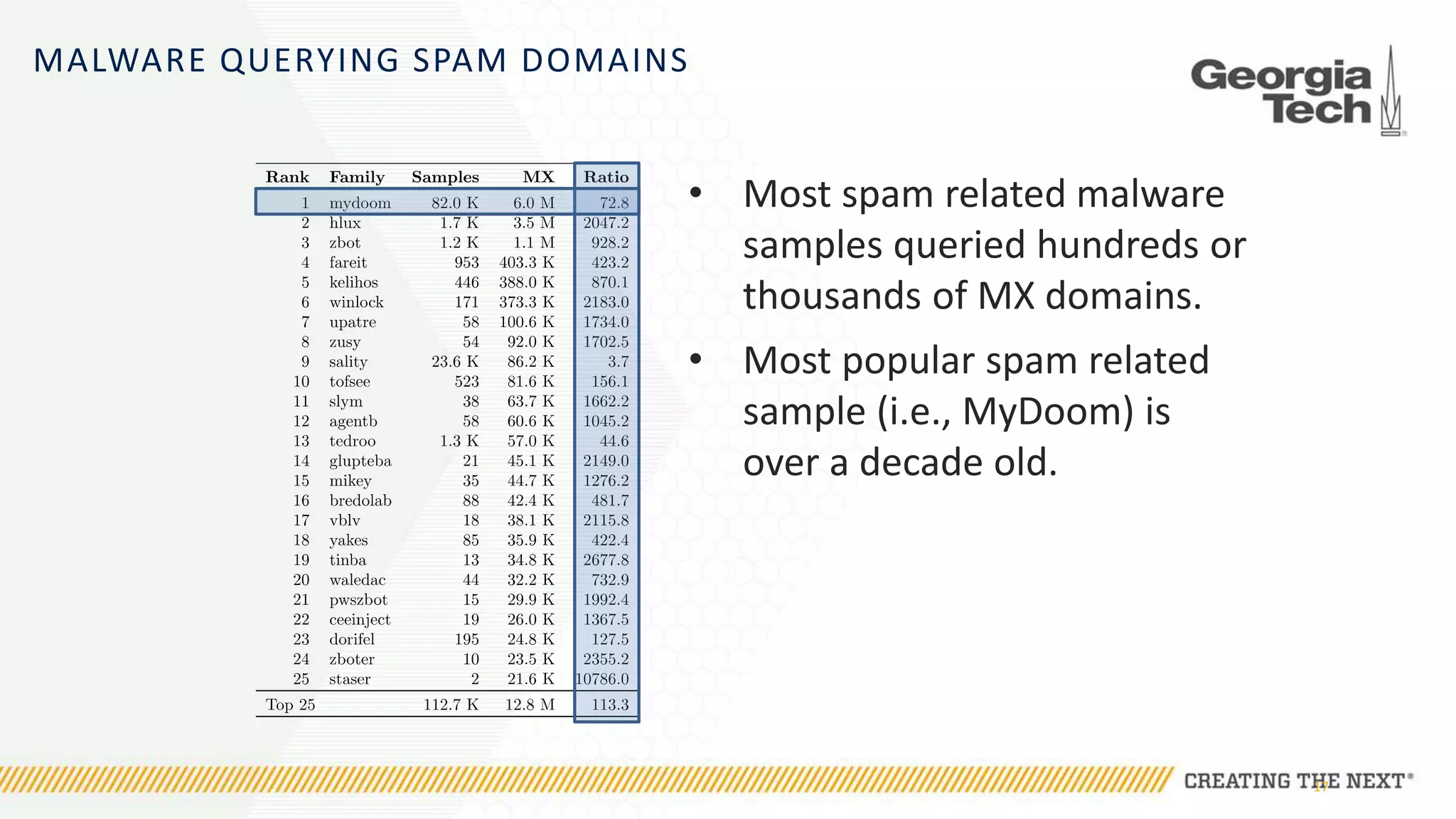
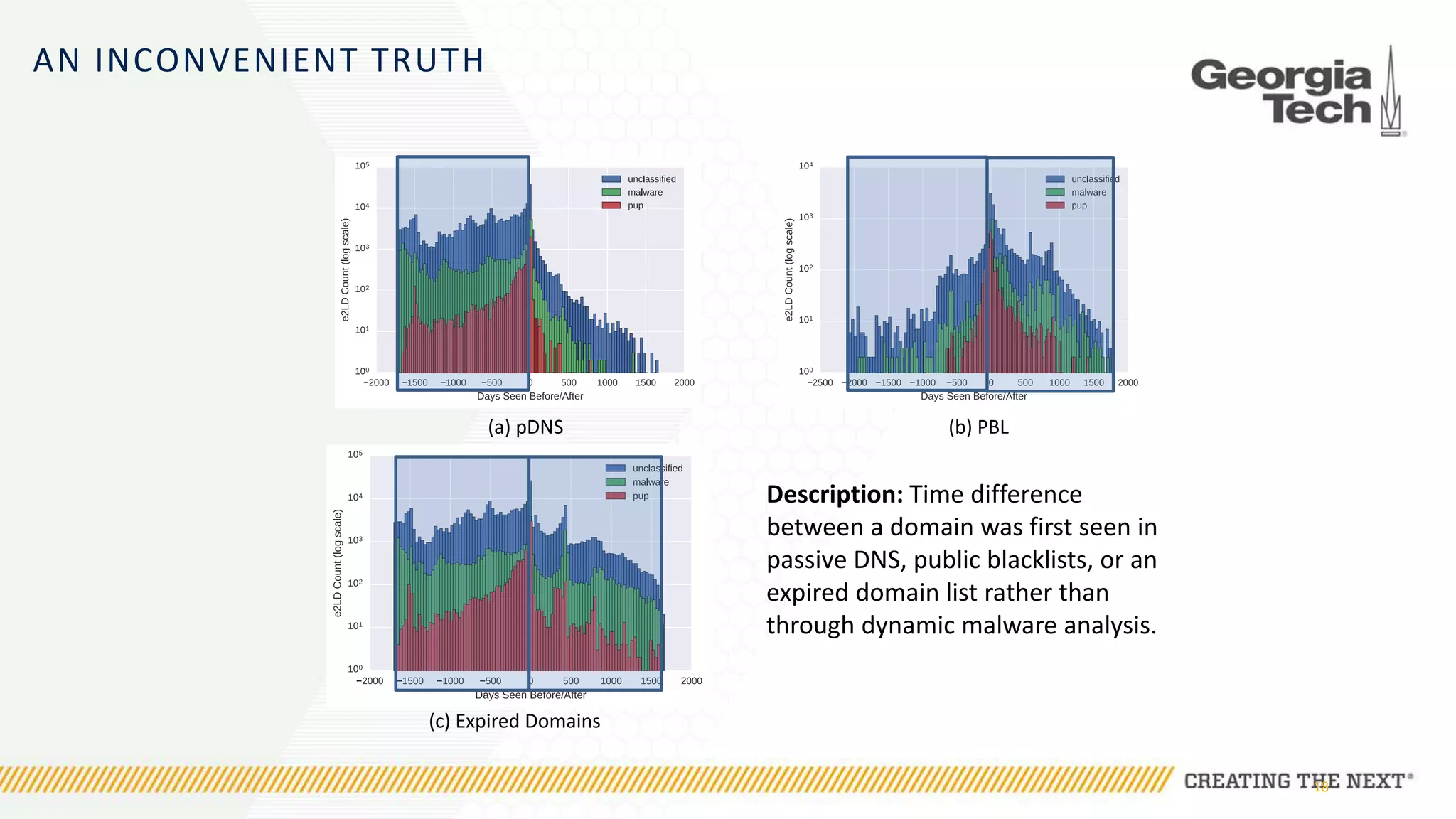
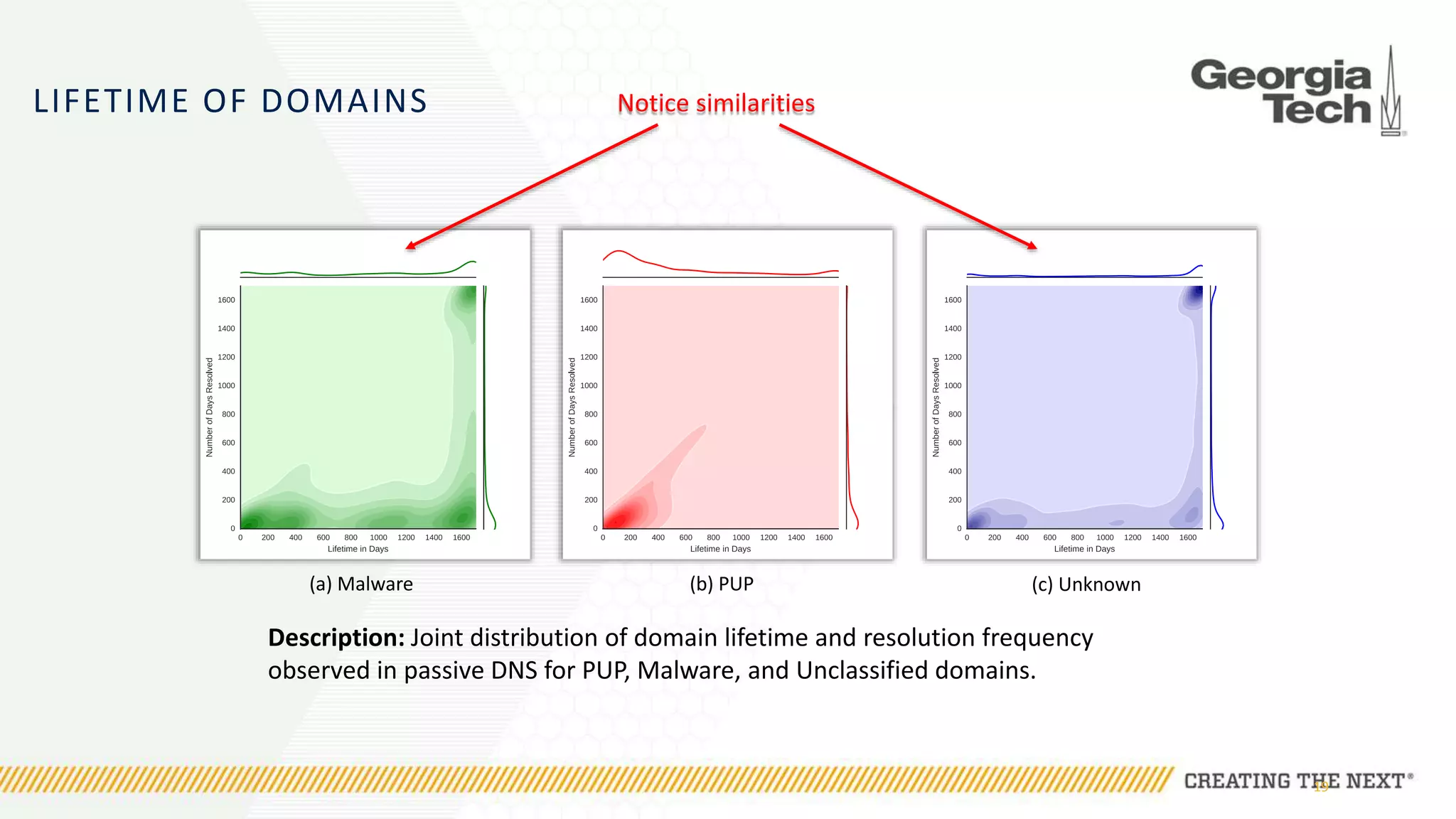
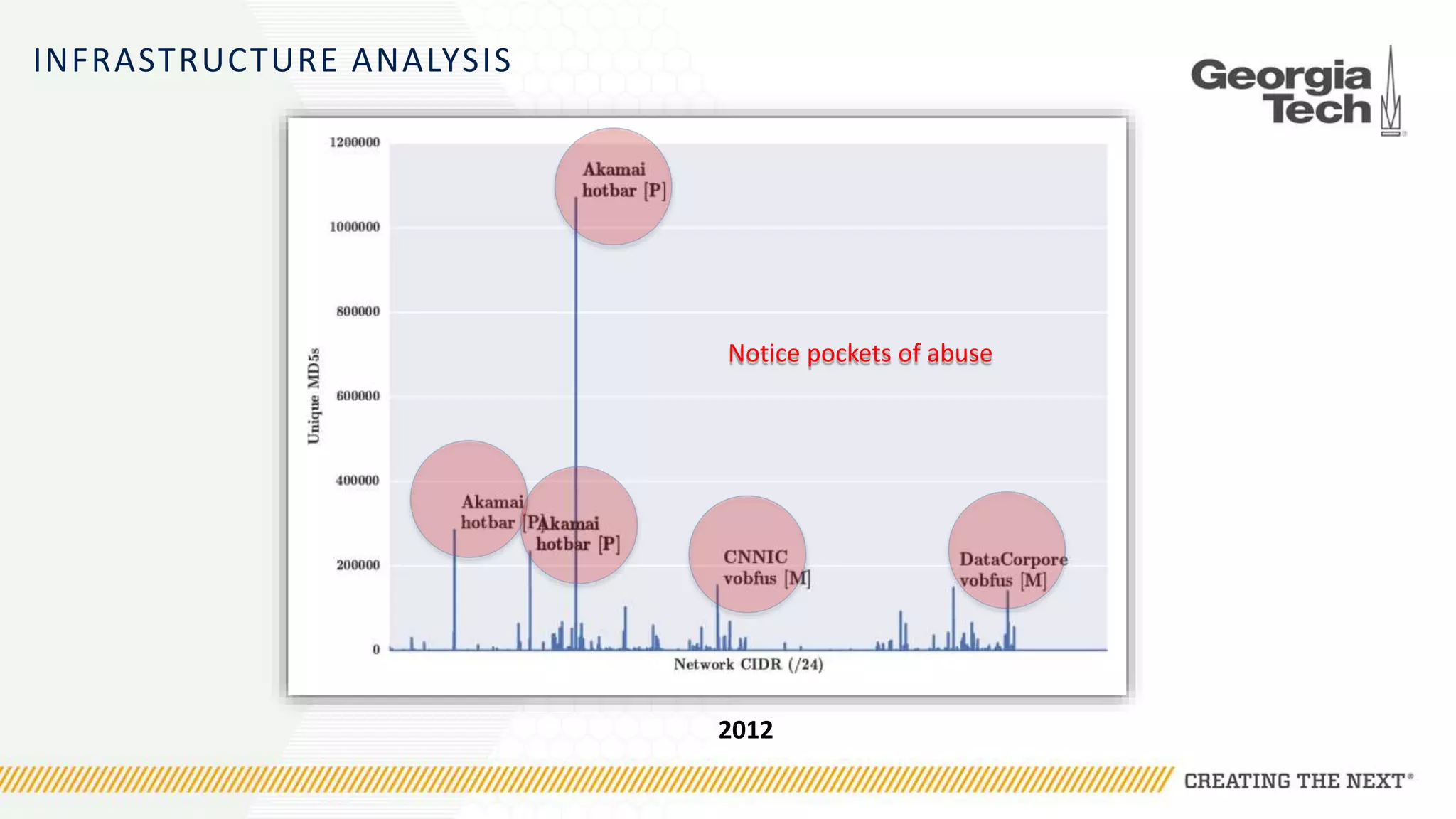
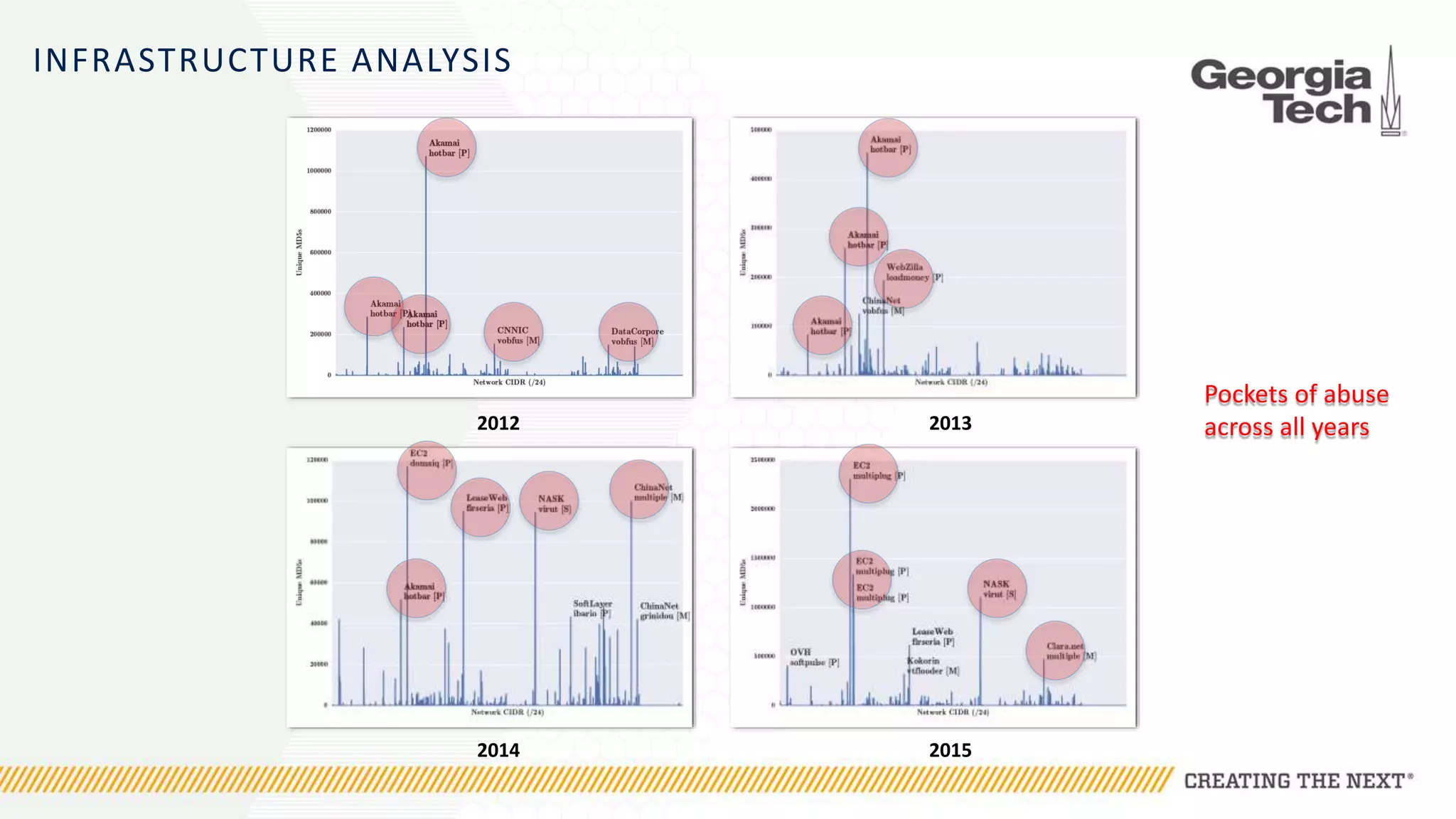
The document discusses the evolution of malware communication and the importance of malware analysis for understanding and defending against cyber threats. It outlines methods of analysis, shows the growth of malware families, and stresses the challenges in detecting and classifying malware effectively. Key findings indicate that waiting for malware to be discovered can result in vulnerabilities, underscoring the need for proactive network defenses.