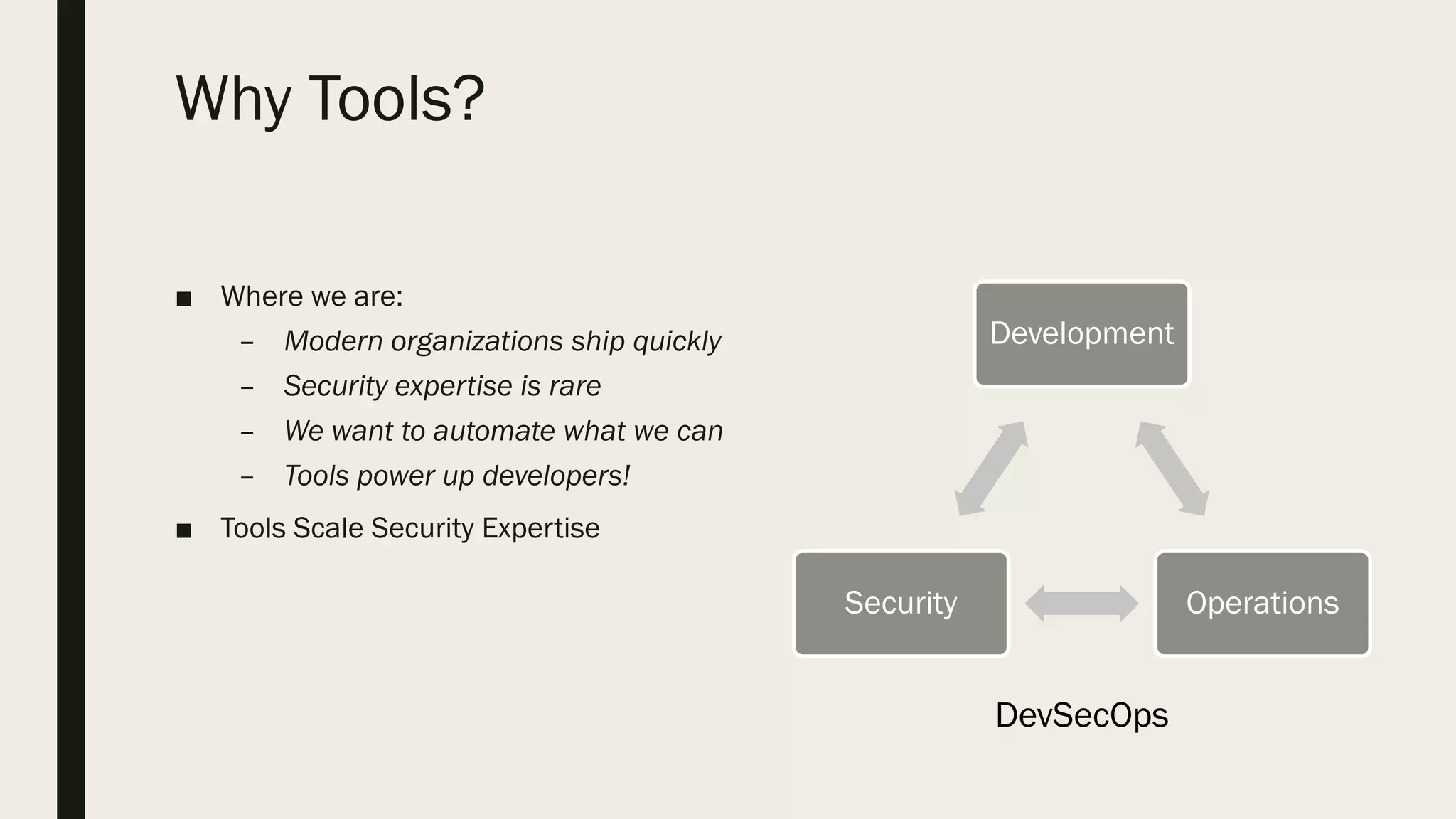
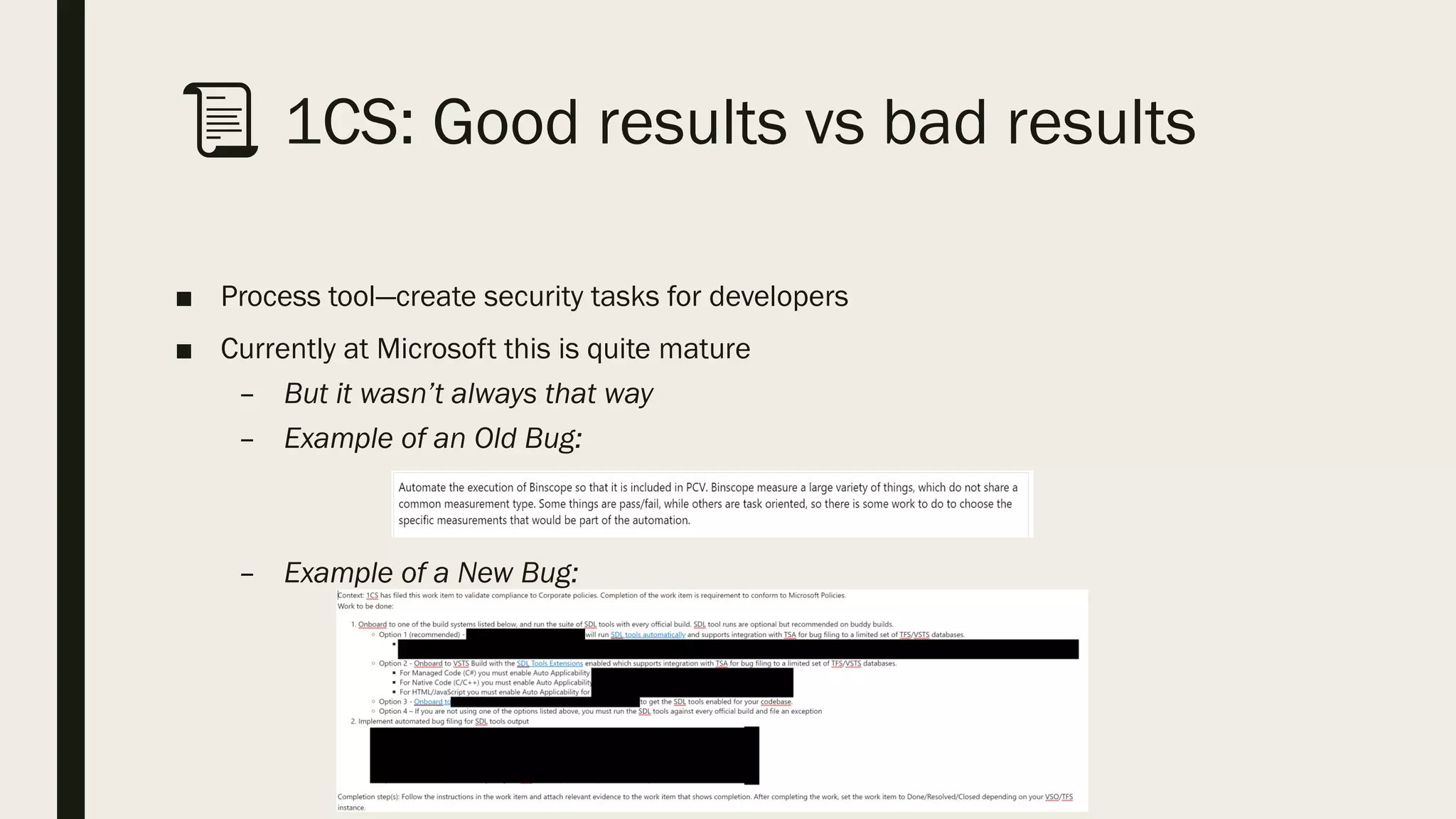
The document discusses a talk aimed at security experts focused on developing effective security tools, emphasizing best practices and personal experiences. It covers tool types, importance for developer integration, the need for simplicity and clear documentation, and considerations for false positives and onboarding. Additionally, it highlights specific tools used at Microsoft, such as SARIF and Binskim, and underscores the importance of scaling and developer trust in tool adoption.