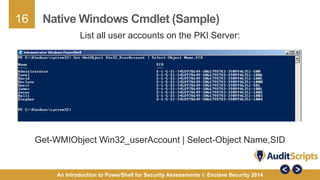
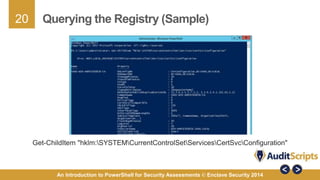
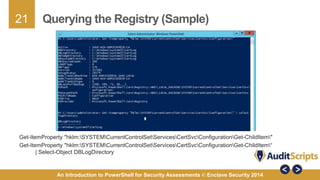
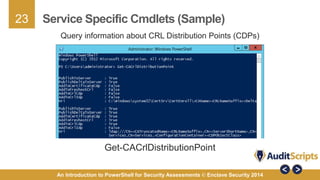
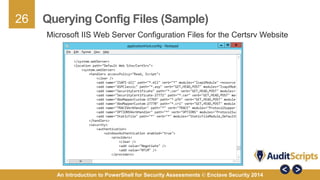
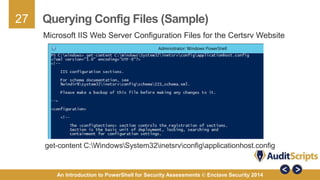
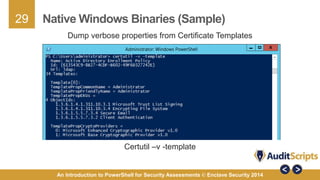
This document introduces the use of PowerShell for security assessments, emphasizing its advantages in security auditing by enabling 'living off the land' practices. It outlines the capabilities of PowerShell as a scripting language and command line tool, detailing its functionality, cmdlets, and modules relevant to assessing the security of Microsoft systems. Additionally, it provides a step-by-step approach for conducting security assessments, highlighting key areas such as governance, registry settings, and service-specific cmdlets.










![12
Accessing .NET Objects
• PowerShell can also even utilize .NET libraries
• Anything .NET can do, PowerShell can also
• There is a fuzzy line between PowerShell & VB.NET
• Both of the following commands are the same:
– [datetime]::now
– Get-Date
An Introduction to PowerShell for Security Assessments © Enclave Security 2014](https://image.slidesharecdn.com/anintroductiontopowershellforsecurityassessments-141128071934-conversion-gate01/85/An-Introduction-to-PowerShell-for-Security-Assessments-12-320.jpg)