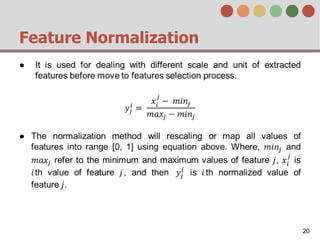
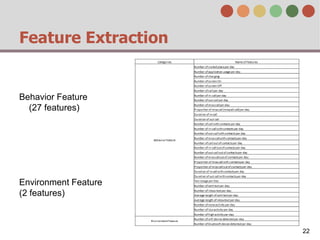
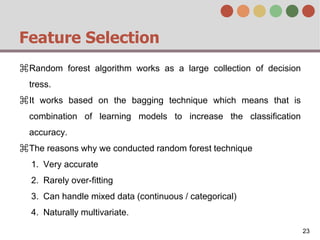
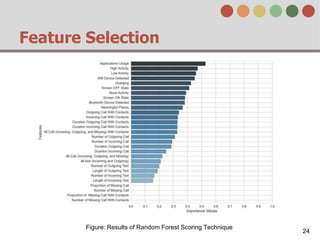
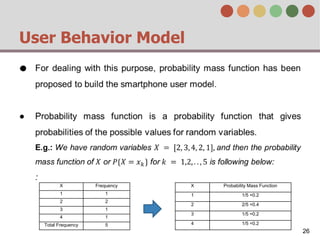
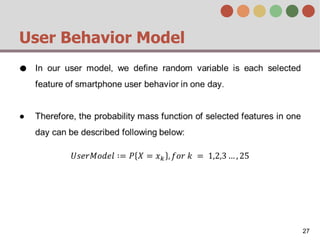
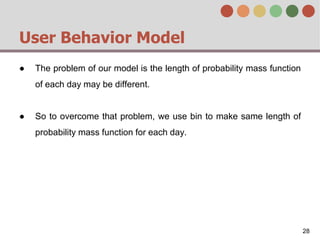
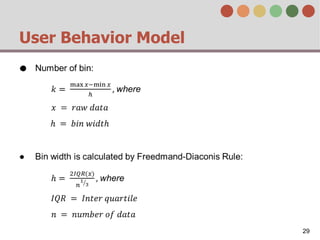
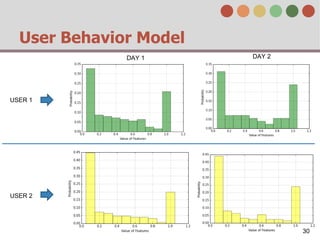
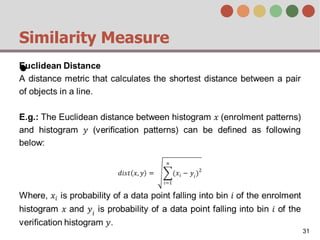
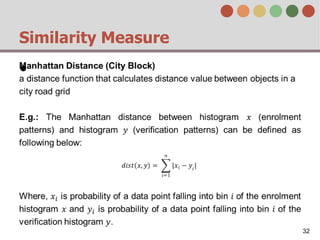
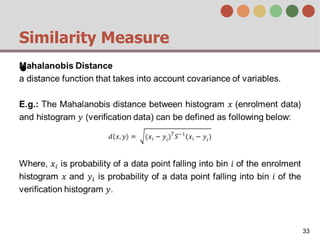
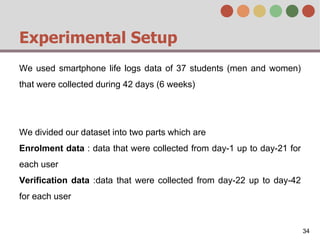
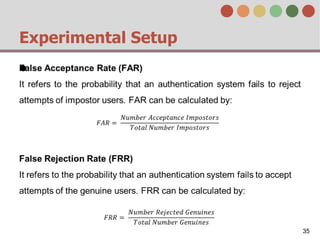
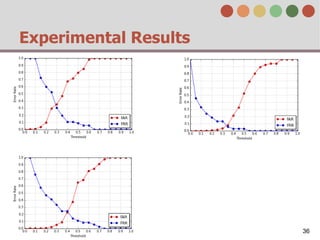
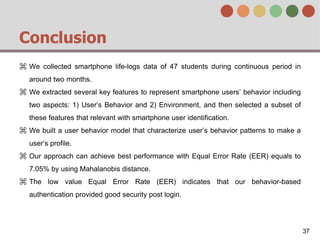
This document describes a behavior-based authentication system for smartphones using life-log data. It collects data from smartphone sensors over 2 months from 47 students. It extracts features related to user behavior and environment, selects relevant features using random forest, builds a user behavior model based on probability distributions of daily behaviors, and measures similarity between models using Mahalanobis distance. Experimental results using data from 37 students over 6 weeks achieved an equal error rate of 7.05%, indicating good post-login security from the behavior-based authentication system.



![Introduction (Cont’d)
Related Works:
1. Implicit Authentication for Mobile Devices [2009]
2. Implicit Authentication Through Learning User Behavior [2011]
3. Multi-sensor Authentication to Improve Smartphone Security
[2015]
4. Continuous Touchscreen Mobile Authentication Using Several
Gestures [2016]
6](https://image.slidesharecdn.com/thesispresentationfinal-180724024922/85/Behavior-Based-Authentication-System-Based-on-Smartphone-Life-Logs-Data-6-320.jpg)