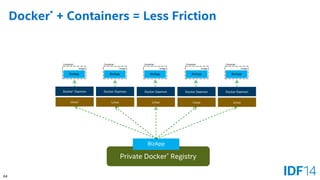
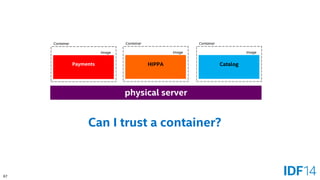
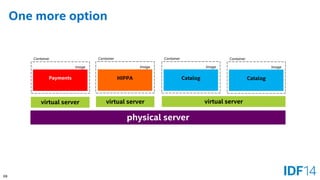
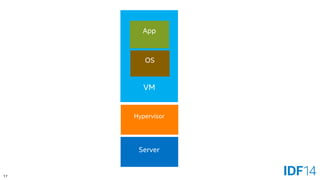
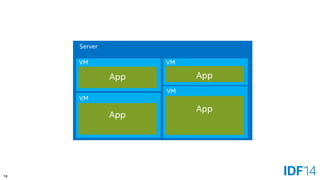
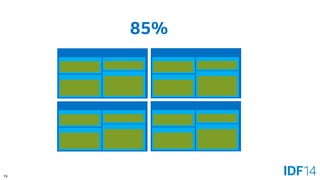
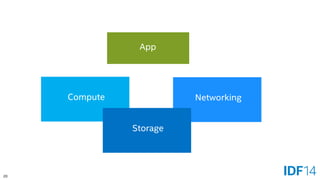
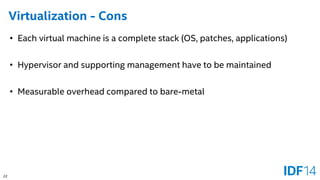
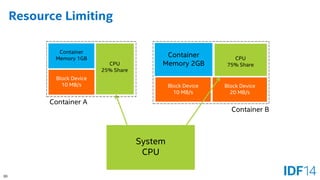
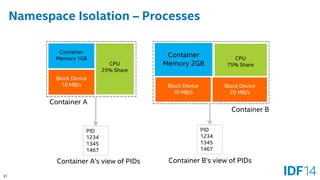
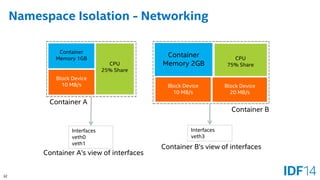
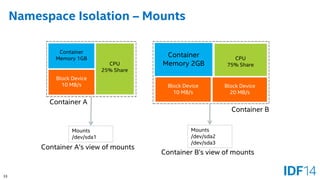
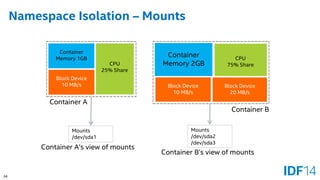
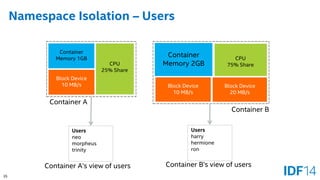
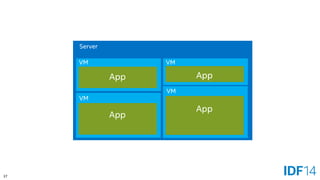
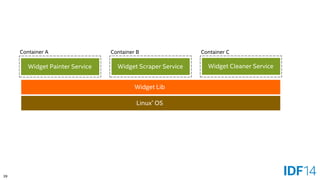
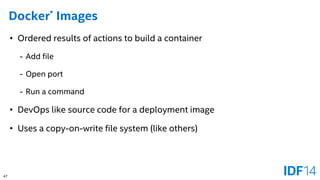
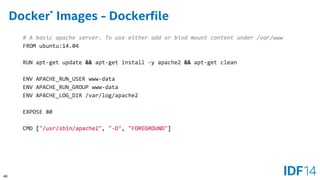
The document discusses the evolution and advantages of cloud application deployment through bare-metal, virtualization, and containerization, specifically highlighting Docker as a management tool for containers. It outlines key pros and cons of both virtualization and container technologies, emphasizing the rapid lifecycle and performance benefits of containers but also acknowledging their security vulnerabilities. Additionally, the document introduces Intel's contributions towards enhancing container capabilities, suggesting a future coexistence of these technologies in IT environments.




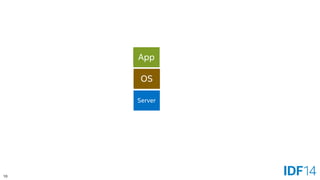



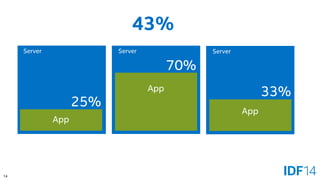
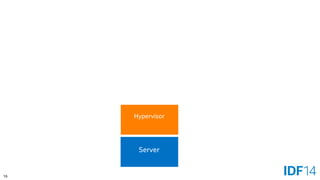







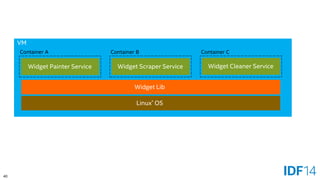





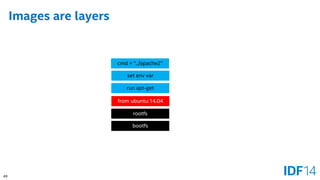

![55
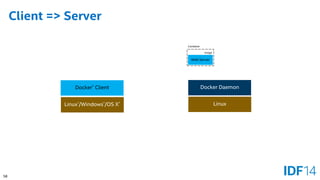
Client => Server
Docker Daemon
Linux
Docker*Client
Linux*/Windows*/OS X*
[docker run web-server]
Container
Web Server
Image](https://image.slidesharecdn.com/sf14dats004100pbare-metaldockerandvirt-140909045046-phpapp01/85/Bare-metal-Docker-Containers-and-Virtualization-The-Growing-Choices-for-Cloud-Applications-55-320.jpg)
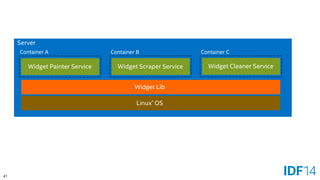
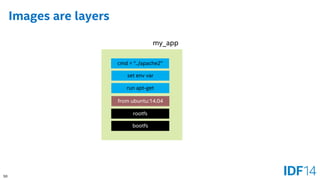
![56
Client => Server
Docker Daemon
Linux
Docker*Client
Linux*/Windows*/OS X*
[docker run database]
Container
Web Server
Image
Container
Database
Image](https://image.slidesharecdn.com/sf14dats004100pbare-metaldockerandvirt-140909045046-phpapp01/85/Bare-metal-Docker-Containers-and-Virtualization-The-Growing-Choices-for-Cloud-Applications-56-320.jpg)
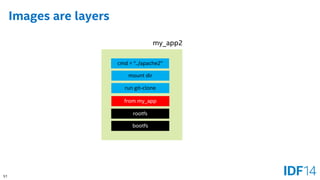
![57
Client => Server
Docker Daemon
Linux
Docker*Client
Linux*/Windows*/OS X*
[docker stop database]
Container
Web Server
Image
Container
Database
Image](https://image.slidesharecdn.com/sf14dats004100pbare-metaldockerandvirt-140909045046-phpapp01/85/Bare-metal-Docker-Containers-and-Virtualization-The-Growing-Choices-for-Cloud-Applications-57-320.jpg)