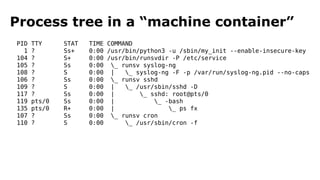
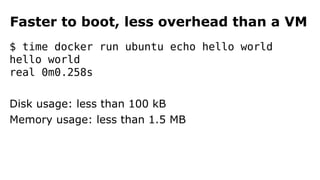
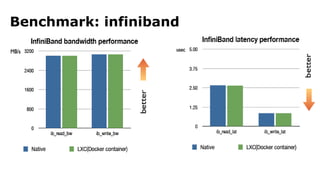
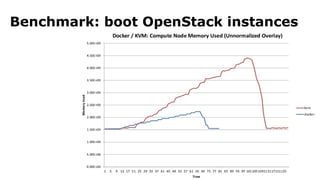
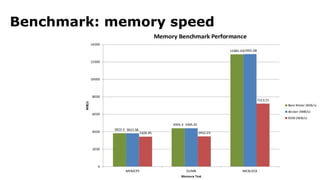
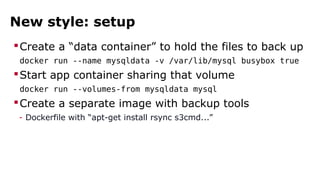
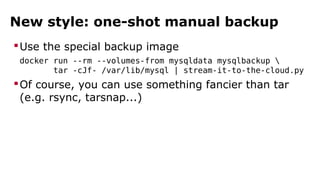
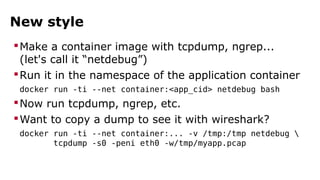
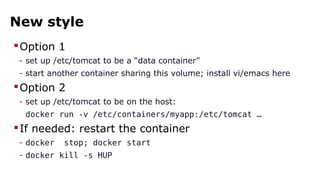
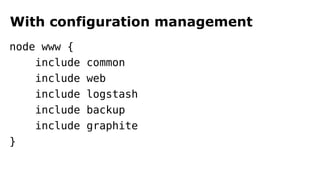
The document discusses containerization, emphasizing how containers function as lightweight virtual machines with distinct advantages over traditional VMs, such as quicker boot times and reduced resource overhead. It outlines various operational benefits, including enhanced isolation, efficient inter-container communication, and simplified management of backups and logging through dedicated containers. The text also touches on the concepts of immutable infrastructure and micro-service architecture, illustrating how containers facilitate easier deployment and management of applications.