Puppet is an open source configuration management tool that has been available since 2005. It uses a desired state configuration language to define how nodes should be configured. Puppet combines node facts, configuration data, and the node model to generate a catalog that is applied at regular intervals to manage nodes. The HashiCorp suite includes tools like Packer, Vagrant, Terraform, Consul, and Vault that can be used along with Puppet for tasks like building images, provisioning VMs, managing infrastructure as code, service discovery, and secrets management.






![PackerPacker
{{
"builders": ["builders": [
{{
"type": "azure-arm","type": "azure-arm",
......
}}
],],
"provisioners": ["provisioners": [
{{
"scripts": ["scripts": [
"scripts/common/consul_install.sh","scripts/common/consul_install.sh",
"scripts/common/puppet_install.sh""scripts/common/puppet_install.sh"
],],
"type": "shell","type": "shell",
}}
]]
}}
$ packer build template.json$ packer build template.json](https://image.slidesharecdn.com/bycwpahshashimeetup2019-190715164622/75/Puppet-and-the-HashiCorp-Suite-7-2048.jpg)
![Packer & PuppetPacker & Puppet
https://github.com/petems/puppet-install-shellhttps://github.com/petems/puppet-install-shell
$ ./puppet_install.sh [-p] [-v version] …$ ./puppet_install.sh [-p] [-v version] …](https://image.slidesharecdn.com/bycwpahshashimeetup2019-190715164622/75/Puppet-and-the-HashiCorp-Suite-8-2048.jpg)

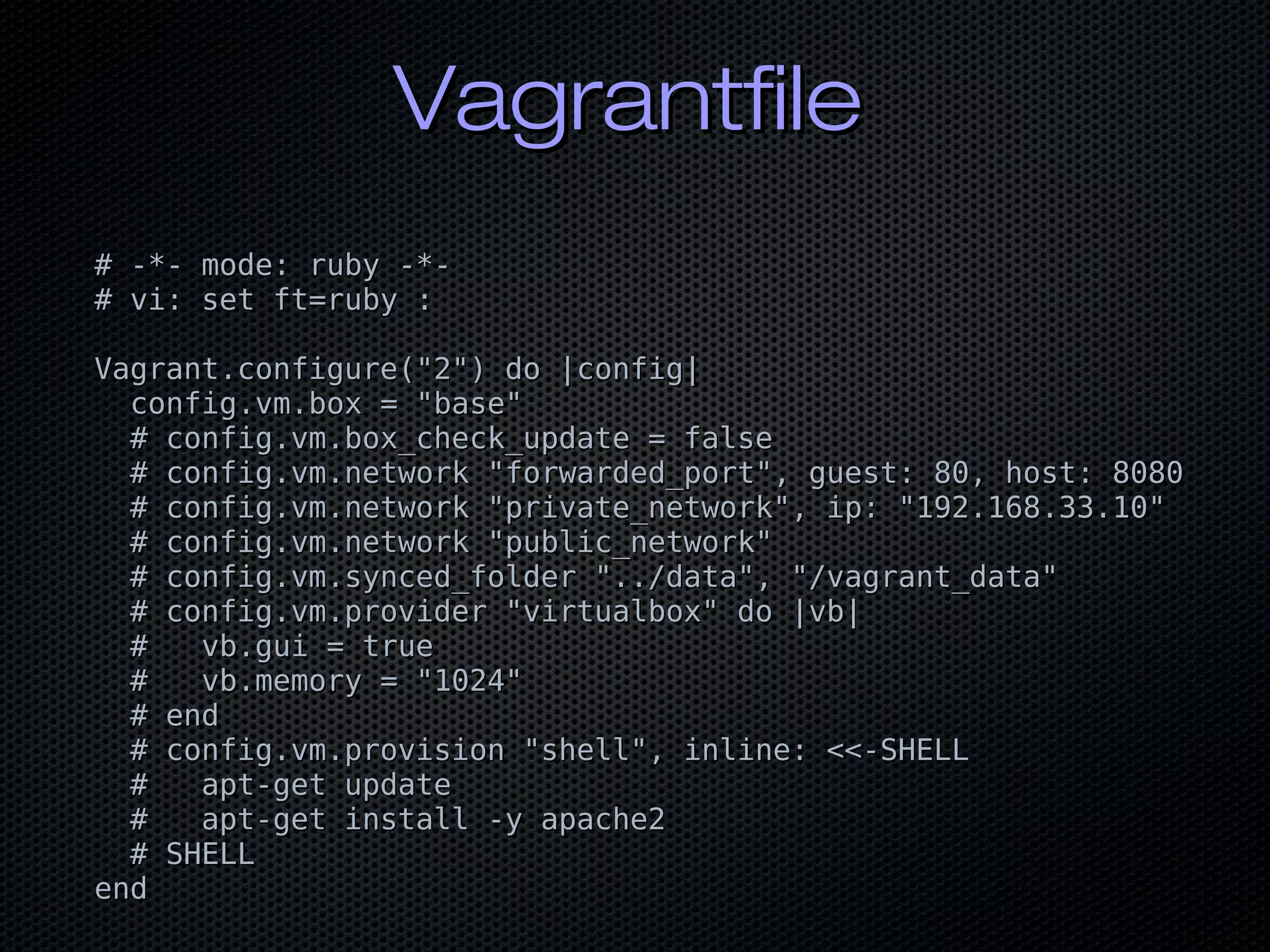

![Vagrant & PuppetVagrant & Puppet
cat Vagrantfilecat Vagrantfile
casecase nodenode[["provision_type""provision_type"]]
whenwhen 'masterless''masterless'
srvsrv.vm.synced_folder.vm.synced_folder ""#{environment}#{environment}/hieradata"/hieradata",,
"/etc/puppetlabs/code/environments/"/etc/puppetlabs/code/environments/#{environment}#{environment}/hieradata"/hieradata"
srvsrv.vm.provision :puppet.vm.provision :puppet dodo ||puppetpuppet||
puppetpuppet.environment_path =.environment_path = ".""."
puppetpuppet.hiera_config_path =.hiera_config_path = ""#{environment}#{environment}/hiera.yaml"/hiera.yaml"
endend
$ vagrant (up,halt,destroy)$ vagrant (up,halt,destroy)](https://image.slidesharecdn.com/bycwpahshashimeetup2019-190715164622/75/Puppet-and-the-HashiCorp-Suite-12-2048.jpg)
![Vagrant & PuppetVagrant & Puppet
cat Vagrantfilecat Vagrantfile
casecase nodenode[["provision_type""provision_type"]]
whenwhen 'puppet_agent''puppet_agent'
srvsrv.vm.provision.vm.provision "puppet_server" do"puppet_server" do ||puppetpuppet||
puppetpuppet.options =.options = "-t --environment"-t --environment #{environment}#{environment}""
puppetpuppet.puppet_server =.puppet_server = "puppetmaster."puppetmaster.#{environment}#{environment}.vagrant".vagrant"
endend
srv.trigger.after :destroy do |trigger|srv.trigger.after :destroy do |trigger|
trigger.name = "Cleaning puppet certificate"trigger.name = "Cleaning puppet certificate"
trigger.run =trigger.run = {inline: "vagrant ssh puppetmaster -c 'sudo{inline: "vagrant ssh puppetmaster -c 'sudo
/opt/puppetlabs/bin/puppetserver ca clean --certname #{node["hostname"]}'"}/opt/puppetlabs/bin/puppetserver ca clean --certname #{node["hostname"]}'"}
endend
$ vagrant (up,halt,destroy)$ vagrant (up,halt,destroy)](https://image.slidesharecdn.com/bycwpahshashimeetup2019-190715164622/75/Puppet-and-the-HashiCorp-Suite-13-2048.jpg)


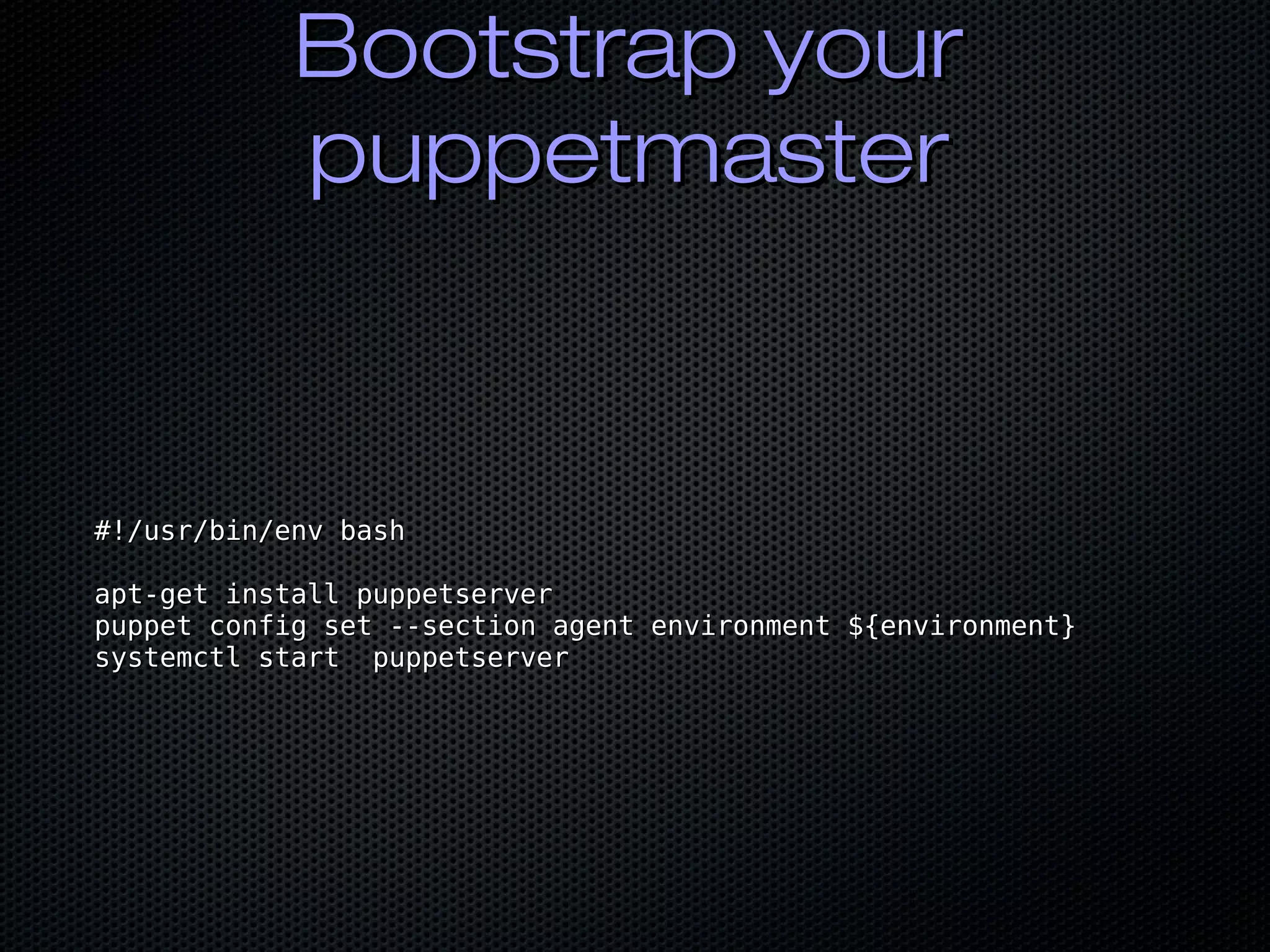
![Lets magic a nodeLets magic a node
resourceresource "azurerm_virtual_machine" "puppetmaster" {"azurerm_virtual_machine" "puppetmaster" {
name = "vm-${var.node_name}"name = "vm-${var.node_name}"
location = "${var.azure_region_name}"location = "${var.azure_region_name}"
resource_group_name = "${var.resource_group}"resource_group_name = "${var.resource_group}"
network_interface_ids = ["$network_interface_ids = ["$
{azurerm_network_interface.puppetmaster.id}"]{azurerm_network_interface.puppetmaster.id}"]
vm_size = "${var.vm_size}"vm_size = "${var.vm_size}"
storage_image_referencestorage_image_reference {{
id = "${var.packerimage_id}" # ← your packer image idid = "${var.packerimage_id}" # ← your packer image id
}}
storage_os_diskstorage_os_disk {{
......
}}
os_profileos_profile {{
......
}}
}}](https://image.slidesharecdn.com/bycwpahshashimeetup2019-190715164622/75/Puppet-and-the-HashiCorp-Suite-17-2048.jpg)

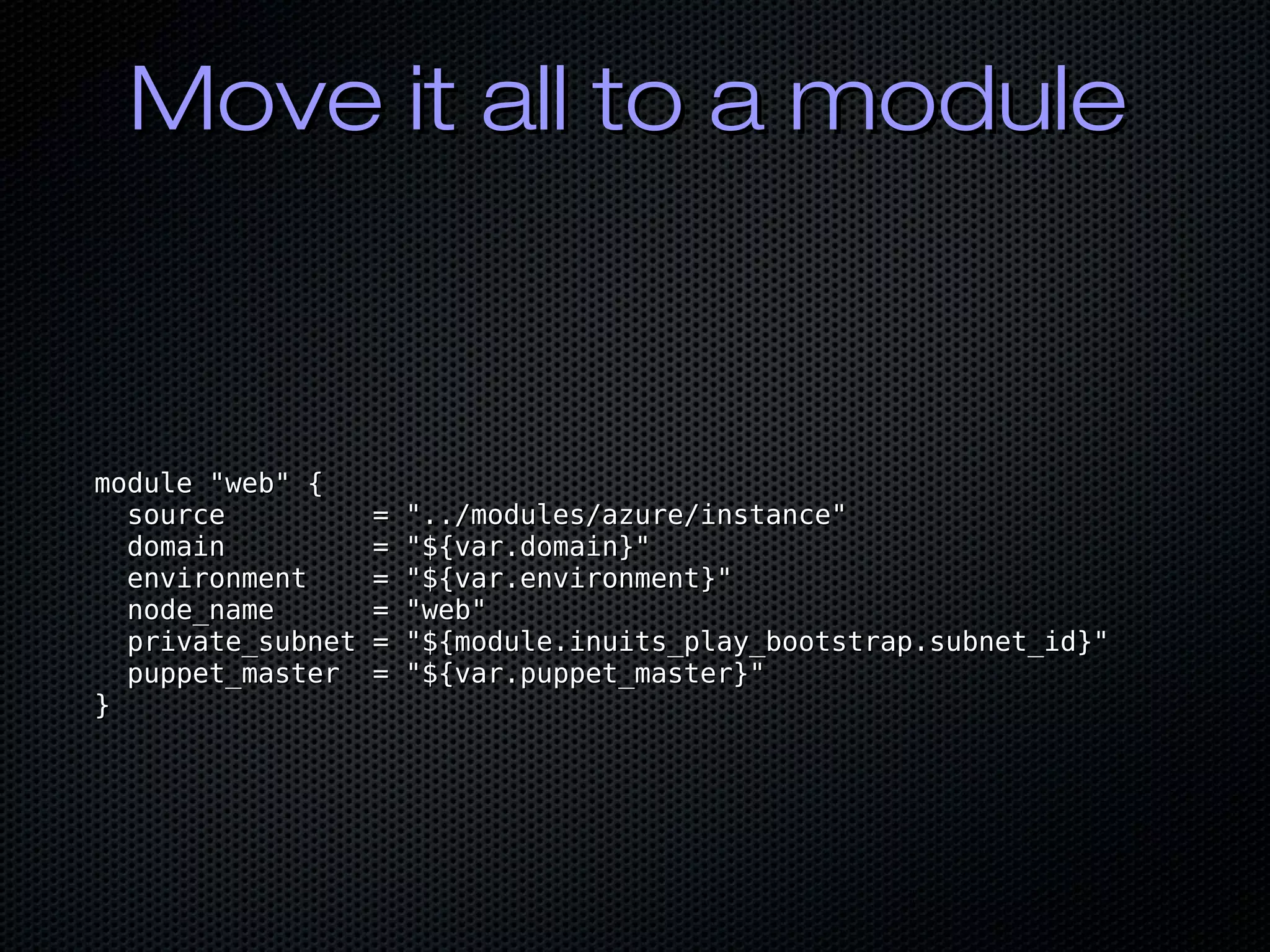




![Geolocation StuffGeolocation Stuff
consul_prepared_query { 'consul_prepared_query { 'puppetmasterpuppetmaster':':
ensure => 'present',ensure => 'present',
service_name => 'service_name => 'puppetmasterpuppetmaster',',
service_failover_n => 1,service_failover_n => 1,
service_failover_dcs => [ 'failover', 'dr' ],service_failover_dcs => [ 'failover', 'dr' ],
service_only_passing => true,service_only_passing => true,
service_tags => [ 'tag1', 'tag2' ],service_tags => [ 'tag1', 'tag2' ],
ttl => 10,ttl => 10,
}}
dig @127.0.0.1 -p 8600 puppetmaster.query.consul ANYdig @127.0.0.1 -p 8600 puppetmaster.query.consul ANY](https://image.slidesharecdn.com/bycwpahshashimeetup2019-190715164622/75/Puppet-and-the-HashiCorp-Suite-26-2048.jpg)
![Fast ExportedFast Exported
ResourcesResources
::consul::watch { 'detect_backend_changes':::consul::watch { 'detect_backend_changes':
type => 'service',type => 'service',
handler => '/usr/bin/runpuppet.sh',handler => '/usr/bin/runpuppet.sh',
service => 'node_exporter',service => 'node_exporter',
passingonly => true,passingonly => true,
require => File['/usr/bin/runpuppet.sh'],require => File['/usr/bin/runpuppet.sh'],
}}](https://image.slidesharecdn.com/bycwpahshashimeetup2019-190715164622/75/Puppet-and-the-HashiCorp-Suite-29-2048.jpg)

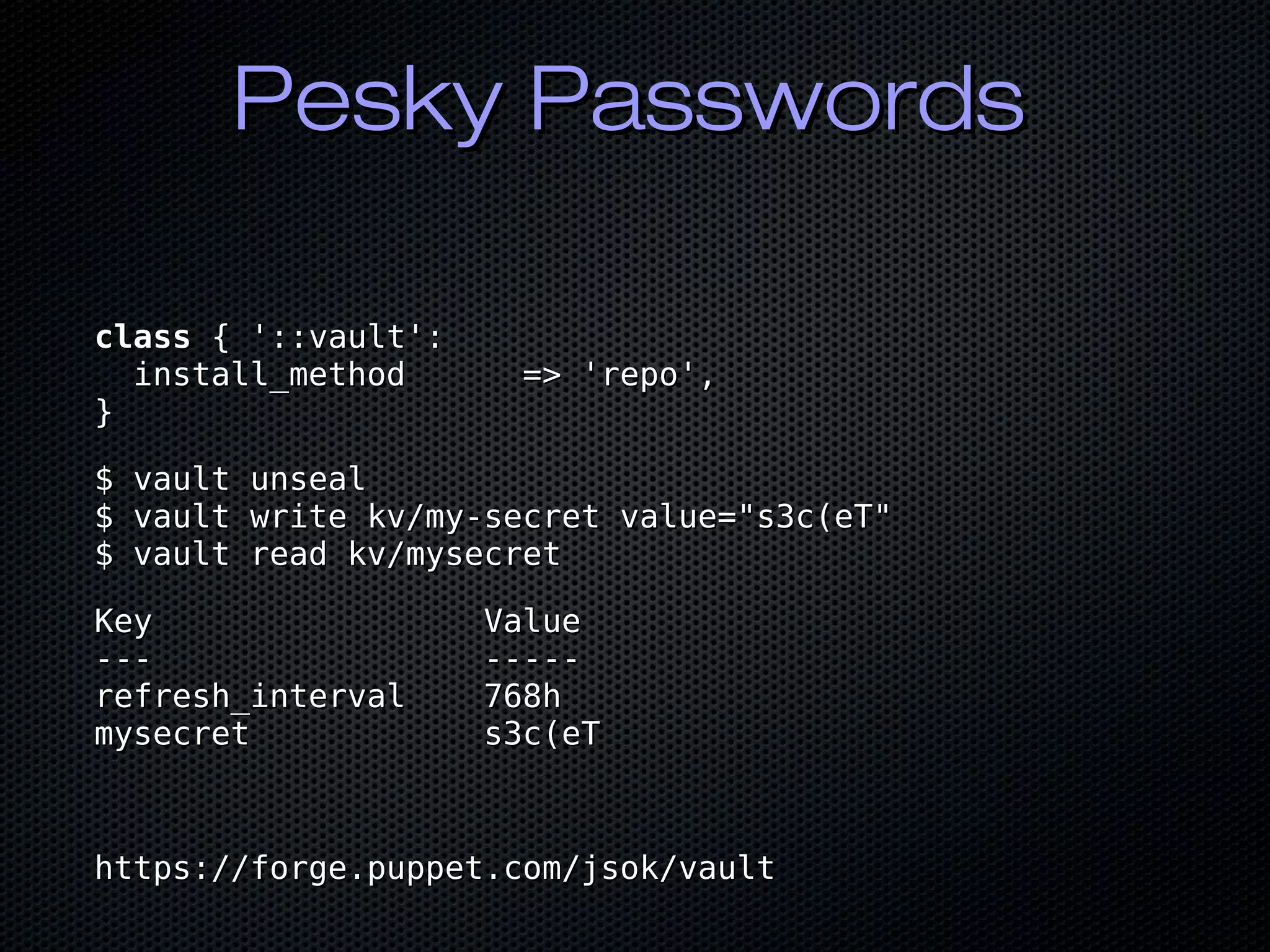
![Pesky PasswordsPesky Passwords
class profiles::security::vault (class profiles::security::vault (
$config_dir = '/etc/vault.d',$config_dir = '/etc/vault.d',
$enable_ui = true,$enable_ui = true,
Variant[Hash, Array[Hash]] $listener = {Variant[Hash, Array[Hash]] $listener = {
'tcp' => {'tcp' => {
'address' => '127.0.0.1:8200','address' => '127.0.0.1:8200',
'cluster_address' => '127.0.0.1:8201','cluster_address' => '127.0.0.1:8201',
'tls_disable' => 1,'tls_disable' => 1,
},},
},},
Hash $storage = { 'consul' => { 'address' => '127.0.0.1:8500', 'path' => 'vault/' }},Hash $storage = { 'consul' => { 'address' => '127.0.0.1:8500', 'path' => 'vault/' }},
String $version = '1.1.3',String $version = '1.1.3',
){){
class {'vault':class {'vault':
config_dir => $config_dir,config_dir => $config_dir,
enable_ui => $enable_ui,enable_ui => $enable_ui,
listener => $listener,listener => $listener,
storage => $storage,storage => $storage,
version => $version,version => $version,
}}
https://forge.puppet.com/jsok/vaulthttps://forge.puppet.com/jsok/vault](https://image.slidesharecdn.com/bycwpahshashimeetup2019-190715164622/75/Puppet-and-the-HashiCorp-Suite-31-2048.jpg)

![Puppet5Puppet5
classclass profiles::database::mysql (profiles::database::mysql (
Sensitive $root_password,Sensitive $root_password,
) {) {
classclass { '::mysql::server':{ '::mysql::server':
root_password => $root_password.unwrap,root_password => $root_password.unwrap,
}}
notice($root_password)notice($root_password)
}}
Notice: Scope(Class[main]): Sensitive [value redacted]Notice: Scope(Class[main]): Sensitive [value redacted]](https://image.slidesharecdn.com/bycwpahshashimeetup2019-190715164622/75/Puppet-and-the-HashiCorp-Suite-35-2048.jpg)
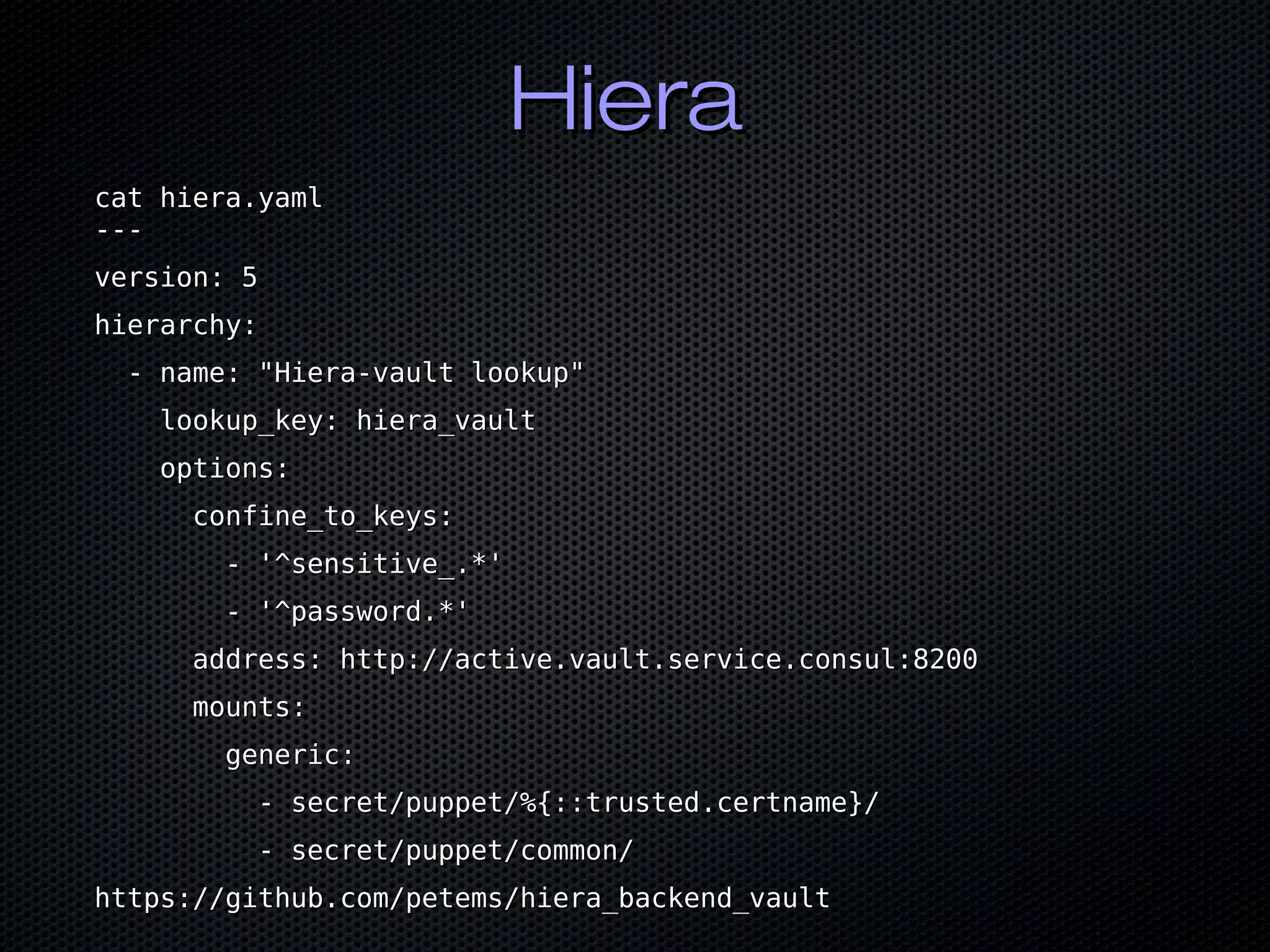
![Puppet 6Puppet 6
$root_password = Deferred($root_password = Deferred(
'vault_lookup::lookup','vault_lookup::lookup',
["password/mysql"],["password/mysql"],
''https://active.vault.service.consul:8200https://active.vault.service.consul:8200',',
))
classclass { '::mysql::server':{ '::mysql::server':
root_password => $root_password,root_password => $root_password,
}}](https://image.slidesharecdn.com/bycwpahshashimeetup2019-190715164622/75/Puppet-and-the-HashiCorp-Suite-36-2048.jpg)




![Bolt && TerraformBolt && Terraform
~/terraform_provision/inventory.yaml~/terraform_provision/inventory.yaml
groups:groups:
- name: terraform- name: terraform
nodes: [] # This will be populated by the Bolt plannodes: [] # This will be populated by the Bolt plan
config:config:
transport: sshtransport: ssh
ssh:ssh:
private-key: ~/.ssh/id_rsa-phraselessprivate-key: ~/.ssh/id_rsa-phraseless
user: ubuntuuser: ubuntu
host-key-check: falsehost-key-check: false](https://image.slidesharecdn.com/bycwpahshashimeetup2019-190715164622/75/Puppet-and-the-HashiCorp-Suite-41-2048.jpg)
![Bolt && TerraformBolt && Terraform
~/terraform_provision/plans/init.pp~/terraform_provision/plans/init.pp
plan terraform_provision(String $tf_path) {plan terraform_provision(String $tf_path) {
$localhost = get_targets('localhost')$localhost = get_targets('localhost')
$ip_string = run_command("cd ${$tf_path} && terraform output interal_ips"$ip_string = run_command("cd ${$tf_path} && terraform output interal_ips"
$localhost).map |$r| { $r['stdout'] }$localhost).map |$r| { $r['stdout'] }
$ips = Array($ip_string).map |$ip| { $ip.strip }$ips = Array($ip_string).map |$ip| { $ip.strip }
# Turn IPs into Bolt targets, and add to inventory# Turn IPs into Bolt targets, and add to inventory
$targets = $ips.map |$ip| {$targets = $ips.map |$ip| {
Target.new("${$ip}").add_to_group('terraform')Target.new("${$ip}").add_to_group('terraform')
}}
# Deploy website# Deploy website
apply_prep($targets)apply_prep($targets)
apply($targets, _run_as => 'root') {}apply($targets, _run_as => 'root') {}
return $ipsreturn $ips
}}](https://image.slidesharecdn.com/bycwpahshashimeetup2019-190715164622/75/Puppet-and-the-HashiCorp-Suite-42-2048.jpg)

![Icinga HostIcinga Host
resource "aws_instance" "node1" {resource "aws_instance" "node1" {
ami = "${var.ami_id}"ami = "${var.ami_id}"
instance_type = "${var.ami_size}"instance_type = "${var.ami_size}"
key_name = "${var.key_pair_name}"key_name = "${var.key_pair_name}"
subnet_id = "${var.private_subnet}"subnet_id = "${var.private_subnet}"
vpc_security_group_ids = ["${var.security_group_id}"]vpc_security_group_ids = ["${var.security_group_id}"]
}}
resourceresource "icinga2_host" "node1" {"icinga2_host" "node1" {
hostname = "hostname = "node1"node1"
address = "address = "${aws_instance.instance.private_ip}${aws_instance.instance.private_ip}""
check_command = "hostalive"check_command = "hostalive"
varsvars {{
os = "linux"os = "linux"
}}
}}](https://image.slidesharecdn.com/bycwpahshashimeetup2019-190715164622/75/Puppet-and-the-HashiCorp-Suite-45-2048.jpg)
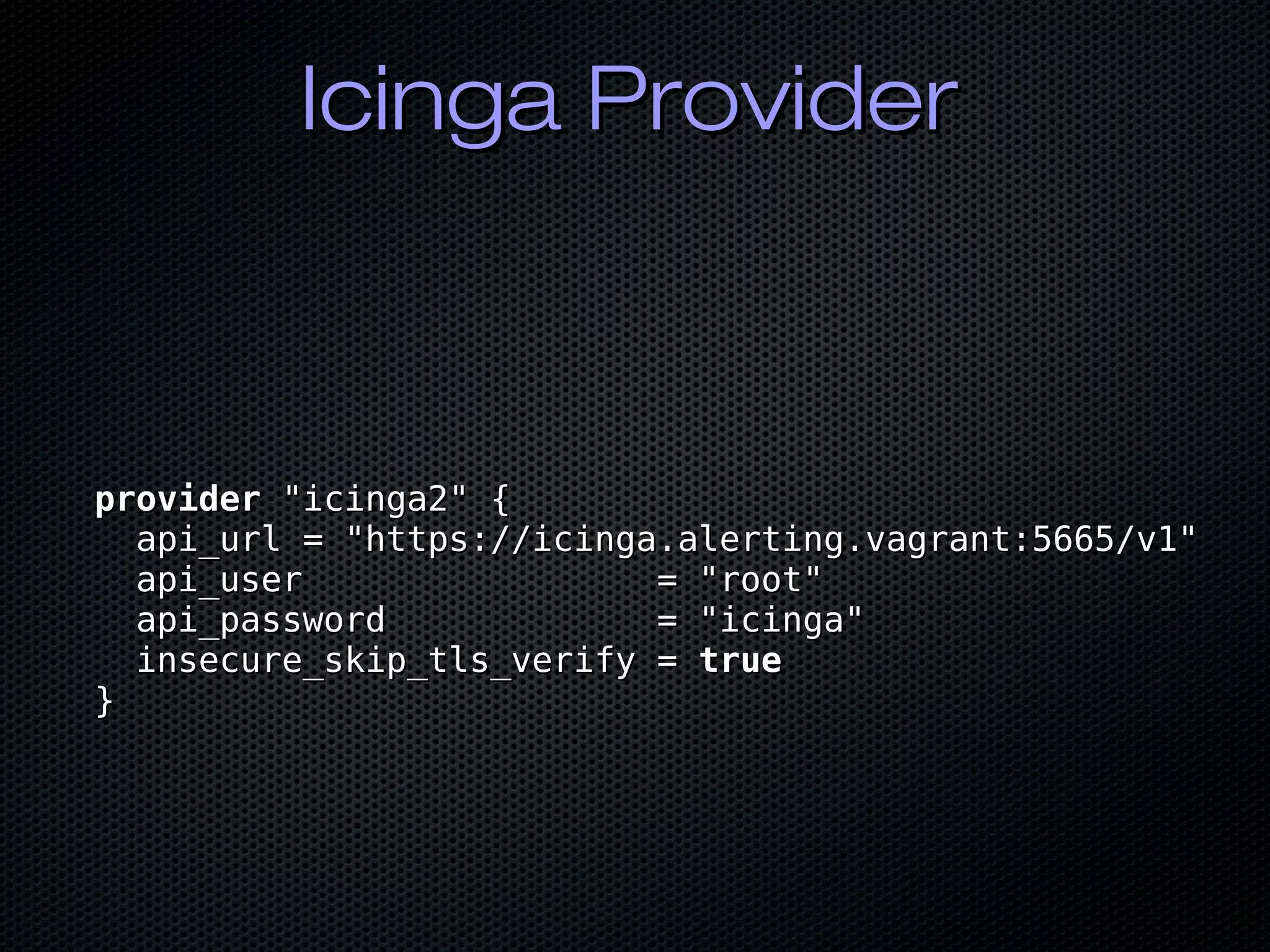
![Check CommandCheck Command
resourceresource "icinga2_checkcommand" "apache_status" {"icinga2_checkcommand" "apache_status" {
name = "apache_status"name = "apache_status"
templates = ["apache-status", "plugin-check-command",templates = ["apache-status", "plugin-check-command",
"plugin-check-command", "ipv4-or-ipv6"]"plugin-check-command", "ipv4-or-ipv6"]
command =command =
"/usr/lib64/nagios/plugins/check_apache_status.pl""/usr/lib64/nagios/plugins/check_apache_status.pl"
arguments = {arguments = {
"-H" = "$apache_status_address$""-H" = "$apache_status_address$"
"-c" = "$apache_status_critical$""-c" = "$apache_status_critical$"
"-p" = "$apache_status_port$""-p" = "$apache_status_port$"
}}
}}
resourceresource "icinga2_service" "my-service" {"icinga2_service" "my-service" {
name = "ssh"name = "ssh"
hostname = "c1-mysql-1"hostname = "c1-mysql-1"
check_command = "ssh"check_command = "ssh"
}}](https://image.slidesharecdn.com/bycwpahshashimeetup2019-190715164622/75/Puppet-and-the-HashiCorp-Suite-46-2048.jpg)
![NotificationsNotifications
resource "icinga2_user" "user" {resource "icinga2_user" "user" {
name = "terraform"name = "terraform"
email = "terraform@dev.null"email = "terraform@dev.null"
}}
resourceresource "icinga2_notification" "host-notification" {"icinga2_notification" "host-notification" {
hostname = "docker-icinga2"hostname = "docker-icinga2"
command = "mail-host-notification"command = "mail-host-notification"
users = ["user"]users = ["user"]
}}
resourceresource "icinga2_notification" "ping-service-notification" {"icinga2_notification" "ping-service-notification" {
hostname = "docker-icinga2"hostname = "docker-icinga2"
command = "mail-service-notification"command = "mail-service-notification"
users = ["user"]users = ["user"]
servicename = "ping"servicename = "ping"
}}](https://image.slidesharecdn.com/bycwpahshashimeetup2019-190715164622/75/Puppet-and-the-HashiCorp-Suite-47-2048.jpg)
![Other ResourcesOther Resources
resourceresource "icinga2_checkcommand" "apache_status" {"icinga2_checkcommand" "apache_status" {
name = "apache_status"name = "apache_status"
templates = ["apache-status", "plugin-check-command",templates = ["apache-status", "plugin-check-command",
"plugin-check-command", "ipv4-or-ipv6"]"plugin-check-command", "ipv4-or-ipv6"]
command =command =
"/usr/lib64/nagios/plugins/check_apache_status.pl""/usr/lib64/nagios/plugins/check_apache_status.pl"
arguments = {arguments = {
"-H" = "$apache_status_address$""-H" = "$apache_status_address$"
"-c" = "$apache_status_critical$""-c" = "$apache_status_critical$"
"-p" = "$apache_status_port$""-p" = "$apache_status_port$"
}}
}}](https://image.slidesharecdn.com/bycwpahshashimeetup2019-190715164622/75/Puppet-and-the-HashiCorp-Suite-48-2048.jpg)


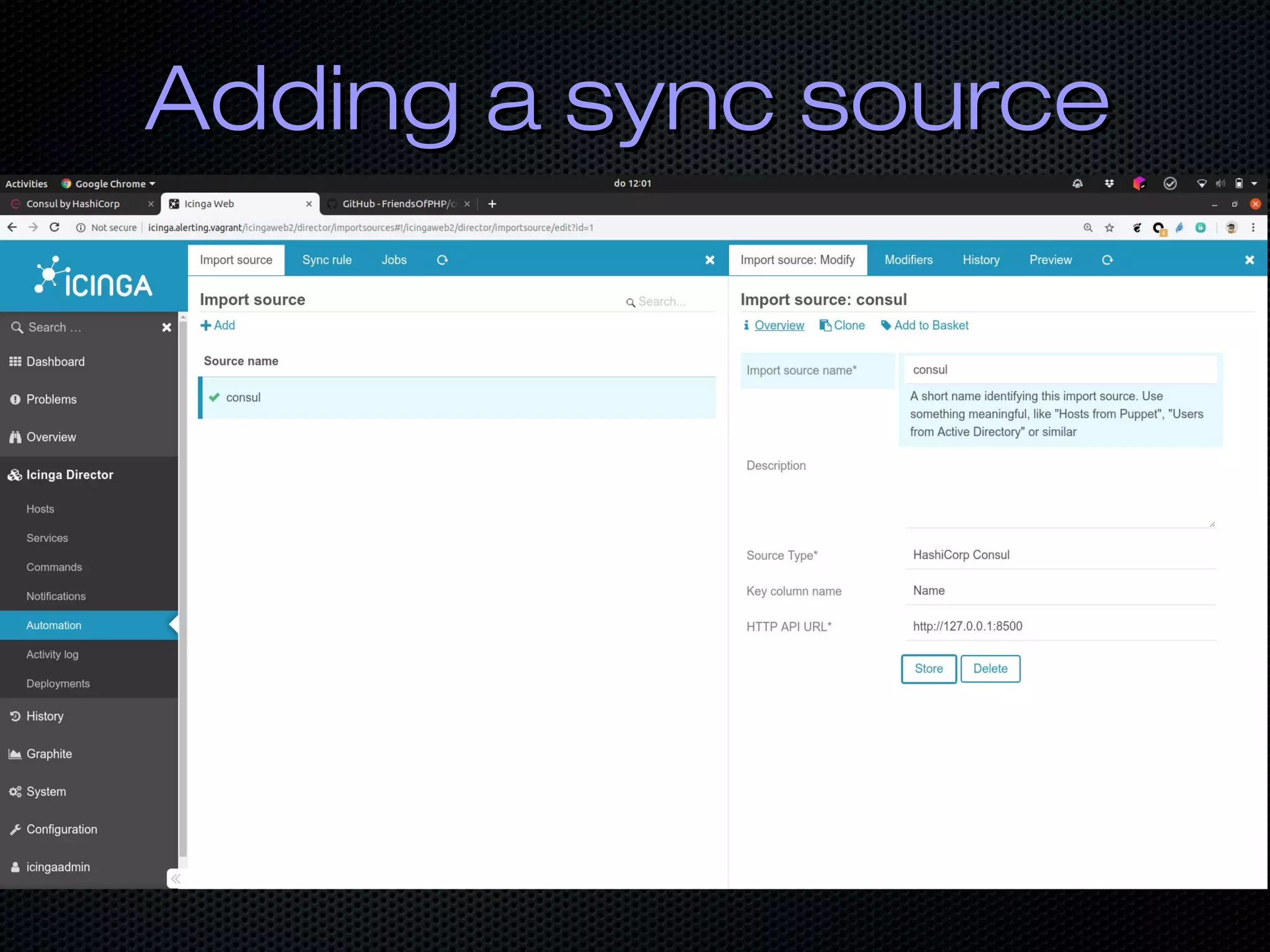
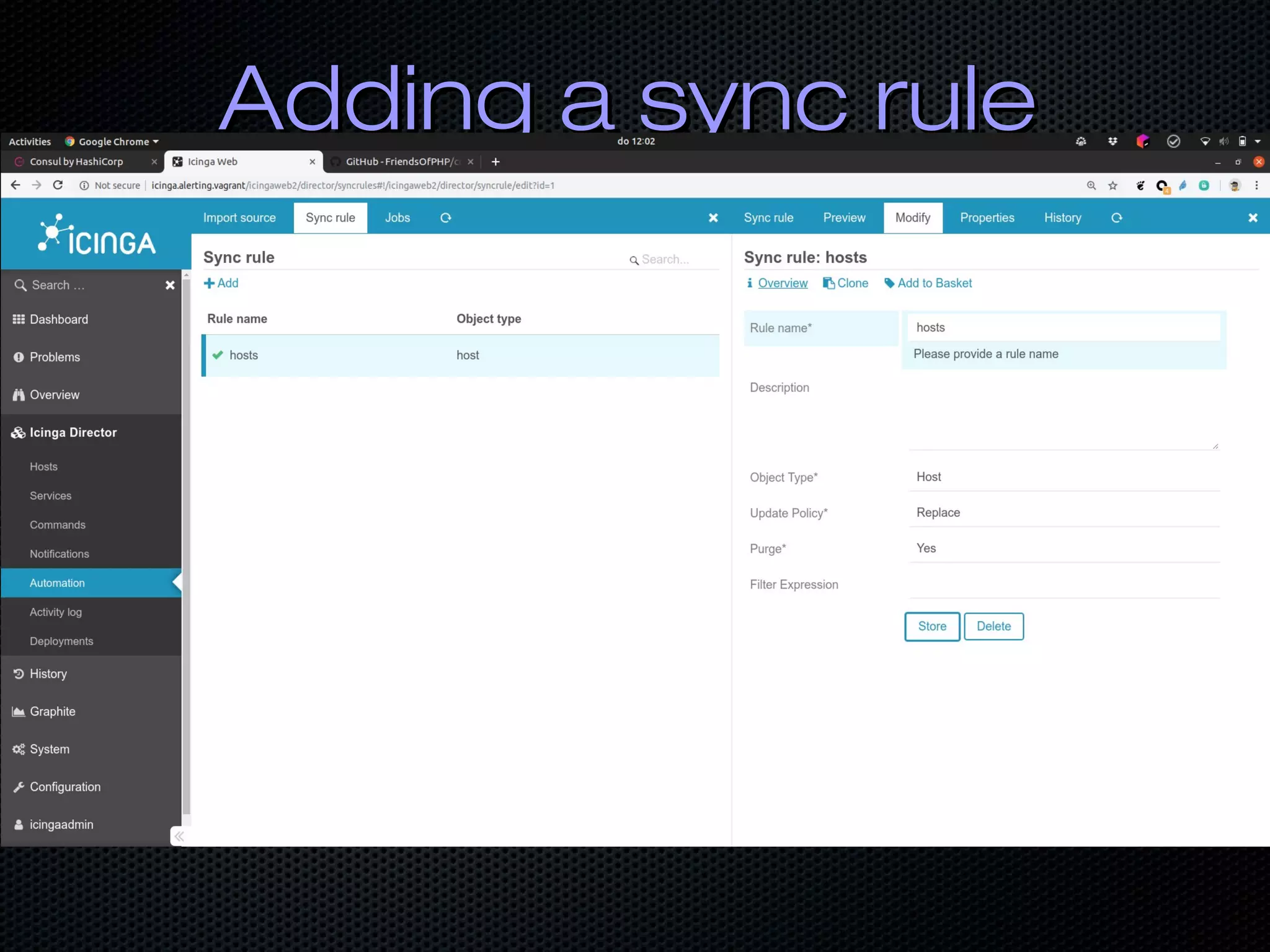

![Fast FeedbackFast Feedback
file { 'Director Sync and Deploy':file { 'Director Sync and Deploy':
path => '/usr/local/bin/director_sync_and_deploy.sh',path => '/usr/local/bin/director_sync_and_deploy.sh',
source =>source =>
'puppet:///modules/profiles/monitoring/icinga2/director_sync_'puppet:///modules/profiles/monitoring/icinga2/director_sync_
and_deploy.sh',and_deploy.sh',
owner => 'consul',owner => 'consul',
group => 'consul',group => 'consul',
mode => '0744',mode => '0744',
}}
::consul::watch { 'director_import':::consul::watch { 'director_import':
type => 'service',type => 'service',
handler =>handler =>
'/usr/local/bin/director_sync_and_deploy.sh','/usr/local/bin/director_sync_and_deploy.sh',
service => 'node_exporter',service => 'node_exporter',
passingonly =>passingonly => truetrue,,
require => File['Director Sync and Deploy'],require => File['Director Sync and Deploy'],
}}](https://image.slidesharecdn.com/bycwpahshashimeetup2019-190715164622/75/Puppet-and-the-HashiCorp-Suite-54-2048.jpg)
