Embed presentation
Download to read offline
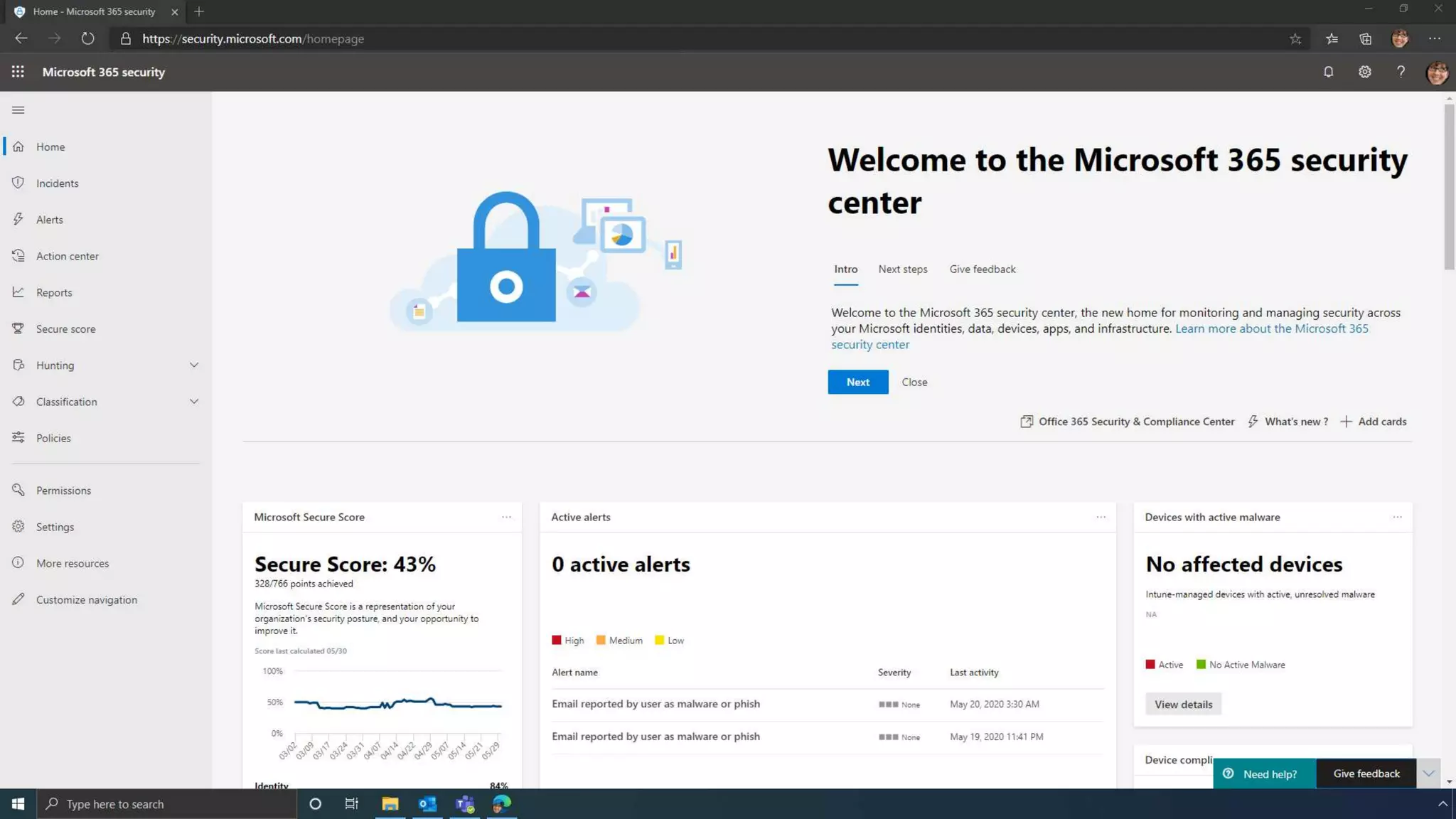
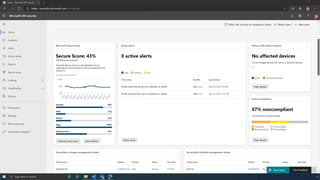
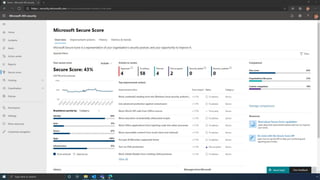
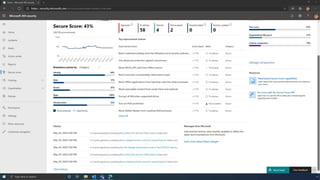
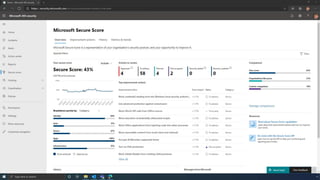
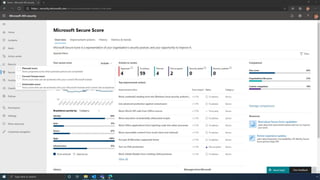
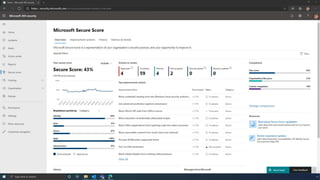
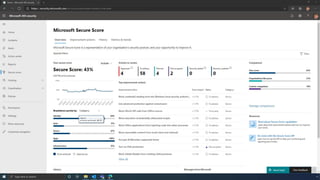
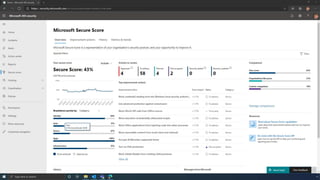
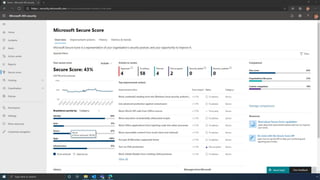
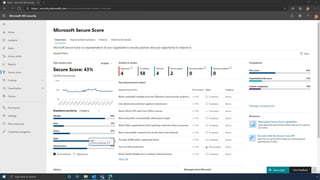
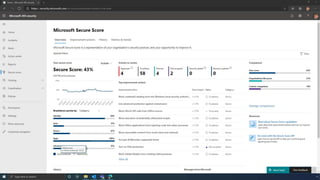
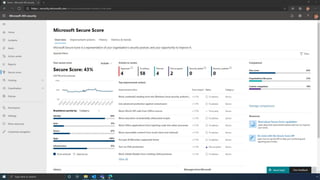
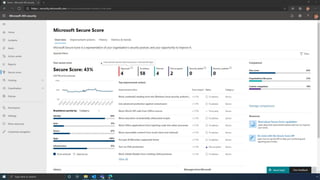
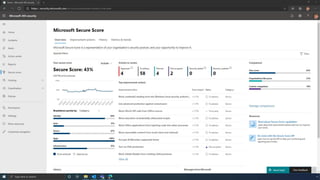
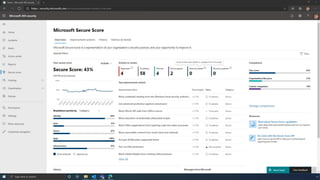
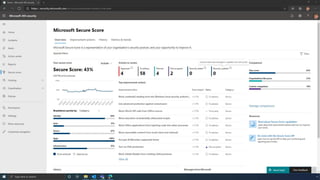
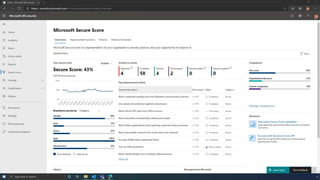
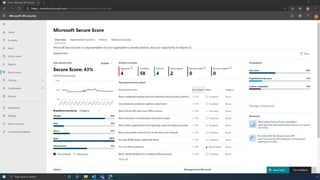
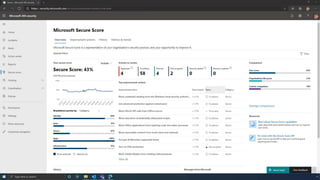
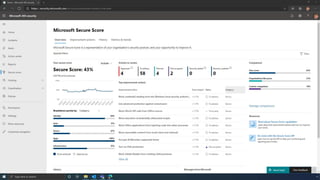
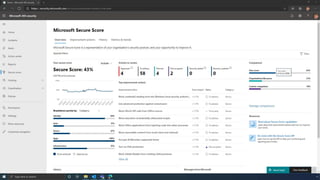
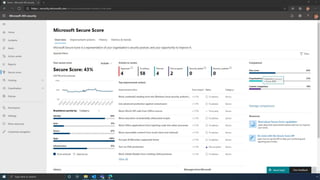
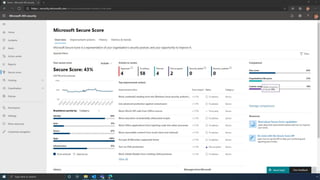
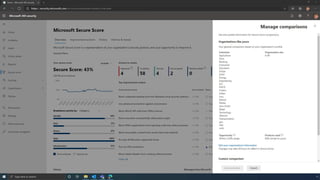
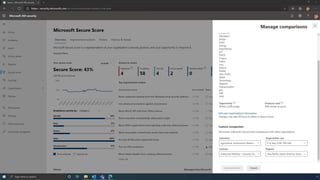
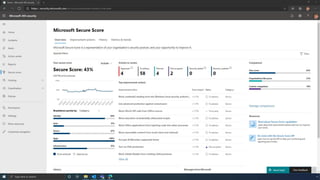

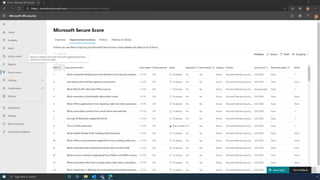
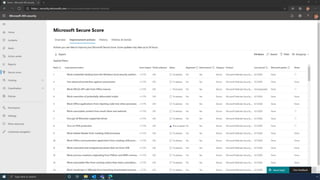
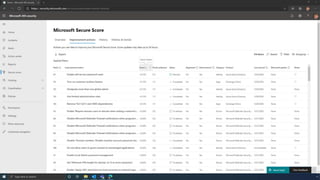
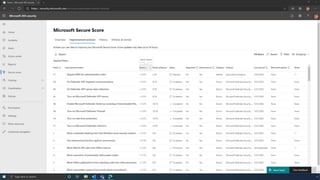
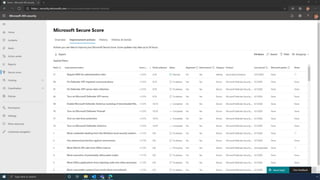
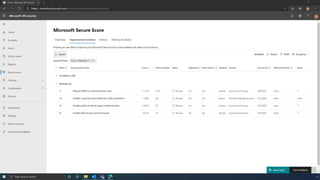

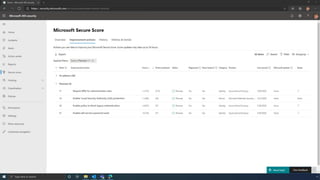
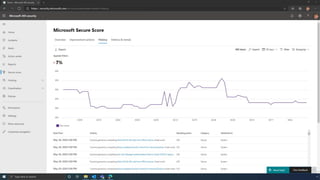
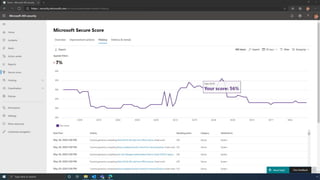
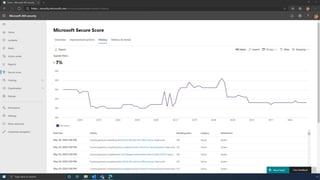
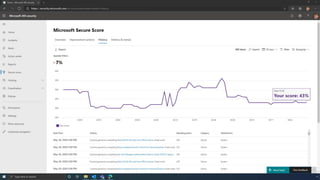
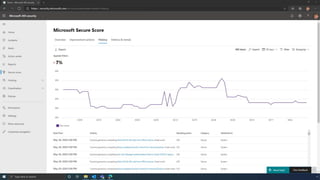
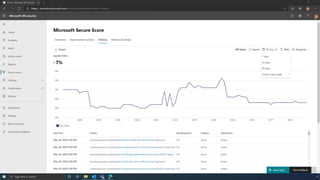
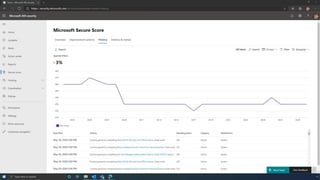
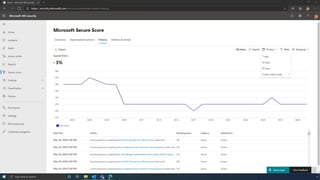
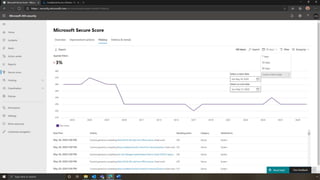
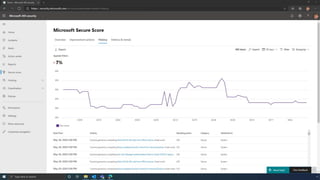
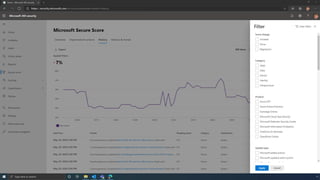
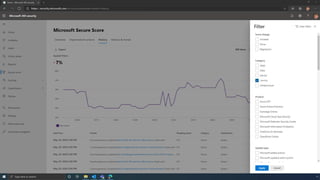
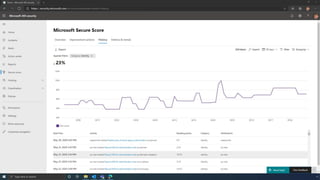
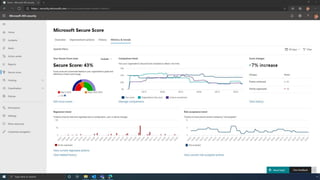
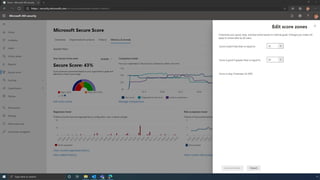
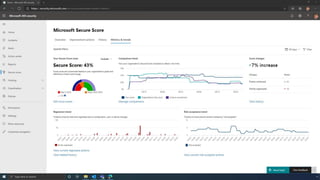
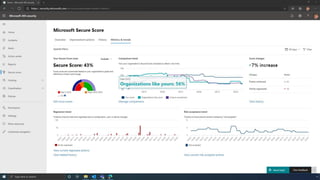
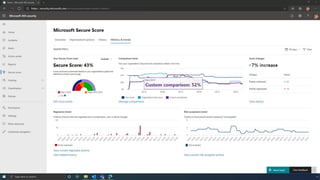
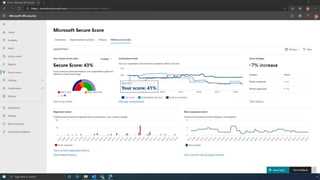
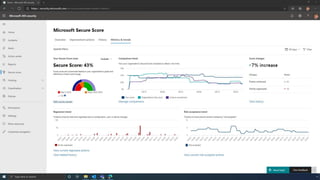
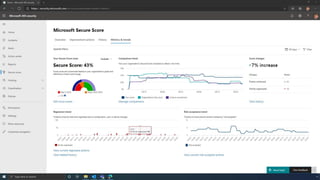
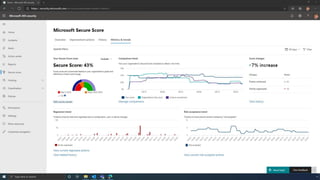
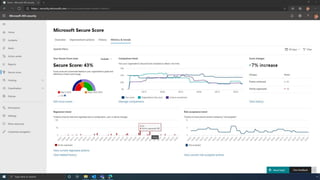
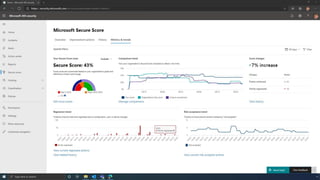
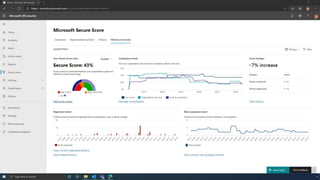
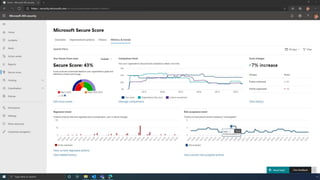

The document discusses the benefits of exercise for mental health. Regular physical activity can help reduce anxiety and depression and improve mood and cognitive functioning. Exercise causes chemical changes in the brain that may help protect against mental illness and improve symptoms.














































































