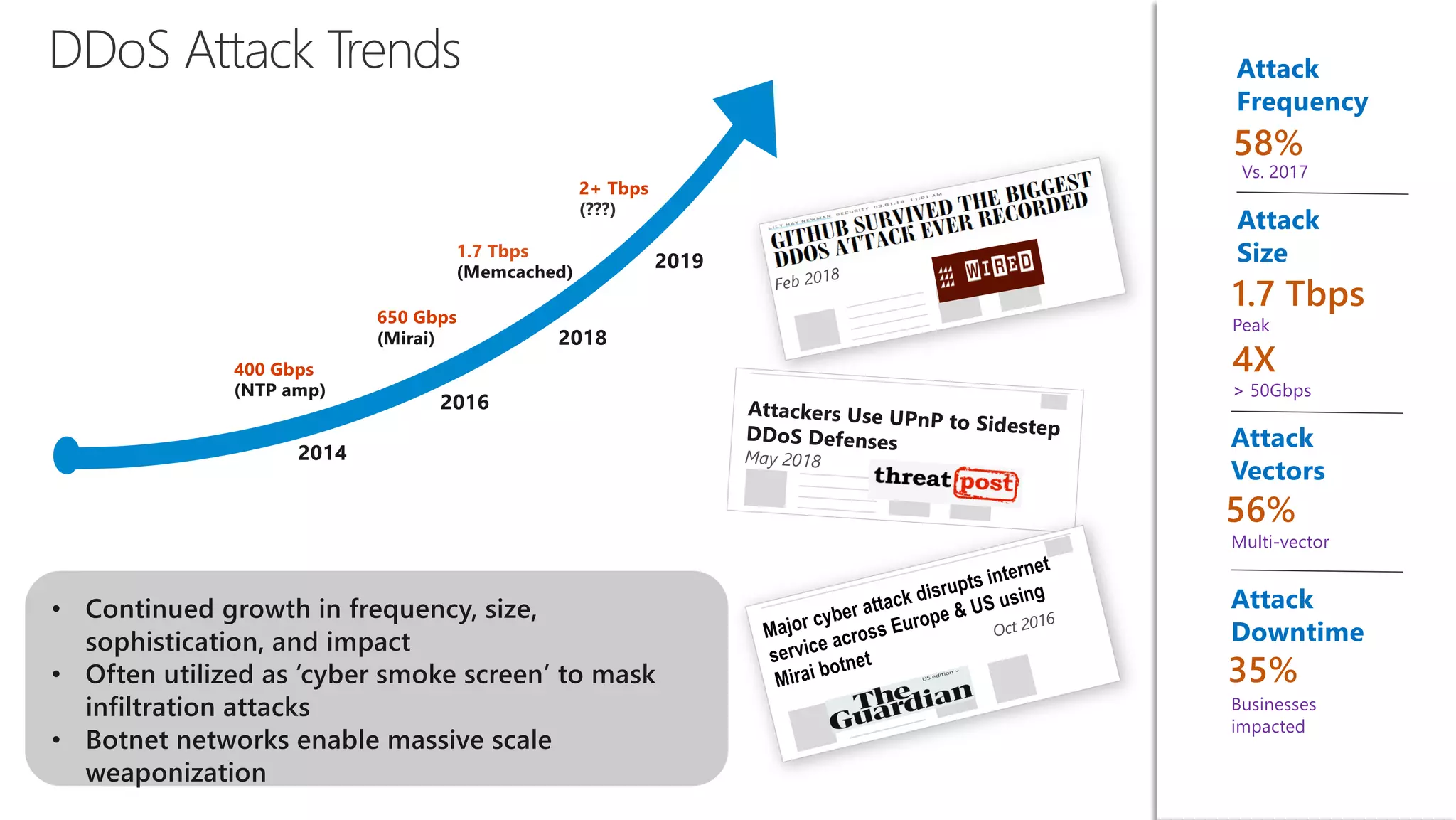
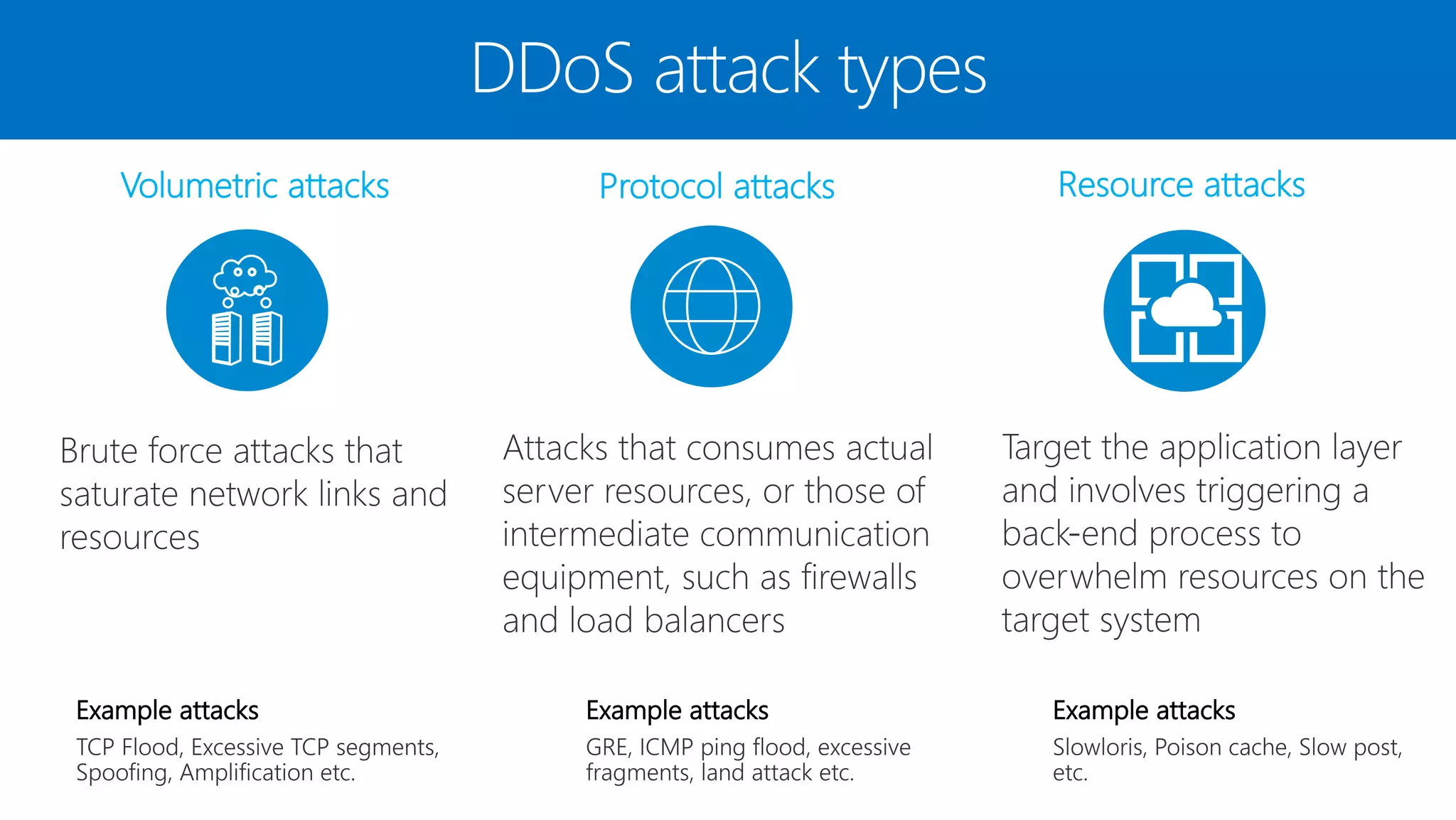
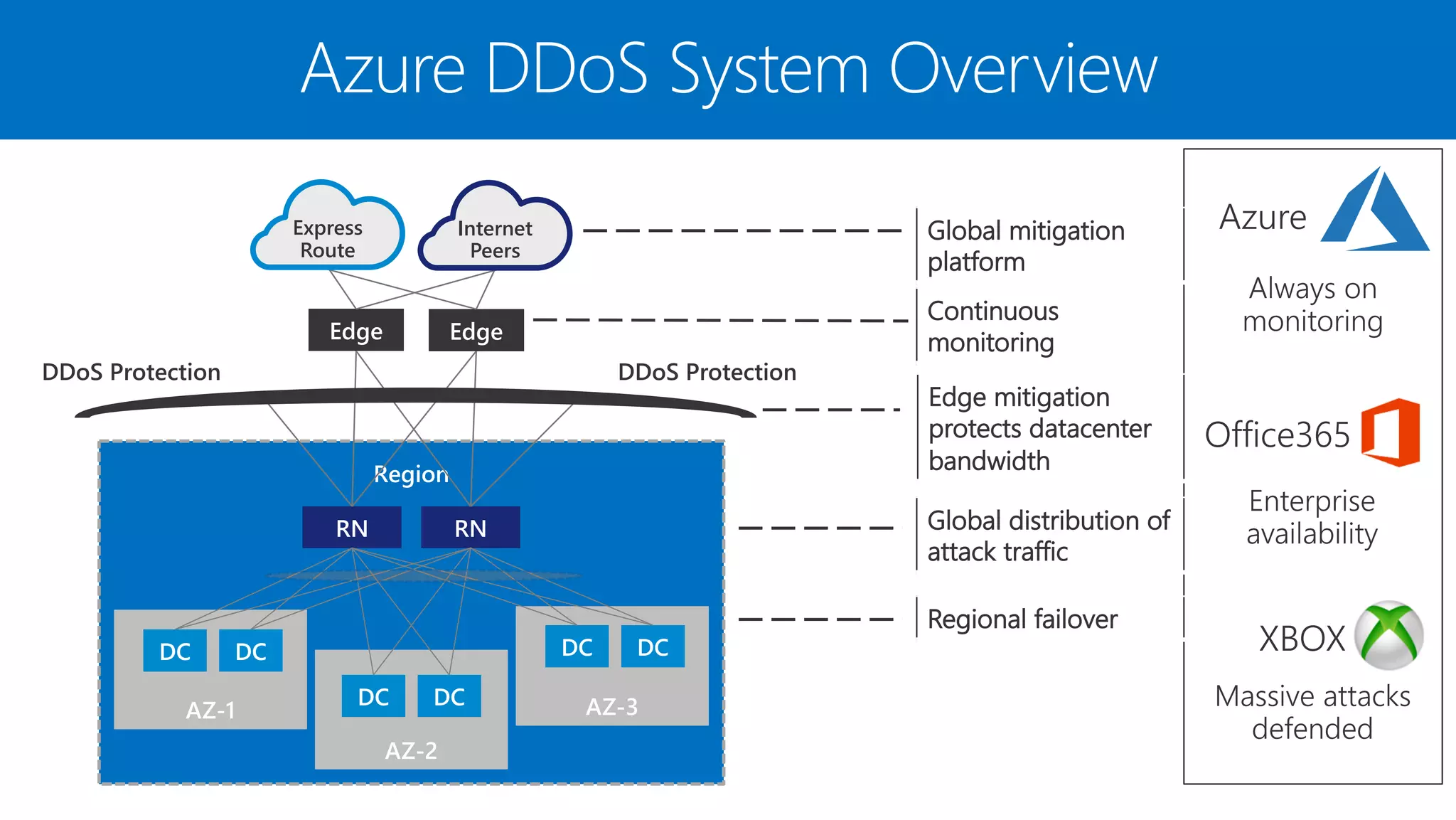
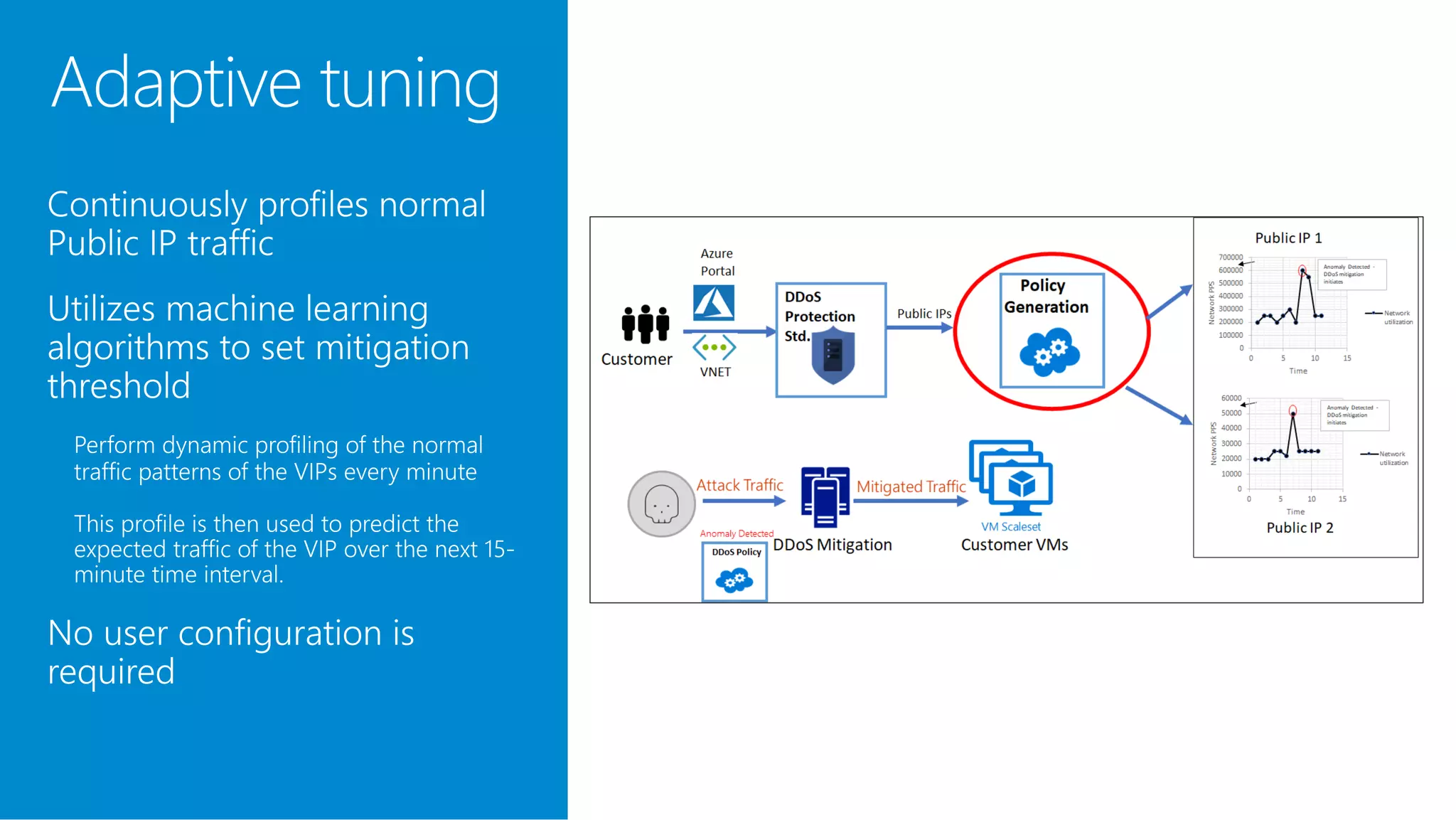
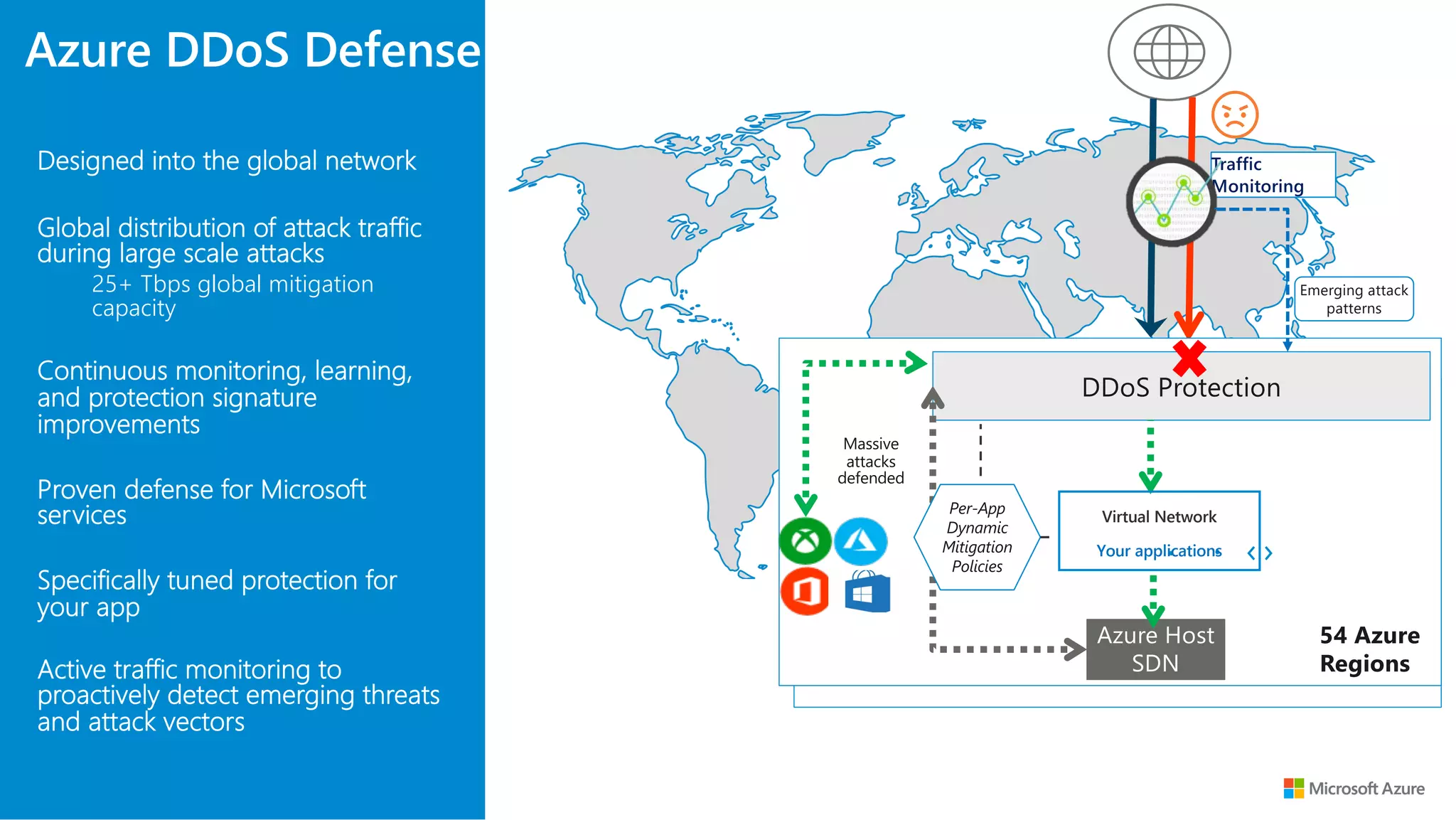
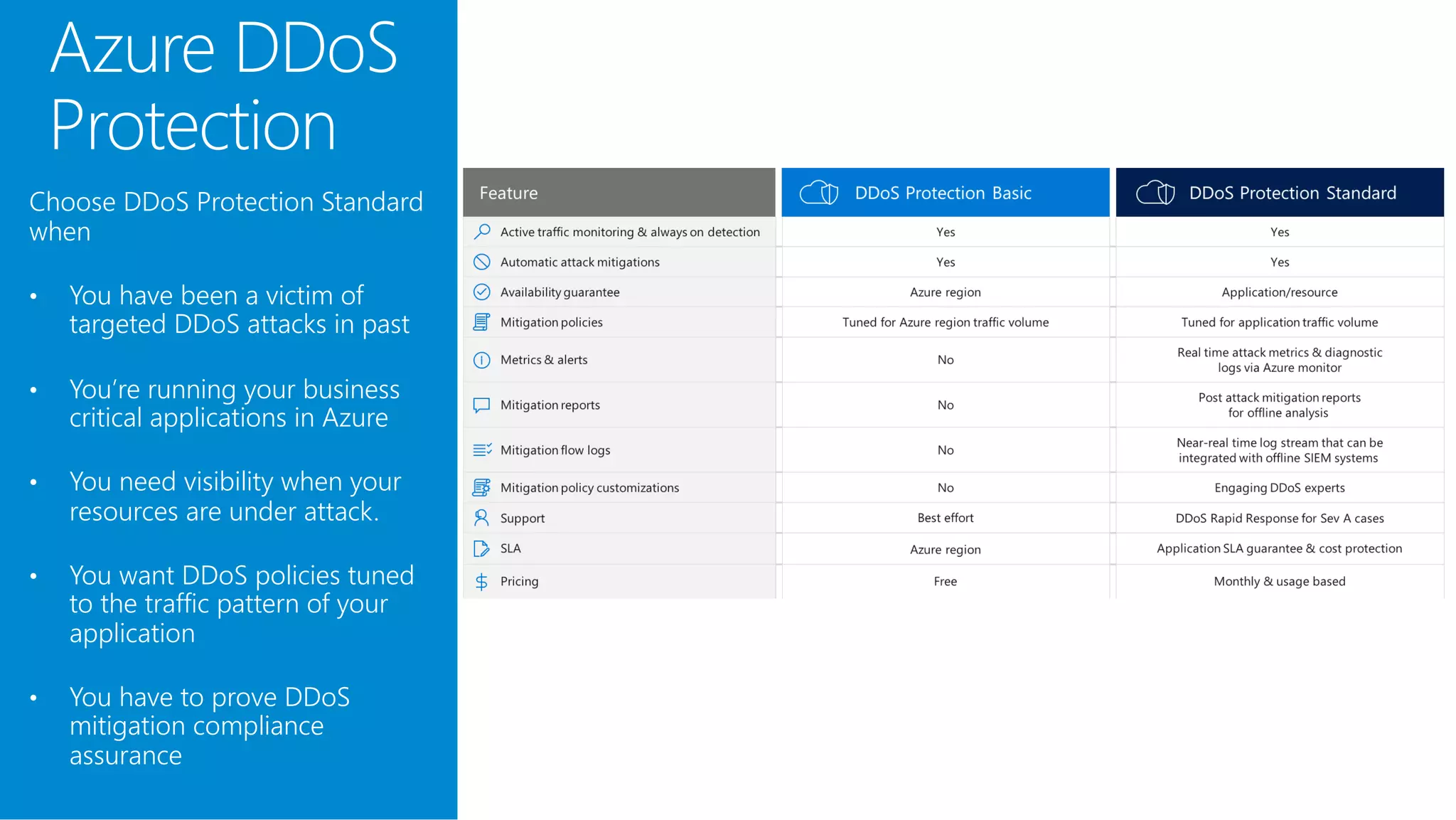
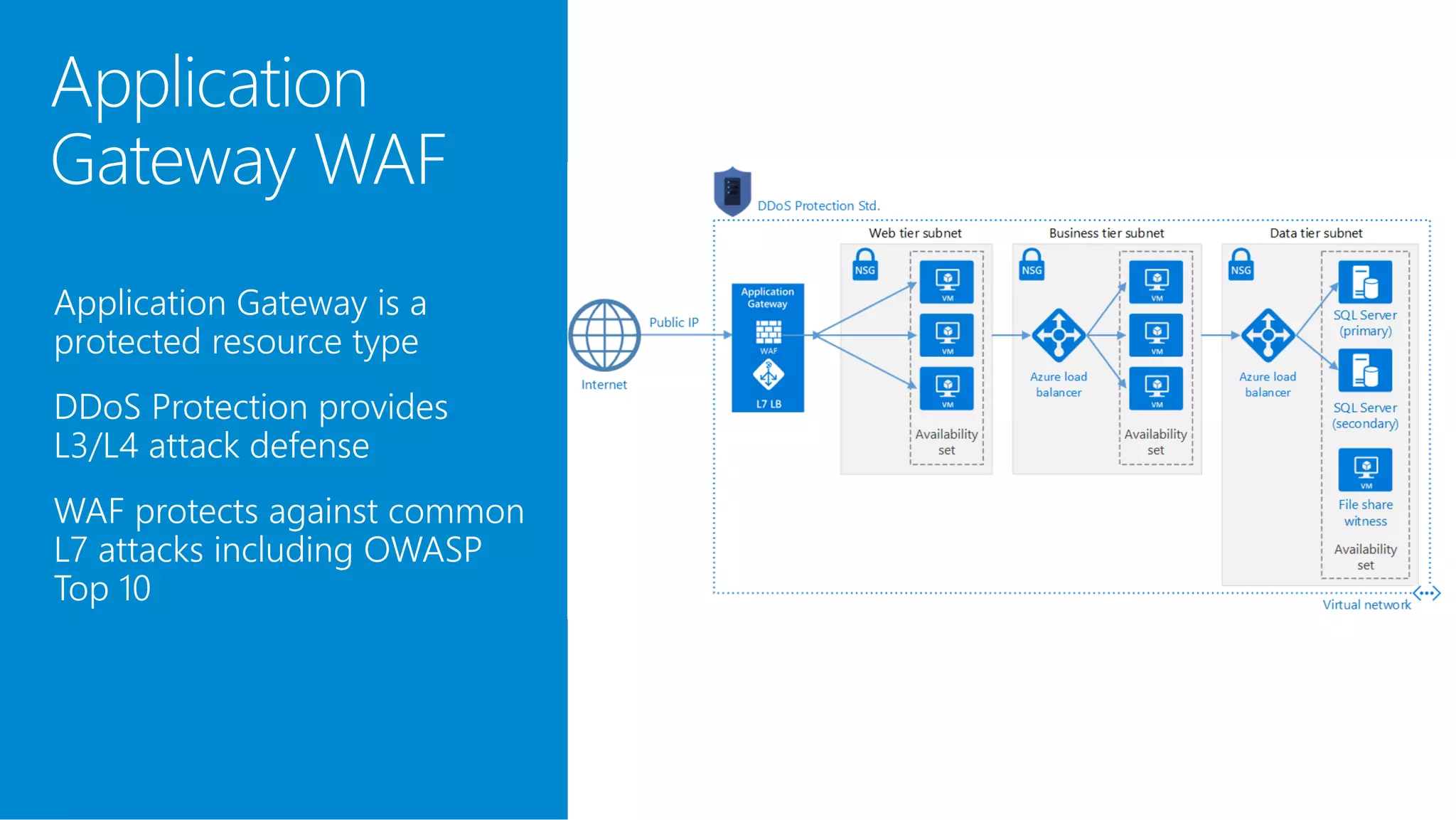
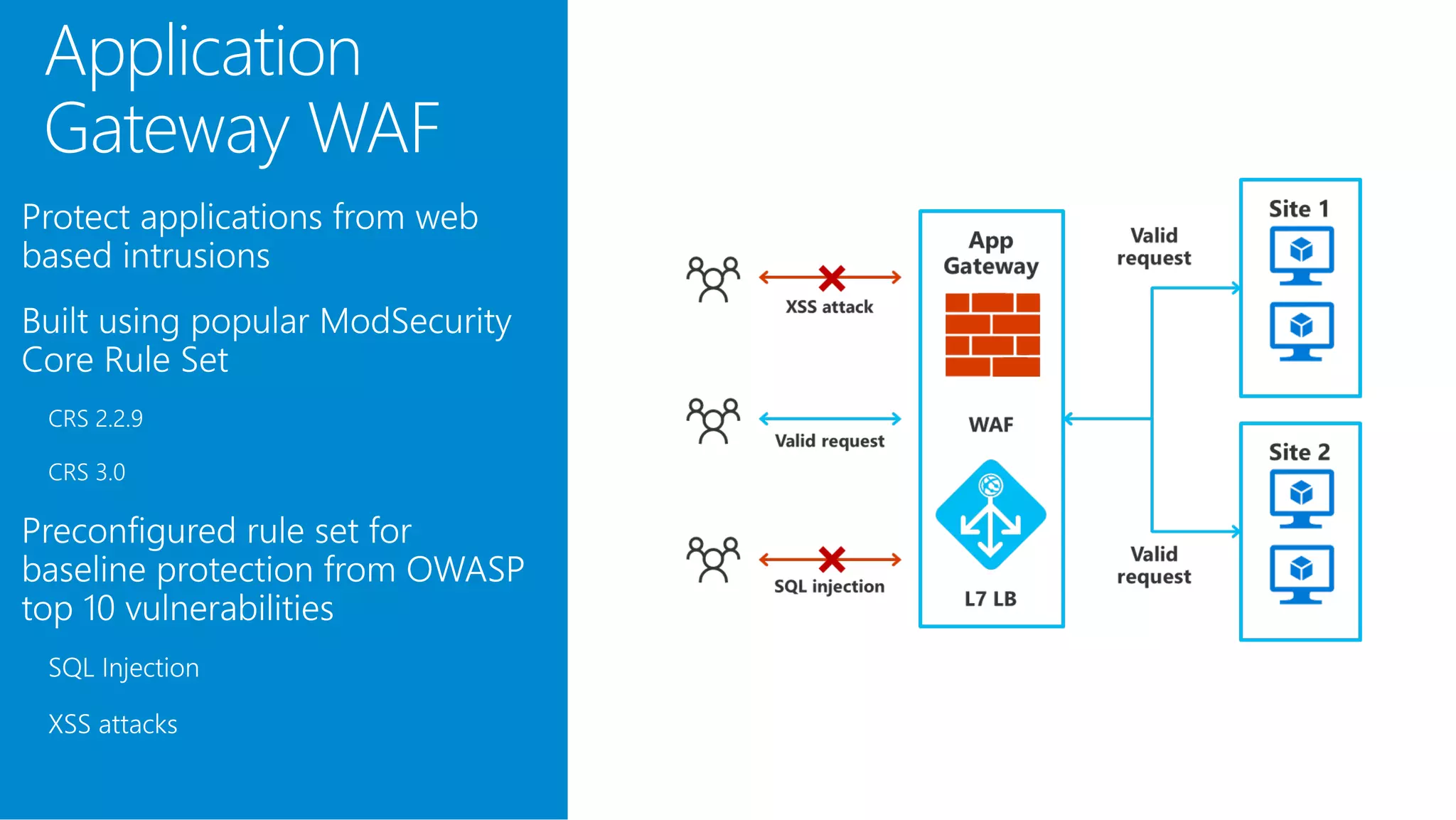
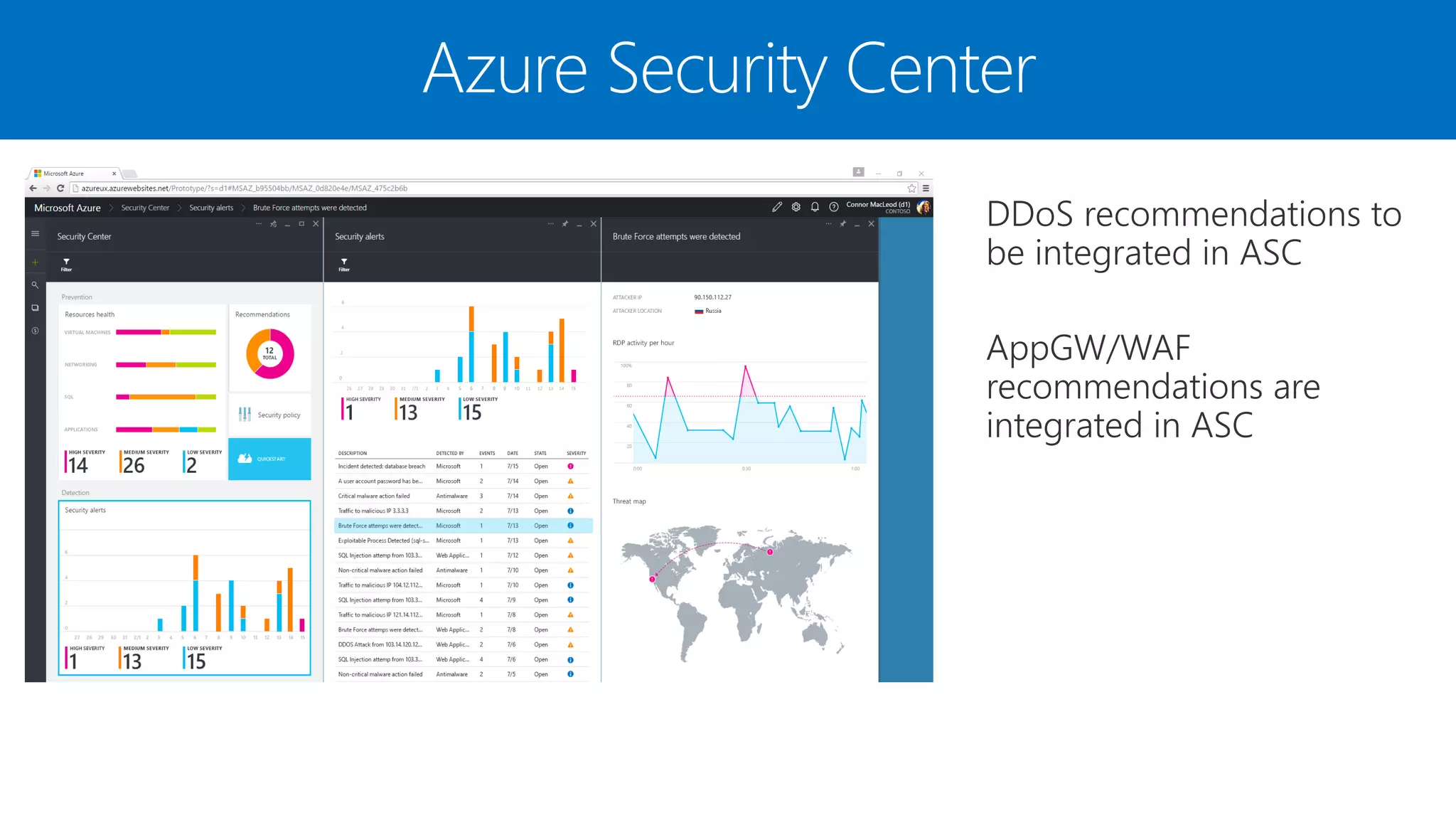
The document discusses Azure DDoS Protection Standard. It notes that DDoS attacks are increasing in frequency, size, and sophistication. Azure DDoS Protection Standard provides continuous monitoring, edge mitigation to protect datacenter bandwidth, regional failover, and global mitigation capacity of over 25 Tbps. It is designed to provide automatic network layer attack protection and analytics for virtual network resources.