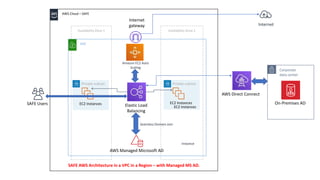
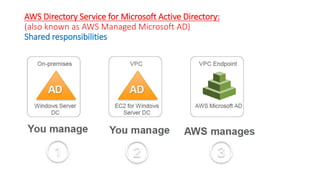
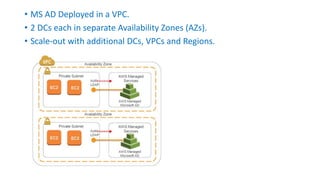
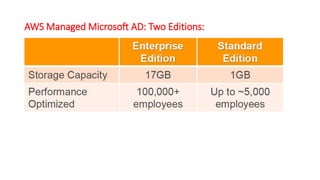
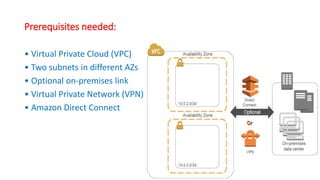
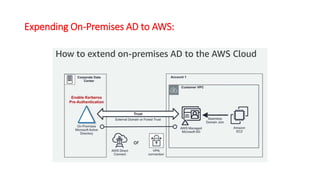
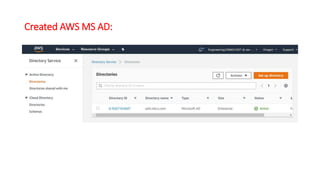
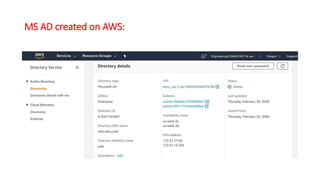
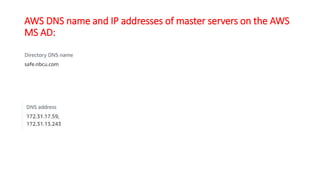
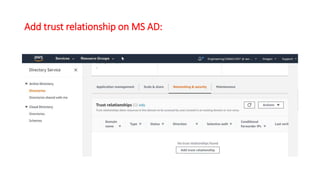
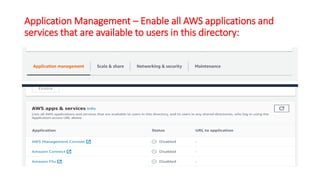
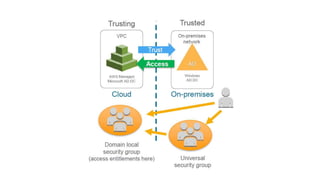
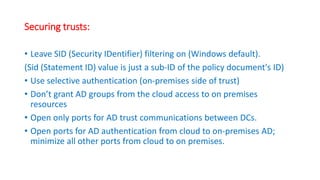
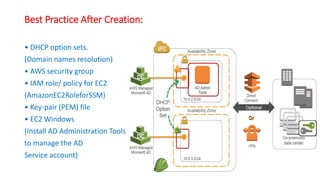
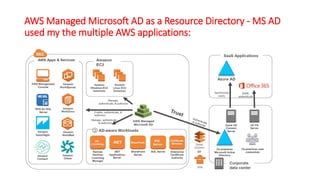
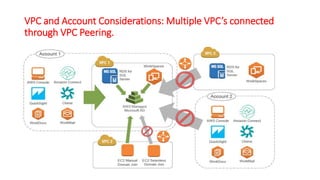
This document describes how to set up AWS Managed Microsoft Active Directory (AD) to connect an on-premises AD to the cloud. It involves creating an AWS Directory Service for Microsoft AD in a VPC with domains controllers in two availability zones for high availability. The AWS-managed AD can then be joined to the on-premises AD by creating a trust relationship between the two forests. This allows users in the on-premises AD to access AWS resources and applications that are connected to the cloud-based AD. The document provides details on directory structure, access control, and best practices for the setup.