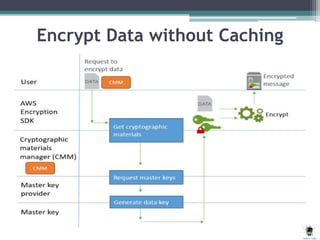
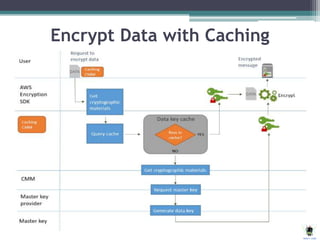
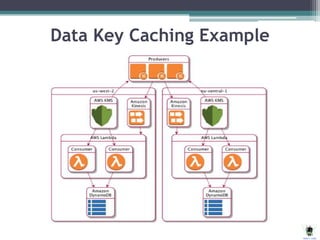
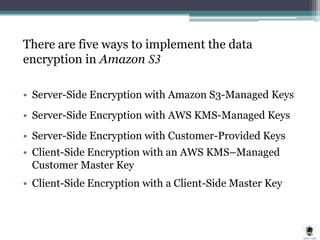
AWS Key Management Service (KMS) simplifies the creation and control of encryption keys for data encryption, utilizing FIPS 140-2 validated hardware security modules. The AWS Encryption SDK supports various AES encryption options and features data key caching to enhance efficiency in cryptographic operations. Different methods, including server-side and client-side encryption, are available for managing encryption in Amazon S3, allowing customers to select the key management approach that best suits their needs.