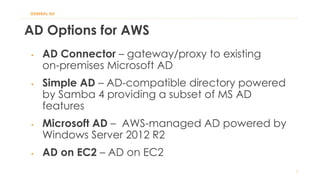
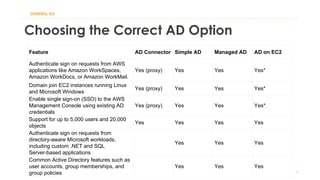
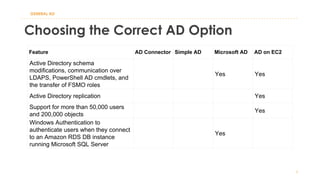
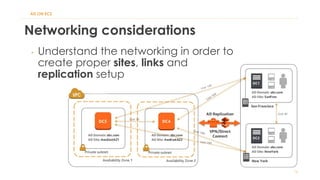
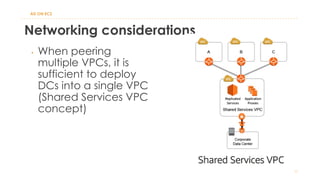
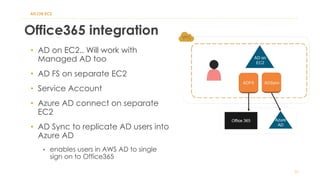
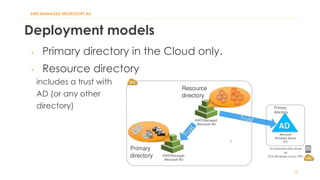
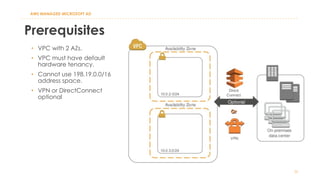
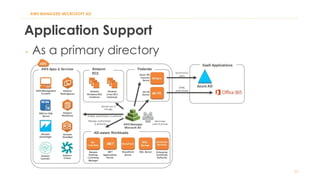
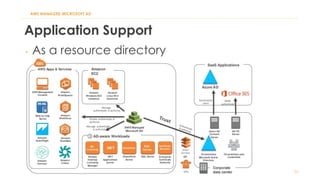
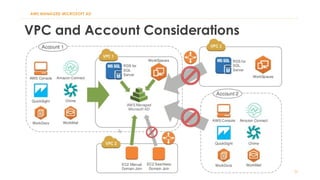
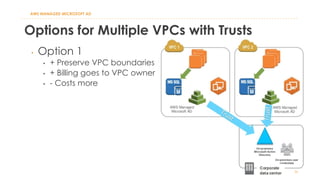
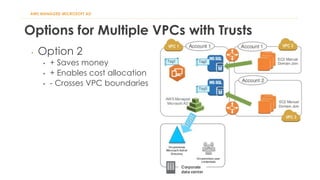
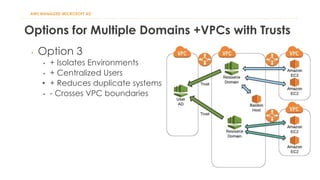
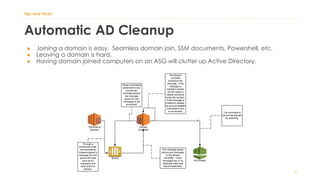
The document discusses various Active Directory (AD) options available in AWS, including AD Connector, Simple AD, Managed Microsoft AD, and deploying AD on EC2. It covers the features, setup considerations, security, networking, and backup strategies associated with each option, providing best practices for implementation in multi-region environments. Additionally, it outlines AWS-managed AD service specifications, deployment models, shared responsibilities, and management tips post-creation.