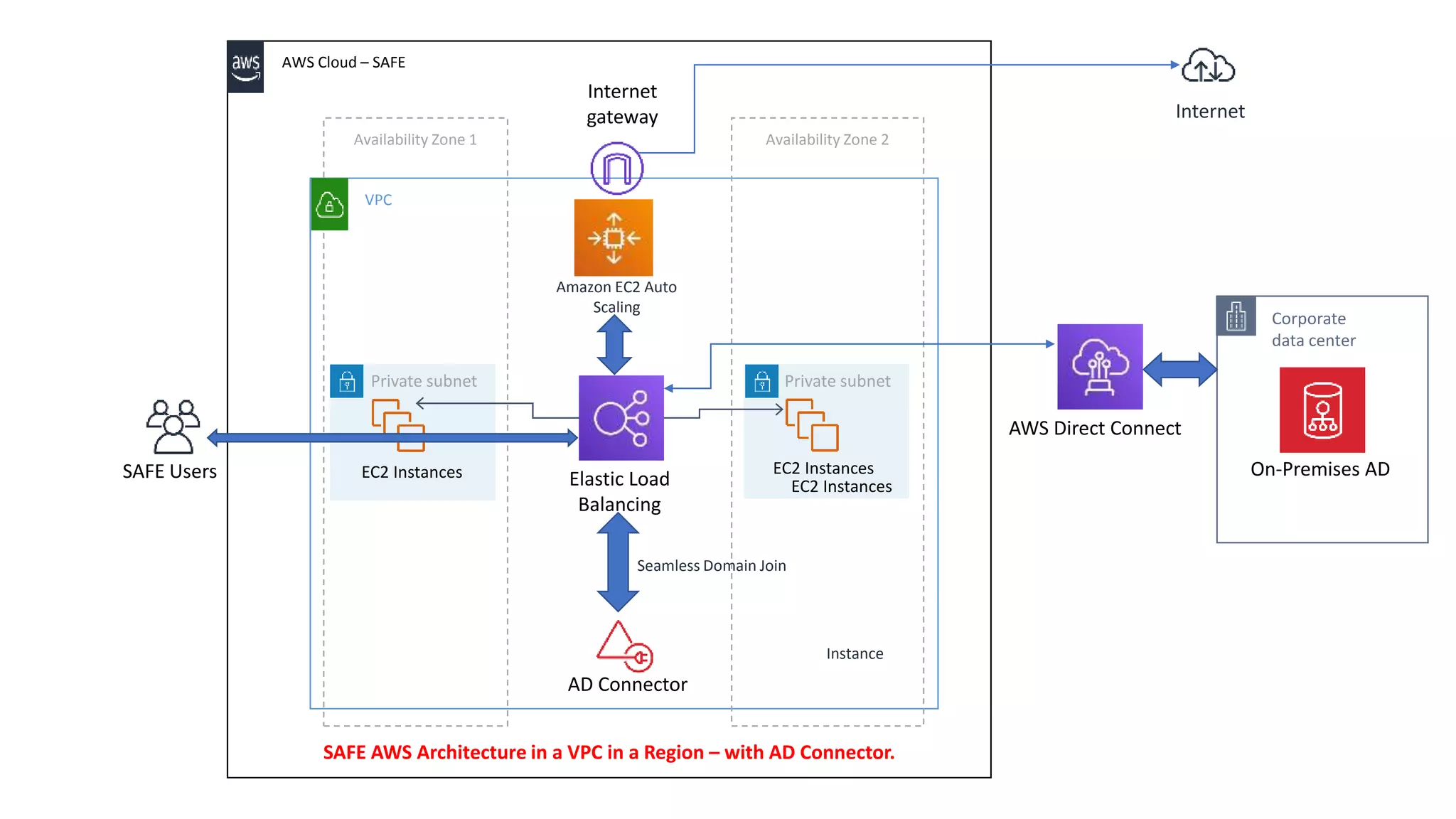
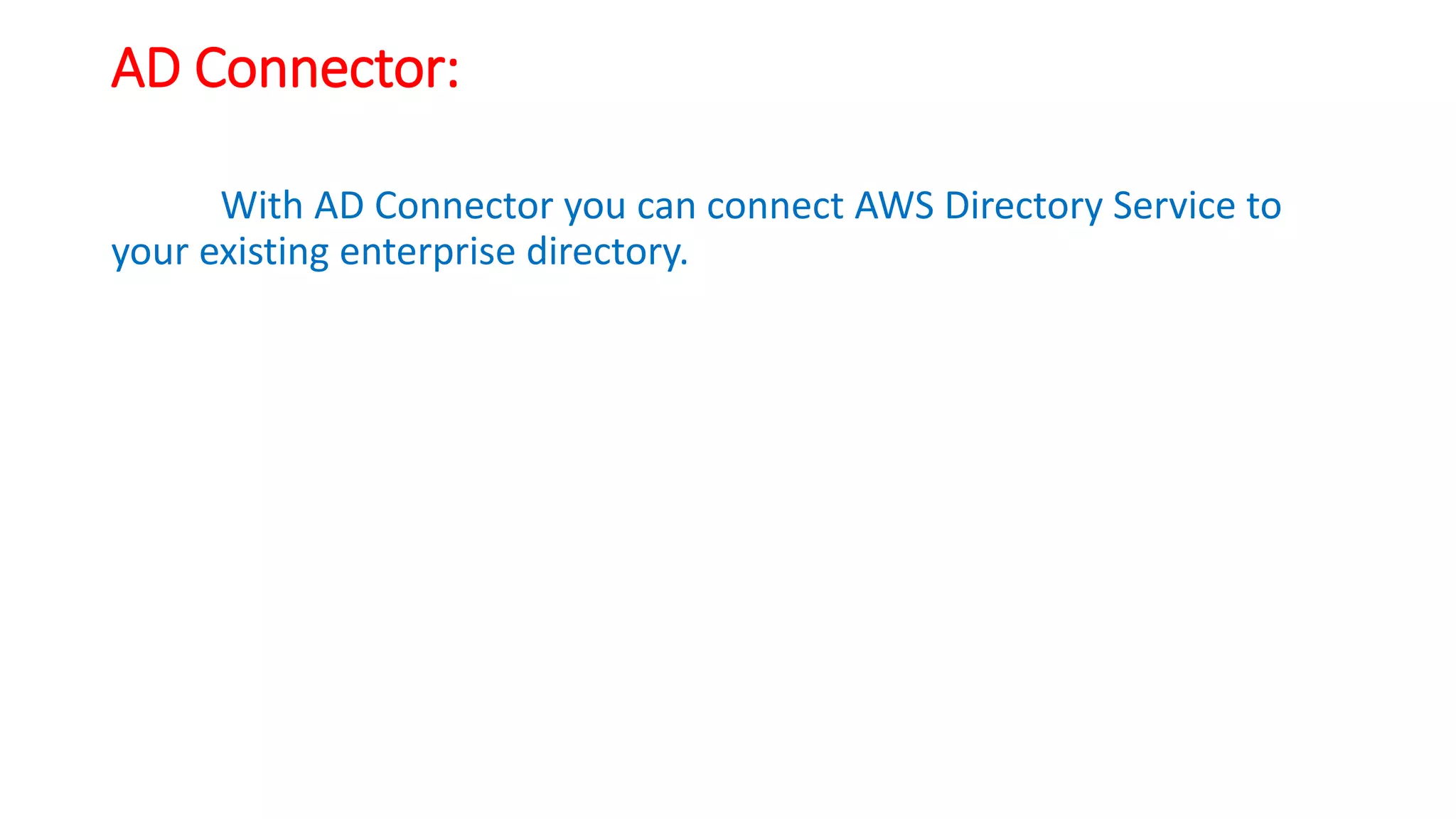
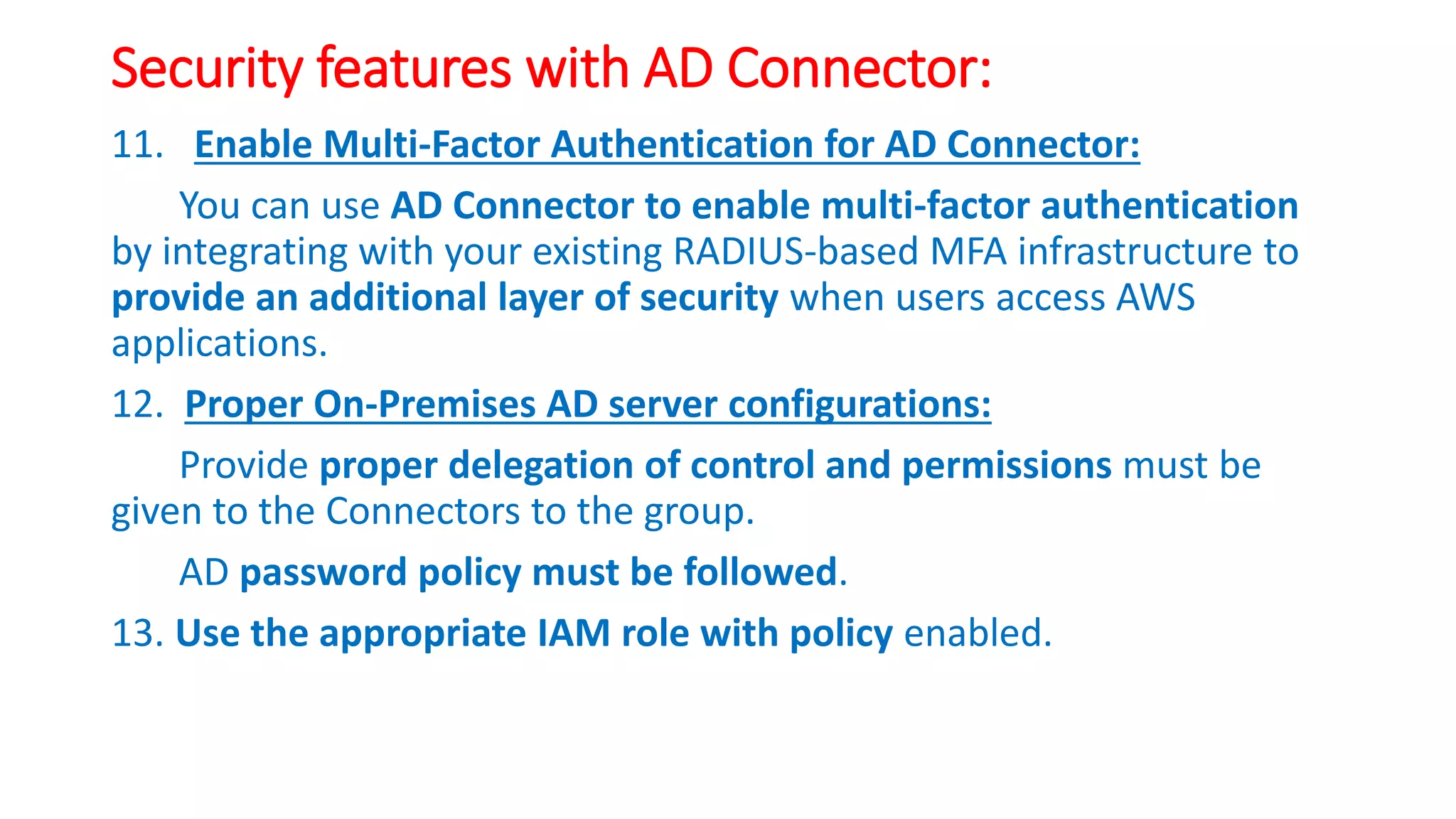
The document discusses AWS AD Connector which allows connecting an AWS Directory Service to an existing on-premises Active Directory. It provides security by keeping directory data on-premises, does not replicate data to AWS, and enforces on-premises security policies. The VPC must be connected to the on-premises network via VPN or Direct Connect. Proper configurations of ports, user accounts, and IAM roles are required for security.