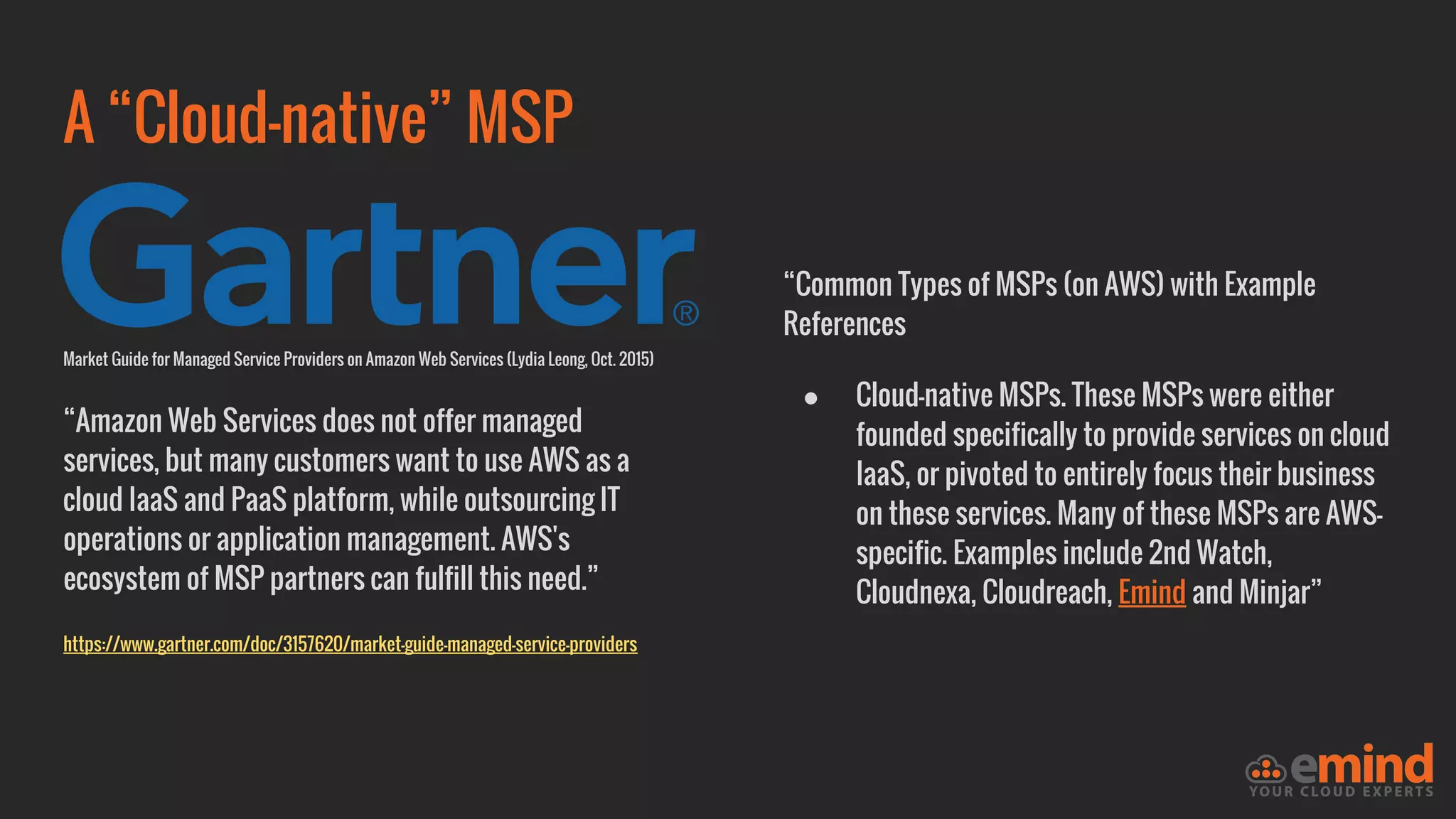
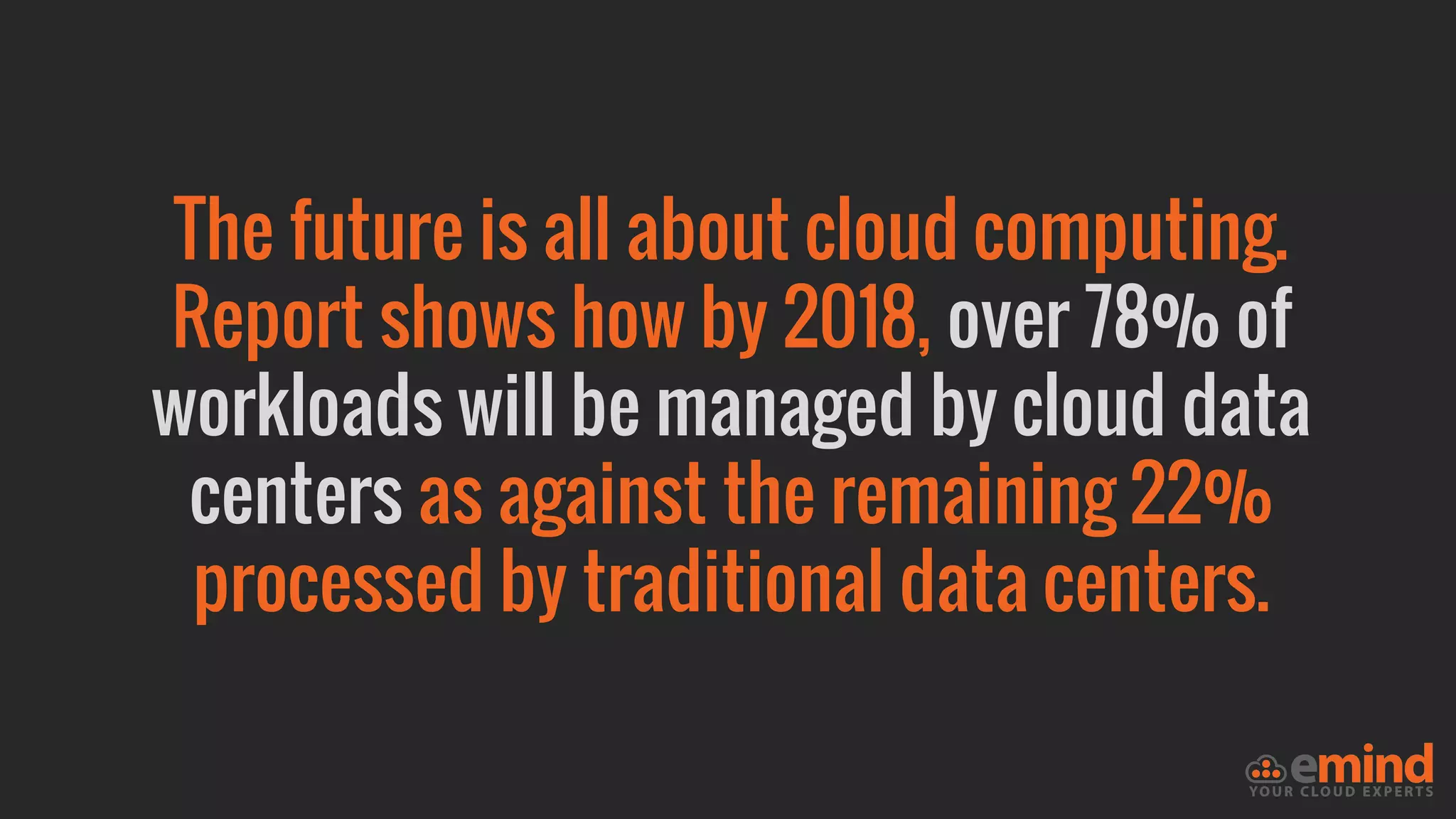
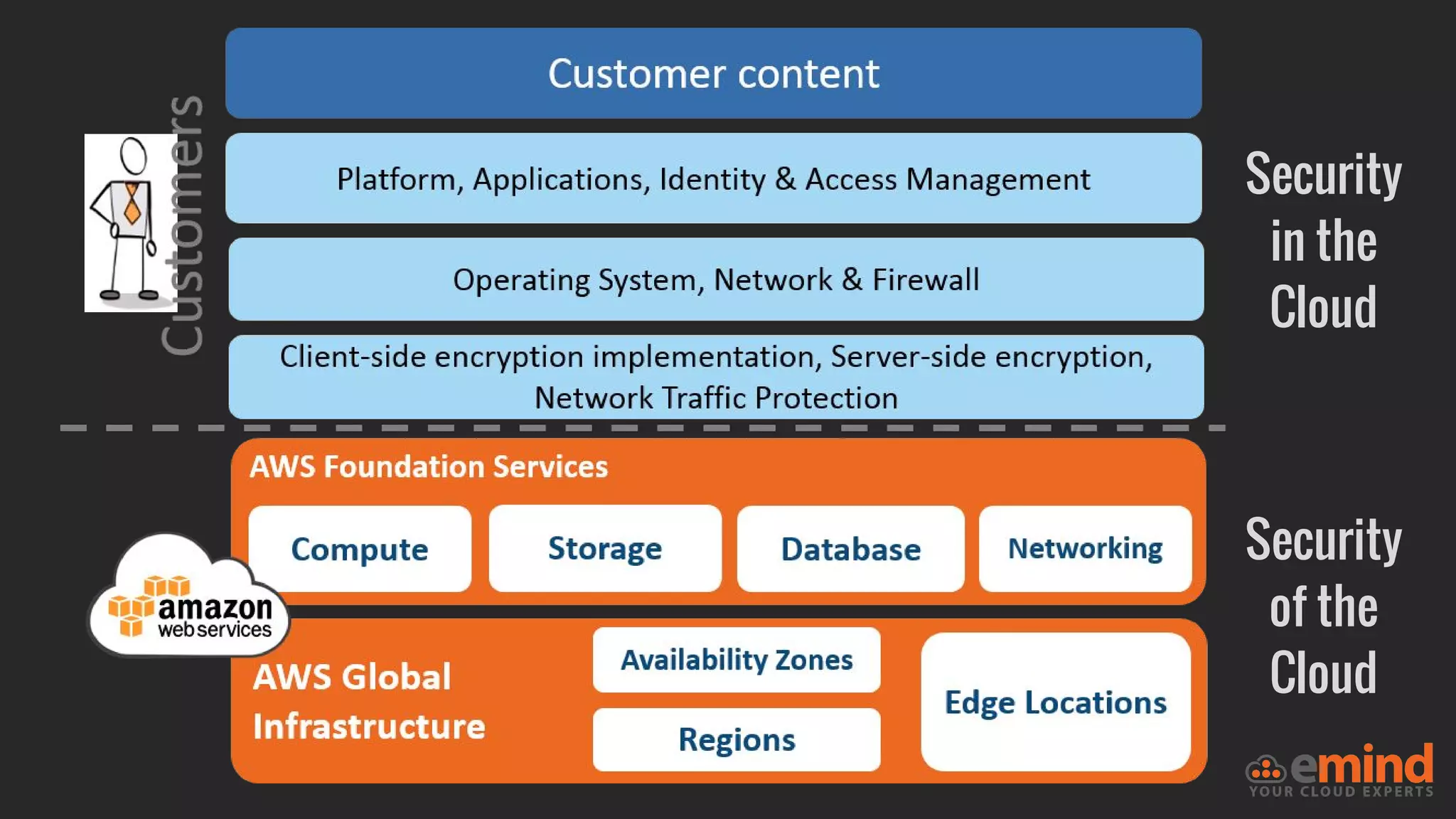
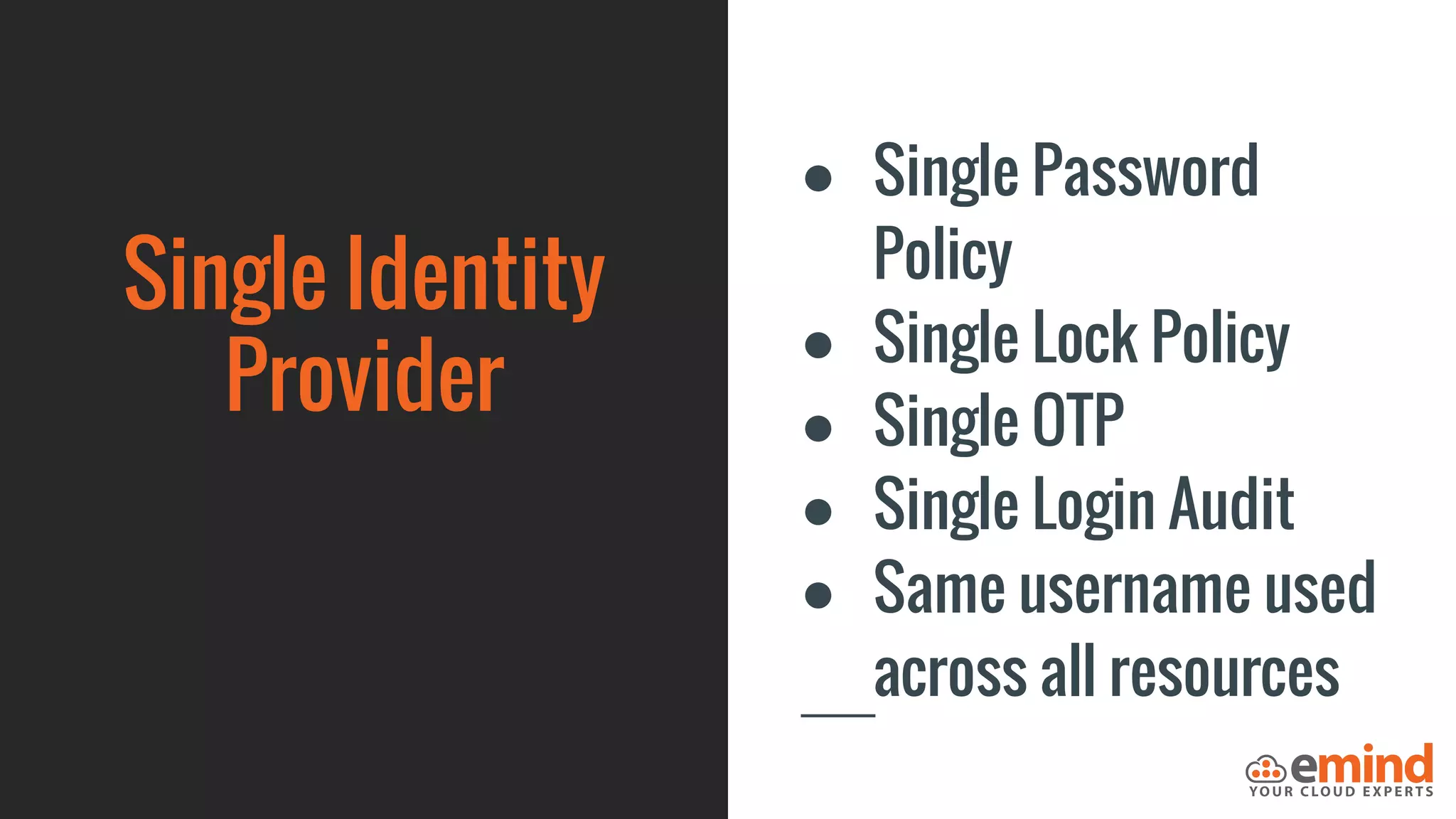
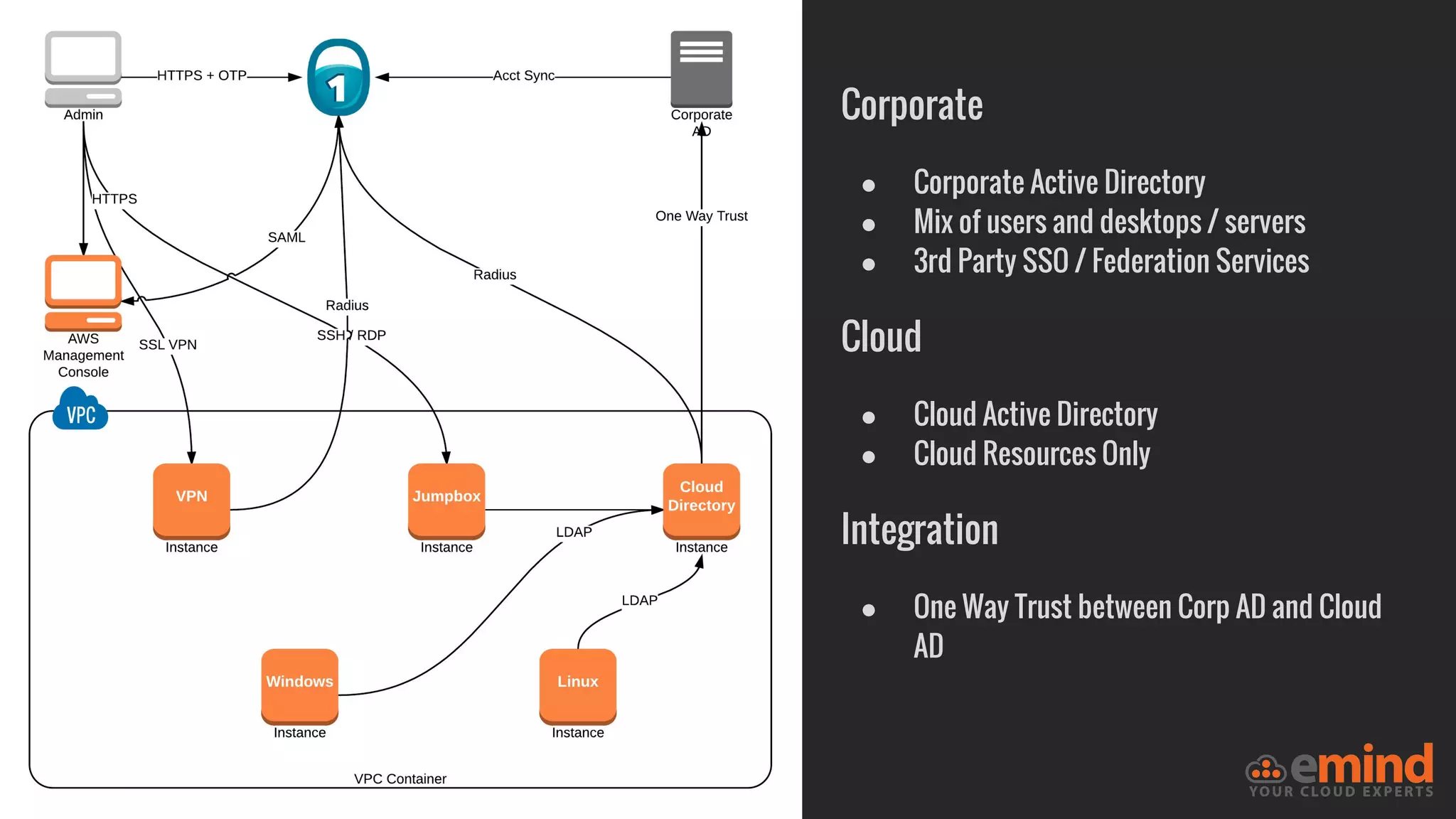
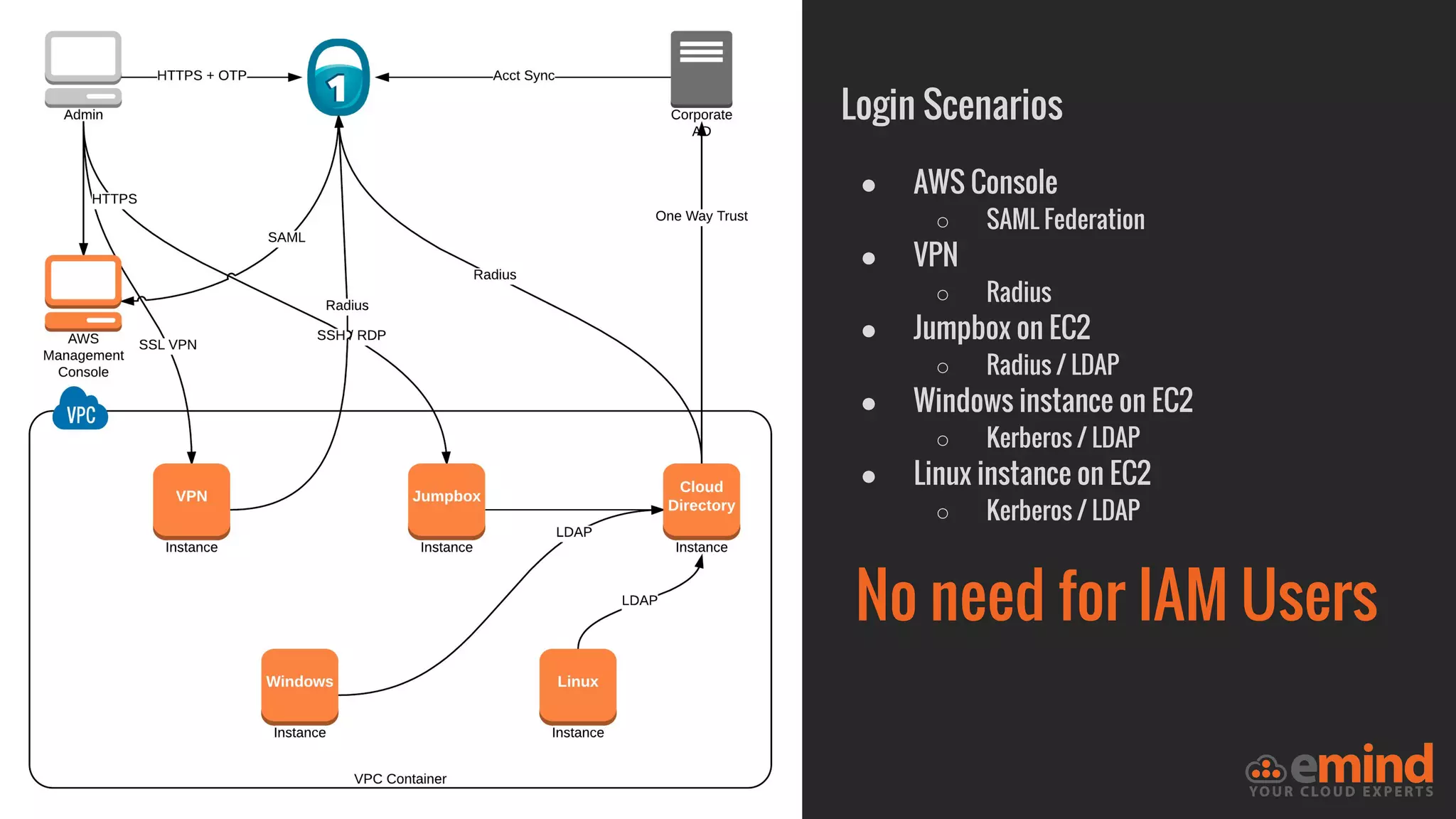
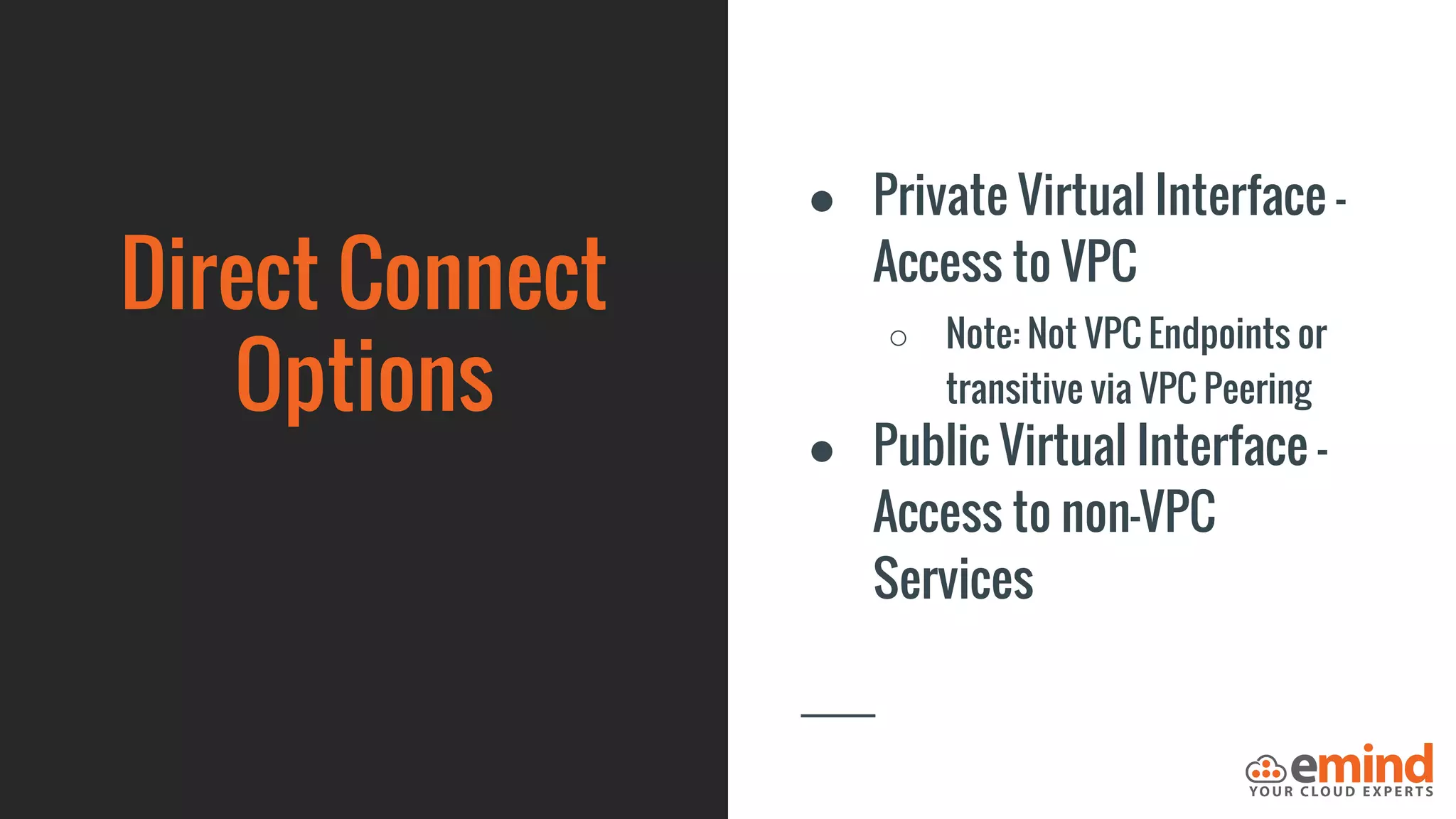
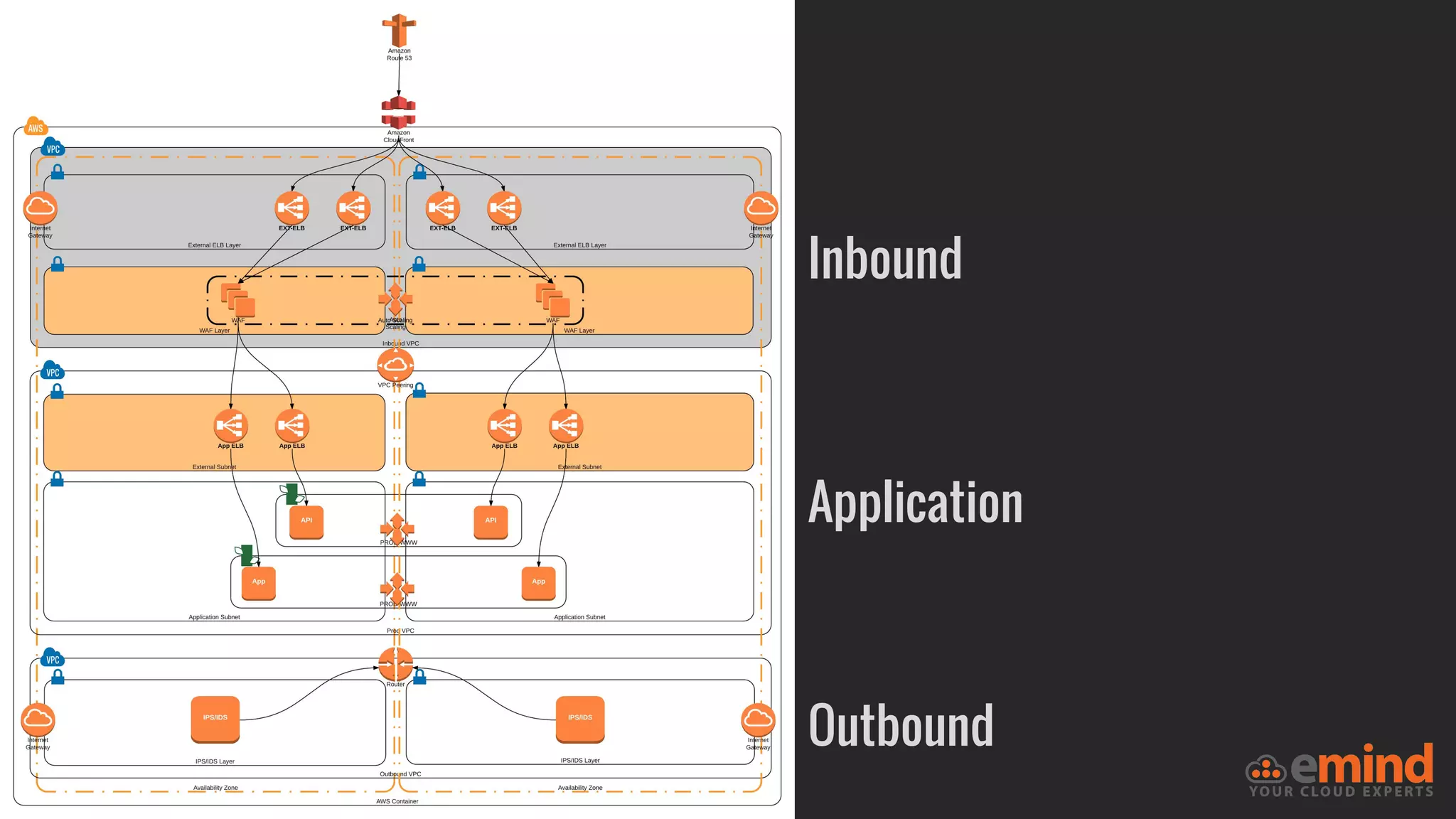
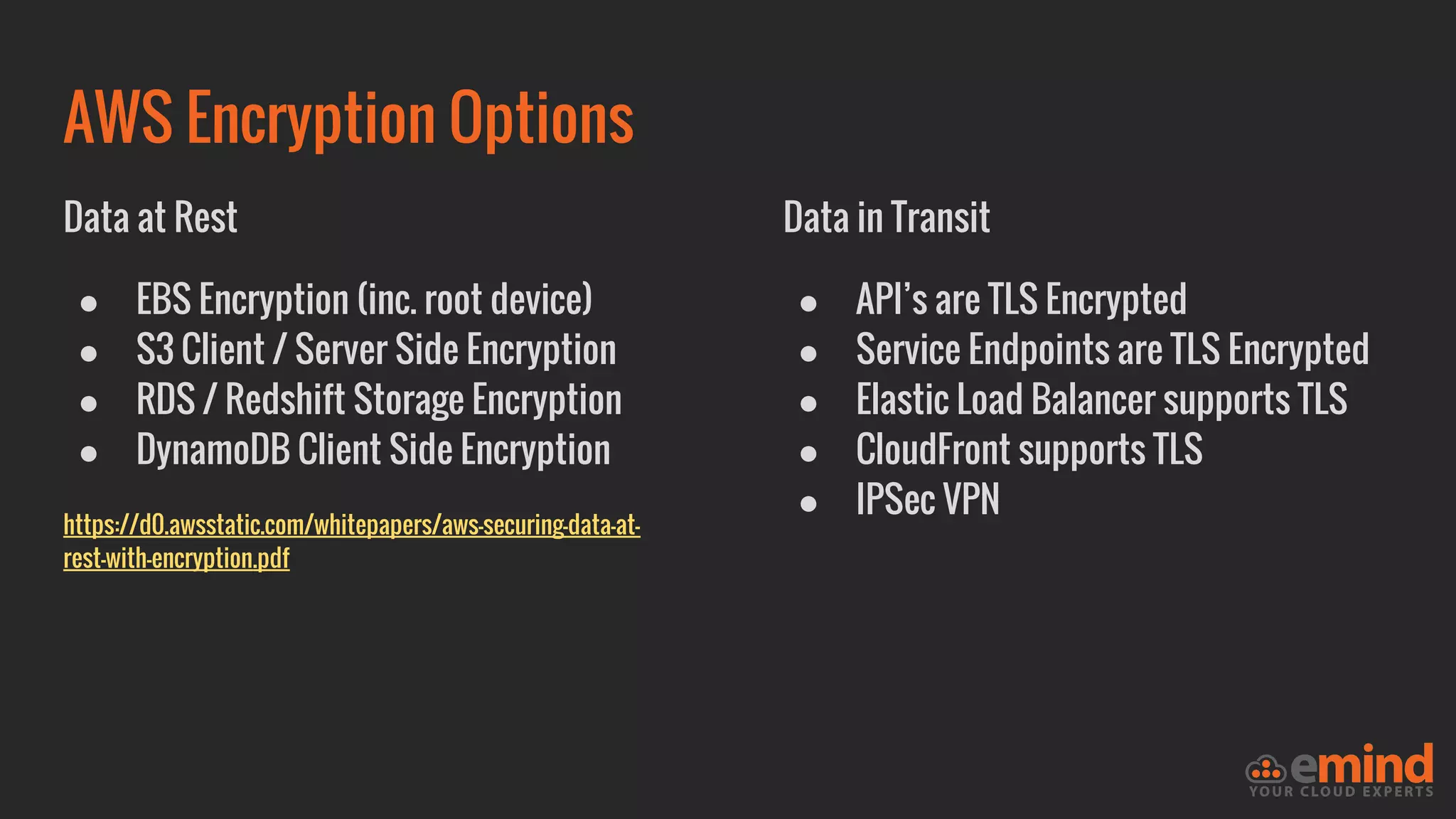
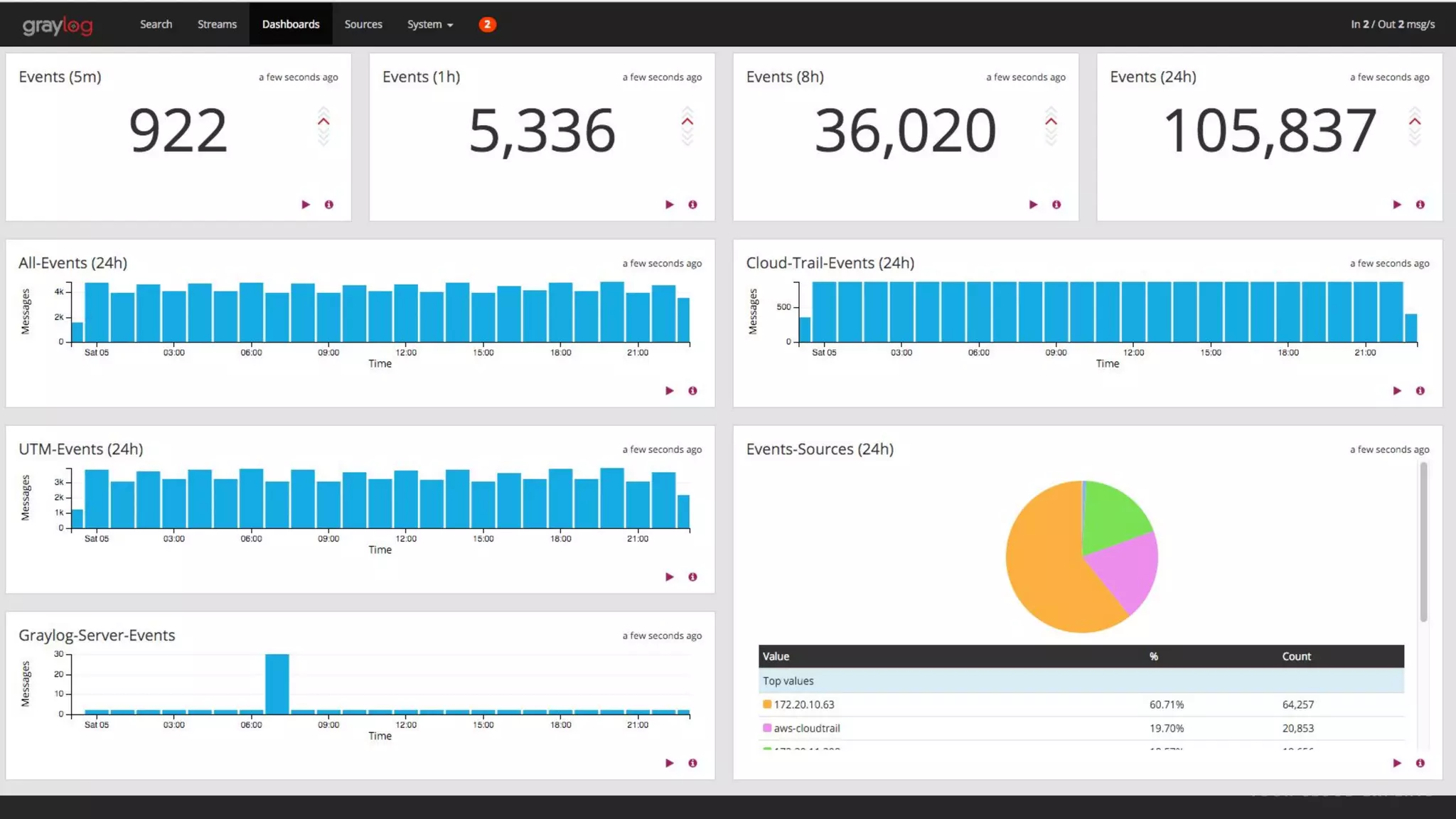
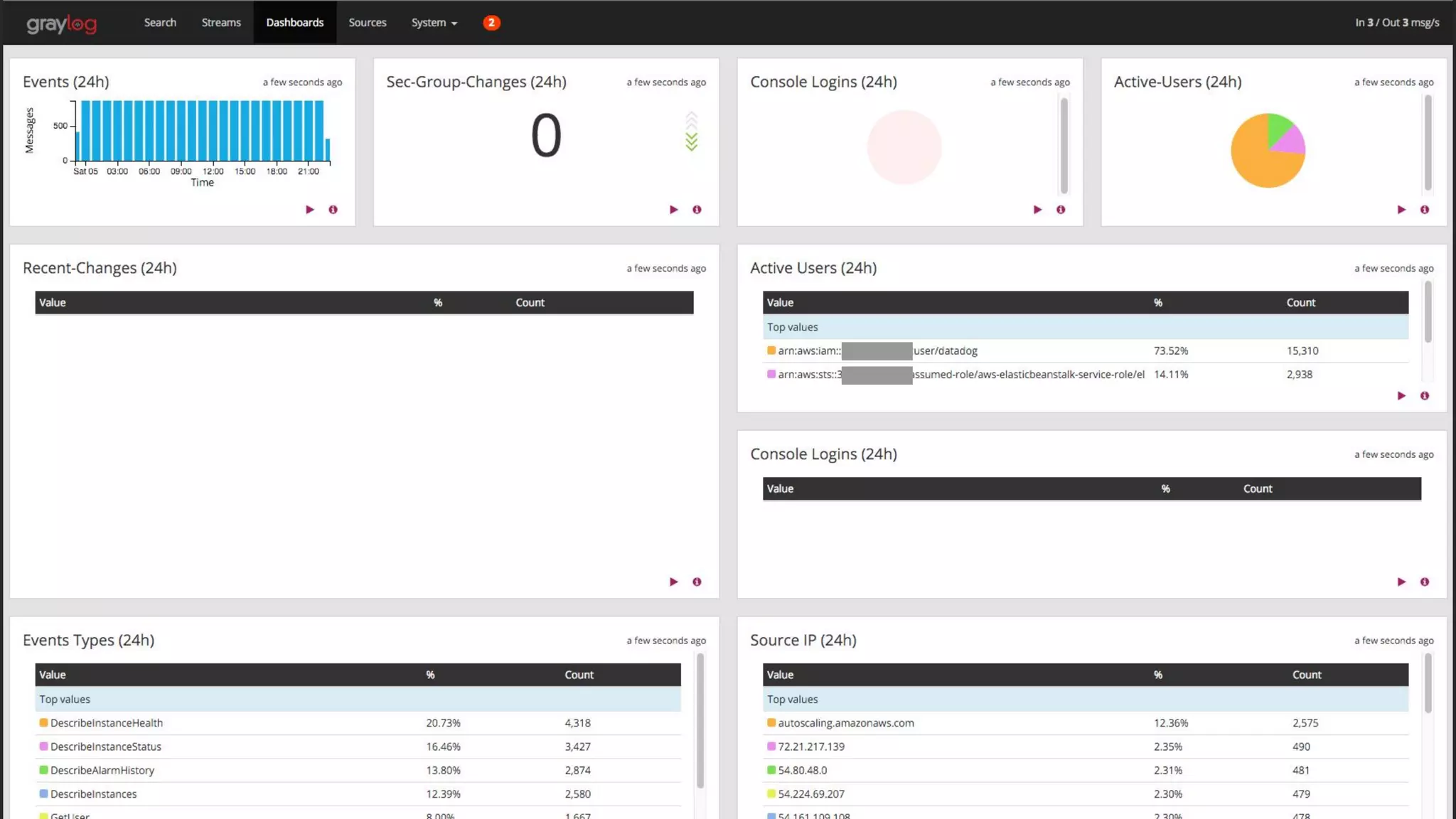
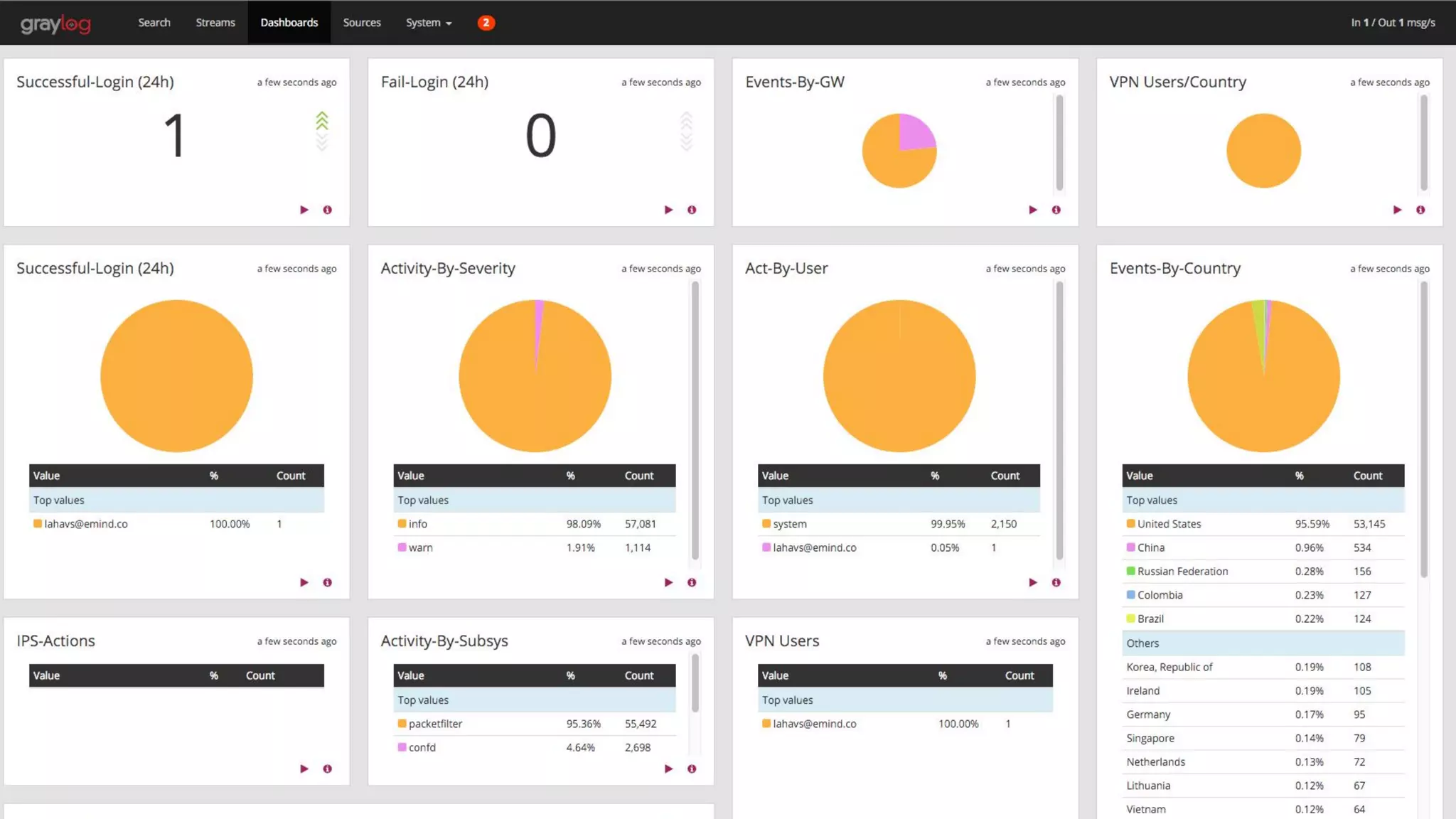
This document provides an overview of how to protect an AWS environment. It discusses common types of managed service providers (MSPs) that focus on AWS, including cloud-native MSPs. It also covers important security topics like infrastructure security, network security, host security, data encryption, identity management, and monitoring/auditing. Specific recommendations are given around securing networking with options like Direct Connect, VPNs, and segmentation. The document emphasizes central monitoring, auditing, and encrypting all data for protection.