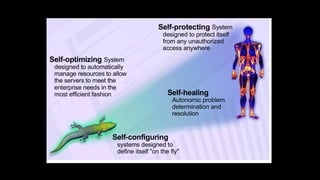
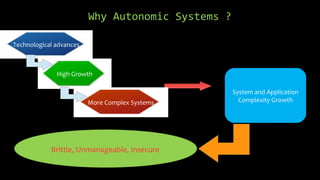
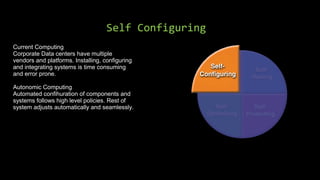
Autonomic computing aims to address the increasing complexity and unmanageable nature of modern computing systems by creating self-managing environments that hide complexity from users. Key features include self-healing, self-configuring, self-protecting, and self-optimizing capabilities, enabling automated management and security across diverse platforms. It combines elements of biological systems and offers a solution to the issues faced in system management and software engineering.