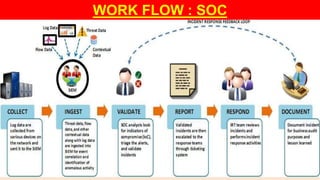
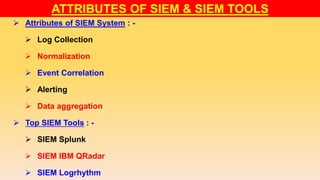
The document discusses security operations centers (SOCs) and security information and event management (SIEM). It describes SOCs as teams that perform advanced security operations like monitoring, detection, and response. Key SOC components are people, processes, and technology like SIEM tools. SIEM tools unify security data from multiple systems and allow threats to be analyzed from a single interface, helping SOCs meet compliance requirements and detect advanced attacks. The document outlines responsibilities and benefits of SOCs and concludes that SIEM is vital for effective security monitoring and response.