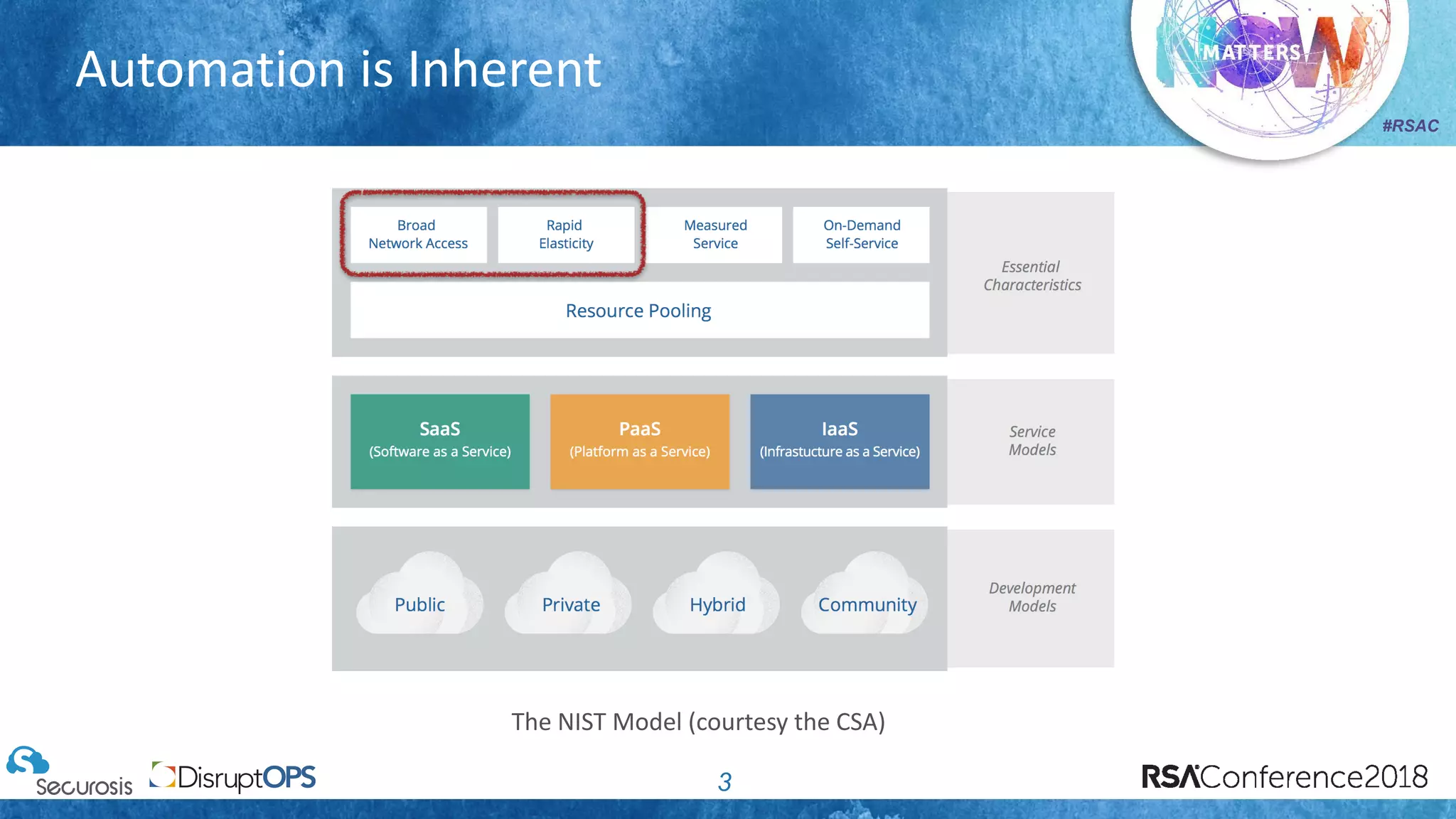
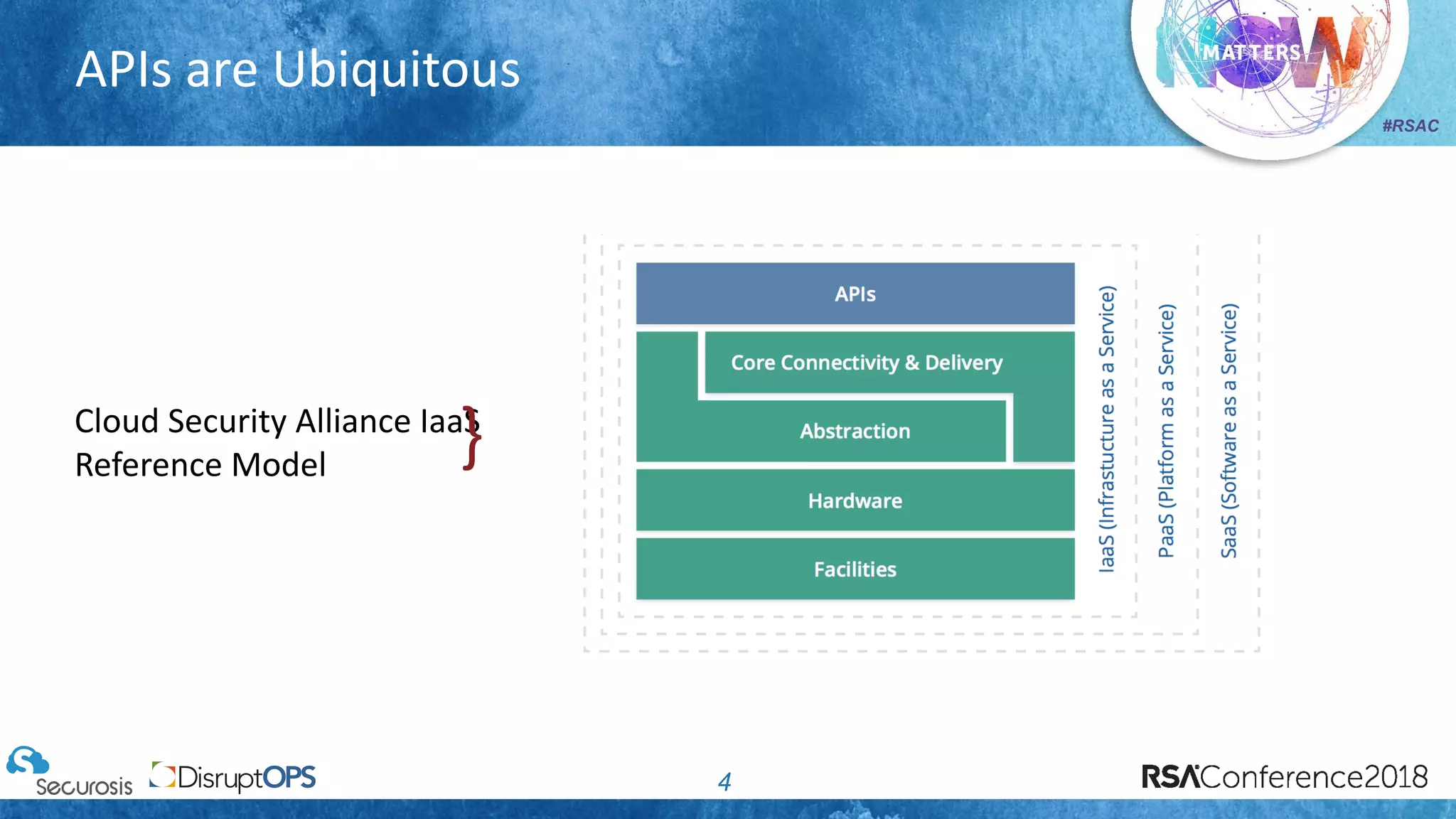
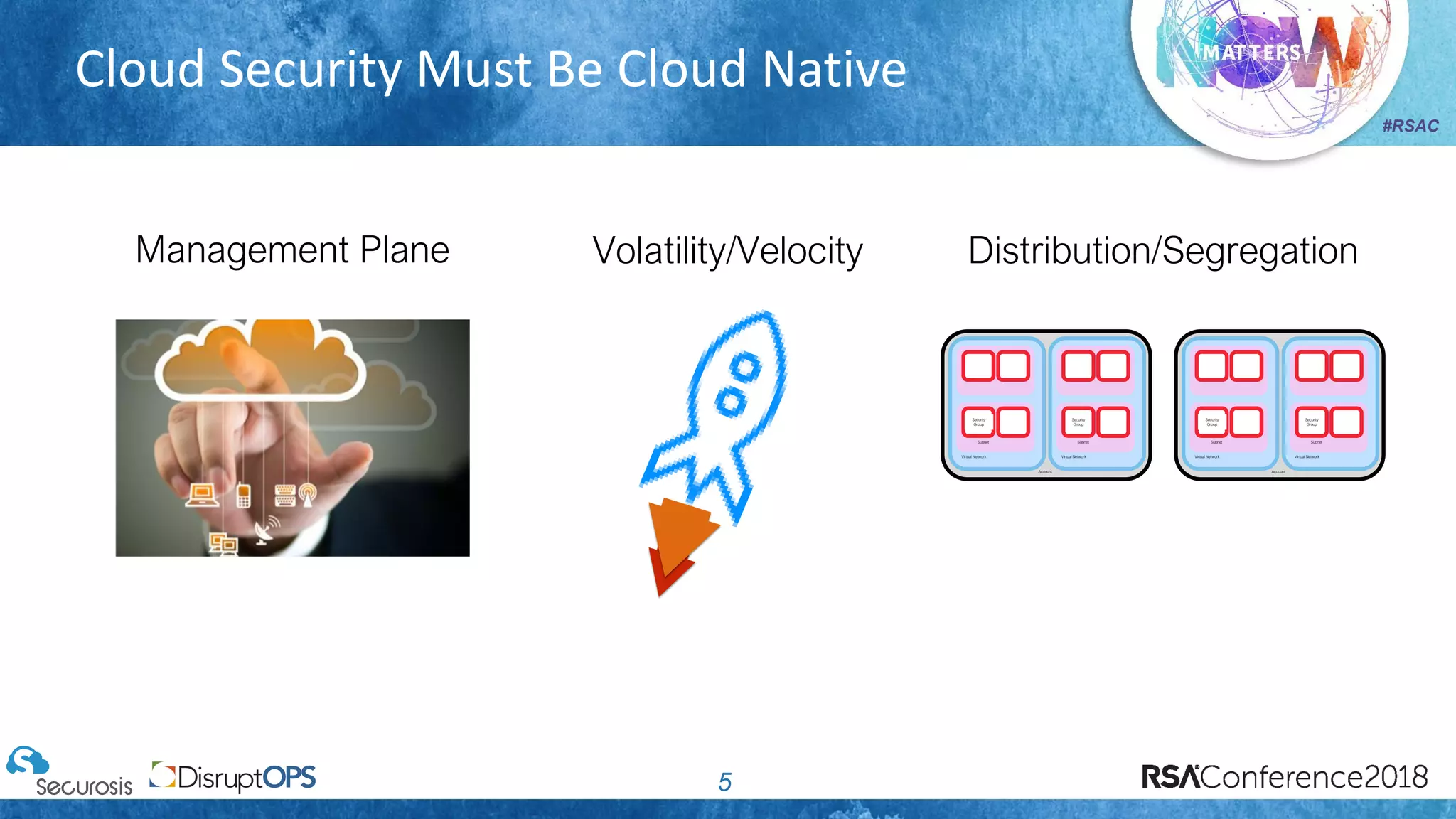
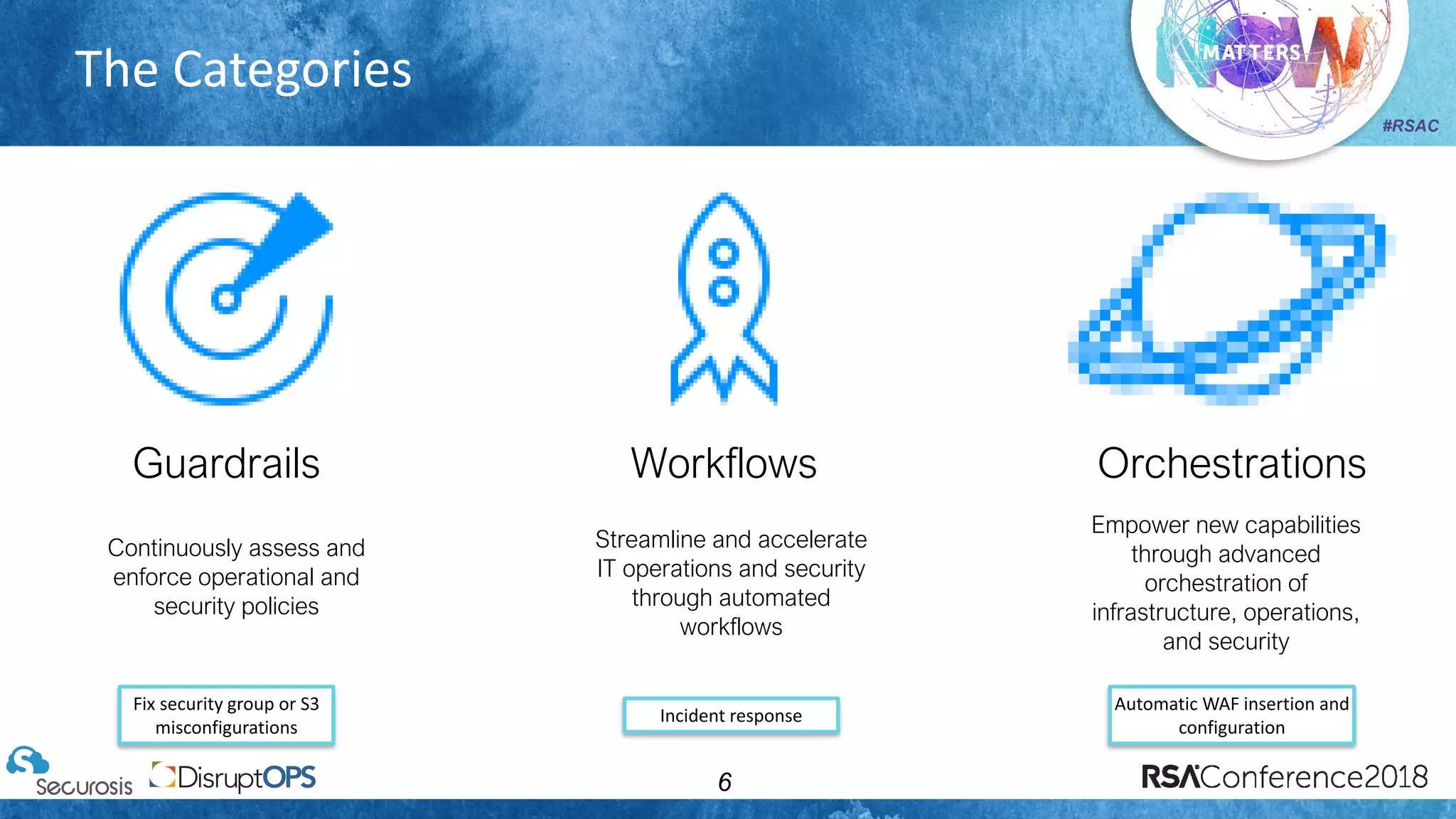
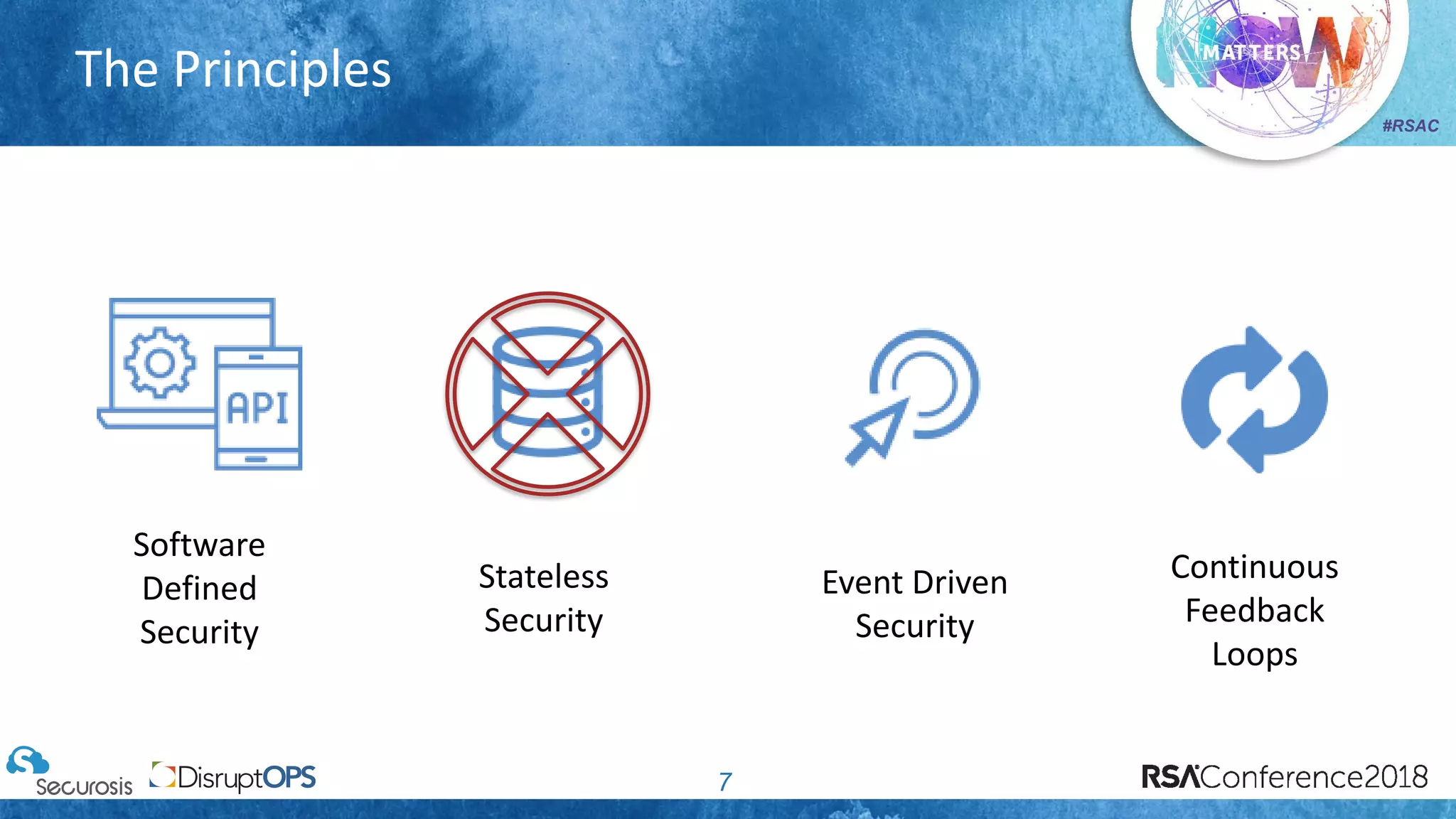
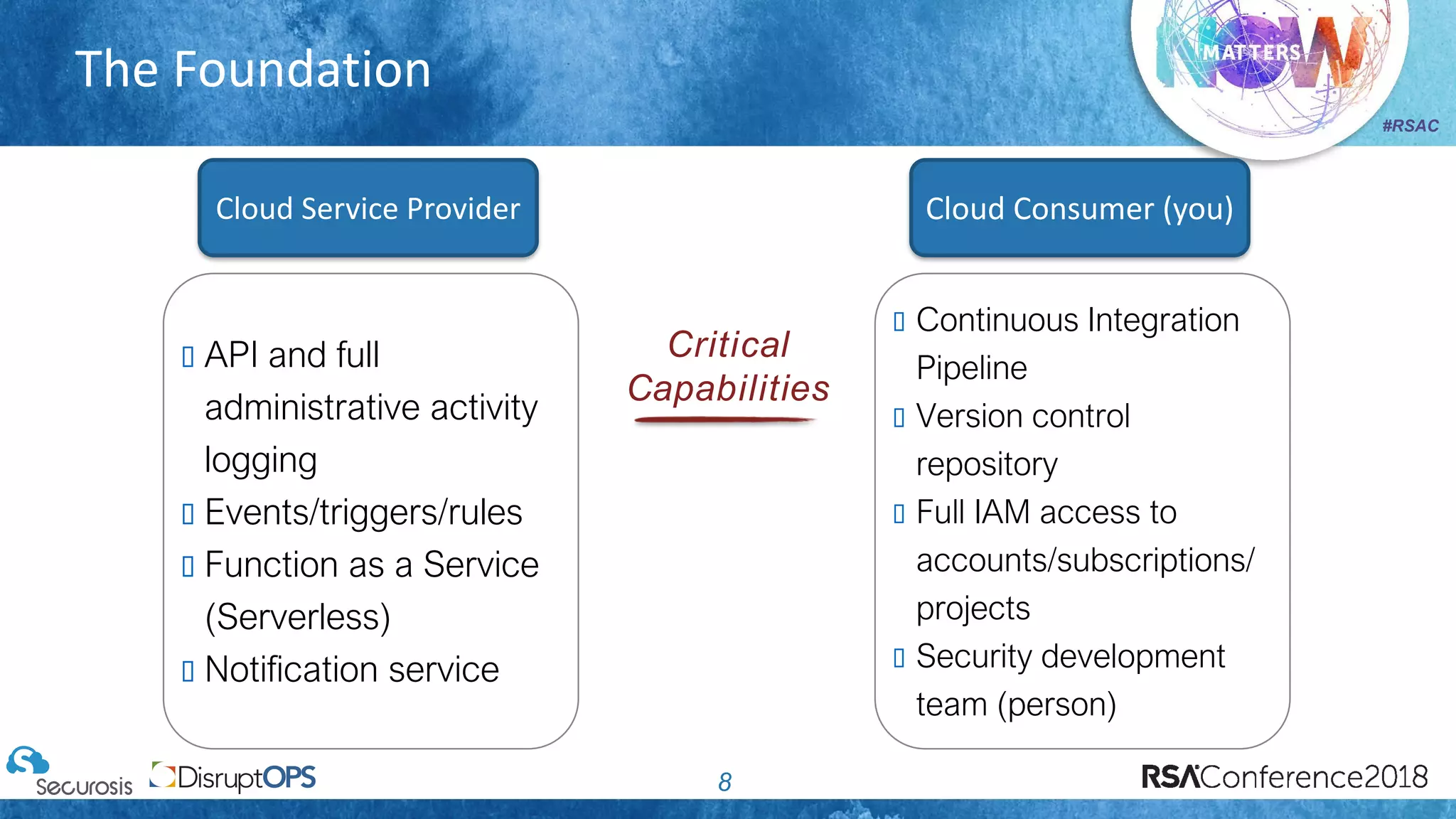
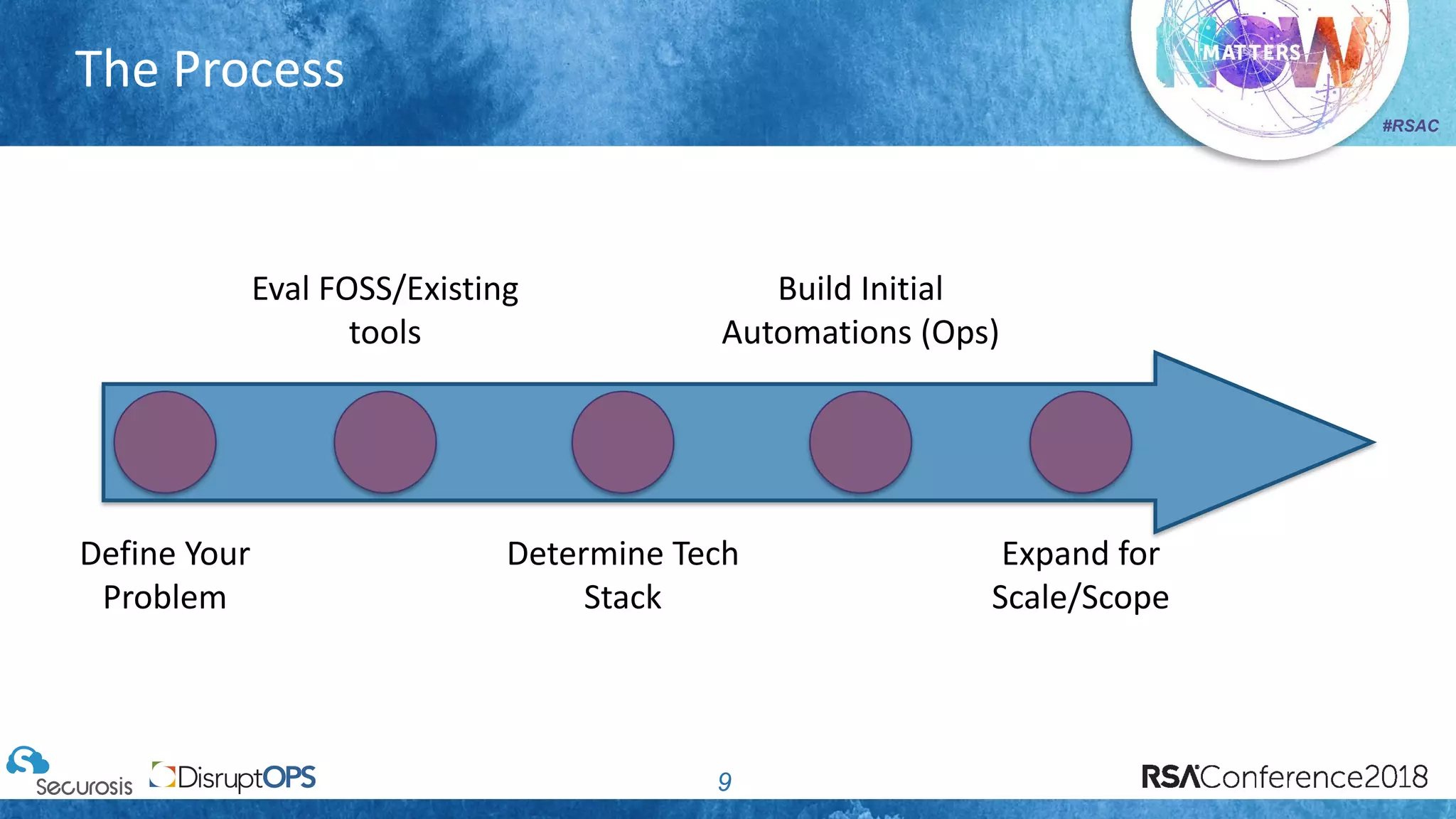
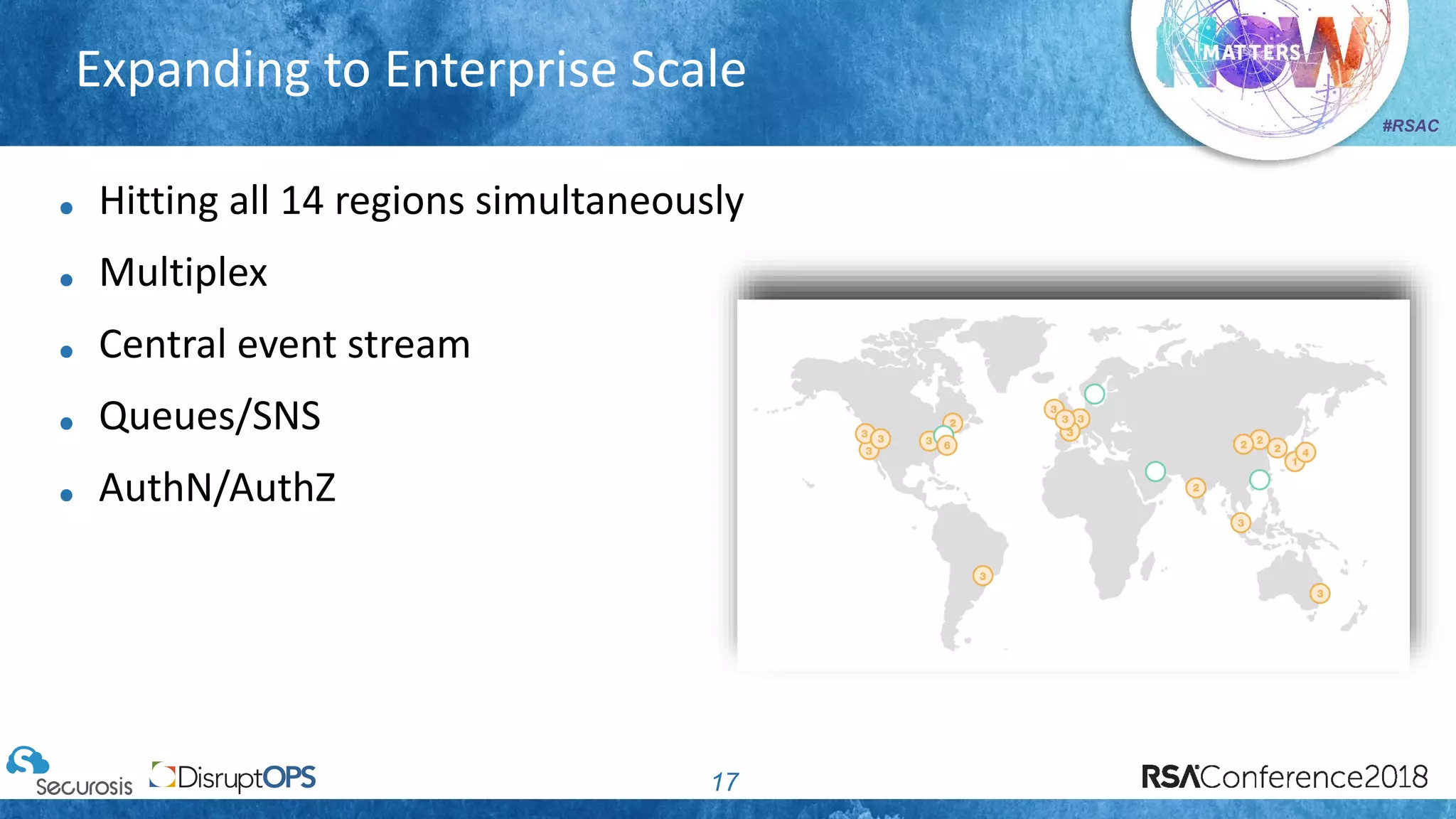
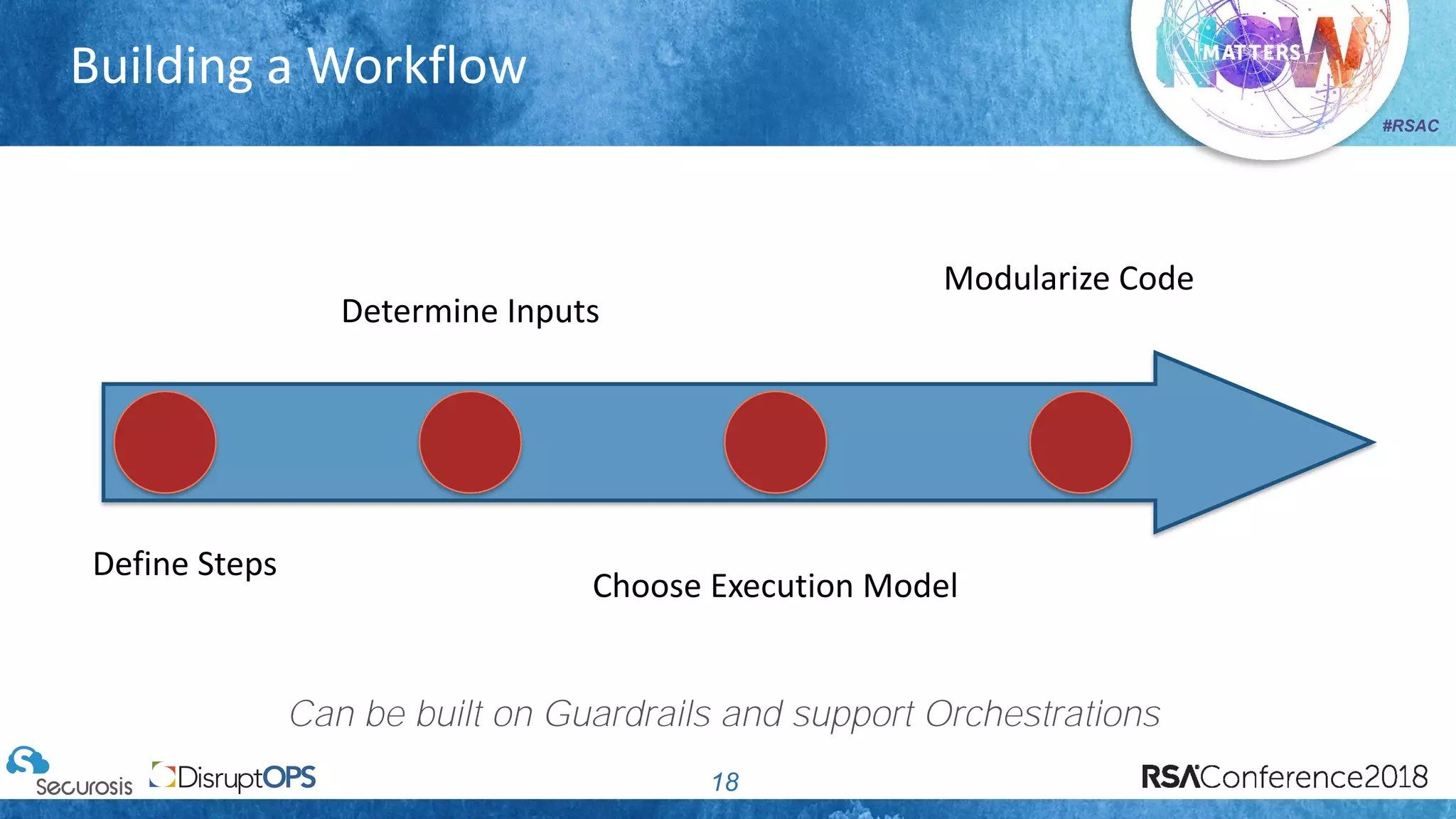
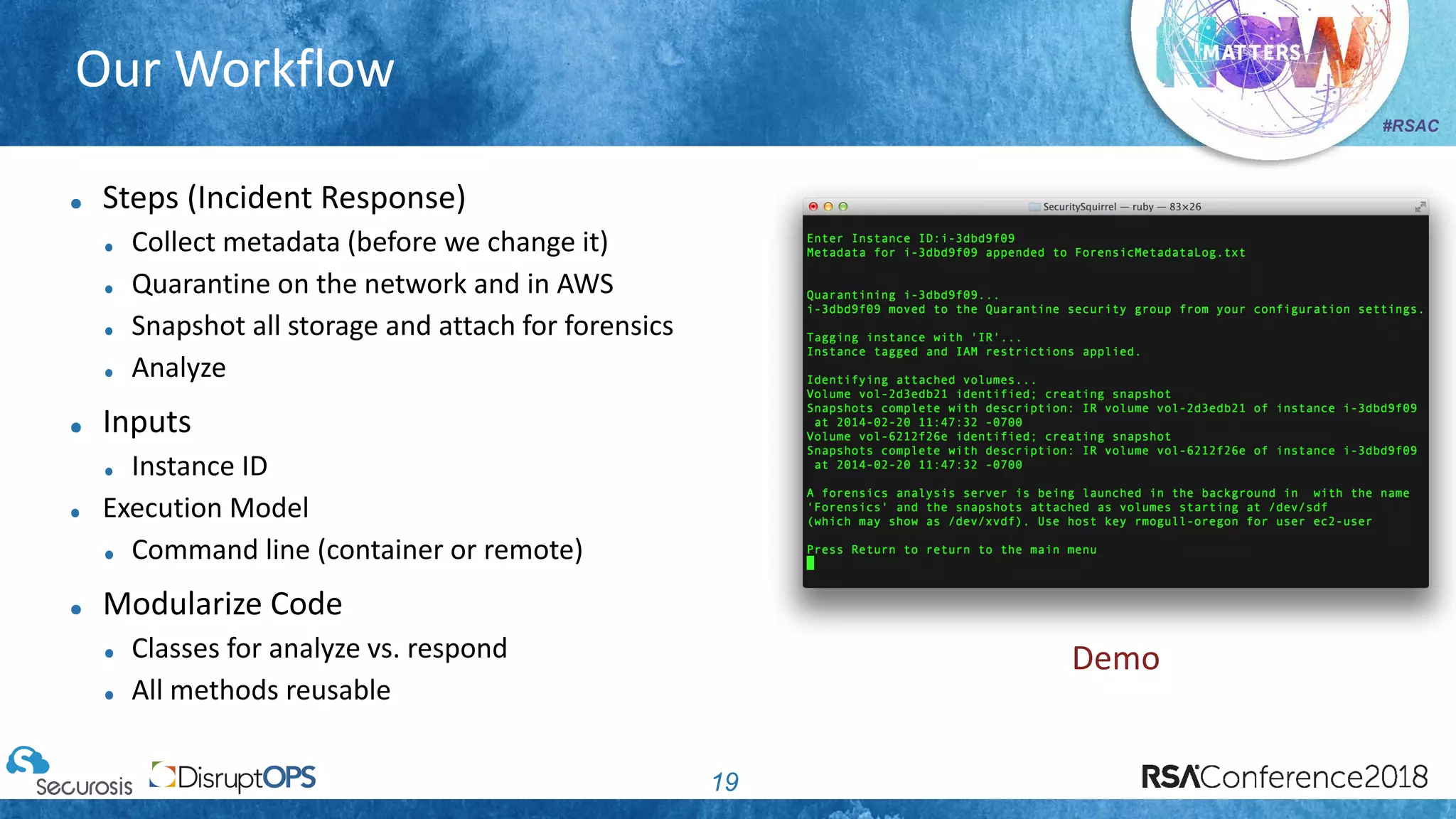
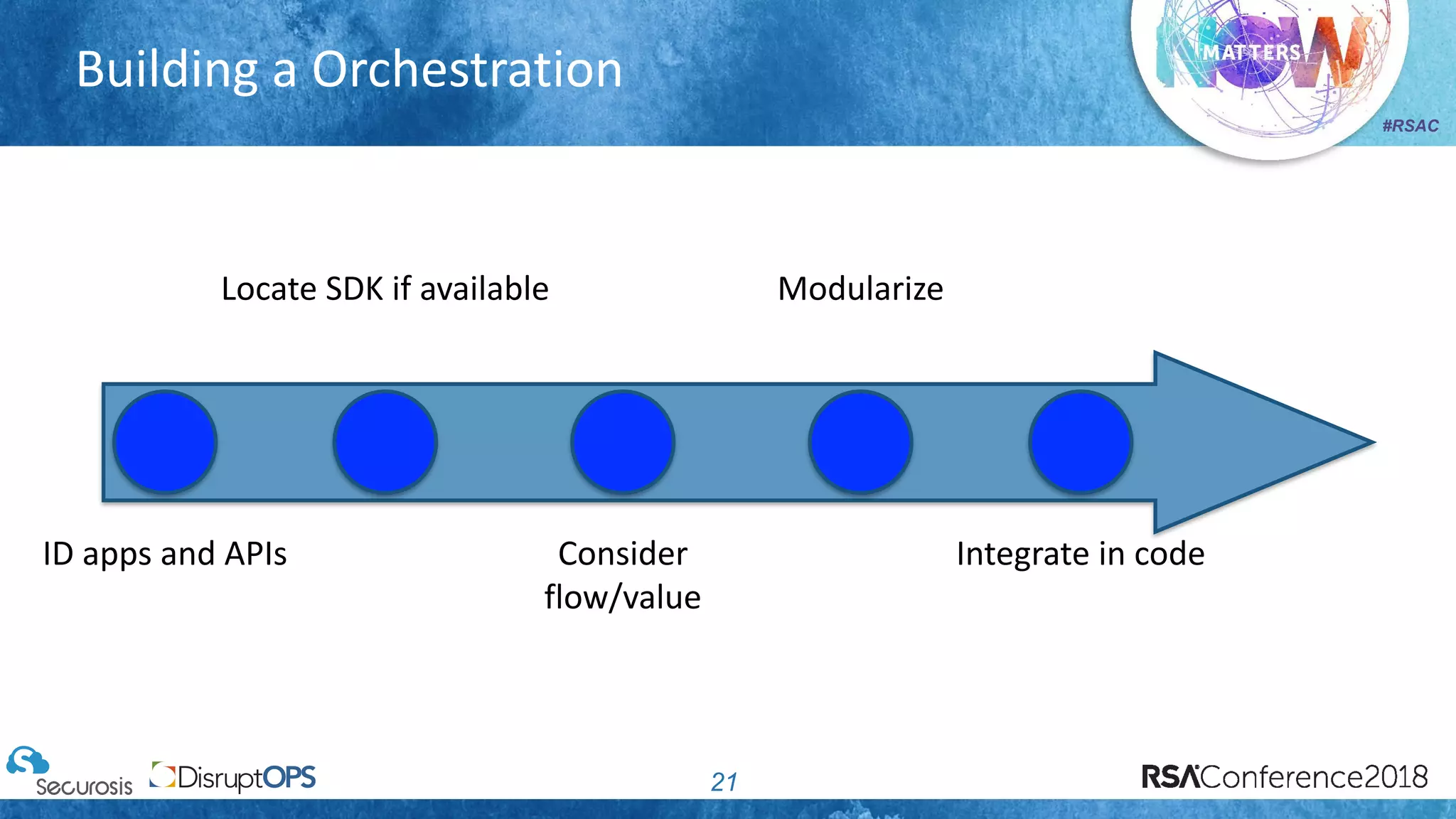
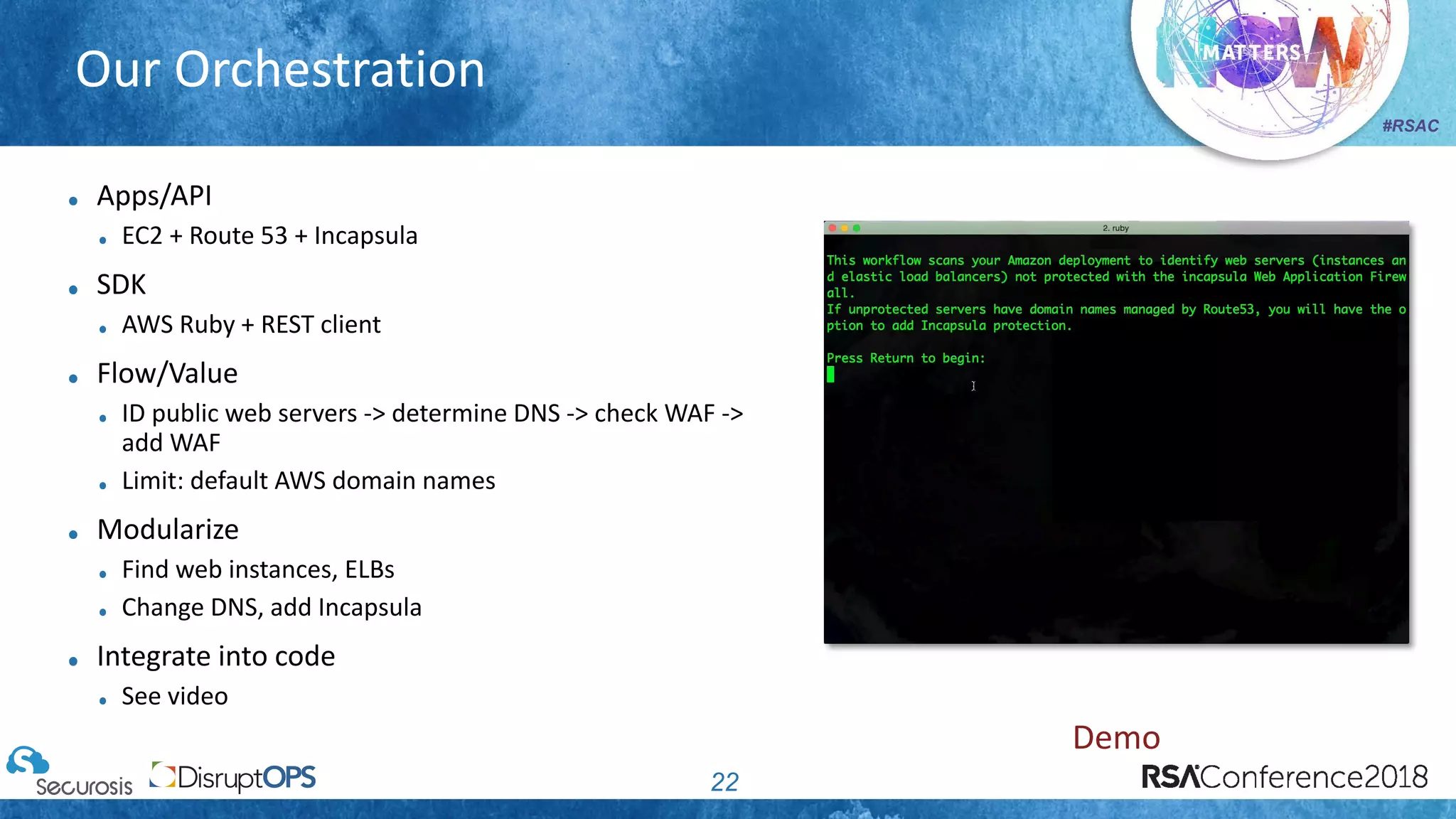
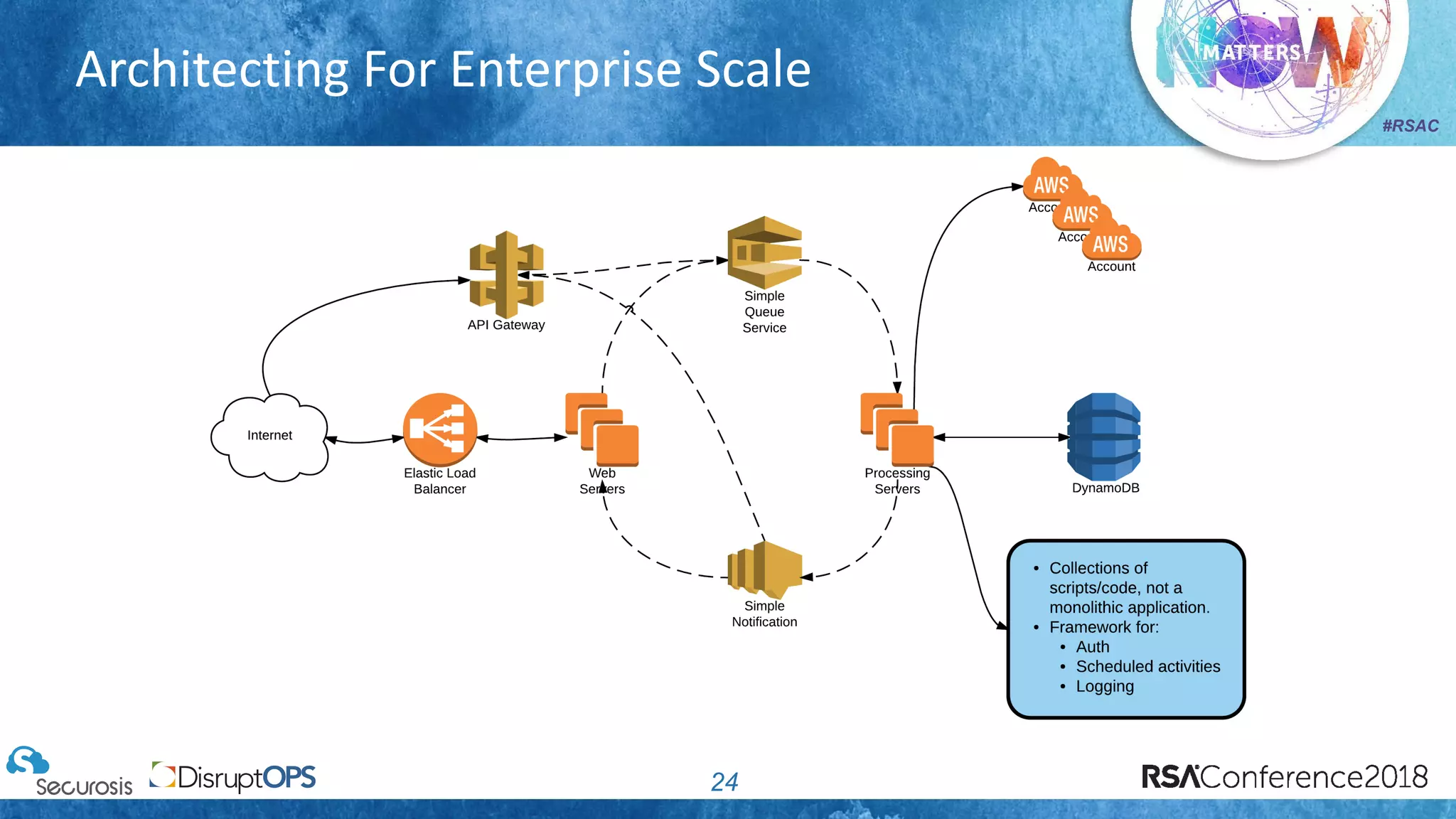
The document discusses pragmatic security automation strategies for cloud environments, emphasizing the importance of cloud-native security practices. It outlines principles such as software-defined security, event-driven models, and the use of guardrails for managing cloud resources effectively. Recommendations for implementing automation include defining problems, building workflows, and using event-driven guardrails to enhance operational security and efficiency.