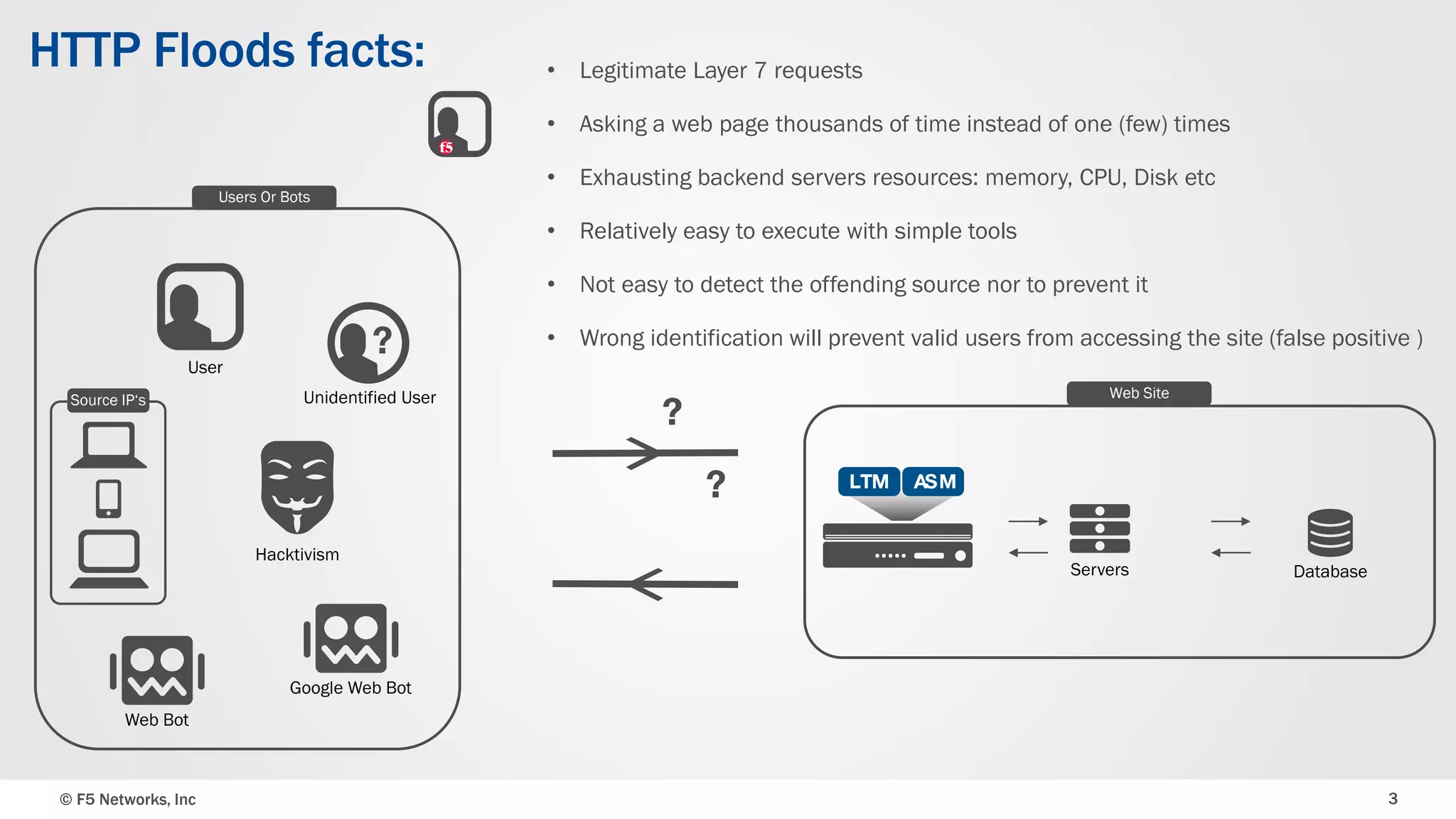
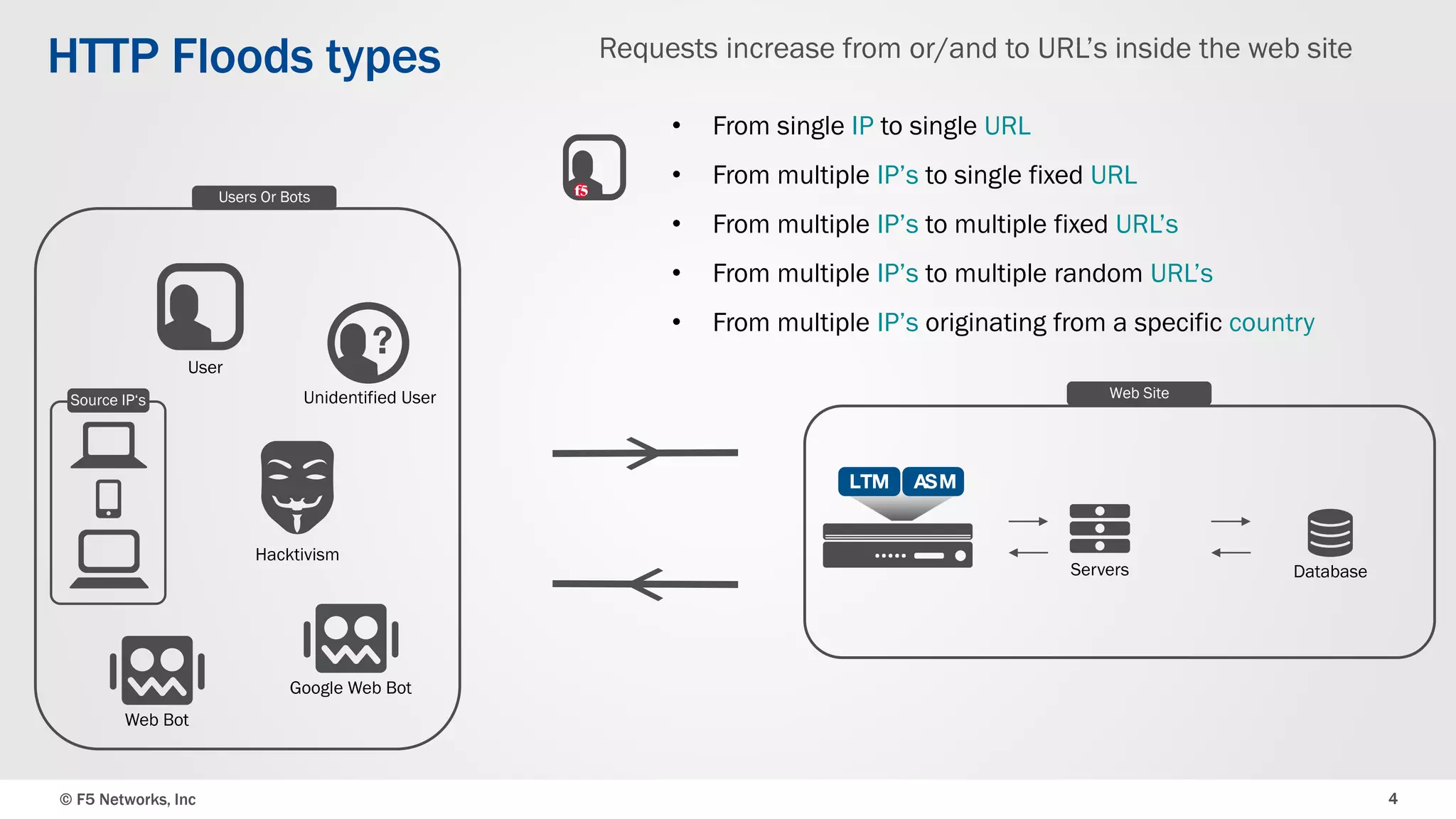
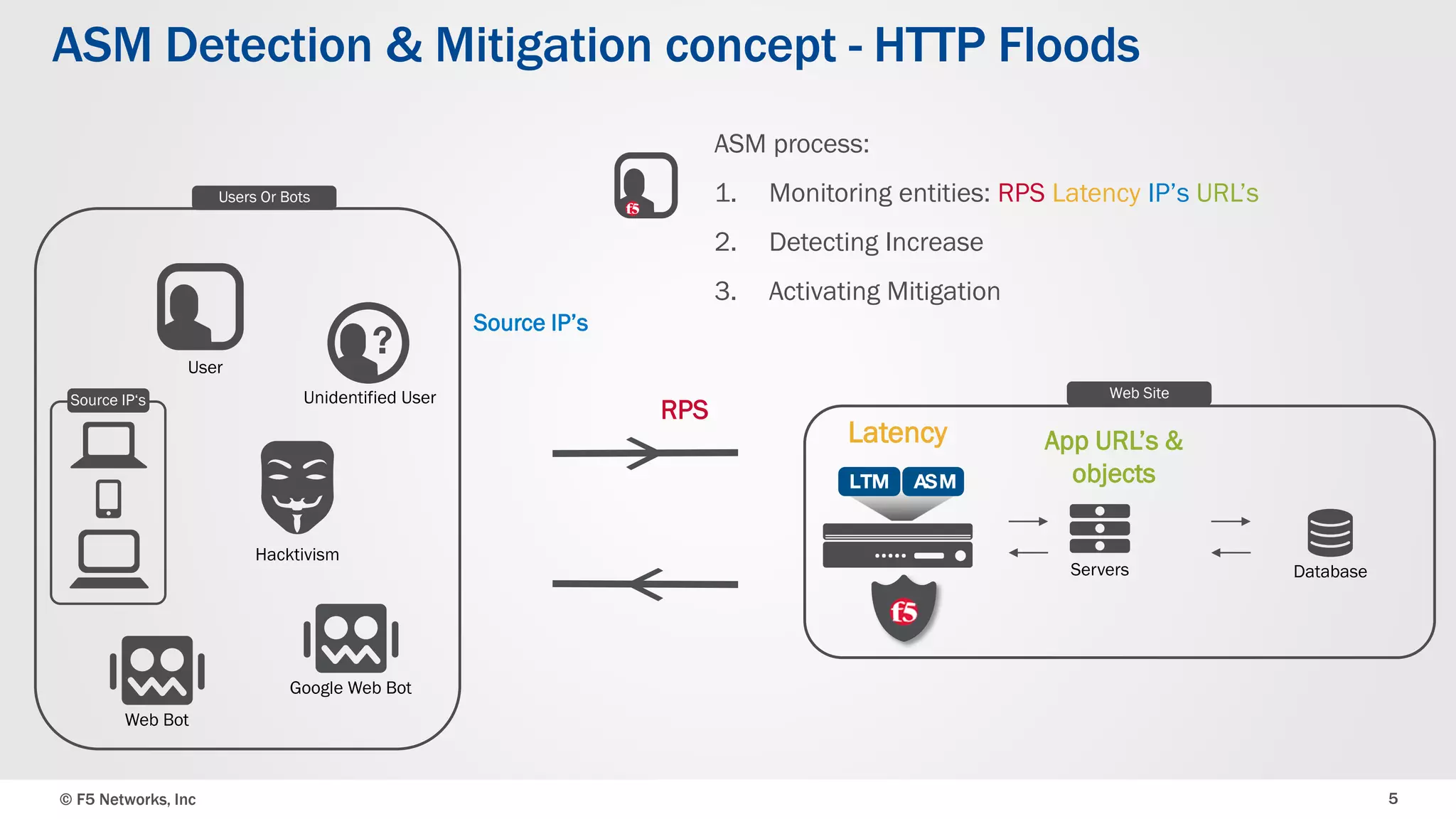
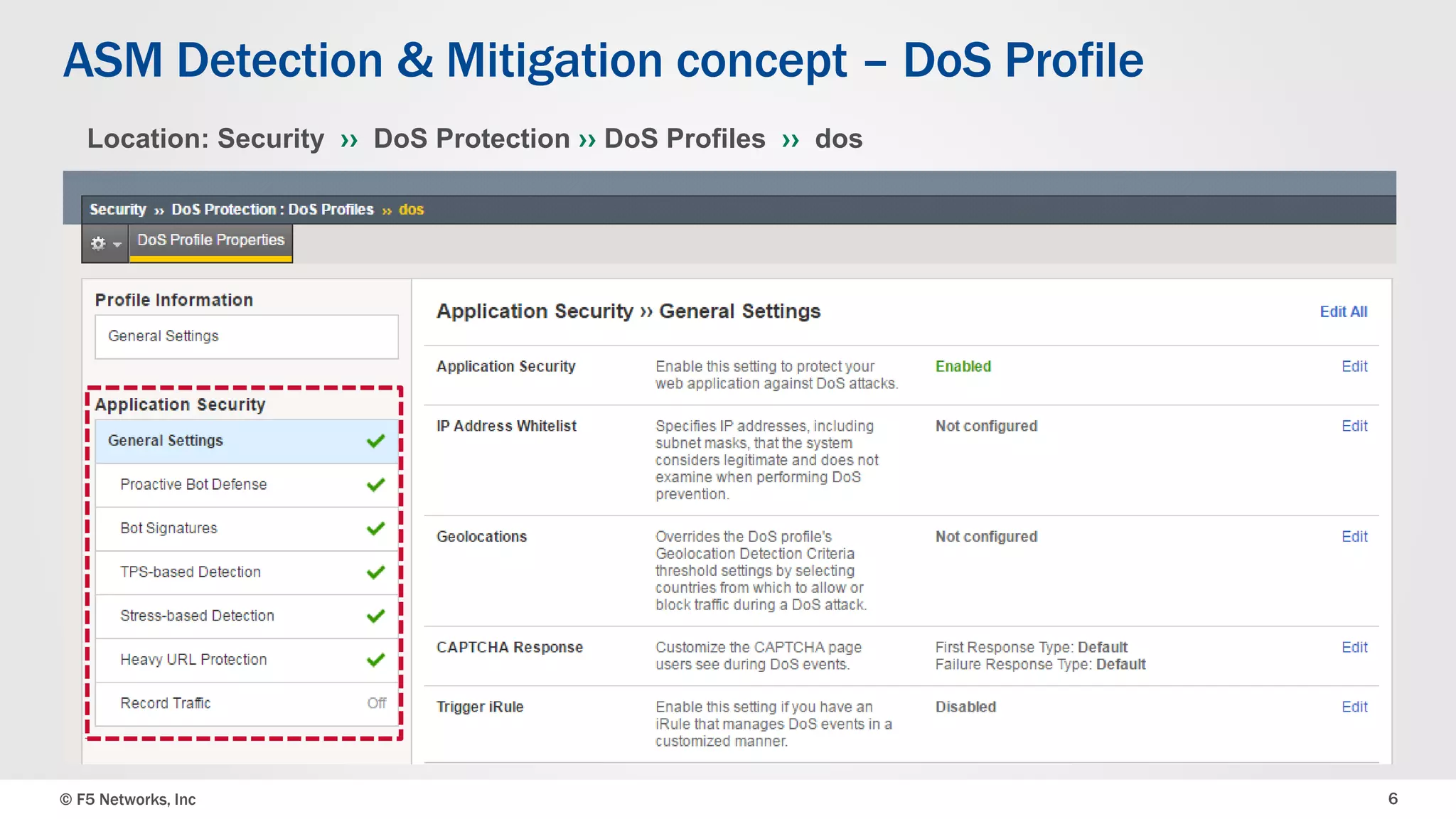
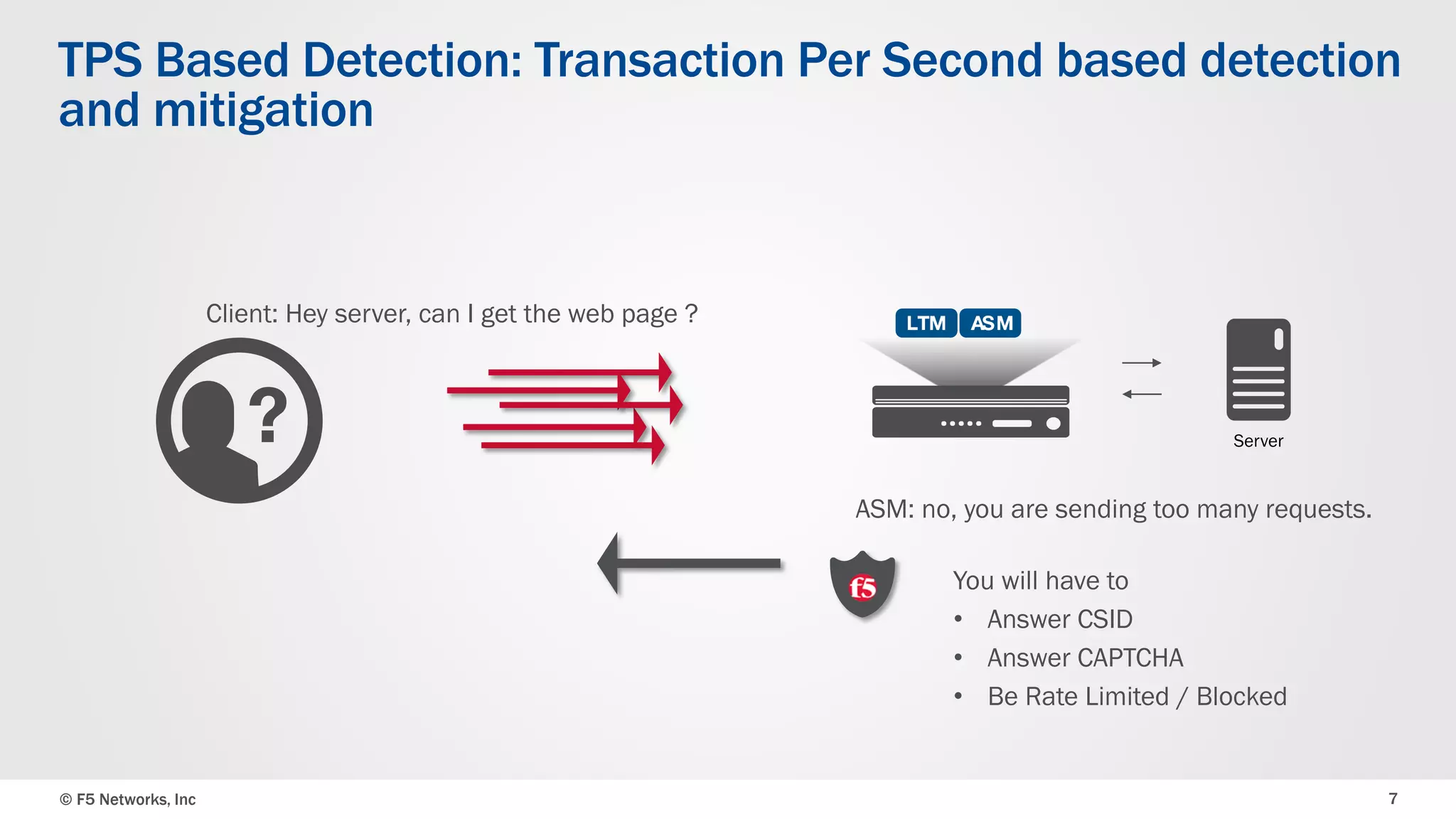
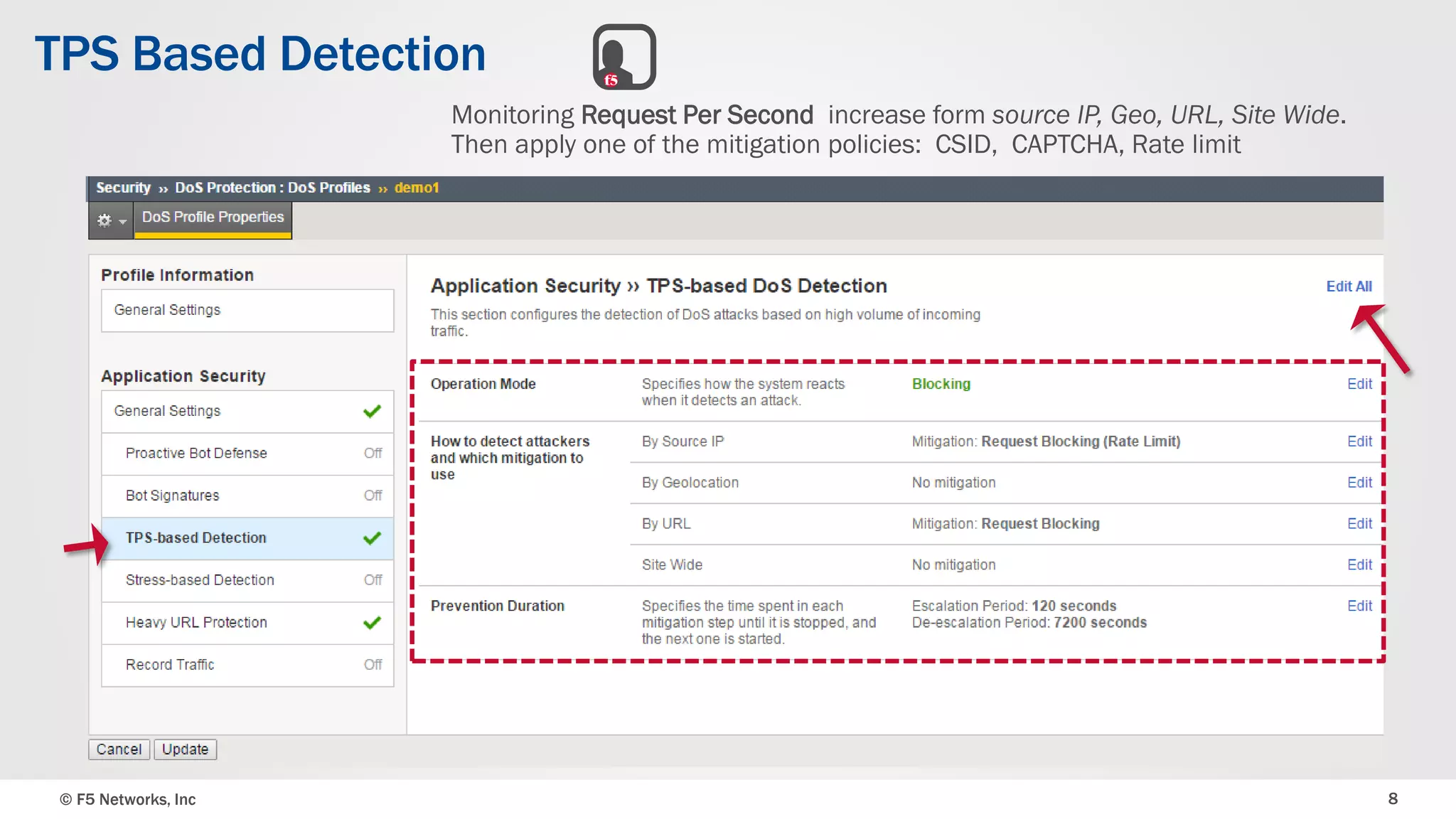
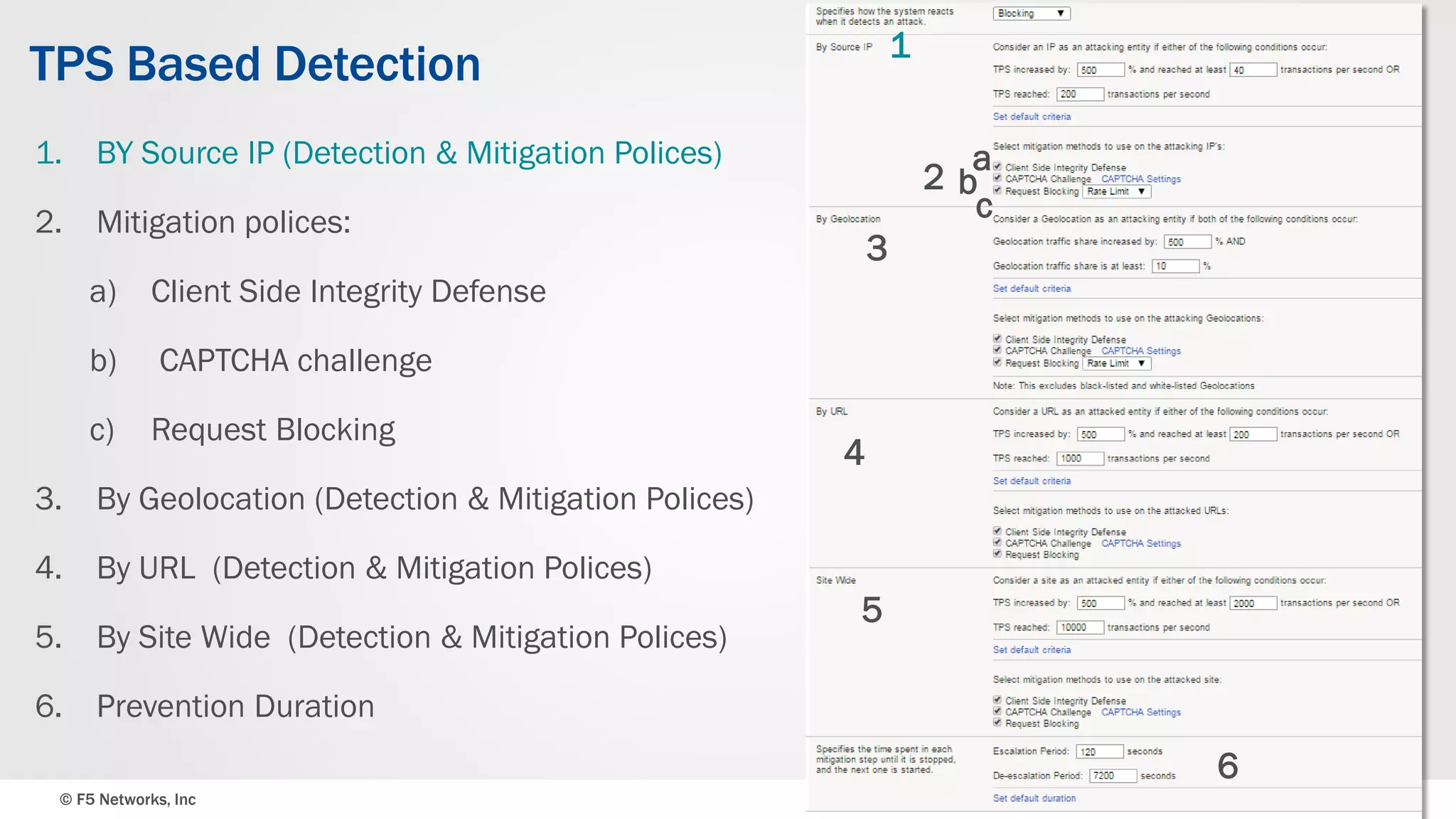
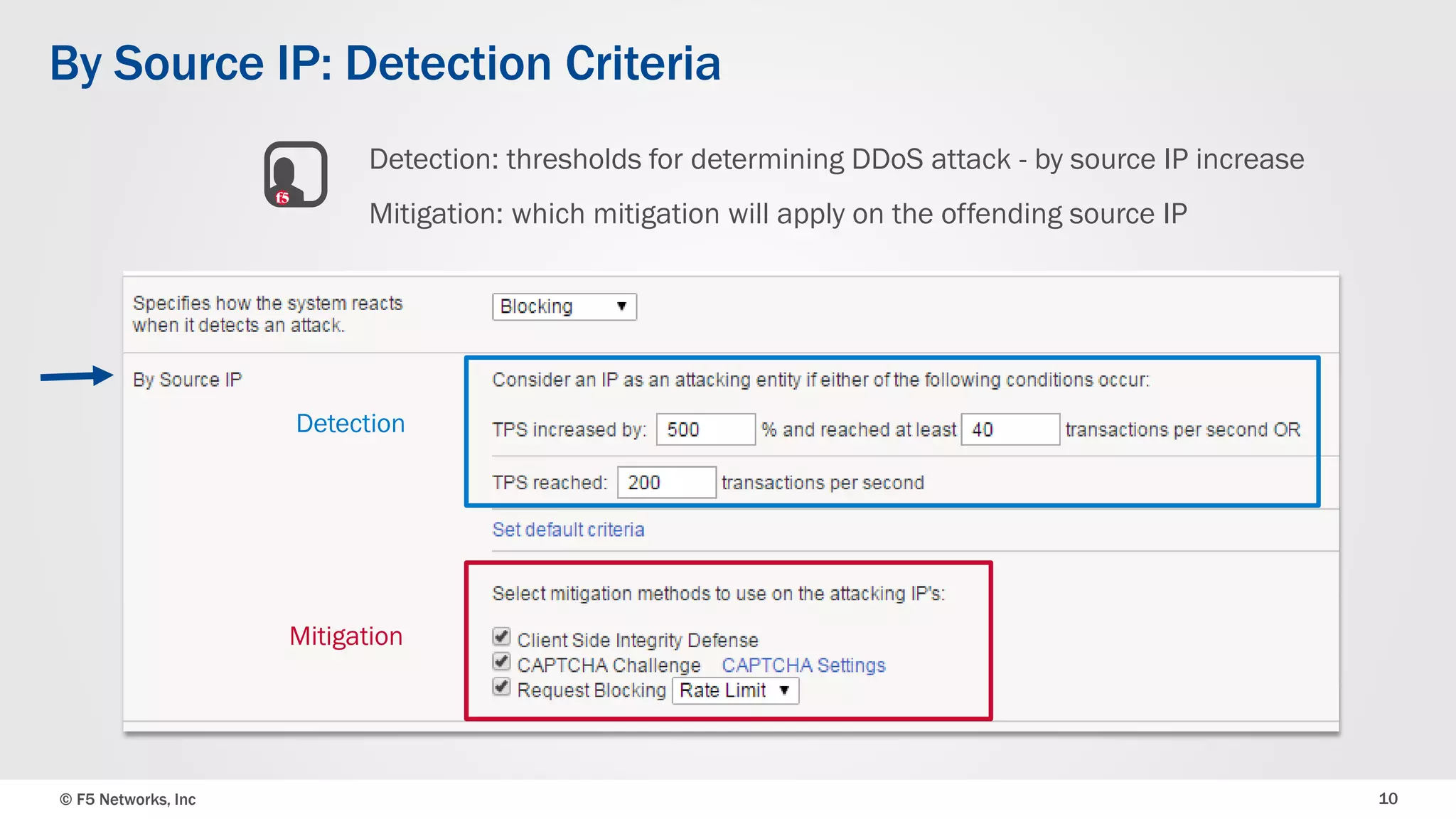
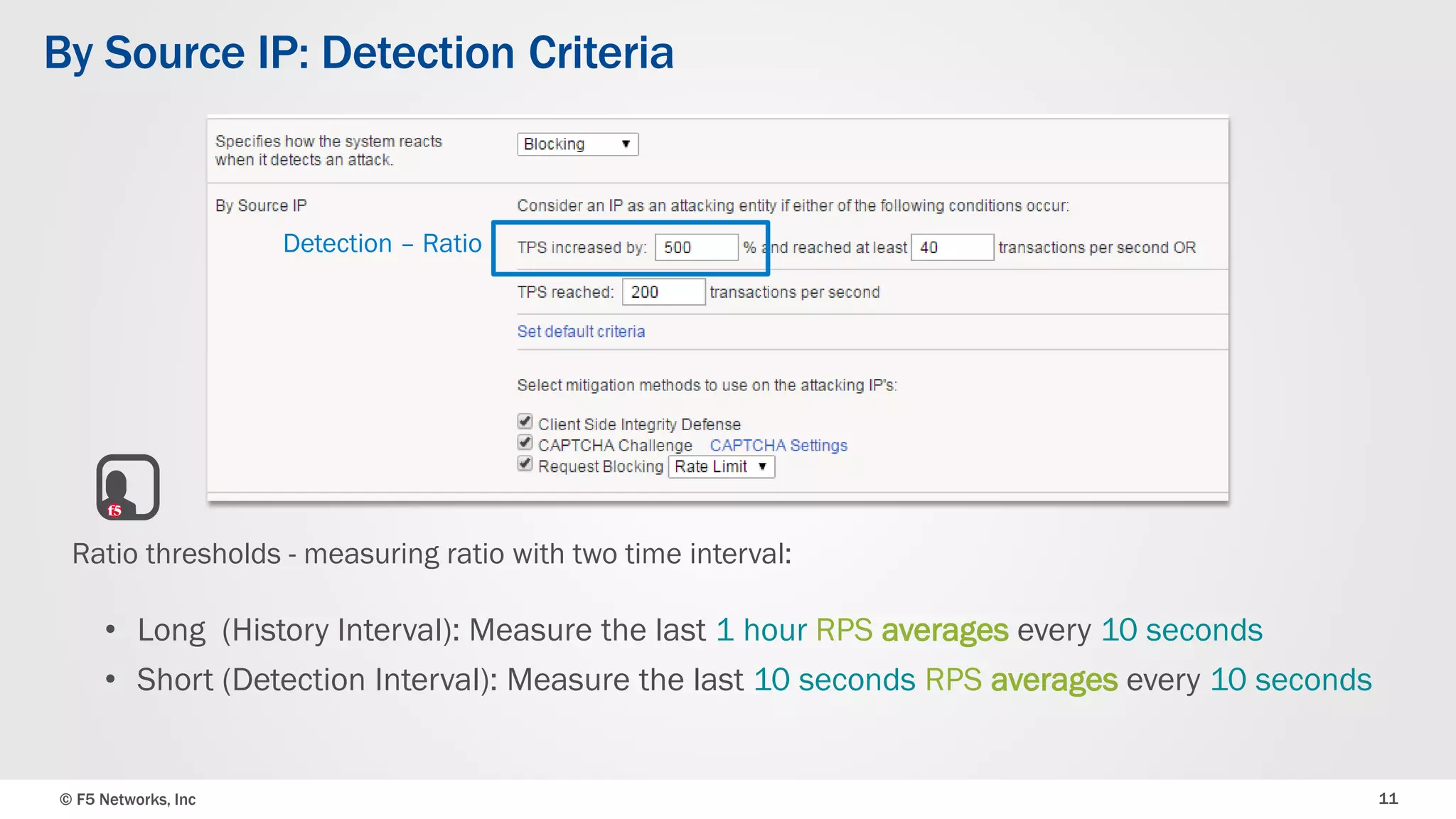
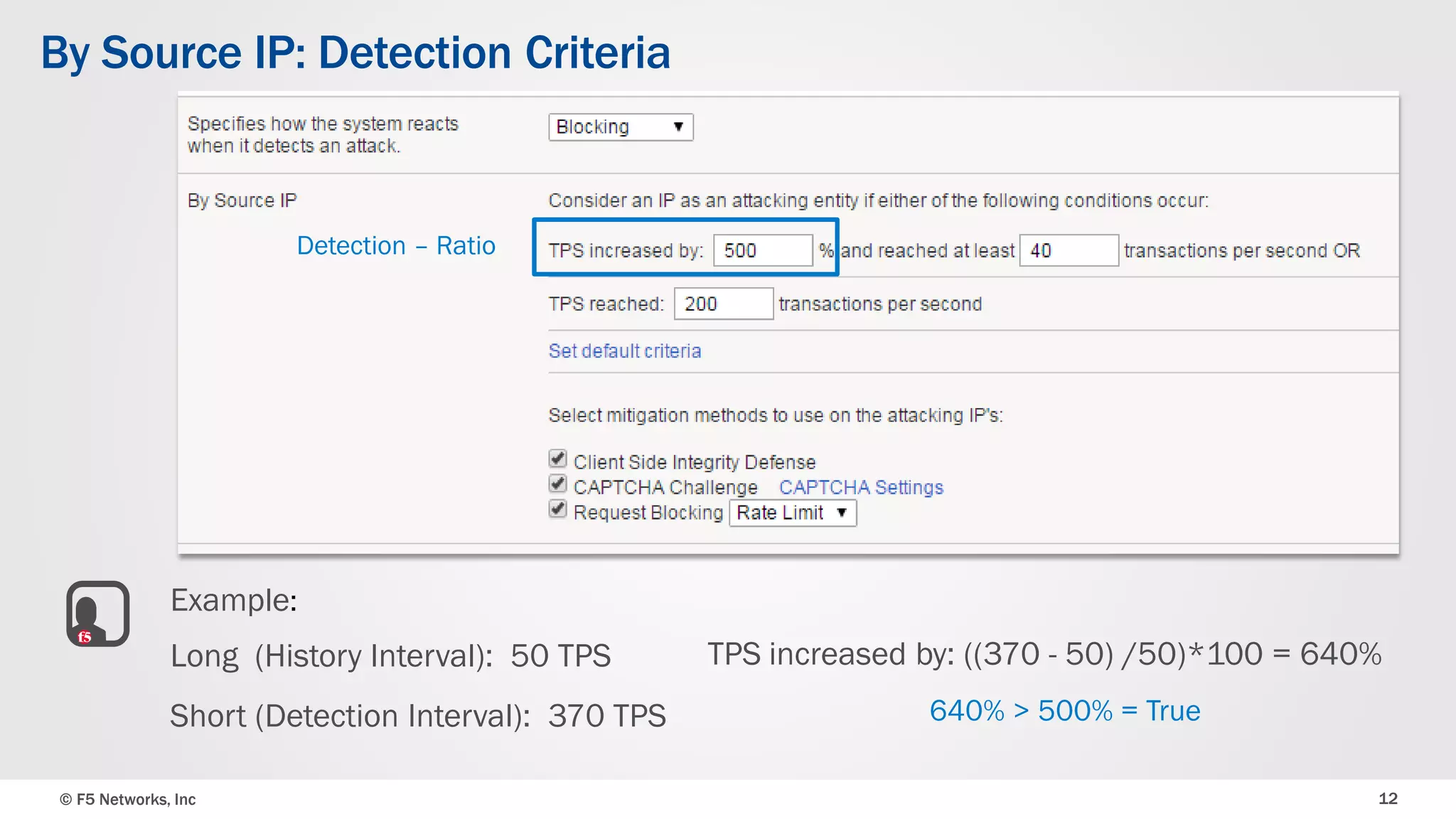
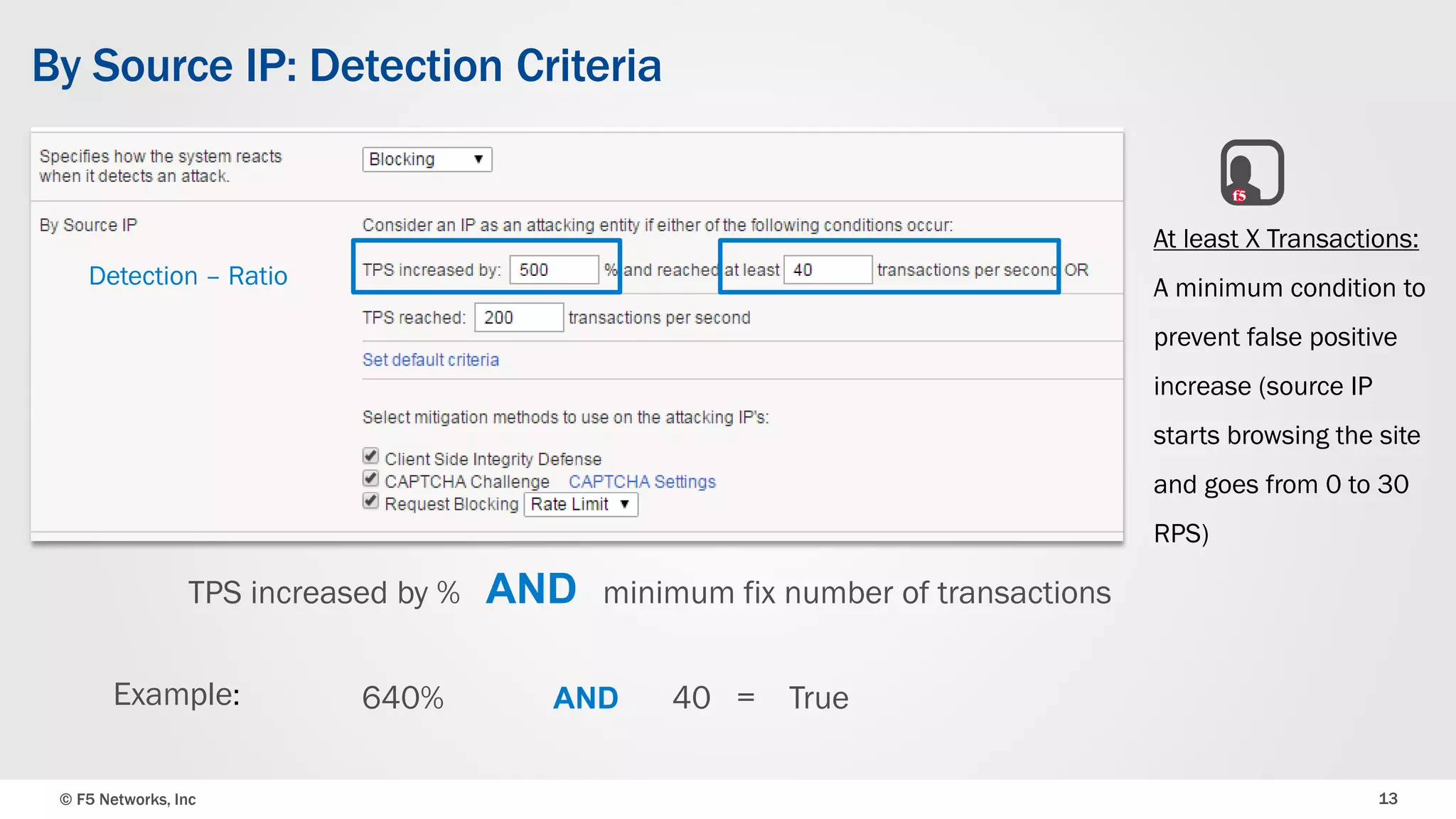
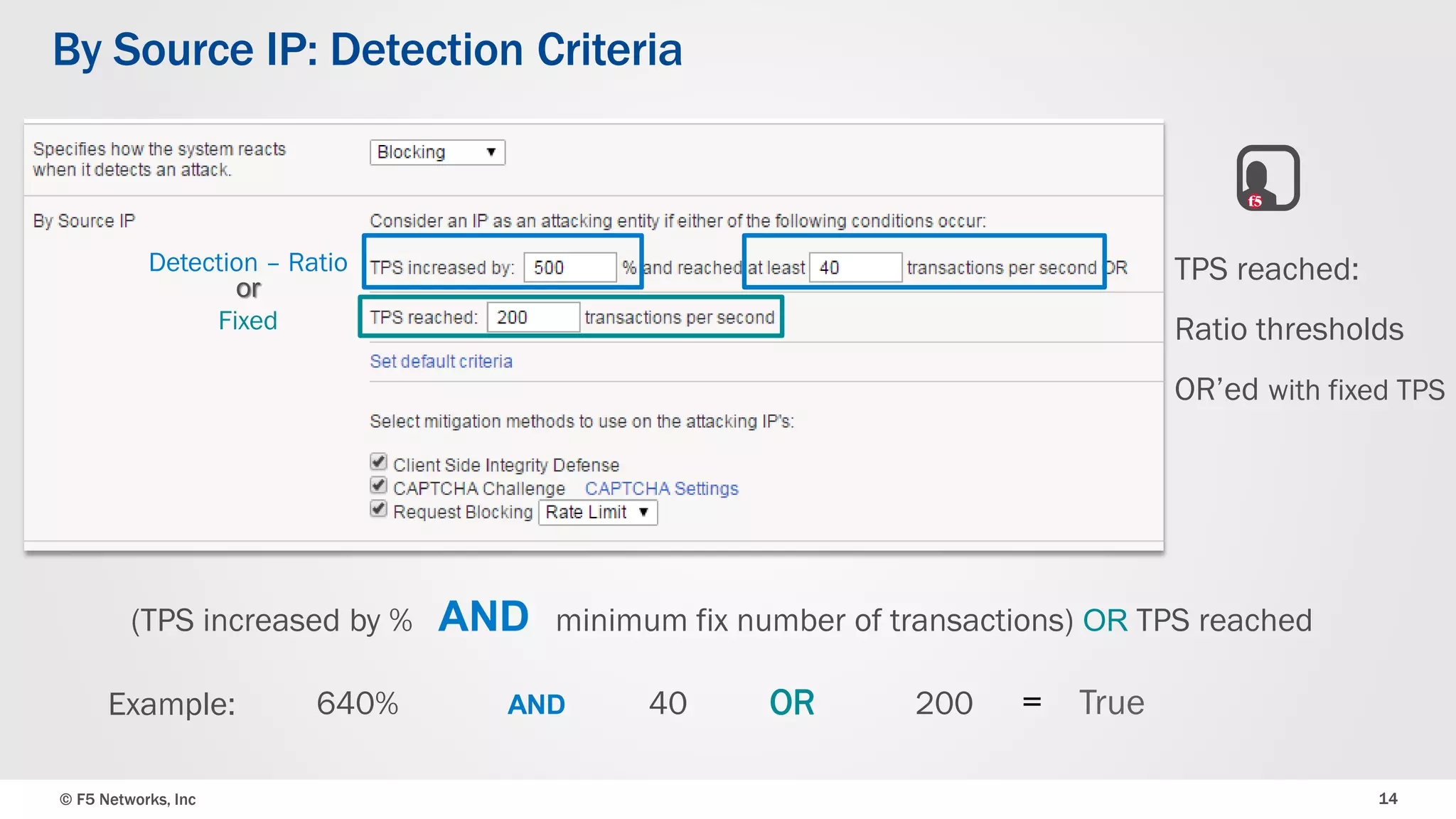
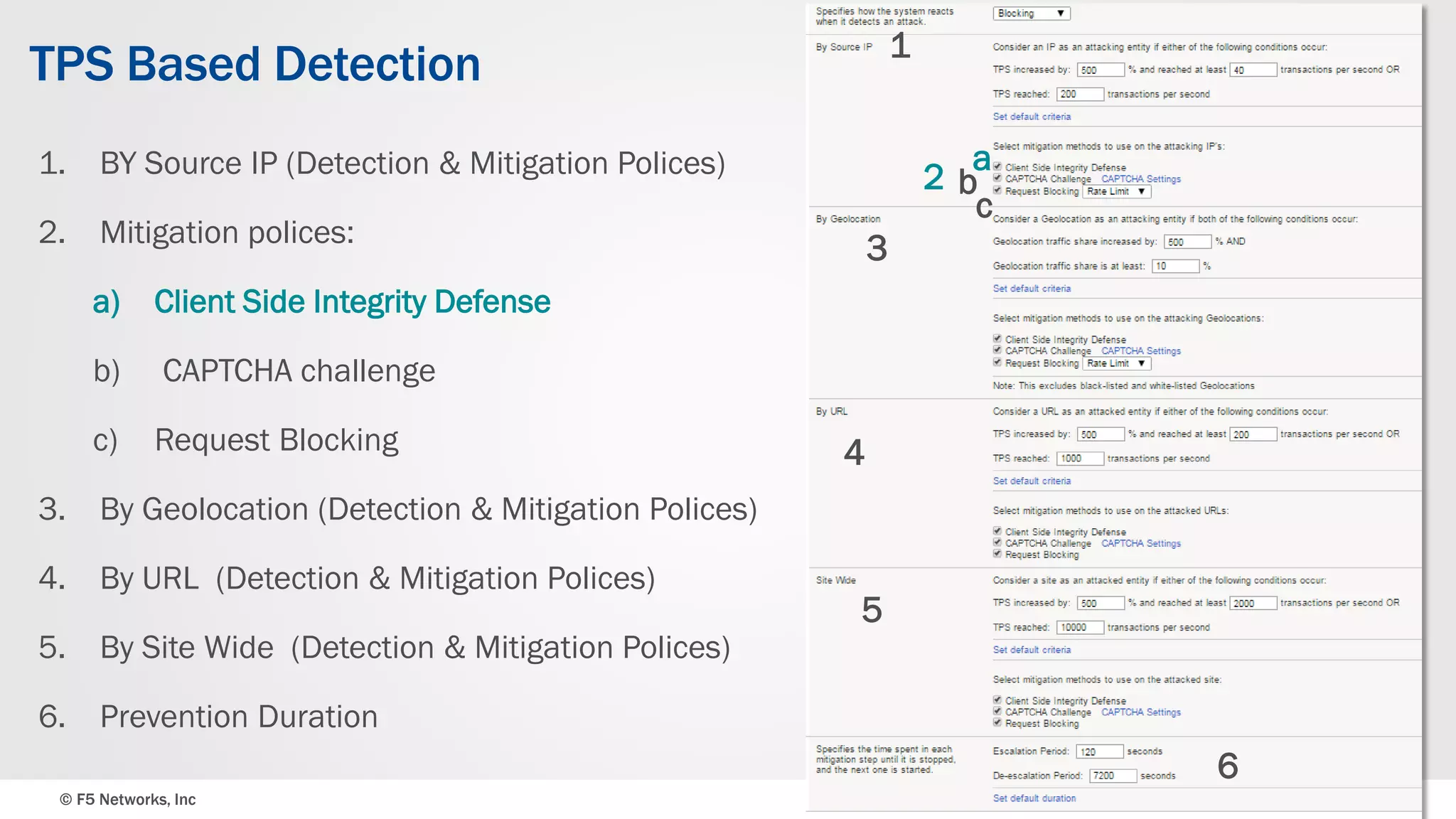
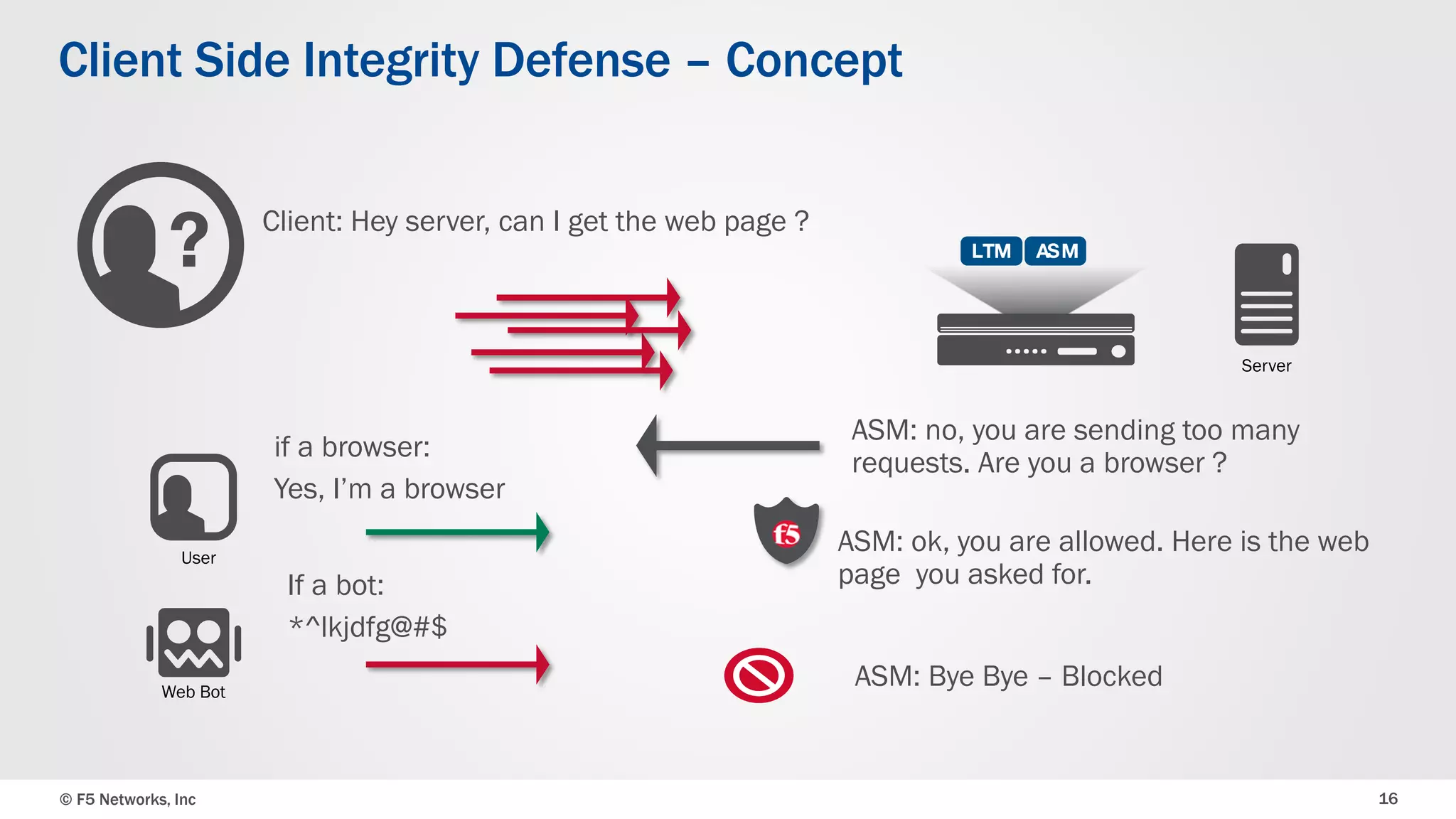
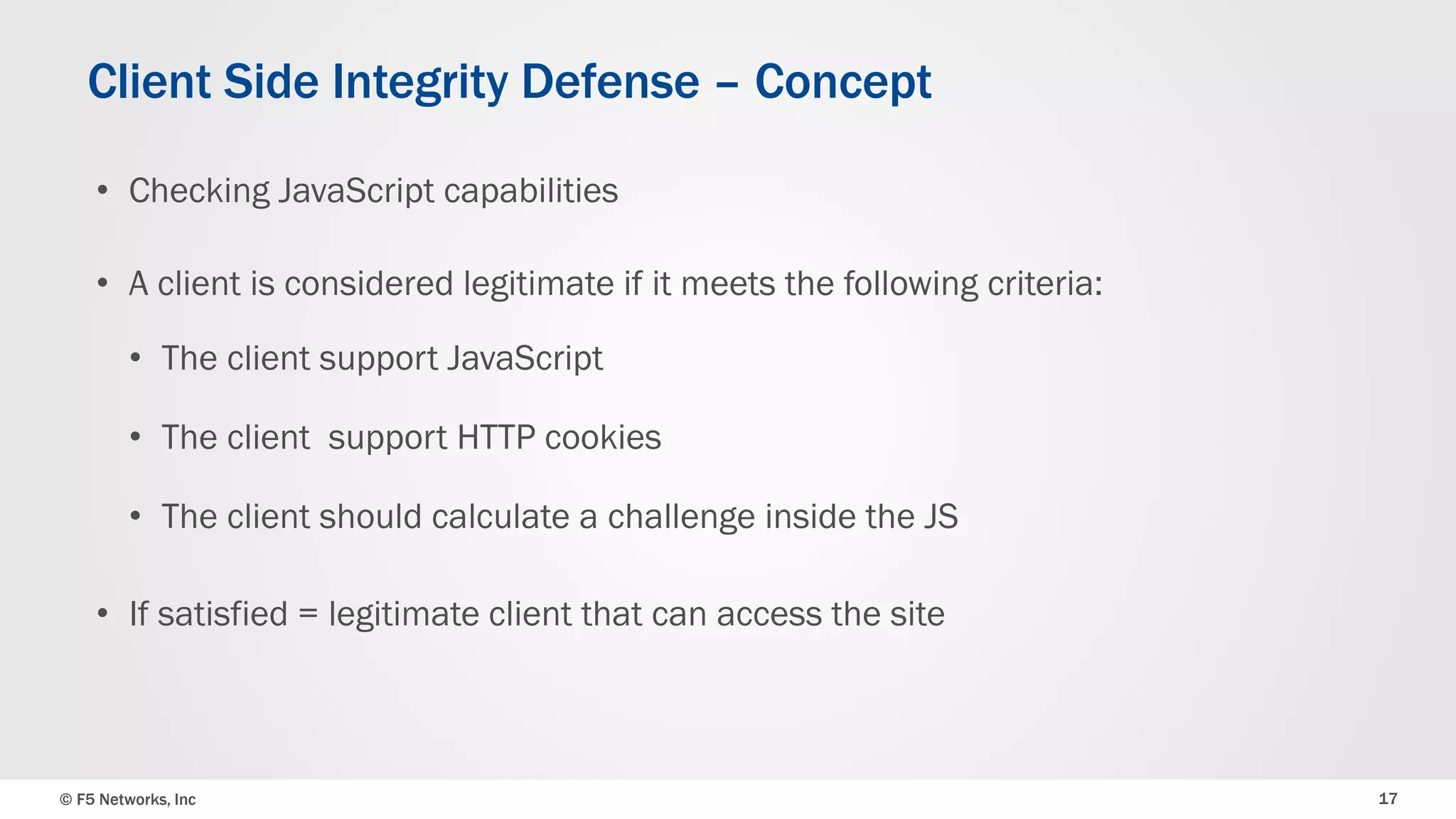
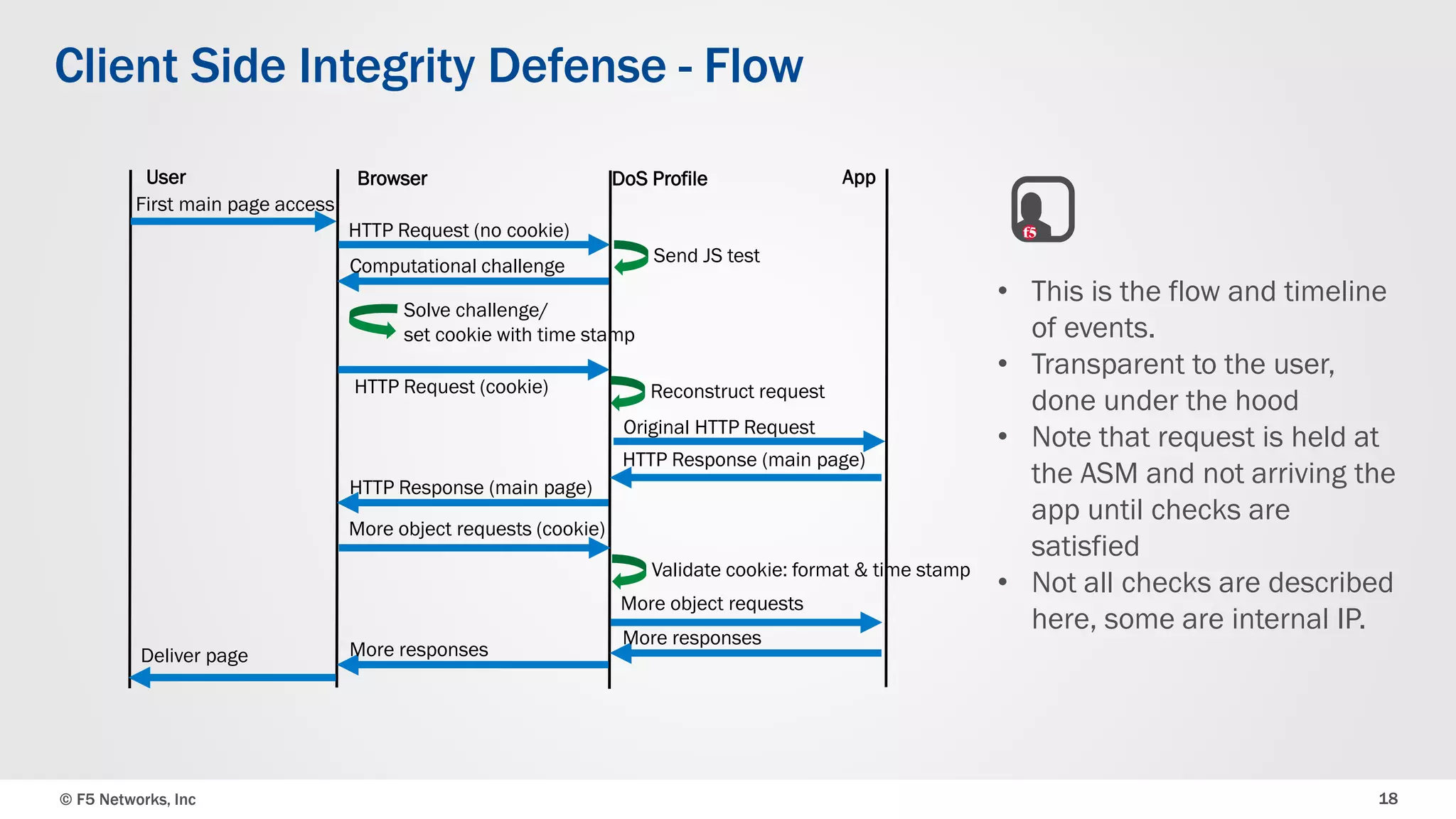
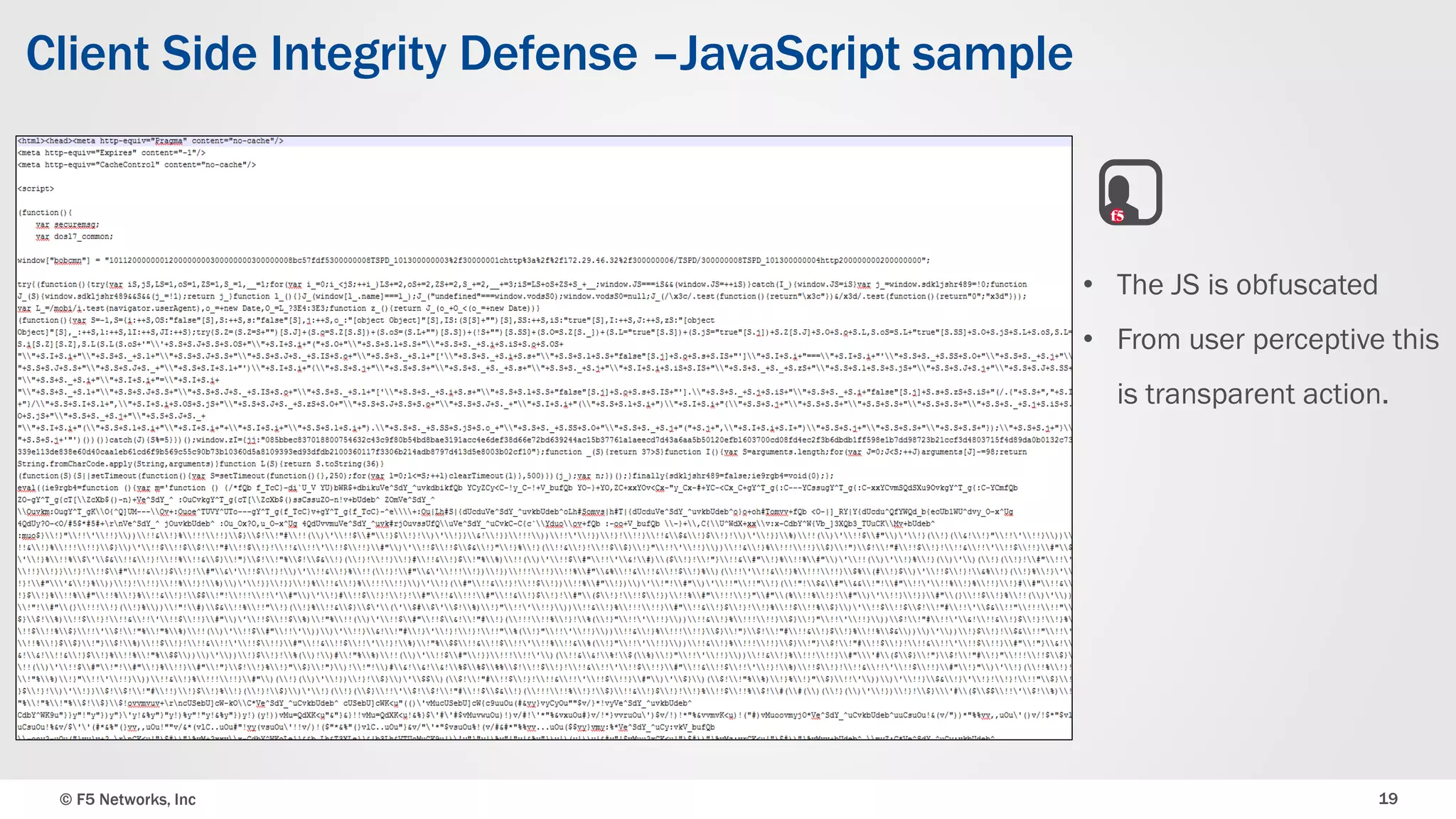
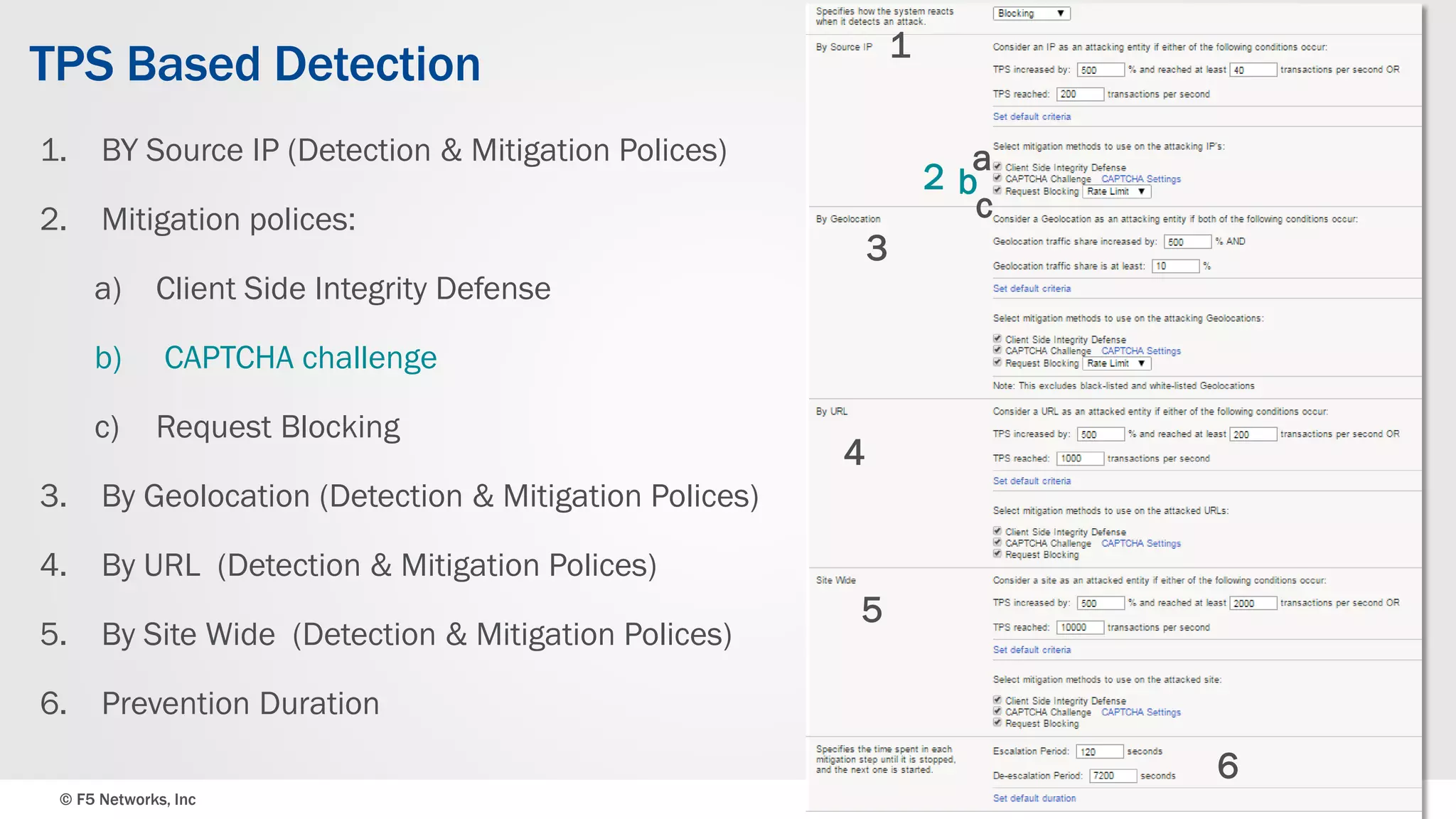
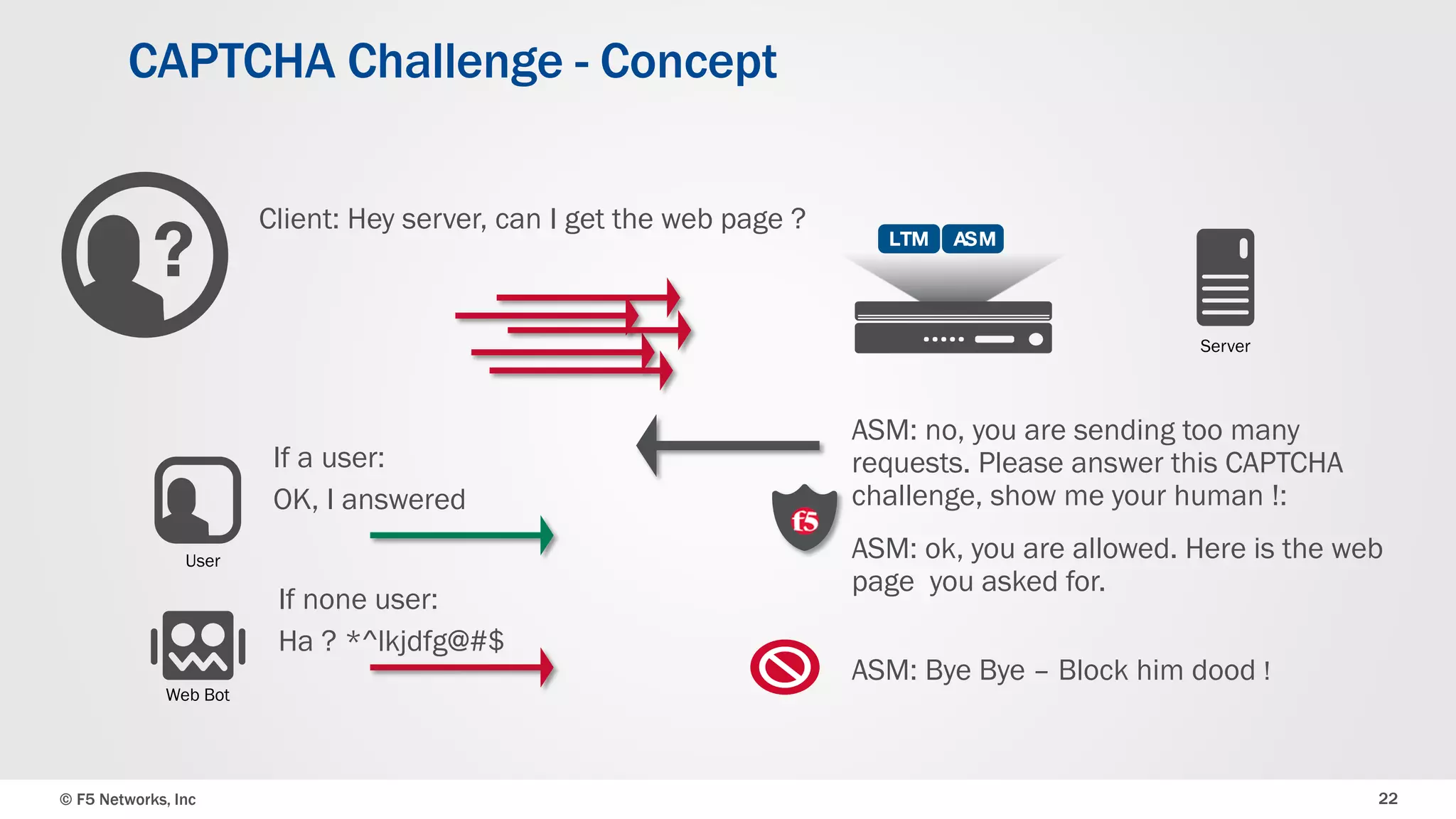
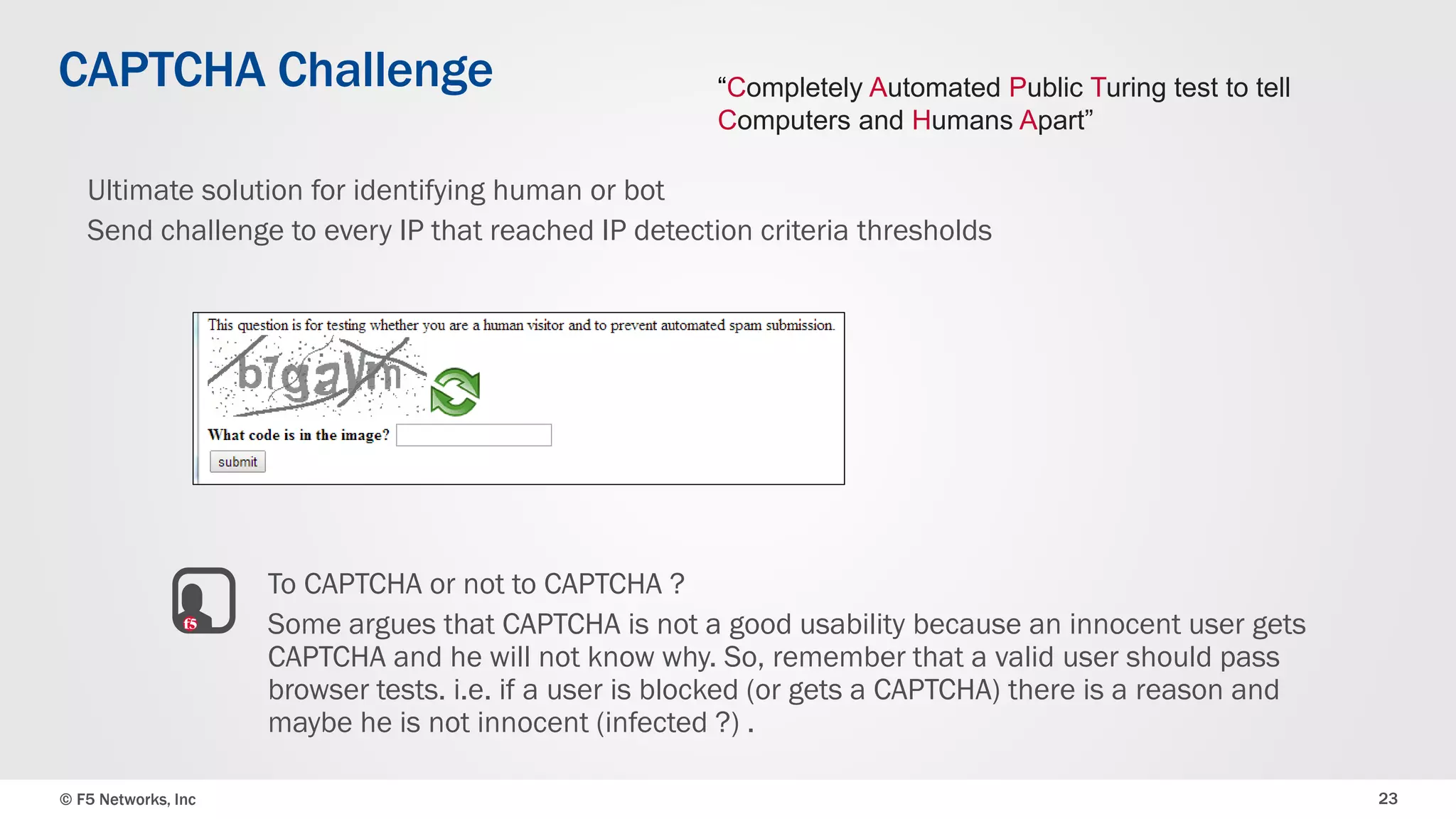
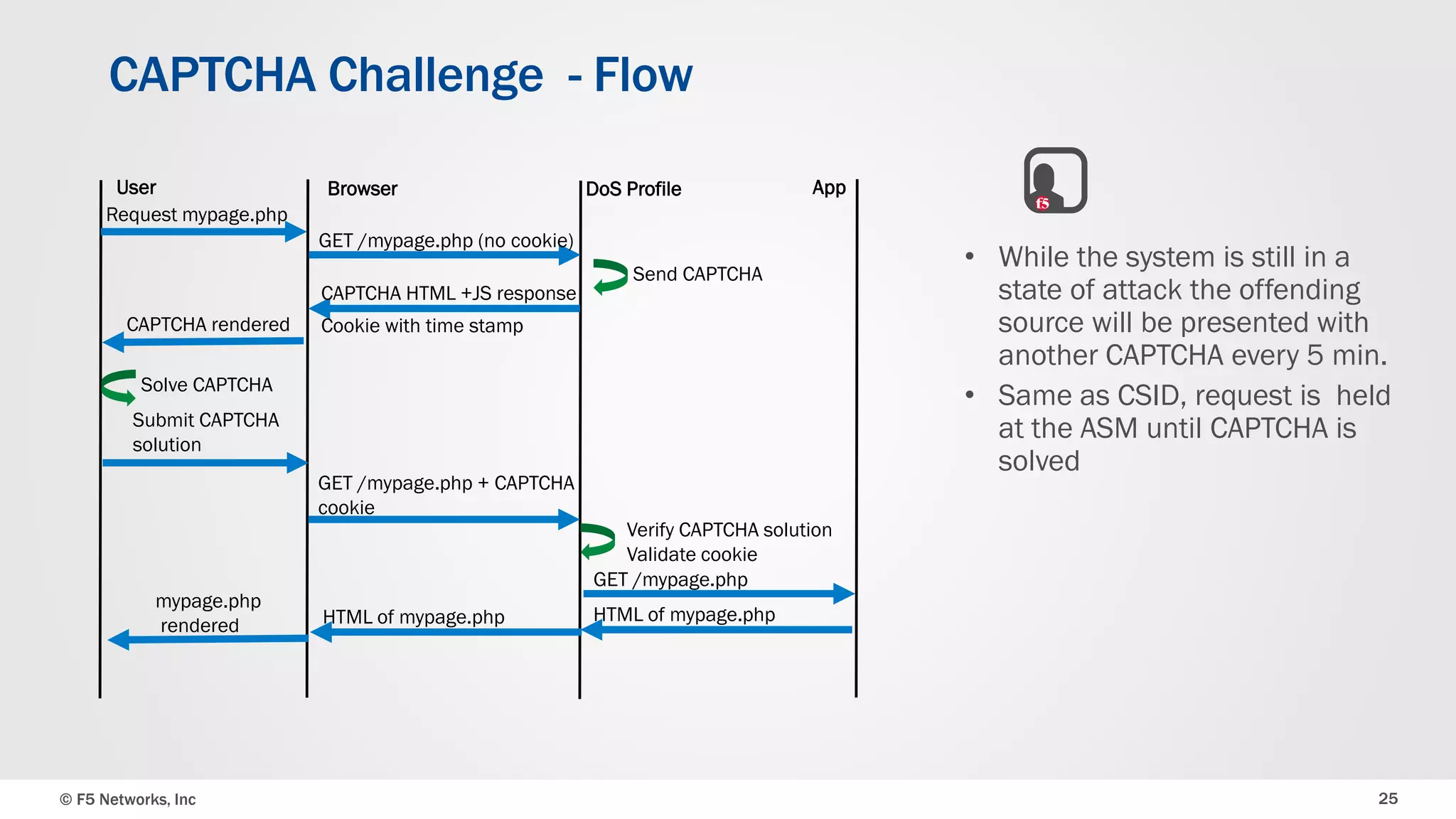
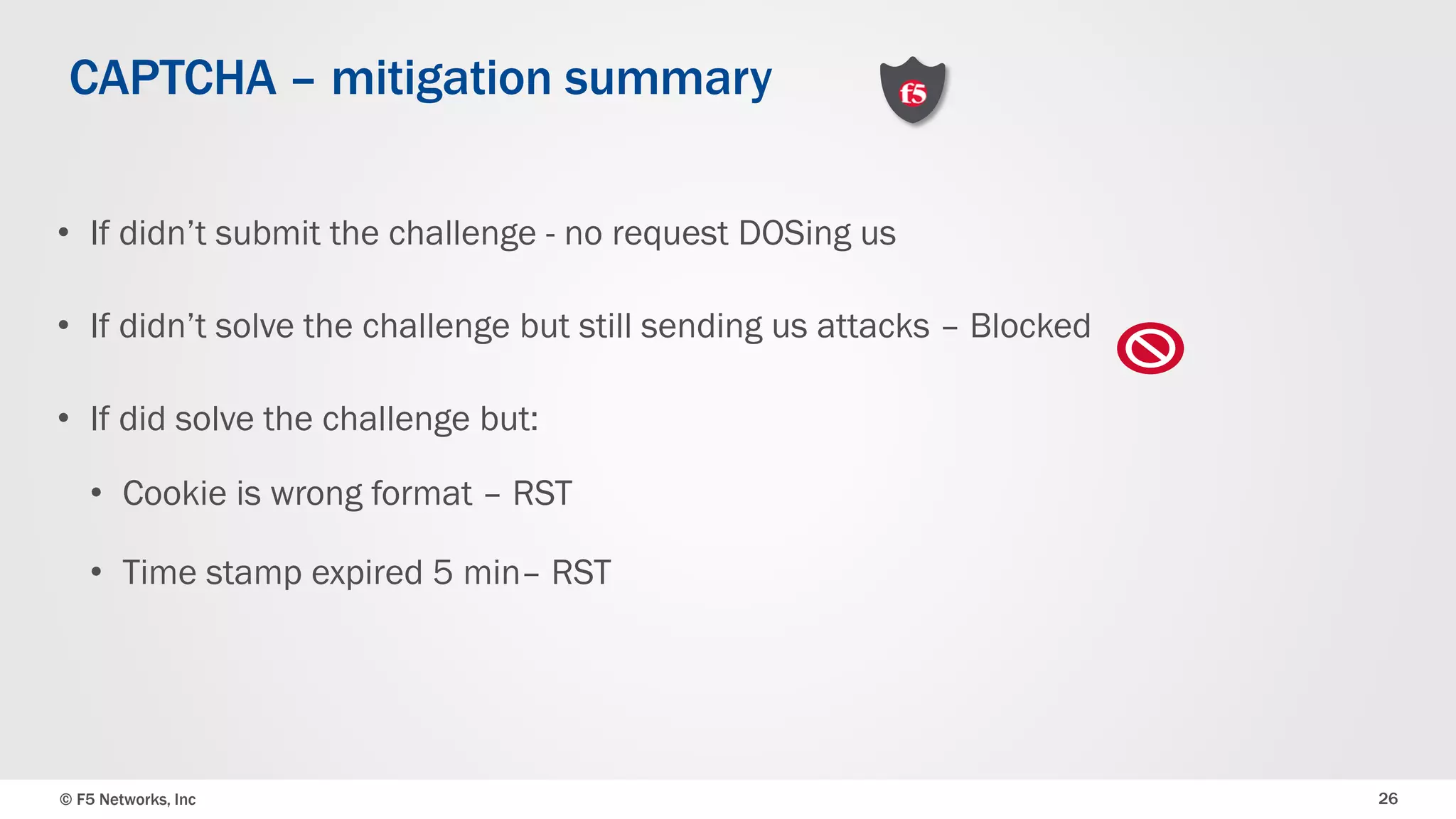
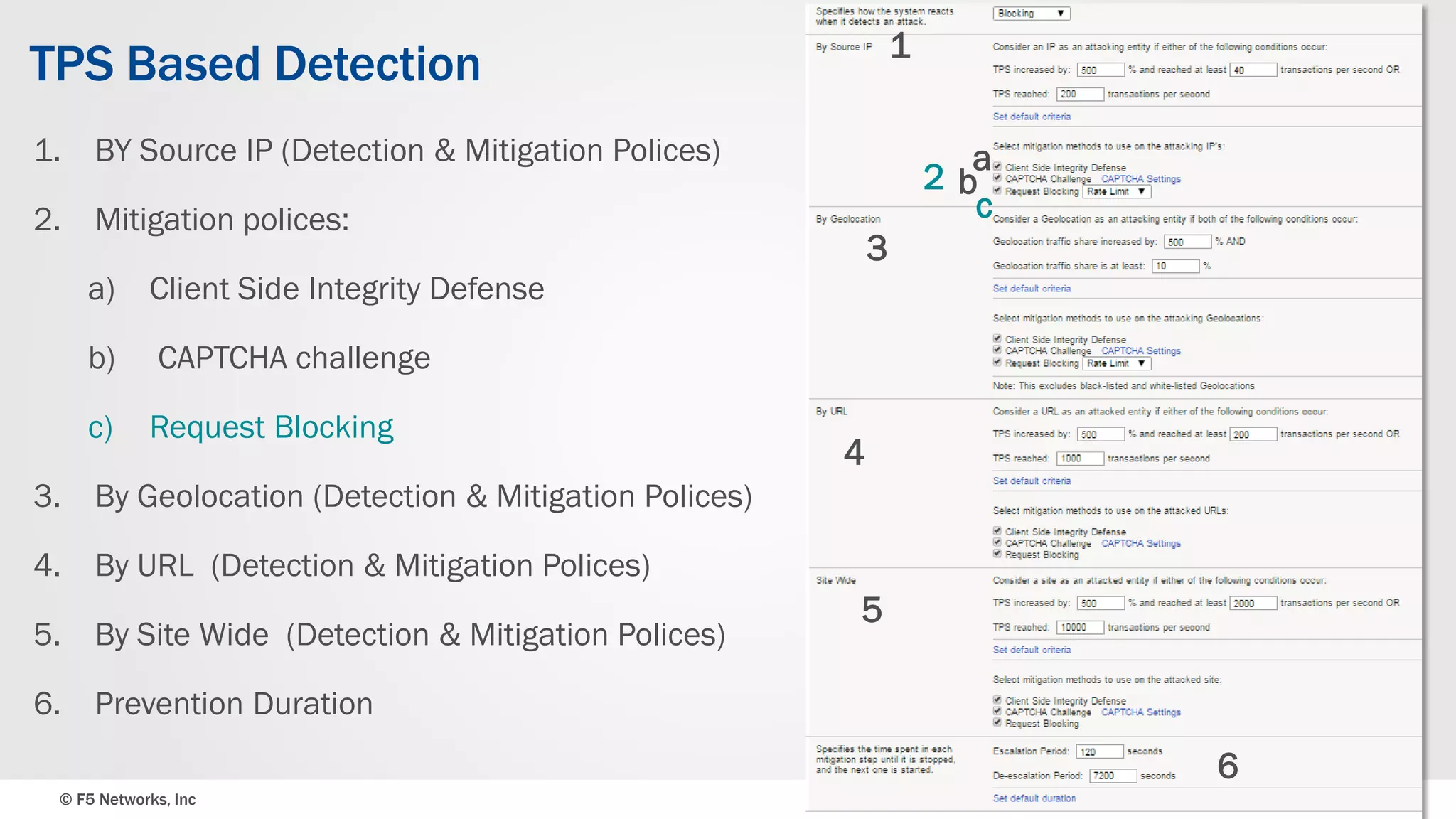
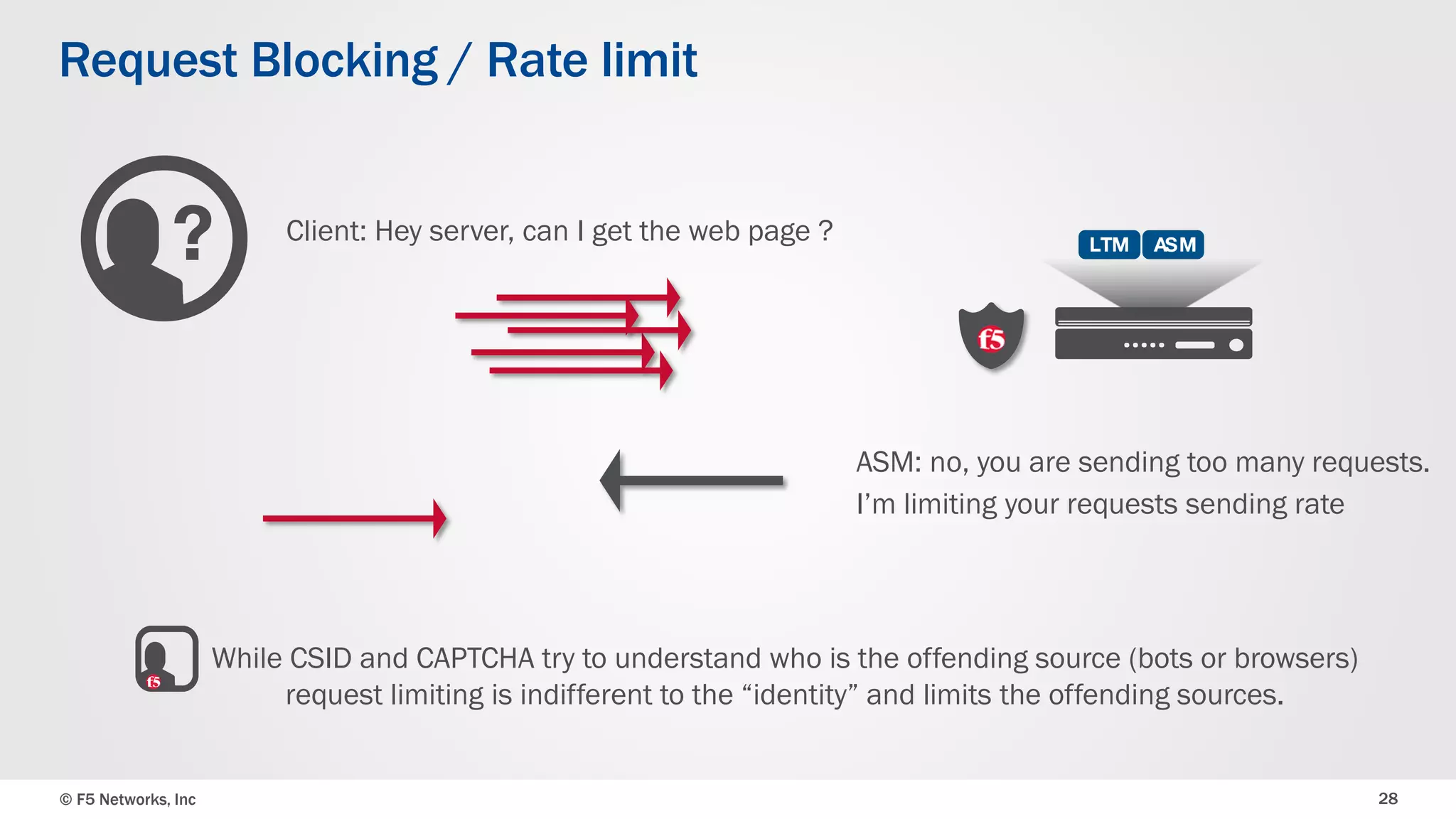
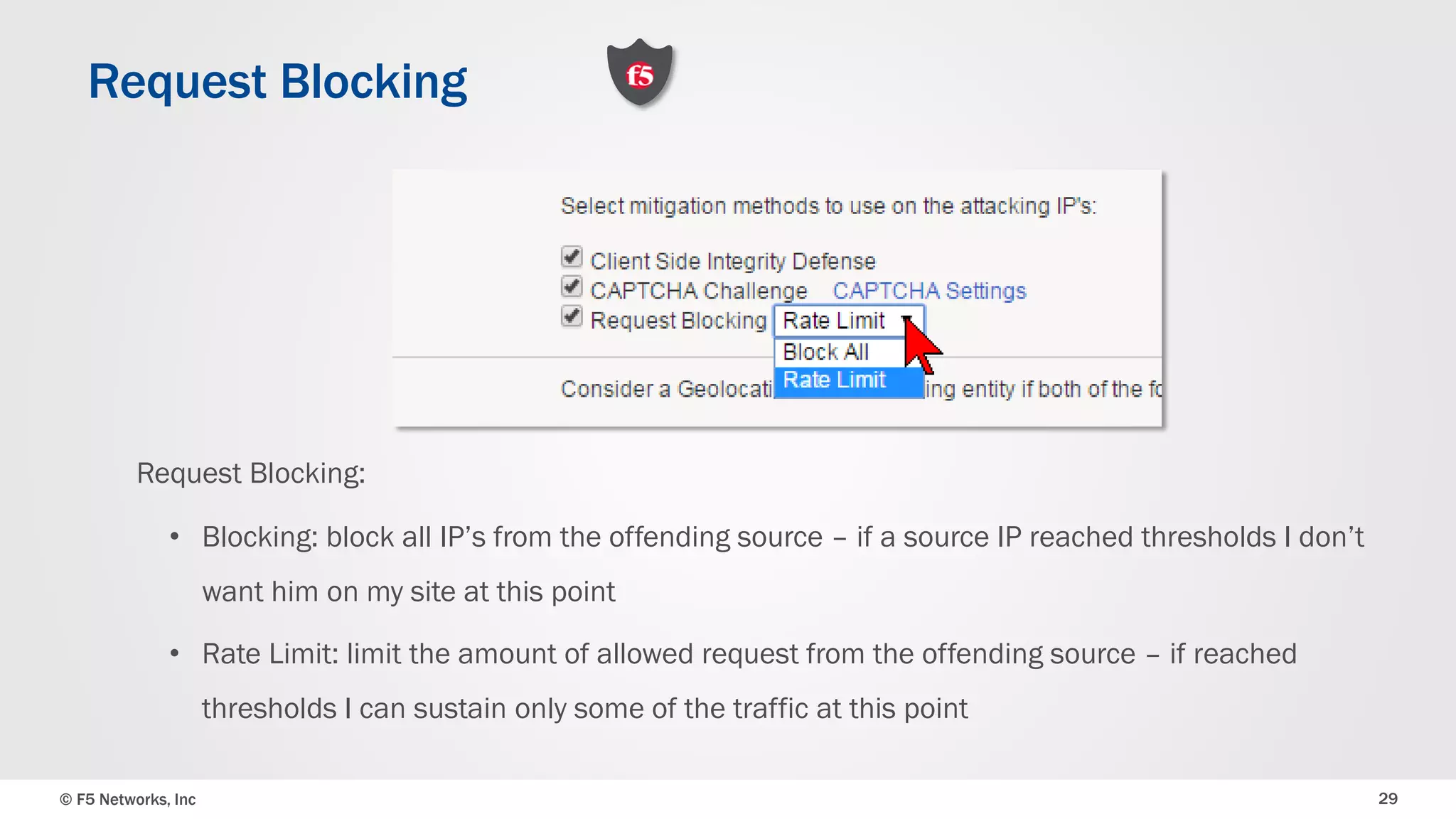
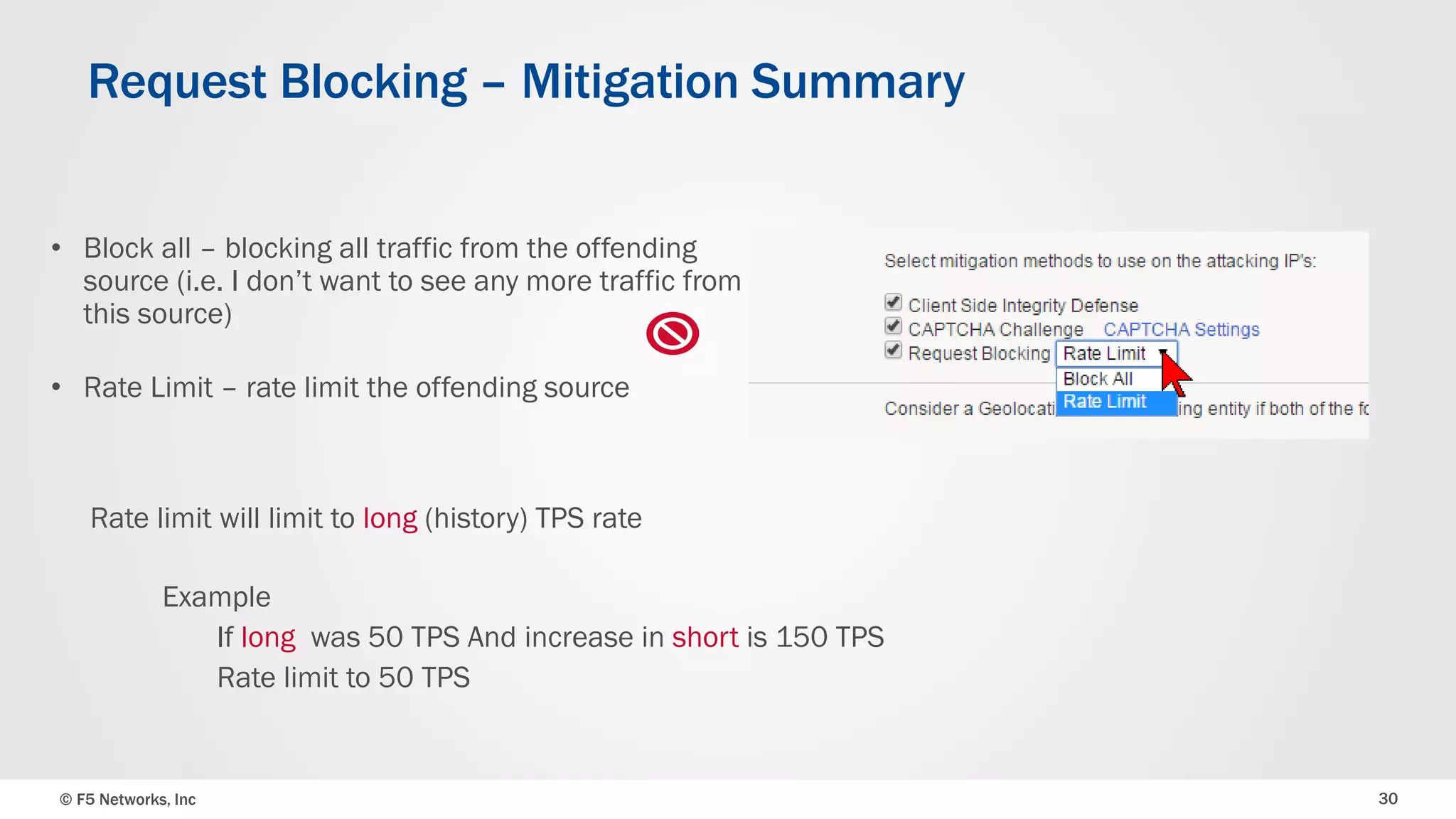
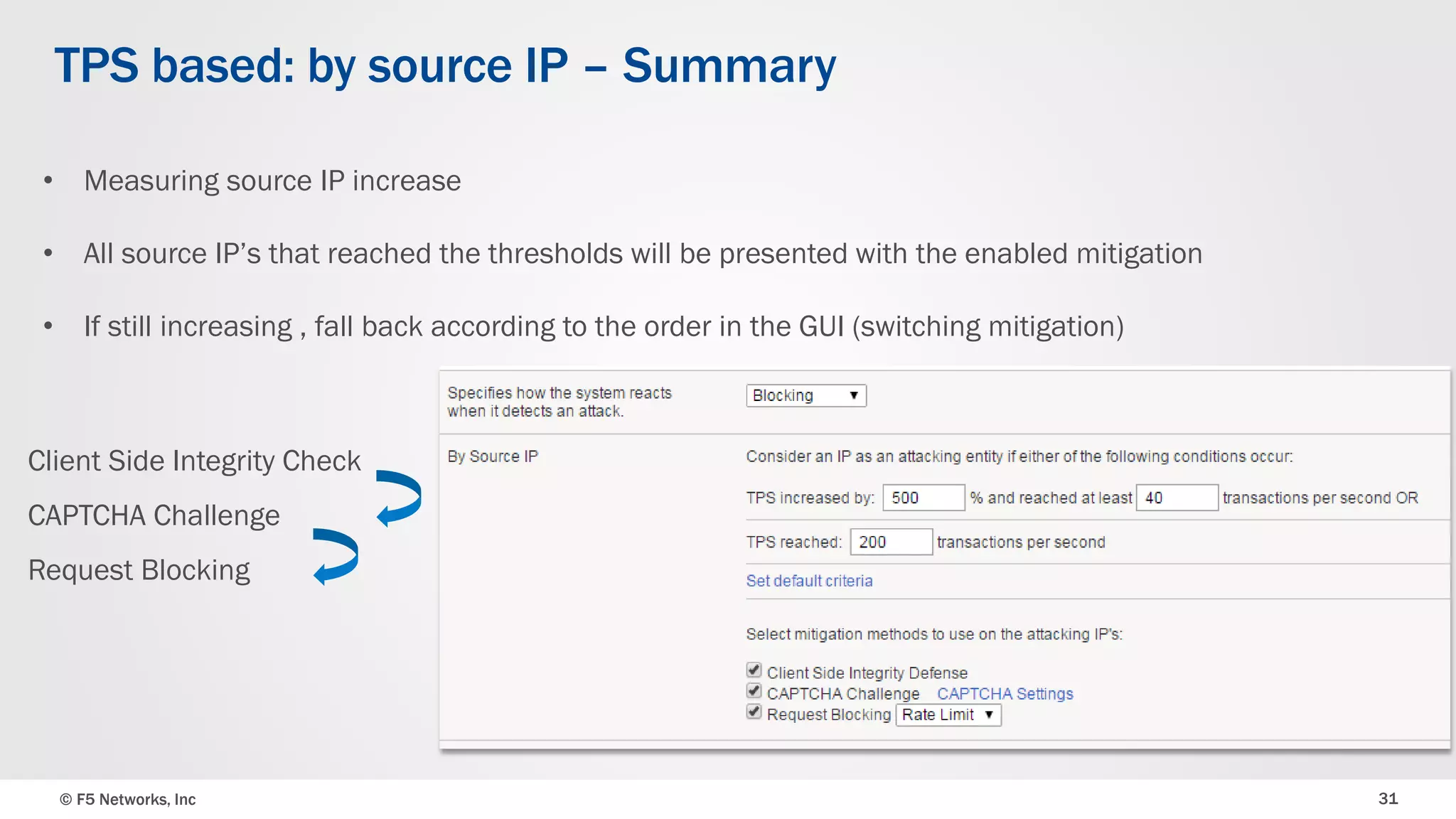
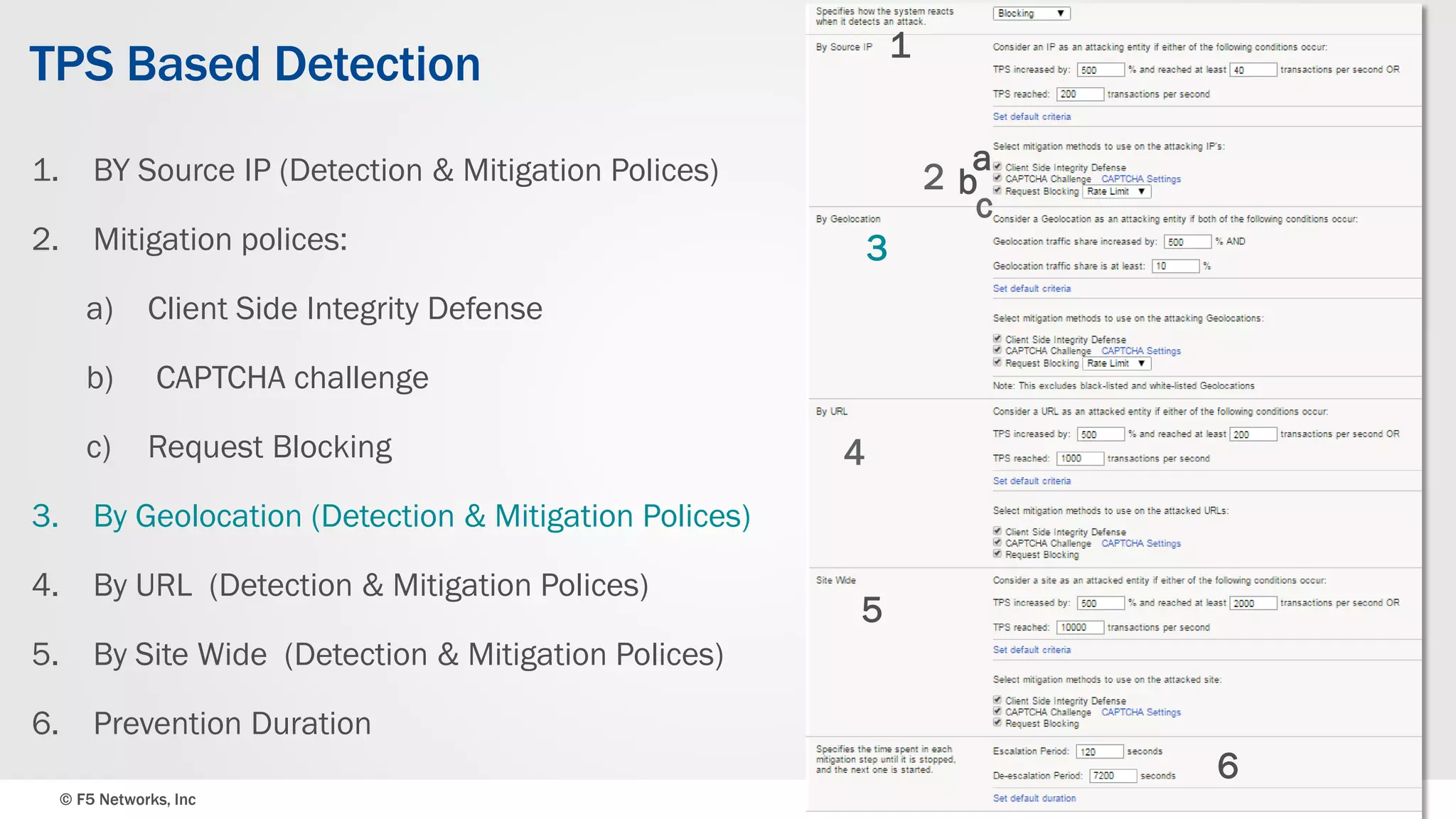
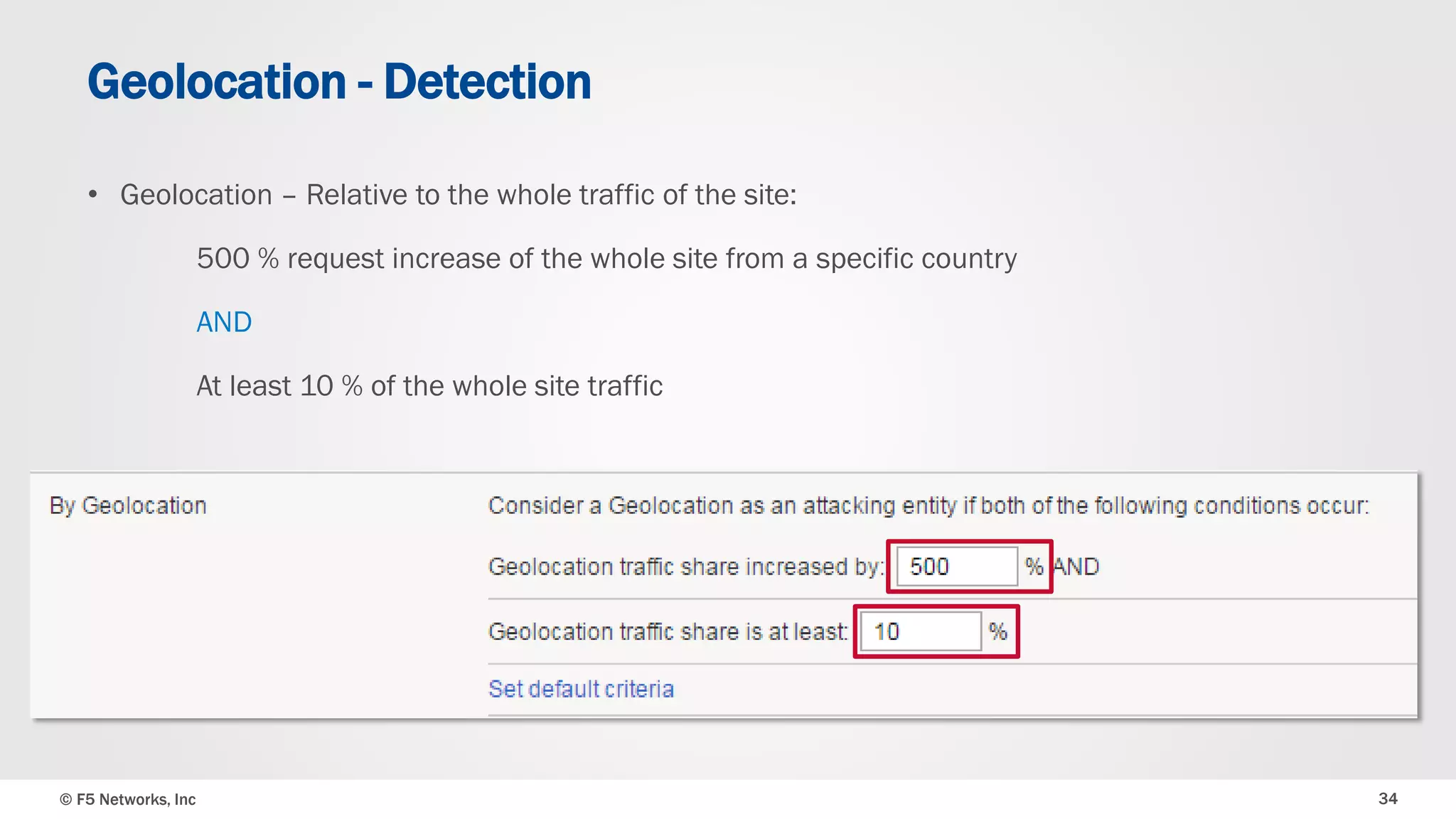
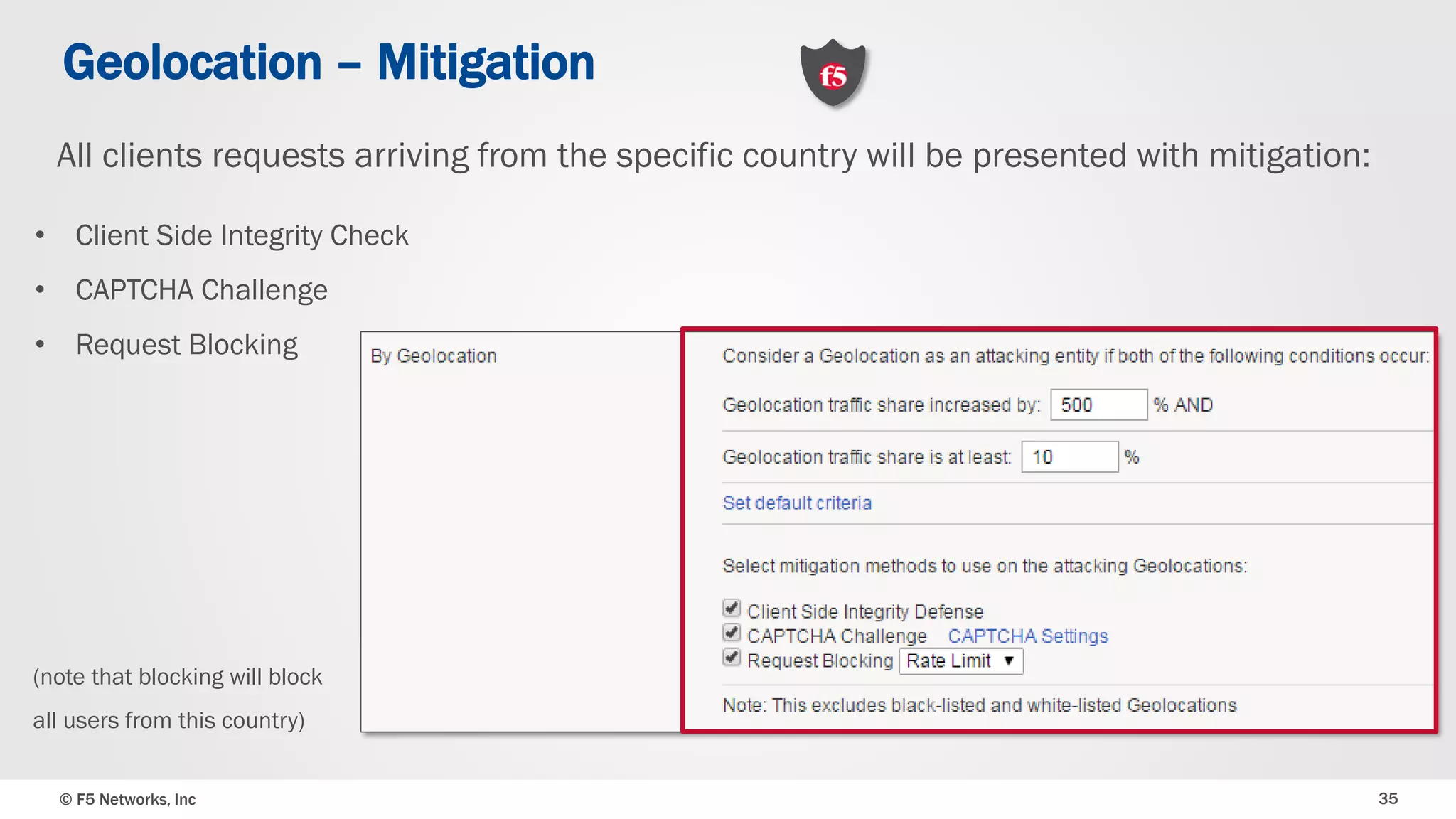
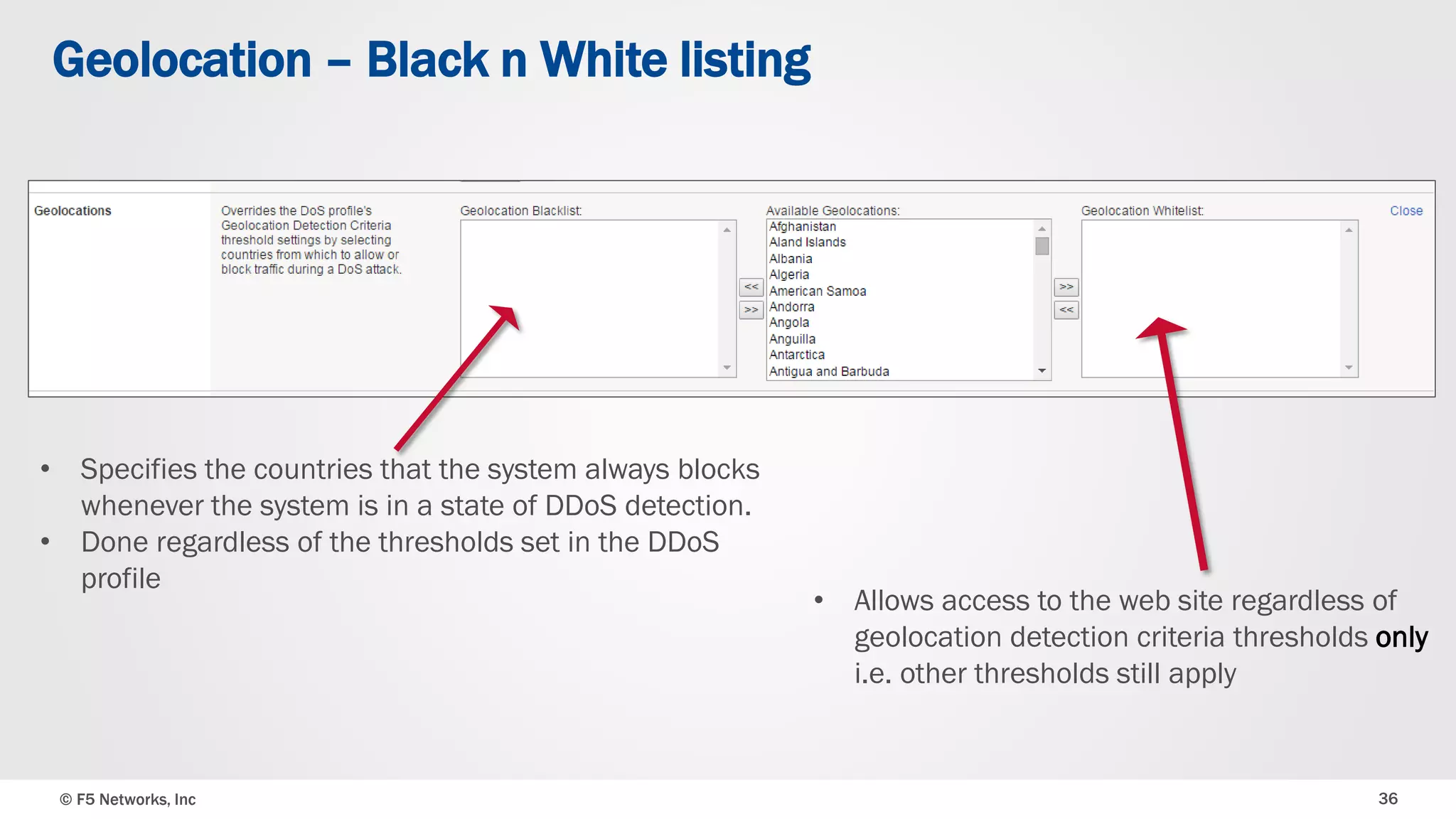
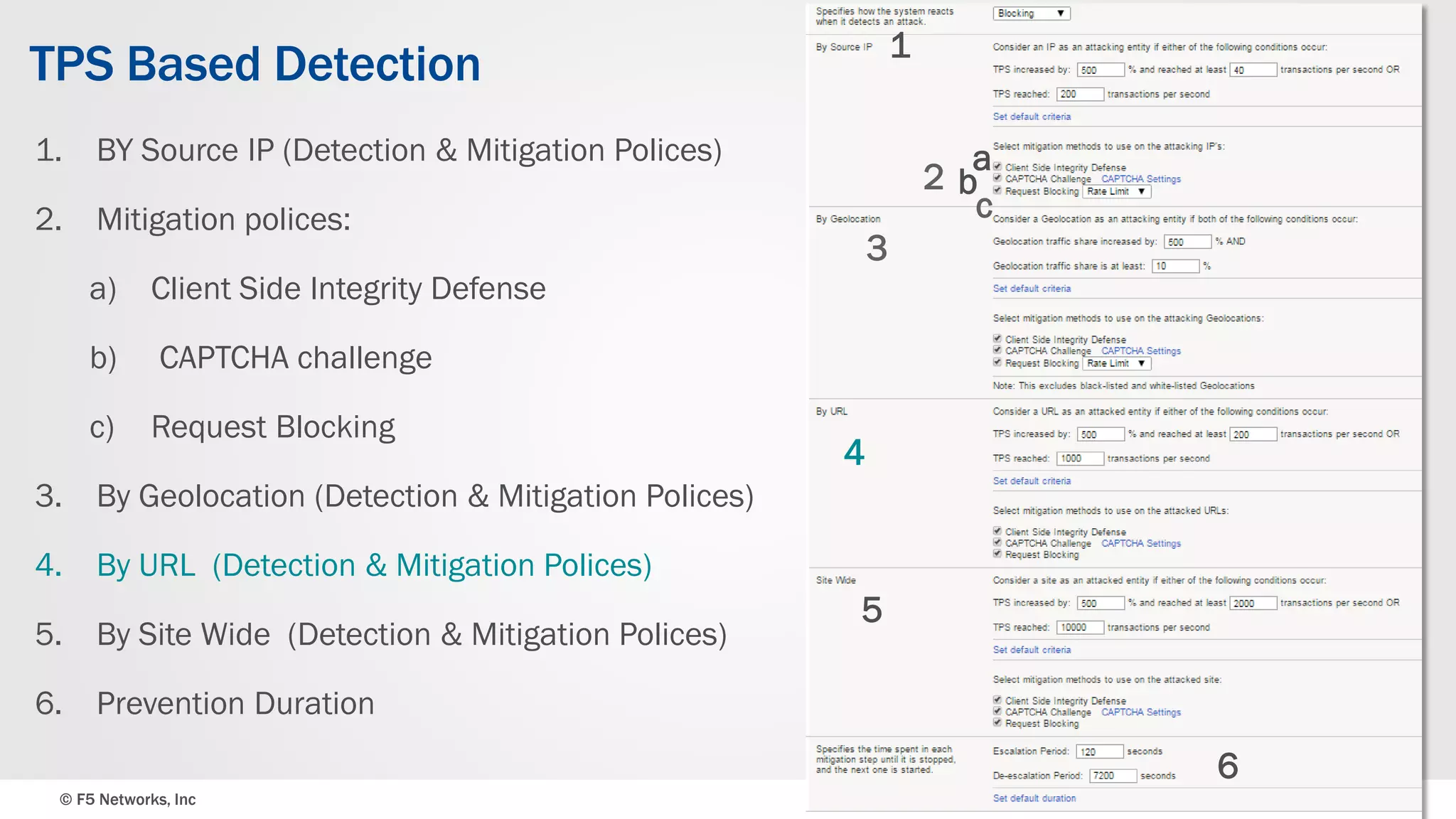
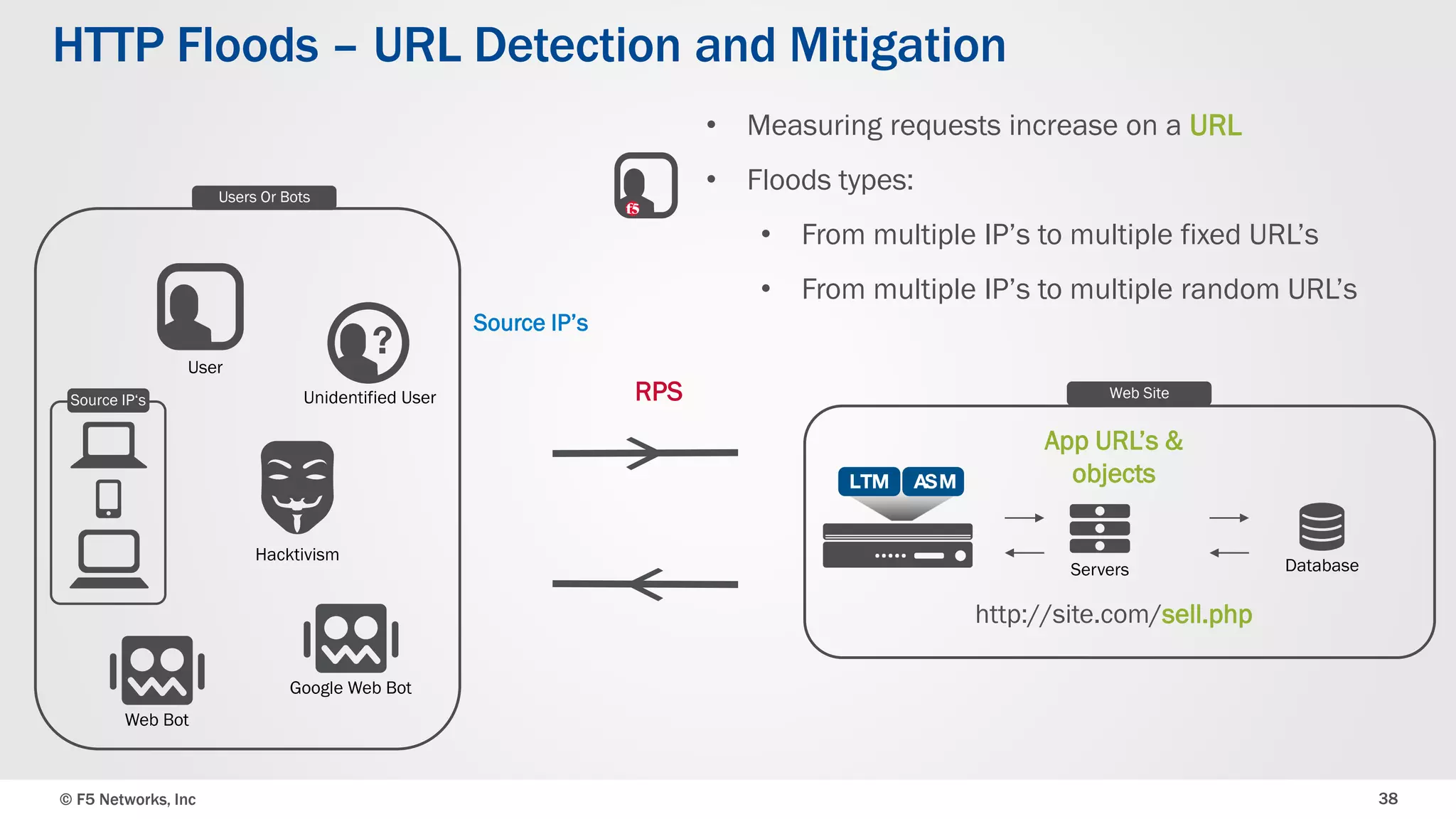
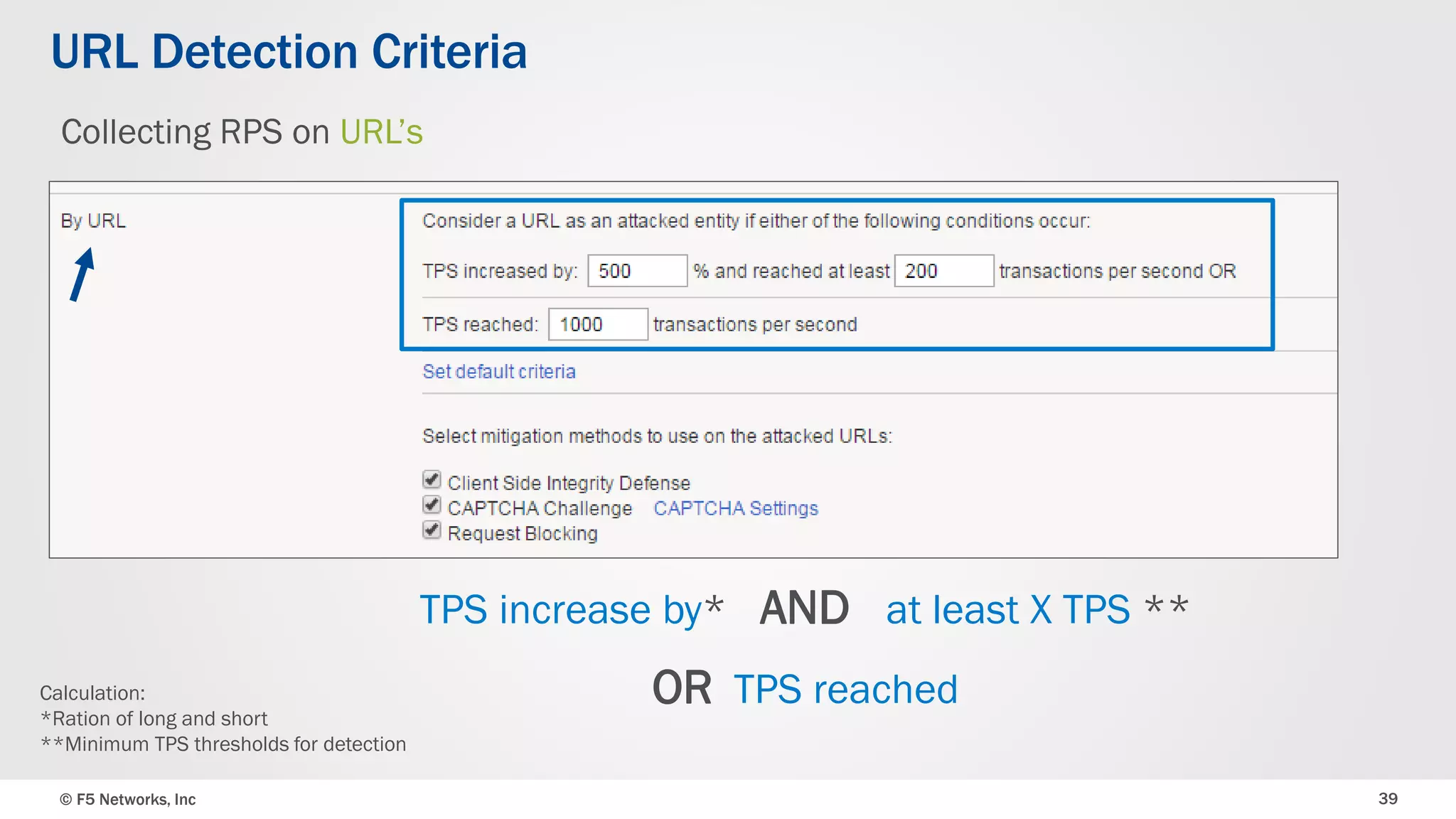
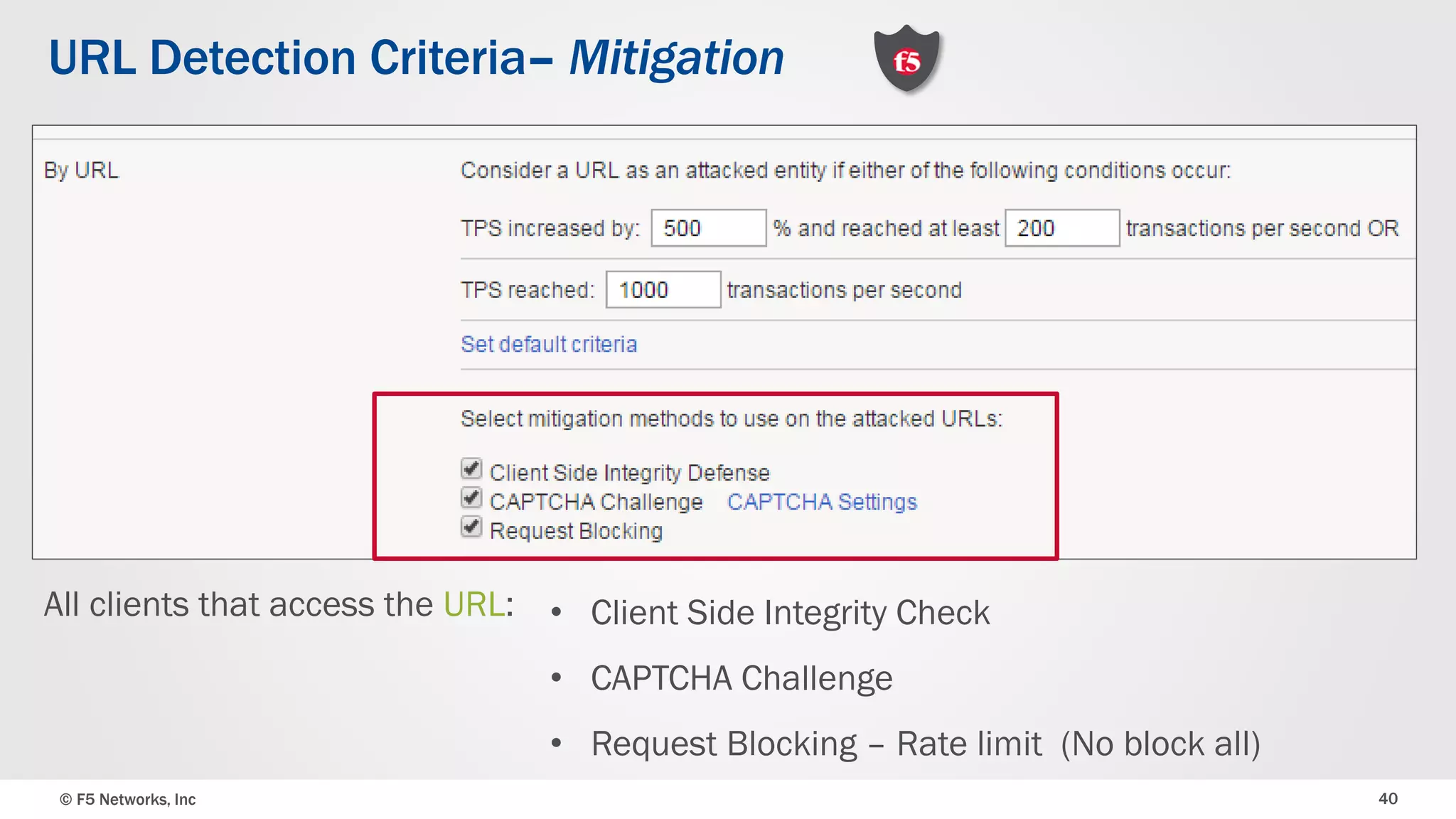
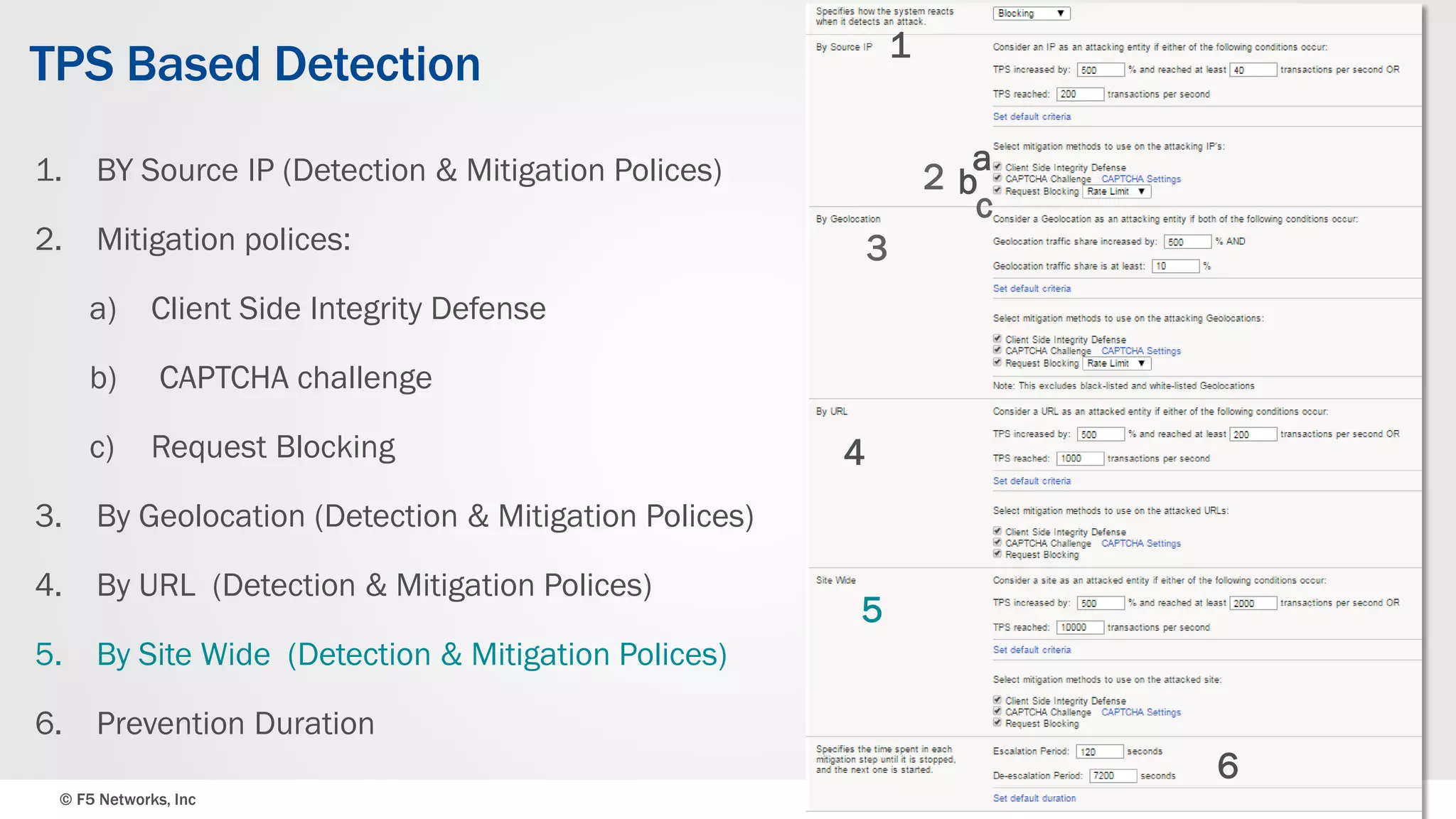
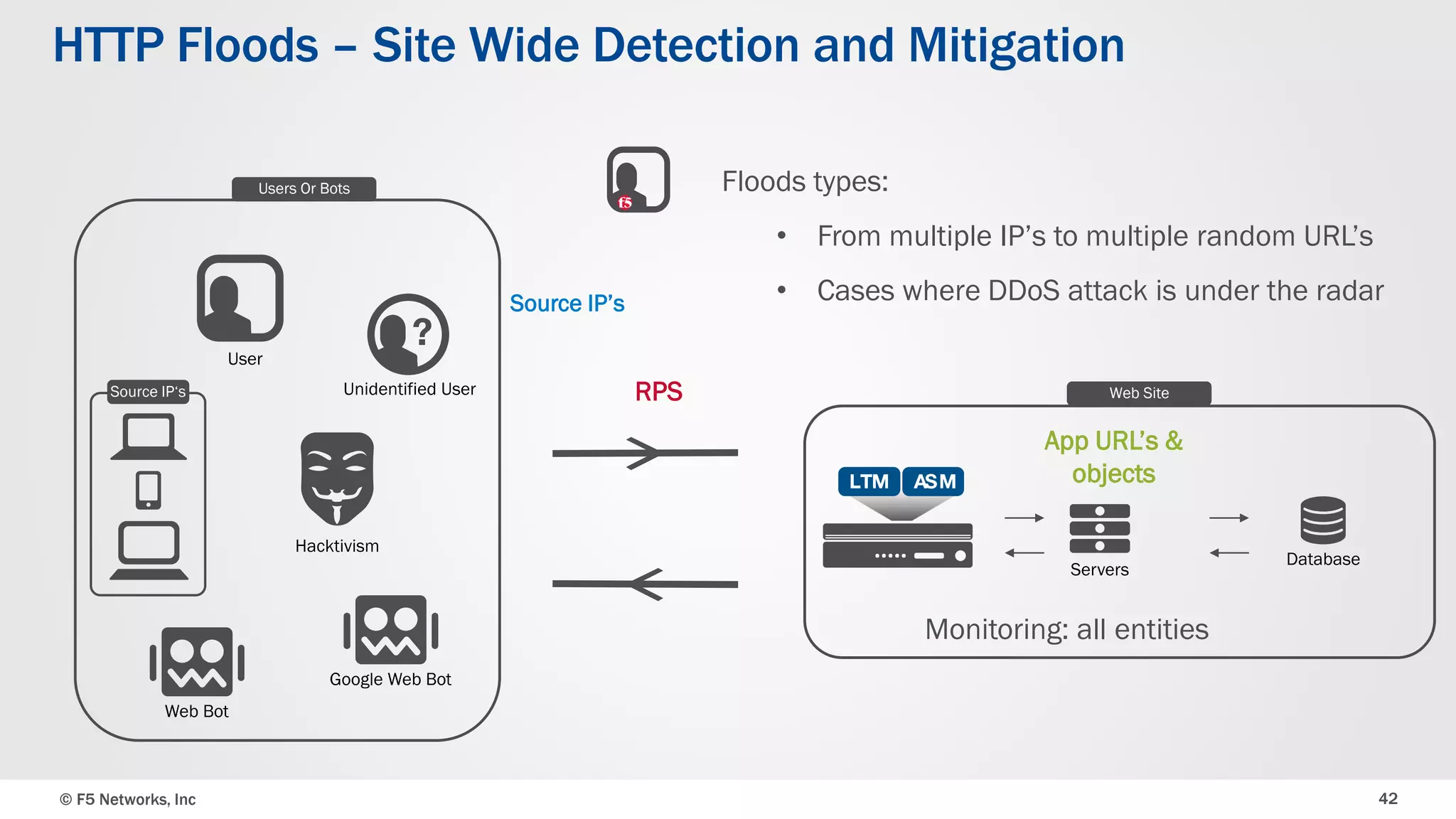
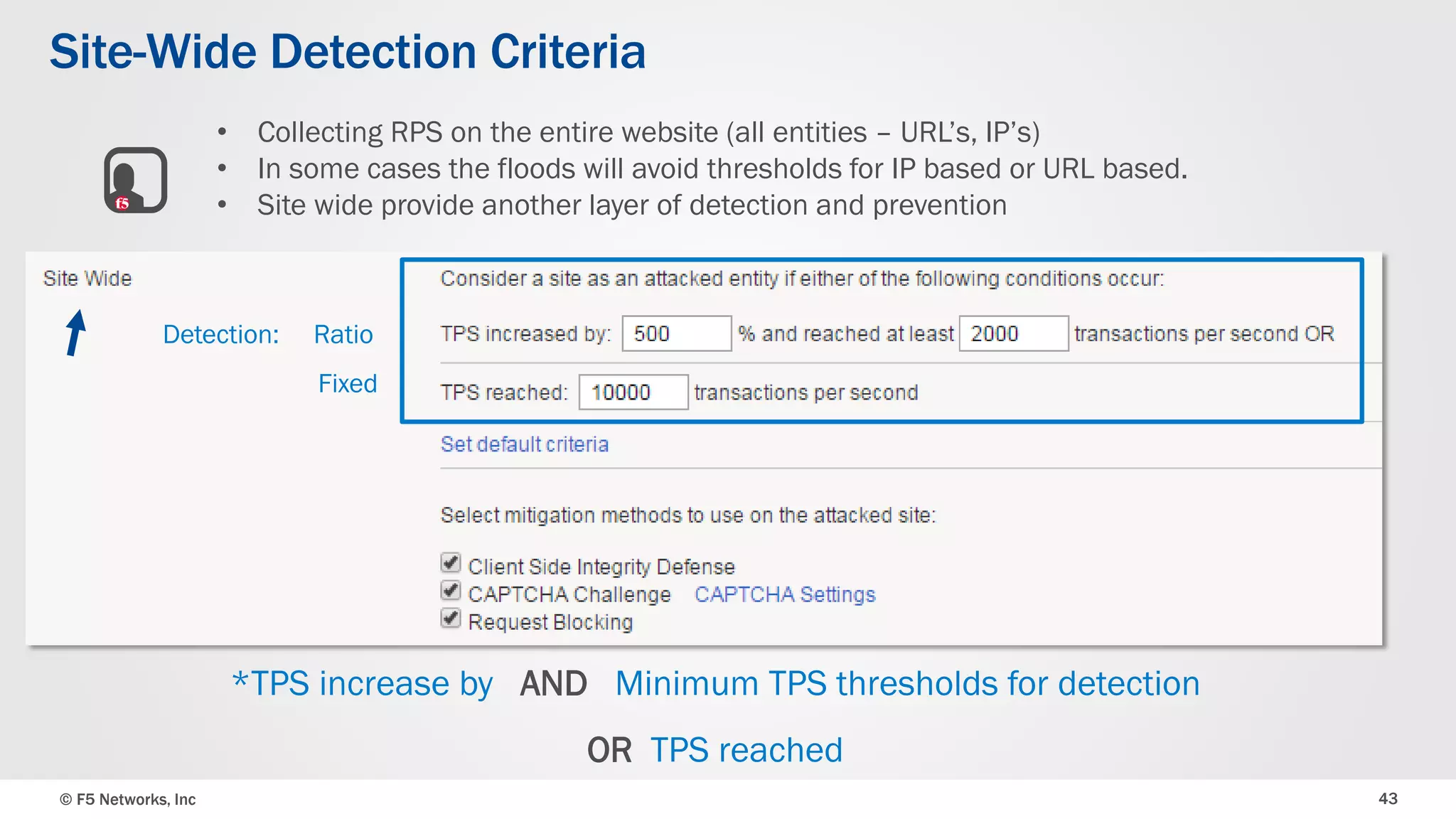
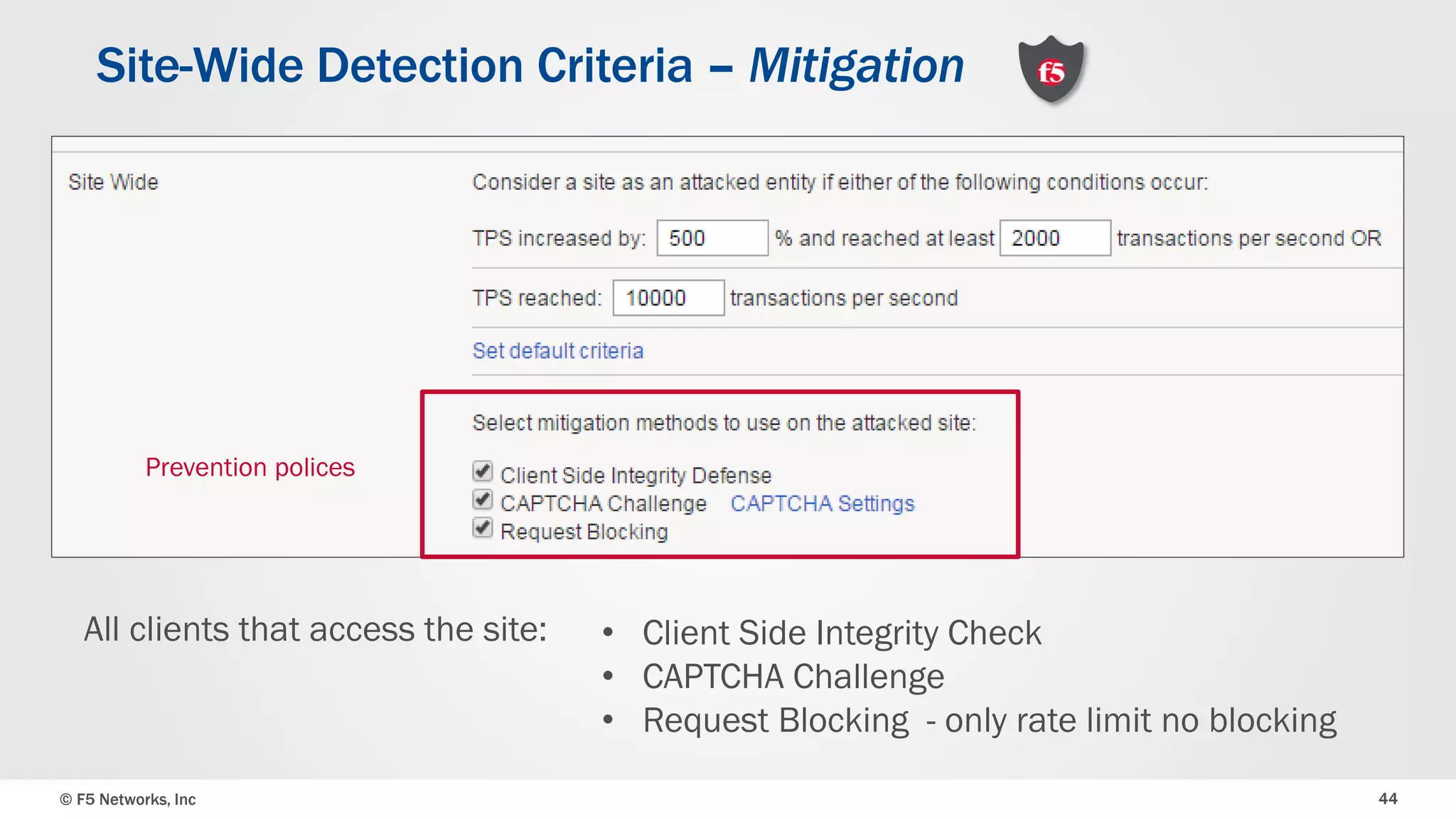
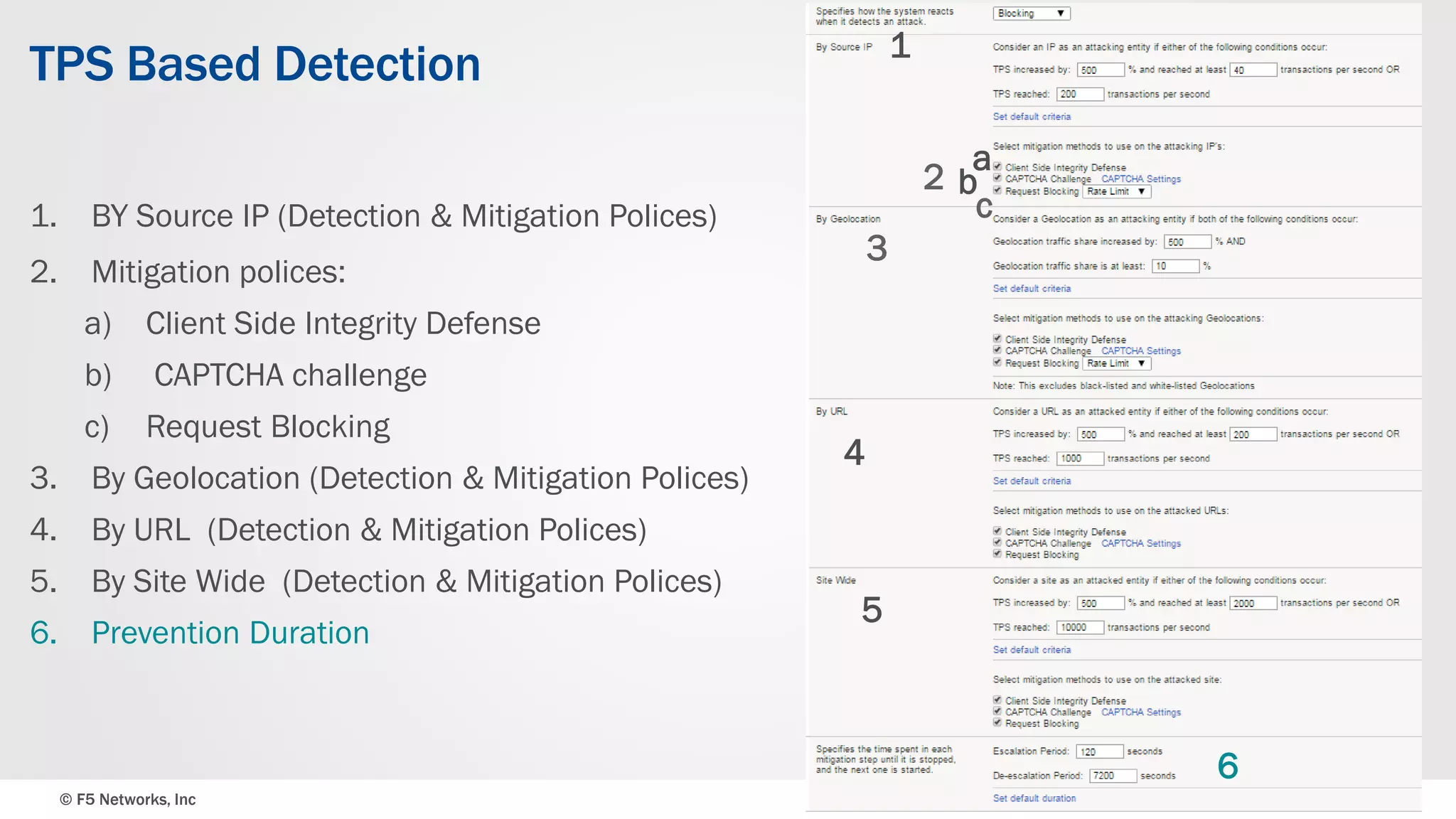
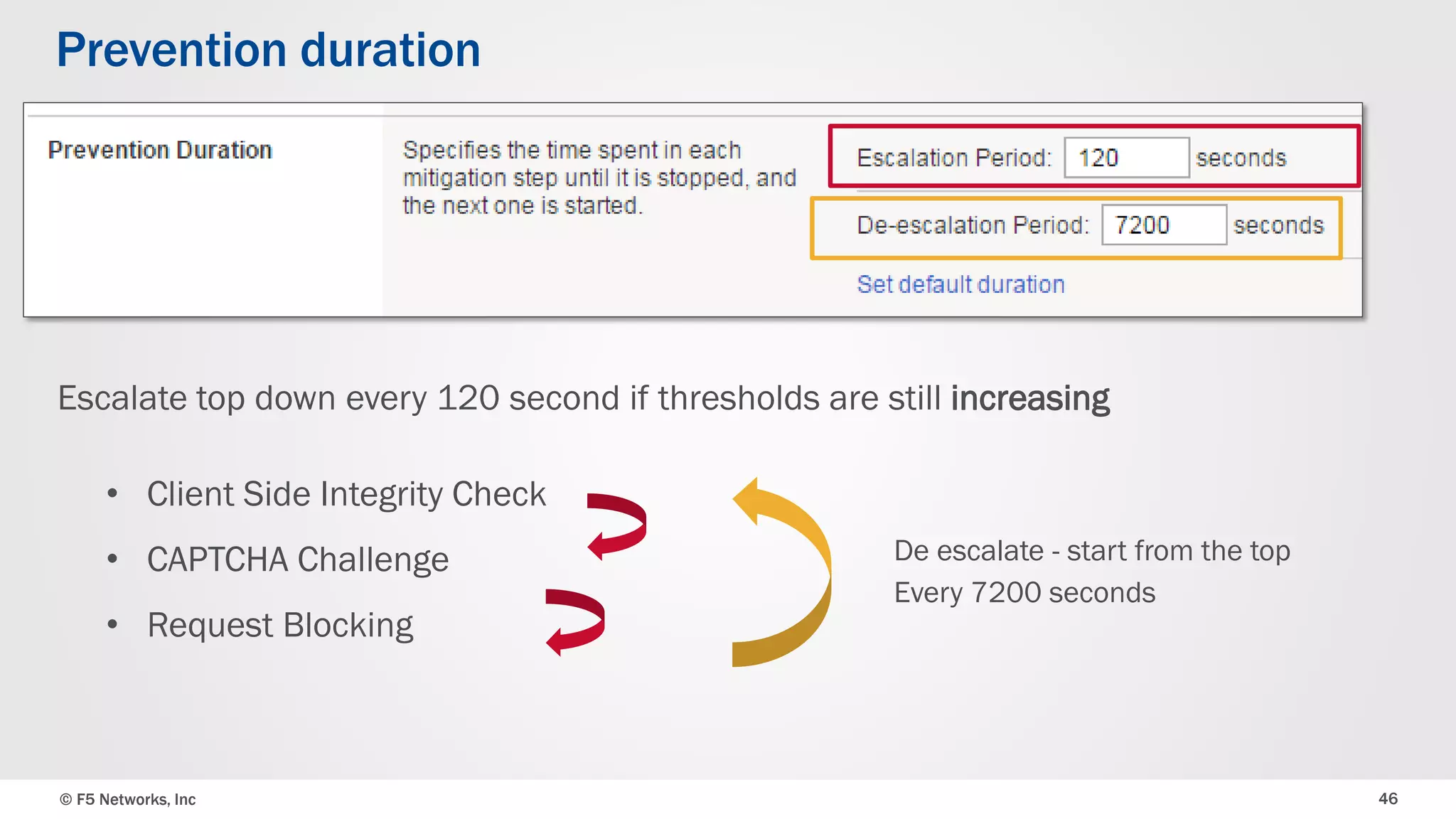
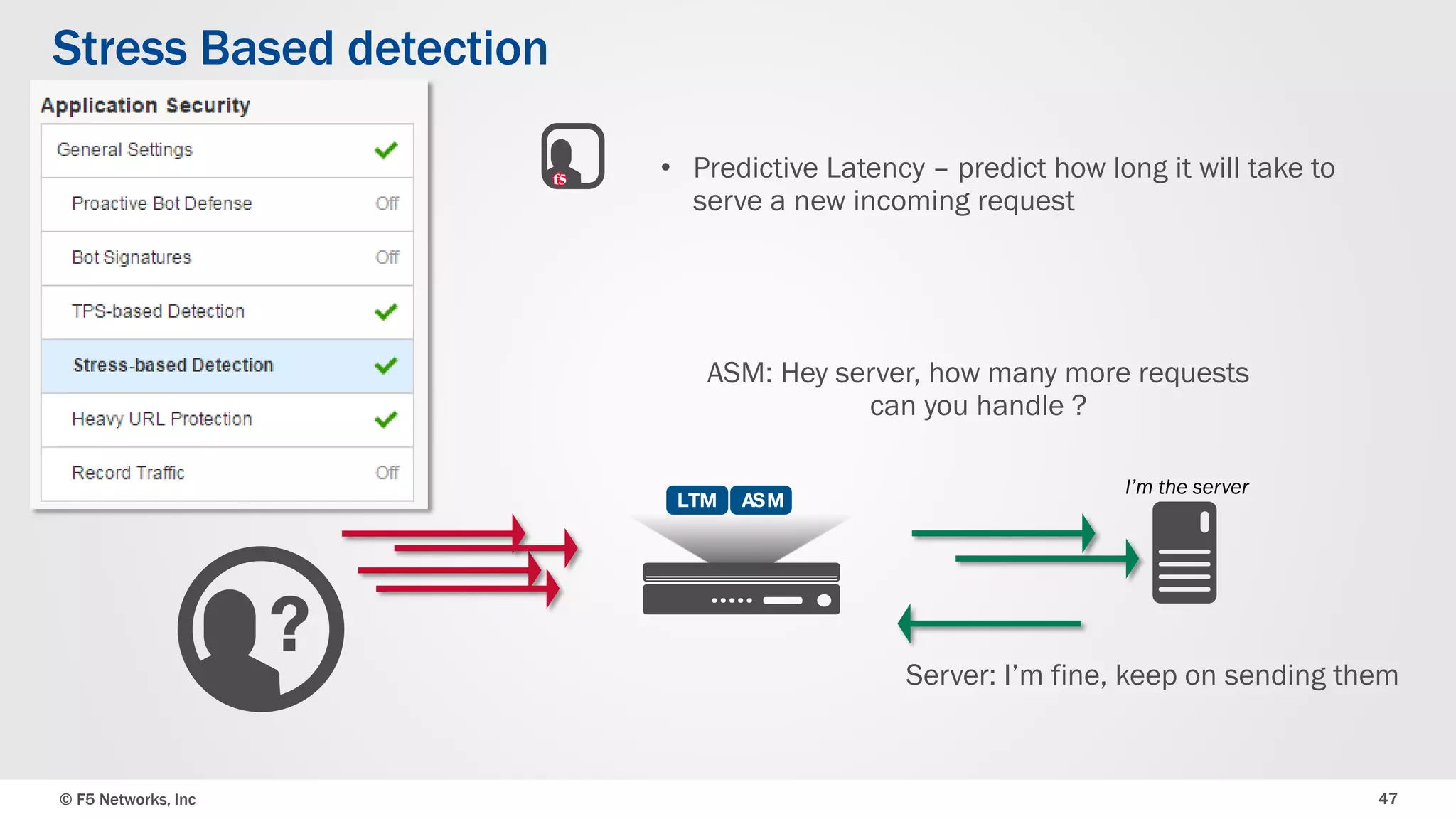
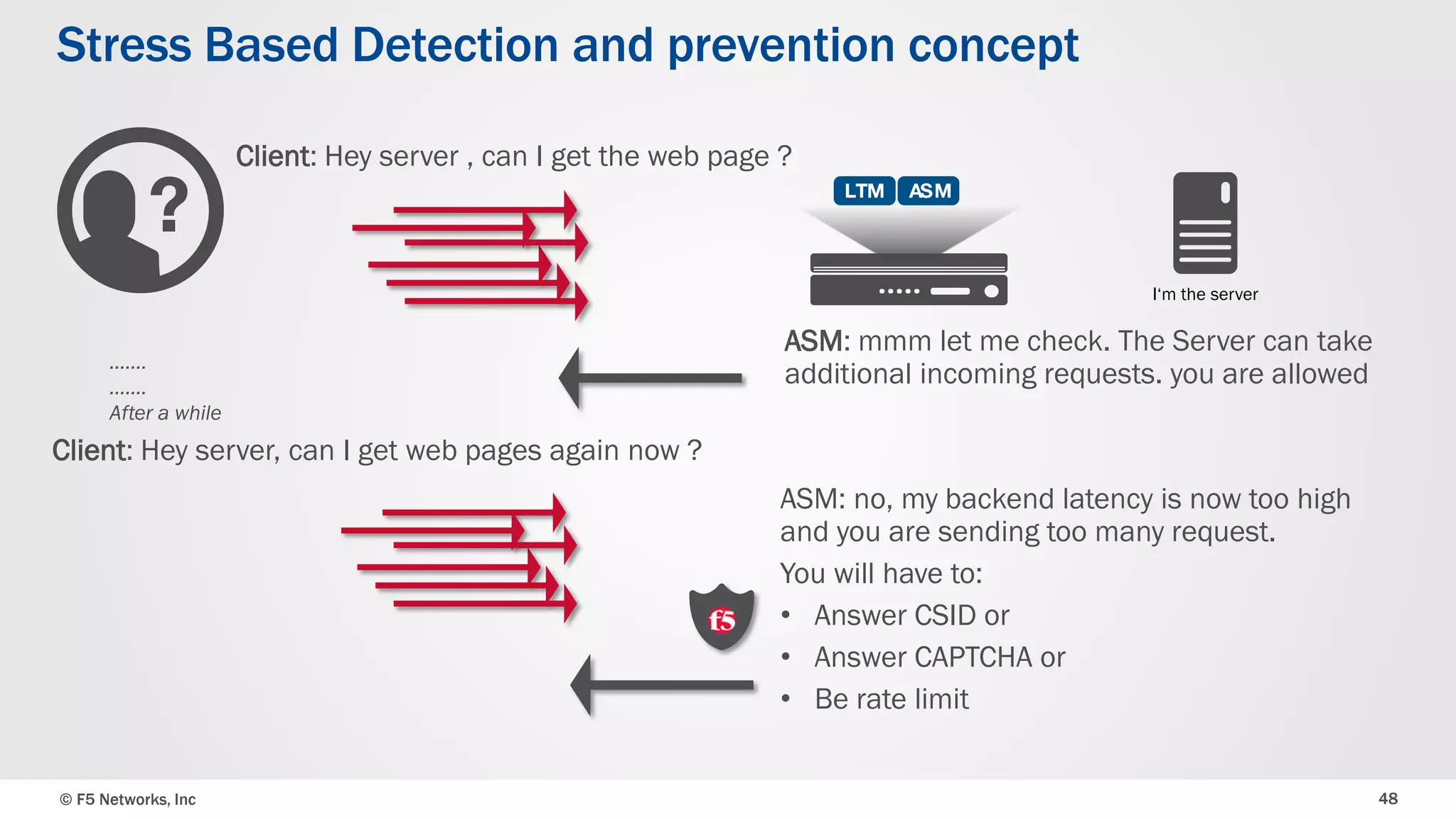
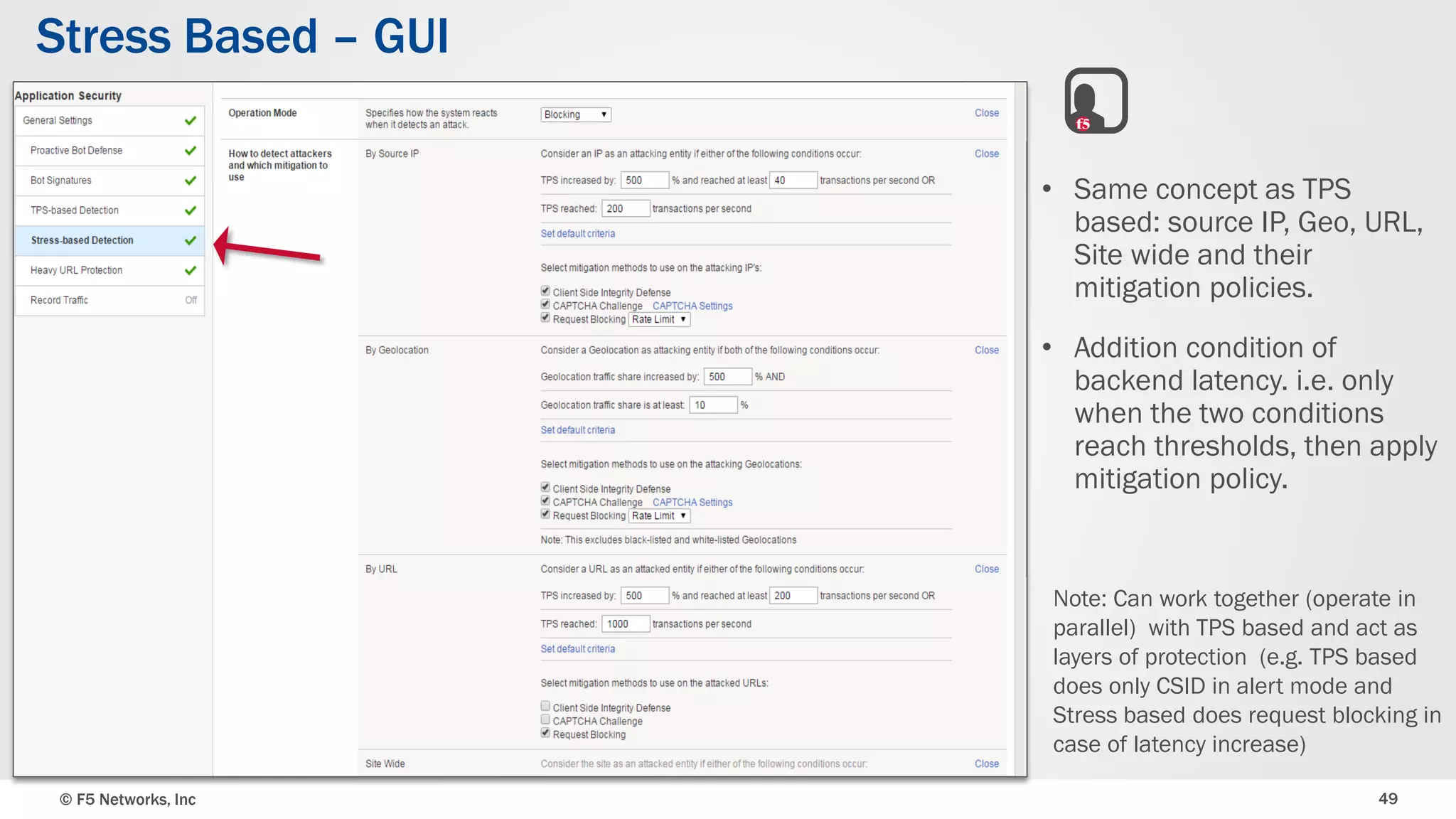
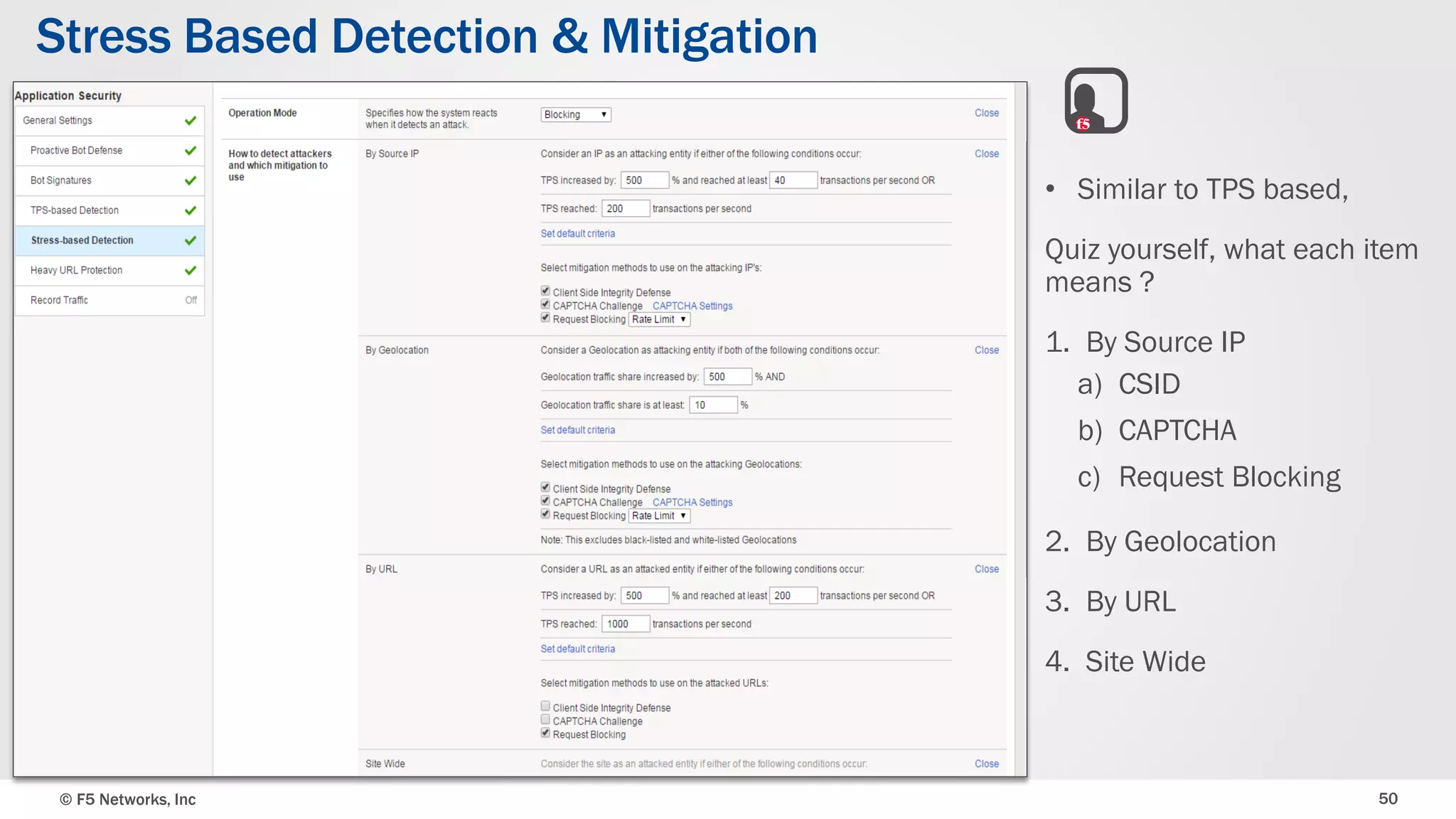
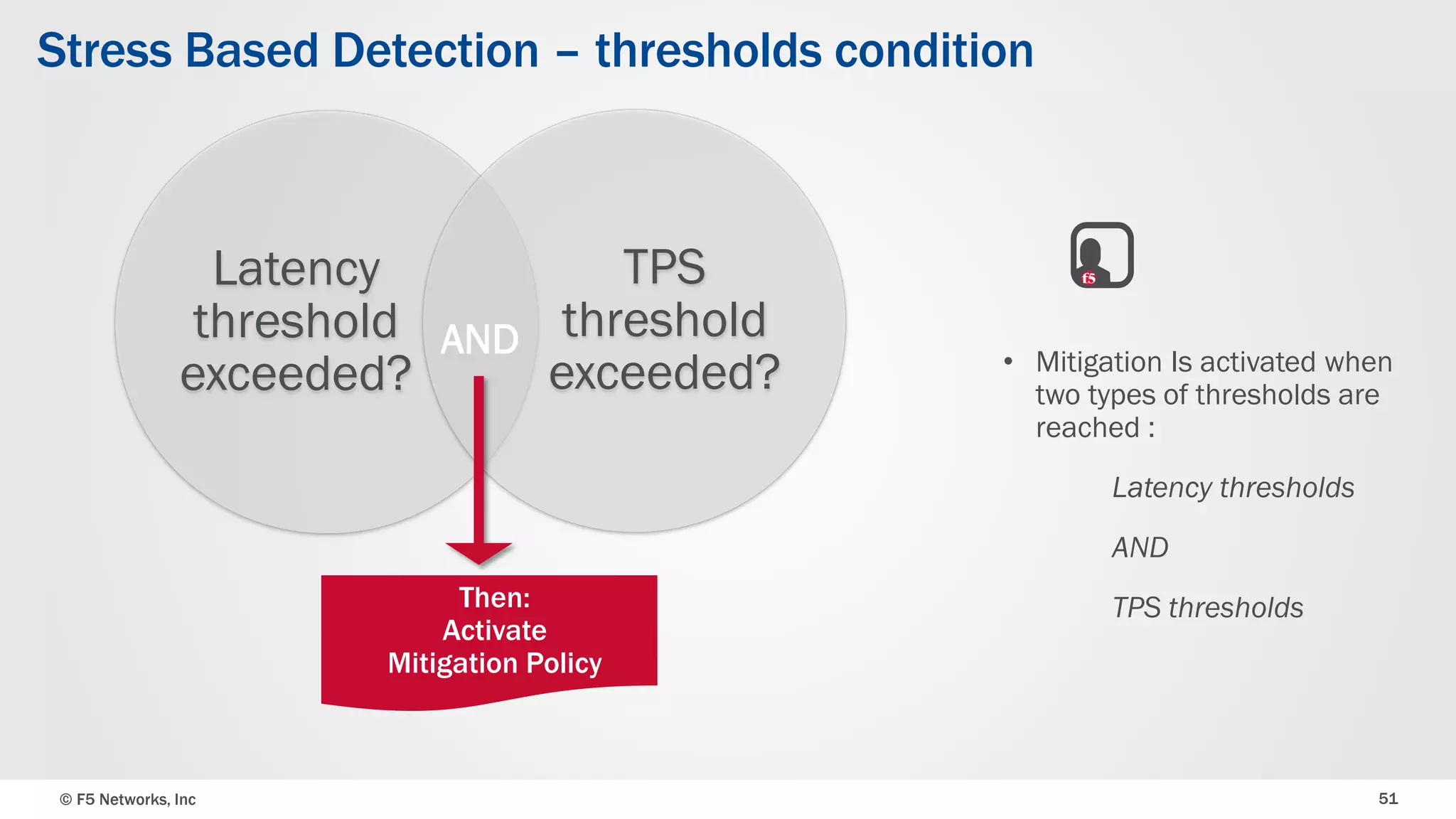
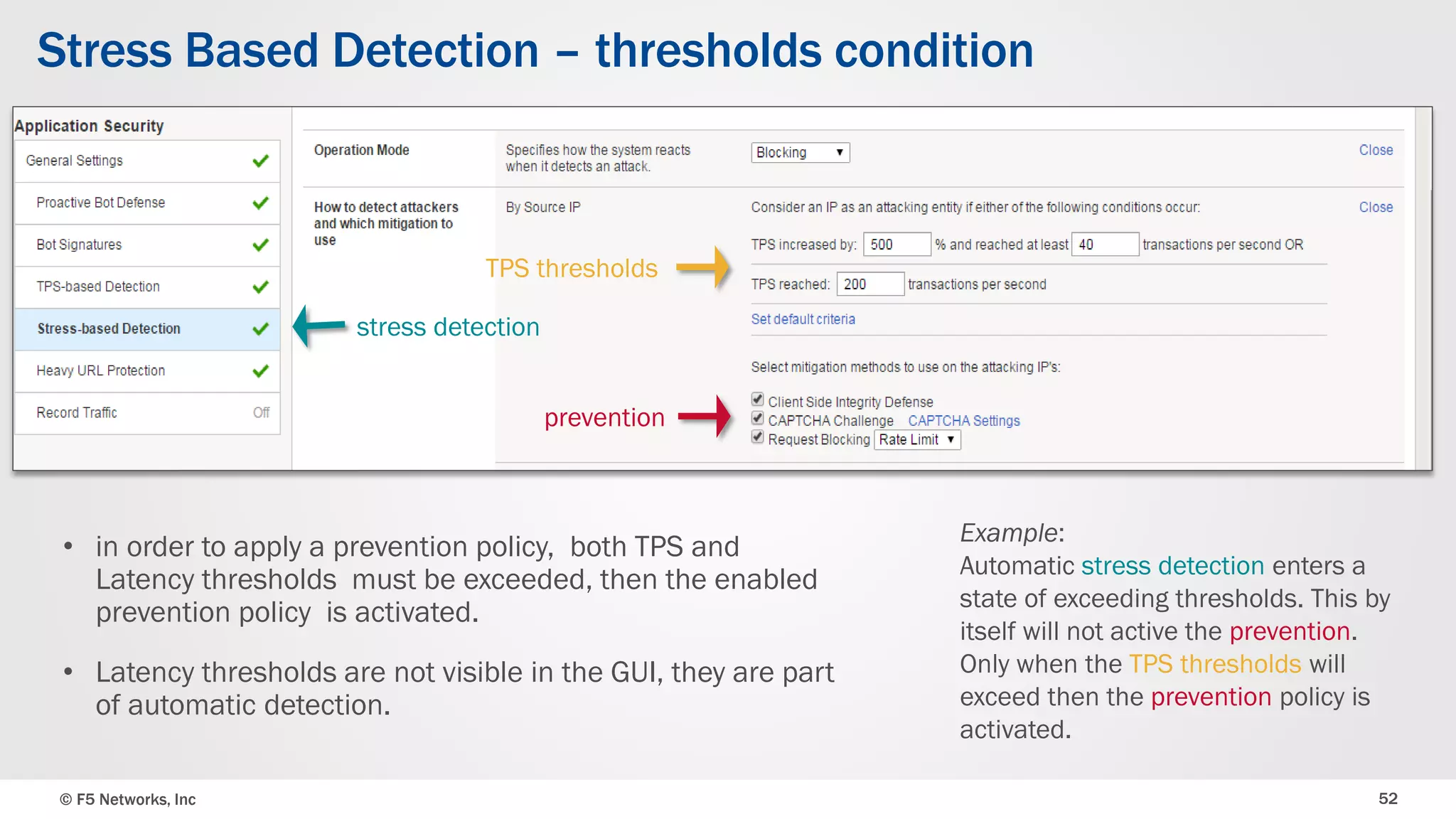
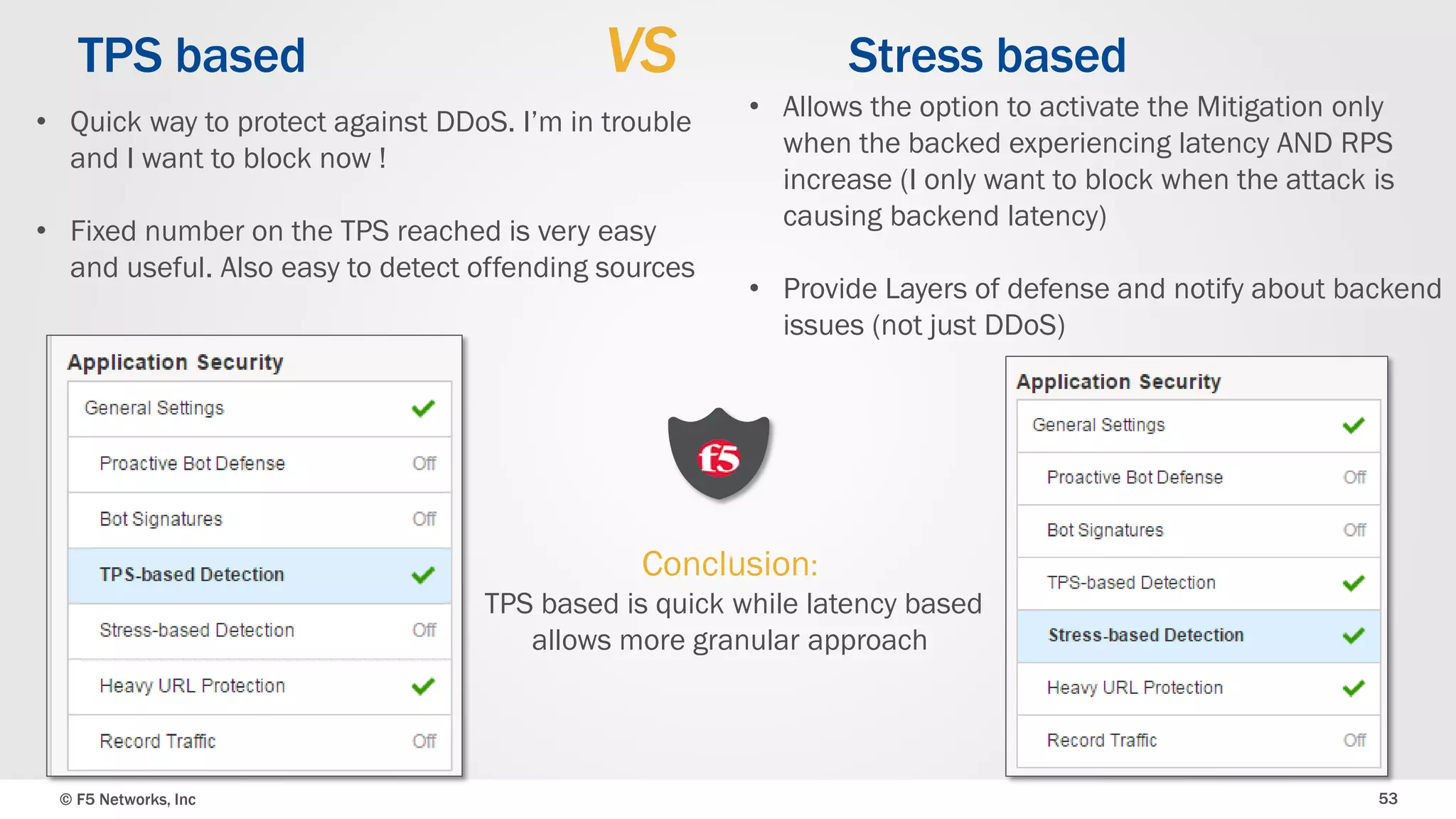
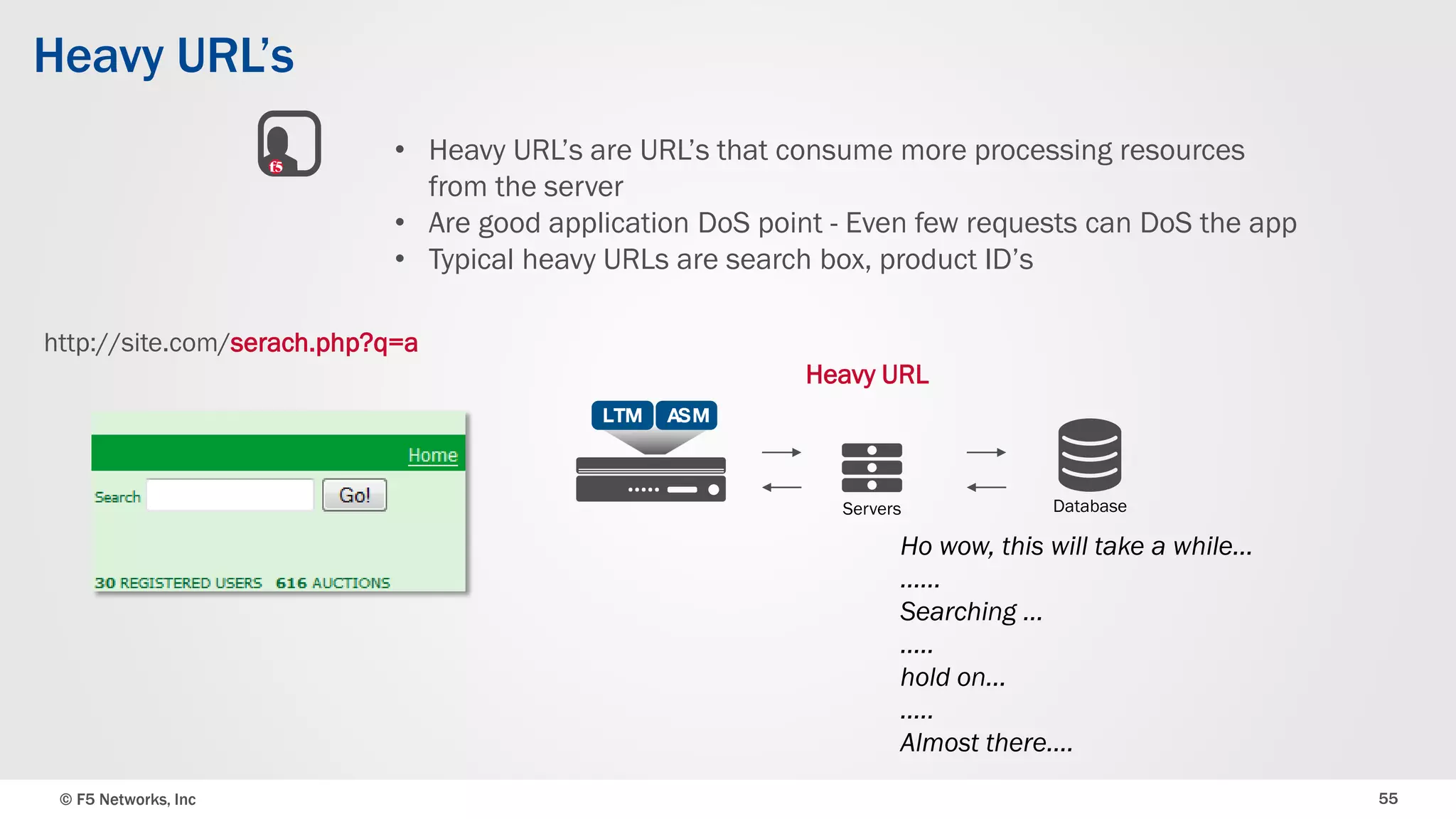
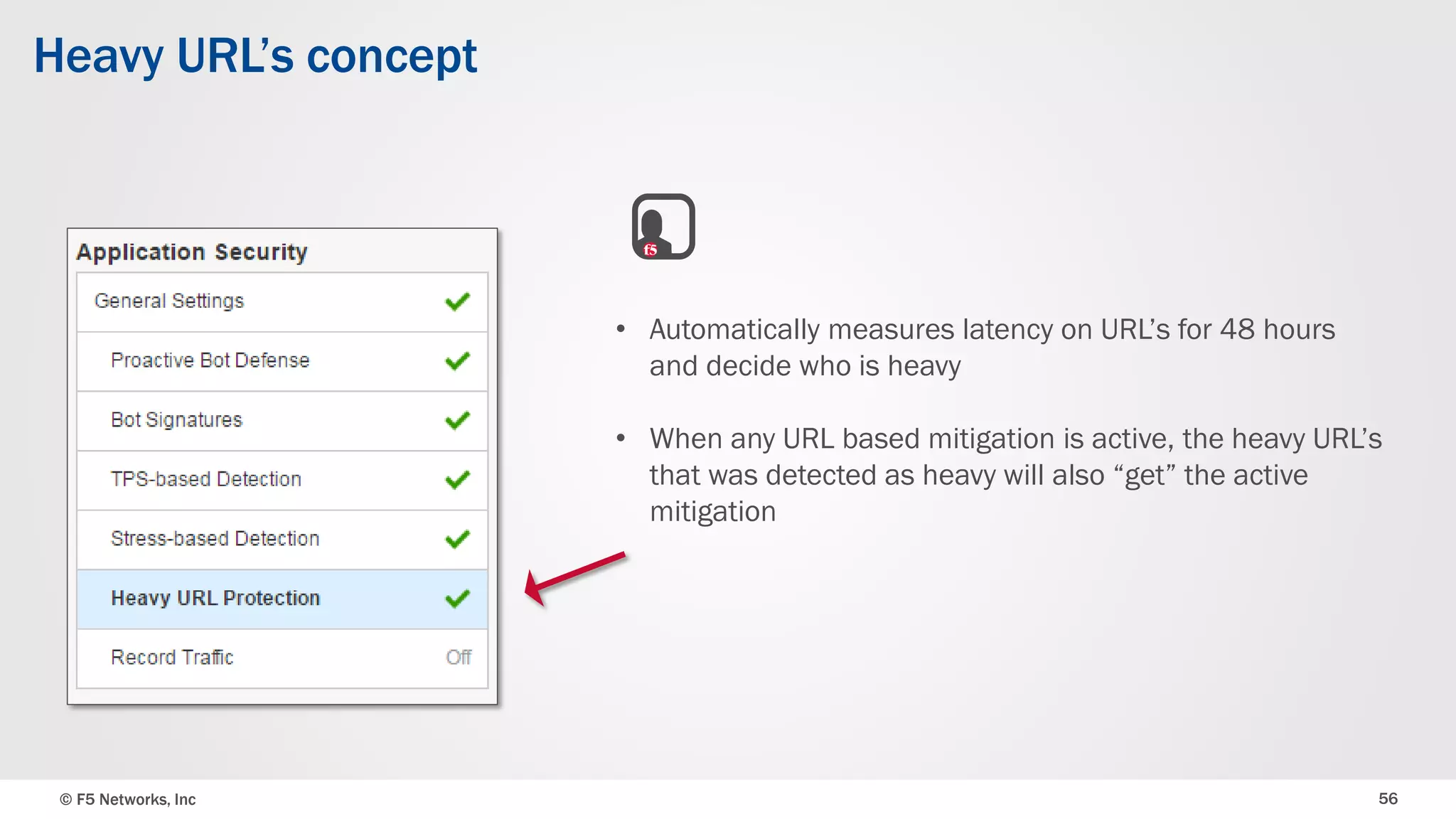
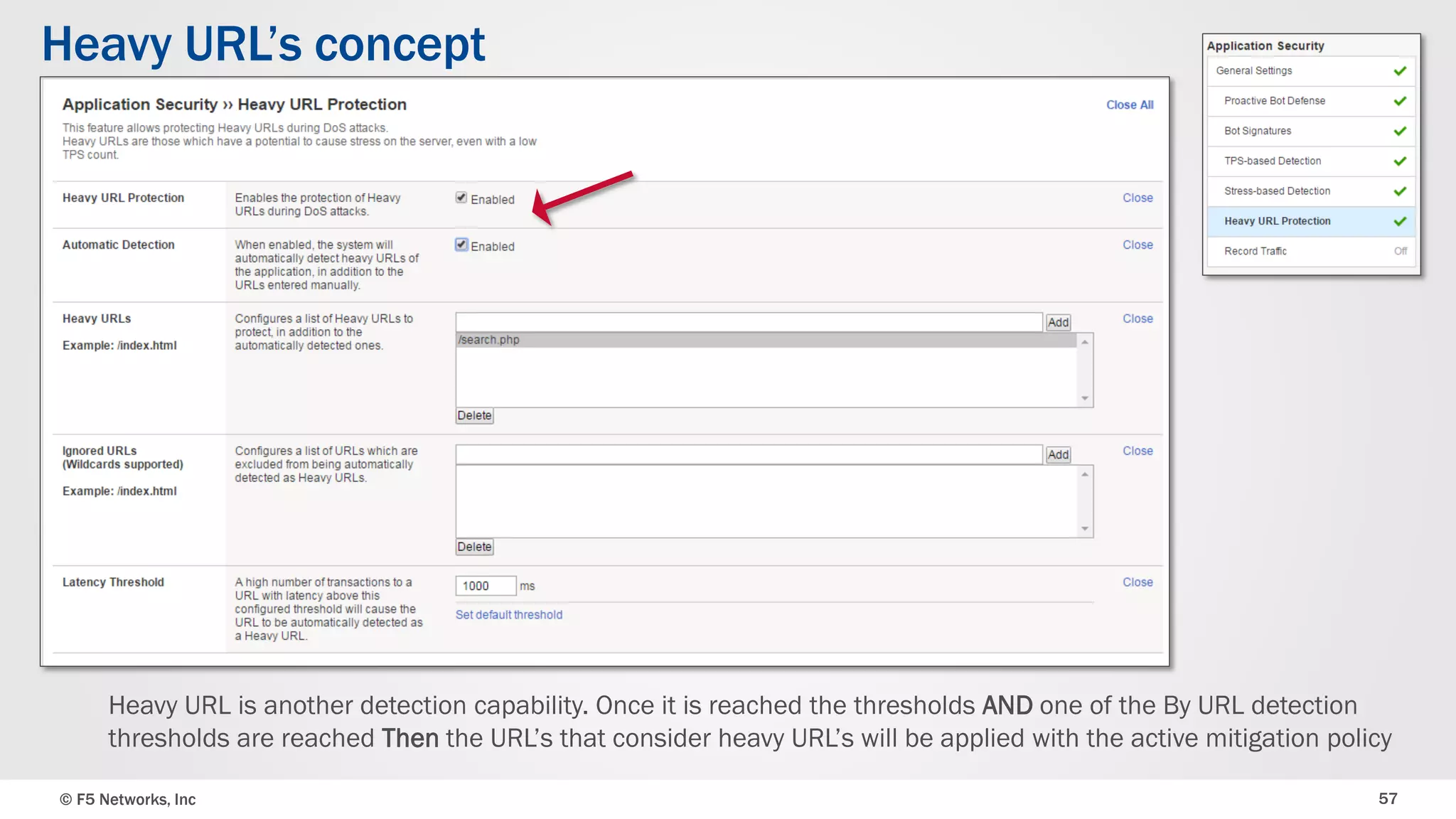
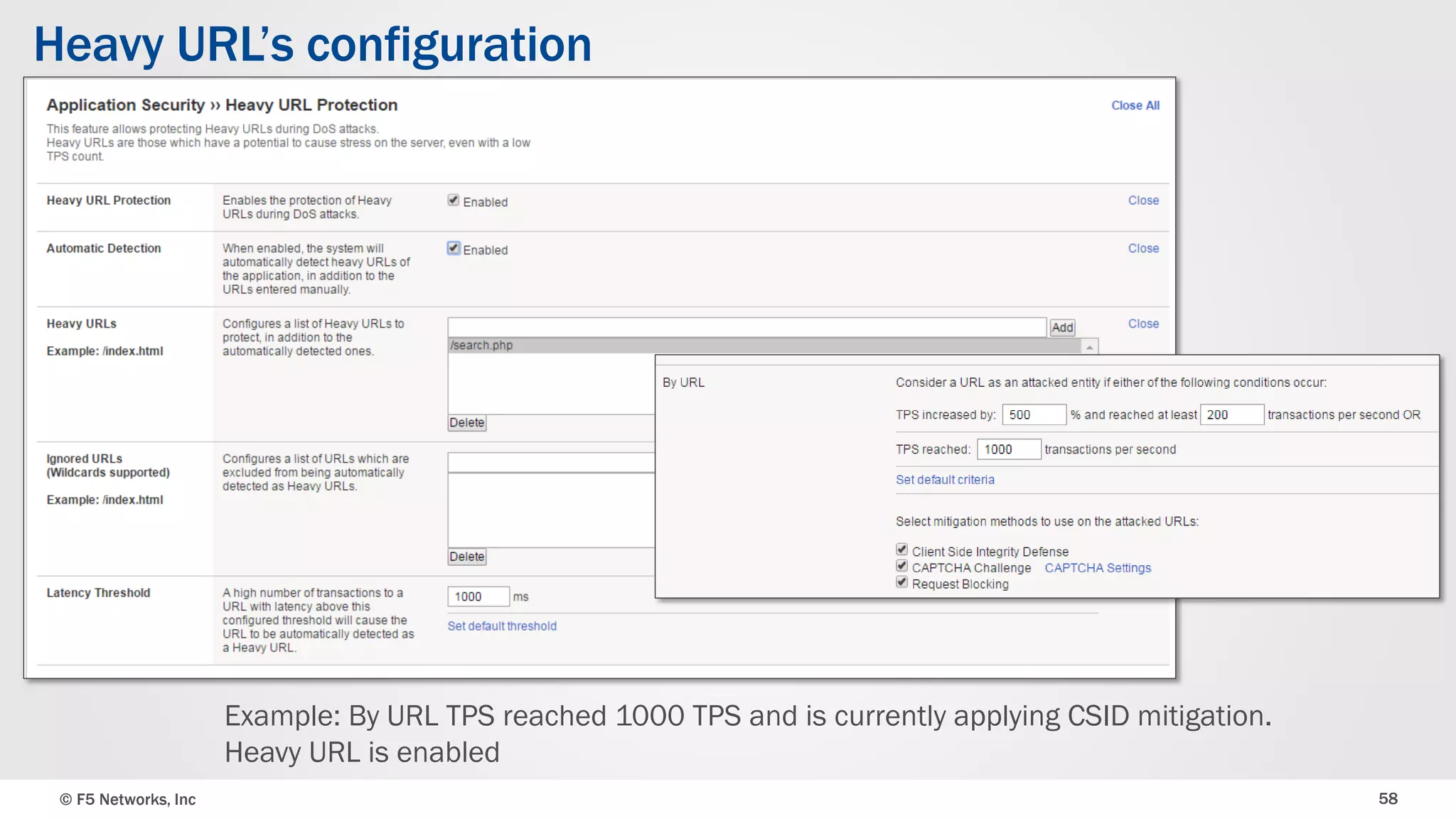
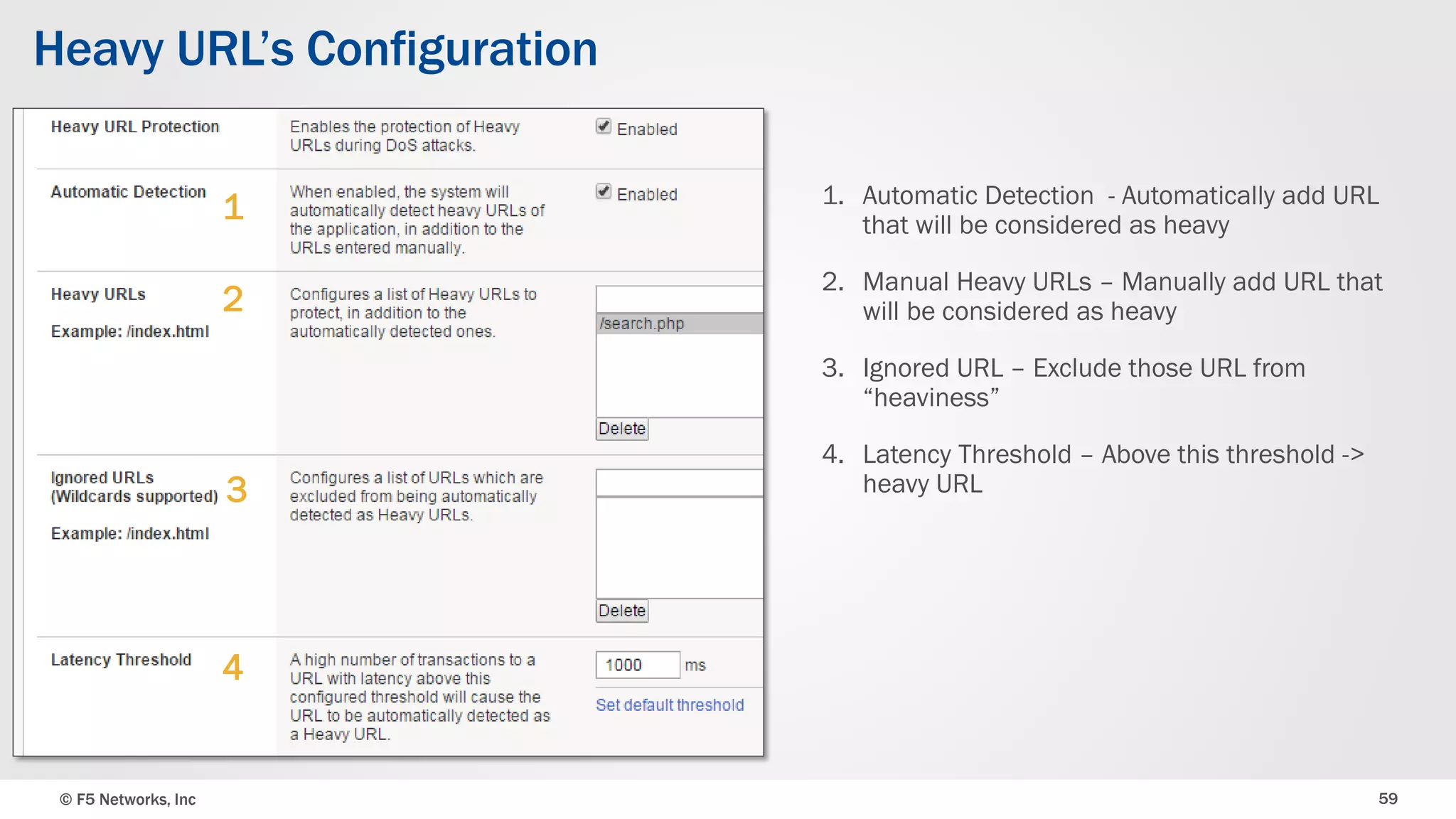
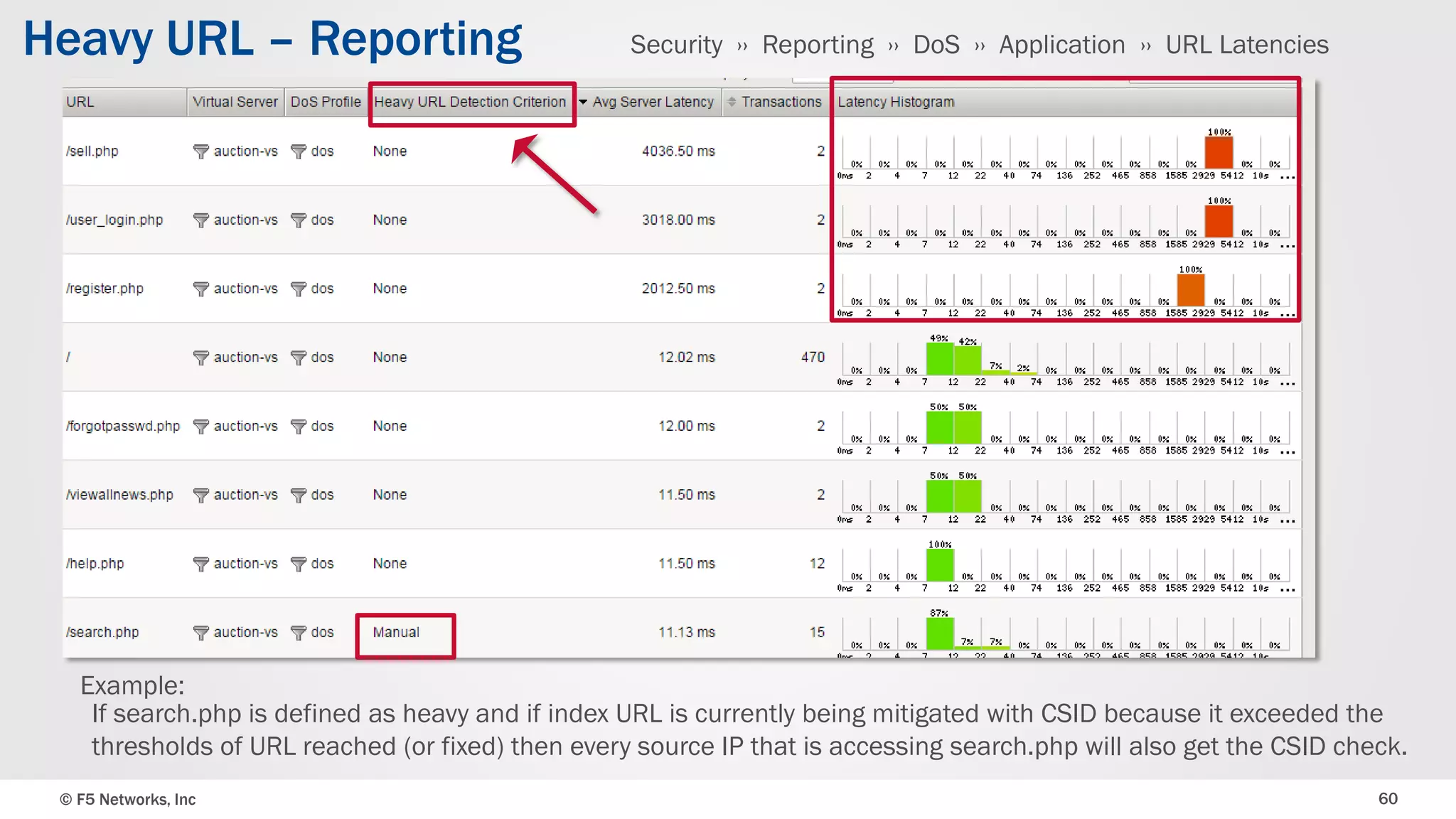
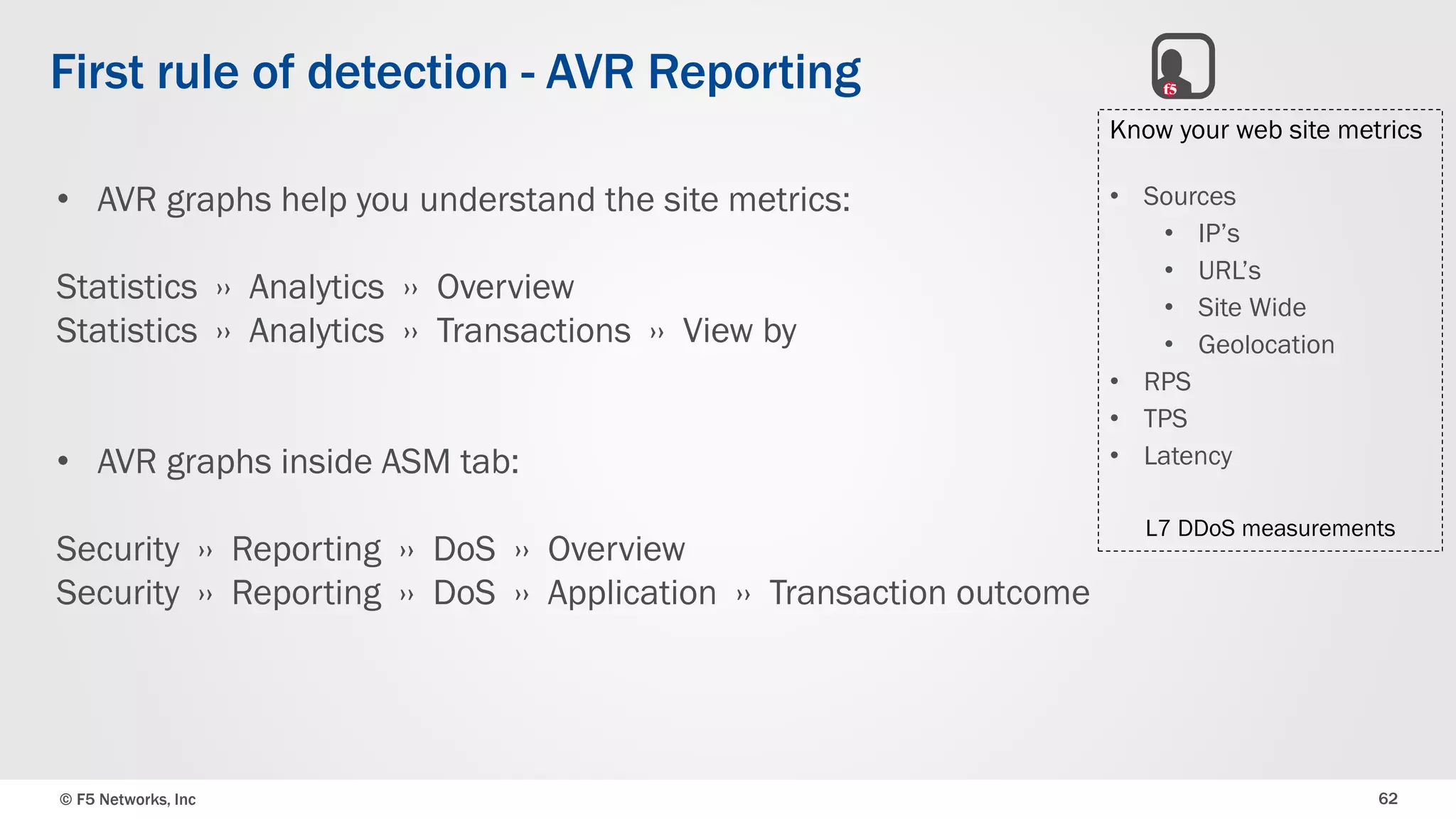
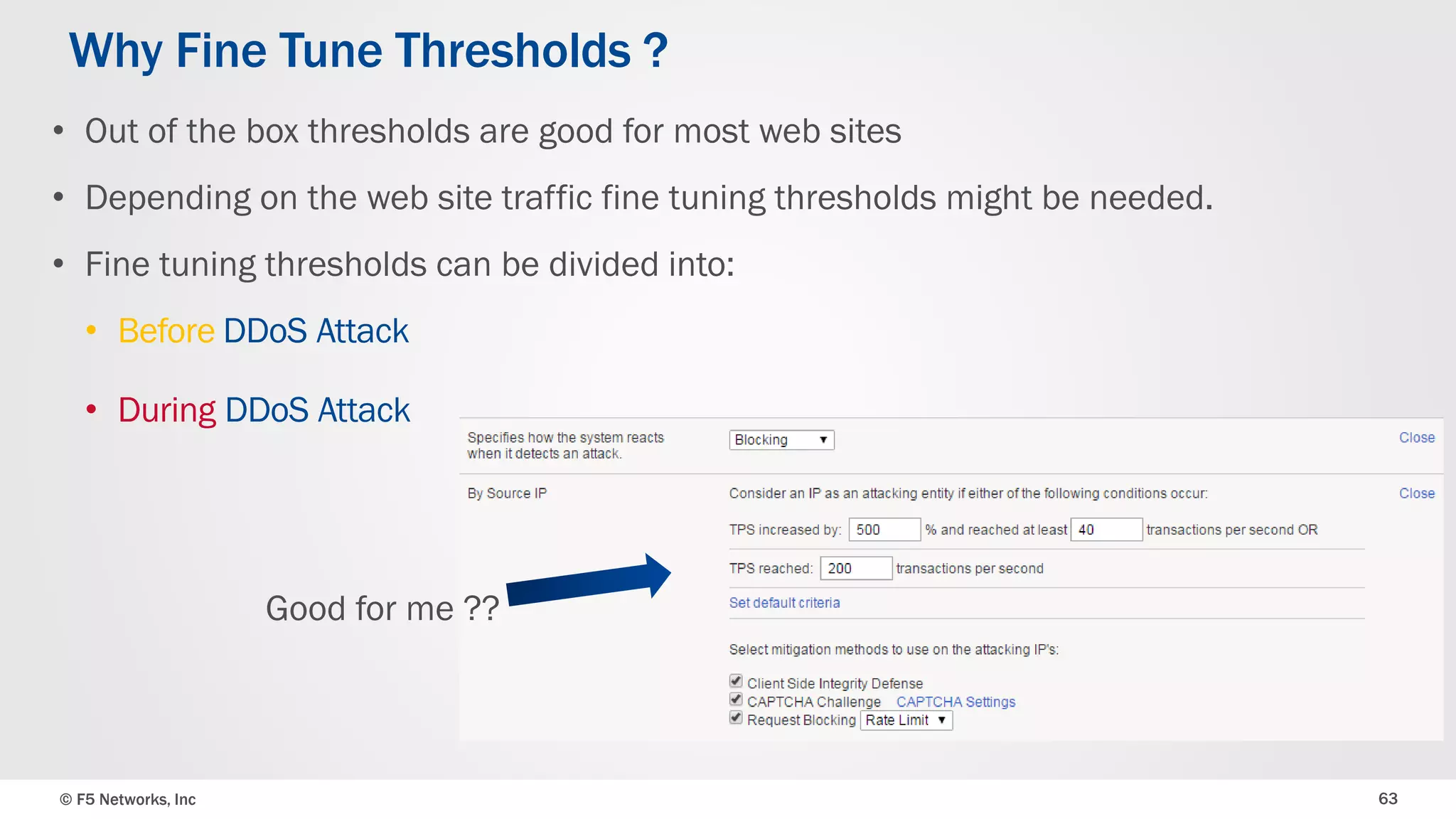
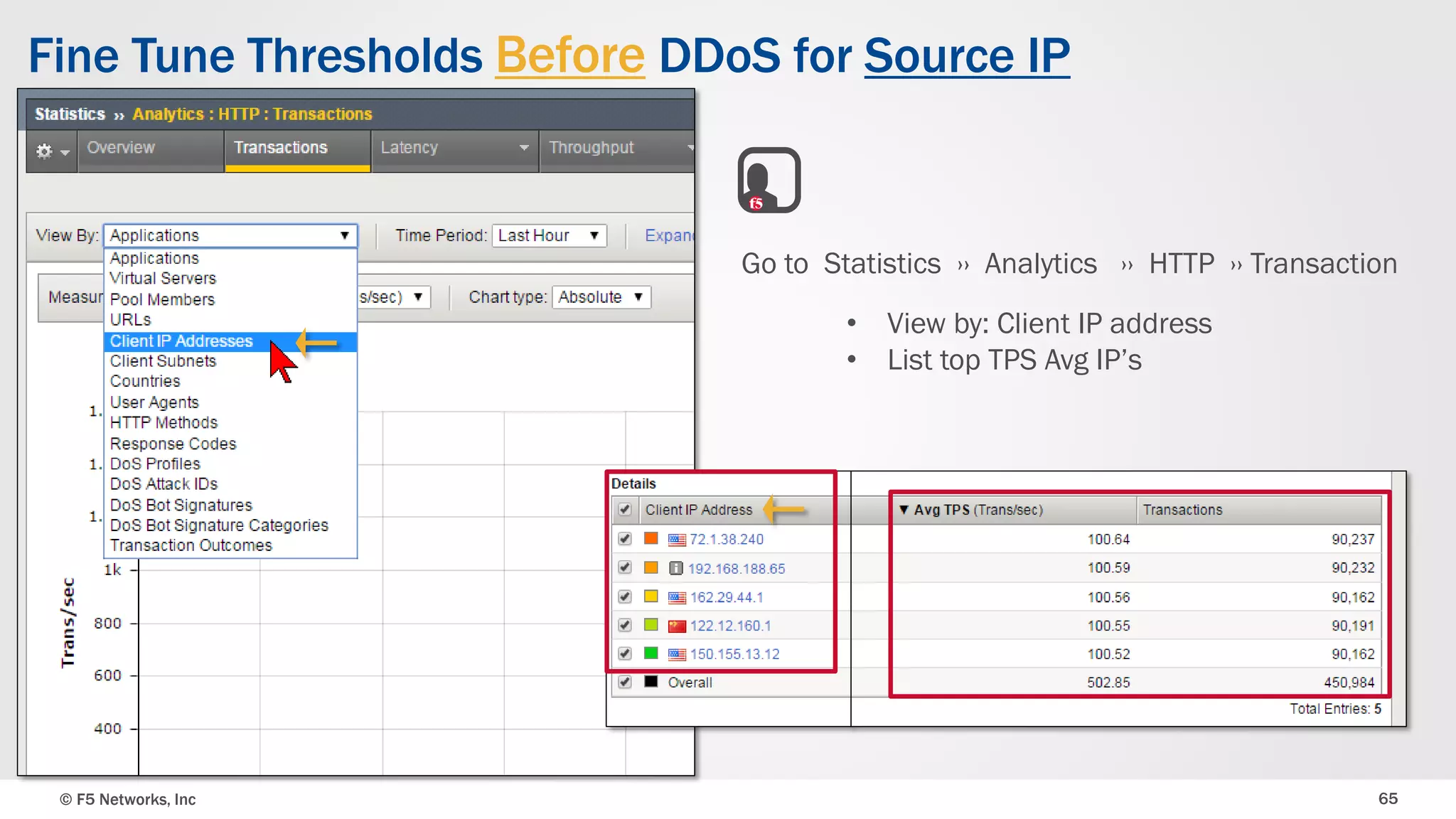
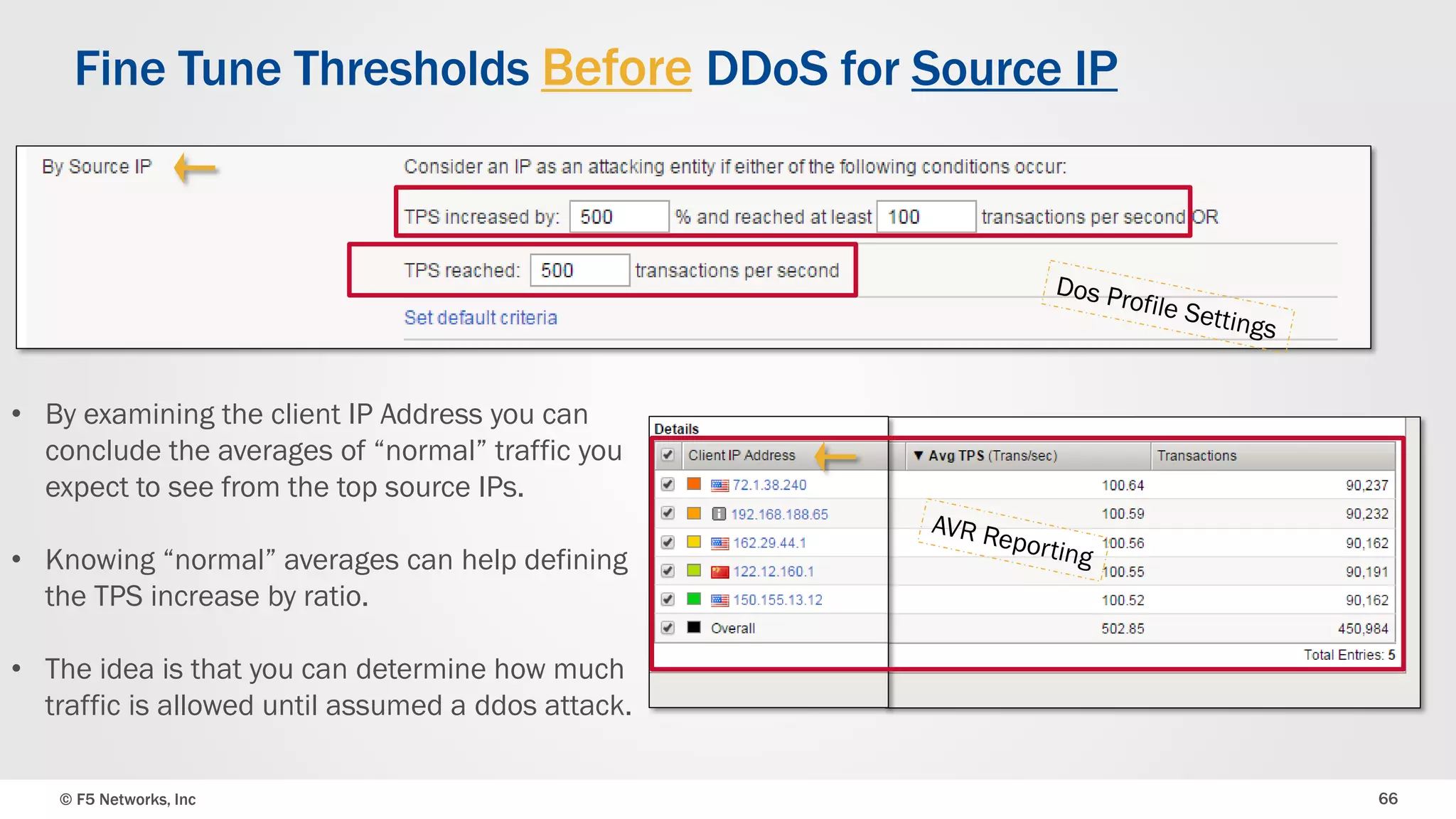
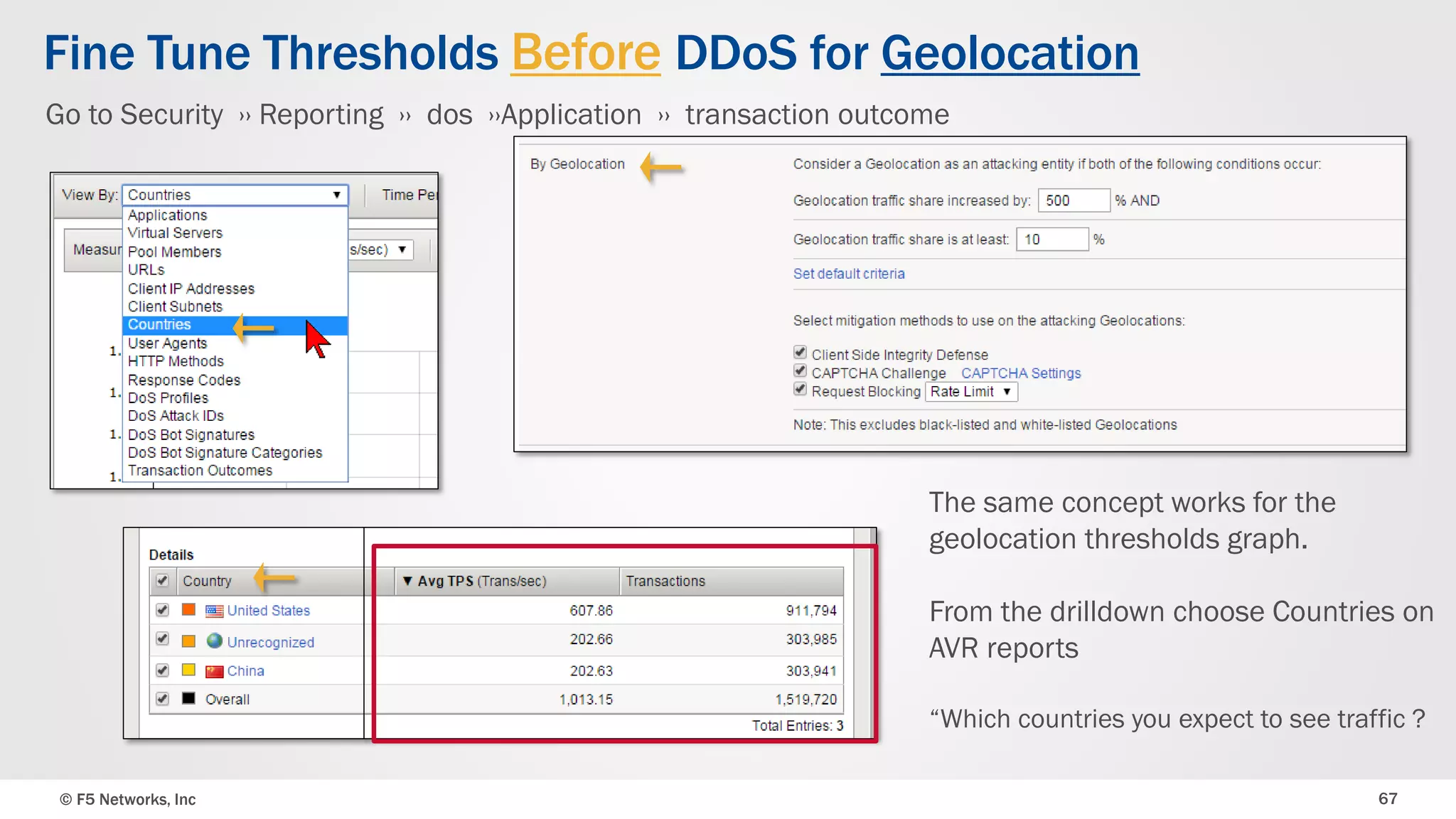
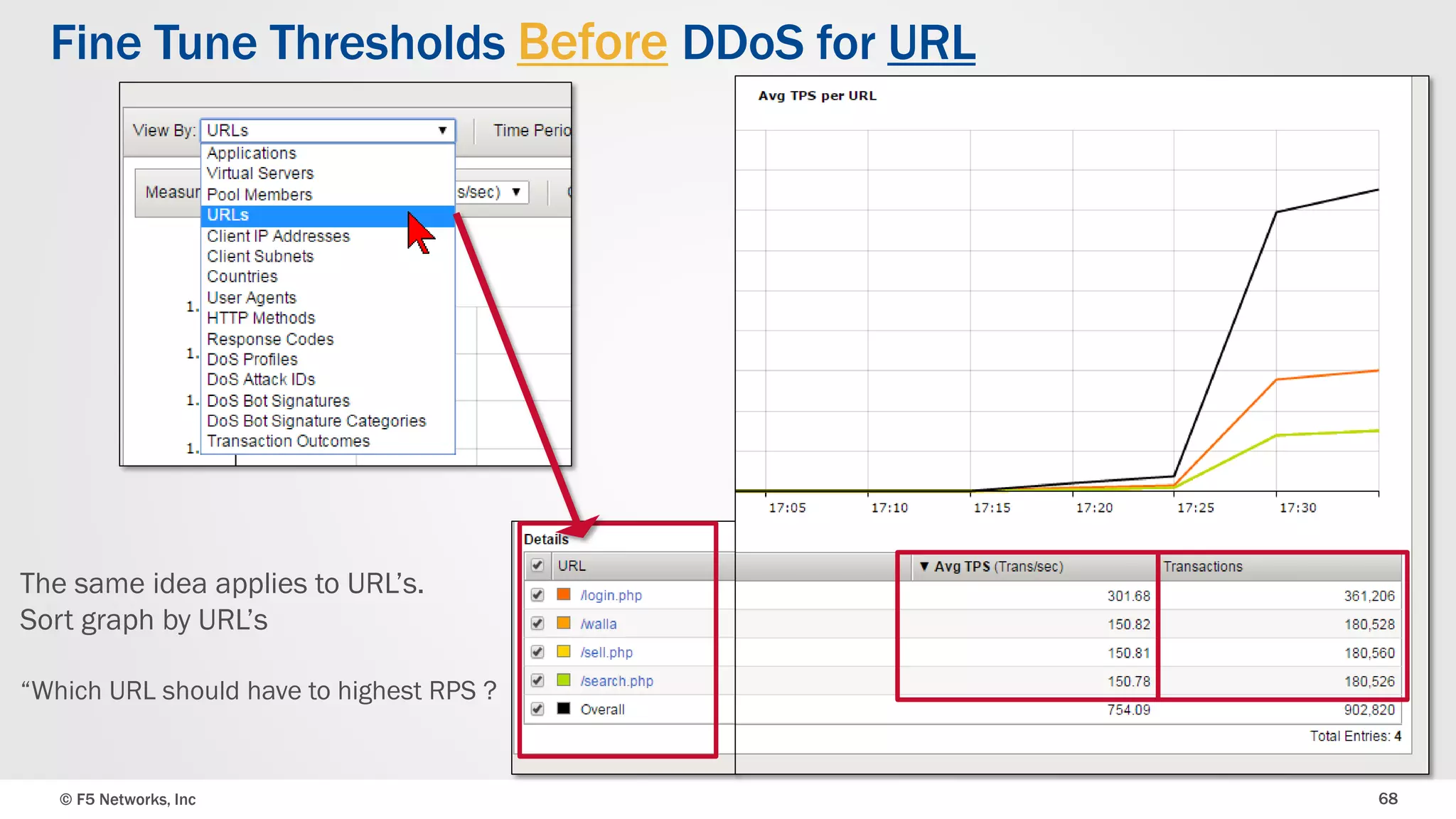
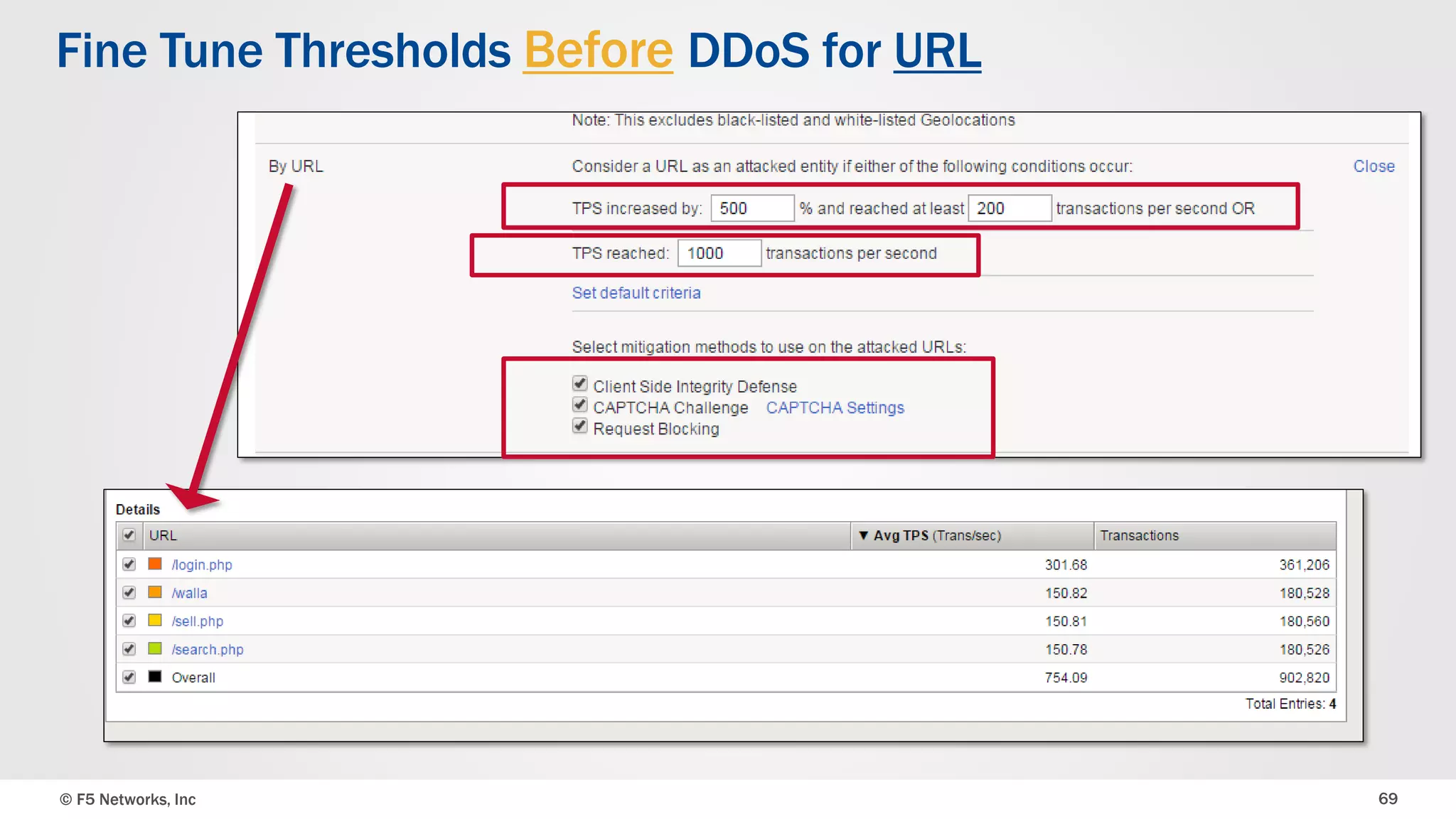
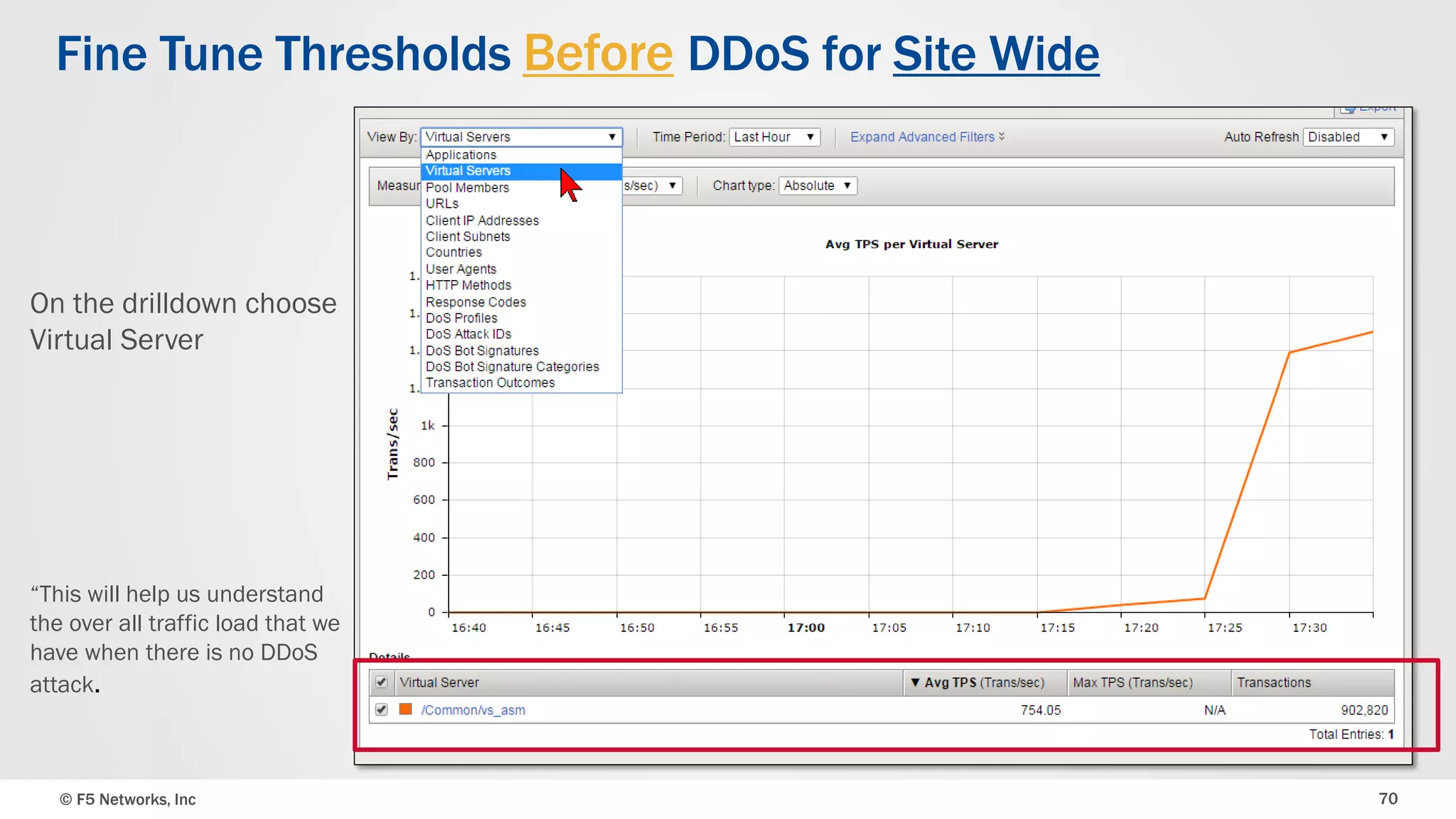
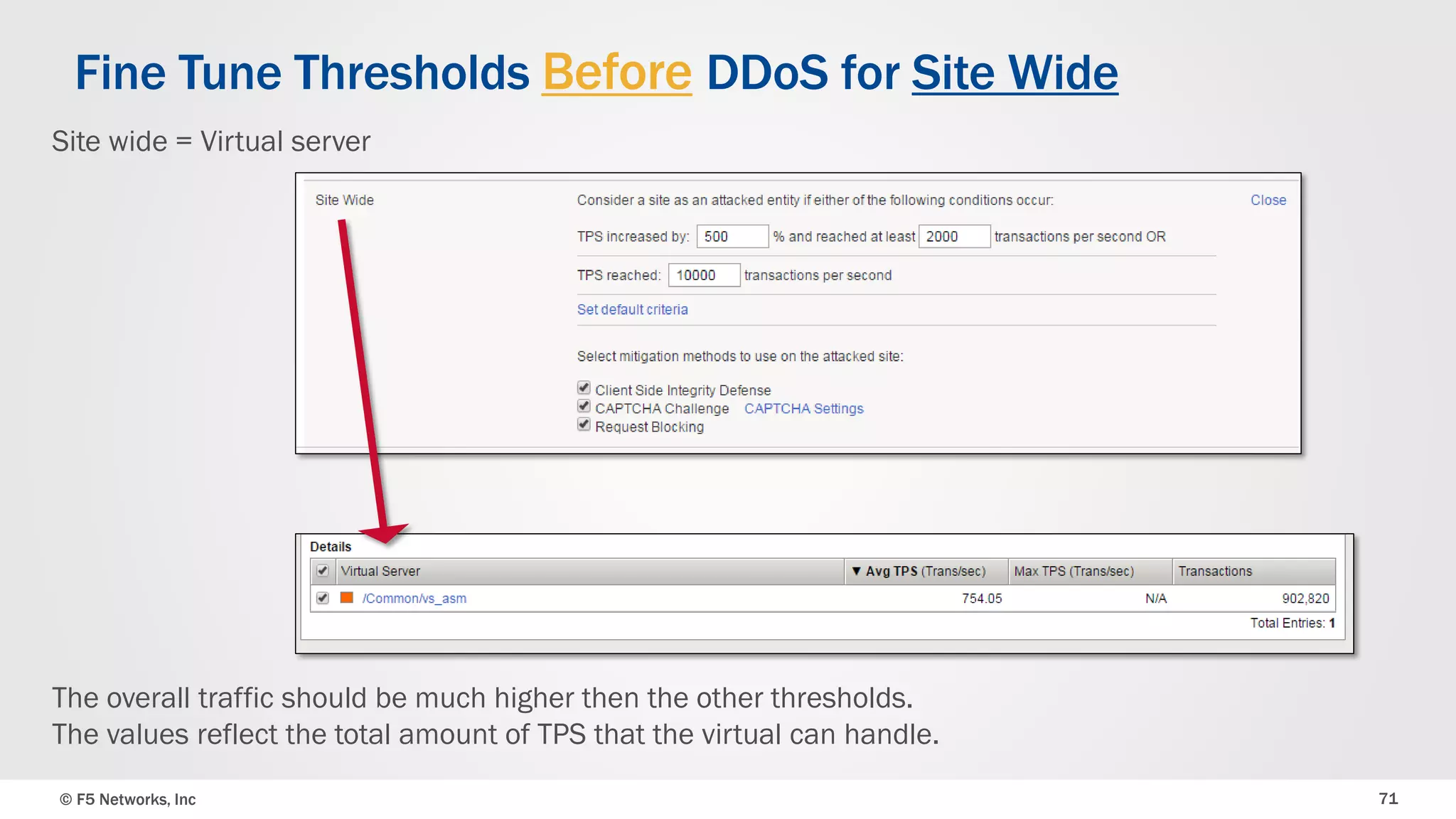
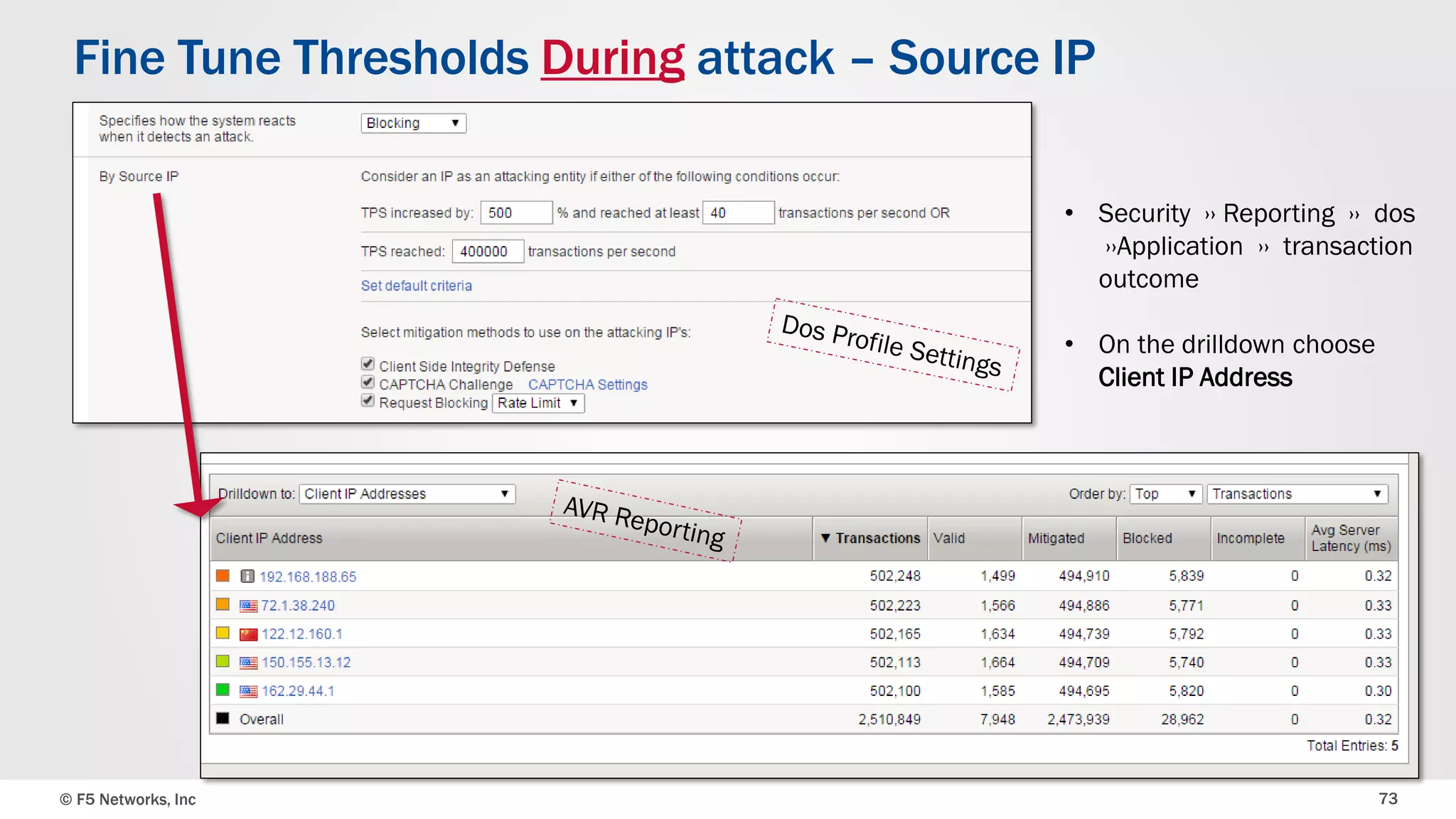
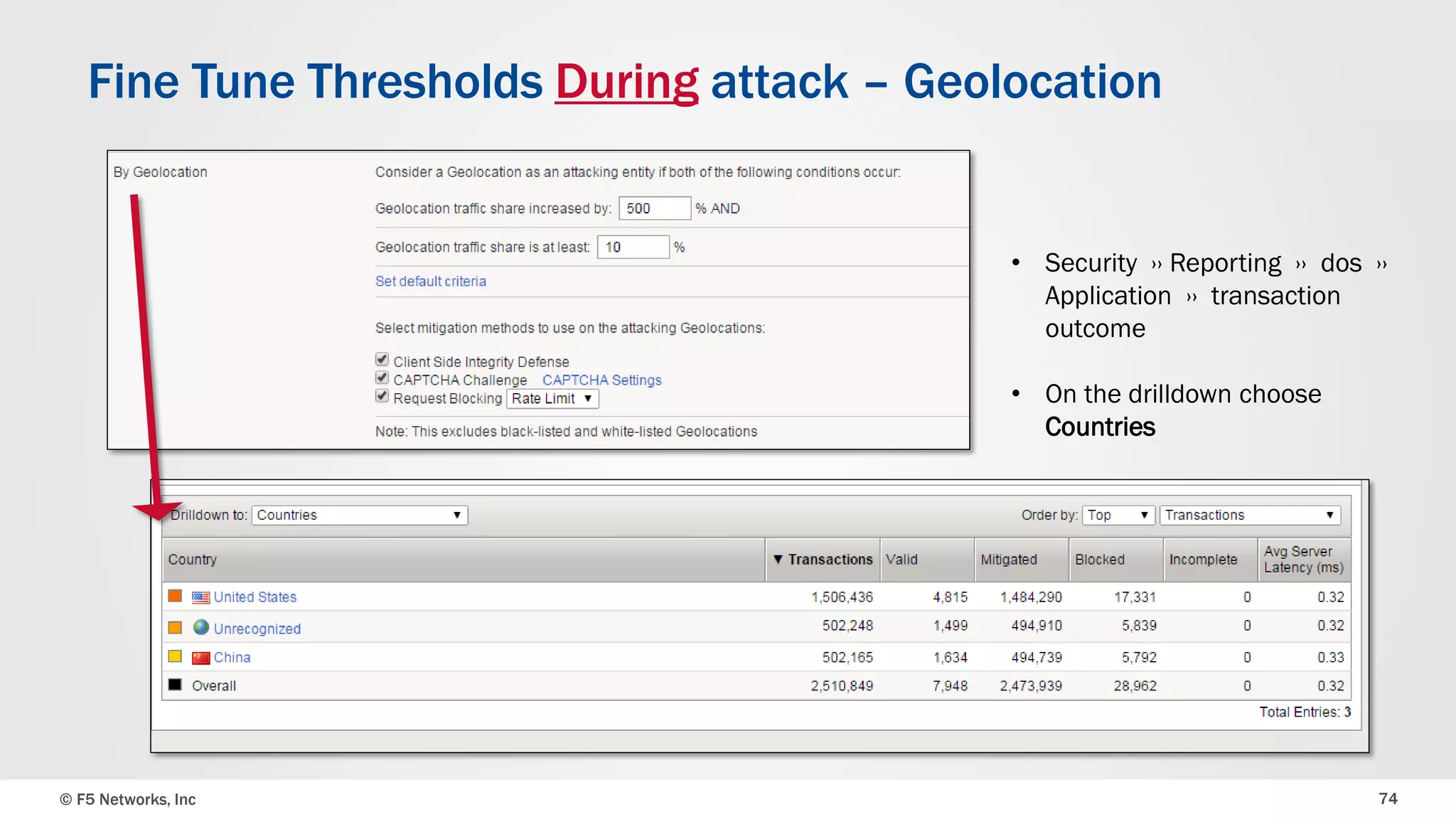
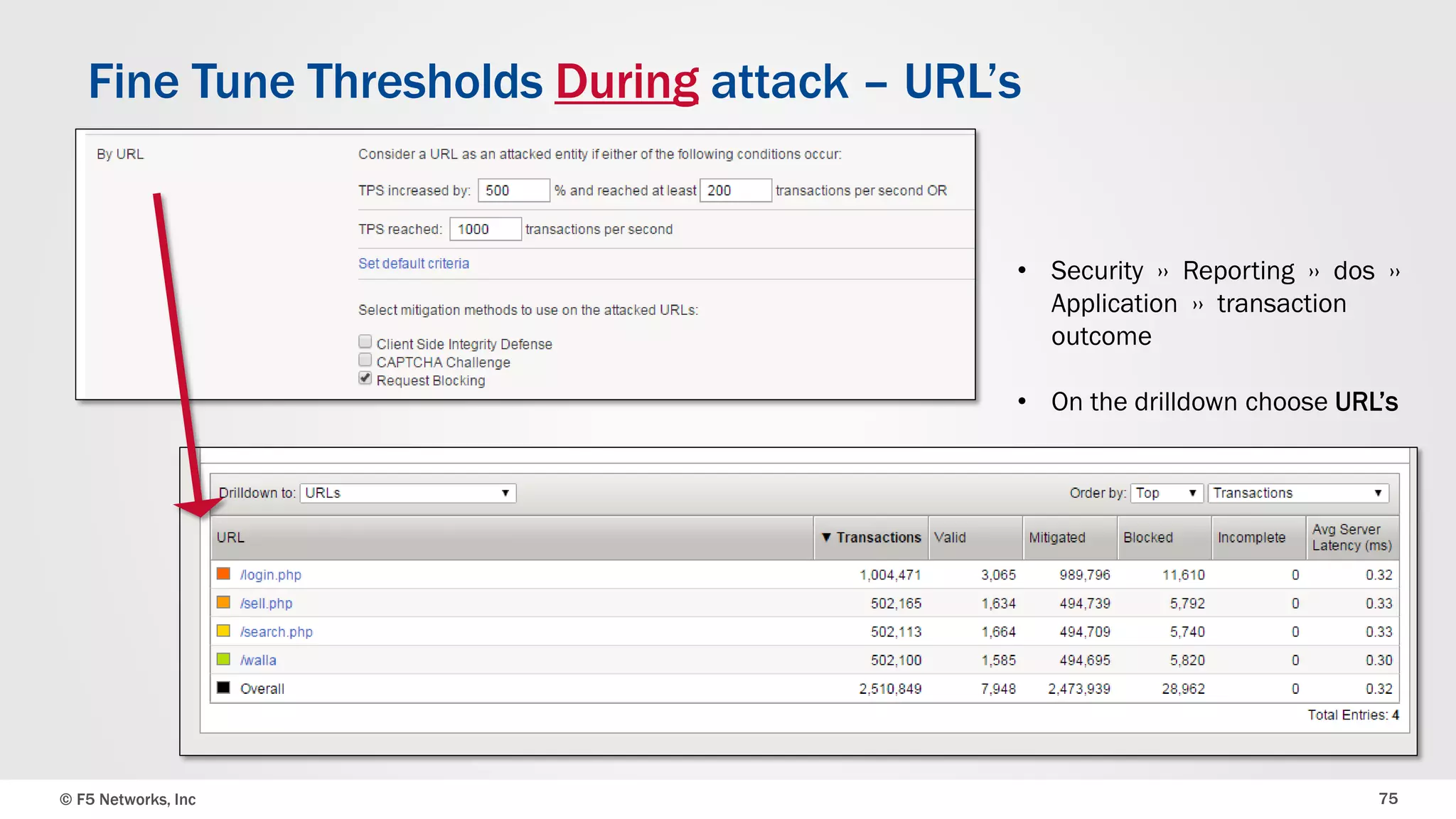
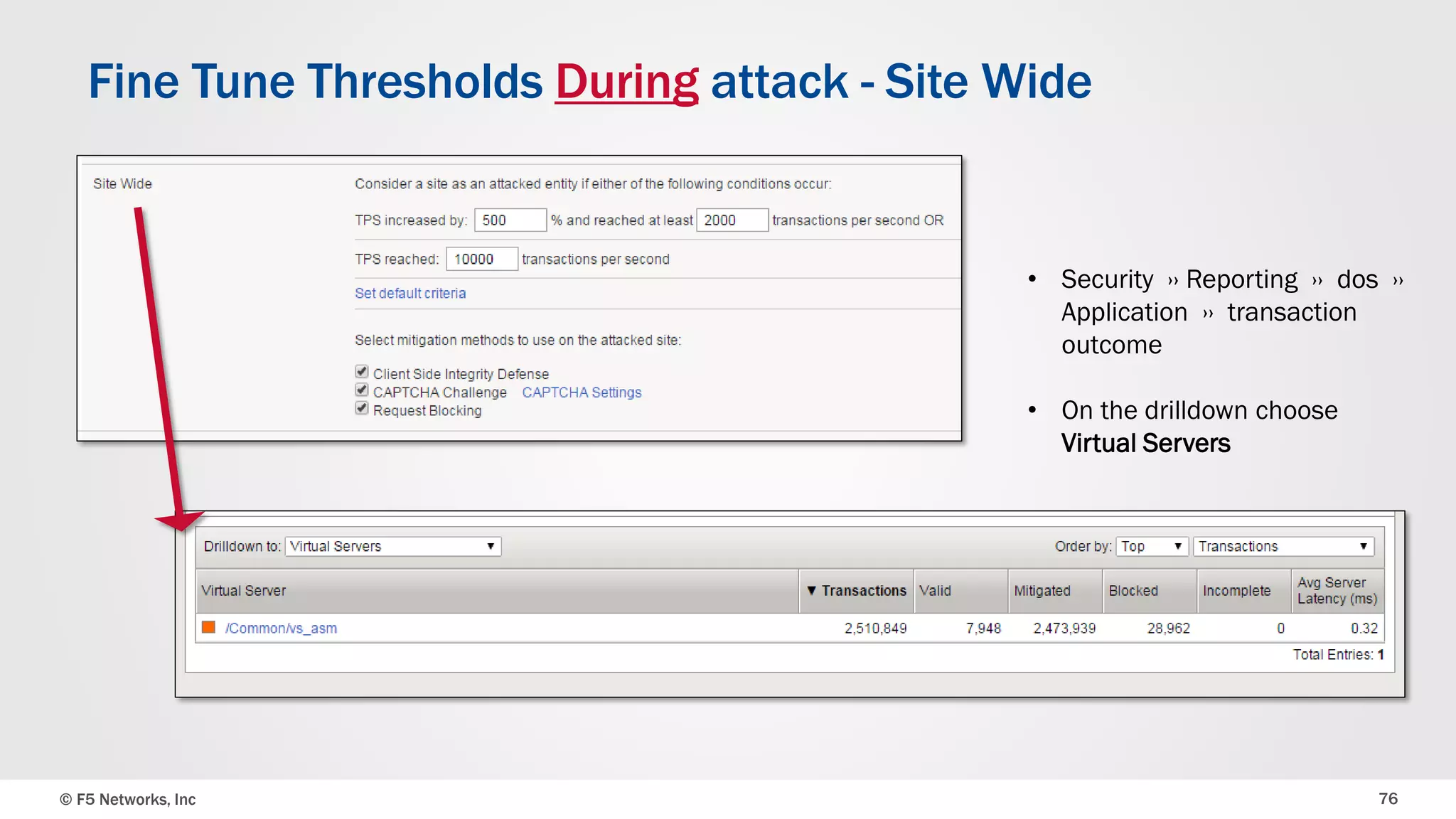
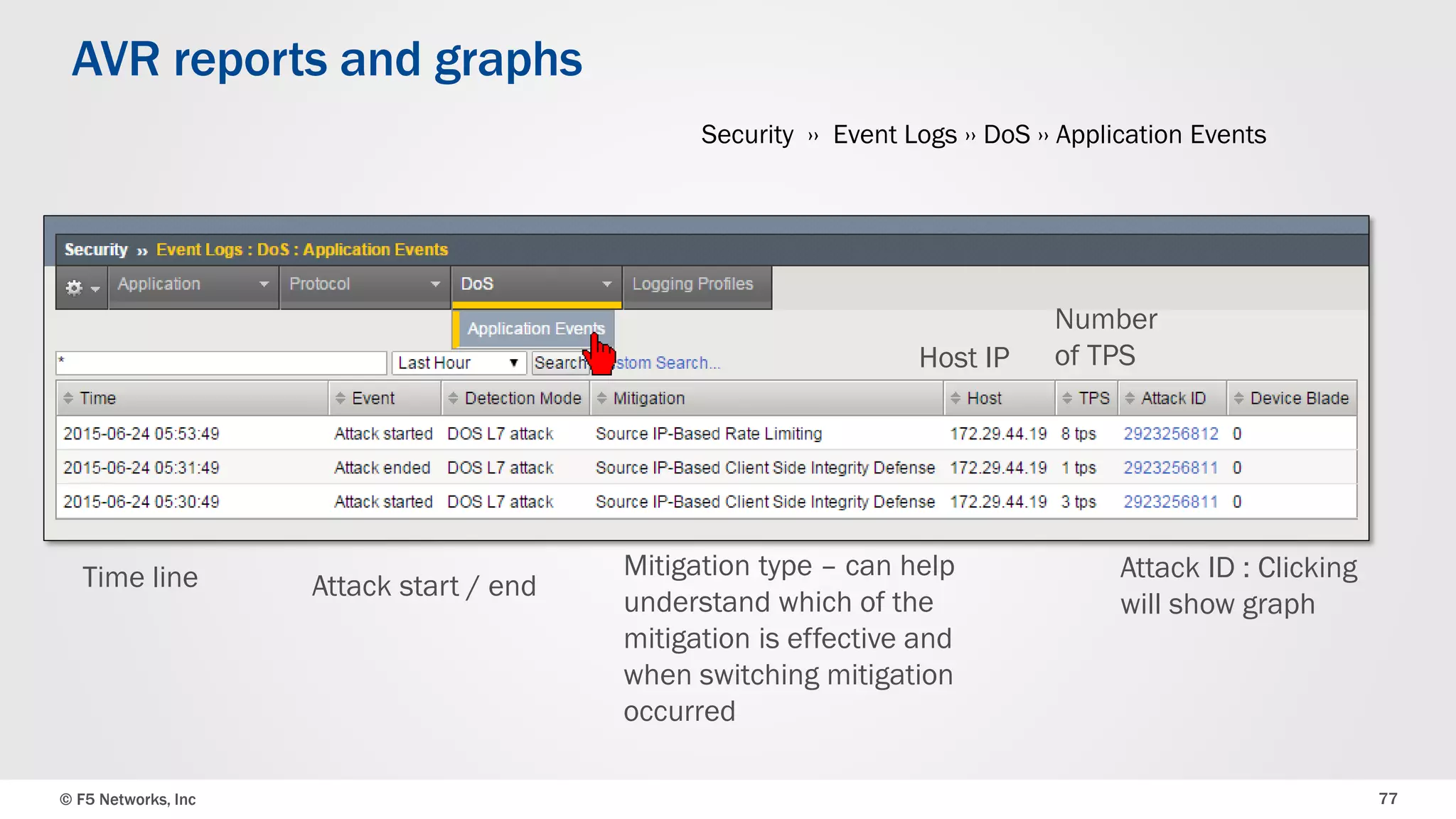
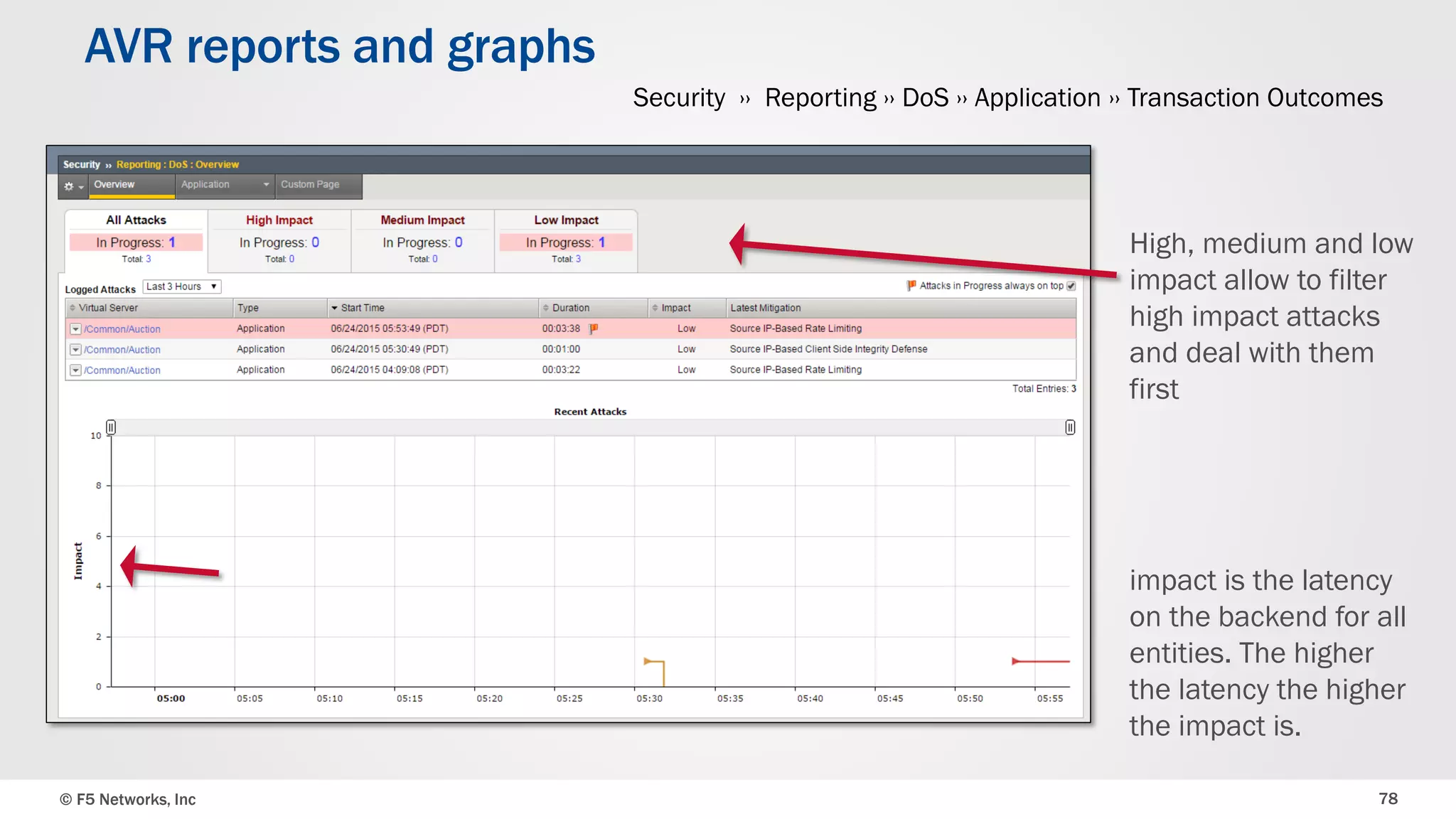
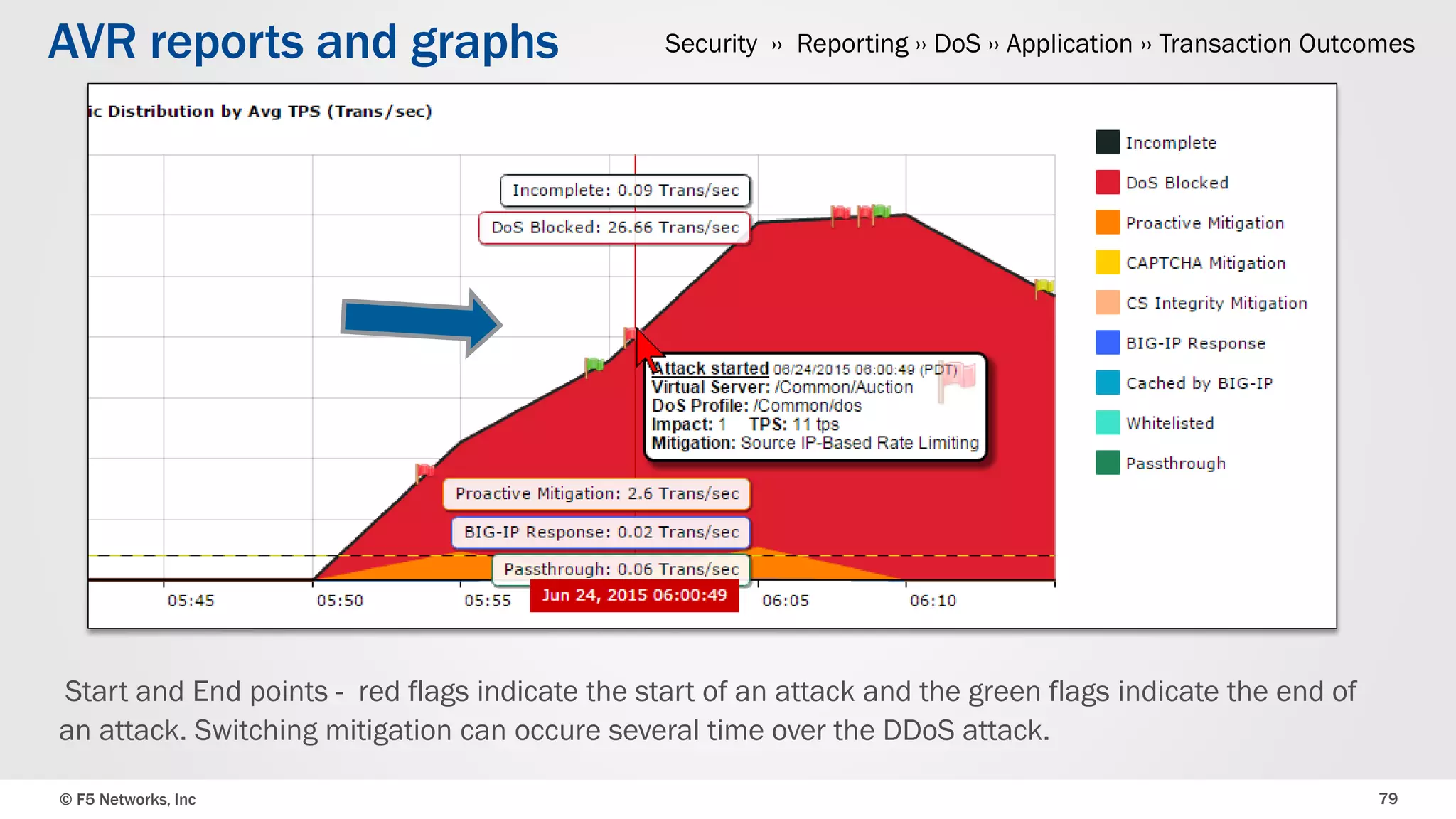
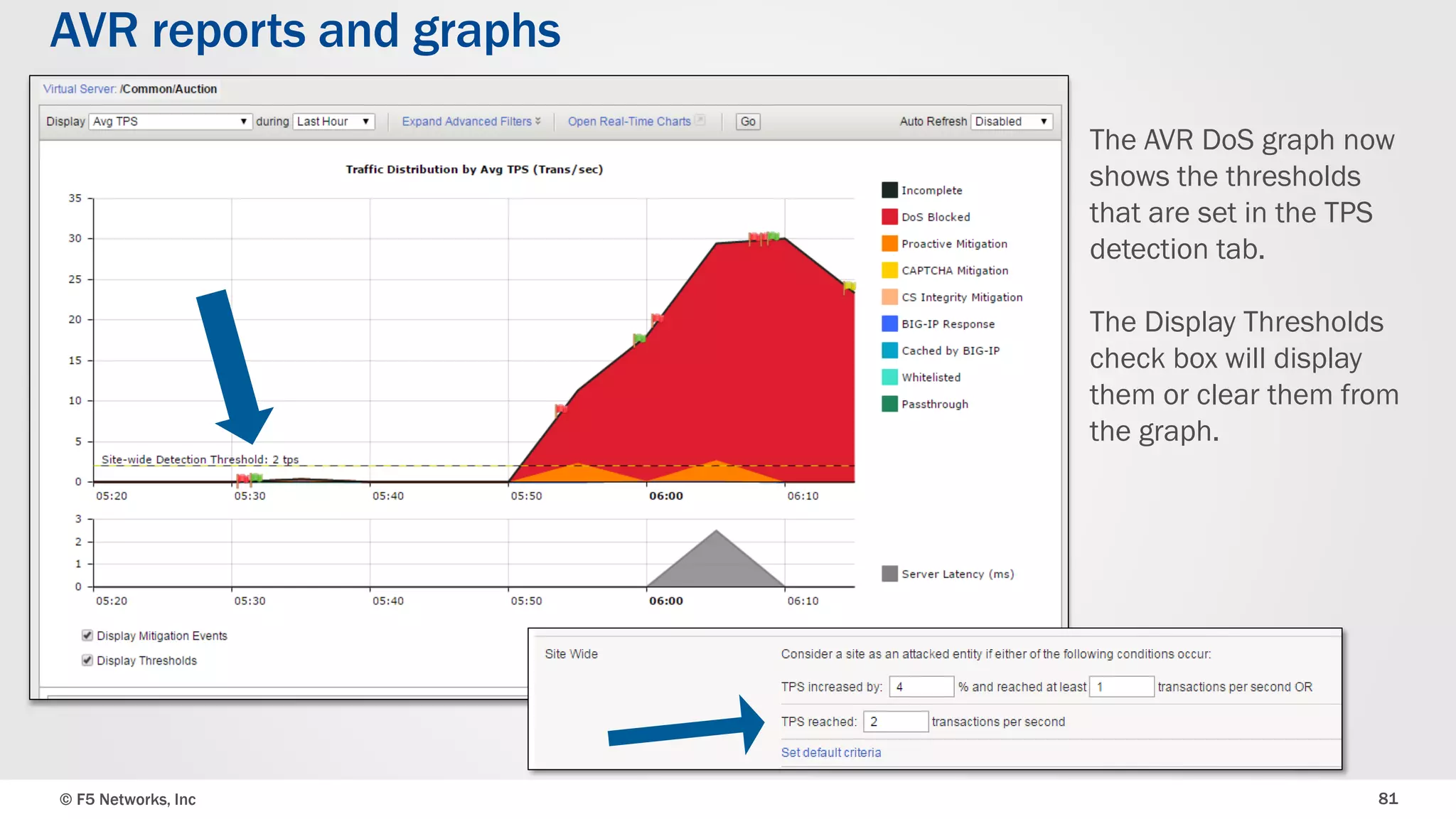
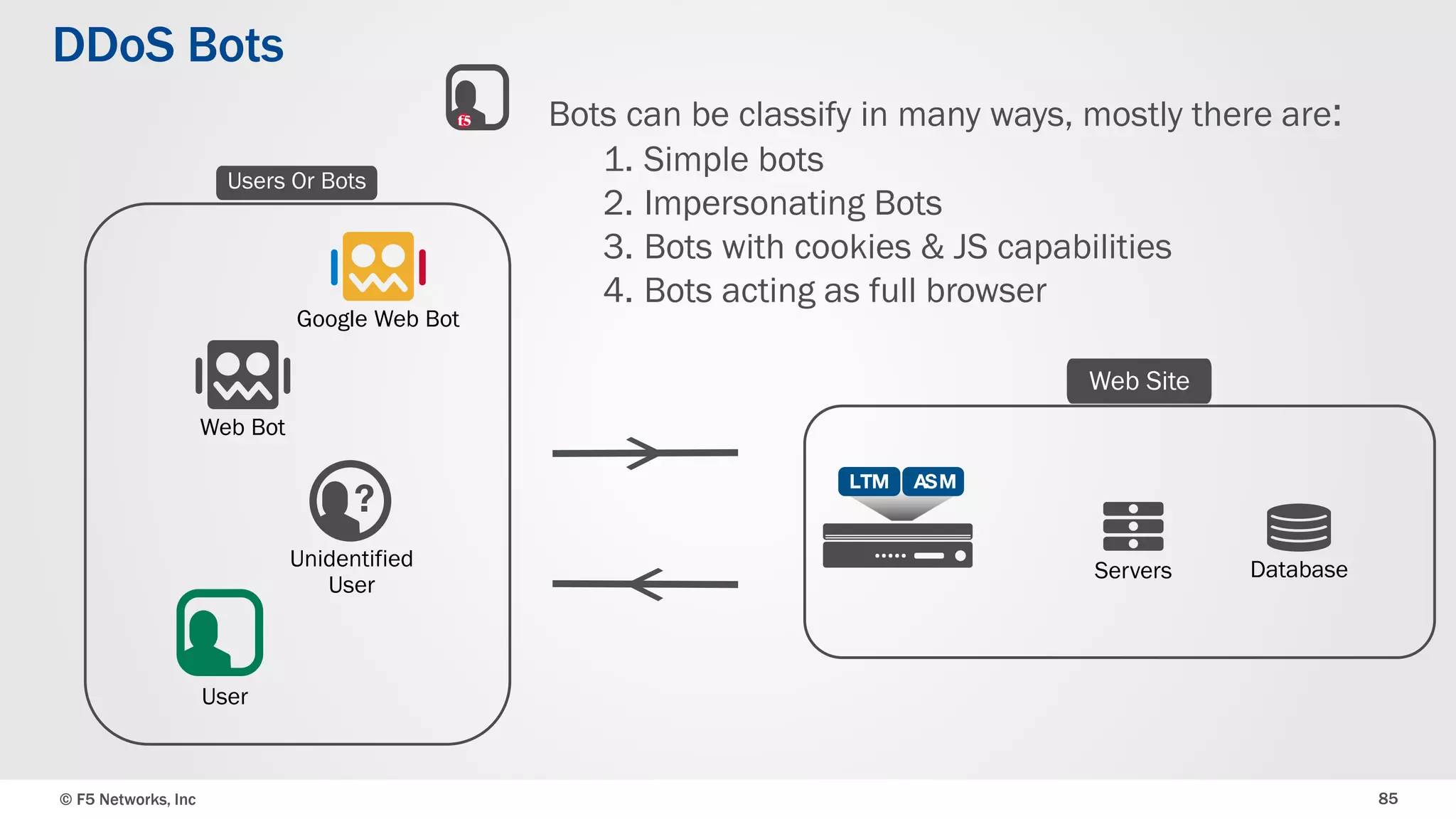
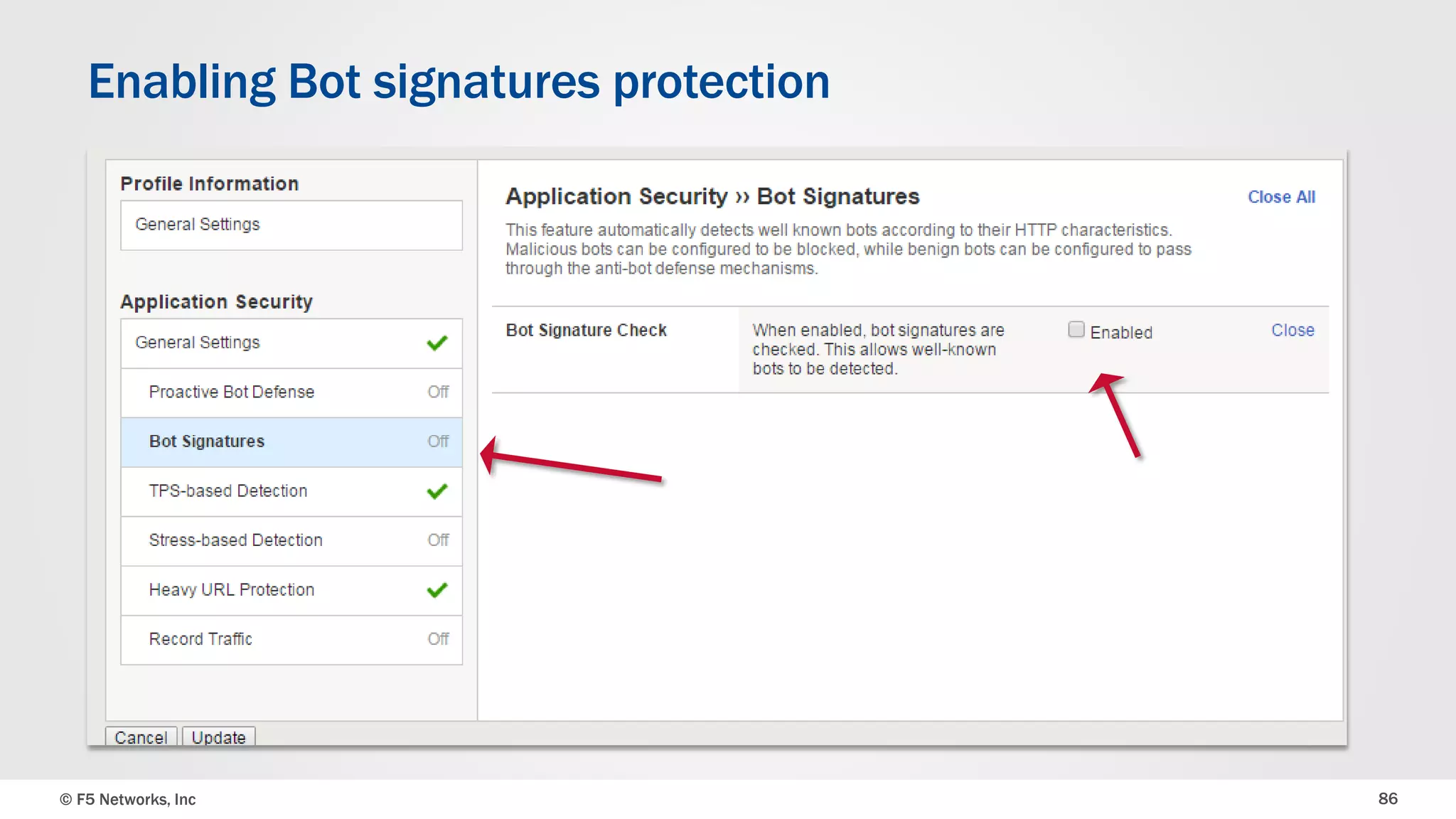
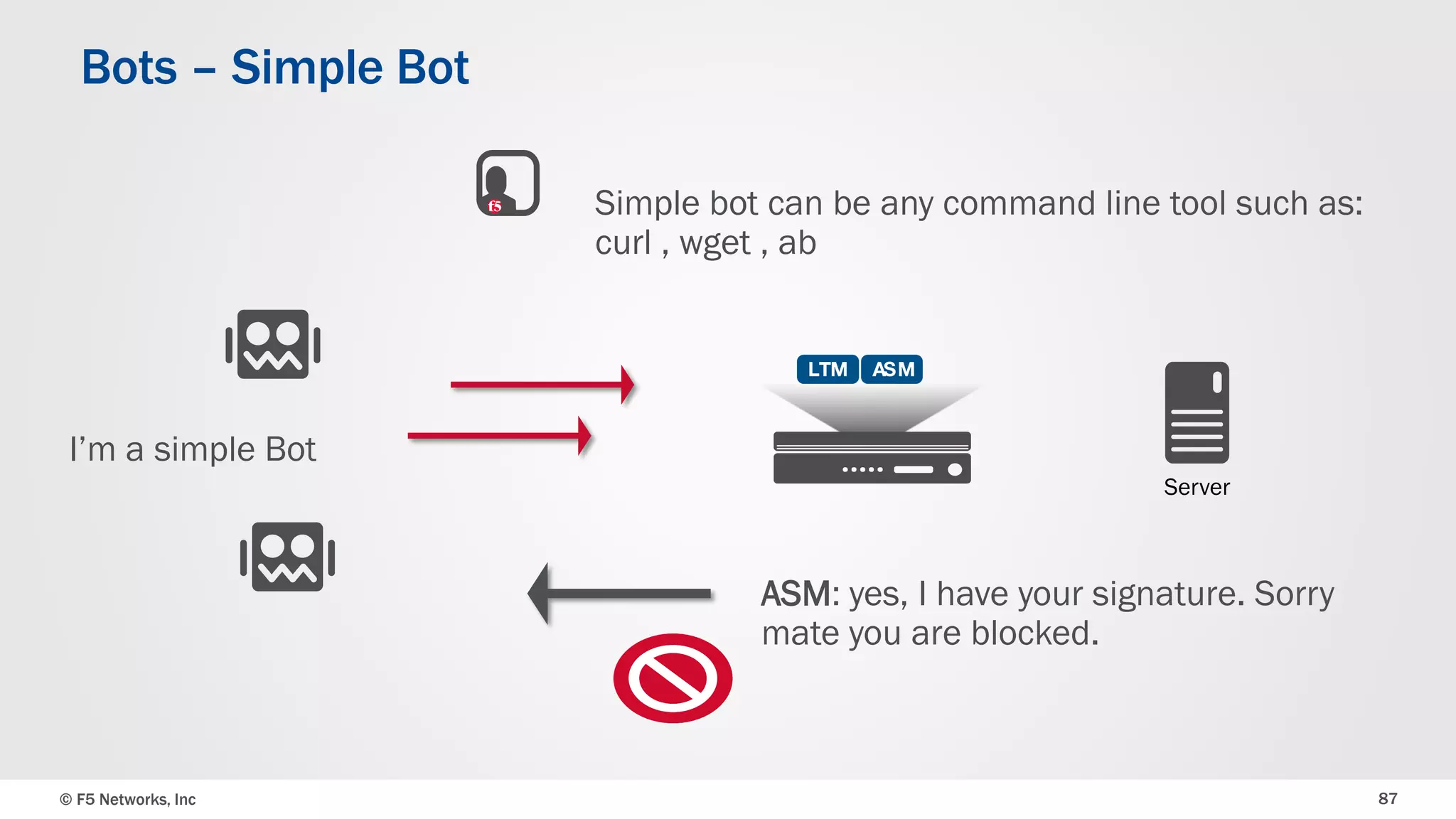
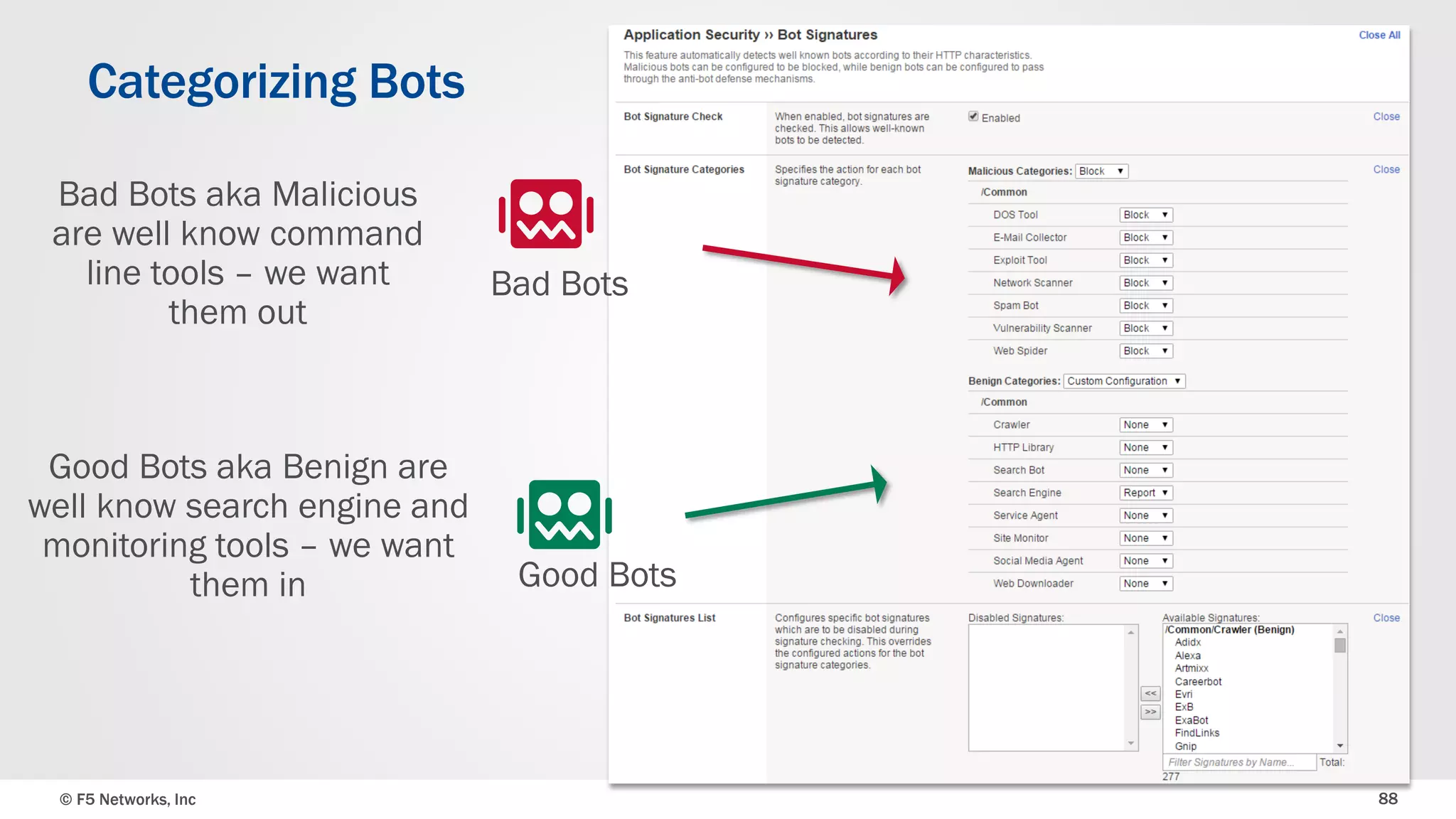
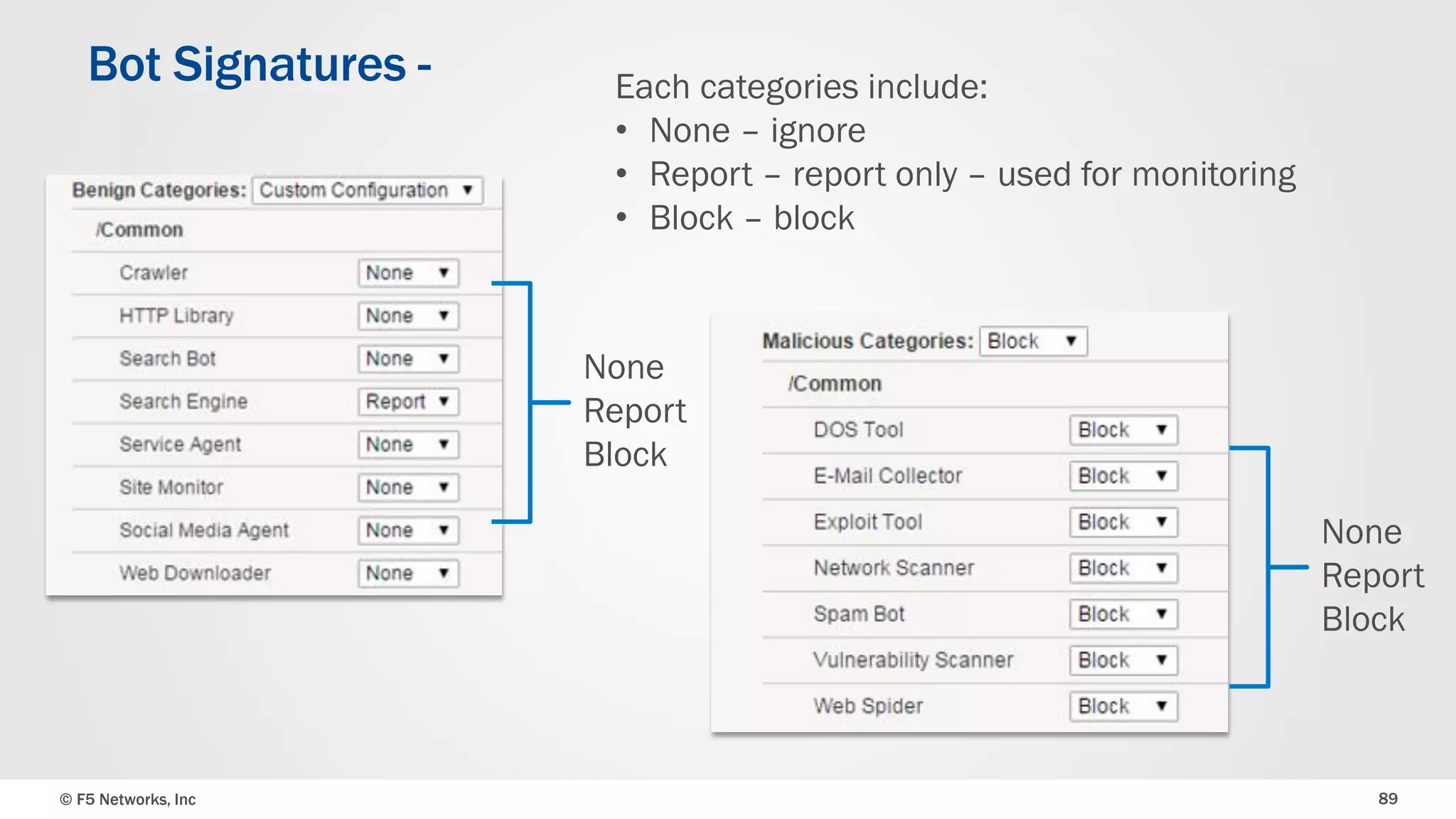
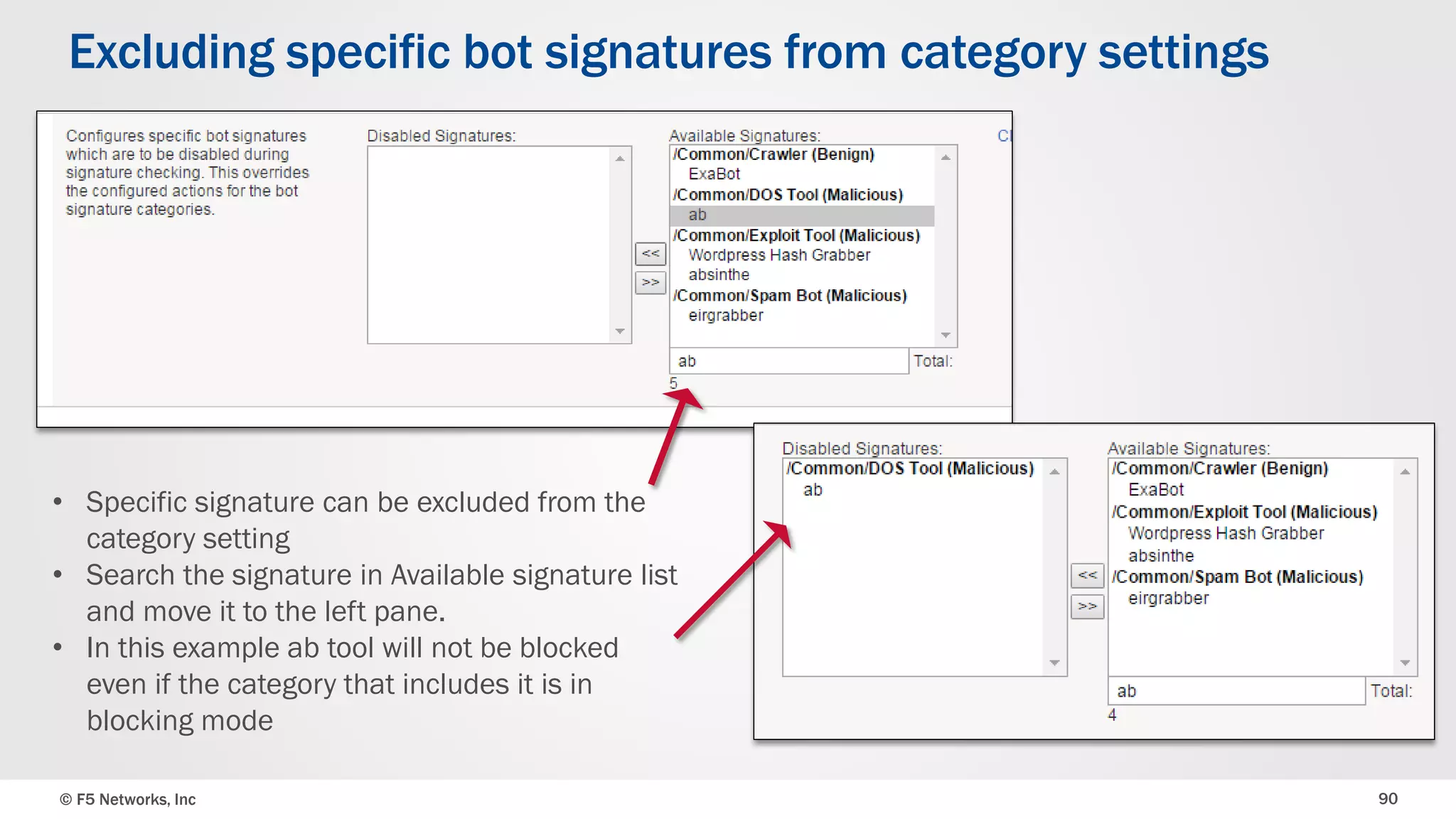
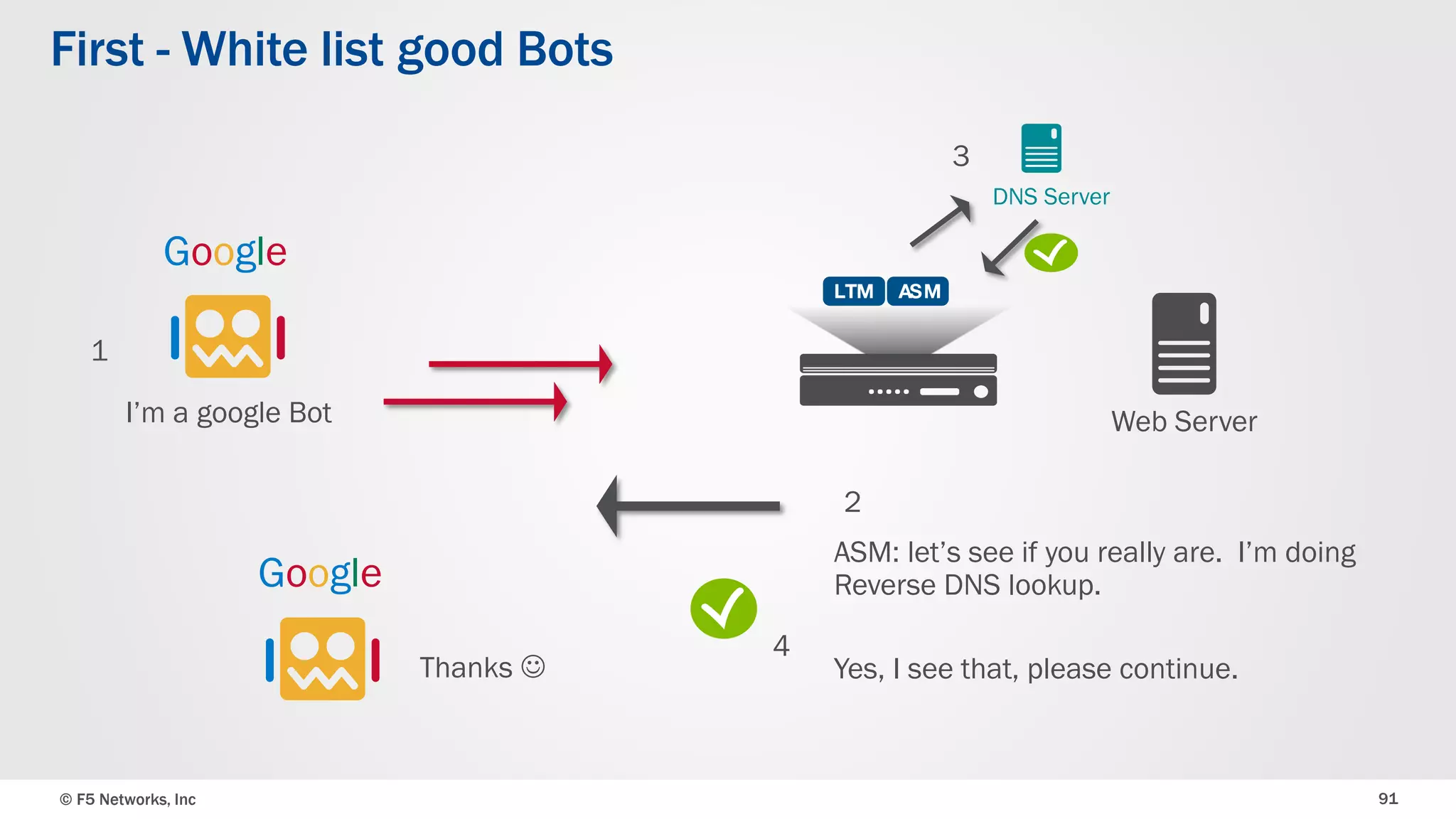
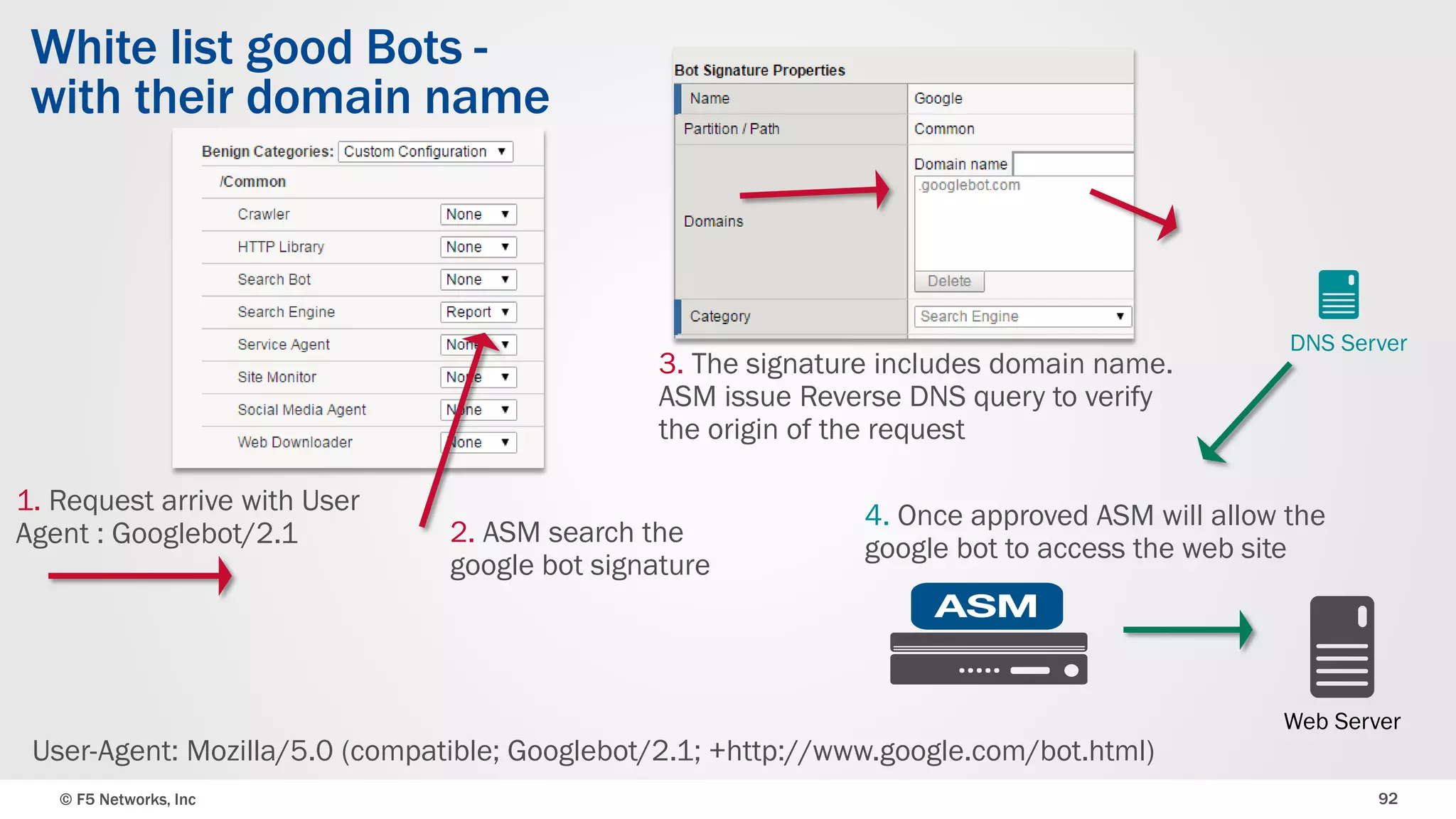
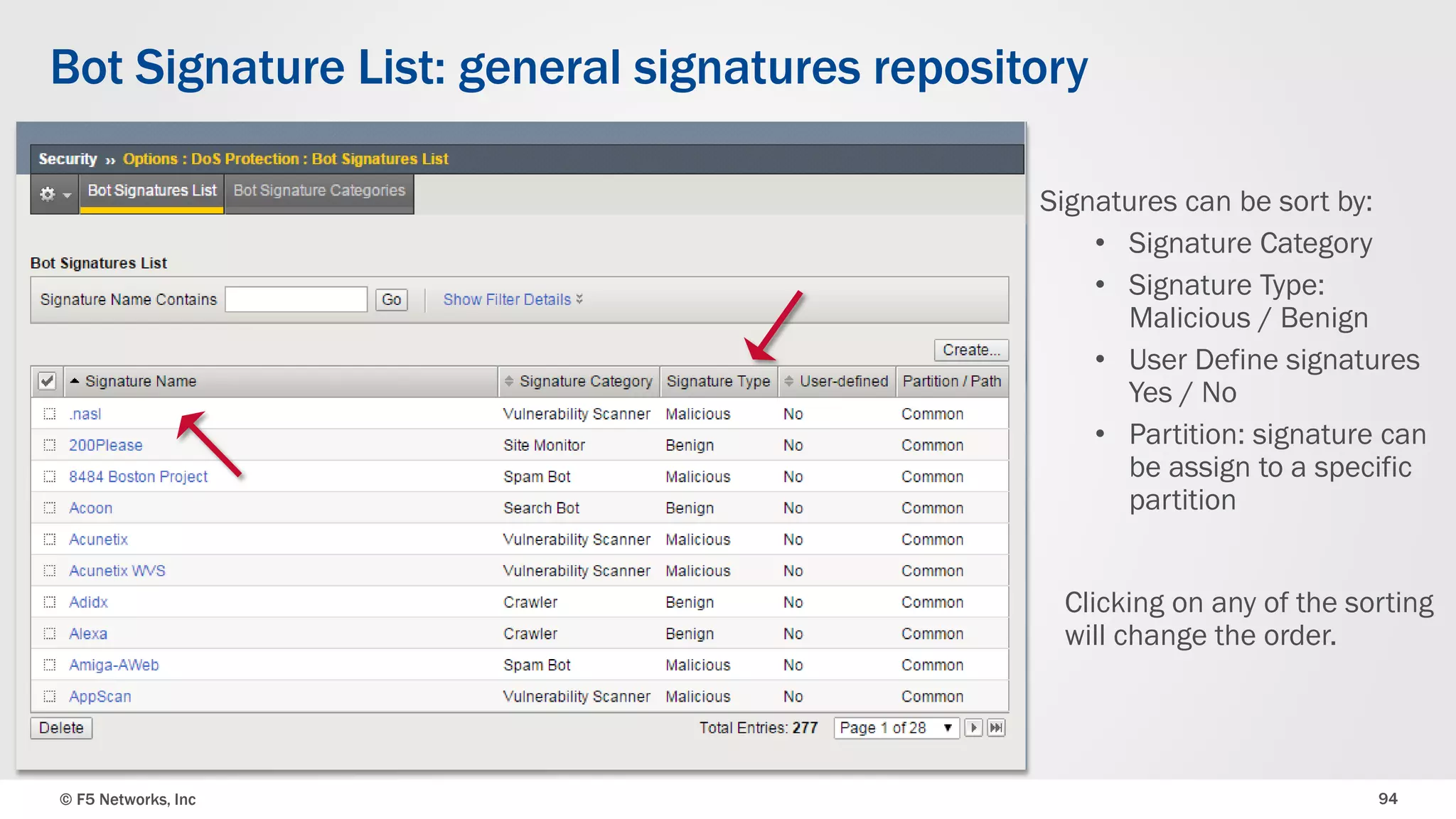
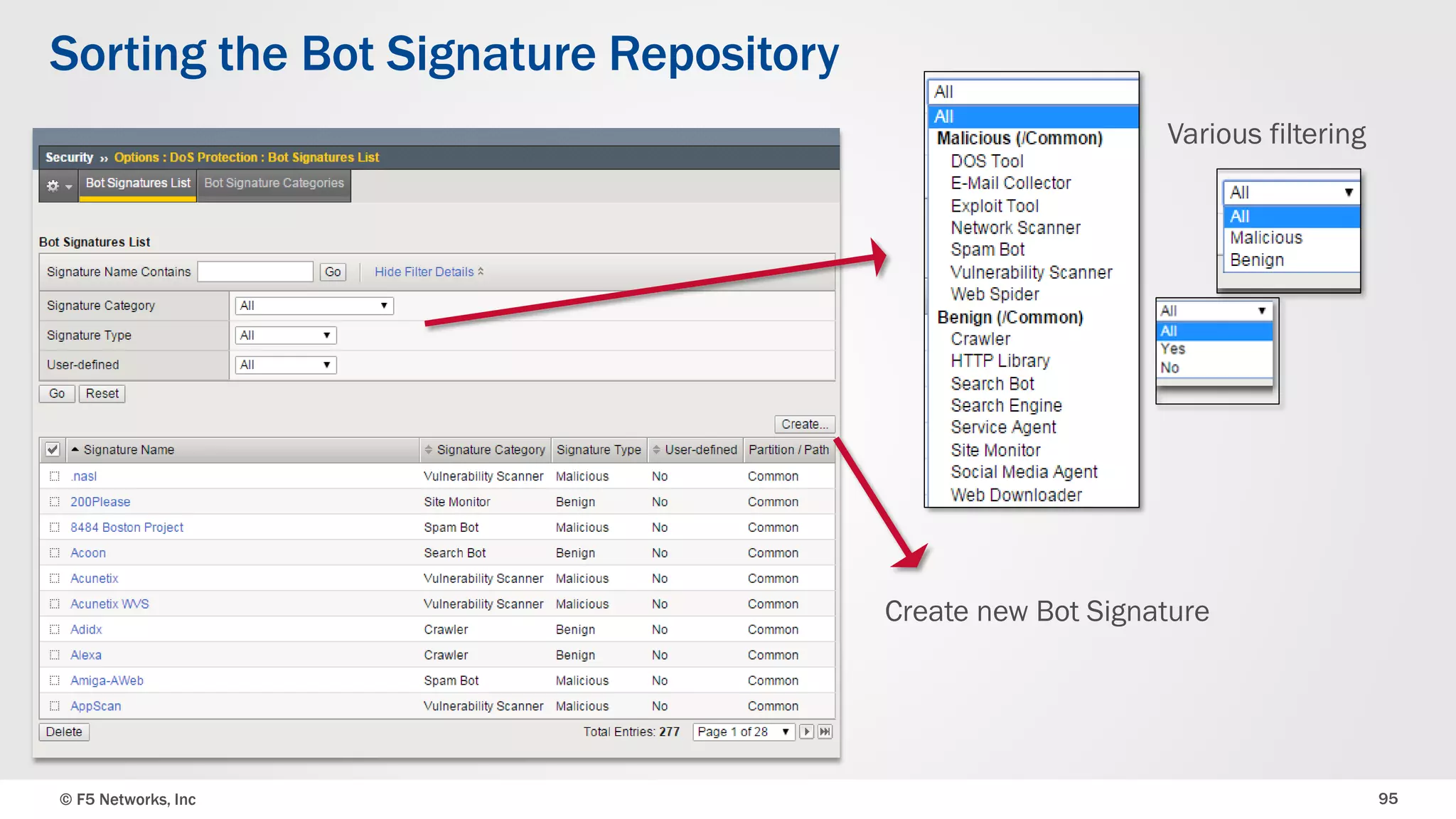
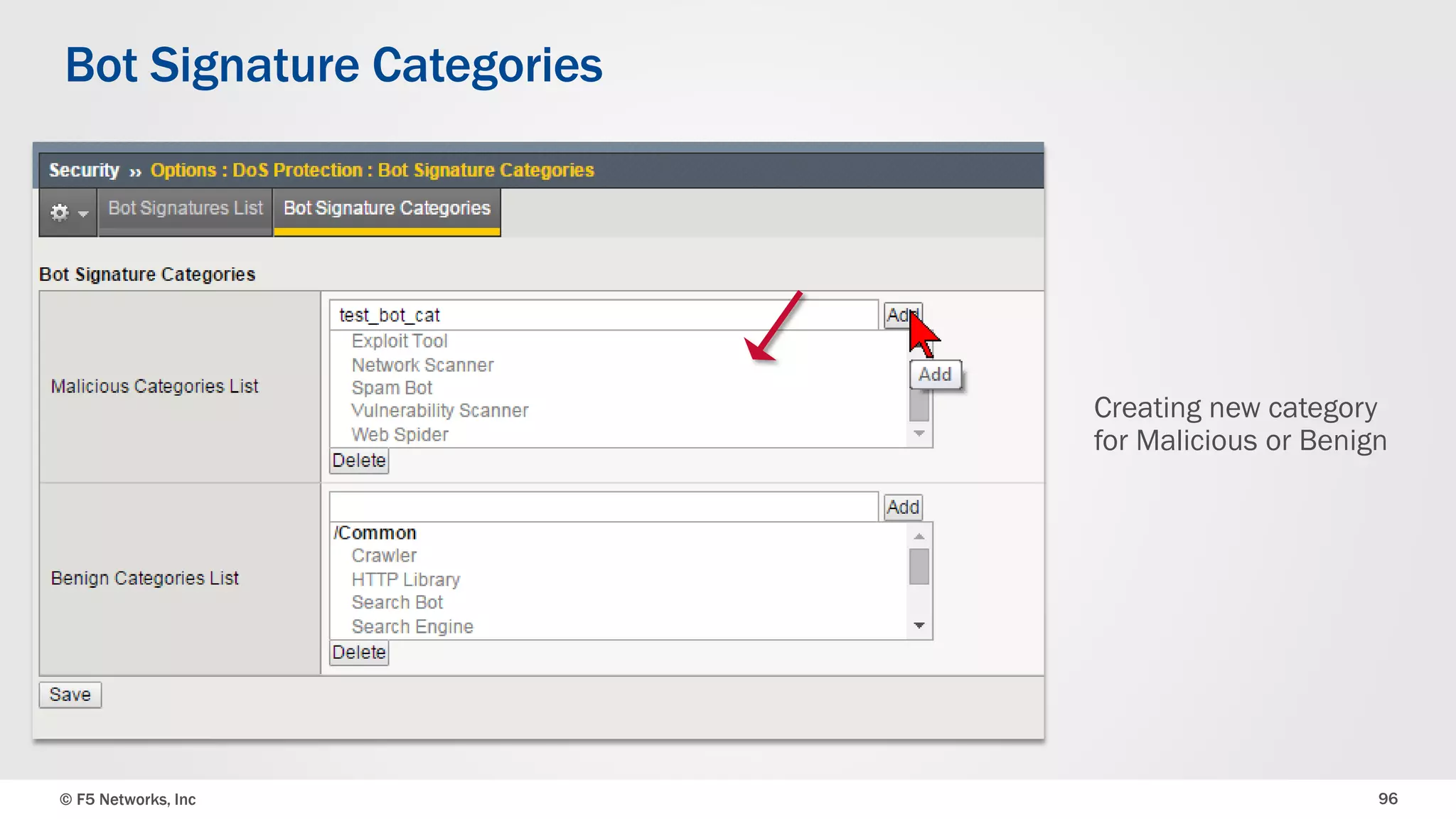
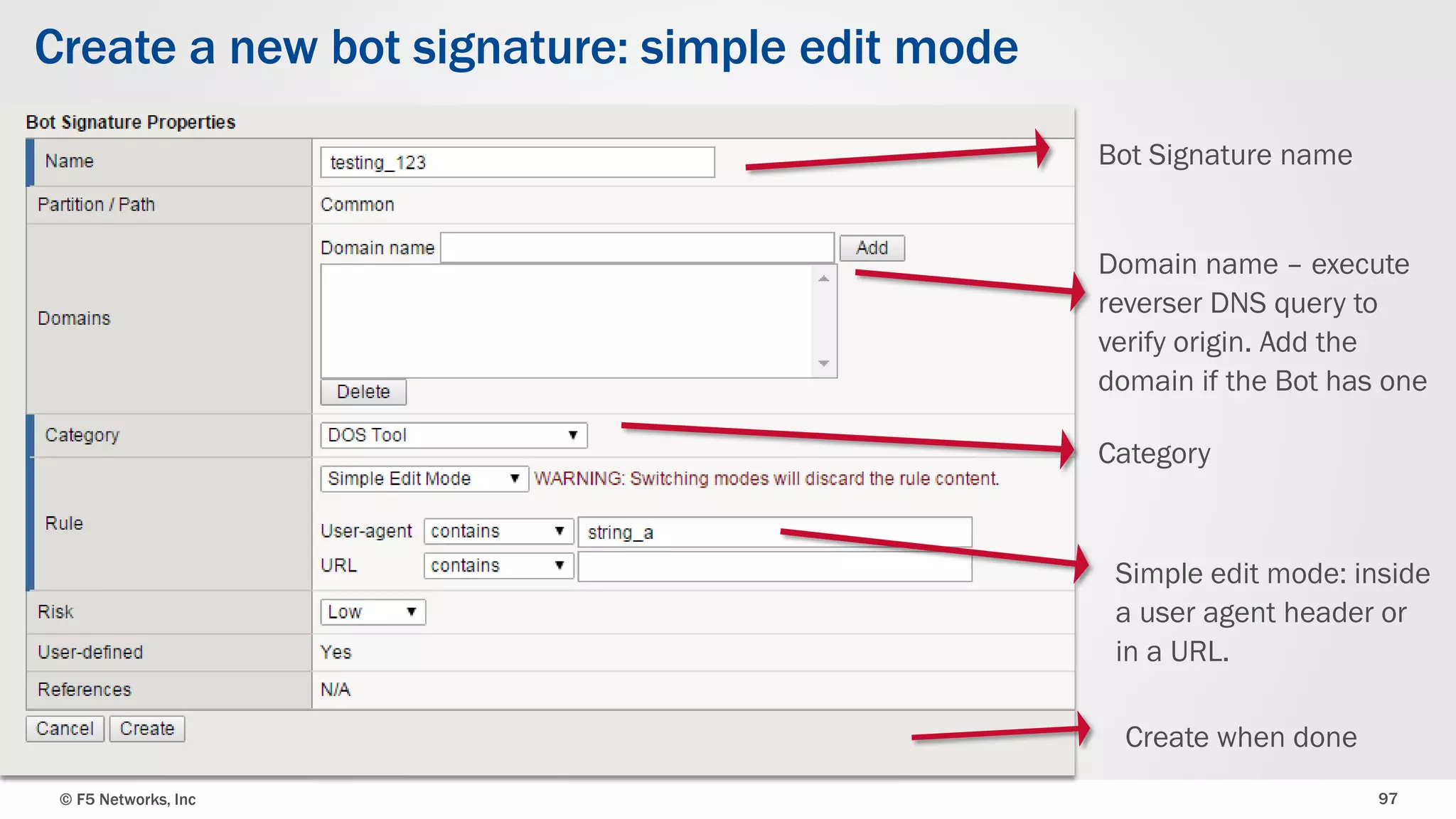
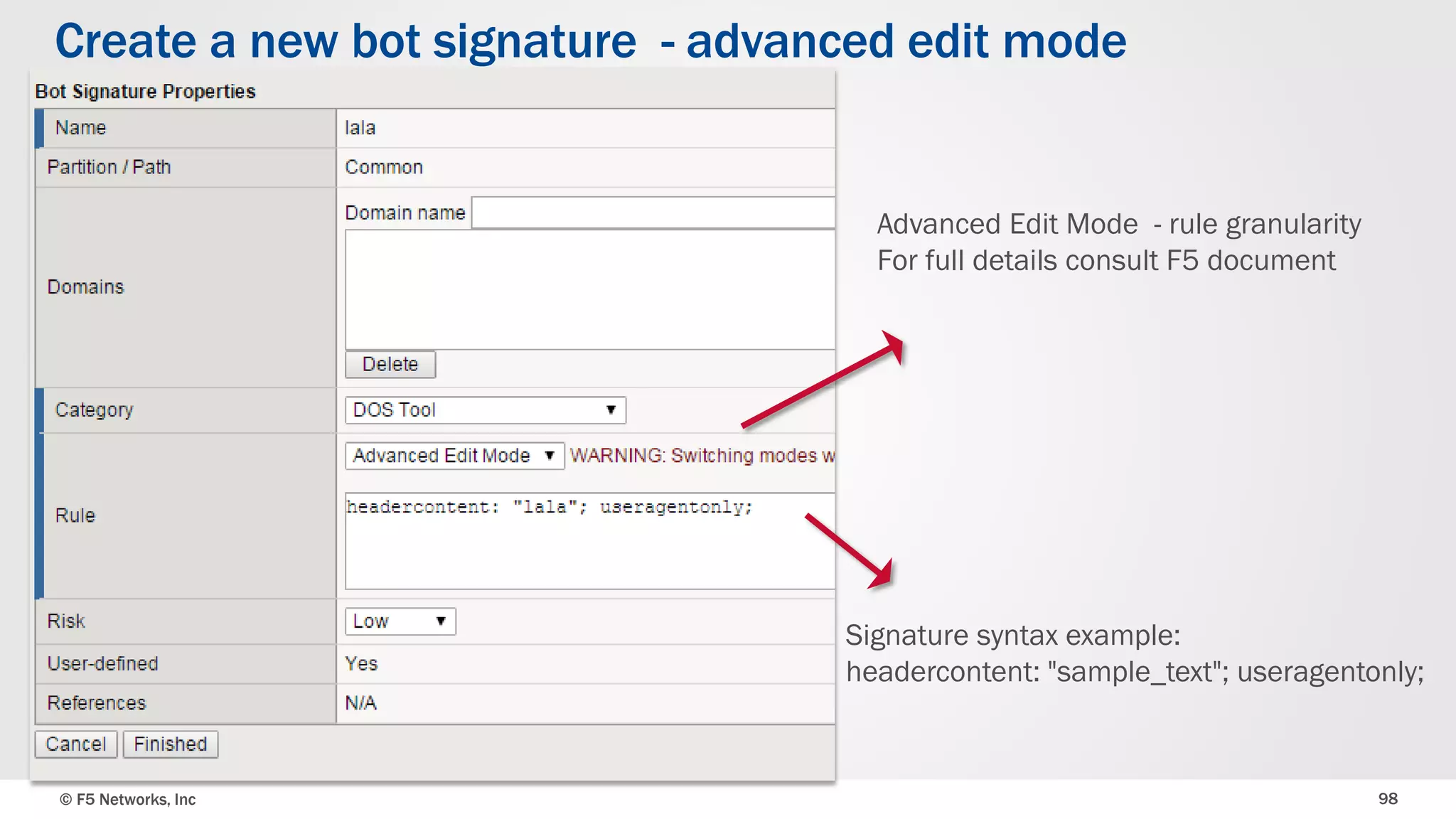
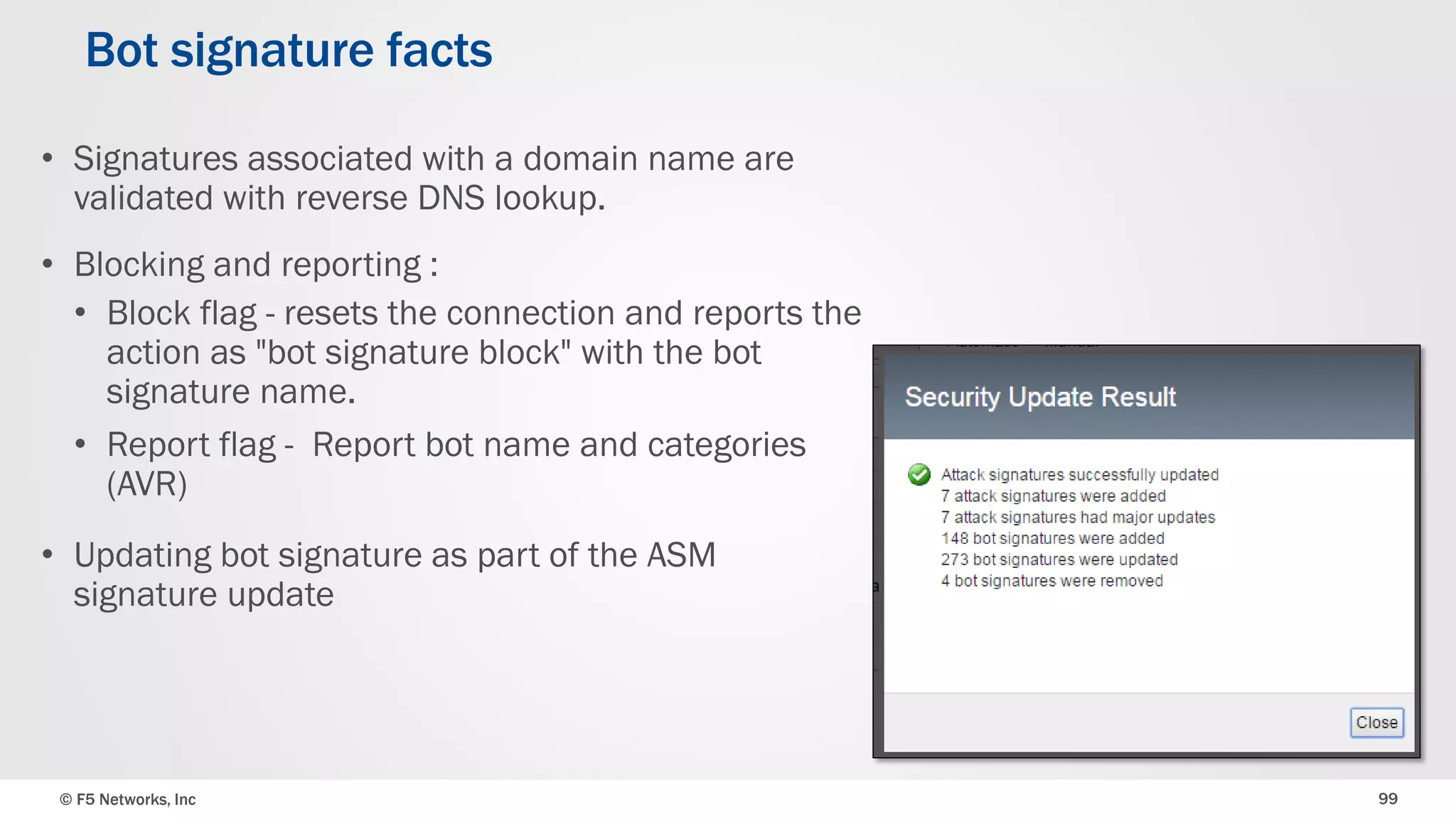
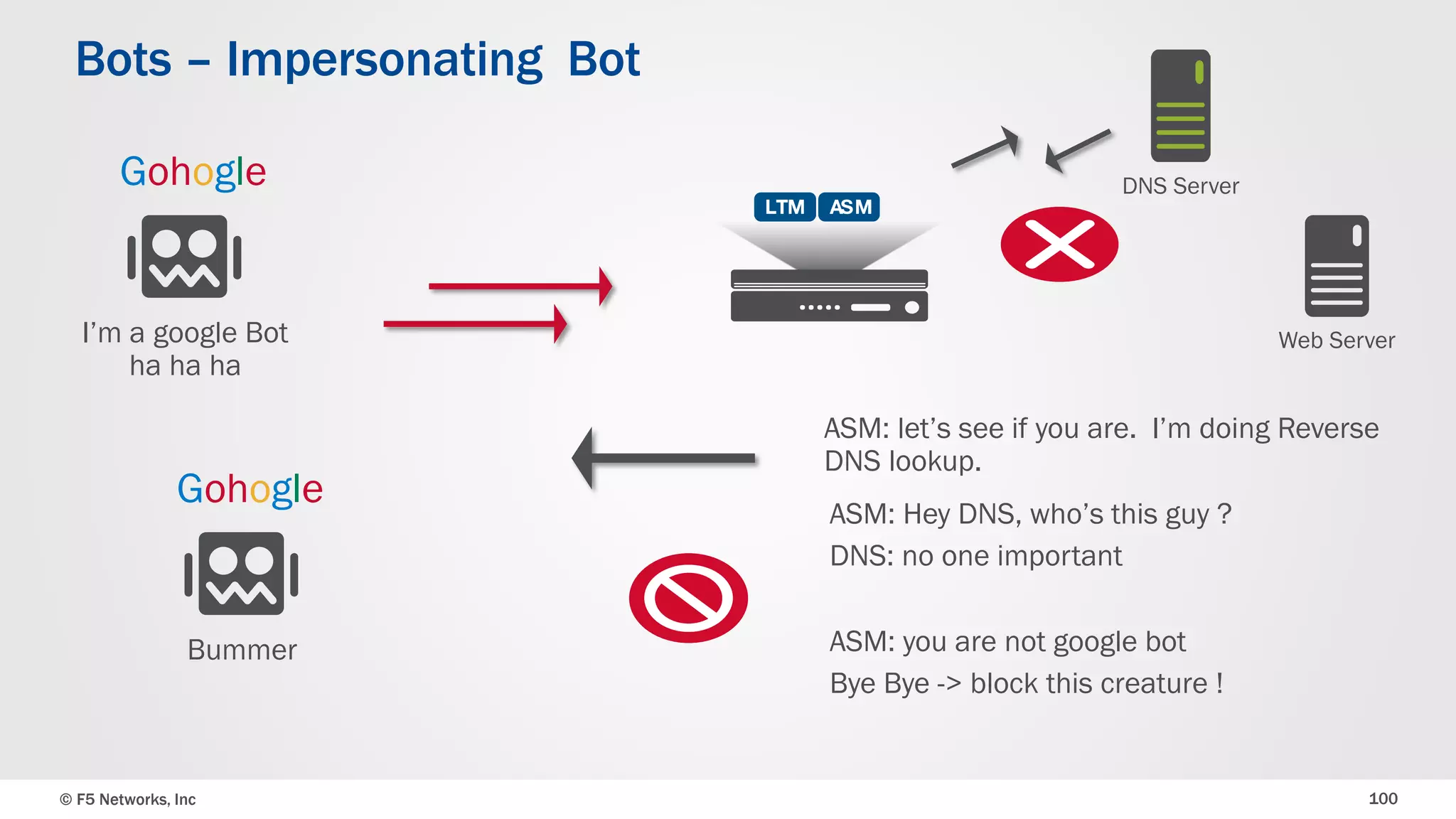
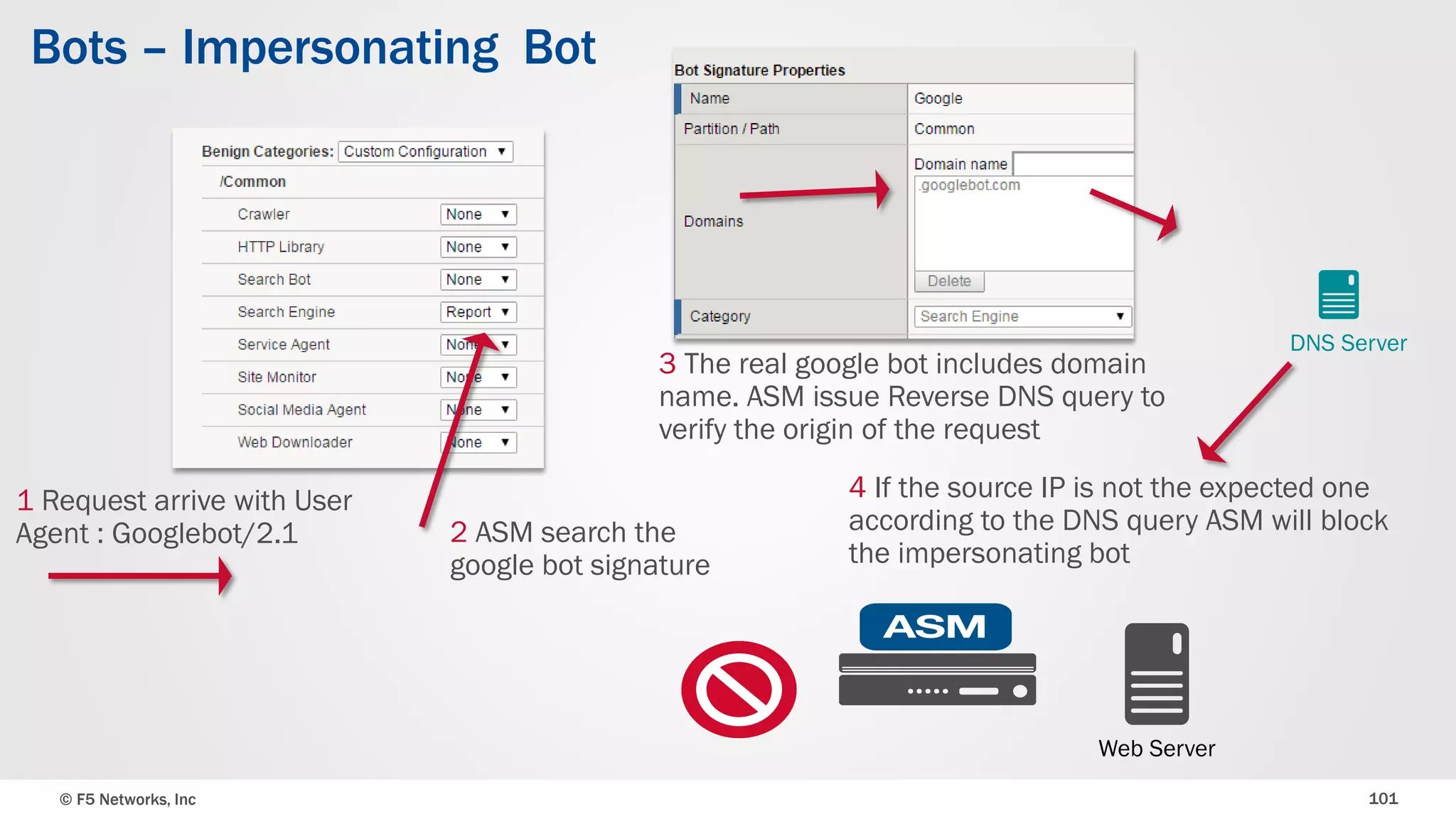
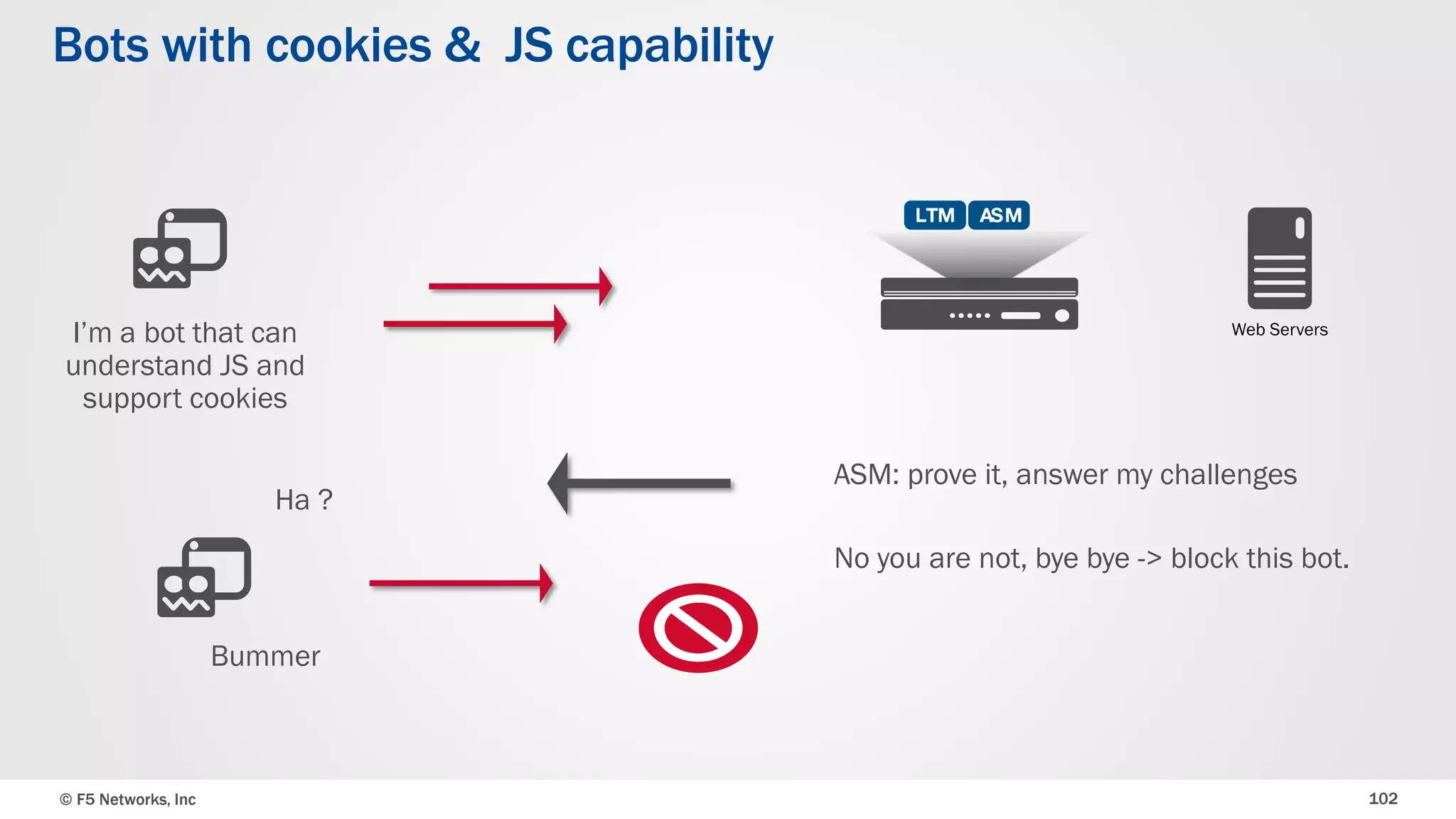
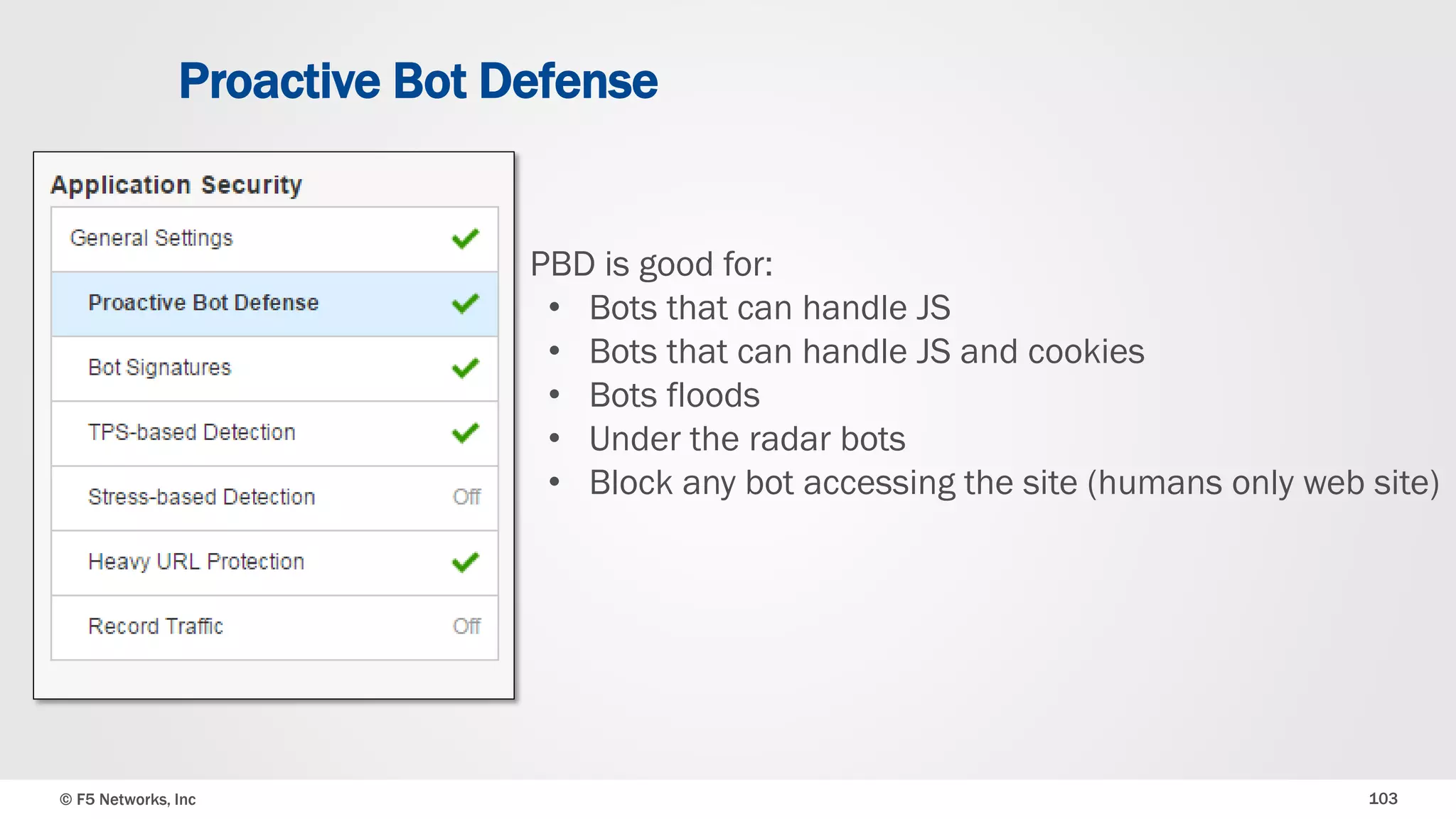
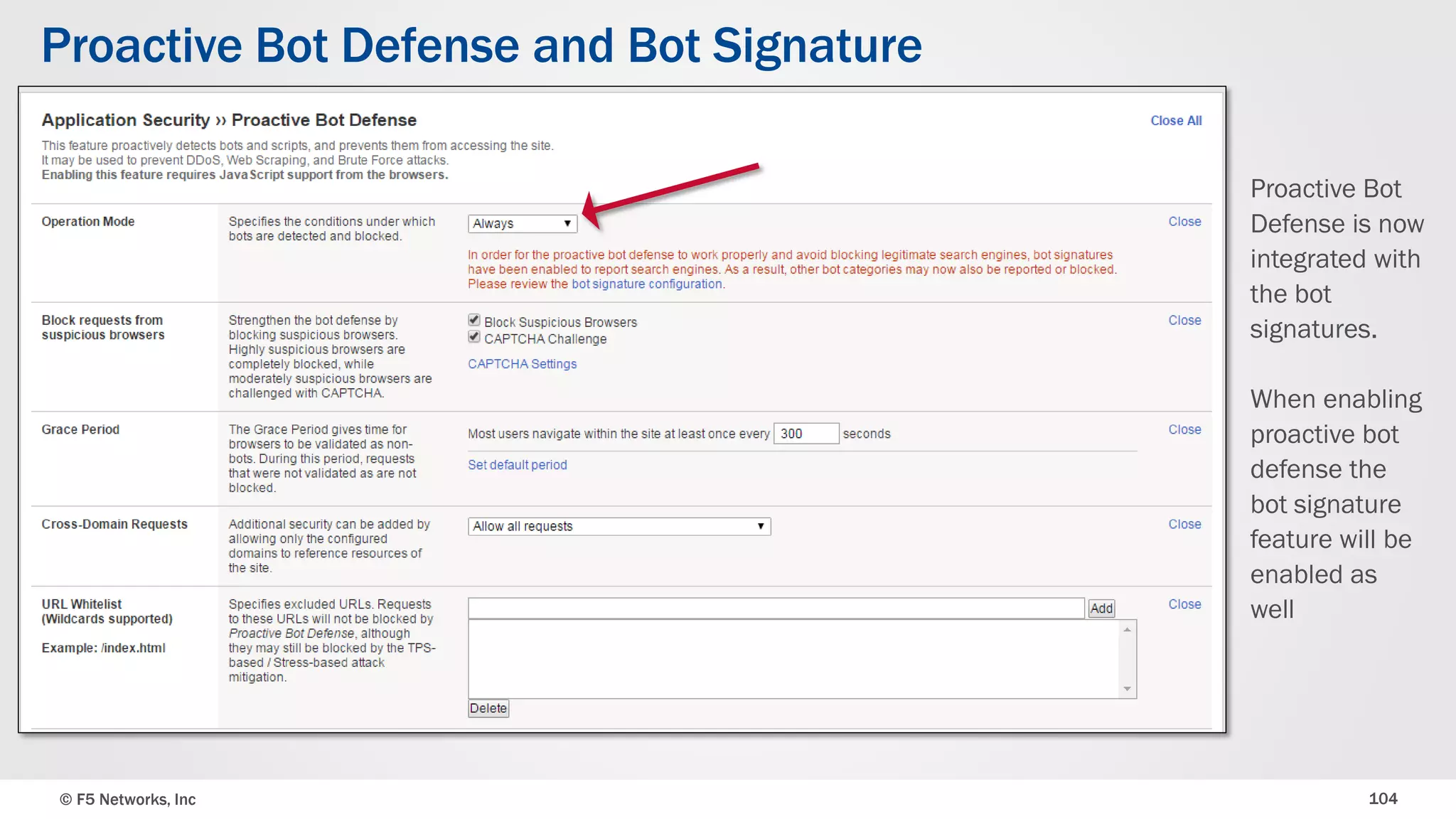
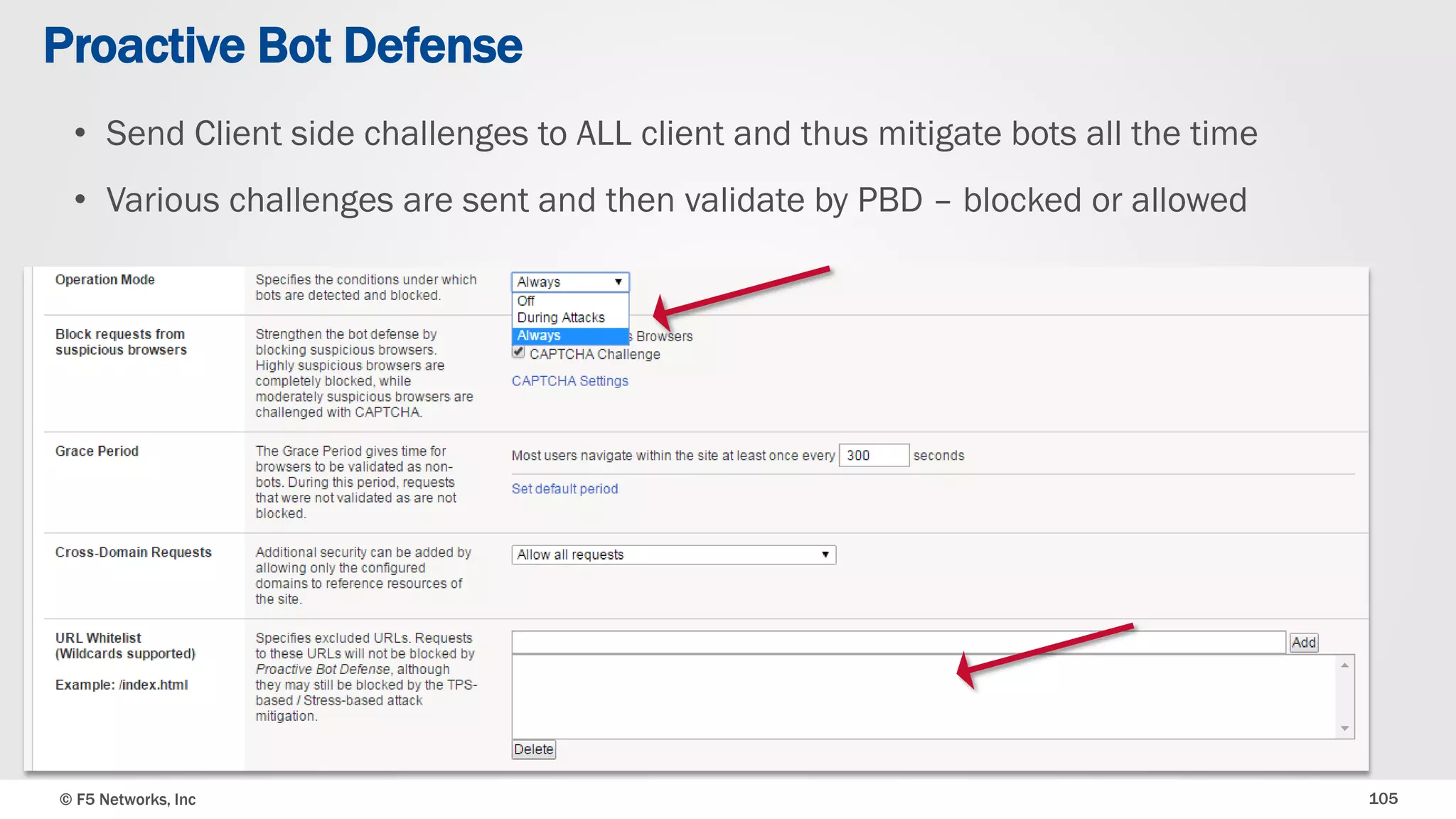
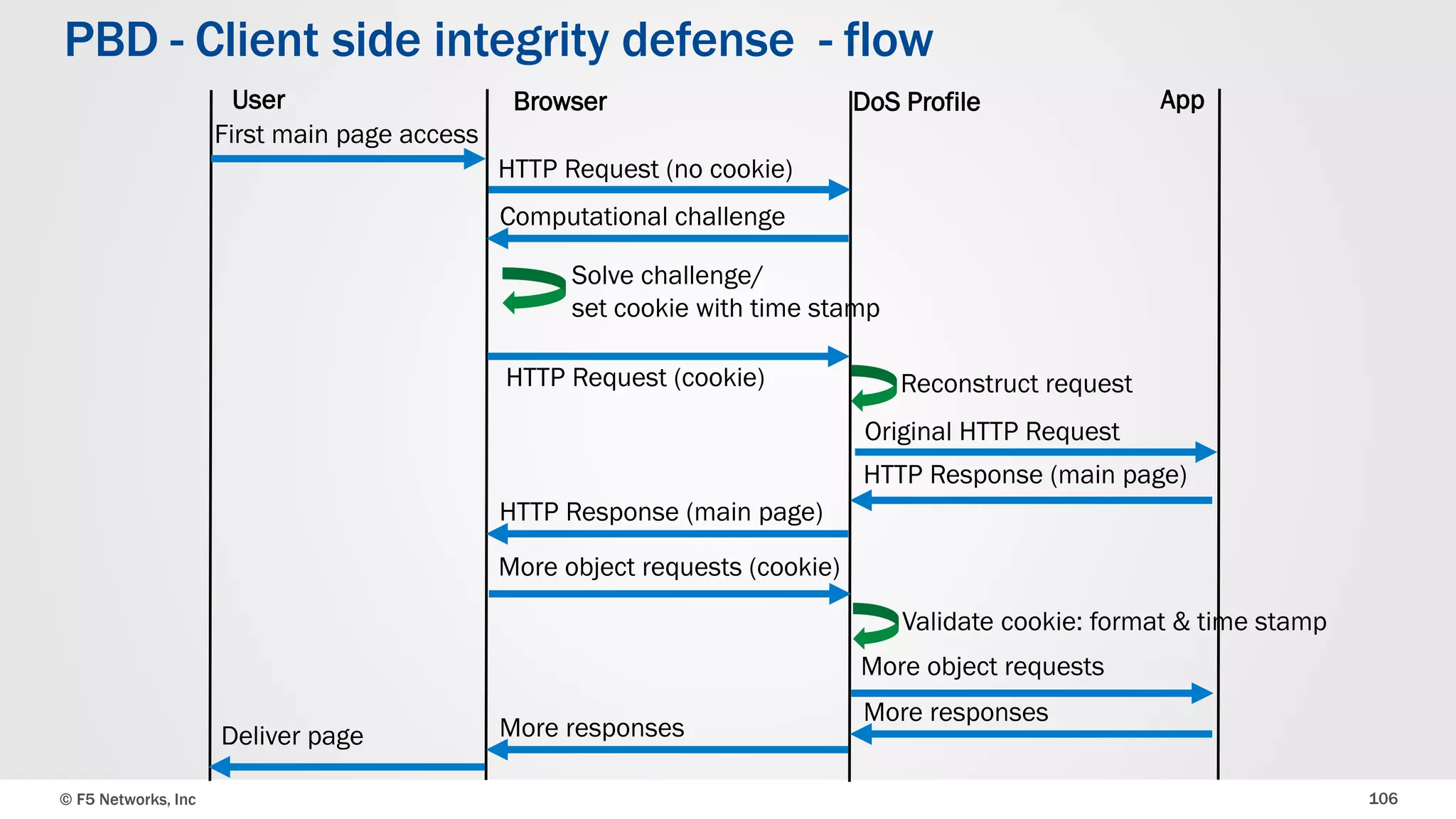
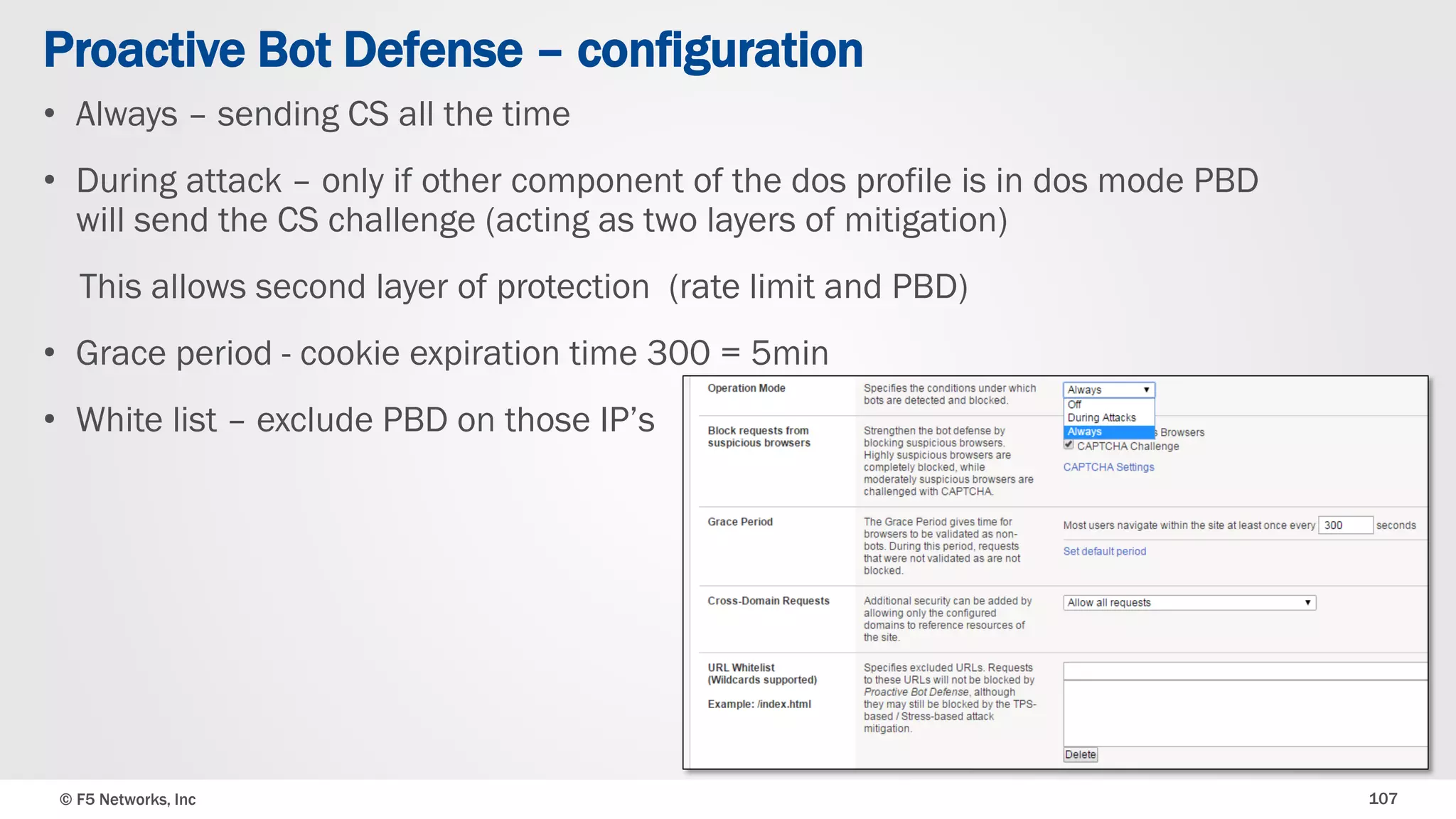
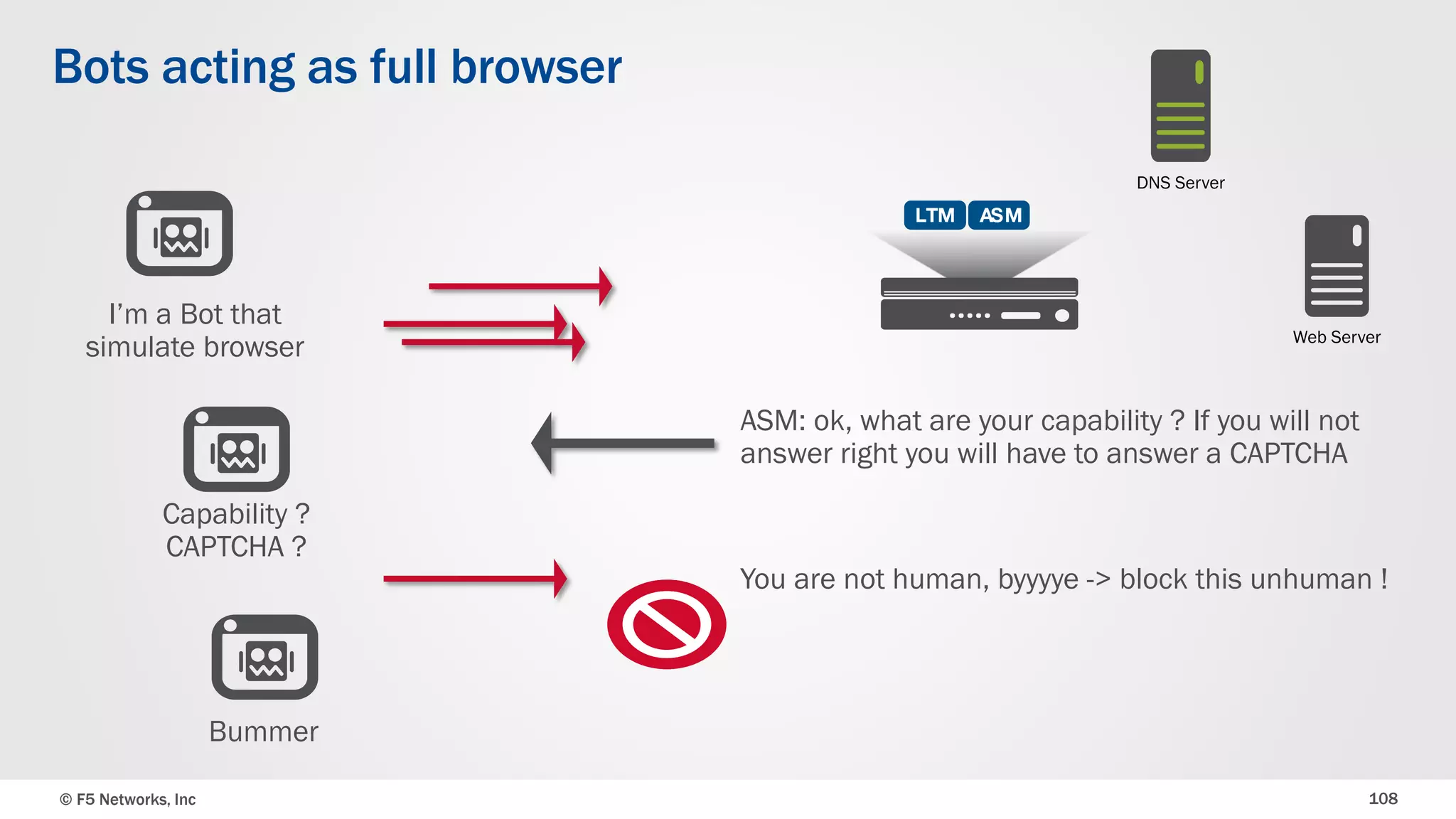
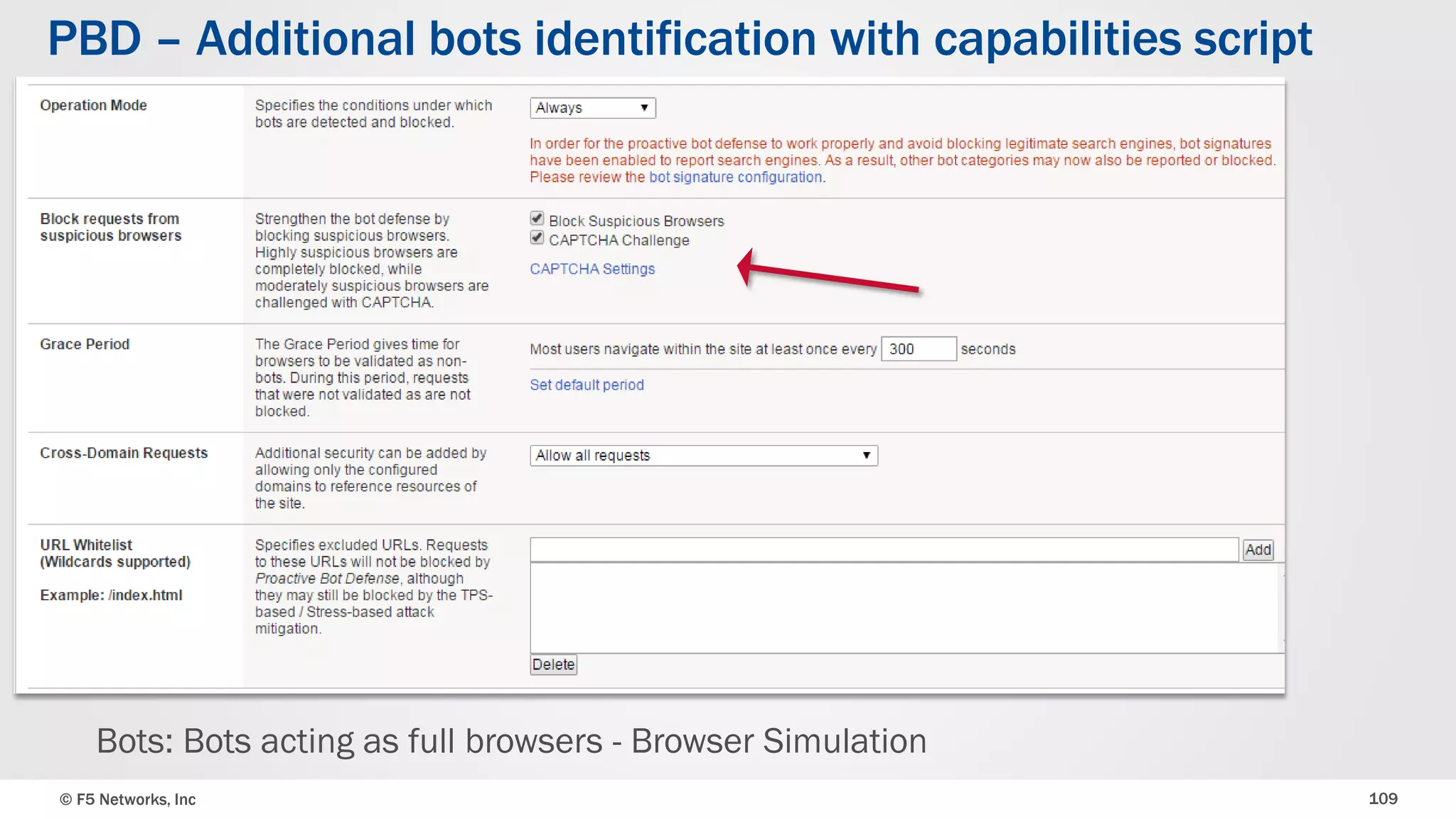
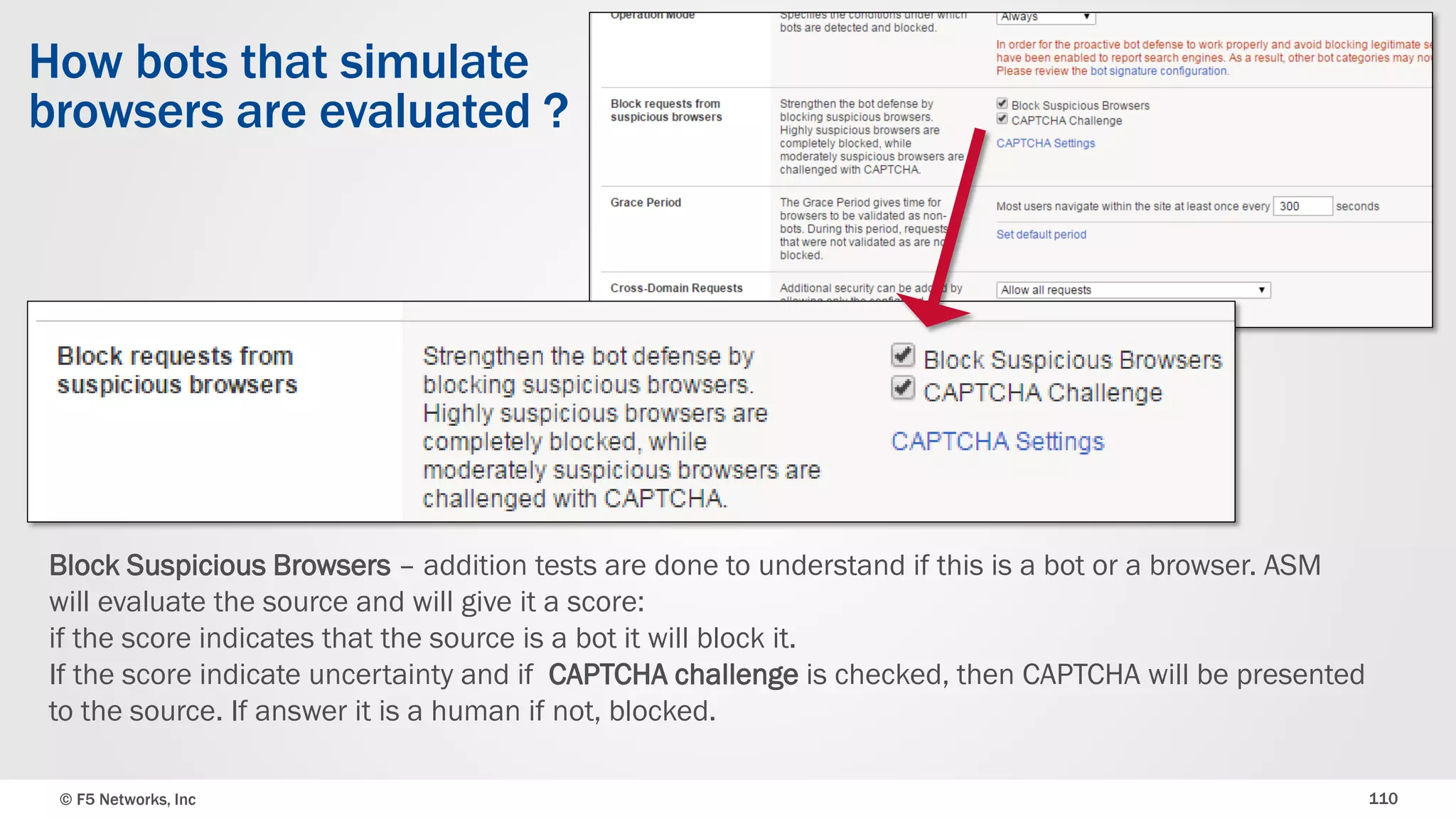
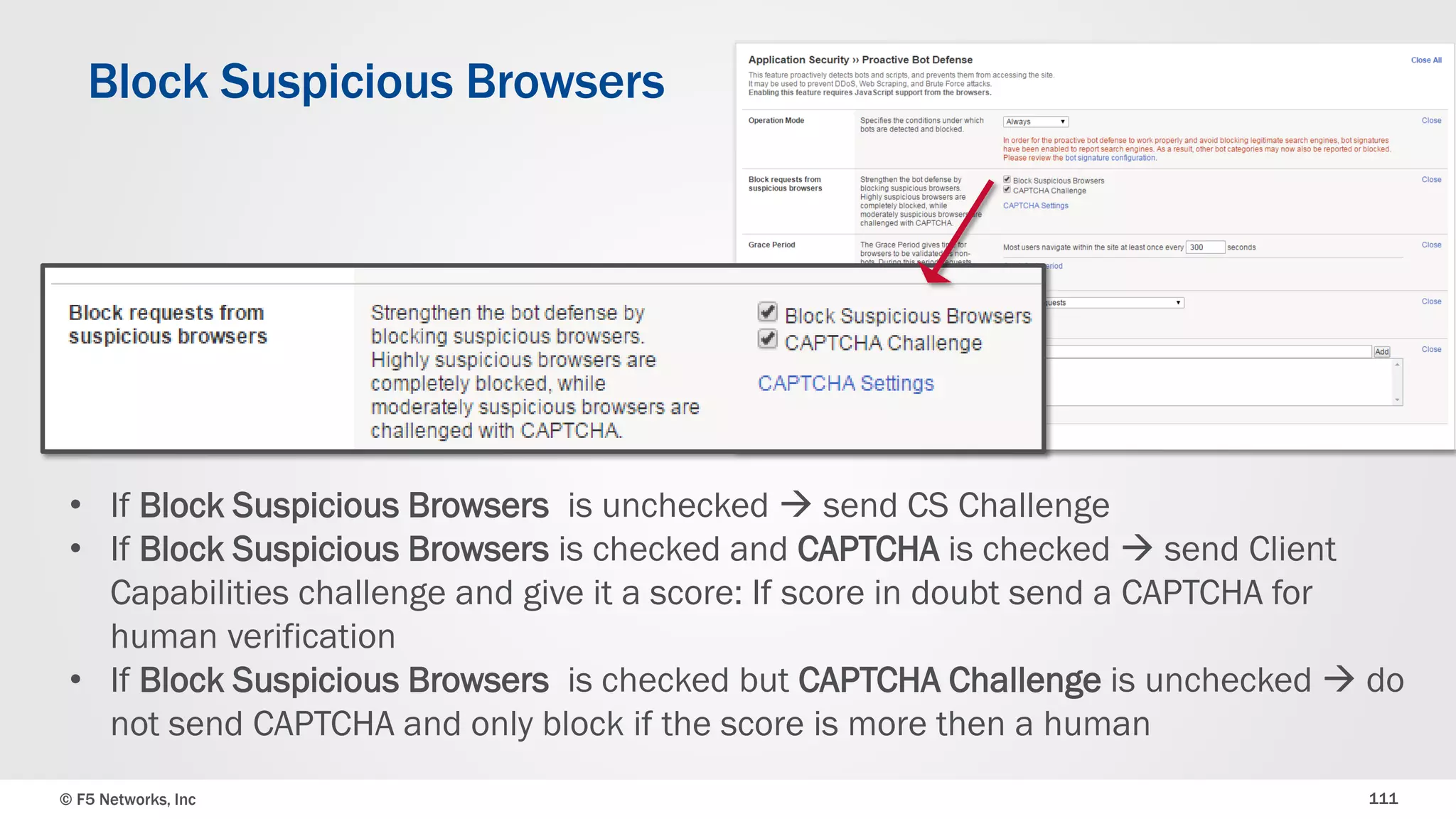
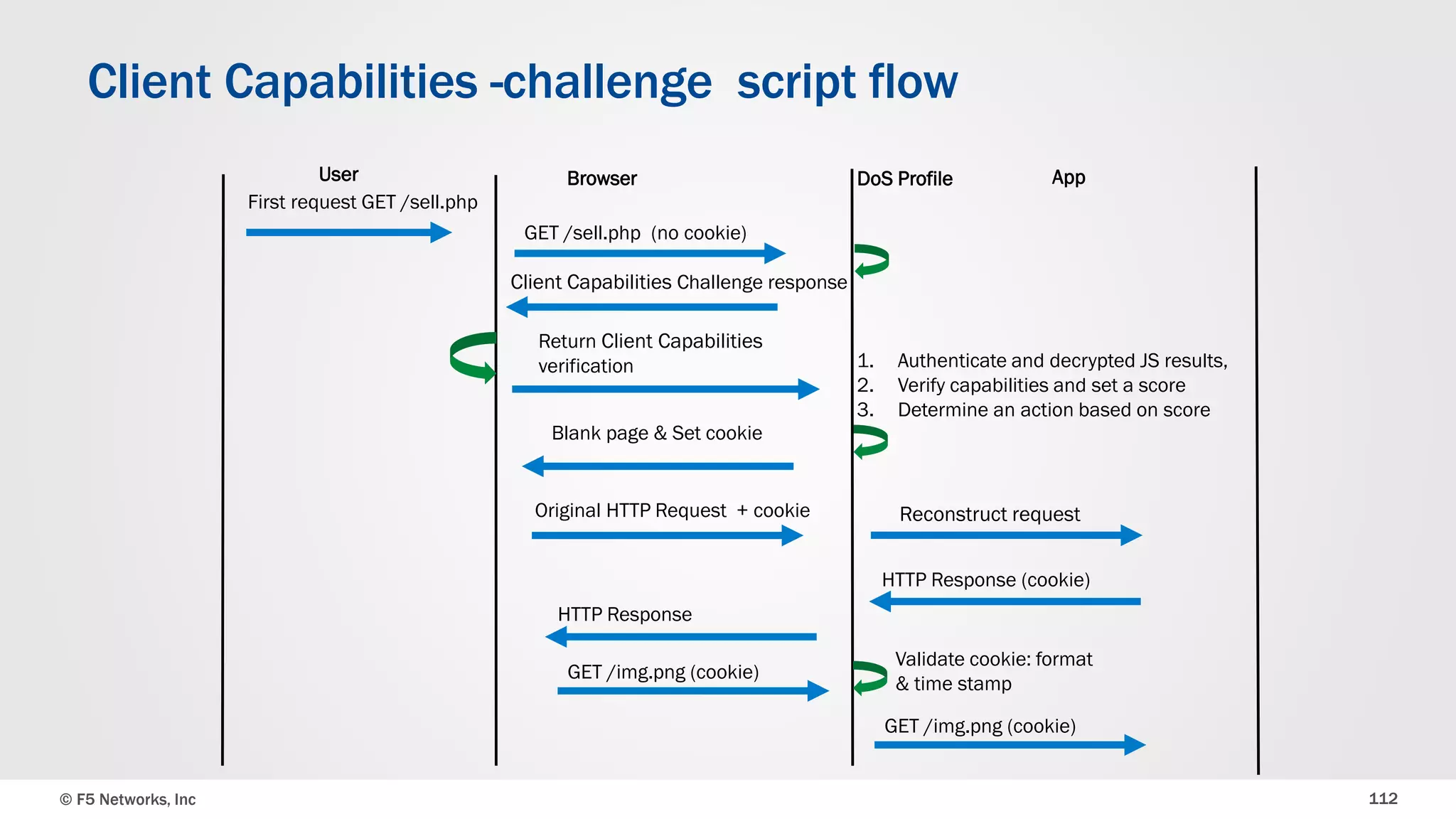
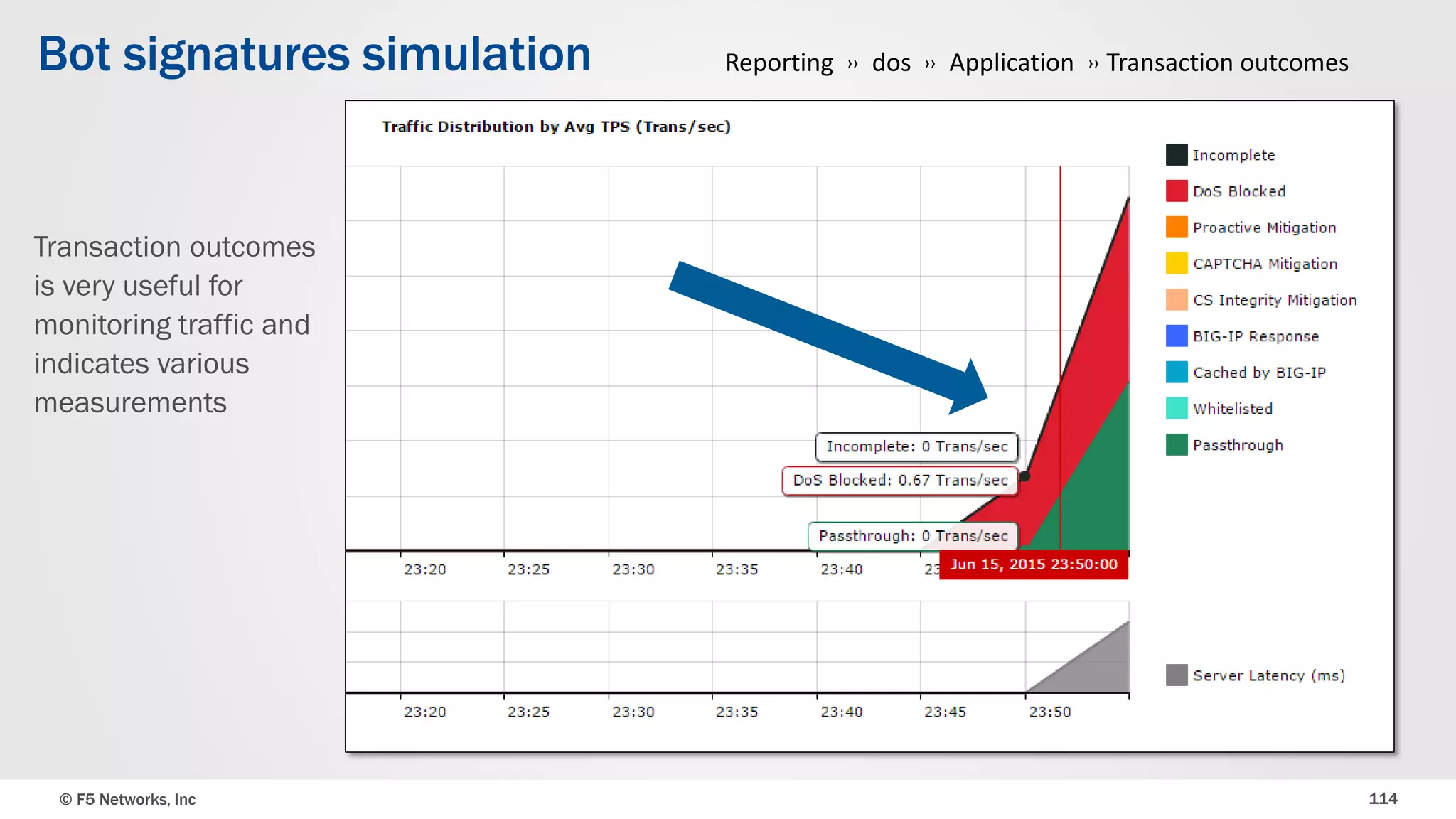
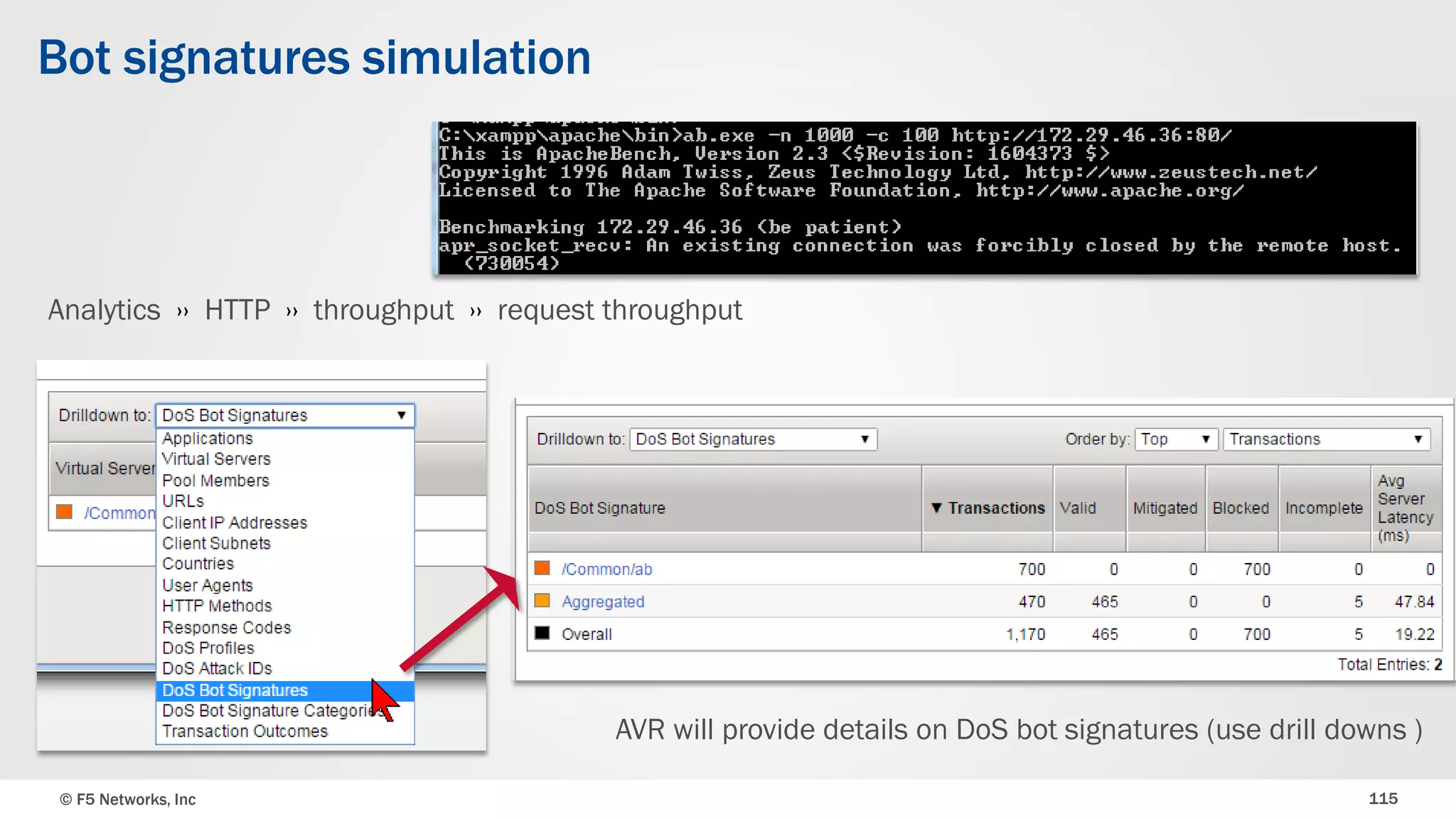
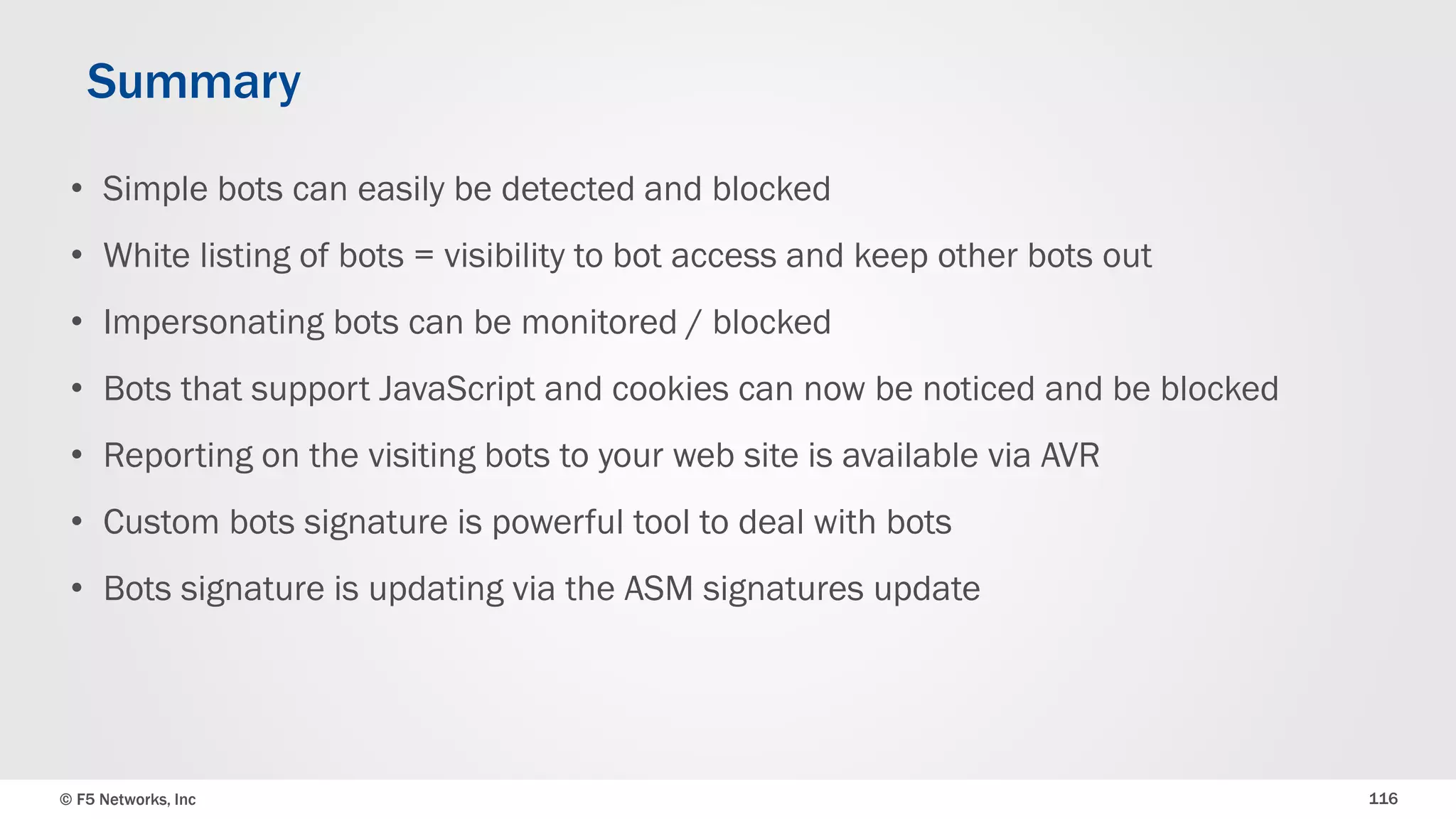
The document discusses the implementation of DDoS protection profiles within the F5 BIG-IP Application Security Manager (ASM), focusing on detection and mitigation strategies for HTTP flood attacks, including the use of various methodologies such as transaction per second (TPS) monitoring, client-side integrity defense, CAPTCHA challenges, and request blocking. It outlines the types of DDoS attacks, detection criteria, and customizable mitigation policies, with emphasis on the importance of accurately distinguishing between legitimate users and malicious bots. Additionally, it touches on geolocation-based detection and the significance of monitoring site-wide traffic during attacks.