Embed presentation








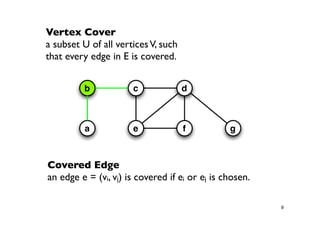

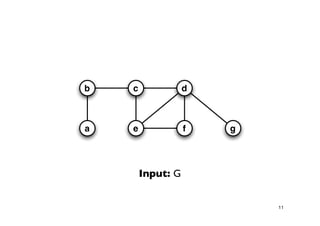
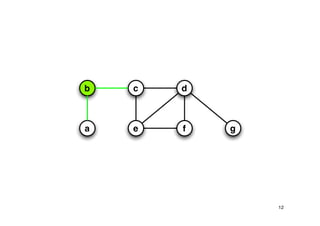
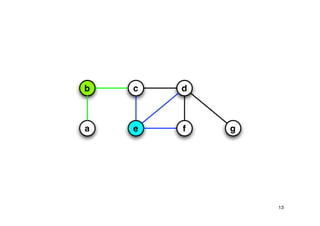
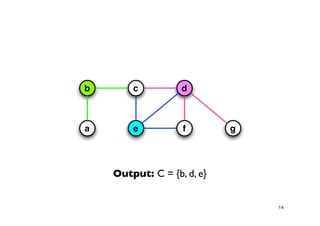

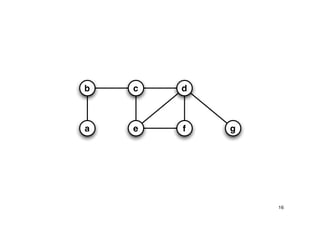
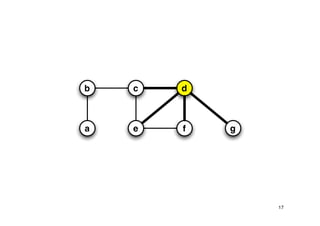
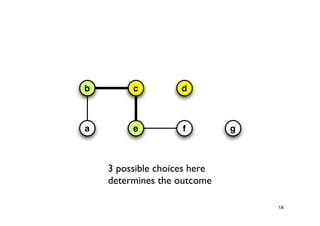
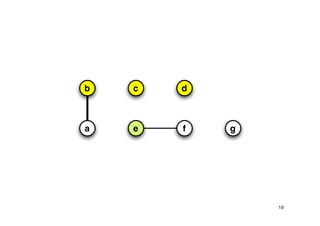
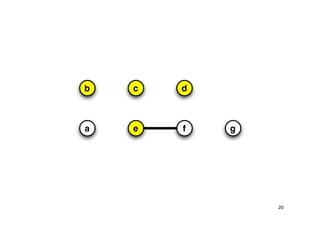
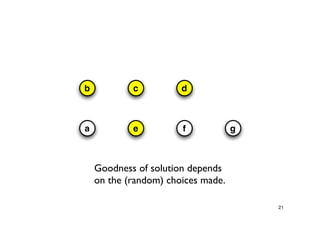

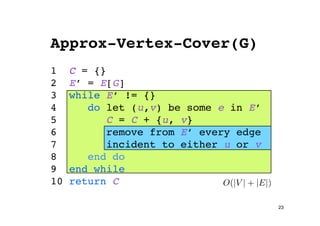
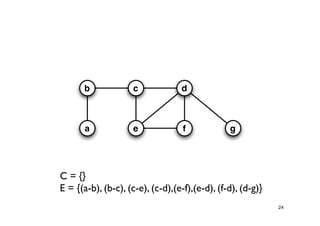
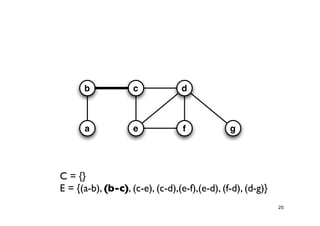
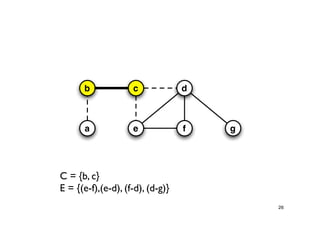
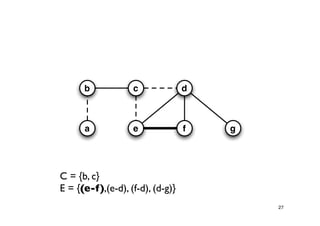
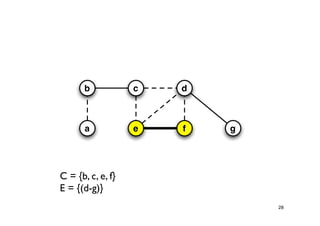
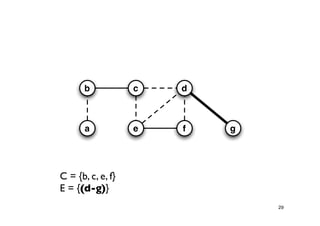
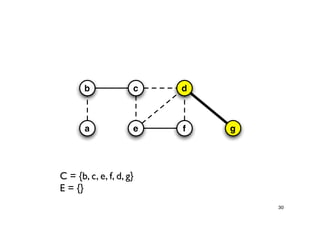
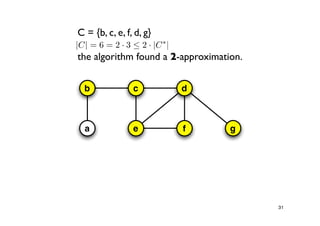


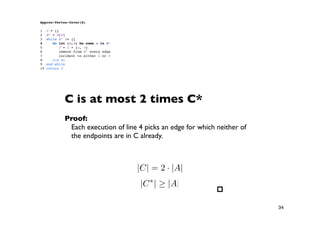

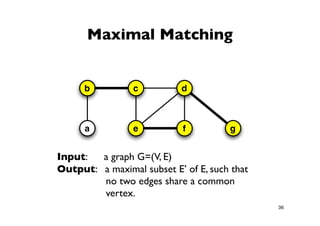

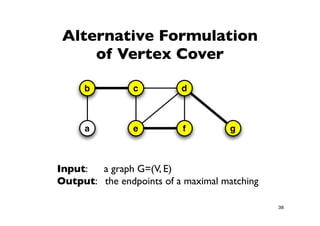

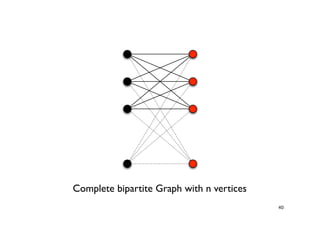
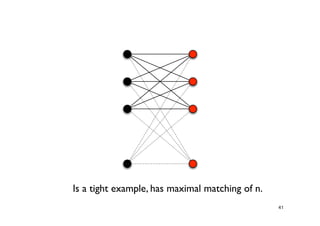
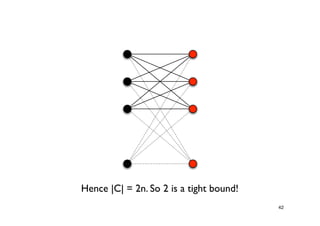




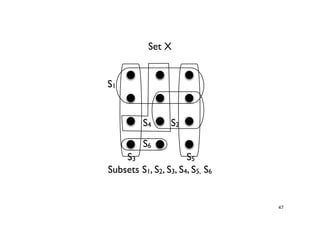
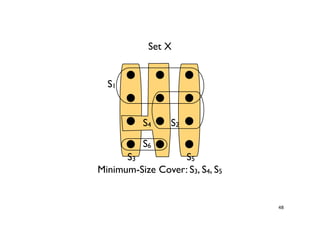






The document discusses approximation algorithms for NP-complete problems. It introduces the idea of finding near-optimal solutions in polynomial time for problems where optimal solutions cannot be found efficiently. It provides examples of the vertex cover problem and set cover problem, describing greedy approximation algorithms that provide performance guarantees for finding near-optimal solutions for these problems. The document also discusses some open questions around whether these approximation ratios can be improved.




















































